Devices and Components Commonly Found in the Remote Access Domain
The Remote Access Domain provides access to remote users and remote resources. It exists, in part, to provide a secure way to exchange data with remote components without sacrificing data privacy. This domain consists of several components that work together with your wide area network (WAN) to ensure that your data are private and your environment is compliant. Figure 13-2 shows the devices and components commonly found in the Remote Access Domain.
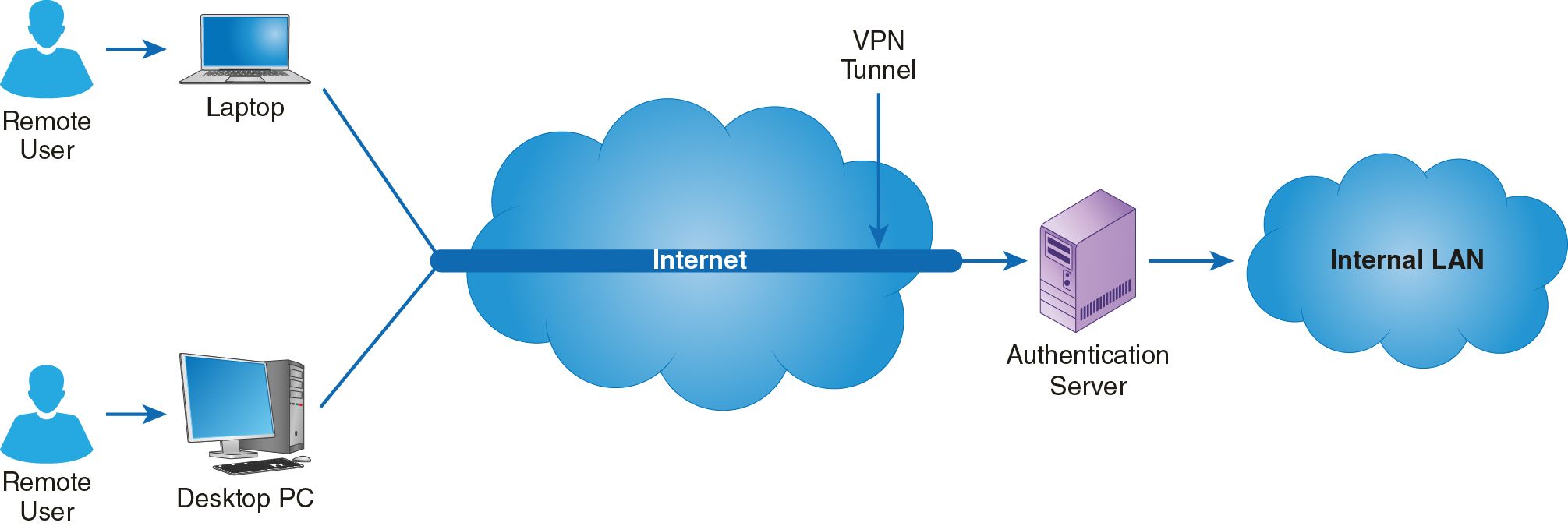
FIGURE 13-2 Devices and components are commonly found in the Remote Access Domain.
Control system architectures are different in the sense that in flat networks users would have access across the entire infrastructure. Access was limited by application layers. In a controlled network, when a system does not have adequate access control capability, added protection is provided by limiting network traffic. For example, network firewalls protect systems from inbound communications by preventing all communication methods except those required for the desired functionality.
The following list describes the commonly found security controls required from any system to protect access to critical resources, services, data, or communications. Every system in the chain of communication between a remote user and the end target host should pass through these controls.
-
Identity establishment—Controls to provide and exchange unique identities
-
Identity validation—A control designed to ensure the identity of each party
-
Roles (optional)—Groups of users or systems organized according to their responsibilities
-
Entitlements—Lists of access rules that govern which groups and individuals are allowed access to certain resources at what times
Remote Users
Remote users refer to enable individuals to access systems where they are not physically capable to connect directly through a tried connection to the network. Employees who traveled often needed to access data from the organization’s central database when they were away from the office. This example is a classic case for remote access. The classic solution to this need was to provide a modem or bank of modems attached to the internal network.
An audit should look broadly across the user population to determine who is remotely accessing the corporate network. Understanding the user population will also you to understand how data are handled. Let’s consider the following sampling user populations:
-
IT or security company employees—These users include people like domain admins, network admins, and others who typically access critical internal systems from inside the office.
-
Third-party hardware and software vendors—Third-party vendors for hardware and software typically require elevated privileges within targeted host systems to perform tasks.
-
Supply chain vendors—These remote users may need access to the network to monitor inventory and have access to financial and forecast data.
-
Services vendors—Vendors that provide specific services such as human resources, legal, and payroll may require access to specific business applications.
-
Consultants—Businesses will sometimes need privileged access to support special projects or deliver custom code to be tested.
It’s important to assess remote users’ access needs based on their roles. In each role an audit should ensure policies are adequate, appropriate management oversight exists, monitoring is in place, and compliance to policies is enforced.
Remote user access should require a higher standard of care than local user access. Local users enjoy the additional protection of the local environment and its security controls to protect data. Remote users do not have these additional layers of protection. You must ensure that your users agree to comply with your remote access AUP and that you have sufficient controls in place to protect the security of your data even in remote locations.
Remote Workstations or Laptops
The user’s computer, laptop, or other device becomes the remote device. Remote devices aren’t special devices— they just have the ability to connect to a WAN and establish a connection to some other resource. In fact, more and more tablets and smartphones are used as remote devices to access corporate email and collaboration applications such as MS Teams.
Remote devices need two main capabilities to handle remote connections in a secure manner:
-
Remote devices must be able to handle encryption—The most common type of encryption used in remote access is the secure VPN. As long as your device supports the VPN you’ve chosen for remote access and can establish a secure connection, the device passes the first test.
-
Remote devices must be able to protect stored data—Even when using a VPN, the data get decrypted at the remote device. If your remote device can’t ensure data privacy through its own controls, it should not be allowed to retrieve or process your confidential data.
As computers and other devices mature, it is common to see VPN support and local data privacy protection as standard features. You can use operating system encryption or third-party utilities to encrypt data. Either way, most of today’s computers with recent operating systems already contain the ability to act as secure remote access devices.
Remote Access Controls and Tools
When it comes to remote access, organizations are concerned about flexibility, reliability, and speed. Wireless connections extend the flexibility to remote devices. Mobile devices and broadband are reliable. However, the speed and reliability with which they can access and exchange data depend on location and carrier. Much like cell phone coverage, mobile broadband coverage can be spotty.
This is one area in which security policies need to keep pace with technology and business requirements. Policies must be clear whether personal devices such as a smartphone should be permitted access to organization information.
The Remote Access Domain must include control standards that address VPN connections, multifactor authentication, and token use. For example, a VPN control standard may describe the security requirements for VPN and other remote access connections to the organization’s network.
It is the responsibility of employees with VPN privileges to ensure that unauthorized users are not allowed access to the organization’s internal networks. VPN use is to be controlled using either a one-time password authentication such as a token device or a public/private key system with a strong passphrase as described in the multifactor authentication to VPN standard.
Each of the following three core controls are included within the remote access environment:
-
Authentication—Controls that test the assertion that prove the identity of the remote user.
-
Authorization—Controls that grant authenticated users the appropriate and limited access.
-
Nonrepudiation—Controls that ensure the user cannot challenge their ownership which in this case is the activity performed during a remote access session. This is achieved through a combination of controls such as authentication with multifactor authentication and encrypted VPN tunnels.
Authentication Servers
The process in the previous section describes authentication for remote users. The two most common methods to authenticate remote users are RADIUS and TACACS+. Both rely on centralized authentication databases and servers to handle all remote users. Either of these approaches works well when there is a large number of remote users or you need to manage remote users in a central location.
RADIUS
Remote Authentication Dial In User Service (RADIUS) is a network protocol that supports remote connections by centralizing the management tasks for authentication, authorization, and accounting for computers to connect and access a network. RADIUS is a popular protocol that many network software and devices support and is often used by Internet service providers (ISPs) and large enterprises to manage access to their networks.
RADIUS is a client/server protocol that runs in the Application Layer and uses User Datagram Protocol (UDP) to transport authentication and control information. UDP is a core protocol of the Internet Protocol (IP) suite. It is a connectionless protocol, which provides no guarantee of delivery. Servers with RADIUS support that control access for remote users and devices communicate with the RADIUS server to authenticate devices and users before granting access. In addition to just granting access and authorizing actions, RADIUS records usage of network services for accounting purposes.
TACACS+
Terminal Access Controller Access-Control System Plus (TACACS+) is another network protocol that was developed by Cisco. TACACS+ has roots back to an earlier protocol, TACACS, but is entirely different. TACACS+ provides access control for remote networked computing devices using one or more centralized servers. TACACS+ is similar to RADIUS in that it provides authentication, authorization, and accounting services, but TACACS+ separates the authentication and authorization information. TACACS+ also uses TCP for more reliability.
One difference between RADIUS and TACACS+ is of interest in a discussion of security. RADIUS only encrypts the password when sending an access request packet to the server. TACACS+ encrypts the entire packet, making it a little harder to sniff data from a TACACS+ packet.
VPNs and Encryption
Remote users create a VPN tunnel connection to the organization network. This tunneling process ensures that your information will be encapsulated so that no one will be able to intercept, alter, or even monitor your activity. Tunneling does more than just hide and tunnel your data from the rest of the Internet. Data in transit are more vulnerable to attacks as the data will travel outside the protected network. The VPN and associated tunnel solve this problem by sending all traffic through the encrypted tunnel.
A VPN is cost-effective by replacing more expensive dedicated point-to-point links. Using a VPN over existing Internet connections adds no additional cost. Two types of VPN are commonly used, and both are secured but require different implementation approaches.
-
Site-to-site VPN—Typically used to connect two or more offices. The VPN connection is typically established between two firewalls and remains up constantly.
-
Remote access VPN—Typically used by remote users. The connection is typically established manually through the users’ laptop or desktop. This would be the type of connection used by employees working from home.
In both these connections the system administrator can choose one of two types of tunnels to be used as follows:
-
Full tunnel—All traffic coming from the employee’s device will go directly to the corporate firewall. This is a completely secured implementation as all the security services of the firewall will be applied to all the traffic coming out from the employee’s device.
-
Split tunnel—Part of the traffic will be encrypted, and part will be sent through the public network. The traffic will be split based on its purpose. A split VPN tunnel is inherently less secure.
ISP WAN Connections
One of the more common ways to establish remote connections is using the Internet. Because it is easy to establish Internet connections and the access points are numerous, it makes sense to at least consider it for your remote connections needs. Historically, there have been several issues that must be resolved to use the Internet as a remote access WAN:
-
Both sides of the connection must use the same WAN—When using the Internet as the WAN, all each side must do is establish an Internet connection. The LAN-to-WAN Domain already ensures your internal networks are connected to your WAN. All that is left is for the remote node to connect.
-
Encryption is an absolute necessity—This is because the Internet is a public use network. VPNs work well to transport data securely over the Internet.
-
Reliable access must be available for remote nodes—Internet access is becoming easier to find than ever before. Many Wi-Fi hotspots exist to enable computers and devices to connect to the Internet.
-
Remote connections must be fast enough to be usable—This requirement is one that will likely cause the most potential issues. Sometimes, especially in more remote areas, it is difficult to find high-speed Internet access. In such cases, it is important to provide access through low-bandwidth methods to ensure data availability.
Although the Internet might not be the fastest WAN, it is quickly becoming the most cost-effective medium and the easiest to use for remote connections.
