Chapter 5
Explain and Select the Appropriate Administrative Tasks Required for a WLAN
The Cisco CCNA exam objectives covered in this chapter include the following:
- Describe standards associated with wireless media (including IEEE, Wi-Fi Alliance, and ITU/FCC).
- Identify and describe the purpose of the components in a small wireless network (including SSID, BSS, and ESS).
- Identify the basic parameters to configure on a wireless network to ensure that devices connect to the correct access point.
- Compare and contrast wireless security features and capabilities of WPA security (including open, WEP, and WPA-1/2).
- Identify common issues with implementing wireless networks (including interfaces and misconfigurations).
If you want to understand the basic wireless LANs, or WLANs, that are the most commonly used today, just think 10BaseT Ethernet with hubs. What this means is that WLANs typically run half-duplex communication—everyone is sharing the same bandwidth and only one user is communicating at a time. This isn’t necessarily bad—it’s just not good enough. Because most people rely on wireless networks today, it’s critical that those networks evolve to keep up with everyone’s rapidly escalating needs.
Cisco has reacted by coming up with the Cisco Unified Wireless Solution, which works, with all types of wireless connections—and it works securely, too!
Describe Standards Associated with Wireless Media (Including IEEE, Wi-Fi Alliance, and ITU/FCC)
Various agencies have been around for a very long time to help govern the use of wireless devices, frequencies, standards, and how the frequency spectrums are used. Table 5-1 shows the current agencies that help create, maintain, and enforce wireless standards worldwide.
Table 5-1: Wireless Agencies and Standards
| Agency | Purpose | Website |
| Institute of Electrical and Electronics Engineers (IEEE) | Creates and maintains operational standards | www.ieee.org |
| Federal Communications Commission (FCC) | Regulates the use of wireless devices in the U.S. | www.fcc.gov |
| European Telecommunications Standards Institute (ETSI) | Chartered to produce common standards in Europe | www.etsi.org |
| Wi-Fi Alliance | Promotes and tests for WLAN interoperability | www.wi-fi.com |
| WLAN Association (WLANA) | Educates and raises consumer awareness regarding WLANs | www.wlana.org |
Because WLANs transmit over radio frequencies, they’re regulated by the same types of laws used to govern things like AM/FM radios. The Federal Communications Commission (FCC) regulates the use of wireless LAN devices, and the Institute of Electrical and Electronics Engineers (IEEE) creates standards based on the frequencies that the FCC releases for public use.
The FCC has released three unlicensed bands for public use: 900MHz, 2.4GHz, and 5.7GHz. The 900MHz and 2.4GHz bands are referred to as the Industrial, Scientific, and Medical (ISM) bands, and the 5GHz band is known as the Unlicensed National Information Infrastructure (UNII) band. Figure 5-1 shows where the unlicensed bands sit within the RF spectrum.
Figure 5-1: Unlicensed frequencies
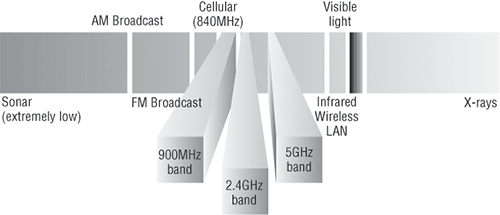
If you opt to deploy wireless in a range outside of the three public bands shown in Figure 5-1, you’ll need to get a specific license from the FCC to do so. When the FCC opened the three frequency ranges for public use, many manufacturers were able to start offering myriad products that flooded the market, with 802.11b/g being the most widely used wireless network today.
The Wi-Fi Alliance grants certification for interoperability among 802.11 products offered by various vendors. This certification provides a sort of comfort zone for the users purchasing the many types of products, although in my personal experience, it’s a whole lot easier to buy all of your access points from the same manufacturer.
In the current U.S. wireless LAN market, the IEEE has created and maintained several accepted operational standards and drafts. Let’s take a look at these standards and then talk about how the most commonly used standards work.
The 802.11 Standards
As you learned in Chapter 2, “Configure, Verify, and Troubleshoot a Switch with VLANs and Interswitch Communications,” the Ethernet standards group committee is 802.3. Likewise, wireless networking has its own 802 standards group, starting with 802.11 and including various other evolving standards groups such as 802.16 and 802.20. There is no doubt that cellular networks will become huge players in the wireless future—but for now, let’s concentrate on the 802.11 standards committee and subcommittees.
IEEE 802.11 was the original standardized WLAN at 1 and 2Mbps. It runs in the 2.4GHz radio frequency and was ratified in 1997, even though not very many products popped up until around 1999 when 802.11b was introduced. All the committees listed in Table 5-2 are amendments to the original 802.11 standard—except for 802.11F and 802.11T, which are both stand-alone documents.
Table 5-2: 802.11 Committees and Subcommittees
| Committee | Purpose |
| IEEE 802.11a | 54Mbps, 5GHz standard |
| IEEE 802.11b | Enhancements to 802.11 to support 5.5 and 11Mbps |
| IEEE 802.11c | Bridge operation procedures; included in the IEEE 802.1D standard |
| IEEE 802.11d | International roaming extensions |
| IEEE 802.11e | Quality of service |
| IEEE 802.11F | Inter-Access Point Protocol |
| IEEE 802.11g | 54Mbps, 2.4GHz standard (backward compatible with 802.11b) |
| IEEE 802.11h | Dynamic Frequency Selection (DFS) and Transmit Power Control (TPC) at 5Ghz |
| IEEE 802.11i | Enhanced security |
| IEEE 802.11j | Extensions for Japan and U.S. public safety |
| IEEE 802.11k | Radio resource measurement enhancements |
| IEEE 802.11m | Maintenance of the standard; odds and ends |
| IEEE 802.11n | Higher throughput improvements using MIMO (multiple input, multiple output) antennas |
| IEEE 802.11p | Wireless Access for the Vehicular Environment (WAVE) |
| IEEE 802.11r | Fast roaming |
| IEEE 802.11s | ESS Extended Service Set Mesh Networking |
| IEEE 802.11T | Wireless Performance Prediction (WPP) |
| IEEE 802.11u | Internetworking with non-802 networks (cellular, for example) |
| IEEE 802.11v | Wireless network management |
| IEEE 802.11w | Protected management frames |
| IEEE 802.11y | 3650–3700 operation in the U.S. |
2.4GHz (802.11b)
The first widely deployed wireless standard was 802.11b. It operates in the 2.4GHz unlicensed radio band and delivers a maximum data rate of 11Mbps. The 802.11b standard has been widely adopted by both vendors and customers who found that its 11Mbps data rate worked pretty well for most applications. However, 802.11b has been mostly replaced by 802.11g, which operates in the same frequency and can go up to 54 Mbps.
An interesting thing about all Cisco 802.11 WLAN products is that they have the ability to data-rate-shift while moving. This allows the person operating at 11Mbps to shift to 5.5Mbps and then to 2Mbps as the distance between the access point (AP) and the station increases. Furthermore, this rate shifting happens without losing connection and with no interaction from the user. Rate shifting also occurs on a transmission-by-transmission basis. This is important because it means that the access point can support multiple clients at varying speeds, depending on the location of each client.
The problem with 802.11b lies in the way in which the Data Link layer is dealt. In order to solve problems in the RF spectrum, a type of Ethernet collision detection was created called CSMA/CA, or Carrier Sense Multiple Access with Collision Avoidance. Check this out in Figure 5-2.
Figure 5-2: 802.11b CSMA/CA
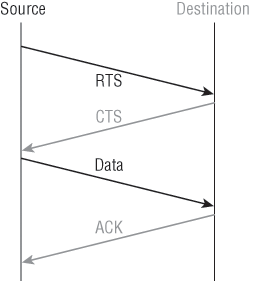
CSMA/CA is more involved than CSMA/CD, which is the contention method used on wired Ethernet. Since, unlike with wired Ethernet, stations cannot detect a collision, each and every wireless frame transfer must be acknowledged. Because of this rather cumbersome process, the method has tremendous overhead. When you also consider that every frame goes through the AP when it traverses from Station A to Station B, the overhead in a single frame transfer is compounded.
Cordless phones and microwave ovens can cause interference in the 2.4GHz range.
In the United States, there are currently 11 channels that can be configured within the 2.4GHz range. However, only three of these channels are considered non-overlapping: 1, 6, and 11.
Figure 5-3 shows the 14 different channels (each 22MHz wide) that the FCC released within the 2.4GHz range:
Figure 5-3: ISM 2.4GHz channels
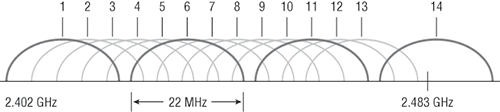
Because there are three channels (1, 6, and 11) that don’t overlap, you can have three access points in the same general area without experiencing interference. One of the first things you should do when configuring an AP is set the AP channel.
2.4GHz (802.11g)
The 802.11g standard was ratified in June 2003 and is backward compatible with 802.11b. The 802.11g standard delivers the same 54Mbps maximum data rate as 802.11a, but it runs in the 2.4GHz range—the same as 802.11b.
Because 802.11b/g operate in the same 2.4GHz unlicensed band, migrating to 802.11g is an affordable choice for organizations with existing 802.11b wireless infrastructures. Just keep in mind that 802.11b products cannot be “software upgraded” to 802.11g, because 802.11g radios use a different chipset in order to deliver the higher data rate.
But still, much like Ethernet and FastEthernet, 802.11g products can be commingled with 802.11b products in the same network. Yet, for example, completely unlike Ethernet, if you have four users running 802.11g cards and one user starts using an 802.11b card, everyone connected to the same access point is then forced to run the 802.11b CSMA/CA method, which negatively affects the throughput. So to optimize performance, it’s recommended that you disable the 802.11b-only mode on all your access points.
To explain this further, 802.11b uses a modulation technique called Direct Sequence Spread Spectrum (DSSS), which is not as robust as the Orthogonal Frequency Division Multiplexing (OFDM) modulation used by both 802.11g and 802.11a. The 802.11g clients using OFDM enjoy much better performance at the same ranges than the 802.11b clients do, but—and remember this—when 802.11g clients are operating at the 802.11b rates (11, 5.5, 2, and 1Mbps), they’re actually using the same modulation that 802.11b uses.
5GHz (802.11a)
The IEEE ratified the 802.11a standard in 1999, but the first 802.11a products didn’t begin appearing on the market until late 2001. The 802.11a standard delivers a maximum data rate of 54Mbps with 12 non-overlapping frequency channels.
Operating in the 5GHz radio band, 802.11a is also immune to interference from devices that operate in the 2.4GHz band, such as microwave ovens, cordless phones, and Bluetooth devices. The 802.11a standard isn’t backward compatible with 802.11b because they have different frequencies, so you can’t just “upgrade” part of your network and expect everything to work together in perfect harmony, but there are plenty of dual-radio devices that will work in both types of networks. A definite plus for 802.11a is that it can work in the same physical environment without interference from 802.11b users.
All 802.11a products also have the ability to data-rate-shift while moving. The 802.11a products allow the person operating at 54Mbps to shift to 48Mbps, 36Mbps, 24Mbps, 18Mbps, 12Mbps, 9Mbps, and finally 6Mbps at the farthest distance at which it can still communicate with the AP.
2.4GHz/5GHz (802.11n)
The 802.11n standard builds on previous 802.11 standards by adding Multiple-Input Multiple-Output (MIMO), which uses multiple transmitters and receiver antennas to increase data throughput and range. The 802.11n standard can allow up to eight antennas, but most of today’s APs use only four to six. This setup permits considerably higher data rates than 802.11a/b/g do.
The following three vital items are combined in 802.11n to enhance performance:
- At the Physical layer, the way a signal is sent is changed, enabling reflections and interferences to become an advantage instead of a source of degradation.
- Two 20MHz-wide channels are combined to increase throughput.
- At the MAC layer, a different way of managing packet transmission is used.
It’s important to note that 802.11n isn’t truly compatible with 802.11b, 802.11g, or even 802.11a, but it is designed to be backward compatible with them. The 802.11n standard achieves backward compatibility by changing the way frames are sent so they can be understood by 802.11a/b/g.
Here’s a list of some of the primary components of 802.11n that together sum up why people claim 802.11n is more reliable and predictable:
40MHz Channels Both 802.11g and 802.11a use 20MHz channels and employ tones on the sides of each unused channel in order to protect the main carrier. This means that 11Mbps go unused and are basically wasted. The 802.11n standard aggregates two carriers to double the speed from 54Mbps to more than 108. Add in those wasted 11Mbps rescued from the side tones and you get a grand total of 119Mbps.
MAC Efficiency The 802.11 protocols require acknowledgment of each and every frame. The 802.11n can pass many packets before an acknowledgment is required, which saves you a huge amount of overhead. This is called block acknowledgment.
Multiple-Input Multiple-Output (MIMO) Several frames are sent by several antennae over several paths and are then recombined by another set of antennae to optimize throughput and multipath resistance. This is called spatial multiplexing.
Comparing 802.11
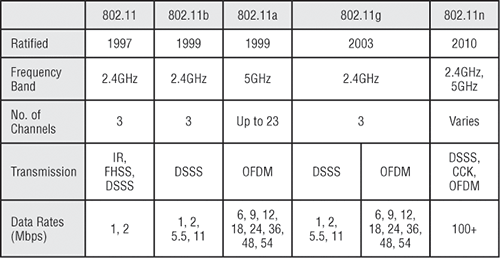
Figure 5-4 lists every IEEE standard in use today, along with the year it was ratified, its frequency, the number of non-overlapping channels, the Physical layer transmission techniques, and the data rates.
Figure 5-4: Standards for Spectrums and Speeds
Exam Essentials
Remember the three overlapping channels used with the 2.4GHz range. In the United States, only 11 channels are configurable, with channels 1, 6, and 11 being non-overlapping.
Remember how many channels are non-overlapping in the 5GHz range. The 802.11a standard delivers a maximum data rate of 54Mbps with 12 non-overlapping frequency channels.
Understand the IEEE 802.11a specification. The 802.11a standard runs in the 5GHz spectrum, and if you use the 802.11h extensions, you have 23 non-overlapping channels. The 802.11a standard can run up to 54Mbps, but only if you are less than 50 feet from an access point.
Understand the IEEE 802.11b specification. IEEE 802.11b runs in the 2.4GHz range and has three non-overlapping channels. It can handle long distances, but with a maximum data rate of up to 11Mpbs.
Understand the IEEE 802.11g specification. IEEE 802.11g is 802.11b’s big brother and runs in the same 2.4GHz range, but it has a higher data rate of 54Mbps if you are less than 100 feet from an access point.
Understand the IEEE 802.11n specification. The 802.11n standard adds efficiency and improvements to existing standards. IEEE 802.11n uses the same frequencies as 802.11b/g and 802.11a, but it uses Multiple-In-Multiple-Out (MIMO) to significantly increase the amount of data that can be transmitted.
Identify the major agencies that create, maintain, and enforce wireless standards. The FCC, Wi-Fi Alliance, the IEEE, the ETSI, and the WLAN associations are important governing bodies as described in Table 5-1.
Identify and Describe the Purpose of the Components in a Small Wireless Network (Including SSID, BSS, and ESS)
Transmitting a signal using the typical 802.11 specifications works a lot like it does with a basic Ethernet hub: They’re both two-way forms of communication, and they both use the same frequency to transmit and receive, often referred to as half-duplex, as mentioned earlier in the chapter. Wireless LANs (WLANs) use RFs that are radiated into the air from an antenna that creates radio waves. These waves can be absorbed, refracted, or reflected by walls, water, and metal surfaces, resulting in low signal strength. Because of this innate vulnerability to surrounding environmental factors, wireless will never offer the same robustness as a wired network, but wireless networks will continue to gain popularity despite this shortcoming.
Transmitting power can be increased to gain a greater transmitting distance, but doing so can create some nasty distortion, so it has to be done carefully. Using higher frequencies can attain higher data rates, but this is, unfortunately, at the cost of decreased transmitting distances. If lower frequencies are used, you get to transmit across greater distances but at lower data rates. This should make it pretty clear to you that understanding all the various types of WLANs you can implement is imperative in creating the LAN solution that best meets the specific requirements of the unique situation with which you’re dealing.
Also important to note is the fact that the 802.11 specifications were developed so that no licensing would be required in most countries to ensure users the freedom to install and operate without any licensing or operating fees. This means that any manufacturer can create products and sell them at a local computer store or wherever. It also means that all our computers should be able to communicate wirelessly without configuring much, if anything at all.
Service Sets
Now that I’ve discussed the very basics of the wireless devices used in today’s simple networks, I’ll describe the different types of networks you’ll run across or design and implement as your wireless networks grow. These include the following:
- Independent Basic Service Set (IBSS)
- Basic Service Set (BSS)
- Extended Service Set (ESS)
All types of networks define what is called a Service Set ID (SSID) that’s used to advertise your wireless network so hosts can connect to the access point (AP). You can have multiple SSIDs configured on an access point for security reasons. For example, you can designate that one SSID is open access for a public hot spot, while another SSID can use WEP or WPA2 for the employees that work at this public hot spot. The SSID name is broadcasted out the AP by default so the clients can find the AP and connect to the wireless network, and of course you can turn this feature off for security reasons.
IBSS
Using an ad IBSS (ad hoc) network is the easiest way to install wireless 802.11 devices. In this mode, the wireless NICs (or other devices) can communicate directly without the need for an AP. A good example of this is two laptops with wireless NICs installed. If both cards are set up to operate in ad hoc mode, they can connect and transfer files as long as the other network settings, like the IP protocols, are set up to enable this as well.
To create an Independent Basic Service Set (IBSS), ad hoc network, you only need two or more wireless-capable devices. Once you’ve placed them within a range of 20 to 40 meters of each other, they’ll “see” each other and be able to connect, assuming they share some basic configuration parameters. One computer may be able to share its Internet connection with the rest of the wireless stations in the IBSS.
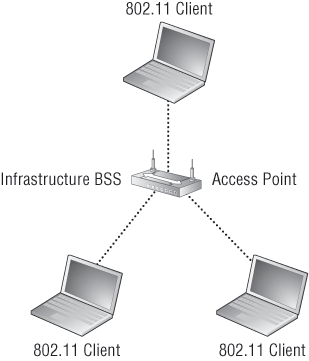
BSS
A BSS involves only a single access point. You create a BSS, bring up an AP, and create a name for the service set ID (SSID). Users can then connect to and use this SSID to access the wireless network, which may also provide connectivity to wired resources. When the AP connects to a wired network, it then becomes known as an Infrastructure Basic Service Set, or IBSS. Keep in mind that if you have a BSS/IBSS, users won’t be able to maintain network connectivity when roaming from AP to AP because each AP is configured with a different SSID name.
BSS wireless networks are also really helpful if you happen to have a couple of hosts that need to establish wireless communication directly between only themselves. You can also make this happen through something called ad hoc networking, but if you have an AP between the hosts it’s just called a BSS.
Figure 5-5 shows a basic service set using one SSID:
Figure 5-5: Basic Service Set (BSS)
ESS
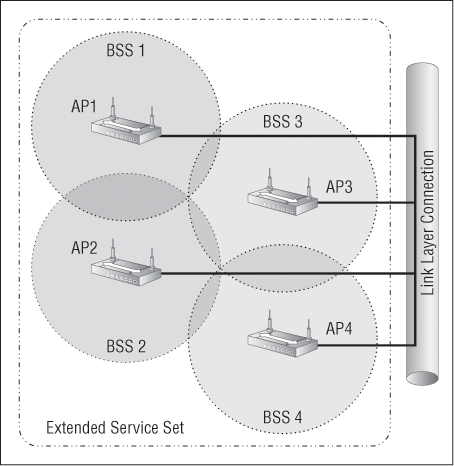
Mobile wireless clients can roam around within the same network if you set all your access points to the same SSID. Doing this creates an Extended Service Set (ESS). Figure 5-6 shows four APs configured with the same SSID in an office, thereby creating the ESS network.
For users to be able to roam throughout the wireless network—from AP to AP without losing their connection to the network—all APs must overlap by at least 10 percent and be set to different channels. As you’ll recall, an 8.02.11b/g network has only three non-overlapping channels (1, 6, and 11), so design is super important here!
Exam Essentials
Differentiate the three types of service sets. An IBSS is a service set with no AP and direct communication between the stations. A BSS is a service set consisting one AP and its associated stations. The ESS is two or more BSSs using the same SSID, which allows for seamless roaming between the APs.
Figure 5-6: Extended Service Set (ESS)
Identify the Basic Parameters to Configure on a Wireless Network to Ensure That Devices Connect to the Correct Access Point
It’s true that a wireless interface can really be just another interface on a router—and it looks just like that in a routing table or a separate device called an access point. In order to bring up a wireless interface, more configurations are needed than for a simple Fast Ethernet interface.
Check out the following output, and then I’ll tell you about the special configuration needs for this wireless interface.
R2(config-if)#int dot11radio0/3/0 R2(config-if)#ip address 10.1.8.1 255.255.255.0 R2(config-if)#description Connection to Corp ISR Router R2(config-if)#no shut R2(config-if)#ssid ADMIN R2(config-if-ssid)#guest-mode R2(config-if-ssid)#authentication open R2(config-if-ssid)#infrastructure-ssid R2(config-if-ssid)#no shut
What you see here is pretty commonplace until you get to the SSID configuration. This is the Service Set Identifier that creates a wireless network to which hosts can connect.
Unlike access points, the interface on the router is actually a routed interface, which is the reason the IP address is placed under the physical interface—typically, the IP address would be placed under the management VLAN or Bridge-Group Virtual Interface (BVI).
That guest-mode line means that the interface will broadcast the SSID so that wireless hosts will understand that they can connect to this interface.
Authentication open means just that: no authentication. (Even so, you still have to at least type that command to make the wireless interface work.)
Last, the infrastructure-ssid indicates that this interface can be used to communicate with other access points, or other devices on the infrastructure—meaning to the actual wired network itself and the resources on the wired network, such as servers.
You’re not done yet. The DHCP pool for the wireless clients still needs to be configured:
R2#config t R2(config)#ip dhcp pool Admin R2(dhcp-config)#network 10.1.8.0 255.255.255.0 R2(dhcp-config)#default-router 10.1.8.1 R2(dhcp-config)#exit R2(config)#ip dhcp excluded-address 10.1.8.1 R2(config)#
Creating DHCP pools on a router is actually a pretty simple process. To do so, you just create the pool name, add the network/subnet and the default gateway, and exclude any addresses you don’t want handed out (like the default gateway address)—and you’d usually add a DNS server as well.
Understand that the pool is basically attached to an interface that has an address from the same subnet created by the DHCP pool. In the preceding example, this is interface dot11radio 0/3/0. You can easily create another pool and have it connected with a LAN interface as in FastEthernet 0/0 by assigning an address on FastEthernet 0/0 that is from the subnet pool.
Exam Essentials
Remember how to set a Service Set Identifier (SSID) on a wireless routed interface. From the interface mode of the wireless routed interface, use the ssid ssid-name command. This is the Service Set Identifier that creates a wireless network to which hosts can connect.
Remember how to configure a wireless interface on a router to allow hosts to communicate to a wired infrastructure. Under the Router(config-if-ssid)# command prompt, use the command infrastructure-ssid to indicate that this interface can be used to communicate to other access points, or to the wired network.
Compare and Contrast Wireless Security Features and Capabilities of WPA Security (Including Open, WEP, and WPA-1/2)
The original 802.11 committee didn’t add security standards that are robust enough to work in a corporate environment. However, an enterprise wireless network demands this security. First let’s look at the basic security that was added into the original 802.11 standards and understand the shortcomings inherent in those methods.
Open Access
All Wi-Fi Certified wireless LAN products are shipped in “open-access” mode, with their security features turned off. While open access or no security may be appropriate and acceptable for public hot spots such as coffee shops, college campuses, and maybe airports, it’s definitely not an option for an enterprise organization, and likely not even adequate for your private home network.
Security needs to be enabled on wireless devices during their installation in enterprise environments. It may come as quite a shock, but some companies actually don’t enable any WLAN security features. Obviously, the companies that don’t are exposing their networks to tremendous risk.
Products are shipped with open access so that even someone who knows absolutely nothing about computers can buy an access point, plug it into a cable or DSL modem, and voilà—be up and running. It’s marketing, plain and simple, and simplicity sells.
SSIDs, WEP, and MAC Address Authentication
What the original designers of 802.11 did to create basic security was include the use of Service Set Identifiers (SSIDs), open or shared-key authentication, static Wired Equivalent Protocol (WEP), and optional Media Access Control (MAC) authentication. That sounds like a lot, but none of these really offers a serious security solution.
SSID is a common network name for the devices in a WLAN system that create the wireless LAN. An SSID prevents access by any client device that doesn’t have the SSID. However, by default, an access point broadcasts its SSID in its beacon many times a second, so even if SSID broadcasting is turned off, a wireless hacker can discover the SSID by monitoring the network and just waiting for a client response to the access point. That response information, as specified in the original 802.11 specifications, must be sent in the clear.
Two types of authentication were specified by the IEEE 802.11 committee: open and shared-key authentication. Open authentication involves little more than supplying the correct SSID—but it’s the most common method in use today. With shared-key authentication, the access point sends the client device a challenge-text packet that the client must then encrypt with the correct WEP key and return to the access point. Without the correct key, authentication will fail and the client won’t be allowed to associate with the access point. Shared-key authentication is still not considered secure because all an intruder has to do to get around this is detect both the cleartext challenge and the same challenge encrypted with a WEP key and then decipher the WEP key. For this reason, shared key isn’t used in today’s WLANs.
With open authentication, even if a client can complete authentication and associate with an access point, the use of WEP prevents the client from sending and receiving data from the access point unless the client has the correct WEP key. A WEP key is composed of either 40 or 128 bits and, in its basic form, is usually statically defined by the network administrator on the access point and all clients that communicate with that access point. When static WEP keys are used, a network administrator must perform the time-consuming task of entering the same keys on every device in the WLAN. Although there are easier methods to accomplish this today, this remains a cumbersome process.
Finally, allowed client MAC addresses can be statically typed into each access point in the form of a MAC address filter and the AP will deny access to any station whose MAC address is not on the list. Of course, because all MAC layer information must be sent in the clear, anyone equipped with a free wireless sniffer can just read the client packets sent to the access point and spoof their MAC address.
Encryption Methods
There are two basic encryption methods used in most wireless networks today: TKIP and AES. I’ll cover TKIP first.
Temporal Key Integrity Protocol (TKIP)
The IEEE 802.11i task group and the Wi-Fi Alliance, joining forces, came up with a remediation to the WEP weaknesses called Temporal Key Integrity Protocol (TKIP), which is based on the RC4 encryption algorithm.
TKIP affords protections to the authentication process, and it is also used after the authentication process to encrypt the data traffic thereafter. The Wi-Fi Alliance unveiled TKIP back in late 2002 and introduced it as Wi-Fi Protected Access (WPA). TKIP doesn’t require an upgrade to legacy hardware equipment in order to use it. In the summer of 2004, the IEEE put its seal of approval on its final version and added 802.1X and AES-CCMP (AES-Counter Mode CBC-MAC Protocol). Upon publishing IEEE 802.11i-2004, the Wi-Fi Alliance responded positively by embracing the now-complete specification and dubbing it WPA2 for marketing purposes.
A big reason new hardware wasn’t required to run TKIP is that it really just kind of wraps around the preexisting WEP RC4 encryption cipher, which was way too short, and upgrades it to a much more impenetrable 128-bit encryption. Another reason for TKIP’s innate compatibility is that both its encryption mechanism and the RC4 algorithm used to power and define WEP remained the same.
AES
Both WPA/2 and the 802.11i standard call for the use of 128-bit Advanced Encryption Standard (AES) for data encryption. It’s widely considered the best encryption available today and has been approved by the National Institute of Standards and Technology (NIST). It’s also referred to as AES-CCMP, or AES Counter Mode with CBC-MAC authentication.
The only shortcoming of AES is that due to the computational requirements, you need a cryptographic processor to run it. Still, it’s much more efficient and secure than RC4.
WPA or WPA 2 Pre-Shared Key
Although this is another form of basic security that’s really just an add-on to the specifications, WPA or WPA2 Pre-Shared Key (PSK) is a better form of wireless security than any other basic wireless security method mentioned so far.
The PSK verifies users via a password or identifying code (also called a passphrase) on both the client machine and the access point. A client only gains access to the network if its password matches the access point’s password. The PSK also provides keying material that TKIP or AES uses to generate an encryption key for each packet of transmitted data. While more secure than static WEP, PSK still has a lot in common with static WEP in that the PSK is stored on the client station and can be compromised if the client station is lost or stolen—even though finding this key isn’t all that easy to do. To prevent PSK guessing, use a strong PSK passphrase that includes a mixture of letters, numbers, and non-alphanumeric characters.
Wi-Fi Protected Access (WPA) is a standard developed in 2003 by the Wi-Fi Alliance, formerly known as WECA. WPA provides a standard for authentication and encryption of WLANs that’s intended to solve known security problems existing up to and including the year 2003. This takes into account the well-publicized AirSnort and man-in-the-middle WLAN attacks.
WPA is a step toward the IEEE 802.11i standard and uses many of the same components, with the exception of encryption—802.11i (WPA2) uses AES-CCMP encryption. The IEEE 802.11i standard replaced Wired Equivalent Privacy (WEP) with a specific mode of the Advanced Encryption Standard (AES) known as the Counter Mode Cipher Block Chaining-Message Authentication Code (CBC-MAC) protocol (CCMP). This allows AES-CCMP to provide both data confidentiality (encryption) and data integrity.
WPA’s mechanisms are designed to be implementable by current hardware vendors, meaning that users should be able to implement WPA on their systems with only a firmware/software modification.
The IEEE 802.11i standard has been sanctioned by WPA and is termed WPA version 2.
Exam Essentials
Remember the two types of original 802.11 authentication. Two types of authentication were specified by the IEEE 802.11 committee: open and shared-key authentication.
Remember the standard developed by the Wi-Fi Alliance. Wi-Fi Protected Access (WPA) is a standard developed by the Wi-Fi Alliance that addresses the weaknesses inherent in the original 802.11 security model.
Identify Common Issues with Implementing Wireless Networks (Including Interfaces and Misconfigurations)
For information about this objective, see the section titled “Identify the Basic Parameters to Configure on a Wireless Network to Ensure That Devices Connect to the Correct Access Point” earlier in this chapter.
1. What is the frequency range of the IEEE 802.11b standard?
A. 2.4Gbps
B. 5Gbps
C. 2.4GHz
D. 5GHz
2. What is the frequency range of the IEEE 802.11a standard?
A. 2.4Gbps
B. 5Gbps
C. 2.4GHz
D. 5GHz
3. What is the frequency range of the IEEE 802.11g standard?
A. 2.4Gbps
B. 5Gbps
C. 2.4GHz
D. 5GHz
4. What is the encryption used in WPA2?
A. AES-CCMP
B. WEP
C. PSK
D. TKIP
5. How many non-overlapping channels are available with 802.11g?
A. 3
B. 12
C. 23
D. 40
6. How many non-overlapping channels are available with 802.11b?
A. 3
B. 12
C. 23
D. 40
7. After the 802.11h standard, how many non-overlapping channels are available with 802.11a?
A. 3
B. 12
C. 23
D. 40
8. What is the maximum data rate for the 802.11a standard?
A. 6Mbps
B. 11Mbps
C. 22Mbps
D. 54Mbps
9. What is the maximum data rate for the 802.11g standard?
A. 6Mbps
B. 11Mbps
C. 22Mbps
D. 54Mbps
10. What is the maximum data rate for the 802.11b standard?
A. 6Mbps
B. 11Mbps
C. 22Mbps
D. 54Mbps
1. C. The IEEE 802.11b and IEEE 802.11g both run in the 2.4GHz RF range.
2. D. The IEEE 802.11a standard runs in the 5GHz RF range.
3. C. The IEEE 802.11b and IEEE 802.11g both run in the 2.4GHz RF range.
4. A. WPA2 uses the Advanced Encryption Standard (AES) known as the Counter Mode Cipher Block Chaining-Message Authentication Code (CBC-MAC) protocol (CCMP).
5. A. The IEEE 802.11g standard provides three non-overlapping channels.
6. A. The IEEE 802.11b standard provides three non-overlapping channels.
7. C. With the 802.11h standard, the IEEE 802.11a standard provides up to 23 non-overlapping channels.
8. D. The IEEE 802.11a standard provides a maximum data rate of up to 54Mbps.
9. D. The IEEE 802.11g standard provides a maximum data rate of up to 54Mbps.
10. B. The IEEE 802.11b standard provides a maximum data rate of up to 11Mbps.
