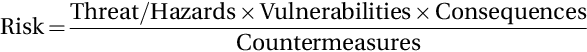Understanding the Risks
Abstract
This chapter explains the terms ‘risk’ and ‘risk assessment.’ It explains how the terms sometimes get misused and the meaning of the terms in this book. Risk is a combination of the likelihood of occurrence of threats, the gaps in effectiveness from standards or vulnerabilities, and the consequences or business impact. The goal of this book is to base countermeasures and programs on risk-based solutions.
Introduction
It is important to understand that the best-structured approach to determining how to enhance protection from business espionage is to have countermeasures that are risk-based. In order to do that, it is important to regularly do a thorough and complete risk assessment. That risk assessment becomes the basis for your company’s counter espionage program.
Having said that, it is important that you do a true and complete risk assessment, not a partial one that someone might, in error, call a “risk assessment.” It sounds simple but I find people often and mistakenly interchange or misuse terms. This is especially true of the terms threat and risk, or people will use the term “risk” in some other context. In the context of this book, we will be using the term risk to mean a very specific security issue. As we have already noted, this approach to risk draws on a number of international programs and standards and we will be applying these standards to risk as it relates to business espionage.
For example, I have had a number of security directors or business leaders say to me something along the lines of: “The People’s Republic of China is a high-risk environment for business espionage and sensitive business information.” As we will learn in Chapter 3 (and we will see more examples in other chapters where there are case studies), the People’s Republic of China has been involved in, or in some way linked to, a number of business espionage situations. Therefore, it may be valid to say the People’s Republic of China is a “high threat” environment, but before we can say it is “high risk” we have to look at how effective your existing security measures are and the consequence levels for your business processes/information there. These two factors are also part of risk determination. Risk is not based entirely on threat, although threat is a factor in determining a security risk.
During discussions about their various operations within the state of Nebraska, in the United States, another security director assured me their operations in Nebraska were “low risk.” When I asked why, that security director said: “Everything in Nebraska is relatively low risk. Everybody knows everybody in Nebraska and it is pretty isolated from a lot of these traditional outside security issues.” My response was, “Maybe it is low risk in Nebraska and maybe it is not, but first we must thoroughly examine the threats in Nebraska, USA.” Then, I shared with him that we needed to see how effective their existing security was in Nebraska and, finally, how critically important the processes/information were for the company when it came to its Nebraska-based operations. Only then could we say what the true security risk was for the company’s Nebraska-based sites.
Therefore, if you have been mindful of the criticality levels for information that will be available in and to China and have implemented good, strong security measures (hence your vulnerability is low), you may find the threat is high but the vulnerability and consequence are low enough to make the risk acceptable in China.
For example, in Nebraska, the threat might be low but security efforts there might be plagued by complacency (“nothing ever happens here” attitudes) and thus are not very effective (high vulnerability), which could also be where some of the most critically important information in the company resides (high consequence/business impact). This means the threat is low but vulnerability and consequence are high.
In fact, in this hypothetical situation, the company’s business espionage security risk in Nebraska is higher than in the People’s Republic of China. Maybe the threat in China is higher than in Nebraska but the overall risk (adding the vulnerability and consequence factors) is higher in Nebraska. Unfortunately, I frequently see this kind of dichotomy in discussions about countering business espionage.
This is why it is so important to understand the differences in terminology and to be precise and consistent. Threat levels and risk levels between the two locations could be very different.
So, before you decide on a pro-active counterespionage program and what countermeasures your business should have in effect, you must have a thorough understanding of the threats, the vulnerabilities, and the consequences/business impact. Together they make up business espionage security risk. Armed with that knowledge you can determine the countermeasures that should be employed to mitigate business espionage risk at any given entity. This is risk management at its best, and this is the approach we will be working from as we examine business espionage security risks.
Risk Methodology
For purpose of this book, business espionage security risk will be defined using a methodology adopted by the International Standards Organization (ISO), the U.S., British, and French governments, Sandia Laboratories, among many security organizations, and others. It is basically the potential for an adverse outcome assessed as a combined function of threats, vulnerabilities, and consequences associated with incidents, events, etc. This combination, as we hinted above, results in business espionage security risk. The same process can work for all kinds of security-related risks such as executive protection, terrorism, theft, workplace violence as well as business espionage. This can allow a candid comparison of risks that truly compares “apples to apples.” To compare and prioritize, it is important that we use the same methodology for all business-espionage-related risks.
Risk Formula
As a result of approaching business espionage in a risk-based manner, companies and individuals have a means for determining how they can best focus their limited time, effort, and money on lowering their vulnerabilities and protecting their most important information from the most likely threats. The risk equation is often depicted as:
When risk management is applied to the process, the formula changes slightly to incorporate countermeasures, which can lower the vulnerabilities or lessen the direct consequences. That formula then looks like this:
In an environment where there are significant issues with business espionage we need to analyze threats using a threat assessment approach. This threat assessment should focus on who is targeting businesses (especially similar businesses), what businesses they are spying on (does location, size, etc. matter?), and how they are spying on businesses (determine their most likely modus operandi—or methods of operation). You can get this type of information from a variety of sources. I highly recommend joining professional security associations, such as ASIS International, and using the membership to create relationships with similar companies. If you share some information, they will likely do the same. Depending on your nationality, you can liaison with the national agencies responsible for countering espionage in your country. You can also talk with the security attaché or equivalent position in the embassy when you have business entities in a foreign country. There are other professional associations such as chambers of commerce, etc., in various countries. Once again, by building relationships you can share and ask about the issues and situations in a given country or business sector. By talking with all of these different entities you can begin to formulate a threat picture of the espionage situation in a given location. Your focus, again, should be on the methods used by business spies within your given location of concern and the likelihood of occurrence for business spying.
The next step is looking at the security standards that should be in place to protect the business from the business-spying threat as determined in the threat assessment. We will then identify any gaps that currently exist in how the company is operating versus these established/accepted standards for the overall threat they face. This is determined in the vulnerability assessment phase of the risk assessment. These gaps will be identified and labeled as “vulnerabilities.”
A good approach to determining the effectiveness (lack of effectiveness is the definition of a vulnerability) of your existing security and identifying vulnerabilities is to focus on how well your security measures fulfill four major security functions. Ask yourself, how well does existing security…
• Detect,
• Delay, and
• Respond.
Deterrence is a difficult measure to determine and quantify, but it is important to know the threats and put yourself in the mindset of the threat vectors. For example, if I were going to try and get inside of this facility posing as a legitimate employee or someone authorized to be inside the facilities, how easily could I do this? How thorough is the access control? Can I piggyback? How should I be dressed? Who provides service here and how quickly are they given access or checked? Can I dress and pose as a delivery person, repair or maintenance person?
When there is signage and barriers, and when it is apparent that employees and security are extremely alert, the result is deterrence. A potential spy decides the opportunity for success is low and the opportunity of being detected is high. From the bad guy standpoint: time to try another place or another method. Deterrence has value.
It is also important to determine how effective your means of detection are. Typical means of detection include alarm notifications or computer penetration attempt alerts. It also includes being spotted on CCTV, or being spotted by a security officer or an alert employee. Detection includes the awareness of a possible problem but it also includes reporting it. An employee who says, “Yes, I saw that and it was suspicious to me. I wondered about it,” but does nothing and does not notify security, police, or some response element then it is not true detection. The “alertness” was only part of the process. Having a CCTV system that is not monitored but simply records does not count as true means of detection. It may help in a follow-up investigation, after-the-fact, but it is not a means of early detection. For CCTV to be a part of a detection process, it almost always has to be monitored by trained and dedicated staff or security personnel. It cannot be a part-time job. It needs to be a dedicated function.
The key to any detection is a quick, timely response that interrupts or prevents the perpetrator from completing the attack on your sensitive information. Once there is detection, and notification, there is usually a time gap before a responder can get to a site. If someone is able to break into the computer server area, for example, but a motion detector sets off an alarm in the security control that indicates someone is inside the server room, it will take a period of time (hopefully only a few minutes) for a responder to get there. The key is to have sufficient delay mechanisms in place that will allow enough time for the responder to arrive. This is the delay mechanism. Ask yourself, what is the earliest likely detection of unauthorized access? If it is an alarm on the outer door to the Research and Development area, then you must assume that the unauthorized individual entering is already inside by the time the alarm signal is received. There is usually some time spent trying to verify the authenticity of the alarm and once that is done, a security officer (for example) will need to be dispatched. This is the final part of the response. If this process takes 5 minutes and it takes another 5 minutes for the officer to get to the server room, 10 minutes has expired since first detection. If absolutely nothing can be done in 10 minutes, then you are okay. But if someone can grab a media and get back out, you did not have sufficient delay built-into your security approach. Perhaps there needs to be a locked metal storage cabinet with sufficient strength and locks that can resist at least 10 minutes of “attack” where sensitive media are stored. Maybe a secondary room with a solid door and lock is what is needed. This is what effective delay is all about.
Now we have already addressed the response to some degree but detection without response is largely worthless. When the first vehicle alarms became popular it became common to walk out into a parking lot and hear two or three car alarms going off. No one paid any attention and no one was responding. The audible alarm was designed as a “detection” system but without a “response” it was worthless. If you have a computer system that detects a possible penetration attempt, it is important to see what the response is. How long does it take for the response? And, of course, the question then is: how effective is the response? For example, if you have an unarmed security officer responding to a break-in and the intruder is armed with an AK-47, you had a response but the response was not appropriate. The key is to get both a timely and an effective response for the situation that was detected.
This is a structure for conducting a vulnerability assessment. You must have all four components, and they must interact to have effective security and not have vulnerabilities.
Depending on the likelihood of occurrence/threat issues and the consequence/business impact analysis (the third part of the risk assessment), we can determine which of the identified vulnerabilities warrants being lowered by implementing various countermeasures. This can even help determine the priority of implementation of countermeasures. A good strategy would be to first implement the countermeasures that can most significantly lower the risk. If you cannot implement all countermeasures, focus first on those that give you the biggest “bang for your buck” or for the time you have invested.
For example, if your threat assessment determines that your business has a relatively high potential threat for business espionage and that the modus operandi of most of the current business spies in the industry and location/locations of concern have been to try and piggyback (follow employees with legitimate access) into the production area to view processes being used there, you might want to focus on your access control standards for the production area.
If, during your vulnerability assessment phase of the risk assessment, you see that there is a considerable amount of piggybacking going on because there is no turnstile and people are entering/exiting and even holding the door open for others, you have to decide if the threat warrants a security officer being stationed there to better control access, or if a turnstile needs to be installed. Maybe that solution, combined with improved employee security (education and awareness) training, could sufficiently lower the vulnerability because employees might begin to understand why they cannot hold the door open for others to enter.
If you cannot protect the entire production area, you might also try and determine if are there any areas where there are some special and sensitive methods or processes being used. Can those be further segregated and access to those areas enhanced, as opposed to trying to invest in strengthening access control for the entire production area? These are consequence-related issues. Or maybe the controls do need to be high for the entire area because the most sensitive information is throughout the area. Once these questions are answered in your consequence/impact assessment, you can determine which of the access control measures needs to be implemented and you will know exactly why (threat and consequence based) you did what you did.
Another strategy is to implement simple and low-cost countermeasures quickly. This “low hanging fruit” may not have as big an impact on lowering the overall vulnerability as another countermeasure but implementing several of these can become an important vulnerability- (and hence risk-) lowering countermeasure. Senior management like these because the cost is low and yet there is a reduction in vulnerability/risk. Examples of “low hanging fruit” might be changing some processes (requiring a government identification when signing in on a roster), a trained and effective escort for visitors, and general or specialized security training.
In this book we address various aspects of business espionage threat. We will focus on the types of businesses being targeted (the diversity of which is apparent from the case studies in Chapters 3, 4, 5, 6, 7, and 8) and on looking for who might be behind the business-spying efforts and, finally, on what methods they are likely to use (also summarized in the case studies). That kind of thorough threat assessment is the first step in an accurate, up-to-date risk assessment. But understand that it is nearly impossible for a business to lower the threat. The threat is largely impacted by outside entities that can include nation states. While a company likely cannot neutralize a threat on its own, it can understand the threat and plan countermeasures that blunt the threat with strong security measures. Strong security measures can sometimes even deter a potential threat.
You should also look at the typical vulnerabilities and gaps in the current security program and how to evaluate those. That vulnerability assessment will suggest the most important corrective actions and/or new/enhanced countermeasures. The ability to reduce vulnerabilities is an important part of lowering risk for a business.
When considering vulnerabilities it is also important to have good security procedures, policies, and standards. The standards must be realistic and effective against the threats faced. If you do not have a good understanding of the standards that should be employed, go with the basic security standards established by various professional security associations (e.g., ASIS International). Many of the basic physical and IT security standards will apply to most threats.
We will focus on the types of businesses being targeted (the diversity of which is apparent from the case studies in Chapters 3, 4, 5, 6, 7, and 8) and on looking for who might be behind the business-spying efforts and, finally, on what methods they are likely to use (also summarized in the case studies).
Summary
In summary, it is important to remember that the vulnerabilities identified probably lead to the most important corrective actions/countermeasures and implementing these can then, in turn, lower business espionage risk. Again, there is little that can be done by a company to lower threats. For example, weather events such as tornadoes or hurricanes are out of our control, and even state-sponsored espionage is bigger than most companies can neutralize on their own. Furthermore, you cannot give your competitors integrity; they either have integrity built into their company culture or they do not.
Companies can sometimes reorganize processes or diversify supply chains, for more redundancy and less exposure than what a consequence assessment has identified. This can lower the consequence score and reduce risk, but even that is sometimes difficult to achieve. So, the main way you can lower your risk is to lower the vulnerability score and that means reducing the number of security vulnerabilities you have, which makes your business a “harder target” for those who would try and spy on you.
In this book, business espionage security risk drives the need for countermeasures. It helps companies determine how much of their limited resources they should allocate to counter business espionage.
By properly focusing your security efforts and optimizing, not necessarily just maximizing, your efforts you can effectively deal with business espionage threat and greatly improve your overall protection against business espionage. The fundamental building block for all of this is a good, solid risk assessment that includes a threat assessment, a vulnerability assessment, and a consequence/business impact assessment. These are then combined to create a more complete risk picture, which is the underlying approach of this book when examining business espionage.
Whether some business leaders recognize it or not, intellectual property is the lifeblood of an enterprise. It is important to protect that “lifeblood,” and we will be addressing how to do that throughout the book but especially through the countermeasures detailed in Chapters 8, 9, 10, and 11.