Chapter 2
Understanding NAC Framework
This chapter covers the following topics:
- NAC Framework authorization process
- Posture token types
- Using information from the host for the admission decision
- Dealing with hosts that are not NAC capable
- NAC modes of operation
- NAC communication protocols
- NAC-L3-IP and NAC-L2-IP posture validation and enforcement process
- NAC-L2-802.1X identity with posture validation and enforcement process
- NAC agentless host auditing process
- Authorization and enforcement methods
- NAC agentless host and exception handling
Network Admission Control (NAC) Framework is a flexible but complex solution involving many parts of your network. This chapter begins with a deeper description of how NAC operates and identifies the types of information that make its admission decisions. NAC uses different modes of operation that are based on the network access device (NAD) that the host connects to. The packet flow processes and protocols involved can differ by the mode used. Hosts and endpoints that do not use NAC protocols but still need to be able to use the network, bypassing the NAC process, require special consideration.
This chapter discusses the following topics:
- NAC communication modes and when they are used
- How host credentials are used in a policy to determine levels of compliance
- Techniques that allow network admission for endpoints and hosts that are not NAC enabled
- Application posture tokens, system posture tokens, and six predefined posture token states
- Enforcement actions available for noncompliant hosts
- Different access control methods used by various Cisco network access devices
- Exempting devices attempting network access that are not NAC capable from the validation and enforcement process
NAC Framework Authorization Process
NAC operates by requesting a set of credentials from a host attempting network access.
It is important to understand the different modes and how they operate differently before proceeding to the later chapters. Figure 2-1 describes the authorization process, this time at a deeper level than the previous chapter. In this example, both identity and host compliance are determined at the same time.
Figure 2-1 NAC Posture Validation Flow
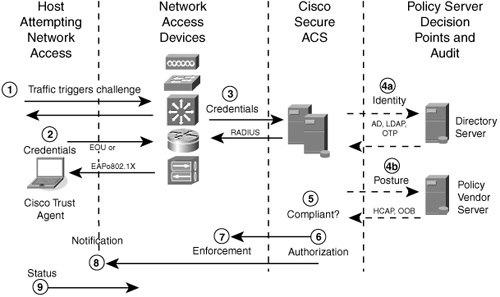
As shown in Figure 2-1, this more complex NAC example has the following nine major steps:
1 The host attempts network access, and its access attempt triggers the NAC process. This causes the NAD to initiate an Extensible Authentication Protocol (EAP) exchange with the Cisco Trust Agent running on the host. The host's identity is requested as part of EAP, and this identity is passed to the back-end authentication, authorization, and accounting (AAA) server, a Cisco Secure Access Control Server (ACS). The Cisco Secure ACS initiates an EAP session with the host. During the Cisco Secure ACS–to–Cisco Trust Agent EAP session, the NAD acts only as a pass-through device, performing reencapsulation of EAP packets.
2 The Cisco Secure ACS negotiates a secure tunnel with the client as part of the EAP session setup. Cisco Secure ACS then requests posture validation credentials from the host's security applications by way of their associated posture plug-ins. Each NAC-enabled application communicates its credentials to Cisco Trust Agent. These credentials can contain one or more attributes that have values associated with them that pertain to the state of the security applications communicating with the NAC solution on the host.
3 The NAD passes the credentials and identity from Cisco Trust Agent to ACS using a protected Transport Layer Security (TLS) tunnel, where the NAD never sees them. Depending on the support for NAC in the security application, ACS can be optionally configured to pass the entire credential from a posture plug-in to a partner's external validation server(s).
4 In this example, multiple external servers validate the user identity as well as the host posture. ACS sends both servers only the information they need to make a decision about their specific credentials.
a ACS receives identity information about the user logged on to the host. ACS has been configured to pass this identity information to an external user database such as an Active Directory server, Lightweight Directory Access Protocol server, One Time Password server, or another type of user store. This is an optional step; however, it relieves ACS from the responsibility for maintaining usernames and user identity credentials. Note that identity information is only present in the Extensible Authentication Protocol over 802.1X (EAPo802.1X) flows.
b Meanwhile, ACS also receives host posture credentials from a NAC-enabled vendor's application on the host. ACS can optionally send posture credentials to a separate vendor's posture validation server (PVS). Doing this can reduce the load on the ACS server while providing more centralized automatic policy updates by the security vendor's external PVS. In this scenario, the policy evaluation responsibility is passed to the security vendor's PVS, which reports the evaluation results to ACS.
5 Each external PVS performs its individual posture check from the received credentials and sends its own posture decision results back to ACS. ACS looks at all the decisions to make a final decision on whether the host is compliant. The decision is based on the most restrictive result. Because identity is a required part of the NAC-L2-802.1X session, if the identity authentication fails when operating in NAC-L2-802.1X mode, the entire session will fail and the authorization process will not perform the posture check.
6 ACS makes the final decision and determines the authorization level. It assigns the appropriate enforcement and action for this user or host. Part of the enforcement actions Cisco Secure ACS sends to the NAD can include timers that can specify how long a NAD can grant access to the host without reposturing that host. When operating in NAC-L2-IP or NAC-L3-IP mode, the enforcement action can also include how often a NAD must check the status of the host.
7 The NAD receives the appropriate network access policy from ACS for the host and enforces the decision. If the host is compliant with network admission policies and valid machine or user credentials exist in NAC-L2-802.1X sessions, network access is granted.
8 A message is also sent back to Cisco Trust Agent running on the host. Optionally, it can inform the end user by way of a notification pop-up message.
9 Because a host cannot be Layer 2 adjacent to the NAD in either the NAC-L2-IP or NAC-L3-IP modes, a status query takes place between the NAD and the Cisco Trust Agent during regular intervals to ensure that the user/host status has not changed since the last validation process. If a status change occurs with a host operating in NAC-L2-802.1X mode, the posture plug-ins signal the 802.1X supplicant operating on that host to initiate the EAP.
Posture Token Types
Prior to NAC, the concept of the network enforcing access policies based on a host's health status was not imaginable. Now NAC can classify hosts into one of several different states that represent the host's relative health on the network. Each individual security application can have a health token associated with it. These tokens are called application posture tokens (APTs). The worst or most restrictive of these APTs becomes the system posture token (SPT). The SPT represents that particular host's health from a network admissions policy standpoint. The following keywords have been reserved for this classification purpose. These keywords are ordered from least restrictive to most restrictive:
- Healthy—A host is compliant with the admission policy because no updates are available. Examples include the operating system (OS), personal firewall policies, and up-to-date antivirus files. No updates to this host are required or available.
Even if updates are available, an administrator might determine that the host is healthy as long as it has an update version greater than a predetermined version number. The determination of what is acceptable is left to the discretion of the administrator. The latest updates available by a vendor might not always be the preferred ones by the administrator.
• Checkup—A host does not have the required antivirus signatures, operating system patches, or firewall policies installed, but it is not so far out of date that network access for that host needs to be restricted. A pop-up window displayed from Cisco Trust Agent should notify the user that security updates are available and recommended.
• Transition—This token is used for two different conditions:
— The first condition is when a partially booted host does not have all necessary services running that allow a healthy posture check. In this scenario, the host would be put into the transition state and the revalidation timer would be set for a short period of time to allow the host to finish its boot process and the necessary services to start.
— The second condition is where a transition token is used for an auditing process for a host that is not NAC enabled. In this scenario, the health of the host is not known until the audit completes. This allows the NAD to grant temporary (and perhaps limited) network access for the auditing to successfully complete as well as to provide a URL redirection if required.
The transition token is not meant to be an assigned token the way that the other tokens are assigned. Transition merely means that the posture validation process has not completed and that a token will be assigned at the conclusion of the posture process.
• Quarantine—A host is out of policy with the network admission requirements. A pop-up notification informs the user that her host is out of compliance, and normal network access is denied until compliance is detected. Instructions should also inform the user of the necessary steps to become compliant to regain normal network access. ACS can also be configured for a Cisco Trust Agent action to automatically launch a browser to the specified remediation server needed to update the user's host. In NACL2-IP or NAC-L3-IP modes, the NAD can be configured to perform URL redirection on web requests for the host to a remediation server.
• Infected—An active virus infection has been detected on that host or the antivirus or personal firewall services have been disabled, assuming an infection has already occurred. This state typically has the greatest restrictions imposed to prevent the host from contacting any network resources except for remediation servers. In some cases, the host can be isolated from gaining access to the network. A pop-up window displayed by Cisco Trust Agent should be configured to notify the user of the actions taken and the reasons behind those actions.
• Unknown—A host type cannot be determined, and some access might be permitted. An example is allowing a guest user or other host that is not NAC enabled to have limited network access such as accessing the Internet only or other accordance with the business's network access policy.
Healthy is considered the best state. Checkup, transition, and quarantine are ranked by sequence. Infected is the worse state.
Using Information from the Host for the Admission Decision
Information is gathered from the host and passed to Cisco Trust Agent. Cisco Trust Agent communicates this information to the NAC policy server ACS. Optionally, ACS can send the vendor-specific information to the vendor's PVS to determine compliance with the admission policy.
The following two forms of data can be collected from the host:
- Host credential information is collected from NAC-enabled application agents.
- Optional arbitrary information can be collected by Cisco Trust Agent using custom scripting.
Host Credential Information
The NAC Framework solution uses credentials provided by the Cisco Trust Agent and any other security applications to inform the policy server about the health of those applications. Each credential contains one or more attributes with data associated with those attributes.
As shown in Table 2-1, different data types and operations can be performed on the received attributes for a given policy.
Table 2-1 Credentials and Attributes
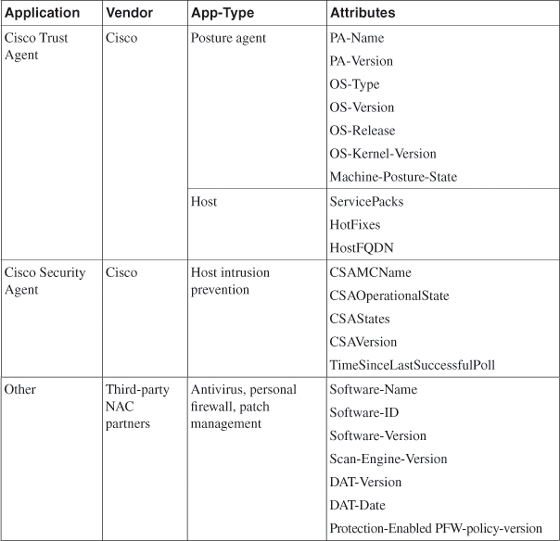
The top row in this table represents attributes from Cisco Trust Agent that can be collected and analyzed. The second row represents Cisco Security Agent (CSA) attributes, and the last row represents other NAC-enabled applications offered by vendors. Vendor attributes vary and can be imported and used by ACS for policy evaluation.
NAC policies use credentials and attributes that represent a variety of different conditions on the host, such as the antivirus signature file version, particular patches or service packs that have been installed on that host, or values associated with the host itself, such as a fully qualified domain name. These attribute values are then tested against specific policies configured in ACS.
For example, a Cisco Trust Agent policy can use the following attributes to check on a specific OS service pack:
- Application: Cisco Trust Agent
- Vendor: Cisco
- App Type: Host
- Attributes: Service Packs
An operation is also assigned to the different attribute value types that are included with different policies in ACS. Table 2-2 shows the different value types.
Table 2-2 Credential and Attribute Operations

The credential and attribute fields allow an almost limitless definition of a credential. For example, a string can be used to perform a registry check.
Operations vary based on the attribute. Operation choices include the following:
- =
- <
- >=
- starts with
- contains
For example, the following operation and value is assigned to the Service Pack attribute:
Service Pack >= 3
In this example, >= is the attribute operation. To comply with this policy, the host service pack must be greater than or equal to 3. Otherwise, it is not compliant with the Cisco Trust Agent host policy.
Typically, multiple attributes are assigned in a policy, where all attributes must be met for compliance. For example, the following must be met for the host to be considered healthy in this scenario:
Service Pack >=3
HotFix = KB888302
HotFix = KB890047
Creating policies with host credentials and attributes are discussed in greater detail in Chapter 4, "Posture Validation Servers."
Arbitrary Information Collection with Cisco Trust Agent Scripting
You might want to collect arbitrary data from your hosts that might not be provided by a posture plug-in associated with a vendor's security application. This data can include version information from non-NAC-participating vendors and windows registry keys. Cisco has provided a method of collecting and using this data with the Cisco Trust Agent scripting interface. The Cisco Trust Agent scripting interface makes use of text files that your custom application creates containing the specific information you want to include in your NAC implementation.
Dealing with Hosts That Are Not NAC Capable
Figure 2-1 describes a high-level operation of NAC with the Cisco Trust Agent installed on a host attempting network access. In some situations, the hosts or other types of endpoints on your network might not be capable of running Cisco Trust Agent, which means they cannot communicate with NAC Framework. If NAC cannot communicate with the host or endpoint, authentication fails and no network access is granted. This might not be desirable.
Hosts that are not NAC capable are referred to as NAC agentless hosts (NAHs). Provisioning for NAHs is available and can be configured by using a variety of static exemption techniques or by using an NAH auditing process.
Static Exemptions for NAH
NAHs can be exempted from the NAC process by creating an exception list that identifies the host's or endpoint's unique static IP address or the MAC address. You can create an exemption list on a NAD; this exempts the hosts listed from the NAC process. As an alternative, the MAC addresses can be entered into specific sections of ACS software for use on a network-wide scale, where the host can be mobile.
Centralized IP whitelisting is no longer possible in ACS 4.0.
In addition to the IP or MAC address, you can also use a device type to create an exception. An example of this would be a Cisco IP Phone, where that phone is connected to a Cisco switch port and communicates with the switch using Cisco Discovery Protocol (CDP). The switch learns about the device type and dynamically exempts that specific device from the NAC process by placing it into the voice VLAN.
NAC Agentless Auditing
Another method of dealing with an NAH is by using an auditing process, as shown in Figure 2-2.
Figure 2-2 NAC Agentless Host Audit Flow
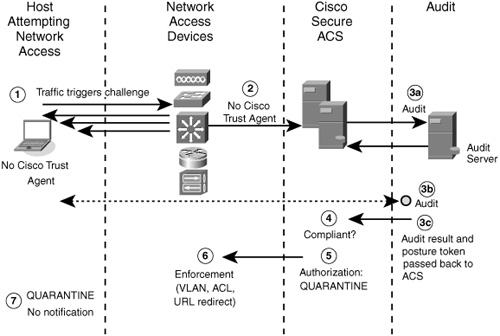
The following process describes the audit flow shown in Figure 2-2:
1 After triggering the NAC process, the NAD attempts to initiate an EAP session with the host.
2 After three unsuccessful EAP hello attempts occur, the NAD and ACS are configured to trigger the NAH audit process in either NAC-L2-IP or NAC-L3-IP mode.
3 The following three steps occur:
a ACS contacts an audit server using the Generic Authorization Message Exchange (GAME) protocol.
b The audit server initiates the auditing process. This audit process can take one of two forms: (a) an active audit, where the audit server contacts the host out-of-band of the NAC process and attempts to assess the condition of the host that triggered the audit using a network-scanning technique or (b) Cisco Secure ACS configures the NAD to perform a URL redirection on HTTP requests from the host. This action would trigger an auditing applet from the audit server.
c The result of the audit is a posture token that the audit server sends back to ACS.
4 ACS then looks at the posture token to determine an appropriate action. In this example, because Cisco Trust Agent is not installed and running on the host, the audit server has assigned a quarantine token to the host. ACS has assigned a quarantine SPT to the host because that is the most restrictive APT.
5 ACS informs the NAD of the enforcement quarantine policy.
6 The NAD enforces network admission by means of a restrictive access control list (ACL) or a URL redirect to a remediation server.
7 The device is quarantined, but because the host does not have a Cisco Trust Agent, a pop-up message does not appear. Instead, the user sees a quarantine web page from his browser if the host has had a URL redirection assigned as part of the enforcement action.
For hosts that do not have Cisco Trust Agent installed, you have the following choices:
- Redirect the NAH to an audit server to scan and determine whether the host is compliant. Then communicate the decision to ACS to determine the admission policy and actions the NAD should enforce on the host. This is an option when operating in NAC-L2-IP or NAC-L3-IP mode.
- Do no provisioning for hosts or endpoints without Cisco Trust Agent. The result is that the NAH fails authentication and network access is denied.
NAC Modes of Operation
NAC operates in at least one of the following modes:
- NAC-L3-IP
- NAC-L2-IP
- NAC-L2-802.1X
Generally, the first part of these terms (Lx) refers not to the protocol used by NAC for communication, but to the type of network port that is communicating with the host undergoing the posture validation procedure. In this manner, L3 refers to a router port working at Layer 3, and L2 is a switch port working at Layer 2.
The final part of the term refers to the protocol that carries the EAP packet between the host undergoing posture validation and the NAD. IP refers to the EAP over UDP (EoU) implementation, and 802.1X refers to the EAP over 802.1X method, which can also carry identity information for a user, a host, or both. Each of these modes has different triggering methods, capabilities, and access enforcement methods.
NAC-L3-IP and NAC-L2-IP Overview
NAC-L2-IP and NAC-L3-IP both use the Internet Protocol (IP) to carry the authentication packets from the host undergoing NAC to the network. Because IP is used for this communication, these hosts do not need to be directly connected to the devices acting as a NAD, but can be several IP subnet hops away. This introduces a problem where the NAD might not know that a host's status has changed. For example, a host completes posture validation into a healthy state. That same host disconnects from the network. Now a different host connects and is assigned the previously used IP address by way of DHCP. The NAD would not see a change in the host IP address or MAC address, assuming that host was connected to a nonlocal network. To prevent this type of problem from occurring, a status query protocol exists and checks back with the host at configurable intervals to make sure that nothing has changed since it last looked.
The discovery of the host varies by the type of NAD port that the host connects through. In the case of a switch port, with NAC-L2-IP, the discovery of the new host is done by DHCP snooping or by Address Resolution Protocol (ARP) inspection. In the case where a host is connected through a router port performing NAC, with NAC-L3-IP, a packet sent by the host that is forwarded through the router triggers the NAC process. Both of these discovery processes are traffic based, meaning that traffic transmitted by the host is required to trigger the NAC process. NAC-L2-IP and NAC-L3-IP work with either static or dynamic network address translation (NAT) but are incompatible with NAT overload or port address translation (PAT). This is because NAC-L2-IP and NAC-L3-IP maintain a session with each individual IP address. PAT hides multiple hosts behind a single IP address and does not permit individual sessions between the host and the NAD.
NAC-L2-802.1X Overview
The IEEE 802.1X protocol is a data-link layer protocol. This implies that the host must be directly connected to the switch port that is performing the NAC process. NAC-L2-802.1X is the NAC mode that combines the 802.1X protocol with NAC for machine and user identity checking along with posturing for endpoint authentication.
Because the host is directly connected to the switch port performing NAC, an Ethernet linkup signal from the host is enough to trigger EAP and the NAC process. The host can also send an EAP over LAN (EAPoL) start packet to trigger this process in certain circumstances while the Ethernet link is maintained. In either case, the NADs begin the actual EAP protocol with the client.
NAC Communication Protocols
Prior to jumping into the detailed operation of NAC, it is helpful to understand the protocols that are used for communications in the NAC solution. NAC uses EAP extensively, both as an established standard and as a proprietary prestandard (at the time of this writing).
EAP Primer
The Extensible Authentication Protocol (EAP) provides a flexible framework for authentication, with support for multiple internal authentication methods. EAP can run directly over a data-link layer protocol, such as IEEE 802, or over a transport layer protocol, such as User Datagram Protocol (UDP). While an in-depth knowledge of EAP is not necessary for administration of a NAC-enabled network, some knowledge of EAP operation is helpful during troubleshooting operations.
EAP is a request/response protocol, where the authenticator makes a request and the peer responds to that request. The EAP authenticator can act as a pass-through device for a backend authentication server. Because EAP is a request/response protocol, only a single packet can be outstanding at a time. For each request sent by the server/authenticator, a response must be received by the peer. EAP attempts a small number of retransmissions but provides no provisioning for reordering of packets, so the lower-layer protocol must not change the packet order. EAP also does not provide reassembly of fragmented packets. This means that the message size is limited to the maximum transmission unit (MTU) of the network medium.
EAP sessions are always initiated by the authenticator or by a back-end server. EAP packets can be one of four types:
- Request
- Response
- Success
- Failure
The receipt of an EAP success packet does not mean that the NAC authentication permits the peer onto the network, only that the EAP authentication protocol completed successfully. The network admission decision is based on the hosts' compliance with network policies. More information regarding EAP can be found in RFC 3748.
Client-Side Front-End Protocols
EAP carries the necessary information from the hosts undergoing admission into the network that is performing NAC. The EAP conversation is started by the NAD after discovery of a new host connected through an interface or traversing a NAD with NAC configured. This works slightly differently depending on whether the network interface is a switch port or a router port and whether the underlying protocol carrying the EAP packet is UDP/IP or IEEE 802.1X.
EAP over UDP (EoU)
In NAC modes where EAP is carried over IP, UDP is used as the transport protocol. It uses a default port of 21862, or 5566 in hexadecimal; this can be changed on both the NAD and the hosts participating in NAC. This was the initial NAC mode introduced by routers at Layer 3. This also works on Layer 3–capable switches that support NAC.
EAP over 802.1X (EAPo802.1X)
In this implementation, the EAP packet is carried from the host to the switch port by an IEEE 802.1X MAC frame. Part of this encapsulation includes the Flexible Authentication with Secure Tunneling (FAST or EAP-FAST) protocol. EAP-FAST allows multiple credential types, such as user identity and posture credentials, to be chained together in a single authentication packet. This allows NAC-L2-802.1X to perform both user and machine identity authentication as well as posture validation. The switch performs the reencapsulation to EAP over RADIUS necessary for transmission of the EAP packet to ACS.
RADIUS and EAP over RADIUS
For communications between the NAD and ACS, the EAP packet is encapsulated into a RADIUS packet by the NAD. These packets follow the same request/respond communication defined by the EAP protocol, with a separate EAP session for each host participating in the NAC solution.
Server-Side Protocols
The following sections describe Cisco-proprietary protocols that are licensed to NAC partners for interoperability between ACS and vendor servers for NAC policy validation and auditing functions. These protocols are the Host Credentials Authorization Protocol (HCAP) and GAME.
Host Credential Authorization Protocol (HCAP)
Administration of a AAA server becomes increasing complex with each additional credential and the associated attributes received from hosts with posture agents. A more efficient method of allowing an external PVS to conduct the evaluation of attributes exists by using HCAP. HCAP is a request/response protocol that is used for communication between the AAA policy server (ACS) and PVS. The AAA server sends an HCAP request to an external PVS along with forwarded credential(s) pertaining to the PVS. The PVS then evaluates the attributes contained in the credential(s) and returns results to the AAA server. HCAP is based on HTTP and can be protected with encryption for additional security.
Generic Authorization Message Exchange (GAME)
ACS uses a specific implementation of Security Assertion Markup Language (SAML) called Generic Authorization Message Exchange (GAME) for its communication with an audit server that is part of NAC. GAME is a request/response protocol that ACS uses to send the audit request to an audit server and then uses to check the progress of an audit session. The GAME protocol also has its roots in HTTP and can be encrypted for additional security.
Vendor-Specific Out-of-Band Protocols
In addition to the previously mentioned protocols, several security application vendors use out-of-band protocols to enable communication between that vendor's server and the security agents that have been deployed on hosts. These protocols are sometimes proprietary and are not part of a standard NAC solution. However, they must be permitted by any enforcement action whenever they are used during the remediation process.
NAC-L3-IP and NAC-L2-IP Posture Validation and Enforcement Process
As described in the "NAC Framework Authorization Process" section, earlier in this chapter, the posture validation process begins with the discovery of a new host attempting to gain access to the network. Figure 2-3 identifies the protocol flows of NAC-L3-IP and NAC-L2-IP posture validation.
Figure 2-3 NAC-L3-IP and NAC-L2-IP Posture Validation Flow
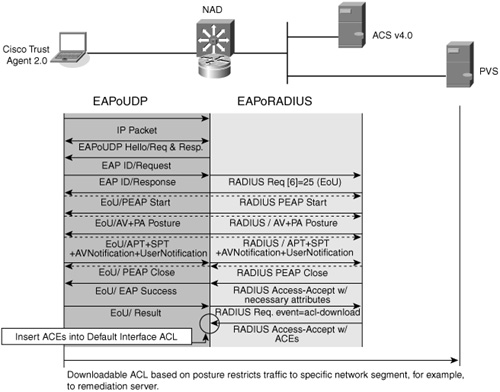
As shown in Figure 2-3, the NAD initiates an EAP session with the host by sending an EAP hello request. The host then responds with an EAP hello response. The NAD sends an EAP identity request that is followed by an EAP identity response from the host. At this point, the NAD initiates a RADIUS request to ACS that includes the identity and address information about the host. ACS then initiates a Protected EAP (PEAP) session with the host. At this point, the NAD acts as a pass-through device only, reencapsulating the EoU packets from the host into EAP over RADIUS packets to be sent to ACS. Part of the PEAP initiation consists of the ACS sending its server certificate to the host. The host then verifies the trust of the ACS server. After the PEAP session has been established, a protected tunnel exists between the host and the ACS server. ACS then requests the host credentials necessary for the policy checks that have been configured. The received credentials and attribute information is compared against locally configured policies and any credentials configured to be sent to an external policy validation server are now sent.
In this example, the host posture is out of compliance and determined to be a quarantine posture, ACS send the NAD quarantine enforcement instructions for the noncompliant host. These enforcement instructions include both Internet Engineering Task Force (IETF) RADIUS standard attributes and Cisco vendor-specific RADIUS attributes. These attributes include the name and access control entry information for ACLs applied, the status query timer value, the revalidation timer value, a text string that contains the SPT for the host, and a URL redirection target URL for the host.
NAC-L3-IP and NAC-L2-IP Status Query
Because the host can be several hops away from the NAD configured for NAC enforcement, a protocol to sense any changes in the host is needed. Figure 2-4 describes the status query protocol.
Figure 2-4 NAC-L3-IP and NAC-L2-IP Status Query
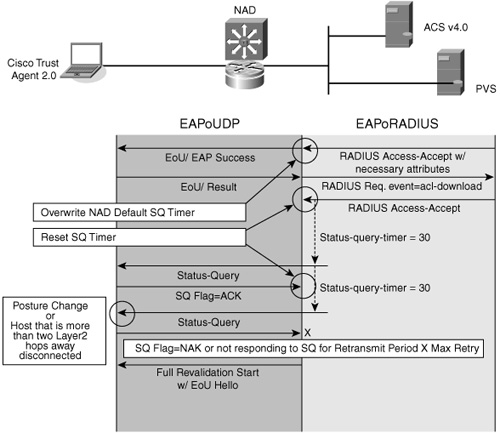
After a host's posture is successfully checked, a status query timer is configured on the NAD as part of the enforcement process shown in Figure 2-4. The value of the timer in seconds can vary depending on the posture token that was set as part of the validation process. When the status query timer expires, a status query challenge is sent from the NAD to the host. If the host responds correctly, the status query timer is reset and no further action is taken. During a status query, the ACS server is not contacted. If the host does not respond correctly or cannot respond correctly because of a host change, the full posture validation process is initiated again, including validation of the host credentials by ACS.
NAC-L3-IP and NAC-L2-IP Revalidation
During normal NAC operation, ACS is only involved during the initial validation of a host. After a host has been validated, it has access rights that might not expire. There is no notification from ACS to a NAD or a host that the policy for network admission has changed. An example of a policy change can be a new mandatory operating system hot fix or an antivirus signature update has become available. To remedy this situation, a revalidation timer is configured to periodically check a host's posture against the network access policy, as shown in Figure 2-5.
Figure 2-5 NAC-L3-IP and NAC-L2-IP Revalidation
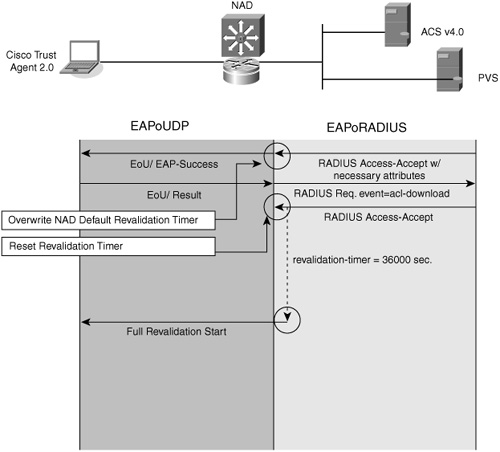
Figure 2-5 describes the NAC revalidation process. This process assures compliance when the policy itself changes as a result of an additional immediate security patch.
Revalidation timers can be configured in the NAD and ACS.
When the revalidation timer expires, the NAD initiates a posture validation session with the host. The difference between an initial validation and a revalidation is that during revalidation, the host has already obtained some set of access rights and those access rights are not removed or changed unless the results of the revalidation process are different from the initial validation.
NAC-L2-802.1X Identity with Posture Validation and Enforcement Process
The previous sections dealt with posture validation communication occurring over IP. This section describes a method of posture validation that can include identity information in the admission decision. The EAP packets can be carried over MAC frames from a host that has not yet received an IP address.
Figure 2-6 describes the L2-802.1X posture validation process that includes checking and enforcement for both device compliance as well as user identity and machine identity.
Figure 2-6 NAC-L2-802.1X Identity with Posture Validation Flow
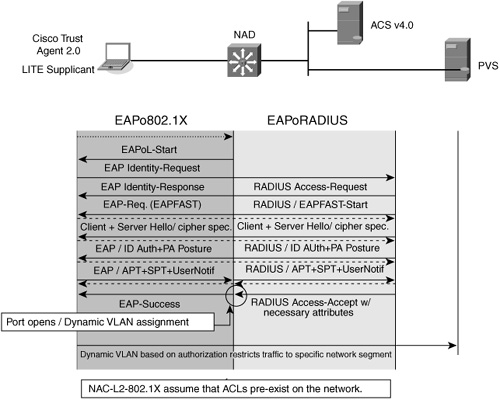
In addition to transporting posture credentials, NAC-L2-802.1X can include identity credentials as part of the decision-making process. NAC-L2-802.1X uses EAP-FAST as a tunneling protocol, which allows authentication credentials to be chained together. As shown in Figure 2-6, the posture session begins when the NAD observes a linkup or the NAD receives an EAPoL start packet from the host. This triggers the initial EAP identity request, which is followed by an EAP identity response from the host. At this point, the NAD reencapsulates the host's identity into an EAP over RADIUS packet that is sent to the ACS. This triggers an EAP session initiated by ACS to the host, with the NAD acting as a pass-through device, similar to the method used in a NAC-L2-IP or NAC-L3-IP session. The host and ACS complete the EAP-FAST tunnel negotiation, which includes an encryption method. The ACS server then requests the identity and posture credentials from the host. Both the posture credentials and any machine identity credentials or user credentials are used in the posture decision process. After a host posture has been determined, the results are passed back to the host. The appropriate access rights and enforcement action are then sent to the NAD.
If identity fails, no posture credentials are checked.
One of the enforcement actions available with NAC-L2-802.1X is dynamic VLAN assignment.
Figure 2-7 describes how the VLAN assignment is derived from ACS and used by the NAD to enforce access to the network.
Figure 2-7 NAC-L2-802.1X Dynamic VLAN Assignment
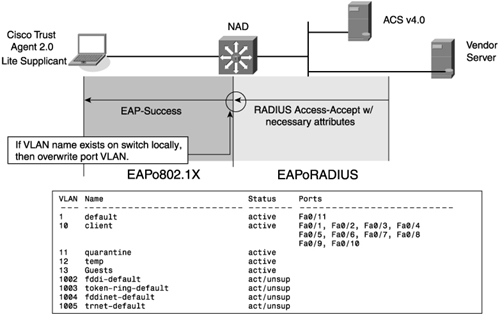
A VLAN assignment is sent to the NAD from ACS as part of the enforcement process after a completed validation. This message uses IETF standard RADIUS attributes to carry the VLAN type, tunnel type, and VLAN name. The VLAN must have been preconfigured on the switch acting as the NAD for this to be successful. NAC-L2-802.1X also has a revalidation mechanism that is available to cover the situation where the network admission policy has changed after a host has completed the validation process. This is configured with the IETF session timeout RADIUS attribute and the terminate-action RADIUS attribute.
In this example, ACS decides the posture token is quarantine for the authenticating device. The switch is instructed to assign a VLAN with the name of quarantine.
As shown in Figure 2-8, after successful authentication, a revalidation timer initiates.
Figure 2-8 NAC-L2-802.1X Reauthentication Process
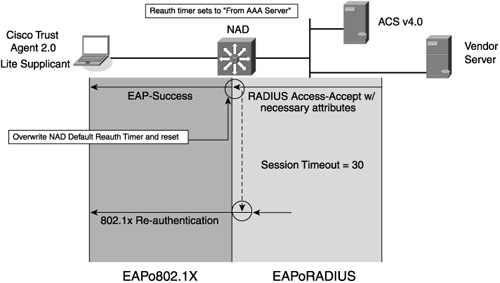
Each host is assigned a revalidation timer as part of the NAC-L2-802.1X validation process. The timer can vary based on the posture. As in this example, where the host is quarantined, the timer is set shorter than a posture of healthy. Upon expiration of this timer, the NAD initiates an EAPoL session with the host by sending an EAPoL identity request packet to the host. As with the NAC-L2-IP mode, the host's access rights remain in place during the validation process. If any change in access rights occurs as a result of a change in the posture revalidation, those changes are applied after the revalidation process completes.
Revalidation timers can be configured in the NAD and ACS.
An additional feature of the NAC-L2-802.1X mode is an asynchronous status query. If the status of the host changes (for example, a user disables the antivirus program or the antivirus program updates itself), the host can initiate a revalidation by the transmission of an EAPoL start packet.
NAC Agentless Host Auditing Process
A NAC agentless host (NAH) refers to a host that does not have a posture agent installed. These hosts cannot fully participate in the NAC solution. If the NAC solution cannot communicate with the host or no exception is made, the host cannot access the network when attempting to connect to NAC-enabled NADs. If your network has been configured for NAC-L2-IP or NAC-L3-IP mode with an auditing solution, NAC might be able to use agentless auditing in situations where an IP host does not, or cannot, run a NAC posture agent. As of this writing, only NAC-L2-IP and NAC-L3-IP modes support agentless auditing because auditing can only take place over an IP session. Auditing of a host can take place using two separate methods: an active network scan and a URL redirection.
As shown in Figure 2-9, an audit server can be part of the NAC posture evaluation process.
Figure 2-9 Audit Server Network Scanning
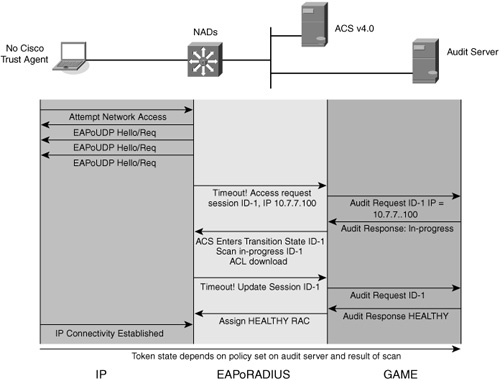
Audit of a host attempting network access using the network-scanning method begins after three unanswered EoU hello request packet attempts from the NAD. The NAD then sends an agentless request to ACS that triggers an audit request to the audit server. ACS periodically checks the audit server to determine the state of the audit session. When the audit is complete, the audit server responds with a token that represents the condition of the host. At that time, ACS sends the appropriate access rights and any enforcement necessary to the NAD.
As shown in Figure 2-10, the auditing process can also be triggered by the host being assigned a URL redirect to the auditing server.
Figure 2-10 Audit Server URL Redirection and Applet Load
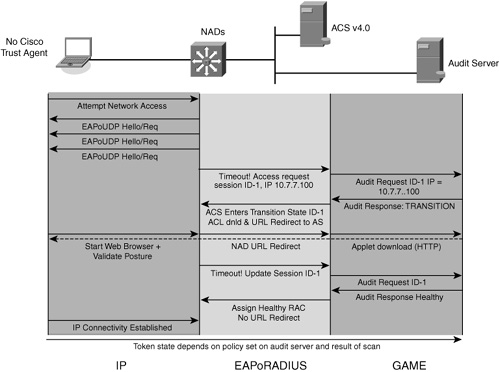
Again, after three successive unanswered EOU hello packets, this time, ACS can send a URL redirection action to the NAD. After opening the browser, the user is redirected to the audit scanner's page, where an applet download occurs and the scanning takes place. ACS temporarily assigns a transition token to the host and configures the NAD to permit audit server access only to the host. The user must manually open his browser to complete the scanning in this scenario because Cisco Trust Agent is not present on the host. ACS checks the progress of the audit in a similar fashion as the network-scanning method. After the scan completes, ACS uses the results to enforce the appropriate access policy.
Authorization and Enforcement Methods
As a result of a successful validation, NAC takes some type of enforcement action. A successful validation is one where the validation process has completed. This does not mean that the host was validated into a healthy state, only that some state was returned to the host and to the NAD and that the EAP session completed successfully. This successful EAP session is known as a successful authentication and is logged in the ACS successful authentication logs, regardless of posture.
The enforcement action is necessary if the host is to have access rights other than what are provided to the host by default. In many cases, the host can be isolated until some access right or enforcement action is sent to the NAD. These enforcement actions vary depending on the mode in which NAC is operating. Although this might change in the future, at the time of this writing, NAC enforcement is implemented in the following ways:
- For IP mode either NAC-L2-IP or NAC-L3-IP, the enforcement action consists of a downloadable ACL to the NAD and optionally a URL redirection.
- For NAC-L2-802.1X mode, VLAN assignment is used as an enforcement action.
The following sections describe each of these enforcement actions.
ACL Types
One of the primary enforcement methods that NAC uses is that of an ACL on a specific host as a result of a validation. The enforcement action uses a downloadable ACL from ACS to limit IP addresses through the NAD interface that services the host. The ACLs differ in name depending on where they are placed as well as the type of port that is used.
An ACL can consist of one of the following two types in NAC:
- Standard ACL—Includes a destination address only.
- Extended ACL—Includes a source address, optional source ports, and destination address and destination ports. In NAC Framework, the extended ACL is most often used in the enforcement action.
The following sections describe the different types of ACLs used by NAC Framework.
PACL
A port access control list (PACL) is an ACL that has been applied on the port of a switch. This switch port can be operating as a network layer interface or as a normal switch port. PACLs work the same as ACLs on router ports.
RACL
A router access control list (RACL) is a specific name for an ACL applied on a router interface. When an ACL is applied on a router interface as a result of enforcement action by the NAC solution, the router replaces the source address in the ACL entries with the source address of the host that this ACL is being applied against. This customizes the enforcement action for that host (and that host only).
VACL
A VLAN access control list (VACL) is an ACL that has been applied on a VLAN in a switch acting as a NAD. Because VLAN ACLs are applied to traffic entering as well as exiting the VLAN, these ACLs need to be written to permit traffic bidirectionally. An example would be to permit a host of 10.1.1.1 as the source address in an ACL entry and also as the destination is a separate entry in the same ACL.
VLANs and Policy-Based ACLs (PBACLs)
Specific to NAC-L2-802.1X mode employing the Catalyst 6500 platform as a NAD, VLAN assignment with assignment to a security policy group can be taken. A security policy group, also called a policy-based ACL (PBACL), is an access list that uses a group as part of the ACL entry. An example would be "permit group quarantine 10.1.1.1." This security policy group assignment uses a Cisco vendor-specific RADIUS attribute "sec:pg" for assignment. When combined with a VLAN assignment, the PBACL can further limit the network resources available to a host. Note that provisioning for bidirectionality must be made for PBACLs just as it has been made for VLAN ACLs.
Cisco Trust Agent and Posture Plug-in Actions
An action can also be taken by the posture agent (Cisco Trust Agent) or posture plug-ins as a result of a validation. As part of the enforcement configuration, Cisco Trust Agent can receive instructions to display a message as part of a completed validation; it can also receive a notification string. This causes Cisco Trust Agent to start the default browser on the host and open it to the page listed in the notification string. This URL could be the page of a remediation server or a page giving the user more instructions about how she should complete the remediation process necessary on her host. Various posture plug-ins have specific actions that are unique to their capabilities and vary by NAC vendors. Some examples of actions are to initiate scanning of the files on a host and to initiate an upgrade of files for that particular posture plug-in.
NAH and Exception Handling
You learned about the network auditing method for handling NAHs earlier in this chapter in the "NAC Agentless Host Auditing Process" section.
Several other methods exist that can handle hosts with no ability to participate in the NAC Framework solution. One of these is the use of a static exception. A static exception is simply the presence of the IP address, the MAC address, or the device type in a NAD configuration. This exempts those particular hosts from participating in NAC. Part of the configuration for a static exception includes the specific access rights for the exempted hosts.
Agentless hosts can also be handled with MAC Authentication Bypass (MAB). MAB consists of a list of MAC addresses that have been configured in ACS that should not be subject to the NAC validation and enforcement process. The operational details and a configuration description for MAB is covered in Chapter 5, "NAC Layer 2 Operations."
Summary
NAC Framework is a solution that allows a network administrator to leverage the investment already made in a network infrastructure to provide additional protection and enforcement of network security policies. Compliance of network endpoints is validated prior to allowing those endpoints to communicate with network resources.
The three NAC Framework modes of operations are NAC-L3-IP, NAC-L2-IP, and NAC-L2-802.1X. The type of port on a network device determines the mode available as well as the NAC triggering process, types of protocol, and enforcement method used.
A posture token classifies hosts into one of several different states that represent the host's relative health on the network. Policy servers can check more than one attribute, resulting in an application posture token being assigned. The worst, or most restrictive, of all the application posture tokens becomes the system posture token.
Hosts that are not in compliance with the network access policy can be forced to complete the remediation process through a variety of enforcement methods.
Hosts that do not have Cisco Trust Agent installed are called NAC agentless hosts. You have choices as to how to handle them, as follows:
- You can configure the NAD to exempt the host from the NAC process by means of a static IP address if operating in NAC-L2-IP or NAC-L3-IP mode or by device type.
- You can configure the ACS to exempt the host from the NAC process by means of a MAC address if operating in NAC-L2-802.1X mode.
- You can redirect the NAH to an audit server to scan and determine whether the host is compliant. Then communicate the decision to ACS to determine the admission policy and actions the NAD will enforce on the host. This is an option when operating in NAC-L2-IP or NAC-L3-IP mode.
- You can do no provisioning for hosts or endpoints without Cisco Trust Agent. The result is that the NAH fails authorization and network access is denied.
Resource
"All About NAC" from Networkers 2005, http://wwwin.cisco.com/Mkt/events/nw/2005/post/presos/docs/TECSEC-112.ppt.
Review Questions
You can find the answers to the review questions in Appendix A.
1 Match the NAC protocol to its function:
a EoU
b HCAP
c GAME
d EAPo802.1X
__ Uses IEEE MAC frame
__ Uses port 21862
__ Queries the PVS
__ Queries an audit server
2 Which of the following are EAP packets types? Choose all that apply.
a Request and response
b Hello and acknowledge
c Request and acknowledge
d Success and failure
3 Which protocol is available for communication of the host credentials to security vendor policy validation servers?
a GAME
b HCAP
c ACS
d RADIUS
4 Which Cisco Trust Agent:Cisco:Host credential attributes can be evaluated by a NAC policy? Choose all that apply.
a Service packs
b Hot fixes
c OS-Version
d Protection-Enabled
5 Which of the following methods can trigger the NAC process for a host connecting to a NAD that uses the NAC-L2-802.1X mode? Choose all that apply.
a Any IP traffic
b DHCP snooping
c EAPoL-Start
d Ethernet linkup signal from the host
e Dynamic ARP inspection
6 Which two methods can trigger the NAC process for a host connecting to a NAD that uses the NAC-L2-IP mode?
a Any IP traffic
b DHCP snooping
c EAPoL-Start
d Ethernet linkup signal from the host
e ARP inspection
7 Which method can trigger the NAC process for a host connecting to a NAD that uses the NAC-L3-IP mode?
a Any IP traffic
b DHCP snooping
c EAPoL-Start
d Ethernet linkup signal from the host
e Dynamic ARP inspection
8 Which of the following defines the situation where the NAD challenges a host to make sure that nothing has changed since the validation process?
a Revalidation
b Status query
c Posture validation
d EAP identity response
9 Which techniques can be used to permit a network printer onto a NAC-protected subnet, even though it is not NAC capable? Choose all that apply.
a Include the printer's MAC in the NAD exception table.
b Include the printer's static IP address in the NAD exception table.
c Include the printer's device type "printer" in the NAD or ACS NAC exception table.
d Use an audit server to scan and validate the printer.
10 Which posture token is assigned to a host when it has not fully booted up and some services have not yet started?
a Checkup
b Unknown
c Transition
d Quarantine
11 Which of the following APTs does ACS decide to use as the SPT and take action against?
Quarantine—Cisco Trust Agent host from local ACS check
Healthy—Cisco Trust Agent PA from local ACS check
Checkup—CSA from local ACS check
Checkup—Antivirus client from vendor PVS
a Both checkup and quarantine actions
b Checkup actions, because two exist
c Quarantine action only
d ACS defers action to antivirus client's PVS
12 Which two methods can be used to audit an agentless host?
a Exception table
b MAC Authentication Bypass
c Network scan
d URL redirection to an audit server
13 Which NAC Framework component causes a user's browser to pop up with the URL redirect from the notification string?
a Posture plug-in agent
b NAD
c Cisco Trust Agent
d Audit server
14 Which of the following ACLs is used for enforcement by routers serving as NADs?
a VACL
b PACL
c RACL
d PBACL
