In this chapter, you will learn about security assessments, penetration testing, risk management, and various testing tools.
- 1.
Identify security assessments.
- 2.
Identify the steps of penetration testing.
- 3.
Examine risk management.
- 4.
Identify various penetration testing tools.
Penetration Testing Overview
A penetration test , also known as a pen test, is used to simulate methods that an attacker would use to gain unauthorized access to a network and compromise the systems. A penetration test is considered a security assessment.
Each type of assessment serves a purpose, and it is important to understand the differences between them. Penetration testing assesses the security model of the network and can help administrators and management understand the potential consequences of an attack.
Security Assessments
Security audits: Security audits focus on the people and processes used to design, implement, and manage security on a network. The National Institute of Standards and Technology (NIST) has several special publications that can be used as guides—SP 800-53 for the specification of security controls and SP 800-53A for the assessment of security control effectiveness. For more information, visit the National Institute of Standards and Technology (www.nist.gov/).
Vulnerability assessments: Vulnerability assessments scan the network for known security weaknesses. Vulnerability scanning tools compare the computer against the Common Vulnerability and Exposure (CVE) Index and security bulletins provided by software vendors. The CVE is a vendor-neutral listing of reported security vulnerabilities and is maintained. For information, visit the CVE website (http://cve.mitre.org/).
Penetration testing: A penetration test goes a step beyond vulnerability scanning because not only will it point out vulnerabilities, but it will also document how weaknesses can be exploited and how minor vulnerabilities can be escalated by an attacker.
Phases of Penetration Testing
External tests can be black-box (zero-knowledge testing), gray-box (partial-knowledge testing), or white-box (complete-knowledge testing). Internal testing can be used for organizations that have the resources available. If there is insufficient expertise in-house, outsourcing is recommended.
- 1.
Planning phase: In the planning phase, rules are identified and testing goals are set. Information about the target is gathered in the preattack phase. The information gathered will form the basis of the attack strategy. After the attack, the tester needs to restore the network back to its original state.
- 2.
Preattack phase: The preattack phase includes identifying threats to help conduct a risk assessment and to calculate the relative criticality of the threat. Business impact of threats can be designated as high, medium, or low. Internal metrics use data available within an organization to assess the risk of attack while external metrics are derived from data collected outside the organization. Assigning probability values to an exploit’s success allows the calculation of relative criticality. During this phase, the testing team will gather as much information as possible about the target company. There are a number of ways that information can be retrieved, as detailed.
- 3.
Attack phase: The attack phase involves the actual compromise of the target by perhaps exploiting a vulnerability found during the preattack phase or using security loopholes such as a weak security policy to gain access.
- 4.
Post-attack phase: It is the responsibility of the tester to restore any systems to the pretest state. Remember, the purpose of pen testing is to show where the failures of security exist, not to correct the problems.
Documentation
Penetration testing reports highlight incidents that occurred and the range of activities.
Fault tree and attack trees specify root events and identify events related to the root. Attack trees in particular look at who, when, why, how, and what.
Gap analysis evaluates the gaps between where an organization wants to be and where it currently stands. External standards can be used as part of the gap analysis to provide recommendations as to how the organization can reduce the gaps found.
Creating Payloads
You can build payloads with Metasploit that connect to the attacker’s machine when the victim runs them. Payloads for Windows, Linux, and Mac OS X operating systems can be created. When creating the payload, you can define the attacker’s port number, IP address, or fully qualified domain name (FQDN) and payload type, like meterpreter or Windows Command Shell.
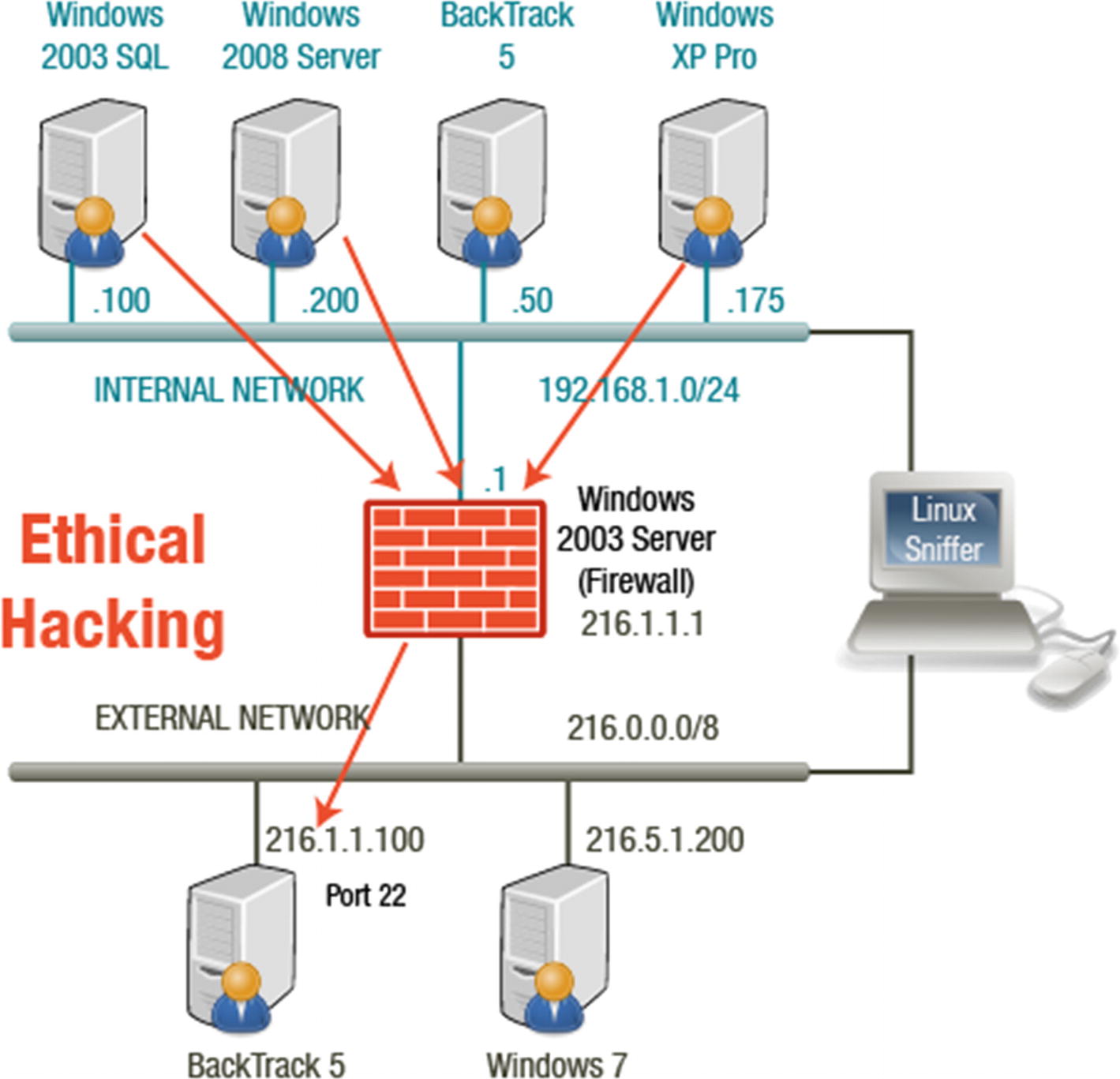
Network Attack 1
Exploiting a Victim Machine

FTP session
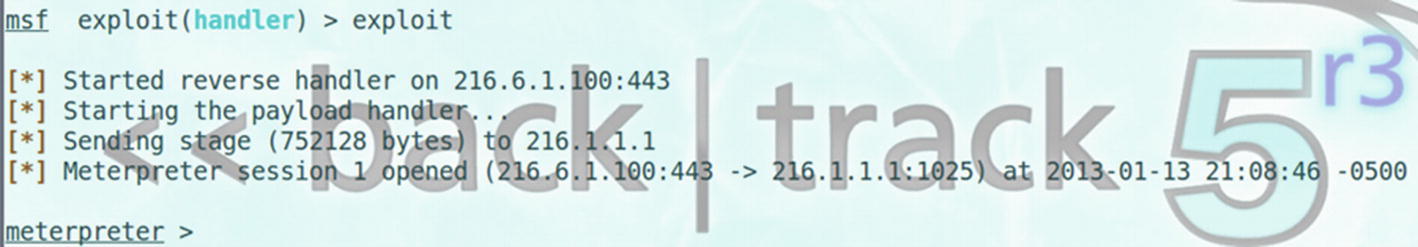
Running the exploit
Summary
In this chapter, you learned about penetration testing. You gained an understanding of what security assessments entail and what is involved in risk management. This chapter also highlighted tools that can be used to conduct penetration testing.
Resources
National Institute of Standards and Technology (NIST): www.nist.gov/
