In an ideal world, we would like to use the best technologies to countermeasure the risks to confidentiality, integrity, and availability. It is learned in the previous chapters that confidentiality is achieved by the use of encryption and the integrity of data can be inspected by the use of cryptographic hash functions. This chapter will look at another aspect of information and communication security, which is access control mechanism. Access control deals with the availability characteristic of security in the CIA model and refers to issues concerning access to system and network resources. There are actually four main parts to the access control mechanism. They are identification, authentication, authorization, and accounting.
In general, a typical approach to the management of information security is to analyze risks and to control or mitigate them through available security mechanisms. In this regard, access control, especially user identification and authentication, plays a vital role by ensuring the assurance of the user’s rights before they are granted access to computer and network resources.
This chapter provides the background knowledge of what authentication mechanism is and what authentication methods are available, before discussing possible threats that could provide dangers to such mechanisms.
What Is Authentication?
Suppose a computer and communication system consisting of hardware, software, processes, data, and network belongs to an organization. From the inside and outside of the organization, only selected individuals or objects (including applications and services) are allowed to enter and use the system. The question is: how do we know which individuals or objects have the permission to do so? This is where an access control mechanism, especially authentication, becomes necessary.
As mentioned, there are four processes to an access control mechanism – identification, authentication, authorization, and accounting. First of all, identification is just identifying who each user is. This is, for example, done by issuing a username or a user ID. Secondly, authentication is a process used for determining whether or not users are allowed access. In addition, authentication is a process used for confirming the identity of a user. That is, once a username is entered, the user must prove that this username really belongs to them. The next thing that usually comes after authentication is authorization. Authorization is a process that deals with restrictions and limitations on access. Authorization tells what each user is and is not allowed to do or access. In other words, authorization gives users their access rights to resources. The fourth part of access control is accounting. Accounting keeps records of who has entered the system, what that person has done, and when. To put it simply, accounting is a process of keeping a log of the system.
We have now learned the overview of what access control is. Let us focus more on authentication.
As mentioned, authentication is a process of confirming or validating an individual’s identity. The fact that the individual or user claims that they are the owner of the identity does not necessarily mean that it is true. Therefore, for the user to be granted the permission or the rights to have an access and use the resources, they must provide an evidence to prove their identity to the system. This is what authentication is.
In an authentication process, an individual is required to provide a credential in order to prove their identity. Different systems may require different types of credentials. Some may even require more than one credential from the individual. In today’s computer and communication systems, an individual is usually asked to present a credential in the form of a password. However, credentials also come in other forms, such as a PIN number, an authentication token, or a representation of a body part.
Typically, there are two components involved in the process of entity authentication . They are known as a supplicant and an authenticator. They are depicted in Figure 3-1 and can be described as follows:
When the term “entity authentication” is mentioned, an entity can be a person, a process, an application, a client, or even a server.
- 1.
Supplicant – This is an entity that will provide their identity and prove that this identity is valid. As a result, this entity will either be authenticated or not be authenticated.
- 2.Authenticator – This is a party that checks the credential or credentials of the supplicant and states whether or not the supplicant’s identity proving process is successful. An authenticator can be a person, a process, or a server.
 Figure 3-1
Figure 3-1Two-Party Authentication Process
However, there are times when a third component is required in the authentication process. This third component is usually known as a trusted third party or TTP, whose job is to analyze the received identity and credential. The trusted third party also makes the decision to whether or not the authentication process is a success, which means that the trusted third party becomes the authenticator of the process. The non-supplicant party can be called a responder as a result. A typical authentication process involving three parties is illustrated in Figure 3-2.
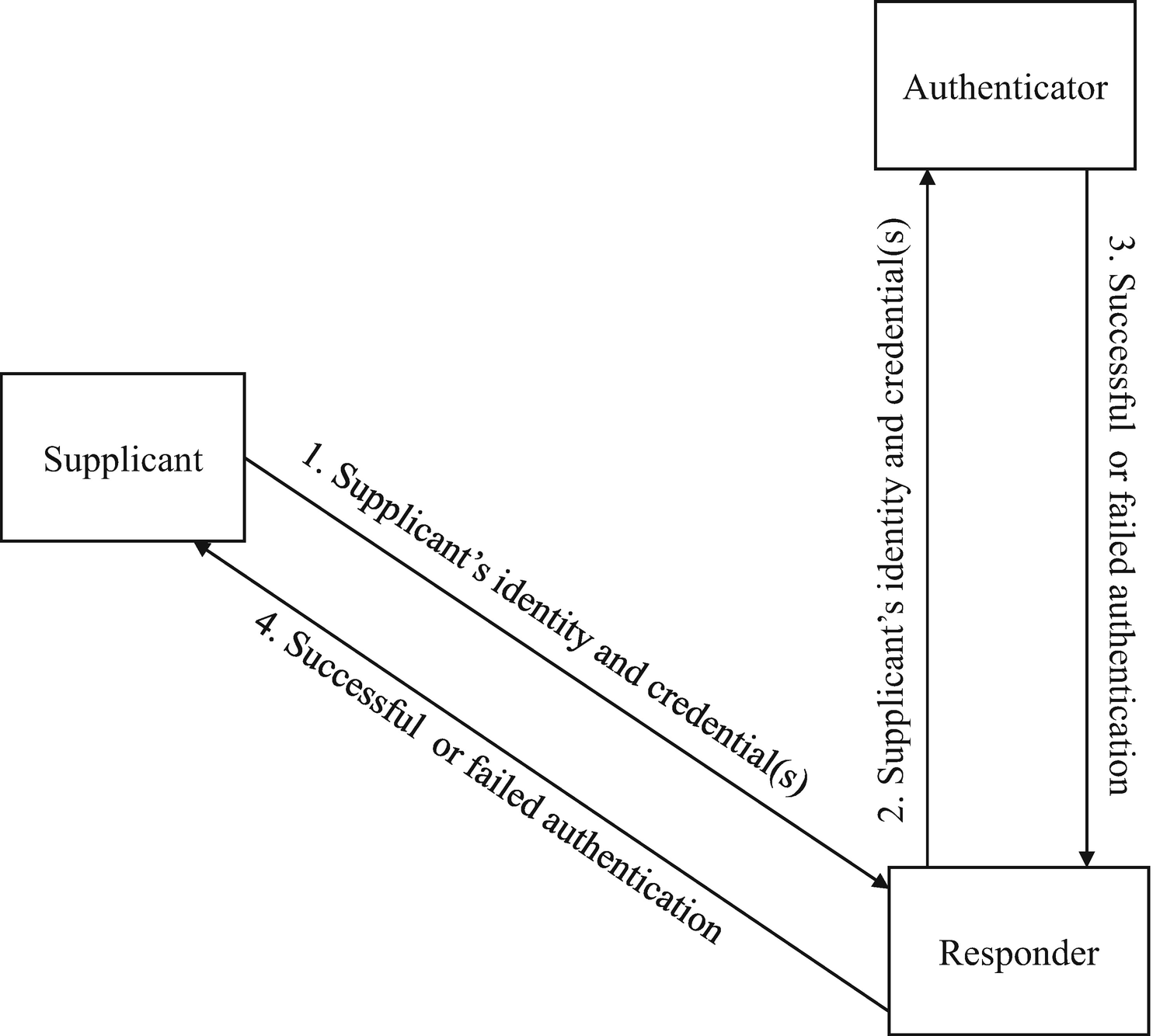
Three-Party Authentication Process
This section provides an overview of what authentication is. The next sections will explain different authentication methods, which include the something-you-know method, something-you-have method, and something-you-are method.
Factors of Authentication
Authentication is the process of confirming one’s identity. In order to carry out the process of confirming the identity, the systems or resources requiring authentication usually ask for evidence from the entity attempting to do the authentication. This evidence is known as factors of authentication. Some may also call them credentials . In other words, when a user claims to be someone, they need to provide further information to prove that they are really who they say they are. That information is a factor or factors of authentication.
For example, a user goes to a cash point in order to withdraw some cash. When the card is inserted into the machine, it is used as a claim of the user’s identity. The next step is for the user to prove that they are really the owner of the card. This is done by the cash point asking something that can only be provided by the actual owner of the card. It could be a four- to six-digit PIN code or a fingerprint. These are examples of factors of authentication.
The next sections will give descriptions of commonly used factors of authentication. They are something you know, something you have, and something you are.
Something You Know
Something you know is a method which a supplicant uses what they remember to prove their identity. In other words, the user would use what is stored in their memory to prove that they are really who they claim to be. A good example for this authentication method is a password or a PIN code for a cash point.
In a simple view, something-you-know authentication process works in two parts as follows: The first is the registration phase. The second is the authentication phase. During the registration, a supplicant or a user chooses a password of their choice. The password is then stored in a password database, which marks the end of the registration. Note that there may be some processing done to the password before storing. However, for the sake of simplicity, this process will be ignored and will be explained in detail in Chapter 4.

Typical Something-You-Know Authentication Process
Some have asked whether or not a username or an email address is a something-you-know factor of authentication since they have to be memorized and entered into a system when logging in. The answer is no. Usernames and email addresses are not considered as a factor of authentication. They are simply used to claim an identity of the user or supplicant, which is known as identification. A password or a PIN code is the element used to prove the ownership of the identity. Hence, it is a something-you-know factor of authentication.
Something You Have
The second factor of authentication requires that a supplicant has a physical item in their possession. This includes smart cards and authentication tokens. An authentication token is a small device, usually in the form of a key ring, with a screen to display a set of numbers. The numbers on the token’s screen is used as a passcode for the authentication process. An authentication token can be either synchronous or asynchronous. A synchronous token is synchronized with an authenticator or an authentication server. They use the time to generate a number that will be entered during the user login phase. That is, the token has a function f() that takes the current time t as an input and computes a password PWDt for that particular moment. In simple terms, this can be expressed as PWDt = f(t). When a user would like to log into a system, they enter a username together with the number displayed on the token.

Synchronous Token Authentication Process at Any Time t
The number or password computed by the token and authentication server changes according to the current time. For an RSA SecurID Token, which is an example of an authentication token, the number on the token changes every minute and is also synchronized with the authentication server.
Asynchronous authentication token is the second type of token which works in a slightly different way from the synchronous one. With this type, the token and server do not have to be time-synchronized. When a user would like to log in, an authentication server will send the user a random sequence of digits, which will then be entered into the token. The authentication token computes a passcode from the entered numerical sequence as a response. To complete the login process, the user enters the passcode into the system to gain access.

Asynchronous Token Authentication Process
The numerical sequence or challenge generated by the authentication server changes every time a supplicant attempts to log in. Hence, the password changes every time, too.
The main advantage of using an authentication token, either synchronous or asynchronous, is that the user’s password changes every time they log in. This is also known as time-based one-time password or TOTP for the synchronous token and hash-based one-time password or HOTP for the asynchronous token. Both of them reduce the risk of passwords being guessed by attackers.
Something You Are
The third authentication factor deals with the characteristics of the supplicant. This is a process of using body measurements, known as biometrics. Simply put, the something-you-are factor of authentication requires that the authenticator authenticates the supplicant by using biometric information. Commonly used biometrics for authentication purposes include fingerprint, palm print, hand geometry, face, iris and retina. However, only fingerprint, retina and iris are considered truly unique. With today’s technology, other types of biometrics include signature dynamics and keyboard typing pattern.
This method of authentication can be thought of as a traditional identification and authentication method. For example, when a person enters a bank, they are asked to show a photo ID. The person is then identified and authenticated based on their biometric parameters. That is, the bank matches the face of the person with the face on the ID card. This is a form of facial recognition and can be analogous with today’s biometric authentication method.
The process of biometric authentication works in two main parts. The first is the registration or enrollment. The second is authentication. In the registration phase, biometric data is captured by a biometric sensing device, such as a fingerprint scanner for fingerprint data or a camera for facial data. The captured data is then processed in order to extract and transform it into a biometric template. The obtained biometric template is stored in a database where an authentication process can be made later.
The authentication process begins when the biometric data of the supplicant is captured and processed for the extraction and transformation to obtain the person’s biometric information. It is then compared with the biometric template which is stored in the database. If they match, the authentication process is a success. Otherwise, the authentication process fails. This process is summarized in Figure 3-6.

Typical Biometric Authentication Process
Other Factors of Authentication
The three factors of authentication mentioned earlier are considered the most commonly used credentials in any computing systems. This section will explore and explain other existing, albeit less popular, authentication factors that can also be used to prove the identity of the supplicant.
Something You Process
This type of authentication factor is based on the ability of a supplicant to process things. The something-you-process factor works with human cognitive level of authentication. In other words, instead of asking the supplicant to enter their password, the system asks them to perform a mathematical or logical task. Typically, these tasks involve some secrets known to the user as well as some variable values provided by the system. The output of the process done by the user will form a new code or a new pass that will be used in this particular authentication session between the user and the system. This authentication method provides a different outcome each time the supplicant processes the given task. It means that the value used to authenticate the supplicant by the authenticator differs from session to session.
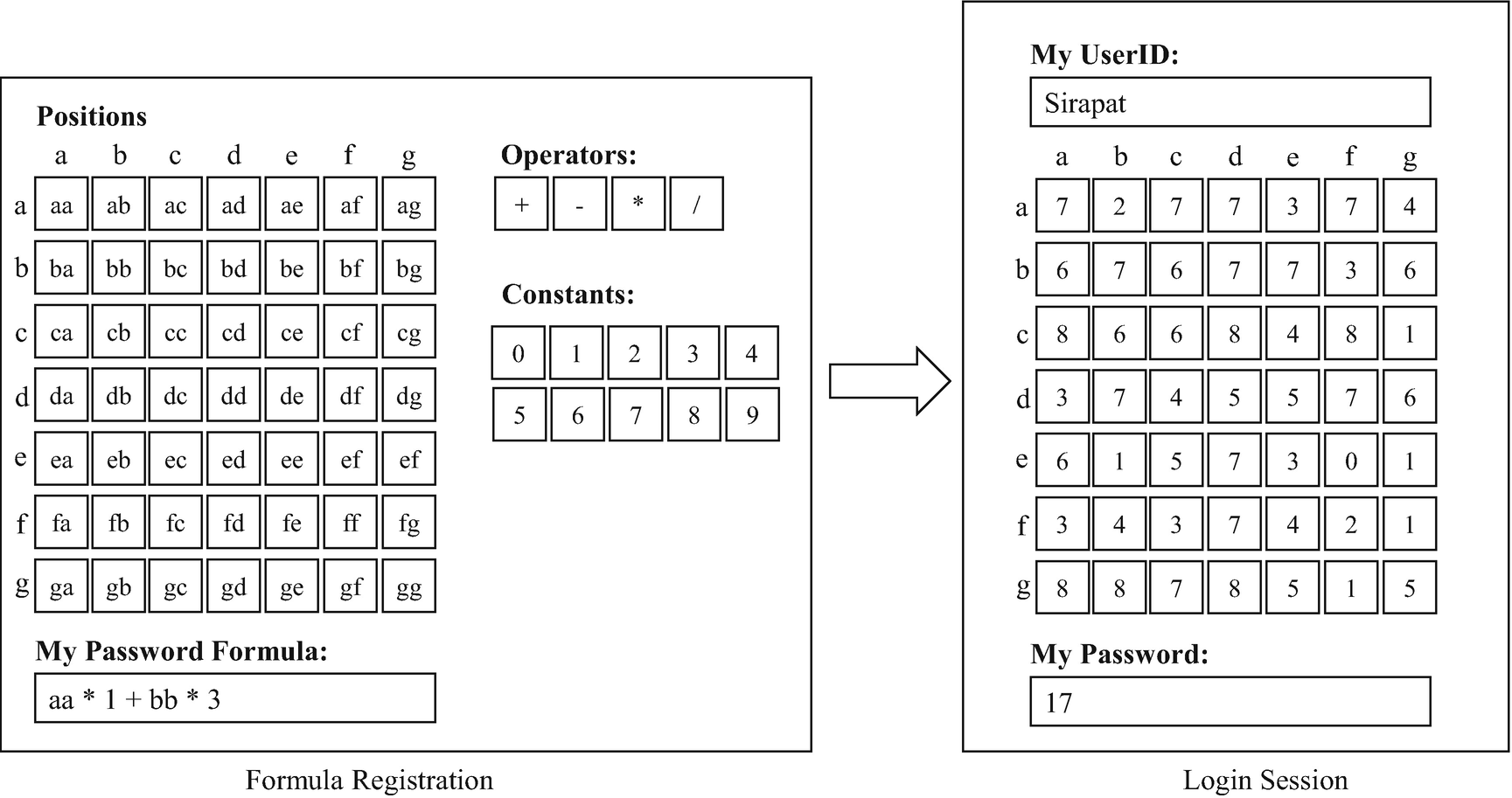
An Example of Something-You-Process Authentication
During the login session, the user is presented with a grid with a random value in each cell. In order to log in, they have to compute the outcome of the formula chosen in the registration stage.
Carrying on with the same example in Figure 3-7, the value in the cell aa is 7. The value in the cell bb is 7. Therefore, the result of the mathematical formula aa ∗ 1 + bb + 3 is 7 ∗ 1 + 7 + 3 = 17, which is entered as the passcode for this particular login session.
The numbers in the cells of the grid change each time a new login session begins. This means that the result of the calculation, based on the memorized formula, should form a one-time passcode that allows the supplicant to login successfully.
Although the one-time passcode, as noted previously, produced by the user’s computational process is a positive point, this something-you-process authentication is time consuming and cognitively demanding. This is due to the process of recalling the mathematical formula and the process of computing the outcome during the login session. This is one of the reasons why this type of authentication factor is not as commonly used as the ones mentioned earlier .
Somewhere You Are
The somewhere-you-are factor of authentication , although not as well-known as the others, has been proposed since the 1990s. Somewhere you are concerns with the physical location of the supplicant. Some may even call it the location-based authentication. The implementation of the somewhere you are is currently limited in online systems. However, there are several methods that can be used to achieve this.
Firstly, an IP address can be used to detect the location of the supplicant. Suppose that the supplicant would like to use a service that requires a geolocation security check. When they register to use the service, they state that they live in the Kingdom of Thailand. That means if someone attempts to log in to this particular account from an IP address located in the United States, the service will either notify the supplicant that an attempt from outside of Thailand has been made or it will terminate the session thinking that it is an adversary trying to log in. The use of an IP address is useful in making an effort to protect the account from an adversary.
Some financial institutions use this particular method to detect payment frauds. For instance, if the last known location of a user was in the Kingdom of Thailand, however, a few minutes later, the same account is logged in or the credit card associated to this account is used in China, this could indicate an unusual activity.
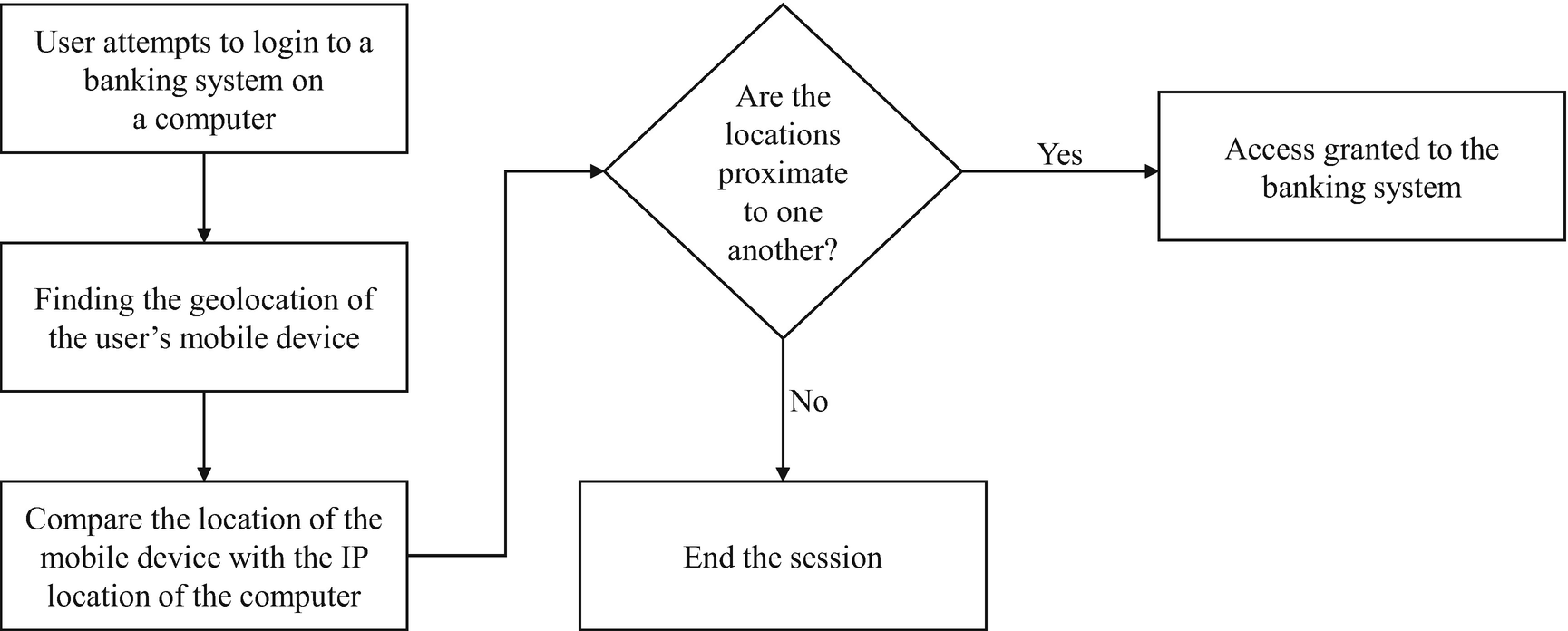
Example of Applying Somewhere-You-Are Factor of Authentication
The preceding authentication procedure has the following advantage: Suppose a user walks away from their computer without logging out, leaving the current session open. In a normal situation, any other user can utilize this opened session to try to impersonate this user. The somewhere-you-are factor can reduce the risk by authenticating the user’s mobile device’s geolocation. The session can remain active if the locations of the mobile device and the computer are identical. However, if there is enough error on the location, the session can automatically be closed. Thus, no other users should be able to come in and use the user’s session.
Somebody You Know
The somebody-you-know factor of authentication works based on the human social relationship. The somebody-you-know authentication method was designed for an emergency situation where an authentication token is not available to the user. When the token is not available, there must be another means for the user to utilize in order to log into a computer system. This is where the relationship between users comes in. The process works as follows.
In the enrollment stage, the relationship between two users, say Alice and Bob, is recorded by the server as an asker and a helper. When Alice, the asker, who has lost the ability to use her authentication token, wants to log into the system, she contacts Bob, the helper. The channel of contact can be either over a telephone or face to face in order to make it easy for Bob to authenticate Alice, either by voice recognition over the phone or face recognition during face-to-face contact, respectively.
Once Bob is certain that the asker is really Alice, he uses his own client machine to carry out his authentication with the server, who also verifies the asker–helper relationship of Alice and Bob. If the relationship verification is successful, Bob receives a vouchcode from the server, who marks that there is an ongoing helping session between Alice and Bob.
Bob, the helper, then gives the vouchcode to Alice, the asker. This can be done orally in the case of telephone communication or as a written value in the case of face-to-face contact .
At this stage, Alice enters her username, password, and the newly received vouchcode to the server. The server then verifies Alice’s password and vouchcode and makes the decision to either accept or reject the authentication attempt.
If the authentication succeeds, the server provides the asker, Alice, with a temporary password. Subsequently, Alice can carry out an authentication process with the server using her password together with this temporary password, which will usually be valid for one or two days.

Somebody-You-Know Authentication Process
It is important to note that this authentication process only works if and only if the relationship between the asker and helper is valid and successfully verified by the server. This implies that it is necessary for a user to know someone if they would like to carry out an authentication process without the availability of their authentication token. There is one disadvantage to this somebody-you-know method. That is, the helper must have an access to the Internet. Otherwise, they will not be able to request and obtain the vouchcode for the asker. However, it is the process that can assist the asker in an emergency situation as explained .
Threats of Authentication
We have seen that the goal of authentication is to validate and confirm the identity of a supplicant. It is normal for computer systems to ask the supplicant or user to carry out authentication. At the same time, there will be an adversary who tries to penetrate the system and compromise the authentication mechanism. This section, therefore, looks at different approaches that an attacker can use to attempt to break the authentication mechanism of computer systems. However, let us first try to understand the differences between the three words that are related to the content of this section. They are vulnerability, threat, and attack.
Firstly, a vulnerability is a weakness in a system that makes a threat occur. It refers to the inability to resist hostile challenges. Secondly, a threat is defined as a potential danger that may occur. In other words, a threat is any danger that has a likelihood of occurring to an asset. It does not matter whether it actually occurs or not. As long as there is a chance of occurring, it can be referred to as a threat. Thirdly, an attack is a malicious action that exploits a vulnerability, damages, or gains unauthorized access to a computing resource. An attack’s aim is almost always to cause harms or damages to an information system.
Some authentication methods, especially the ones that rely solely on usernames and passwords, are considered broken. In fact, the Open Web Application Security Project or OWASP has ranked broken authentication as number 2 in the list of most seen application vulnerabilities. It is, therefore, important to understand the threats that are common to authentication mechanisms.
Default Passwords
A default password is a predefined and preconfigured password for a piece of software or a device. Default passwords are commonly used for network equipment such as routers, switches, wireless access points, as well as Internet of Things (IoT) devices. Typical examples of a default password include admin, password, attack, and 1234. Default passwords represent one of the major issues to authentication mechanisms and are very often overlooked.
In many cases, system engineers and developers are so busy working on the implementation of functionality of the systems that they forget about the default passwords. If the default passwords remain unchanged, it can cause a serious problem in that an adversary can easily find a default password for any devices or software on the Internet. Once the password is obtained, the attacker can then log into the device or system and often has the privilege of an administrator. The problem becomes more severe in the case of the IoT environment where many devices’ make and brand can be readily seen by anyone. Hence, a default password can also be comfortably found.
Fortunately, there are ways to counteract the security of default passwords. Firstly, the vendor of software and hardware can employ more secure and unique default passwords. Secondly, the software and hardware vendor can design their devices or systems in such a way that the users are forced to change the password when the default password is used for the first time. Thirdly, on users’ responsibility, the users or device owners must change the default password to a stronger password when they first enter the system or the device .
Eavesdropping
Eavesdropping or sniffing is basically an act of listening to private communications of others without their permission. Therefore, eavesdropping is an easy method to obtain a supplicant’s password as well as other credentials from the traffic on a computer network.
Many applications, devices, and systems transmit information, including passwords and other credentials over the network in an unencrypted format. Typical examples include FTP and HTTP. In their default configurations, these protocols do not encrypt any messages and packets. That means if an adversary wants to eavesdrop or sniff packets off the network, using such application as Wireshark, they will be able to easily obtain passwords in the plaintext format.
In order to protect users’ passwords and credentials, encryption techniques such as AES-128 and AES-256 can be applied. This way, even if the information is sniffed by an attacker, they will still not be able to read it in a meaningful way, making it more secure.
Replay Attacks
A replay attack is another popular way to attack authentication mechanisms. To carry out this attack, it is required that an attacker has an access to the network between two communicating principals. This type of attack can still work even though the attacker does not have an access to the plaintext format of users’ credentials.
The replay attack is done by the attacker copying an entity’s password or credential and using it to carry out authentication with the other entity. The purpose is to impersonate the user whose password or credential is copied. Put it simply, the attacker copies the message or credentials and then sends this same message to an authenticator, hoping that they will be successfully verified.
Timestamping is when the sender of the message records and includes the time that the message is constructed and transmitted. When the message is received, the recipient can check whether the time on the message is current or has already past. It is, therefore, a mechanism that can be used to prevent this type of attack.


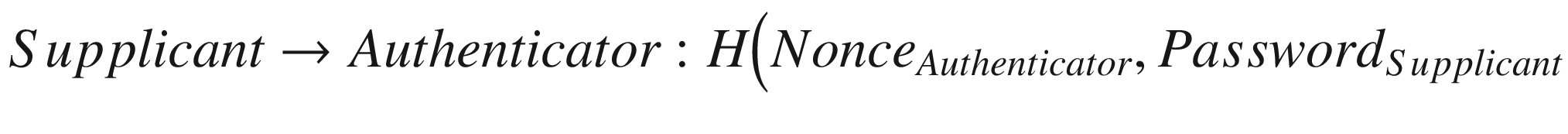
Man-in-the-Middle Attacks
Man-in-the-middle or MitM attacks occur when an adversary comes in between two hosts, whether they are a supplicant and an authenticator or a customer and a website, and all messages and communications go through them. By being in between two entities, the attacker can receive and send messages to both parties. That means the attacker can impersonate both entities, making one believe that the attacker is the other. Moreover, not only receiving and transmitting messages from the involving entities, the attacker can also alter and even delete portions of those messages. Thus, an attack on authentication can be carried out as follows.
Provided that the attacker is in between the supplicant and the authenticator usually by acting as a legitimate wireless access point, they can intercept authentication messages, which may include the username and password of the supplicant. The intercepted information can then be relayed by the attacker to the authenticator, making the authenticator believe that the attacker is the supplicant.
In order to reduce the risk of this type of attack, strong encryption is recommended. Another method that can help prevent the attack is the application of a virtual private network or VPN. Both of these methods ensure that the attacker cannot decipher the messages being transmitted during the authentication session.
Password Guessing
Since the beginning of information technology, entity authentication is usually done with a username and a password. Therefore, password guessing is when an adversary tries to guess the username and password and then authenticate as the legitimate user. Obtaining usernames is not difficult for an attacker. This is because a username is frequently just an email address of that user or the attacker might know the naming convention used by that particular organization. Sometimes the attacker even has an access to the directory containing all the usernames of an organization. This is especially the case for an internal attacker. For the password guessing attack, the attacker simply guesses one or more passwords that are likely to be the one used by the user.
The first method that an adversary can use to guess a password is a brute-force attack , which is also known as an exhaustive search. This is an attack where the attacker tries to generate all possible combinations of a password and attempts to authenticate to the system using the username with different combinations of password. The amount of time taken to carry out this attack depends on the size of the password. In simple terms, if the size of the password is 8 characters, which is 64 bits, the total number of password combinations will be 264. With today’s technology, the number of different guesses per second by an ordinary computer is approximately 100,000,000 guesses. That means it would take a normal computer around 184,467,440,737 seconds or 5,850 years.
It is clear that password brute-force attack is very time consuming due to the large number of password combinations. Therefore, to decrease the time required to guess the password, a dictionary attack can be carried out. A dictionary attack is a method an attacker uses to breach a password-protected authentication mechanism by attempting each word in a dictionary as a password. It is possible for this attack to be successful because many users tend to use word in a dictionary as their password. However, the dictionary attack becomes more complicated when users choose longer and stronger passwords. As a result, a new variety of the dictionary attack, known as password dictionary attack, has been formed.
A password dictionary attack is still considered a brute-force attack and also a dictionary attack. This time an attacker tries to guess a user’s password by using a dictionary of commonly used passwords. Over a period of time, an attacker or a community of attackers has collected a lot of data containing passwords that are thought to have been chosen by users. The data in the database can then be used as password guesses when attempting to compromise the authentication system. In addition, these commonly used passwords can lead to an attack called password spraying attack.
A password spraying attack is a type of attack that relies on a few popular passwords that are used by users. These passwords are used to attempt to access a large number of accounts. In other words, a password spraying attack is when an attacker takes a large number of accounts or usernames and tries to authenticate them with one or a very small number of passwords. It is done with the hope that they will be successfully authenticated by the authenticator, hence being able to impersonate the legitimate user.
All the password guessing attacks can be prevented by asking users to select a strong password and to stop password reuse in different password-protected systems. More detail on passwords and password-based authentication will be provided in the next chapter.
Credential Stuffing
Credential stuffing is actually another form of password guessing attack. This type of password attack has become more widespread in recent years. Credential stuffing is an attack that takes advantage of the users’ failure to select different passwords for different accounts. In other words, credential stuffing works because users reuse their password for various accounts, and statistically more than 73% of passwords are reused.
The way the attacker carries out credential stuffing is as follows: First, the attacker tries to acquire a password or credential of a user by breaching a system or from a leaked-password directory that may be available on the Internet. A compromised password is then used in an attempt to log into various other accounts or systems of the same user.
There are several suggestions made by OWASP for preventing credential stuffing attack. They include the use of different passwords for different accounts, the use of a CAPTCHA, and the use of multi-factor authentication (MFA) which will be explained in detail in Chapter 6.
Social Engineering
Social engineering is considered a very powerful approach to attacking user authentication. Social engineering techniques usually involve the use of personal and interpersonal skills, but very often without the need of information technology. When carrying out social engineering, what an adversary does is to try to trick a user into believing that they are required to provide some specific information or even perform a specific action. In the context of information security, social engineering is normally carried out with an aim of having the user disclose their confidential information.
For example, a social engineer might act as a system administrator, ring a user, and inform them that their user account needs an immediate fix. The user, being worried and scared as well as believing that this is a genuine request, provides the attacker with their username and password. The attacker can now log into the user’s account and accomplish their goal of impersonating the user.
Nowadays, social engineering comes in three different shapes and forms. They are in-person social engineering, phone social engineering, and digital social engineering.
In-Person Social Engineering
In-person social engineering is carried out in order to gain access and gather confidential information. A common example is when an adversary pretends to be a technician to gain access to an organization or even employees’ computers. In some cases, a person is hired as a rogue employee so that they can gain access to the competitor’s information and premises. Several other notable examples of the in-person social engineering techniques include neurolinguistic programming (NLP), six degrees of separation, and bar hopping.
Neurolinguistic programming or NLP is performed by an attacker in order to get another person to like them. Once the attacker gets physically close to the target, they will try to match the voice, tone, vocabulary, and body language so that the target subconsciously becomes more comfortable. This way, the social engineer is able to control the conversation, which allows them to direct the conversation and gain what they are after – information.
Six degrees of separation is when a social engineer selects a target and uses social media to gain their trust. In other words, the attacker first identifies a victim, which could be an executive of a target company. The attacker then tries to reach out the victim’s friends and family on social media. They will eventually request an introduction to the victim via the friends or family as a mutual friend. Once the victim is comfortable with the attacker, the attacker can begin the process of going after the information they want.
Bar hopping is basically when a social engineer buys a victim a few drinks in a pub or at a bar with an aim of getting the victim drunk, so that information can be extracted from them more easily. This is done with the fact that people tend to talk more when they are drunk.
Phone Social Engineering
The phone social engineering is said to be the most common method of social engineering. The preceding administrator phone call is just one example of this technique. The phone social engineering technique is typically used to apply anger and panic and to carry out a vishing attack.
The anger tactic begins by an attacker tracking the movement of the executive-level employees. Suppose an executive is about to leave for another city or country; the attacker will make a call to the executive’s office and fake their frustration that they cannot access some very important files. The attacker will at some point pretend to be very angry and demand access to those files immediately. The ultimate objective is for the office employees to give in and the attacker able to access those files.
In the panic tactic, an attacker makes a phone call to a user saying that their account has been compromised. The attacker convinces that user that the attacker is a person from the technical support unit and is able to help. However, in order to fix the problem, the attacker informs the user that a username and password are required. In many cases, the social engineer pretends to walk the user through the process, making them believe that this is a complex issue and the attacker is helpful as well as authentic. The problem is that the user has already given the adversary their confidential information.
Vishing occurs when a social engineer, pretending to be a bank, rings a target with a prerecorded message. Typically, the message informs the target of an unusual activity of their bank account. The automated message then instructs the target to make a phone call to a specified number. When the call is made, the victim is asked to enter the credit card number, bank account number, and other confidential information such as date of birth and expiration date of the credit card. This way, the attacker can end up with the information necessary to access the account and make fraudulent use of the credit card.
Digital Social Engineering
Digital is another social engineering technique that is gaining popularity these days. Many tactics have been employed by an attacker, including pretexting, device leave behind, broad-based phishing, and spear phishing.
Example of Pretexting
Once an attention is received from the recipient, the attachment might be clicked and the malware is installed on the target’s computer, which can allow an attacker to monitor or gain access to the machine.
The device leave behind tactic is another example of digital social engineering. This is when an attacker intentionally leaves behind a USB flash drive, an external hard disk, or any type of storage device around an office. The adversary often writes a tempting label on such device, such as salary records or secret documents. Anyone who falls for this trap and uses the device can be infected by malicious software once the device is plugged into their computer. Again, if the machine is infected, the adversary will be able to access it. Hence, confidential information can be obtained by the attacker.
The next tactic in the digital social engineering is phishing. A phishing attack uses email, social media, or instant messaging application to trick victims into providing confidential information or visiting malicious websites. Statistically, a phishing attack can successfully compromise around 1 in 20 people.

Example of a Broad-Based Phishing Email

Example of a Spear Phishing Email
It should be noted and understood that in phishing attacks, when a phishing email appears to be from or to be targeting the executive-level employees in an organization or a government agency, the phishing attack becomes a whaling attack . Of course, the aim of the attack is to steal sensitive information or to gain access to a computer system.
Since it is easier to hack humans than machines, there needs to be a way to prevent social engineering. A better way to reduce the risk of being attacked by social engineering is to educate users so that they become more aware of the risk. Another way is for users to be more cautious. That is, when an email is received, the users should look more carefully at the domain of the sender’s email. In some cases, if unsure of the email or the actions asked to be carried out, the users can always check with the source, such as their university or their bank. Moreover, in the case of in-person social engineering, users should be careful not to give out any confidential information to strangers.
Potential Threats to Authentication and Countermeasures
Potential Threats to Authentication | Possible Countermeasures |
|---|---|
1. Default Passwords | - Use unique default passwords - Force users to change the default passwords |
2. Eavesdropping | - Use strong encryption |
3. Replay Attacks | - Apply a challenge-and-response mechanism |
4. Man-in-the-Middle Attacks | - Use strong encryption - Use a virtual private network (VPN) |
5. Password Guessing | - Create strong passwords - Stop password reuse |
6. Credential Stuffing | - Use different passwords for different accounts - Apply multi-factor authentication |
7. Social Engineering | - Increase user awareness |
Summary
This chapter introduces different methods and factors of authentication, including something you know, something you have, and something you are as well as other existing factors. Authentication, as claimed, is said to be the first line of defense before an adversary enters a system or a network. It is not without any risks, however. The chapter, therefore, presents threats that are common to authentication mechanisms. In addition, suggestions to countermeasures that can help reduce the risks from those threats are also explained.
Bibliography
Al-Fairuz, M. A. (2011). An Investigation into the Usability and Acceptability of Multi-channel Authentication to Online Banking Users in Oman. Ph.D. Thesis, University of Glasgow, School of Computing Science, Glasgow.
Boonkrong, S. (2012, December). Security of Passwords. Journal of Information Technology, 8(2), 112–117.
Boonkrong, S. (2014). The Art of Protecting Networks and Information. Bangkok, Thailand: King Mongkut's University of Technology North Bangkok Press.
Jesudoss, A., & Subramaniam, N. P. (2014). A Survey on Authentication Attacks and Countermeasures in a Distributed Environment. Indian Journal of Computer Science and Engineering, 5(2), 71–77.
Perez, L. P. (2015). Seamless and Strong Authentication on Mobile Devices Based on User Activity. Ph.D. Thesis, Universidade Da Beira Interior Engenharia, Portugal.
Todorov, D. (2007). Mechanics of User Identification and Authentication: Fundamentals of Identity Management. New York, USA: Auerbach Publications, Taylor & Francis Group.
Vongsingthong, S., & Boonkrong, S. (2015, July). A Survey on Smartphone Authentication. Walailak Journal of Science and Technology, 12(1), 1–19.
