Chapter 6
Identify Security Threats to a Network and Describe General Methods to Mitigate Those Threats
The Cisco CCNA exam objectives covered in this chapter include the following:
- Describe today’s increasing network security threats and explain the need to implement a comprehensive security policy to mitigate the threats.
- Explain general methods to mitigate common security threats to network devices, hosts, and applications.
- Describe the functions of common security appliances and applications.
- Describe security recommended practices, including initial steps to secure network devices.
If you’re a sysadmin, it’s my guess that shielding sensitive, critical data, as well as your network’s resources, from every possible evil exploit is a top priority. Cisco has some really effective security solutions that will arm you with the tools you need to make this happen.
In this chapter, you’ll learn a lot about deterring the most common threats to your network’s security with Cisco routers and IOS Firewalls that, together, offer quite a powerful, integrated detection package against many types of invasions. I’m going to give you the lowdown on how the Cisco IOS Firewall provides actual security and policy enforcement for both your internal and external networking needs. I’ll also show you how to create secure connections to remote routers and switches.
Describe Today’s Increasing Network Security Threats and Explain the Need to Implement a Comprehensive Security Policy to Mitigate the Threats
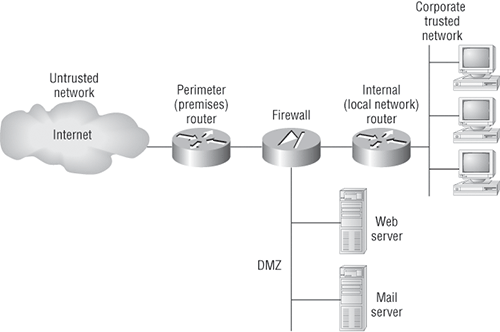
In medium-sized to large enterprise networks, the various strategies for security are based on a recipe of internal and perimeter routers plus firewall devices. Internal routers provide additional security to the network by screening traffic to various parts of the protected corporate network, and they do this by using access lists. Figure 6-1 shows where these devices are located in a typical secured network.
I’ll use the terms trusted network and untrusted network throughout this chapter, so it’s important that you can see where they are found in a typical secured network. The demilitarized zone (DMZ) can be global (real) Internet addresses or private addresses, depending on how you configure your firewall, but this is typically where you’ll find the HTTP, DNS, email, and other Internet-type corporate servers.
As discussed previously, instead of having routers, you can use virtual local area networks (VLANs) with switches on the inside trusted network. Multilayer switches containing their own security features can sometimes replace internal (LAN) routers to provide higher performance in VLAN architectures.
First, let’s discuss the security threats a typical secured internetwork faces; then I’ll explain some methods of protecting the internetwork using the Cisco IOS Firewall feature set and access lists.
Figure 6-1: A typical secured network
Recognizing Security Threats
Security attacks vary considerably in their complexity and threat level, and some even happen because of user error.
It all comes down to planning, or rather, lack thereof. Basically, the vital tool that the Internet has become today was absolutely unforeseen by those who brought it into being. This is a big reason why security is now such an issue—most IP implementations are innately insecure. Fortunately, Cisco has a few tricks up its sleeve to help us with this, but first, let’s examine some common attack profiles:
Application Layer Attacks These attacks commonly zero in on well-known holes in the software that is typically found running on servers. Favorite targets include FTP, sendmail, and HTTP. Because the permissions level granted to these accounts is most often “privileged,” intruders simply access and exploit the machine that’s running one of the applications I just mentioned.
Autorooters You can think of these as a kind of hacker automaton. Hackers use something called a rootkit to probe, scan, and then capture data on a strategically positioned computer that’s poised to give them “eyes” into entire systems—automatically!
Backdoors These are simply paths leading into a computer or network. Through simple invasions, or via more elaborate “Trojan horse” code, intruders can use their implanted inroads into a specific host or even a network whenever they want to—until you detect and stop them, that is!
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks Basically, a service is made unavailable by overwhelming the system that normally provides it. A Denial of Service attack is characterized by a flood of packets that are requesting a TCP connection to a server, and there are several different flavors:
TCP SYN Flood This type of attack begins when a client initiates a seemingly run-of-the-mill TCP connection and sends a SYN message to a server. The server predictably responds by sending a SYN-ACK message back to the client machine, which then establishes the connection by returning an ACK message. This sounds fine, but it’s actually during this process—when the connection is only halfway open—that the victim machine is literally flooded with a deluge of half-open connections and pretty much becomes paralyzed.
“Ping of Death” Attacks TCP/IP’s maximum packet size is 65,536 octets, and this attack is executed by simply pinging with oversized packets, causing a device to keep rebooting incessantly, freeze up, or just totally crash.
Tribe Flood Network (TFN) and Tribe Flood Network 2000 (TFN2K) TFN and TFN2K initiate synchronized DoS attacks from multiple sources and can target multiple devices. This is achieved, in part, by something known as “IP spoofing,” which I’ll be describing soon.
Stacheldraht This attack is actually a mélange of methods, and it translates from the German term for barbed wire. It basically incorporates TFN and adds a dash of encryption. It all begins with a huge invasion at the root level, leading up to a DoS attack.
IP Spoofing This is pretty much what it sounds like it is—an intruder from within or outside your network masquerades as a trusted host machine by doing one of two things: presenting with an IP address that’s inside your network’s scope of trusted addresses, or using an approved, trusted external IP address. Because the hacker’s true identity is veiled behind the spoofed address, this is often just the beginning of your problems.
Man-in-the-Middle Attacks These attacks involve stealing packets when they are en route. A common guilty party could be someone working for your own ISP using a tool known as a sniffer (discussed later) and augmenting it with routing and transport protocols.
Network Reconnaissance Before breaking into a network, hackers often gather all the information they can about it, because the more they know about the network, the better they can compromise it. They accomplish their objectives through methods such as port scans, DNS queries, and ping sweeps.
Packet Sniffers This is the tool I mentioned earlier, but I didn’t tell you what it is, and it may come as a surprise that it’s actually software. Here’s how it works: A network adapter card is set to promiscuous mode so that it will send all packets snagged from the network’s Physical layer through to a special application to be viewed and sorted. A packet sniffer can nick some highly valuable, sensitive data including, but not limited to, passwords and usernames, making them prized among identity thieves.
Password Attacks These come in many varieties, and even though they can be achieved via more sophisticated types of attacks like IP spoofing, packet sniffing, and Trojan horses, their sole purpose is to discover user passwords so that the thief can pretend to be a valid user and then access that user’s privileges and resources.
Brute Force Attack This is another software-oriented attack. It employs a program running on a targeted network that tries to log in to some type of shared network resource such as a server. For the hacker, it’s ideal if the accessed accounts have a lot of privileges, because then they can form backdoors to gain access later and bypass the need for passwords entirely.
Port Redirection Attacks This approach requires a host machine that the hacker has broken into and uses to get malicious traffic (that normally wouldn’t be allowed passage) through a firewall.
Trojan Horse Attacks and Viruses These two are actually pretty similar. Both Trojan horses and viruses infect user machines with malicious code and mess them up with varying degrees of paralysis, destruction, and even death! They do have their differences, though. Viruses are really just nasty programs attached to command.com, which just happens to be the main interpreter for all Windows systems. Viruses then run amok, deleting files and infecting any flavor of command.com they find on the diseased machine. The difference between a virus and a Trojan horse is that Trojans are actually complete applications encased inside code that makes them appear to be completely different entities—say, a simple, innocent game—instead of the ugly implements of destruction they truly are.
Trust Exploitation Attacks These happen when someone exploits a trust relationship inside your network. For example, a company’s perimeter network connection usually shelters important things like SMTP, DNS, and HTTP servers, making the servers really vulnerable because they’re all on the same segment.
I’m not going to go into detail on how to mitigate each and every one of the security threats I just talked about, not only because that would be outside the scope of this book, but also because the methods I am going to teach you will truly protect you from being attacked in general. You will learn enough tricks to make all but the most determined hackers give up on you and search for easier prey. So basically, think of this as a chapter on how to practice “safe networking.”
Exam Essentials
Remember the basic strategy for security. In medium-sized to large enterprise networks, the various strategies for security are based on some recipe of internal and perimeter routers plus firewall devices.
Remember the four typical Denial of Service (DoS) attacks. There are four typical DoS attacks used on today’s networks: TCP SYN flood, Ping of Death, Tribe Flood Network (TFN), and Stacheldraht.
Explain General Methods to Mitigate Common Security Threats to Network Devices, Hosts, and Applications
Cisco IOS software runs on upward of 80 percent of the Internet backbone routers out there, and it’s probably the most critical part of the network infrastructure. Therefore, the discussion for this section will assume that Cisco IOS’s software-based security, known as the Cisco IOS Firewall feature set, is being used for the end-to-end Internet, intranet, and remote-access network security solutions. Let’s take a look.
Cisco’s IOS Firewall
Here’s where you’re going to find out how to mitigate some of the more common security threats on the list I gave you earlier in this chapter by using these Cisco IOS Firewall features:
Stateful IOS Firewall Inspection Engine This is your perimeter protection feature because it gives your internal users secure access control on a per-application basis. People often call it Context-Based Access Control (CBAC).
Intrusion Detection A deep packet inspection tool that lets you monitor, intercept, and respond to abuse in real time by referencing 102 of the most common attack and intrusion detection signatures.
Firewall Voice Traversal An application-level feature based on the protocol’s understanding of call flow, as well as the relevant open channels. It supports both the H.323v2 and Session Initiation Protocol (SIP) voice protocols.
ICMP Inspection Basically permits responses to ICMP packets, such as ping and traceroute, that come from inside your firewall while denying other ICMP traffic.
Authentication Proxy A feature that makes users authenticate any time they want to access the network’s resources through HTTP, HTTPS, FTP, and Telnet. It keeps personal network access profiles for users and automatically retrieves them from a RADIUS or TACACS+ server and applies them.
Destination URL Policy Management A suite of features that’s commonly referred to as URL filtering.
Per-User Firewalls Personalized, user-specific, downloadable firewalls obtained through service providers. You can also get personalized ACLs and other settings via AAA server profile storage.
Cisco IOS Router and Firewall Provisioning Allows for automatic router provisioning based on the role of the device, version updates, and security policies.
Denial of Service (DoS) Detection and Prevention A feature that checks packet headers and drops any packets it finds suspicious.
Dynamic Port Mapping A sort of adapter that permits applications supported by firewalls on nonstandard ports.
Java Applet Blocking Protects you from any strange, unrecognized Java applets.
Basic and Advanced Traffic Filtering
You can use standard, extended, and even dynamic ACLs like Lock-and-Key traffic filtering with Cisco’s IOS Firewall. You also get to apply access controls to any network segment you want. Plus, you can specify the exact kind of traffic you want to allow to pass through any segment.
Here are some of the variations of access control and security enhancing options available:
Policy-Based, Multi-Interface Support Allows you to control user access by IP address and interface depending on your security policy.
Network Address Translation (NAT) Conceals the internal network from the outside, increasing security.
Time-Based Access Lists Determines security policies based on the exact time of day and the particular day of the week.
Peer Router Authentication Guarantees that routers are getting dependable routing information from actual, trusted sources. (For this to work, you need a routing protocol that supports authentication, such as RIPv2, EIGRP, or OSPF.)
Now that you’ve been briefed on security threats, relevant features of the Cisco IOS Firewall, and how to use that software to your advantage, let’s dive deep into the world of access lists and learn how to use ACLs to mitigate security threats.
Exam Essentials
Remember the basic services that the Cisco IOS Firewall provides. The Cisco IOS Firewall provides, at a minimum, a stateful IOS firewall inspection engine, intrusion detection, firewall voice traversal, ICMP inspection, and authentication proxy, among many other services.
Describe the Functions of Common Security Appliances and Applications
In this section, I’ll discuss the most commonly used advanced access control lists and applications used by Cisco routers. First, however, I am going to mention two security appliances typically found on a network.
Security Appliances
The two most noteworthy technologies that you can use to provide network security are intrusion prevention systems (IPS) and intrusion detection systems (IDS).
An IPS is an appliance that monitors network activities for malicious or unwanted behavior and can react in real time to block or prevent those activities. For example, an IPS will operate in-line to monitor all network traffic for malicious code or attacks. When an attack is detected, it can drop the offending packets while still allowing all other traffic to pass.
An IDS generally detects unwanted manipulations to computer systems, mainly through the Internet. The manipulations may take the form of attacks by crackers. An IDS is used to detect many types of malicious network traffic and computer usage that can’t be detected by a conventional firewall. This includes network attacks against vulnerable services, data-driven attacks on applications, host-based attacks such as privilege escalation, unauthorized logins and access to sensitive files, and malware (viruses, Trojan horses, and worms).
Lock and Key (Dynamic ACLs)
This type of ACL depends on either remote or local Telnet authentication in combination with extended ACLs.
Before you can configure a dynamic ACL, you need to apply an extended ACL on your router to stop the flow of traffic through it. The only way anyone can get through the blockade is if they telnet the router and gain authentication. It works like this: The Telnet connection the user initiated gets dropped and is replaced with a single-entry dynamic ACL that’s appended to the extended ACL already in place. This allows traffic to get through for a specific amount of time—and as you may have guessed, time-outs can and do happen.
Reflexive ACLs
These ACLs filter IP packets depending on upper-layer session information, and they often permit outbound traffic to pass but place limitations on inbound traffic. You can’t define reflexive ACLs with numbered or standard IP ACLs, or any other protocol ACLs for that matter. They can be used along with other standard or static extended ACLs, but they’re only defined with extended named IP ACLs.
Context-Based Access Control (Cisco IOS Firewall)
Context-Based Access Control (CBAC) is available only if you have the Cisco IOS Firewall set in the IOS. It’s used to allow or deny connections based on the context in which the connections are requested.
CBAC’s job is to scrutinize any and all traffic that’s attempting to come through the firewall, so it can find out about and control the state information for TCP and UDP sessions. It uses the information it’s gathered to determine whether to create a temporary pathway into the firewall’s access lists.
To make this happen, just configure ip inspect lists in the same direction that the traffic is flowing. If you don’t do this, any return traffic will be unable to get back through, which will negatively impact any session connections originating from inside the internal network.
Take a look at Figure 6-2, which illustrates in a very simple way how a Cisco IOS Firewall (CBAC) works.
Figure 6-2: A Cisco IOS Firewall (CBAC)
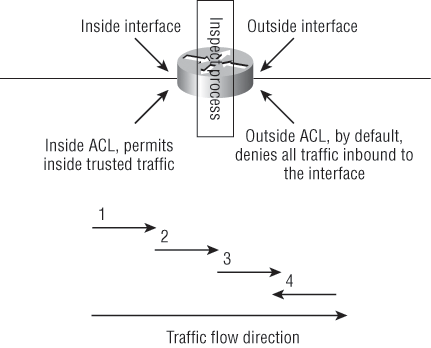
A router that’s configured with the Cisco IOS Firewall will process traffic in the following manner:
1. If the inside ACL approves, the router will get all of the inside packets sent to it.
2. The approved traffic is subjected to the firewall’s ip inspect process, which adds the approved connection’s state information into the state table.
3. The traffic passes through the IP inspect process, which then creates a dynamic ACL entry and puts it into the outside ACL so that the return traffic will be allowed to pass back through the router.
Authentication Proxy
I have Authentication Proxy set on all of my routers. In order for me to do that, I also had to have the Cisco IOS Firewall feature set up. I have the configuration set up this way because the authentication proxy is a good thing to have on my side.
This is true because it authenticates inbound users, outbound users, or both. Those who would normally be blocked by an ACL can just bring up a browser to get through the firewall and then authenticate on a TACACS+ or RADIUS server.
Exam Essentials
Remember the two types of security appliances typically found on a network. The two types of security appliances that you’ll typically find on a network are intrusion prevention systems (IPS) and intrusion detection systems (IDS).
Understand what CBAC is. Context-Based Access Control scrutinizes any and all traffic that’s attempting to come through the firewall, so it can find out about and control the state information for TCP and UDP sessions.
Describe Security Recommended Practices, Including Initial Steps to Secure Network Devices
Here’s a list of the many security threats you can mitigate with ACLs:
- IP address spoofing, inbound
- IP address spoofing, outbound
- Denial of service (DoS) TCP SYN attacks, blocking external attacks
- DoS TCP SYN attacks, using TCP Intercept
- DoS smurf attacks
- Filtering ICMP messages, inbound
- Filtering ICMP messages, outbound
- Filtering traceroute
You should never configure a private network to allow IP packets that contain the source address of any internal hosts or networks. Moreover, when configuring ACLs from the Internet to your production network, you should follow these rules in order to mitigate security problems:
- Deny any addresses from your internal networks.
- Deny any local host addresses (127.0.0.0/8).
- Deny any reserved private addresses.
- Deny any addresses in the IP multicast address range (224.0.0.0/4).
None of these addresses should be allowed to enter your internetwork!
Exam Essentials
Remember the security rules that you should follow when configuring ACLs from the Internet to your production network. Deny any addresses from your internal networks, deny any local host addresses (127.0.0.0/8), deny any reserved private addresses, and deny any addresses in the IP multicast address range (224.0.0.0/4).
1. Which Cisco IOS Firewall feature set allows you to use a browser to get through the firewall and then authenticate on a TACACS+ or RADIUS server?
A. Reflexive ACLs
B. Authentication proxy
C. CBAC
D. Dynamic ACLs
2. What does the Cisco IOS use to scrutinize any and all traffic that’s attempting to come through the firewall so that it can find out about and control the state information for TCP and UDP sessions?
A. Reflexive ACLs
B. Authentication proxy
C. CBAC
D. Dynamic ACLs
3. Which type of ACLs filter IP packets depending on upper-layer session information and can permit outbound traffic to pass but place limitations on inbound traffic?
A. Reflexive ACLs
B. Authentication proxy
C. CBAC
D. Dynamic ACLs
4. Which type of ACL depends on either remote or local Telnet authentication in combination with extended ACLs?
A. Reflexive ACLs
B. Authentication proxy
C. CBAC
D. Dynamic ACLs
5. Which two of the following are considered to be Denial of Service attacks (DoS)?
A. TCP SYN flood
B. Application layer attacks
C. Ping of Death attacks
D. Autorooters
6. Which of the following commonly zero in on well-known holes in the software that is typically found running on servers?
A. Application layer attacks
B. Autorooters
C. Backdoors
D. Denial of Service (DoS) attacks
7. Which of the following refers to paths leading into a computer or network that can be used for Trojan horse code?
A. Application layer attacks
B. Autorooters
C. Backdoors
D. Denial of Service (DoS)
8. Which of the following probe, scan, and then capture data on a strategically positioned computer?
A. Application layer attacks
B. Autorooters
C. Backdoors
D. Denial of Service (DoS) attacks
9. Which of the following makes a service unavailable by overwhelming the system that normally provides it?
A. Application layer attacks
B. Autorooters
C. Backdoors
D. Denial of Service (DoS) attacks
10. Which two of the following are security appliances that can be installed in a network?
A. IDS
B. IPS
C. AAA
D. SDM
1. B. Users who would normally be blocked by an ACL can just bring up a browser to get through the firewall and then authenticate on a TACACS+ or RADIUS server.
2. C. The Context-based Access Control’s (CBAC’s) job is to scrutinize any and all traffic that’s attempting to come through the firewall so it can find out about and control the state information for TCP and UDP sessions. It also uses the information it’s gathered to determine whether to create a temporary pathway into the firewall’s access lists.
3. A. Reflexive ACLs filter IP packets depending on upper-layer session information, and they often permit outbound traffic to pass but place limitations on inbound traffic. You can’t define reflexive ACLs with numbered or standard IP ACLs, or any other protocol ACLs for that matter.
4. D. Dynamic ACLs first drop the Telnet connection that the user initiated and replace it with a single-entry dynamic ACL that’s appended to the extended ACL already in place. This causes traffic to be allowed through for a specific amount of time.
5. A, C. The four typical types of Denial of Service attacks are TCP SYN flood, Ping of Death, Tribe Flood Network (TFN), and Stacheldraht.
6. A. Application layer attacks commonly zero in on well-known holes in the software that’s typically found running on servers. Favorite targets include FTP, sendmail and HTTP.
7. C. Backdoors are simply paths leading into a computer or network. However, through simple invasions, or via more elaborate Trojan horse code, hackers can use them as inroads into a specific host or even a network.
8. B. Intruders use something called a rootkit to probe, scan, and then capture data on a strategically positioned computer that’s poised to give them “eyes” into entire systems.
9. D. DoS attacks make a service unavailable by overwhelming the system that normally provides it, and there are several different versions.
10. A, B. The two technologies that you can use to provide network security are intrusion prevention systems (IPS), which (hopefully) prevent intrusions, and intrusion detection systems (IDS), which only detect intrusions and tell you about them.
