Chapter 2
IEEE 802.11 Standard and Amendments
IN THIS CHAPTER, YOU WILL LEARN ABOUT THE FOLLOWING: The 802.11 working group has about 400 active members from more than 200 wireless companies. It consists of standing committees, study groups, and numerous task groups. For example, the Standing Committee—Publicity (PSC) is in charge of finding means to better publicize the 802.11 standard. An 802.11 Study Group (SG) is authorized by the executive committee (EC) and is expected to have a short lifespan, typically less than six months. A study group is in charge of investigating the possibility of putting new features and capabilities into the 802.11 standard. Various 802.11 task groups are in charge of revising and amending the original standard that was developed by the MAC task group (MAC) and the PHY task group (PHY). Each group is assigned a letter from the alphabet, and it is common to hear the term 802.11 alphabet soup when referring to all the amendments created by the multiple 802.11 task groups. When task groups are formed, they are assigned the next highest available letter in the alphabet, although the amendments may not necessarily be ratified in the same order. Quite a few of the 802.11 task group projects have been completed, and amendments to the original standard have been ratified. Other 802.11 task group projects still remain active and exist as draft amendments. In this chapter, we discuss the original 802.11 standard, the ratified amendments (many of which were incorporated into the 802.11-2007 standard, the 802.11-2012 standard, and the current 802.11-2016 standard), and the draft amendments of various 802.11 task groups. The original 802.11 standard was published in June 1997 as IEEE Std 802.11-1997, and it is often referred to as 802.11 Prime because it was the first WLAN standard. The standard was revised in 1999, reaffirmed in 2003, and published as IEEE Std 802.11-1999 (R2003). On March 8, 2007, another iteration of the standard was approved, IEEE Std 802.11-2007, and on March 29, 2012, the IEEE Std 802.11-2012 standard was approved. The most recent revision of the standard, IEEE 802.11-2016, was approved on December 7, 2016. The IEEE specifically defines 802.11 technologies at the Physical layer and the MAC sublayer of the Data-Link layer. By design, the 802.11 standard does not address the upper layers of the OSI model, although there are interactions between the 802.11 MAC layer and the upper layers for parameters such as quality of service (QoS). The PHY task group worked in conjunction with the MAC task group to define the original 802.11 standard. The PHY task group defined three original Physical layer specifications: Infrared Infrared (IR) technology uses a light-based medium. Although an infrared medium was indeed defined in the original 802.11 standard, it has since been deprecated and removed from the 802.11-2016 standard. Frequency-Hopping Spread-Spectrum Radio frequency signals can be defined as narrowband signals or as spread-spectrum signals. An RF signal is considered spread-spectrum when the bandwidth is wider than what is required to carry the data. Frequency-hopping spread-spectrum (FHSS) is a spread-spectrum technology that was first patented during World War II. Frequency-hopping 802.11 has been deprecated and removed from the 802.11-2016 standard. Direct-Sequence Spread-Spectrum Direct-sequence spread-spectrum (DSSS) is another spread-spectrum technology that uses fixed channels. DSSS 802.11 radios are known as Clause 15 devices. As defined by 802.11 Prime, the original frequency space in which 802.11 radios were allowed to transmit was the license-free 2.4 GHz industrial, scientific, and medical (ISM) band. DSSS 802.11 radios could transmit within channels subdivided from the entire 2.4 GHz to 2.4835 GHz ISM band. The IEEE was more restrictive for FHSS radios, which were permitted to transmit on 1 MHz subcarriers in the 2.402 GHz to 2.480 GHz range of the 2.4 GHz ISM band. You will probably never work with any of the legacy radios defined in 802.11 Prime, because the technology is over 20 years old and has been replaced in working WLAN environments. Originally, WLAN vendors had the choice of manufacturing either FHSS radios or DSSS radios. The majority of legacy WLAN deployments used frequency hopping, but some DSSS solutions were available as well. It should also be noted that any references to FHSS radios has been decremented from the current 802.11-2016 standard. What about the speeds? Data rates defined by the original 802.11 standard were 1 Mbps and 2 Mbps, regardless of which spread-spectrum technology was used. A data rate is the number of bits per second the Physical layer carries during a transmission, normally stated as a number of millions of bits per second (Mbps). Keep in mind that data rate is the speed, not actual throughput. Because of medium access methods and communications overhead, aggregate throughput is typically around half of the available data rate speed. In the years that followed the publishing of the original 802.11 standard, new task groups were assembled to address potential enhancements to the standard. As of this writing, almost 30 amendments have been ratified and published by the distinctive task groups. In 2007, the IEEE consolidated 8 ratified amendments along with the original standard, creating a single document that was published as IEEE Std 802.11-2007. This revision also included corrections, clarifications, and enhancements. In 2012, the IEEE consolidated 10 ratified amendments into the IEEE Std 802.11-2007 standard, creating a single document that was published as IEEE Std 802.11-2012. In addition to consolidating the ratified amendments and making corrections, clarifications, and enhancements to the document, the IEEE reviewed all of the clauses and annexes chronologically. Some of the clauses and annexes were rearranged and renumbered so that they were listed in the order that they were ratified. Most recently, in 2016, the IEEE consolidated 5 ratified amendments into the IEEE Std 802.11-2012 standard, creating the most recent iteration of the standard, IEEE Std 802.11-2016. In addition to consolidating the ratified amendments and making corrections, some obsolete clauses were removed from the document and some clauses were renumbered. During the same year that the 802.11b amendment was approved, another important amendment was also ratified and published as IEEE Std 802.11a-1999. The engineers in the Task Group a (TGa) set out to define how 802.11 technologies would operate in the 5 GHz frequency space using an RF technology called orthogonal frequency-division multiplexing (OFDM). 802.11a radios could transmit in three different 100 MHz unlicensed frequency bands in the 5 GHz range. These three bands are called the Unlicensed National Information Infrastructure (U-NII) frequency bands. A total of 12 channels were available in the original three U-NII bands. All aspects of the 802.11a ratified amendment can now be found in Clause 17 of the 802.11-2016 standard. The 2.4 GHz ISM band is a much more crowded frequency space than the 5 GHz U-NII bands. Bluetooth devices, microwave ovens, cordless phones, and numerous other devices all operate in the 2.4 GHz ISM band and are potential sources of interference. In addition, the sheer number of 2.4 GHz WLAN deployments is a problem, especially in environments such as multitenant office buildings. A big advantage of using 5 GHz WLAN equipment is that the U-NII bands are less crowded. As time passed, the three original U-NII bands also started to become crowded. Regulatory bodies such as the FCC opened up more frequency space in the 5 GHz range, and the IEEE addressed this in the 802.11h amendment. The FCC has also proposed even more 5 GHz spectrum be made available in the near future. Greater detail about all of the 5 GHz U-NII bands can be found in Chapter 6 “Wireless Networks and Spread Spectrum Technologies.” Legacy 802.11a radios initially could transmit in the 12 channels of the U-NII-1, U-NII-2, and U-NII-3 bands; however, the 5 GHz frequency range and channels used by 802.11a radios are dependent on the RF regulatory body of individual countries. The amendment was mostly about the introduction of OFDM technology that provided better higher rates. 802.11a radios operating in the 5 GHz U-NII bands are classified as Clause 17 devices. As defined by the 802.11a amendment, these devices are required to support data rates of 6, 12, and 24 Mbps, with a maximum of 54 Mbps. With the use of a technology called orthogonal frequency-division multiplexing (OFDM), data rates of 6, 9, 12, 18, 24, 36, 48, and 54 Mbps are supported. OFDM is also discussed in Chapter 6. It should be noted that 802.11a radios cannot communicate with 802.11 legacy, 802.11b, or 802.11g radios for two reasons. First, 802.11a radios use a different RF technology than 802.11 legacy or 802.11b devices. Second, 802.11a devices transmit in the 5 GHz U-NII bands, whereas the 802.11/802.11b/802.11g devices operate in the 2.4 GHz ISM band. The good news is that 802.11a can coexist in the same physical space with 802.11, 802.11b, or 802.11g devices because these devices transmit in separate frequency ranges. When 802.11a was first ratified, it took almost two years before devices were readily available. When 802.11a devices did become available, the radio chipsets using OFDM were quite expensive. Because of these two factors, widespread deployment of 5 GHz WLANs in the enterprise was rare. Eventually the chipsets become affordable, and the use of 5 GHz frequency bands has grown considerably over the years. WLAN vendors developed dual-frequency access points (APs) with both 2.4 and 5 GHz radios. Most laptops manufactured since 2007 supported dual-frequency radios. The majority of enterprise wireless deployments run both 2.4 GHz and 5 GHz 802.11 wireless networks simultaneously. Although the Wi-Fi consumer market continued to grow at a tremendous rate, 802.11b-compatible WLAN equipment gave the industry the first needed huge shot in the arm. In 1999, the IEEE Task Group b (TGb) published IEEE Std 802.11b-1999, which was later amended and corrected as IEEE Std 802.11b-1999/Cor1-2001. All aspects of the 802.11b ratified amendment can now be found in Clause 16 of the 802.11-2016 standard. The Physical layer medium that was defined by 802.11b is High-Rate DSSS (HR-DSSS). The frequency space in which 802.11b radio cards can operate is the unlicensed 2.4 GHz to 2.4835 GHz ISM band. The TGb’s main goal was to achieve higher data rates within the 2.4 GHz ISM band. 802.11b radio devices accomplished this feat by using a different spreading/coding technique called complementary code keying (CCK) and modulation methods using the phase properties of the RF signal. 802.11 devices used a spreading technique called the Barker code. The end result is that 802.11b radio devices supported data rates of 1, 2, 5.5, and 11 Mbps. 802.11b systems are backward compatible with the 802.11 DSSS data rates of 1 Mbps and 2 Mbps. The transmission data rates of 5.5 Mbps and 11 Mbps are known as HR-DSSS. Once again, understand that the supported data rates refer to available bandwidth, not aggregate throughput. 802.11b radios were not backward compatible with legacy 802.11 FHSS radios, because the different spread-spectrum technologies cannot communicate with each other. An optional technology called Packet Binary Convolutional coding (PBCC) was removed from the IEEE Std 802.11-2016 standard. The original 802.11 standard was written for compliance with the regulatory domains of the United States, Japan, Canada, and Europe. Regulations in other countries might define different limits on allowed frequencies and transmit power. The 802.11d amendment, which was published as IEEE Std 802.11d-2001, added requirements and definitions necessary to allow 802.11 WLAN equipment to operate in areas not served by the original standard. Country code information is delivered in fields inside two wireless frames called beacons and probe responses. This information is then used by 802.11d-compliant devices to ensure that they are abiding by a particular country’s frequency and power rules. Figure 2.1 shows an AP configured for use in Mongolia and a capture of a beacon frame containing the country code, frequency, and power information. FIGURE 2.1 802.11d settings All aspects of the 802.11d ratified amendment can now be found in the 802.11-2016 standard. The original 802.11 standard did not define adequate quality of service (QoS) procedures for the use of time-sensitive applications such as Voice over Wi-Fi. Voice over Wi-Fi is also known as Voice over Wireless LAN (VoWLAN). The terminology used by most vendors and the CWNP program is Voice over Wi-Fi (VoWiFi). Application traffic such as voice, audio, and video has a lower tolerance for latency and jitter and requires priority before standard application data traffic. The 802.11e amendment defines the layer 2 MAC methods needed to meet the QoS requirements for time-sensitive applications over IEEE 802.11 WLANs. The original 802.11 standard defined two methods in which an 802.11 radio card may gain control of the half-duplex medium. The default method, Distributed Coordination Function (DCF), is a contention-based method determining who gets to transmit on the wireless medium next. The original standard also defined another medium access control method, called Point Coordination Function (PCF), where the access point briefly takes control of the medium and polls the clients. It should be noted that the PCF medium access method was never adopted by WLAN vendors and is considered obsolete. The 802.11e amendment defines enhanced medium access methods to support QoS requirements. Hybrid Coordination Function (HCF) is an additional coordination function that is applied in an 802.11e QoS wireless network. HCF has two access mechanisms to provide QoS. Enhanced Distributed Channel Access (EDCA) is an extension to DCF. The EDCA medium access method provides for the “prioritization of frames” based on upper-layer protocols. Application traffic, such as voice or video, is transmitted in a timely fashion on the 802.11 wireless medium, meeting the necessary latency requirements. Hybrid Coordination Function Controlled Channel Access (HCCA) is an extension of PCF. HCCA gives the access point the ability to provide for “prioritization of stations.” In other words, certain client stations will be given a chance to transmit before others. Much like PCF, the HCCA medium access method defined by 802.11e has never been adopted by WLAN vendors. The Wi-Fi Alliance also has a certification known as Wi-Fi Multimedia (WMM). The WMM certification defines many components of 802.11e and defines traffic prioritization in four access categories with varying degrees of importance. Most aspects of the 802.11e ratified QoS amendment can now be found in Clause 10 of the 802.11-2016 standard. Another amendment that generated a lot of excitement in the Wi-Fi marketplace was published as IEEE Std 802.11g-2003. 802.11g radios used a new technology called Extended Rate Physical (ERP) but were still meant to transmit in the 2.4 GHz to 2.4835 GHz ISM frequency band. All aspects of the 802.11g ratified amendment can now be found in Clause 18 of the 802.11-2016 standard. The main goal of the Task Group g (TGg) was to enhance the 802.11b Physical layer to achieve greater bandwidth yet remain compatible with the 802.11 MAC sublayer. Two mandatory and two optional ERP Physical layers (PHYs) were defined by the 802.11g amendment. The mandatory PHYs are ERP-OFDM and ERP-DSSS/CCK. To achieve the higher data rates, a PHY technology called Extended Rate Physical OFDM (ERP-OFDM) was mandated. Data rates of 6, 9, 12, 18, 24, 36, 48, and 54 Mbps are possible using this technology, although once again the IEEE required only the data rates of 6, 12, and 24 Mbps. To maintain backward compatibility with 802.11 (DSSS only) and 802.11b networks, a PHY technology called Extended Rate Physical DSSS (ERP-DSSS/CCK) was used with support for the data rates of 1, 2, 5.5, and 11 Mbps. The 802.11g ratified amendment also defined two optional PHYs called ERP-PBCC and DSSS-OFDM. Both of these were removed from the latest standard, IEEE Std 802.11-2016. The ratification of the 802.11g amendment triggered monumental sales of Wi-Fi gear in the small office, home office (SOHO), and enterprise markets because of both the higher data rates and the backward compatibility with older equipment. As mentioned earlier in this chapter, different spread-spectrum technologies cannot communicate with each other, yet the 802.11g amendment mandated support for both ERP-DSSS/CCK and ERP-OFDM. In other words, ERP-OFDM and ERP-DSSS/CCK technologies can coexist, yet they cannot speak to each other. Therefore, the 802.11g amendment called for a protection mechanism that allows the two technologies to coexist. The goal of the ERP protection mechanism was to prevent older 802.11b HR-DSSS or 802.11 DSSS radio cards from transmitting at the same time as 802.11g (ERP) radios. Table 2.1 shows a brief overview and comparison of 802.11, 802.11b, 802.11g, and 802.11a. TABLE 2.1 Original 802.11 amendments comparison ERP: ERP-OFDM and ERP-DSSS/CCK are mandatory. DSSS: 1, 2 Mbps HR-DSSS: 5.5 and 11 Mbps Published as IEEE Std 802.11h-2003, this amendment defined mechanisms for dynamic frequency selection (DFS) and transmit power control (TPC). It was originally proposed to satisfy regulatory requirements for operation in the 5 GHz band in Europe and to detect and avoid interference with 5 GHz satellite and radar systems. These same regulatory requirements have also been adopted by the FCC in the United States. The main purpose of DFS and TPC is to provide services where 5 GHz 802.11 radio transmissions will not cause interference with 5 GHz satellite and radar transmissions. The 802.11h amendment also introduced the capability for 802.11 radios to transmit in a new frequency band, called U-NII-2 Extended, with 11 more channels in some regulatory domains. The 802.11h amendment effectively is an extension of the 802.11a amendment. OFDM transmission technology is used in all of the U-NII bands. The radar detection and avoidance technologies of DFS and TPC are defined by the IEEE. However, the RF regulatory organizations in each country still define the RF regulations. In the United States and Europe, radar detection and avoidance is required in both the U-NII-2 and U-NII-2 Extended bands. DFS is used for spectrum management of 5 GHz channels by OFDM radio devices. The European Radiocommunications Committee (ERC) and the FCC mandate that radio cards operating in the 5 GHz band implement a mechanism to avoid interference with radar systems. DFS is essentially radar-detection and radar-interference avoidance technology. The DFS service is used to meet these regulatory requirements. The dynamic frequency selection (DFS) service provides for the following: TPC is used to regulate the power levels used by OFDM radio cards in the 5 GHz frequency bands. The ERC mandates that radio cards operating in the 5 GHz band use TPC to abide by a maximum regulatory transmit power and are able to alleviate transmission power to avoid interference. The TPC service is used to meet the regulatory transmission power requirements. The transmit power control (TPC) service provides for the following: The information used by both DFS and TPC is exchanged between client stations and APs inside of management frames. The 802.11h amendment effectively introduced two major enhancements: more frequency space, with the introduction of the U-NII-2 Extended band, and radar avoidance and detection technologies. Some aspects of the 802.11h ratified amendment can now be found in Clause 11.8 and Clause 11.9 of the 802.11-2016 standard. It should be noted that DFS technology is most often used for radar avoidance as opposed to TPC. Careful consideration should be given when planning a 5 GHz WLAN with DFS channels enabled. A deeper discussion of DFS operations can be found in Chapter 13, “WLAN Design Concepts.” From 1997 to 2004, not much was defined in terms of security in the original 802.11 standard. Three key components of any wireless security solution are data privacy (encryption), data integrity (protection from modification), and authentication (identity verification). For seven years, the only defined method of encryption in an 802.11 network was the use of 64-bit static encryption called Wired Equivalent Privacy (WEP). WEP encryption has long been cracked and is not considered an acceptable means of providing data privacy. The original 802.11 standard defined two methods of authentication. The default method is Open System authentication, which effectively allows access to all users regardless of identity. Another defined method is called Shared Key authentication, which opens up a whole new can of worms and potential security risks. The 802.11i amendment, which was ratified and published as IEEE Std 802.11i-2004, defined stronger encryption and better authentication methods. The 802.11i amendment defined a robust security network (RSN). The intended goal of an RSN was to better hide the data flying through the air while at the same time placing a bigger guard at the front door. The 802.11i security amendment is without a doubt one of the most important enhancements to the original 802.11 standard because of the seriousness of properly protecting a wireless network. The major security enhancements addressed in 802.11i are as follows: Data Privacy Confidentiality needs have been addressed in 802.11i with the use of a stronger encryption method called Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP), which uses the Advanced Encryption Standard (AES) algorithm. The encryption method is often abbreviated as CCMP/AES, AES CCMP, or often just CCMP. The 802.11i amendment also defined an optional encryption method known as Temporal Key Integrity Protocol (TKIP), which uses the ARC4 stream cipher algorithm and is basically an enhancement of WEP encryption. Data Integrity All of the WLAN encryption methods defined by the IEEE employ data-integrity mechanisms to ensure that the encrypted data has not been modified. WEP uses a data-integrity method called the integrity check value (ICV). TKIP uses a method known as the message integrity check (MIC). CCMP uses a much stronger MIC as well as other mechanisms for data integrity. Finally, in the trailer of all 802.11 frames is a 32-bit CRC known as the frame check sequence (FCS) that protects the entire body of the 802.11 frame. Authentication 802.11i defines two methods of authentication using either an IEEE 802.1X authorization framework or preshared keys (PSKs). An 802.1X solution requires the use of an Extensible Authentication Protocol (EAP), although the 802.11i amendment does not specify which EAP method to use. Robust Security Network A robust security network (RSN) defines the entire method of establishing authentication, negotiating security associations, and dynamically generating encryption keys for client stations and access points. The Wi-Fi Alliance also has a certification known as Wi-Fi Protected Access 2 (WPA2), which is a mirror of the IEEE 802.11i security amendment. WPA version 1 was considered a preview of 802.11i, whereas WPA version 2 is fully compliant with 802.11i. All aspects of the 802.11i ratified security amendment can now be found in Clause 12 of the 802.11-2016 standard. The main goal set out by the IEEE Task Group j (TGj) was to obtain Japanese regulatory approval by enhancing the 802.11 MAC and 802.11a PHY to additionally operate in Japanese 4.9 GHz and 5 GHz bands. Not all WLAN vendors support this band. The 802.11j amendment was approved and published as IEEE Std 802.11j-2004. In Japan, 802.11a radio cards could transmit in the lower U-NII band at 5.15 GHz to 5.25 GHz as well as a Japanese licensed/unlicensed frequency space of 4.9 GHz to 5.091 GHz. 802.11a radio cards use OFDM technology and are required to support channel spacing of 20 MHz. When 20 MHz channel spacing is used, data rates of 6, 9, 12, 18, 24, 36, 48, and 54 Mbps are possible using OFDM technology. Japan also has the option of using OFDM channel spacing of 10 MHz, which results in available bandwidth data rates of 3, 4.5, 6, 9, 12, 18, 24, and 27 Mbps. The data rates of 3, 6, and 12 Mbps are mandatory when using 10 MHz channel spacing. The goal of the 802.11 Task Group k (TGk) was to provide a means of radio resource measurement (RRM). The 802.11k-2008 amendment called for measurable client statistical information in the form of requests and reports for the Physical layer 1 and the MAC sublayer of the Data-Link layer 2. 802.11k defined mechanisms in which client station resource data is gathered and processed by an access point or WLAN controller. (WLAN controllers are covered in Chapter 11, “WLAN Architecture.” For now, think of a WLAN controller as a core device that manages many access points.) In some instances, the client may also request information from an access point or WLAN controller. The following are some of the key radio resource measurements defined under 802.11k: Transmit Power Control The 802.11h amendment defined the use of transmit power control (TPC) for the 5 GHz band to reduce interference. Under 802.11k, TPC will also be used in other frequency bands and in areas governed by other regulatory agencies. Client Statistics Physical layer information, such as signal-to-noise ratio, signal strength, and data rates, can all be reported back to the access point or WLAN controller. MAC information, such as frame transmissions, retries, and errors, may all be reported back to the access point or WLAN controller as well. Channel Statistics Clients may gather noise-floor information based on any RF energy in the background of the channel and report this information back to the access point. Channel-load information may also be collected and sent to the AP. The access point or WLAN controller may use this information for channel management decisions. Neighbor Reports 802.11k gave client stations the ability to learn from access points or WLAN controllers about other access points where the client stations might potentially roam. AP neighbor report information is shared among WLAN devices to improve roaming efficiency. Using proprietary methods, a client station keeps a table of known access points and makes decisions on when to roam to another access point. Most client stations make a roaming decision based on the received amplitude of known access points. In other words, a client station decides to roam based on its individual perspective of the RF environment. 802.11k mechanisms provide a client station with additional information about the existing RF environment. As defined by 802.11k, a client station will request information about neighbor access points on other channels from an access point or WLAN controller. The current AP or WLAN controller will then process that information and generate a neighbor report detailing available access points from best to worst. Before a station roams, it will request the neighbor report from the current AP or controller and then decide whether to roam to one of the access points on the neighbor report. Neighbor reports effectively give a client station more information about the RF environment from other existing radios. With the additional information, a client station should make a more informed roaming decision. An event that had a major impact on the Wi-Fi marketplace was the ratification of the 802.11n-2009 amendment. Since 2004, the 802.11 Task Group n (TGn) worked on improvements to the 802.11 standard to provide for greater throughput. Some of the IEEE 802.11 amendments in the past have addressed bandwidth data rates in the 2.4 GHz frequency band. However, the specific objective of the 802.11n-2009 amendment was to increase the throughput in both the 2.4 GHz and 5 GHz frequency bands. The 802.11n-2009 amendment defined a new operation known as high throughput (HT), which provides PHY and MAC enhancements to support data rates of up to 600 Mbps and therefore aggregate throughput above 100 Mbps. HT Clause 19 radios use multiple-input, multiple-output (MIMO) technology in unison with OFDM technology. MIMO uses multiple receiving and transmitting antennas and actually capitalizes on the effects of multipath, as opposed to compensating for or eliminating them. The beneficial consequences of using MIMO are increased throughput and even greater range. 802.11n radios are also backward compatible with legacy 802.11a/b/g radios. The mission of the 802.11 Task Group p (TGp) was to define enhancements to the 802.11 standard to support Intelligent Transportation System (ITS) applications. Data exchanges between high-speed vehicles are possible in the licensed ITS band of 5.9 GHz. Additionally, communications between vehicles and roadside infrastructure are supported in the 5 GHz bands, specifically the 5.850 GHz–5.925 GHz band within North America. Communications may be possible at speeds of up to 200 kilometers per hour (124 mph) and within a range of 1,000 meters (3,281 feet). Very short latencies will also be needed, as some applications must guarantee data delivery within 4 to 50 milliseconds. 802.11p is also known as Wireless Access in Vehicular Environments (WAVE) and is a possible foundation for a US Department of Transportation project called Dedicated Short Range Communications (DSRC). The DSRC project envisions a nationwide vehicle and roadside communication network utilizing applications such as vehicle safety services, traffic jam alerts, toll collections, vehicle collision avoidance, and adaptive traffic light control. In Europe, the ETSI Intelligent Transport System (ITS) is based on IEEE 802.11 and 802.11p technology. This standard is designed to provide vehicle to vehicle and vehicle to infrastructure communication. 802.11p will also be applicable to marine and rail communications. The 802.11r-2008 amendment is known as the fast basic service set transition (FT) amendment. The technology is more often referred to as fast-secure roaming because it defines faster handoffs when roaming occurs between cells in a WLAN using the strong security defined by a robust secure network (RSN). Be aware that there are multiple types of fast-secure roaming that are implemented by different vendors. These include CCKM, PKC, OKC, and fast session resumption. Some vendors support 802.11r, while others do not. 802.11r was proposed primarily because of the time constraints of applications such as VoWiFi. Average time delays of hundreds of milliseconds occur when a client station roams from one access point to another access point. Roaming can be especially troublesome when using a WPA-Enterprise or WPA2-Enterprise security solution, which requires the use of a RADIUS server for 802.1X/EAP authentication and often takes 700 milliseconds or greater for the client to authenticate. VoWiFi requires a handoff of 100 milliseconds or less to avoid a degradation of the quality of the call or, even worse, a loss of connection. Under 802.11r, a client station is able to establish a QoS stream and set up a security association with a new access point in an efficient manner that allows bypassing 802.1X/EAP authentication when roaming to a new access point. The client station is able to achieve these tasks either over the wire via the original access point or through the air. Eventually, the client station will complete the roaming process and move to the new access point. Tactical enterprise deployments of this technology are extremely important for providing more secure communications for VoWiFi. The details of this technology are heavily tested on the CWSP exam. The 802.11s-2011 amendment was ratified in July 2011. 802.11 access points typically act as portal devices to a distribution system (DS) that is usually a wired 802.3 Ethernet medium. The 802.11-2016 standard, however, does not mandate that the distribution system use a wired medium. Access points can therefore act as portal devices to a wireless distribution system (WDS). The 802.11s amendment proposes the use of a protocol for adaptive, autoconfiguring systems that support broadcast, multicast, and unicast traffic over a multihop mesh WDS. The 802.11 Task Group s (TGs) set forth the pursuit of standardizing mesh networking using the IEEE 802.11 MAC/PHY layers. The 802.11s amendment defined the use of mesh points (MPs), which are 802.11 QoS stations that support mesh services. A mesh point is capable of using a mandatory mesh routing protocol called Hybrid Wireless Mesh Protocol (HWMP) that uses a default path selection metric. Vendors may also use proprietary mesh routing protocols and metrics. As depicted in Figure 2.2, a mesh access point (MAP) is a device that provides both mesh functionalities and AP functionalities simultaneously. A mesh point portal (MPP) is a device that acts as a gateway to one or more external networks, such as an 802.3 wired backbone. FIGURE 2.2 Mesh points, mesh APs, and mesh portal The primary objective of the 802.11 Task Group u (TGu) was to address interworking issues between an IEEE 802.11 access network and any external network to which it is connected. A common approach is needed to integrate IEEE 802.11 access networks with external networks in a generic and standardized manner. 802.11u is also often referred to as Wireless Interworking with External Networks (WIEN). The 802.11u-2011 amendment, ratified in February 2011, defined functions and procedures for aiding network discovery and selection by STAs, information transfer from external networks using QoS mapping, and a general mechanism for the provision of emergency services. The 802.11u-2011 amendment is the basis for the Wi-Fi Alliance’s Hotspot 2.0 specification and its Passpoint certification. This standard and certification is designed to provide seamless roaming for wireless devices between your Wi-Fi network and other partner networks, similar to how cellular telephone networks provide roaming. Passpoint and Hotspot 2.0 are discussed in great detail in Chapter 18, “Bring Your Own Device (BYOD) and Guest Access.” The 802.11v-2011 amendment was ratified in February 2011. While 802.11k defines methods of retrieving information from client stations, 802.11v provides for an exchange of information that can potentially ease the configuration of client stations wirelessly from a central point of management. 802.11v-2011 defines wireless network management (WNM), which gives 802.11 stations the ability to exchange information for the purpose of improving the overall performance of the wireless network. Access points and client stations use WNM protocols to exchange operational data so that each station is aware of the network conditions, allowing stations to be more cognizant of the topology and state of the network. In addition to providing information on network conditions, WNM protocols define mechanisms in which WLAN devices can exchange location information, provide support for the multiple BSSID capability, and offer a new WNM-Sleep mode, in which a client station can sleep for long periods of time without receiving frames from the AP. Some of the 802.11v mechanisms are defined by the Wi-Fi Alliance as optional mechanisms in the Voice-Enterprise certification. A common type of attack on an 802.11 WLAN is a denial-of-service (DoS) attack. There are a multitude of DoS attacks that can be launched against a wireless network; however, a very common DoS attack occurs at layer 2 using 802.11 management frames. Currently, it is simple for an attacker to edit deauthentication or disassociation frames and then retransmit the frames into the air, effectively shutting down the wireless network. The goal of the IEEE Task Group w (TGw) was to provide a way of delivering management frames in a secure manner, therefore preventing the management frames from being able to be spoofed. The 802.11w-2009 amendment provided protection for unicast, broadcast, and multicast management frames. These 802.11w frames are referred to as robust management frames. Robust management frames can be protected by the management frame protection service and include disassociation, deauthentication, and robust action frames. Action frames are used to request a station to take action on behalf of another station, and not all action frames are robust. When unicast management frames are protected, frame protection is achieved by using CCMP. Broadcast and multicast frames are protected using the Broadcast/Multicast Integrity Protocol (BIP). BIP provides data integrity and replay protection using AES-128 in Cipher-Based Message Authentication Code (CMAC) mode. It should be noted that the 802.11w amendment will not put an end to all layer 2 DoS attacks. Although 802.11 devices mostly operate in unlicensed frequencies, they can also operate on frequencies that are licensed by national regulatory bodies. The objective of the IEEE Task Group y (TGy) was to standardize the mechanisms required to allow high-powered, shared 802.11 operations with other non-802.11 devices in the 3650 MHz–3700 MHz licensed band in the United States. It should be noted that the mechanisms defined by the 802.11y-2008 amendment can be used in other countries and in other licensed frequencies. The licensed 3650 MHz to 3700 MHz band requires content-based protocol (CBP) mechanisms to avoid interference between devices. The medium contention method, CSMA/CA (which is used by Wi-Fi radios), can normally accommodate this requirement. However, when standard CSMA/CA methods are not sufficient, the 802.11y-2008 amendment defines dynamic STA enablement (DSE) procedures. 802.11 radios broadcast their actual location as a unique identifier in order to help resolve interference with non-802.11 radios in the same frequency. The purpose of IEEE Task Group z (TGz) was to establish and standardize a direct link setup (DLS) mechanism to allow operation with non-DLS-capable access points. In most WLAN environments, all frame exchanges between client stations that are associated to the same access point must pass through the access point. DLS allows client stations to bypass the access point and communicate with direct frame exchanges. Some of the earlier amendments have defined DLS communications. The 802.11z-2010 amendment defined enhancements to DLS communications. It should be noted that DLS communications have yet to be used by enterprise WLAN vendors. The 802.11aa amendment specifies QoS enhancements to the 802.11 Media Access Control (MAC) for robust audio and video streaming for both consumer and enterprise applications. 802.11aa provides improved management, increased link reliability, and increased application performance. The amendment defines Groupcast with Retries (GCR), a flexible service to improve the delivery of group addressed frames. GCR can be provided in an infrastructure BSS by the AP to its associated STAs or in a mesh BSS by a mesh STA and its peer mesh STAs. The 802.11ac-2013 amendment defines very high throughput (VHT) enhancements below 6 GHz. The technology is used only in the 5 GHz frequency bands where 802.11a/n radios already operate. 802.11ac takes advantage of the greater spectrum space that the 5 GHz U-NII bands can provide. The 2.4 GHz ISM band cannot provide the needed frequency space that would be able to take full advantage of 802.11ac technology. To take full advantage of 802.11ac, even more spectrum would be preferred in 5 GHz. The 802.11ac amendment defines a maximum data rate of 6933.3 Mbps. 802.11ac provides gigabit speeds using the following four major enhancements: Wider Channels 802.11n introduced the capability of 40 MHz channels, which effectively doubled the data rates. 802.11ac supports channel widths of 20 MHz, 40 MHz, 80 MHz, and 160 MHz channels. This is the main reason that enterprise 802.11ac radios would not be able to operate in the 2.4 GHz ISM band. New Modulation 802.11ac provides the capability to use 256-QAM modulation, which can provide at least a 30 percent increase in speed over previous modulation methods. 256-QAM modulation requires a very high signal-to-noise (SNR) ratio to be effective. More Spatial Streams According to the standard, 802.11ac radios could be built to transmit and receive up to eight spatial streams. In reality, the first couple of generations of 802.11ac chipsets only support up to four spatial streams. Improved MIMO and Beamforming While 802.11n defined the use of single-user MIMO radios, very high throughput (VHT) introduces the use of multi-user MIMO (MU-MIMO) technology. An access point with MU-MIMO capability could transmit a signal to multiple client stations on the same channel simultaneously, if the client stations support MU-MIMO and are in different physical areas. 802.11ac can utilize explicit beamforming. The 802.11ad amendment defines performance enhancements using the much higher unlicensed frequency band of 60 GHz and a transmission method known as directional multi-gigabit (DMG). The higher frequency range is big enough to support data rates of up to 7 Gbps. The downside is that 60 GHz will have significantly less effective range than a 5 GHz signal and be limited to line-of-sight communications, as the high frequency signal will have difficulty penetrating walls. The 60 GHz Wi-Fi technology has the potential to be used for wireless docking, wireless displays, wired equivalent data transfers, and streaming of uncompressed video. To provide seamless transition when roaming between the 60 GHz frequency band and legacy 2.4 GHz or 5 GHz bands, a “fast session transfer” feature was added to the specification. The DMG technology also required the adoption of a new encryption mechanism. There was concern that the current CCMP encryption methods may not be able to properly process the higher anticipated data rates. CCMP uses two chained-together AES cryptographic modes to process 128-bit blocks of data. The 128-bit blocks of data must also be processed “in order” from the first AES cryptographic mode to the second mode. The 802.11ad amendment specifies the use of the Galois/Counter Mode Protocol (GCMP), which also uses AES cryptography. However, GCMP calculations can be run in parallel and are computationally less intensive than the cryptographic operations of CCMP. The 802.11ae amendment specifies enhancements to QoS management. A quality-of-service management frame (QMF) service can be enabled, allowing some of the management frames to be transmitted using a QoS access category that is different from the access category assigned to voice traffic. This can improve the quality of service of other traffic streams. The 802.11af amendment allows the use of wireless in the TV white space (TVWS) frequencies between 54 MHz and 790 MHz. This technology is sometimes referred to as White-Fi or Super Wi-Fi, but we recommend that you shy away from using these terms, as this technology is not affiliated with the Wi-Fi Alliance, which is the trademark holder of the term Wi-Fi. In different regions or TV marketplaces, not all of the available TV channels are used by licensed stations. TVWS is the range of TV frequencies that are not used by any licensed station in a specific area. 802.11af-based radios will have to verify what frequencies are available and make sure that they do not cause interference. To achieve this, the 802.11af AP will first need to determine its location, likely through the use of GPS technology. Then the radio device will need to interact with a geographic database to determine the available channels for that given time and location. The Physical layer is based on the OFDM technology used in 802.11ac, using smaller channel widths than 802.11ac along with a maximum of four spatial streams. This new PHY is known as television very high throughput (TVHT), and is designed to support the narrow TV channels that are made available by TVWS. The low-bandwidth frequencies that are used mean lower data rates than 802.11a/b/g/n/ac technology. Maximum transmission speed is 26.7 Mbps or 35.6 Mbps, depending on the width of the channel, which is determined by the regulatory domain. Channel width is between 6 MHz and 8 MHz, and up to 4 channels can be bonded together. 802.11af radios can also support up to 4 spatial streams. Using 4 channels and 4 spatial streams, 802.11af has a maximum data rate of about 426 Mbps or 568 Mbps, depending on the regulatory domain. Although the lower TVWS frequencies mean lower data rates, the lower frequencies will provide longer-distance transmissions, along with better penetration through obstructions such as foliage and buildings. This greater distance could result in coverage that is more pervasive, providing contiguous roaming in outdoor office parks, campuses, or public community networks. Another anticipated use is to provide broadband Internet services to rural areas. It is important to note that the IEEE 802.22-2011 standard, along with at least one other standard that is in development, also specifies wireless communications using the TV white space frequencies. This may cause coexistence problems in the future between these competing technologies. Also, the existence of multiple technologies in the same frequency space may splinter product development and acceptance. Since the 802.11-2016 document was published, other amendments have been ratified to define further enhancements to 802.11 technology. These amendments include 802.11ah and 802.11ai, as discussed in the following sections. The 802.11ah amendment defines the use of Wi-Fi in frequencies below 1 GHz. The Wi-Fi HaLow certification from the Wi-Fi Alliance is based on mechanisms defined in the IEEE 802.11ah amendment. The lower frequencies will mean lower data rates but longer distances. A likely use for 802.11h will be sensor networks along with backhaul for sensor networks and with extended range Wi-Fi, such as smart homes, automobiles, healthcare, industrial, retail, and agriculture. This internetworking of devices is known as Internet-of-Things (IoT) or machine-to-machine (M2M) communications. The available frequencies will vary between countries. For example, the 902–928 MHz unlicensed ISM frequencies are available in the United States, whereas the 863–868 MHz frequencies would likely be available in Europe, and the 755–787 frequencies would likely be available in China. The goal of the 802.11ai amendment is to provide a fast initial link setup (FILS). It is designed to address the challenges that exist in high-density environments where large numbers of mobile users are continually joining and disconnecting from an extended service set. The amendment is designed to improve user connectivity in high-density environments, such as airports, sports stadiums, arenas, and shopping malls. FILS is especially important for ensuring that robust security network association (RSNA) links are not degraded as clients roam. What does the future hold in store for us with 802.11 wireless networking? The draft amendments are a looking glass into the enhancements and capabilities that might be available in the near future for 802.11 wireless networking devices. Even greater throughput as well as operations on higher and lower frequencies await us on the wireless horizon. It is important to remember that draft amendments are proposals that have yet to be ratified. Although some vendors may already be selling products that have some of the capabilities described in the following sections, these features are still considered proprietary. Even though a vendor might be marketing these pre-ratified capabilities, there is no guarantee that their current product will work with future products that are certified as compliant with the forthcoming ratified amendment. The remaining pages of this chapter provide a glimpse into the future of more advanced and sophisticated Wi-Fi products that could bring this technology to even greater heights. The 802.11aj draft amendment is to provide modifications to the IEEE 802.11ad-2012 amendment’s PHY and MAC layer to provide support for operating in the Chinese Milli-Meter Wave (CMMW) frequency bands. The CMMW frequency bands are 59–64 GHz. The amendment will also provide modifications to the IEEE 802.11ad-2012 amendment’s PHY and MAC layer to provide support for operating in the Chinese 45 GHz frequency band. The 802.11ak draft amendment is also referred to as General Link (GLK). The task group is exploring enhancement to 802.11 links for use in bridged networks. These bridged networks will be evaluated as potential support for home entertainment systems, industrial control devices, and other products that have both 802.11 wireless and 802.3 wired capabilities. GLK aims to simplify the use of 802.11 between access points and wireless stations, allowing the stations to provide bridging services. The 802.11aq pre-association service discovery task group is working to develop an 802.11 amendment that enables delivery of network service information prior to the association of stations on an 802.11 network. This amendment hopes to be able to allow advertisement of services to stations prior to the stations’ actual association to the network. The 802.11ax draft amendment, also known as the high efficiency (HE) WLAN amendment, is expected to be the next big PHY enhancement to the 802.11 standard. 802.11ax will operate in both the 2.4 GHz and 5 GHz bands. In addition to increasing client throughput, it is also being designed to provide support for more users and higher density environments. Chapter 19, “802.11ax-High Efficiency (HE),” is dedicated to 802.11ax. Although earlier amendments defined methods to achieve higher data rates, 802.11ax uses PHY and MAC layer enhancements for better traffic management of the existing WLAN medium. A key component of 802.11ax is orthogonal frequency-division multiple access (OFDMA) technology. OFDMA is a multi-user version of the popular orthogonal frequency-division multiplexing (OFDM) digital modulation scheme. Multiple access is achieved in OFDMA by assigning subsets of subcarriers to individual clients. This allows simultaneous low data rate transmission to/from multiple users. The 802.11ay draft amendment is an improvement of the 802.11ad amendment, providing faster speeds and longer range. It is expected to have a maximum data rate of 176 Gbps. 802.11ad uses maximum channel widths of 2.16 GHz. 802.11ay will provide channel bonding of up to four channels, while also adding MIMO, with a maximum of 4 spatial-streams. 256-QAM modulation is also expected to be added. 802.11ay will operate in the unlicensed bands above 45 GHz, and it will provide backward compatibility with 802.11ad. It is expected to be approved some time in 2019. The main uses of 802.11y appear to be DisplayPort, HDMI and USB connectivity, along with connectivity for TV and monitor displays. One of the goals of 802.11az is to improve physical location tracking and positioning of 802.11 devices. Better accuracy could be used with smart building applications and tracking IoT devices. Another goal of this amendment is to increase the energy efficiency of the network. This amendment is expected to define an energy-efficient data-reception mode, referred to as wake-up radio(WUR). The objective is to increase battery life of devices, such as battery powered IoT devices, without increasing network latency or slowing down performance. The next two amendments were never ratified and are considered dead in the water. However, the subject matter (roaming and performance testing) of the two amendments is important and therefore we will discuss them in this book. The IEEE Task Group F (TGF) published IEEE Std 802.11F-2003 as a recommended practice in 2003. The amendment was never ratified and was withdrawn in February 2006. The original published 802.11 standard mandated that vendor APs support roaming. A mechanism is needed to allow client stations that are already communicating through one AP to be able to jump from the coverage area of the original AP and continue communications through a new AP. A perfect analogy is the roaming that occurs when using a cell phone. When you are talking on a cell phone while inside a moving vehicle, your phone will roam between cellular towers to allow for seamless communications and hopefully an uninterrupted conversation. Seamless roaming allows for mobility, which is the heart and soul of true wireless networking and connectivity, as depicted in Figure 2.3. FIGURE 2.3 Seamless roaming Although the 802.11 standard calls for the support of roaming, it fails to dictate how roaming should actually transpire. The IEEE initially intended for vendors to have flexibility in implementing proprietary AP-to-AP roaming mechanisms. The 802.11F amendment was an attempt to standardize how roaming mechanisms work behind the scenes on the distribution system medium, which is typically an 802.3 Ethernet network using TCP/IP networking protocols. 802.11F addressed “vendor interoperability” for AP-to-AP roaming. The final result was a recommended practice to use the Inter-Access Point Protocol (IAPP). IAPP uses announcement and handover processes that result in APs informing other APs about roamed clients as well as delivery of buffered packets. Because the 802.11F amendment was never ratified, the use of IAPP is basically nonexistent. The original goal of the IEEE 802.11 Task Group T (TGT) was to develop performance metrics, measurement methods, and test conditions to measure the performance of 802.11 wireless networking equipment. The 802.11T proposed amendment was also called Wireless Performance Prediction (WPP). Its final objective was consistent and universally accepted WLAN measurement practices. These 802.11 performance benchmarks and methods could be used by independent test labs, manufacturers, and even end users. The IEEE Task Group m (TGm) started an initiative in 1999 for internal maintenance of the 802.11 standard’s technical documentation. 802.11m is often referred to as 802.11 housekeeping because of its mission of clarifying and correcting the 802.11 standard. Unless you are a member of TGm, this amendment is of little significance. However, this task group also is responsible for “rolling up” ratified amendments into a published document. The following list shows the revisions of the standard that have been created over the years, along with the task group responsible for them. IEEE Std 802.11-2007 802.11 TGma IEEE Std 802.11-2012 802.11 TGmb IEEE Std 802.11-2016 802.11 TGmc Next 802.11 consolidation 802.11 TGmd This chapter covered the original 802.11 standard, the amendments consolidated into the 802.11-2007 standard, the 802.11-2012 standard, and the 802.11-2016 standard, as well as 802.11 amendments ratified since the consolidation of the 802.11-2016 standard. This chapter also discussed possible future enhancements. We covered the following: Although proprietary Wi-Fi solutions exist and will continue to exist in the foreseeable future, standardization brings stability to the marketplace. The 802.11-2016 standard and all the future enhanced supplements provide a much needed foundation for vendors, network administrators, and end users. The CWNA exam will test your knowledge of the 802.11-2016 standard and all the related technologies. Know the defined spread-spectrum technologies of the original 802.11 standard and the subsequent 802.11-2007, 802.11-2012, and 802.11-2016 standards. Although the original 802.11 standard defined infrared, FHSS, and DSSS, later amendments that are now incorporated in the 802.11-2016 standard also define HR-DSSS, OFDM, ERP, HT, and VHT. Remember both the required data rates and supported data rates of each PHY. DSSS and FHSS require and support data rates of 1 and 2 Mbps. Other PHYs offer a wider support for data rates. For example, OFDM and ERP-OFDM support data rates of 6, 9, 12, 18, 24, 36, 48, and 54 Mbps, but only the rates of 6, 12, and 24 Mbps are mandatory. With the introduction of 802.11n, it is important to understand the concept of modulation coding schemes (MCSs), which is also defined in 802.11ac. Please understand that data rates are transmission speeds, not aggregate throughput. Know the frequency bands used by each PHY as defined by the 802.11-2016 standard. 802.11a and 802.11ac equipment operate in the 5 GHz U-NII bands. DSSS, FHSS, HR-DSSS, and ERP (802.11g) devices transmit and receive in the 2.4 GHz ISM band. Understand that 802.11n devices transmit in either the 2.4 GHz or 5 GHz frequency bands. Define transmit power control and dynamic frequency selection. TPC and DFS are mandated for use in the 5 GHz band. Both technologies are used as a means to avoid interference with radar transmissions. Explain the defined wireless security standards, both pre-802.11i and post-802.11i. Before the passage of 802.11i, WEP and TKIP were defined. The 802.11i amendment called for the use of CCMP/AES for encryption. For authentication, 802.11i defines either an 802.1X/EAP solution or the use of PSK authentication. An ERP (802.11g) network mandates support for which two spread-spectrum technologies? Which amendment defines performance enhancements using the much higher unlicensed frequency band of 60 GHz, and a transmission method known as directional multi-gigabit (DMG)? Which types of devices were defined in the original 802.11 standard? (Choose all that apply.) Which 802.11 amendment defines wireless mesh networking mechanisms? A robust security network (RSN) requires the use of which security mechanisms? (Choose all that apply.) An 802.11ac radio card can transmit on the _______________ frequency and uses _______________ spread-spectrum technology. What are the required data rates of an OFDM station? When implementing an 802.1X/EAP RSN network with a VoWiFi solution, what is needed to avoid latency issues during roaming? Which new technologies debuted in the 802.11ac-2013 amendment? (Choose all that apply.) What is the primary reason that OFDM (802.11a) radios cannot communicate with ERP (802.11g) radios? Which two technologies are used to prevent 802.11 radios from interfering with radar and satellite transmissions at 5 GHz? Which 802.11 amendments provide for throughput of 1 Gbps or higher? (Choose all that apply.) As defined by the 802.11-2016 standard, which equipment is compatible? (Choose all that apply.) What is the maximum data rate defined by the 802.11ac amendment? What are the security options available as defined in the original IEEE Std 802.11-1999 (R2003)? (Choose all that apply.) The 802.11u-2011 amendment is also known as what? The 802.11-2016 standard defines which two technologies for quality of service (QoS) in a WLAN? The 802.11h amendment (now part of the 802.11-2016 standard) introduced which two major changes for 5 GHz radios? The 802.11n amendment defined which PHY? Which layers of the OSI model are referenced in the 802.11 standard? (Choose all that apply.)
![]() Original IEEE 802.11 standard
Original IEEE 802.11 standard
![]() Post 802.11-2016 ratified amendments
Post 802.11-2016 ratified amendments
![]() IEEE 802.11 draft amendments
IEEE 802.11 draft amendments
![]() Defunct amendments
Defunct amendments
![]() IEEE Task Group m
IEEE Task Group m As discussed in Chapter 1, “Overview of Wireless Standards, Organizations, and Fundamentals,” the Institute of Electrical and Electronics Engineers (IEEE) is the professional society that creates and maintains standards that we use for communications, such as the 802.3 Ethernet standard for wired networking. The IEEE has assigned working groups for several wireless communication standards. For example, the 802.15 working group is responsible for personal area network (PAN) communications using radio frequencies, such as Bluetooth. Another example is the 802.16 standard, which is overseen by the Broadband Wireless Access Standards working group; this technology is often referred to as WiMAX. The focus of this book is the technology as defined by the IEEE 802.11 standard, which provides for local area network (LAN) communications using radio frequencies (RFs).
As discussed in Chapter 1, “Overview of Wireless Standards, Organizations, and Fundamentals,” the Institute of Electrical and Electronics Engineers (IEEE) is the professional society that creates and maintains standards that we use for communications, such as the 802.3 Ethernet standard for wired networking. The IEEE has assigned working groups for several wireless communication standards. For example, the 802.15 working group is responsible for personal area network (PAN) communications using radio frequencies, such as Bluetooth. Another example is the 802.16 standard, which is overseen by the Broadband Wireless Access Standards working group; this technology is often referred to as WiMAX. The focus of this book is the technology as defined by the IEEE 802.11 standard, which provides for local area network (LAN) communications using radio frequencies (RFs).Original IEEE 802.11 Standard
IEEE 802.11-2016 Ratified Amendments
802.11a-1999
802.11b-1999
802.11d-2001

802.11e-2005
802.11g-2003
802.11 legacy
802.11b
802.11g
802.11a
Frequency
2.4 GHz ISM band
2.4 GHz ISM band
2.4 GHz ISM band
5 GHz U-NII-1, U-NII-2, and U-NII-3 bands
Spread-spectrum technology
FHSS or DSSS
HR-DSSS
OFDM
Data rates
1, 2 Mbps
ERP-DSSS/CCK: 1, 2, 5.5, and 11 Mbps
6, 12, and 24 Mbps are mandatory.
ERP-OFDM: 6, 12, and 24 Mbps are mandatory.
Also supported are 9, 18, 36, 48, and 54 Mbps.
Also supported are 9, 18, 36, 48, and 54 Mbps.
Backward compatibility
N/A
802.11 DSSS only
802.11b HR-DSSS and 802.11 DSSS
None
Ratified
1997
1999
2003
1999
802.11h-2003
802.11i-2004
802.11j-2004
802.11k-2008
802.11n-2009
802.11p-2010
802.11r-2008
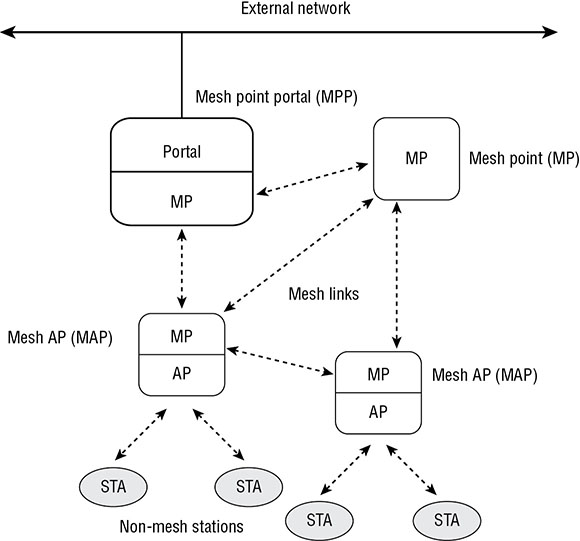
802.11s-2011
802.11u-2011
802.11v-2011
802.11w-2009
802.11y-2008
802.11z-2010
802.11aa-2012
802.11ac-2013
802.11ad-2012
802.11ae-2012
802.11af-2014
Post 802.11-2016 Ratified Amendments
802.11ah-2016
802.11ai-2016
IEEE 802.11 Draft Amendments
802.11aj
802.11ak
802.11aq
802.11ax
802.11ay
802.11az
802.11ba
Defunct Amendments
802.11F

802.11T
IEEE Task Group m
Summary
Exam Essentials
Review Questions
