Remote Access Business Drivers
This dramatic shift that increased the remote workforce has multiple benefits for both the employer and employee. In understanding these benefits we also understand the potential risk. As the old saying goes, “there is no free lunch.” For each benefit, we need to consider the risk. For example, an employee may find the peace and quiet in a home office beneficial. At the same time, employees are less supervised and there is less informal collaboration. While everyone’s situation may be different, let’s consider the potential benefits outlined in Table 13-1.
TABLE 13-1 Employer and Employee Remote Access Potential Benefit
| Employer | Employee |
|---|---|
| Talent retention | Freedom and flexibility |
| Cost saving | Cost saving |
| Reduction in absenteeism | Time saved from not commuting |
| Loyalty | Location freedom |
| Productivity | Peace and quiet |
| Expanded talent pool | Less stress |
| Work-life balance | |
| Personalized environment |
The Remote Access Domain of a typical IT infrastructure contains the components that can bring your distributed environment together and make its resources available to remote users. When your organization provides this level of service, you are enabling remote users to operate more effectively and efficiently without requiring them to physically be at your main location. This capability is a benefit to users who are geographically separated from your physical resources, either permanently or temporarily. Your users can do their jobs from more locations if they can access your resources remotely. The Remote Access Domain provides the access path for your remote users. Figure 13-1 shows the Remote Access Domain in the context of the seven domains in the information technology (IT) infrastructure.
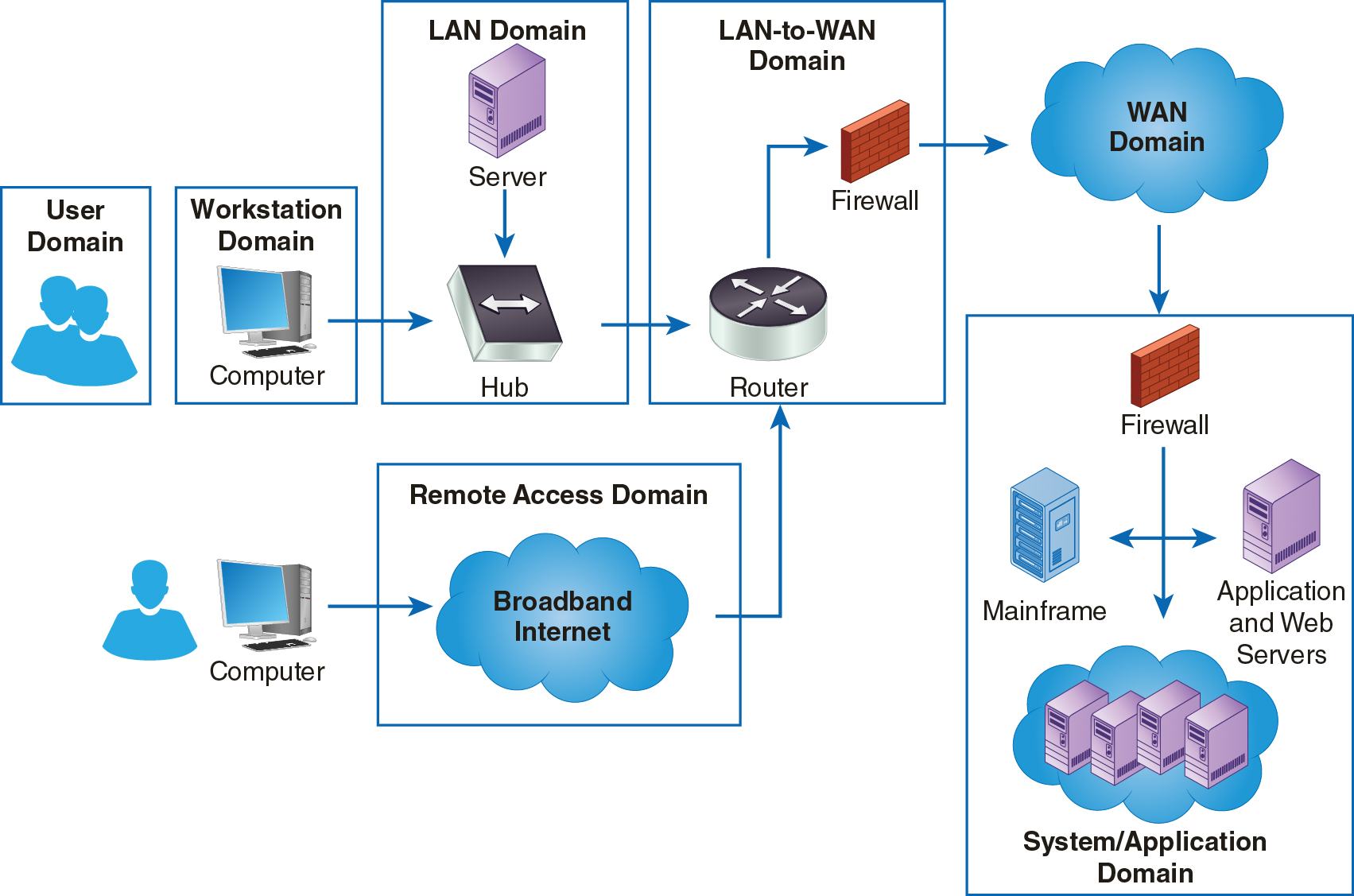
FIGURE 13-1 The Remote Access Domain within the seven domains of a typical IT infrastructure.
Take necessary steps to secure your data in all seven domains of the IT infrastructure. Distributing your data far from its secure storage locations exposes it to more threats of attack. You’ll likely need to show compliance with one or more requirements that directly address sensitive data sent to remote users. For example, the Health Insurance Portability and Accountability Act (HIPAA) requires controls to protect the privacy of medical data. The Payment Card Industry (PCI) requires credit card privacy controls. Many states require privacy controls on any personally identifiable data. These are only a few of the requirements you’ll need to satisfy when supporting remote users. Your security policy should include all the necessary elements to meet compliance requirements and support efficient and cost-effective operation. Making sure you have the proper controls in place to secure the Remote Access Domain is one important part of an overall plan for data security.
Protecting Data Privacy
A 2021 study from the Tessian Group reports that 48% of employees report being less likely to follow safe data practices while working from home. Additionally, 84% of technology leaders report concerns over the adequacy of data loss prevention controls for the remote workforce.
Assessing remote access monitoring and capability should be a priority given these new remote force realities and risks. Protecting data privacy and an organization starts with strong security controls and security assessment of potential vulnerabilities. The following are steps an organization should take to assess and improve remote access security:
-
Penetration testing—Test all connectivity points between the end user and the corporate network for vulnerabilities
-
Policy creation—Clear and concise policies and awareness training on what is permitted for remote work environments such as are allowed to print, secure material, and share with family a workspace
-
Remote device testing—Test samples of remote user devices for compliance with policies
-
Check protocols and authentication—Identify how users connect to the corporate network and access sensitive data; dual-factor authentication should be at a minimum the de facto standard
-
Governance—How are remote workers’ access with sensitive information monitored and policies enforced; what are the consequences for a noncompliance to following safe data practices
-
Logging and reporting—Ensure activities by remote devices are properly monitored and the ability to generate reports and audits required by its compliance obligations
Implementing Proper Security Controls for the Remote Access Domain
Implementing proper remote access controls makes good business sense. Equally important in many industries, it is required by law, and evidence will be required by regulators. Consider the Federal Financial Institutions Examination Council (FFIEC) examination handbook for the financial services industry. Section II.C.15(c) is dedicated to remote access. Specifically the regulatory guidance states:
Management should develop policies to ensure that remote access by employees, whether using institution or personally owned devices, is provided safely and soundly. Such policies and procedures should define how the institution provides remote access and the controls necessary to offer remote access securely.
The FFIEC guidance, as with many best practices frameworks, lays out a series of requirements. These regulatory requirements include the following control measures:
-
Disable remote unused communications.
-
Tightly control remote access through management approvals and subsequent audits.
-
Implement robust controls over configurations at both ends of the communication.
-
Implement remote connections to prevent potential malicious use.
-
Log and monitor all remote access communications.
-
Secure remote access devices.
-
Restrict remote access during specific times.
-
Limit the applications available for remote access.
-
Use robust authentication methods for access.
-
Use encryption to secure communications.
Notice the guidance in the second bullet requires audits of the remote access environment. A formal audit puts management on notice when any major defects are found in the form of audit issues. Additionally, notice the level of control the organization is expected to have of the end-user devices. This may include ensuring virus protection is installed and current, preventing users from installing software on the devices, as well as the use of firewalls, host-based intrusion detection system (IDS), and packet content filtering to identify, monitor, and limit remote access activities.
A secure connection between the remote user and the organization’s network will typically mean creating an encrypted point-to-point tunnel through the Internet. The most common form of remote access is through a virtual private network (VPN). The VPN provides an encrypted isolated “tunnel” or connection between a remote user’s computer and the internal network.
Although the most common security control in the Remote Access Domain is encryption, don’t forget the controls on remote users and the computers they use to access your network from a remote location. Remote users must adhere to your remote access acceptable use policy (AUP). Encryption can help protect your sensitive data, but a user who isn’t careful or a poorly secured laptop can leave the data vulnerable.
