Chapter Nine
220-1102 Practice Exam C
Let’s turn up the heat a bit more. The previous 220-1102 exam is an intermediate test. This third and final 220-1102 test could be considered an advanced practice test. A large percentage of the questions have a higher difficulty rating. Be ready for questions with longer, more in-depth scenarios and more complex answers.
If you haven’t taken a break already, I suggest taking one between exams. If you just completed the second exam, give yourself a half hour or so before you begin this one. If you didn’t score 90% or higher on exam B, study some more and then retake exam B until you pass with a 90% or higher score.
Write down your answers and check them against the Quick-Check Answer Key, which immediately follows the exam. After the answer key, you will find the explanations for all of the answers. Good luck!
Practice Questions
1. You work as a technician for an organization that has a custom web-based application that is used for the monitoring of networking devices. While using a web browser to access the application, you press F12, and within the js folder, you see the following code:
$(function() {
// Attach collapsible behavior to select options(
function()
{
. var selects = $('select[data-
toggle="collapse"]');Which of the following script types is this?
![]() A. Python
A. Python
![]() B. PowerShell
B. PowerShell
![]() C. Bash
C. Bash
![]() D. JavaScript
D. JavaScript
![]() E. Visual Basic Script
E. Visual Basic Script
Quick Answer: 248
Detailed Answer: 249
2. Viruses have been detected and removed on a customer’s computer several times over the course of several weeks. Which of the following methods will best help prevent future occurrences?
![]() A. Delete temporary files, cookies, and browser history.
A. Delete temporary files, cookies, and browser history.
![]() B. Defragment the hard drive.
B. Defragment the hard drive.
![]() C. Install antivirus software that uses manual updates.
C. Install antivirus software that uses manual updates.
![]() D. Discuss safer web browsing habits with the customer.
D. Discuss safer web browsing habits with the customer.
Quick Answer: 248
Detailed Answer: 249
3. Which of the following sends an invitation by email asking for help?
![]() A. Remote Desktop Connection
A. Remote Desktop Connection
![]() B. Service call
B. Service call
![]() C. VNC
C. VNC
![]() D. Remote Assistance
D. Remote Assistance
Quick Answer: 248
Detailed Answer: 249
4. When you are performing a clean Windows installation, which of the following is the default location for the Windows system files?
![]() A. C:Windows
A. C:Windows
![]() B. C:WindowsSystem32Config
B. C:WindowsSystem32Config
![]() C. C:WindowsSystem32
C. C:WindowsSystem32
![]() D. C:System Files
D. C:System Files
Quick Answer: 248
Detailed Answer: 250
5. You are required to set up a remote backup solution for music and photos stored on an Android tablet. The files cannot be stored at any company location. Which technology should be used?
![]() A. iCloud
A. iCloud
![]() B. Google Cloud
B. Google Cloud
![]() C. Microsoft OneDrive
C. Microsoft OneDrive
![]() D. Local NAS device
D. Local NAS device
Quick Answer: 248
Detailed Answer: 250
6. You have been contracted to repair a computer at an organization that has strict rules about information leaving the premises. While troubleshooting the computer, you determine that the computer should be taken offsite to complete the repair. Which of the following should you do next?
![]() A. Get authorization from your manager.
A. Get authorization from your manager.
![]() B. Delete proprietary information before leaving the building.
B. Delete proprietary information before leaving the building.
![]() C. Check corporate policies for guidance.
C. Check corporate policies for guidance.
![]() D. Remove the HDD and send the computer for repair.
D. Remove the HDD and send the computer for repair.
Quick Answer: 248
Detailed Answer: 250
7. You need to copy and paste information from a web page, but you want to remove all formatting so that the information can be pasted cleanly into Word. Which program should be used as an intermediary?
![]() A. CMD
A. CMD
![]() B. Excel
B. Excel
![]() C. Notepad
C. Notepad
![]() D. MMC
D. MMC
Quick Answer: 248
Detailed Answer: 250
8. A computer is responding slowly, and the Windows Task Manager shows that spoolsv.exe is using 95% of system resources. Which of the following is most likely the cause of this problem?
![]() A. Windows Update is running.
A. Windows Update is running.
![]() B. A virus infection has occurred.
B. A virus infection has occurred.
![]() C. Hyper-Threading has been disabled.
C. Hyper-Threading has been disabled.
![]() D. The printing subsystem is failing.
D. The printing subsystem is failing.
Quick Answer: 248
Detailed Answer: 251
9. Which of the following describes the protocol IMAP?
![]() A. A protocol that allows real-time messaging
A. A protocol that allows real-time messaging
![]() B. An email protocol that allows users to selectively download messages
B. An email protocol that allows users to selectively download messages
![]() C. An email protocol that allows users to send but not receive messages
C. An email protocol that allows users to send but not receive messages
![]() D. A protocol that authenticates users who are sending email
D. A protocol that authenticates users who are sending email
Quick Answer: 248
Detailed Answer: 251
10. From which of the following locations could you disable a hardware component on a laptop in Windows?
![]() A. Device Manager
A. Device Manager
![]() B. Task Manager
B. Task Manager
![]() C. File Explorer
C. File Explorer
![]() D. Services console
D. Services console
Quick Answer: 248
Detailed Answer: 251
11. A customer browses to a company’s intranet page and receives an invalid certificate message. After analysis, you discover that the certificate has expired. You install a new certificate on the user’s computer. However, the user still receives the same message when going to the intranet page. You try again with a different web browser, and it connects without error. You figure out that you need to make sure the old certificate is no longer used in the browser. Which of the following Internet Options settings should you use to ensure that the old certificate is removed?
![]() A. Certificates
A. Certificates
![]() B. Advanced
B. Advanced
![]() C. Clear SSL State
C. Clear SSL State
![]() D. Publishers
D. Publishers
Quick Answer: 248
Detailed Answer: 251
12. Users are reporting to you that a Windows feature asks them for confirmation before running certain applications or when making system changes. What is the name of this Windows feature, and where should you direct users to turn off the functionality?
![]() A. Security Center; it can be turned off in the Services console window.
A. Security Center; it can be turned off in the Services console window.
![]() B. User Account Control; it can be turned off under Security in the Control Panel.
B. User Account Control; it can be turned off under Security in the Control Panel.
![]() C. Windows Defender Firewall; it can be turned off under System Properties.
C. Windows Defender Firewall; it can be turned off under System Properties.
![]() D. User Account Control; it can be turned off under User Accounts in the Control Panel.
D. User Account Control; it can be turned off under User Accounts in the Control Panel.
Quick Answer: 248
Detailed Answer: 252
13. You are a LAN administrator in charge of printers. Which of the following should you check first when a Windows user is trying to print a document and gets the error message “Print sub-system not available”?
![]() A. The correct printer driver is installed.
A. The correct printer driver is installed.
![]() B. The printer has been added.
B. The printer has been added.
![]() C. The spooler service is running.
C. The spooler service is running.
![]() D. The printer has power from the jack.
D. The printer has power from the jack.
Quick Answer: 248
Detailed Answer: 252
14. Your manager’s Windows computer locks up after the graphical user interface starts to load. However, the computer will boot in Safe Mode. When you access the Event Viewer, you see an entry stating that a driver failed. Which of the following steps will help you further diagnose the problem?
![]() A. Run sigverif.
A. Run sigverif.
![]() B. Enable Boot Logging and then, in Safe Mode, analyze the ntbtlog.txt file.
B. Enable Boot Logging and then, in Safe Mode, analyze the ntbtlog.txt file.
![]() C. Disable Driver Signature Enforcement.
C. Disable Driver Signature Enforcement.
![]() D. Access Debugging Mode.
D. Access Debugging Mode.
Quick Answer: 248
Detailed Answer: 252
15. Which of the following commands is used to fix errors on the system disk?
![]() A. robocopy
A. robocopy
![]() B. tracert /w
B. tracert /w
![]() C. diskpart
C. diskpart
![]() D. chkdsk /F
D. chkdsk /F
Quick Answer: 248
Detailed Answer: 253
16. You are troubleshooting a computer that has a web browser issue. The end user says that multiple browser pages open by themselves when she surfs the Internet. Also, you observe that the computer is running slowly. Which of the following actions should you perform first?
![]() A. Install anti-malware software.
A. Install anti-malware software.
![]() B. Update antivirus definitions.
B. Update antivirus definitions.
![]() C. Reboot the computer.
C. Reboot the computer.
![]() D. Enable a pop-up blocker.
D. Enable a pop-up blocker.
Quick Answer: 248
Detailed Answer: 253
17. A new program is crashing and causing the computer to lock up. What is the best location to check for further information about the cause of the crash?
![]() A. System log
A. System log
![]() B. Security log
B. Security log
![]() C. Application log
C. Application log
![]() D. Setup log
D. Setup log
Quick Answer: 248
Detailed Answer: 253
18. You are tasked with disabling services from starting on a Windows PC. Which command should be run to bring up a window to make these changes?
![]() A. sfc
A. sfc
![]() B. chkdsk
B. chkdsk
![]() C. msconfig
C. msconfig
![]() D. gpupdate
D. gpupdate
Quick Answer: 248
Detailed Answer: 253
19. You are tasked with creating a laptop naming convention that will make a customer’s laptops easier to track and identify while in use. Which of the following naming conventions should you use?
![]() A. Asset ID and MAC address
A. Asset ID and MAC address
![]() B. Location and RFID
B. Location and RFID
![]() C. Domain name, location, and asset ID
C. Domain name, location, and asset ID
![]() D. Domain name, location, and IP address
D. Domain name, location, and IP address
Quick Answer: 248
Detailed Answer: 253
20. One of your customers has a wireless network that is secured with WPA. The customer wants to improve data encryption so that the transmission of data has less chance of being compromised. Which of the following statements best describes the recommended course of action?
![]() A. Reconfigure the network to use WPA3.
A. Reconfigure the network to use WPA3.
![]() B. Use MAC address filtering.
B. Use MAC address filtering.
![]() C. Modify the WPA key every week.
C. Modify the WPA key every week.
![]() D. Disable the SSID broadcast.
D. Disable the SSID broadcast.
![]() E. Install WEP.
E. Install WEP.
Quick Answer: 248
Detailed Answer: 254
21. Which of the following commands is used to display hidden files?
![]() A. dir /o
A. dir /o
![]() B. dir /a
B. dir /a
![]() C. dir /d
C. dir /d
![]() D. dir /?
D. dir /?
Quick Answer: 248
Detailed Answer: 254
22. After you install a new video card, the PC loads Windows and continuously reboots. Which of the following statements best describes your first course of action?
![]() A. Go into Safe Mode.
A. Go into Safe Mode.
![]() B. Run chkdsk.
B. Run chkdsk.
![]() C. Run the System Configuration utility.
C. Run the System Configuration utility.
![]() D. Check the System log.
D. Check the System log.
Quick Answer: 248
Detailed Answer: 254
23. Which of the following statements best describes how to prepare a mobile device to be protected in the event that it is stolen or lost? (Select the three best answers.)
![]() A. Disable Bluetooth.
A. Disable Bluetooth.
![]() B. Configure remote backup.
B. Configure remote backup.
![]() C. Enable Wi-Fi encryption.
C. Enable Wi-Fi encryption.
![]() D. Enable GPS.
D. Enable GPS.
![]() E. Enable Wi-Fi tethering.
E. Enable Wi-Fi tethering.
![]() F. Configure a pattern screenlock.
F. Configure a pattern screenlock.
Quick Answer: 248
Detailed Answer: 255
24. Two accounting coworkers share the same file inside a folder. User A works on the file, makes changes, and saves the file. User B then works on the file, makes changes, and saves the file as well. The next time User A attempts to open the file, she receives an “access denied” error. Which of the following statements best describes the most likely cause of this error message?
![]() A. The NTFS permissions were changed on the file to allow only execute.
A. The NTFS permissions were changed on the file to allow only execute.
![]() B. The file was set with the system and hidden attributes.
B. The file was set with the system and hidden attributes.
![]() C. The file was set to read-only by the accounts receivable administrator.
C. The file was set to read-only by the accounts receivable administrator.
![]() D. The file was moved before being modified and then moved back to the share.
D. The file was moved before being modified and then moved back to the share.
Quick Answer: 248
Detailed Answer: 255
25. A customer calls you, reporting that a computer is experiencing the following problems:
![]() Random slowness during the day
Random slowness during the day
![]() Intermittent BSODs
Intermittent BSODs
![]() Random screensaver activation
Random screensaver activation
Which Windows tool should you use to analyze the computer?
![]() A. Task Manager
A. Task Manager
![]() B. Event Viewer
B. Event Viewer
![]() C. Top
C. Top
![]() D. Performance Monitor
D. Performance Monitor
Quick Answer: 248
Detailed Answer: 255
26. Which of the following are the best options for securing a data center? (Select the two best answers.)
![]() A. Bollard
A. Bollard
![]() B. Badge reader
B. Badge reader
![]() C. Cable lock
C. Cable lock
![]() D. USB-based hardware token
D. USB-based hardware token
![]() E. Biometric lock
E. Biometric lock
![]() F. Privacy shade
F. Privacy shade
Quick Answer: 248
Detailed Answer: 256
27. Which of the following is the best Windows utility to use if an administrator wants to perform administrative tasks that integrate scripts over a network?
![]() A. PowerShell
A. PowerShell
![]() B. Command Prompt
B. Command Prompt
![]() C. Mission Control
C. Mission Control
![]() D. Bash
D. Bash
Quick Answer: 248
Detailed Answer: 256
28. You are working in the console of a Linux server. What command should you type to find out the type of file system used by the server’s storage drives?
![]() A. diskpart
A. diskpart
![]() B. rm
B. rm
![]() C. df -T
C. df -T
![]() D. pwd
D. pwd
Quick Answer: 248
Detailed Answer: 256
29. Which of the following file systems is suited specifically for USB flash drives?
![]() A. FAT32
A. FAT32
![]() B. exFAT
B. exFAT
![]() C. NTFS
C. NTFS
![]() D. ext4
D. ext4
Quick Answer: 248
Detailed Answer: 256
30. A program has been found to be collecting information such as the computer name and IP address and sending that information to a specific IP address on the Internet. Which kind of threat is this an example of?
![]() A. Spyware
A. Spyware
![]() B. Virus
B. Virus
![]() C. Rootkit
C. Rootkit
![]() D. Spam
D. Spam
Quick Answer: 248
Detailed Answer: 257
31. You are required to stop the Windows Defender Firewall service. Which of the following best describes how to accomplish this? (Select the three best answers.)
![]() A. In Performance Monitor
A. In Performance Monitor
![]() B. With the net stop mpssvc command
B. With the net stop mpssvc command
![]() C. Within MSConfig
C. Within MSConfig
![]() D. Within the Task Manager
D. Within the Task Manager
![]() E. In System Information
E. In System Information
![]() F. With gpedit.exe
F. With gpedit.exe
![]() G. In services.msc
G. In services.msc
Quick Answer: 248
Detailed Answer: 257
32. You spill a chemical on your hands. It does not appear to be life threatening. Which of the following statements best describes the recommended course of action?
![]() A. Call 911.
A. Call 911.
![]() B. Call the building supervisor.
B. Call the building supervisor.
![]() C. Consult the MSDS for the chemical.
C. Consult the MSDS for the chemical.
![]() D. Ignore it.
D. Ignore it.
Quick Answer: 248
Detailed Answer: 257
33. Which command allows a user to change a file’s permissions in Linux?
![]() A. chown
A. chown
![]() B. passwd
B. passwd
![]() C. ls
C. ls
![]() D. chmod
D. chmod
Quick Answer: 248
Detailed Answer: 257
34. While you are working on a computer at a customer’s home, the customer informs you that he needs to leave for about 10 minutes and that his eight-year-old son can help you with anything, if you need it. Which of the following statements best describes the recommended course of action?
![]() A. Tell the customer to get back home as soon as possible.
A. Tell the customer to get back home as soon as possible.
![]() B. Tell the customer that you are not responsible for the child.
B. Tell the customer that you are not responsible for the child.
![]() C. Tell the customer that an adult must be home while you work.
C. Tell the customer that an adult must be home while you work.
![]() D. Tell the customer that the child must be removed.
D. Tell the customer that the child must be removed.
Quick Answer: 248
Detailed Answer: 257
35. You have encountered a previously unidentified customer issue. Being awesome, you fix the problem! Now, you are ready to close out the ticket. However, one thing remains. Which system should you access?
![]() A. Bluetooth PAN
A. Bluetooth PAN
![]() B. Knowledge base
B. Knowledge base
![]() C. Asset management system
C. Asset management system
![]() D. IoT screened subnet
D. IoT screened subnet
Quick Answer: 248
Detailed Answer: 258
36. You have been asked to recommend an anti-malware program for a home user. However, the user does not want to pay for a license. Which of the following should you suggest?
![]() A. Personal license
A. Personal license
![]() B. Corporate license
B. Corporate license
![]() C. Open license
C. Open license
![]() D. Enterprise license
D. Enterprise license
Quick Answer: 248
Detailed Answer: 258
37. A customer experiences a server crash. When you arrive, the manager is upset about this problem. Which of the following statements best describes the recommended course of action?
![]() A. Stay calm and do the job as efficiently as possible.
A. Stay calm and do the job as efficiently as possible.
![]() B. Take the customer out for a cup of coffee.
B. Take the customer out for a cup of coffee.
![]() C. Avoid the customer and get the job done quickly.
C. Avoid the customer and get the job done quickly.
![]() D. Refer the customer to your supervisor.
D. Refer the customer to your supervisor.
Quick Answer: 248
Detailed Answer: 258
38. You complete a difficult repair of a laptop for a customer. The next day, the customer complains that the repair took too long and questions the steps you took to fix the problem. Which of the following should you do next?
![]() A. Record the customer’s concerns and post them to your organization’s social media page.
A. Record the customer’s concerns and post them to your organization’s social media page.
![]() B. Inform the customer that the job has been completed and refer the customer to your supervisor.
B. Inform the customer that the job has been completed and refer the customer to your supervisor.
![]() C. Verbally defend each step you took and why it was necessary.
C. Verbally defend each step you took and why it was necessary.
![]() D. Provide documentation of the repair to the customer.
D. Provide documentation of the repair to the customer.
Quick Answer: 248
Detailed Answer: 258
39. As you are servicing a manager’s PC at your company, you run across a list of names of employees who are supposedly about to be let go from the company. Some of these people are coworkers of yours. Which of the following statements best describes the recommended course of action?
![]() A. Shred the list.
A. Shred the list.
![]() B. Act as if you never saw the list.
B. Act as if you never saw the list.
![]() C. In secret, tell everyone who was on the list.
C. In secret, tell everyone who was on the list.
![]() D. Yell at the manager for having that list out where it can be seen.
D. Yell at the manager for having that list out where it can be seen.
Quick Answer: 248
Detailed Answer: 259
40. Which macOS graphical utility is most like the Windows “end task” feature?
![]() A. Time Machine
A. Time Machine
![]() B. Finder
B. Finder
![]() C. kill 3035
C. kill 3035
![]() D. Force quit
D. Force quit
Quick Answer: 248
Detailed Answer: 259
41. Which of the following statements best describes how to reduce the chance of ESD? (Select the three best answers.)
![]() A. Use an antistatic strap.
A. Use an antistatic strap.
![]() B. Use an antistatic mat.
B. Use an antistatic mat.
![]() C. Raise the temperature.
C. Raise the temperature.
![]() D. Raise the humidity.
D. Raise the humidity.
![]() E. Lower the humidity.
E. Lower the humidity.
![]() F. Work in a carpeted area.
F. Work in a carpeted area.
Quick Answer: 248
Detailed Answer: 259
42. While you explain a technical concept to a customer, which of the following statements best describes the recommended course of action?
![]() A. Recommend a training class.
A. Recommend a training class.
![]() B. Sit next to the customer.
B. Sit next to the customer.
![]() C. Use acronyms so that the customer feels comfortable about your knowledge.
C. Use acronyms so that the customer feels comfortable about your knowledge.
![]() D. Tell the customer to read the manual.
D. Tell the customer to read the manual.
Quick Answer: 248
Detailed Answer: 260
43. You are viewing the output of ipconfig /all on a Windows computer. You see the name dpro42.com toward the beginning of the results. Which type of network is this Windows computer most likely a part of?
![]() A. Workgroup
A. Workgroup
![]() B. SAN
B. SAN
![]() C. Domain
C. Domain
![]() D. VPN
D. VPN
Quick Answer: 248
Detailed Answer: 260
44. Which of the following should be used to clean a monitor’s screen when you are not sure how to do so?
![]() A. Isopropyl alcohol
A. Isopropyl alcohol
![]() B. Mild detergent
B. Mild detergent
![]() C. Water
C. Water
![]() D. Boric acid
D. Boric acid
Quick Answer: 248
Detailed Answer: 260
45. A customer tells you that he has difficulty remembering the dozen different sets of credentials for the various banks, online stores, and other websites that he logs into. Which of the following should you recommend to the customer?
![]() A. Trusted sources
A. Trusted sources
![]() B. Hashing
B. Hashing
![]() C. Password manager
C. Password manager
![]() D. Secure certificates
D. Secure certificates
Quick Answer: 248
Detailed Answer: 260
46. As part of risk management for your company, you have been tasked with backing up three physical servers on a daily basis. These backups will be stored to a NAS device on the LAN. Which of the following can you do to make sure the backup will work when needed?
![]() A. Create alerts to let the administrators know when backups fail.
A. Create alerts to let the administrators know when backups fail.
![]() B. Set up scripts to automatically rerun failed backup jobs.
B. Set up scripts to automatically rerun failed backup jobs.
![]() C. Store copies of the backups offsite at a data center.
C. Store copies of the backups offsite at a data center.
![]() D. Frequently restore the servers from the backup files and test them.
D. Frequently restore the servers from the backup files and test them.
![]() E. Configure the backups to restore to VMs for rapid recovery.
E. Configure the backups to restore to VMs for rapid recovery.
Quick Answer: 248
Detailed Answer: 261
47. You have an Intel Core i7 system with a UEFI-enabled motherboard. Which of the following types of storage drive partitioning schemes should be selected when installing Windows?
![]() A. MBR
A. MBR
![]() B. FAT32
B. FAT32
![]() C. Dynamic drive
C. Dynamic drive
![]() D. GPT
D. GPT
Quick Answer: 248
Detailed Answer: 261
48. Which of the following statements best describes the recommended course of action to take prior to attempting to remediate infected Windows systems of malware?
![]() A. Educate the end user.
A. Educate the end user.
![]() B. Disable System Restore.
B. Disable System Restore.
![]() C. Schedule scans.
C. Schedule scans.
![]() D. Update the anti-malware program.
D. Update the anti-malware program.
Quick Answer: 248
Detailed Answer: 261
49. A customer’s mobile device cannot connect to Wi-Fi. According to the customer, it was working fine yesterday. Troubleshoot! Which of the following statements best describes the recommended course of action? (Select the three best answers.)
![]() A. Power cycle the device.
A. Power cycle the device.
![]() B. Re-pair the device.
B. Re-pair the device.
![]() C. Perform a hard reset.
C. Perform a hard reset.
![]() D. Forget the Wi-Fi network.
D. Forget the Wi-Fi network.
![]() E. Ensure that the correct SSID was entered.
E. Ensure that the correct SSID was entered.
![]() F. Change the IP address.
F. Change the IP address.
Quick Answer: 248
Detailed Answer: 262
50. Which of the following utilities enables a Windows user to edit a file offline and then automatically update the changes when the user returns to the office?
![]() A. Sync Center
A. Sync Center
![]() B. PowerShell
B. PowerShell
![]() C. Windows Defender Firewall
C. Windows Defender Firewall
![]() D. Resource Monitor
D. Resource Monitor
Quick Answer: 248
Detailed Answer: 262
51. A help desk phone support technician is finding it difficult to understand a customer due to a heavy accent. Which of the following statements best describes the first course of action the technician should take to help the customer resolve the problem?
![]() A. Repeat the problem back to the customer.
A. Repeat the problem back to the customer.
![]() B. Have the customer call back at a later time.
B. Have the customer call back at a later time.
![]() C. Ask the customer to not speak with an accent.
C. Ask the customer to not speak with an accent.
![]() D. Tell the customer that her accent is preventing the problem from being solved.
D. Tell the customer that her accent is preventing the problem from being solved.
Quick Answer: 248
Detailed Answer: 262
52. You are acquiring hardware devices and setting up a computer lab that will use virtual desktops. The lab computers need to connect automatically to the remote session upon boot and must be started remotely. Which of the following solutions must the hardware be able to support? (Select the two best answers.)
![]() A. PXE
A. PXE
![]() B. Image deployment
B. Image deployment
![]() C. USB
C. USB
![]() D. Multiboot
D. Multiboot
![]() E. Wake-on-LAN
E. Wake-on-LAN
![]() F. Unattended installation
F. Unattended installation
Quick Answer: 248
Detailed Answer: 262
53. Which of the following will occur if %temp% is executed from Run?
![]() A. Applications located in the %temp% folder will be executed.
A. Applications located in the %temp% folder will be executed.
![]() B. The operating system’s temporary folder will be opened.
B. The operating system’s temporary folder will be opened.
![]() C. The current user’s temporary folder will be opened.
C. The current user’s temporary folder will be opened.
![]() D. Applications will be deleted from the %temp% folder.
D. Applications will be deleted from the %temp% folder.
Quick Answer: 248
Detailed Answer: 263
54. If you want to prevent a home user from being able to install software, to which group should you assign the home user? (Select the best answer.)
![]() A. Administrators
A. Administrators
![]() B. Power Users
B. Power Users
![]() C. Remote Desktop Users
C. Remote Desktop Users
![]() D. Users
D. Users
Quick Answer: 248
Detailed Answer: 263
55. A Windows PC is not booting correctly. You need to locate bad sectors and recover information. Which command is best in this scenario?
![]() A. chkdsk C: /R
A. chkdsk C: /R
![]() B. chkdsk C: /F
B. chkdsk C: /F
![]() C. chkdsk C: /C
C. chkdsk C: /C
![]() D. chkdsk C: /I
D. chkdsk C: /I
Quick Answer: 248
Detailed Answer: 263
56. One of your coworkers has a smartphone that contains PII. Because the data is required for use and is valuable, the coworker cannot have the phone automatically wiped if it is lost or stolen. Which of the following is the best option for securing the device?
![]() A. Passcode
A. Passcode
![]() B. Swipe
B. Swipe
![]() C. PIN
C. PIN
![]() D. Fingerprint
D. Fingerprint
Quick Answer: 248
Detailed Answer: 263
57. A user at your organization is working on an older shared computer and attempts to open the email application, which freezes when it is opened. The user calls you and tells you that the email application is not working. You remote into the computer, log in to it, and open the email application without issue. You ask the user to log back in, but the email application still freezes. You find out that other users of the shared computer do not have any issues with the email application. Which of the following should you do next to fix the problem?
![]() A. Rebuild the user’s mail profile.
A. Rebuild the user’s mail profile.
![]() B. Apply software updates.
B. Apply software updates.
![]() C. Add the user to the local administrators group.
C. Add the user to the local administrators group.
![]() D. Run a repair installation of the email application.
D. Run a repair installation of the email application.
Quick Answer: 248
Detailed Answer: 264
58. A user who is part of a workgroup reports that she cannot print to a new printer. Everyone else in the workgroup can print to the new printer, and the user can still automatically send print jobs to the old printer. Which of the following statements describe how to remedy the problem? (Select the two best answers.)
![]() A. Add the new printer to the user’s computer.
A. Add the new printer to the user’s computer.
![]() B. Clear the print queue on the new printer.
B. Clear the print queue on the new printer.
![]() C. Change the user’s password and permissions.
C. Change the user’s password and permissions.
![]() D. Set the new printer as the default printer.
D. Set the new printer as the default printer.
Quick Answer: 248
Detailed Answer: 264
59. Your organization has an Active Directory domain. One of the users, Bill, should not have read access to a folder named Accounting. The Accounting folder is shared on a network server, on a partition formatted as NTFS. Which of the following statements best describes how to stop Bill from having read access to the folder without impacting any other users on the network?
![]() A. Remove Bill from all domain groups that have access to the Accounting folder.
A. Remove Bill from all domain groups that have access to the Accounting folder.
![]() B. Deny read access to the Accounting folder for Bill through local access security.
B. Deny read access to the Accounting folder for Bill through local access security.
![]() C. Deny read access to the Accounting folder for any group that Bill is a member of.
C. Deny read access to the Accounting folder for any group that Bill is a member of.
![]() D. Deny read access to the Accounting folder for Bill through shared access security.
D. Deny read access to the Accounting folder for Bill through shared access security.
Quick Answer: 248
Detailed Answer: 264
60. Examine the following figure. Then answer the question that follows.
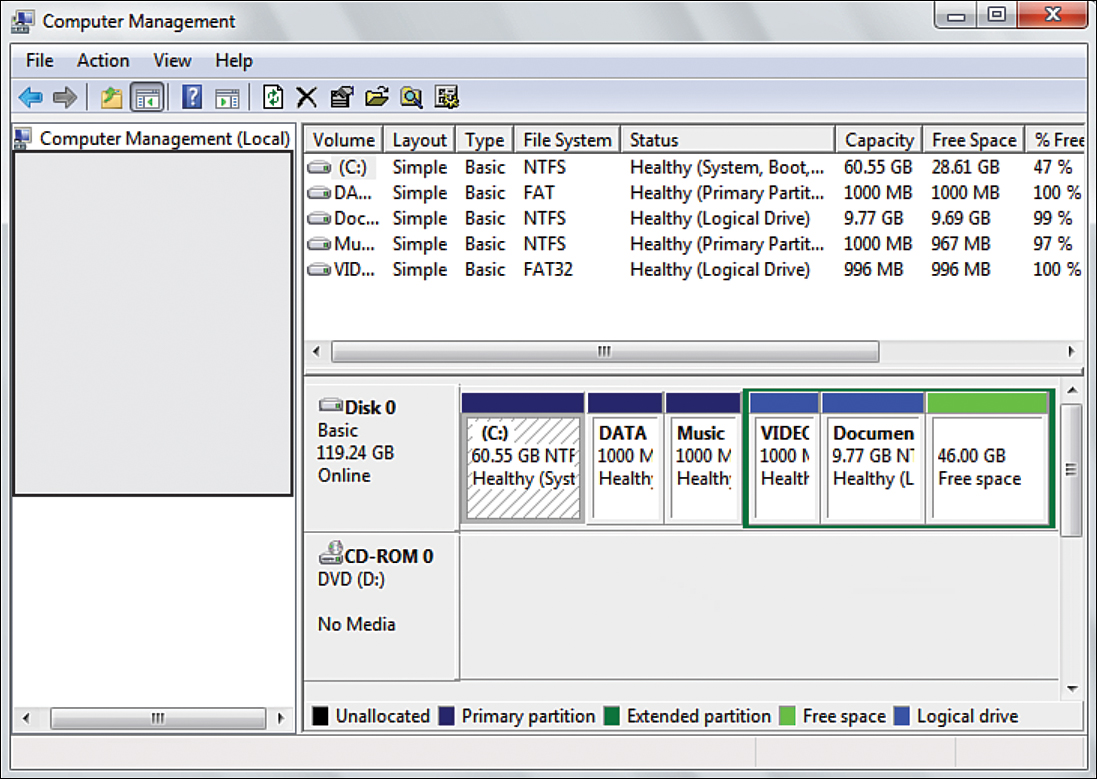
Which portion of Computer Management is displayed in the figure?
![]() A. Event Viewer
A. Event Viewer
![]() B. Disk Management
B. Disk Management
![]() C. gnome-disks
C. gnome-disks
![]() D. diskpart
D. diskpart
Quick Answer: 248
Detailed Answer: 264
61. Which of the following is the best Windows utility for backing up important system settings without requiring external storage?
![]() A. MSConfig
A. MSConfig
![]() B. Task Manager
B. Task Manager
![]() C. System Restore
C. System Restore
![]() D. robocopy
D. robocopy
Quick Answer: 248
Detailed Answer: 265
62. Your boss wants to encrypt a storage drive that will store critical data. Your boss needs to be able to drag and drop folders onto the volume and have them encrypted in real time. Which encryption technique should you suggest?
![]() A. BitLocker
A. BitLocker
![]() B. PKI
B. PKI
![]() C. TPM
C. TPM
![]() D. Kerberos
D. Kerberos
Quick Answer: 248
Detailed Answer: 265
63. Your boss asks you to troubleshoot a computer. Based on his observations, he thinks it might have been infected by some type of malware, but he is not sure. Which of the following statements best describes the first step you should take to remedy the problem?
![]() A. Run System Restore.
A. Run System Restore.
![]() B. Identify the malware.
B. Identify the malware.
![]() C. Roll back drivers.
C. Roll back drivers.
![]() D. Research malware types.
D. Research malware types.
Quick Answer: 248
Detailed Answer: 265
64. User A is part of the Users group on a Windows computer. User A attempts to access files at the following network path: \serverfileshare. The share called fileshare has the following share permissions:
Administrators: Full Control
Users: Read-Only
Guests: No Access
However, the directory on the storage drive where the share is located has the following permissions:
Administrators: Full Control
Users: Change
Guests: No Access
Which level of access will the User A account have?
![]() A. Read-Only
A. Read-Only
![]() B. Change
B. Change
![]() C. Full Control
C. Full Control
![]() D. No Access
D. No Access
Quick Answer: 248
Detailed Answer: 265
65. Your boss wants to implement BitLocker on a second laptop for traveling purposes. Which of the following should be performed before implementing BitLocker?
![]() A. Enable TPM in the BIOS/UEFI.
A. Enable TPM in the BIOS/UEFI.
![]() B. Disable UAC.
B. Disable UAC.
![]() C. Defrag the hard drive.
C. Defrag the hard drive.
![]() D. Convert the file system to NTFS.
D. Convert the file system to NTFS.
Quick Answer: 248
Detailed Answer: 266
66. You need to edit a protected .dll file on a Windows PC, but you cannot find the file you are looking for in the System32 folder. Which of the following Control Panel utilities should you configure?
![]() A. Display
A. Display
![]() B. System
B. System
![]() C. Indexing Options
C. Indexing Options
![]() D. File Explorer Options
D. File Explorer Options
Quick Answer: 248
Detailed Answer: 266
67. The CEO of your company clicked on a malicious email link. As a result, the system was hacked, and a year’s worth of extremely confidential company data was stolen. Which of the following could have possibly prevented this from happening? (Select the two best answers.)
![]() A. AES
A. AES
![]() B. firewall.cpl
B. firewall.cpl
![]() C. AUP
C. AUP
![]() D. User education regarding common threats
D. User education regarding common threats
Quick Answer: 248
Detailed Answer: 266
68. You have been asked to load a copy of the company’s purchased software on a personal computer. Which of the following statements best describes the first step you should take to remedy the problem?
![]() A. Verify that the installation is allowed under the company’s licensing agreements.
A. Verify that the installation is allowed under the company’s licensing agreements.
![]() B. Notify the company’s owner of the breach.
B. Notify the company’s owner of the breach.
![]() C. Advise the individual that downloading unlicensed software is illegal.
C. Advise the individual that downloading unlicensed software is illegal.
![]() D. Leave the premises and call local law enforcement.
D. Leave the premises and call local law enforcement.
Quick Answer: 248
Detailed Answer: 266
69. Your friend is playing the latest first-person game on a PC, but the screen is pausing during game play. Your friend has a high-end graphics card and the maximum memory for the motherboard. Which of the following statements best describes how to remedy the problem?
![]() A. Upgrade the drivers.
A. Upgrade the drivers.
![]() B. Reinstall the OS.
B. Reinstall the OS.
![]() C. Replace the NVMe drive.
C. Replace the NVMe drive.
![]() D. Reinstall the game.
D. Reinstall the game.
Quick Answer: 248
Detailed Answer: 267
70. You have been asked to move data from one user’s laptop to another user’s laptop. Both laptops have EFS functioning. Which of the following statements best describes the first step you should take during this procedure?
![]() A. Give the user of the second laptop administrator privileges.
A. Give the user of the second laptop administrator privileges.
![]() B. Export the user’s certificate.
B. Export the user’s certificate.
![]() C. Disable networking.
C. Disable networking.
![]() D. Convert the partition to FAT32.
D. Convert the partition to FAT32.
Quick Answer: 248
Detailed Answer: 267
71. Which of the following statements is true?
![]() A. Authentication can be something a user knows, such as a smart card.
A. Authentication can be something a user knows, such as a smart card.
![]() B. Authentication can be something a user is, such as a fingerprint.
B. Authentication can be something a user is, such as a fingerprint.
![]() C. Authentication can be something a user does, such as a PIN or password.
C. Authentication can be something a user does, such as a PIN or password.
![]() D. Authentication can be something a user has, such as a signature.
D. Authentication can be something a user has, such as a signature.
Quick Answer: 248
Detailed Answer: 267
72. You are required to implement an organizational policy that states user passwords can’t be used twice in a row. Which of the following policies should be configured?
![]() A. Minimum password length
A. Minimum password length
![]() B. Enforce password history
B. Enforce password history
![]() C. Minimum password age
C. Minimum password age
![]() D. Complexity requirements
D. Complexity requirements
Quick Answer: 248
Detailed Answer: 267
73. You are working on a computer in which you just installed a new storage drive. The system already runs Windows. The new drive does not appear in File Explorer. Which of the following statements best describes the next step you should take to ensure that the drive will be recognized by the operating system?
![]() A. Reboot the computer.
A. Reboot the computer.
![]() B. Initialize and format the drive in Disk Management.
B. Initialize and format the drive in Disk Management.
![]() C. Configure the drive in the BIOS/UEFI.
C. Configure the drive in the BIOS/UEFI.
![]() D. Assign a drive letter to the drive in Disk Management.
D. Assign a drive letter to the drive in Disk Management.
![]() E. Set the drive to active.
E. Set the drive to active.
Quick Answer: 248
Detailed Answer: 268
74. An external attacker is constantly trying to break into one of your customer’s SOHO networks. Which of the following statements best describes the easiest, most practical way to protect the network from intrusion?
![]() A. Disable the SSID broadcast.
A. Disable the SSID broadcast.
![]() B. Install an antivirus server application.
B. Install an antivirus server application.
![]() C. Disconnect the Internet connection.
C. Disconnect the Internet connection.
![]() D. Install a firewall.
D. Install a firewall.
![]() E. Install an IDS.
E. Install an IDS.
Quick Answer: 248
Detailed Answer: 268
75. One of the administrators recently moved a large chunk of data from one server to another. Now, several users are reporting that they cannot access certain data shares and that they get an “access denied” error. The admin confirms that the users are in the proper security groups, but the users are still unable to access the shares. Which of the following are the most likely causes of the problem? (Select the two best answers.)
![]() A. Denied permissions
A. Denied permissions
![]() B. User account time of day restriction
B. User account time of day restriction
![]() C. Mapped drives
C. Mapped drives
![]() D. Administrative share permissions
D. Administrative share permissions
![]() E. Disabled proxy settings
E. Disabled proxy settings
Quick Answer: 248
Detailed Answer: 268
76. You are tasked with formatting an 8 TB external storage drive with a file system. The drive will be connected directly to a computer that dual boots to Windows and Linux. Which file system should you use?
![]() A. exFAT
A. exFAT
![]() B. NFS
B. NFS
![]() C. FAT32
C. FAT32
![]() D. ext4
D. ext4
Quick Answer: 248
Detailed Answer: 269
77. You want to write a PowerShell script that will turn off a remote computer. Which of the following can you use to accomplish this? (Select the two best answers.)
![]() A. stop-computer
A. stop-computer
![]() B. poweroff
B. poweroff
![]() C. kill
C. kill
![]() D. shutdown
D. shutdown
![]() E. restart-computer
E. restart-computer
Quick Answer: 248
Detailed Answer: 269
78. Which switch to the robocopy command copies subdirectories but skips empty ones?
![]() A. /E
A. /E
![]() B. /B
B. /B
![]() C. /S
C. /S
![]() D. /DCOPY:T
D. /DCOPY:T
Quick Answer: 248
Detailed Answer: 269
79. Which of the following are components of dealing with prohibited content? (Select the three best answers.)
![]() A. First response
A. First response
![]() B. Maintaining a positive attitude
B. Maintaining a positive attitude
![]() C. Preserving data
C. Preserving data
![]() D. Creating a chain of custody
D. Creating a chain of custody
![]() E. Avoiding distraction
E. Avoiding distraction
Quick Answer: 248
Detailed Answer: 269
80. You are designing the environmental controls for a server room that contains several servers and other network devices. Which of the following statements best describes the role of an HVAC system in this environment? (Select the two best answers.)
![]() A. It shields equipment from EMI.
A. It shields equipment from EMI.
![]() B. It provides isolation in the event of a fire.
B. It provides isolation in the event of a fire.
![]() C. It provides an appropriate ambient temperature.
C. It provides an appropriate ambient temperature.
![]() D. It maintains appropriate humidity levels.
D. It maintains appropriate humidity levels.
![]() E. It vents fumes from the server room.
E. It vents fumes from the server room.
Quick Answer: 248
Detailed Answer: 270
Quick-Check Answer Key
1. D
2. D
3. D
4. C
5. B
6. C
7. C
8. D
9. B
10. A
11. A
12. D
13. C
14. B
15. D
16. A
17. C
18. C
19. A
20. A
21. B
22. A
23. B, D, and F
24. D
25. B
26. B and E
27. A
28. C
29. B
30. A
31. B, D, and G
32. C
33. D
34. C
35. B
36. C
37. A
38. D
39. B
40. D
41. A, B, and D
42. B
43. C
44. C
45. C
46. A
47. D
48. B
49. A, D, and E
50. A
51. A
52. A and E
53. C
54. D
55. A
56. D
57. A
58. A and D
59. D
60. B
61. C
62. A
63. B
64. A
65. A
66. D
67. C and D
68. A
69. A
70. B
71. B
72. B
73. B
74. D
75. A and C
76. C
77. A and D
78. C
79. A, C, and D
80. C and D
Answers and Explanations
1. Answer: D
Explanation: The snippet of code shown is an example of JavaScript. You can press F12 in a web browser to open the developer tools. Within this sidebar, the Sources section displays the code used by the web page, which often includes HTML, CSS, and JavaScript. For this question, you don’t even need to look at the code because the question states that you are looking in the js folder, which is short for JavaScript. However, you could also tell by the code. For example, $(function() is from jQuery, a library that makes it easy to use JavaScript. Also, var is commonly used in JavaScript; it is a statement that declares a variable. In this example, a table or other data structure is “collapsible,” which means it can be shrunk into a smaller space. So this question might seem complex, but it really isn’t. Remember: The extension .js is normally associated with JavaScript.
Incorrect answers: .py is associated with Python, .ps1 is associated with PowerShell, .sh is associated with Bash and the Terminal (Linux/Unix), and .vbs is associated with Visual Basic Script (or VBScript).
2. Answer: D
Explanation: Because this situation happens often, you should educate the user on safer web browsing habits, such as being very careful when clicking on links brought up by search engines, not clicking on pop-up windows, and being conservative about the websites that are accessed. Also, the browser can be updated, add-ons can be installed to the web browser for increased protection, phishing filters can be enabled, and so on.
Incorrect answers: Deleting temporary files won’t stop the user from visiting the same websites that probably caused the problem in the first place. Defragmenting the hard drive will help the drive and the OS perform better but won’t help in the malware department. The computer should have an antivirus solution or, better yet, an anti-malware solution, and it should be set to update automatically every day.
3. Answer: D
Explanation: Connections can be made by sending Remote Assistance invitations by email. These invitations could ask for help or could offer help. This approach is often implemented in help desk scenarios in which a user invites a technician to take control of his computer so that it can be repaired. It’s effectively a virtual service call. The technician doesn’t need to come physically to the user’s desk but instead connects remotely.
Incorrect answers: You can also take control of a computer without an invitation (if you are an administrator or a user with appropriate permissions); this can be done only if the computer to be controlled has the Remote Desktop feature turned on. Virtual network computing (VNC) is similar to Remote Desktop; it enables control of a computer remotely. Several third-party VNC companies offer free software. Microsoft doesn’t refer to its software as VNC, though. Collectively, the Microsoft client software is referred to as Remote Desktop Services. (Originally, it was called Microsoft Terminal Services Client [MSTSC]. Mstsc.exe is the executable that can also be used in the Command Prompt.)
4. Answer: C
Explanation: The default folder location for Windows system files is C:WindowsSystem32—that is, if C: is the drive being installed to (which is the default). You might also see this referred to as X:\%windir%System32 or simply \%windir%System32. The X: is a variable meaning whichever volume is installed to. %windir% is a variable that refers to the main installation folder (usually Windows). %windir% is also expressed sometimes as %systemroot%.
Incorrect answers: C:Windows is the systemroot, where the OS is installed (although it also inhabits subfolders). C:WindowsSystem32Config is the folder where the registry hives are stored. There is no C:System Files folder, unless you create it yourself.
5. Answer: B
Explanation: You would use the Google Cloud solution so that files can be backed up to a location outside the company. This backup—or full synchronization—method is great for Android-based smartphones and tablets as well as Google Chromebooks. Several other third-party solutions are available as well.
Incorrect answers: iCloud is the Apple solution for backup of files, apps, and so on. Microsoft OneDrive has the same types of features in a variety of solutions. Although there is some crossover between cloud platforms, generally Android users back up to Google Cloud. Using a company-based local network-attached storage (NAS) device would go against what you have been asked to do in the scenario. If the NAS were on the Internet or part of a cloud, however, that would be a different story.
6. Answer: C
Explanation: You should check the company’s policies and procedures first (or inquire with a compliance officer). If there is confidential or proprietary information that should not leave the premises (under normal circumstances), the company guidelines should define what to do in a repair situation.
Incorrect answers: If the computer ultimately does have to leave the premises, you will probably have to obtain authorization and signatures from one or more people who work at the company; this goes beyond your manager, who works at your company, not the company you have been contracted to help. You should never delete any information from computers that you work on unless, of course, doing so is required as part of a storage drive scrub or drive replacement, and the data has been backed up. Removing the drive is not enough; there could be data elsewhere in the computer. Also, repairing a system without a drive can, in many cases, be difficult.
7. Answer: C
Explanation: Use Notepad. This text-based editor applies virtually no formatting. Text and other information can be copied from a web page, pasted to a Notepad document, and then copied again and pasted into Word; all formatting is removed. Notepad (and third-party tools such as Notepad++) can also be used for scripting and web page development.
Incorrect answers: CMD (or, more specifically, cmd.exe) is the executable that opens the Microsoft Command Prompt. Excel is a program from Microsoft that enables you to create and modify spreadsheets. MMC, which stands for Microsoft Management Console, is a utility in Windows that enables you to work with several console windows within the same program; it saves the last place you were working.
8. Answer: D
Explanation: The printing subsystem is most likely failing for one of a variety of reasons. The first solution is to terminate spoolsv.exe (which is the Print Spooler service) in the Task Manager or from the command line with the taskkill command. Then restart the computer. If that approach doesn’t work, the system may have to be repaired, restored, or modified in the registry (which could be an in-depth process). It is also possible that a virus has compromised the system. There are viruses that are also called spoolsv.exe; a quick sweep of the system folders with AV software should uncover this… hopefully.
Incorrect answers: If Windows Update is running, it should not take up nearly that many resources. FYI, the executable for Windows Update is wuauclt.exe. Hyper-Threading can be disabled in the BIOS/UEFI on some systems. This should have no effect on the system’s ability to multitask, though, and multiple processes should be able to run simultaneously without a problem.
9. Answer: B
Explanation: IMAP, which stands for Internet Message Access Protocol, allows an email client to access email on a remote mail server. Generally, the email client software leaves the messages on the server until the user specifically deletes them. So, the user can selectively download messages. This allows multiple users to manage the same mailbox.
Incorrect answers: Real-time messaging can be accomplished by using instant messaging and chat programs. IMAP, like POP3, allows users to download or receive messages, but it does not send messages; a protocol such as SMTP would be used to send mail. IMAP, like POP3, authenticates the user, but again not for sending email—just when receiving email.
10. Answer: A
Explanation: Use Device Manager to disable a component in Windows, regardless of whether it is a laptop or a PC. When you disable a device, a down arrow appears over the icon of the device, next to the name.
Incorrect answers: Use the Task Manager to analyze basic system performance and stop processes. Use File Explorer to view folders, files, and other computers. Use the Services console (services.msc) to stop and start and modify the startup type of services.
11. Answer: A
Explanation: You need the Certificates option. To get to this, go to Control Panel > Internet Options > Content tab. This is where you can remove old browser certificates. This holds true for the older Internet Explorer and Microsoft Edge (as of the writing of this book). You can also access Internet Options in Edge by typing edge://settings in the address bar and searching for “Manage certificates.”
Incorrect answers: The Advanced tab has many options, such as for enabling TLS (1.2 or 1.3) and other security options. Clear SSL State is also in the Content tab of Internet Options. That removes any cached certificates. You can also remove cached certificates by closing the browser or restarting the computer, but these methods won’t remove permanent certificates listed in the Certificates section. Publishers is also available in the Content tab; this is where trusted certificate publishers are listed.
12. Answer: D
Explanation: User Account Control (UAC) is the portion of Windows that asks for confirmation of administrative rights before allowing a user to make system changes or run certain applications. It can be disabled in the User Accounts applet within the Control Panel by clicking the Change User Account Control Settings link. But beware: Only users who have administrative rights should even be permitted to turn off this setting. UAC can be further configured in the Group Policy Editor and in the Registry Editor. For more information about how UAC works, see https://docs.microsoft.com/en-us/windows/security/identity-protection/user-account-control/how-user-account-control-works.
Incorrect answers: UAC is not turned off in the Security Center or with Windows Defender Firewall. It has separate functionality that is built into Control Panel > User Accounts. It cannot be turned off as a service in the Services console window (services.msc), though there is a related service called the Application Information service (using the service name appinfo), which deals with the usage of additional administrative privileges.
13. Answer: C
Explanation: If a “print sub-system not available” or similar message appears, it most likely means the spooler has stalled. You can turn the spooler back on in the Services section of Computer Management or by issuing the command net start spooler in the Command Prompt.
Incorrect answers: If the wrong printer driver was installed, either the user would get a message stating that the printer is not available or the document would print but the information would be garbled. If the printer was not added, the user would not be able to print any documents to any printers and therefore should not get an error message. If the printer was not getting power, the user would most likely get a message stating that the printer is not available.
14. Answer: B
Explanation: Boot Logging can be enabled from the Windows Recovery Environment (WinRE) in Startup Settings. After this option is enabled, the system automatically creates a file called ntbtlog.txt. Afterward, you can access the system by booting into Safe Mode, once again from the Recovery Environment.
Incorrect answers: sigverif is a program that can be run in Windows to verify whether drivers have been signed by Microsoft. Disabling Driver Signature Enforcement is another Startup Settings (WinRE) option; you might use it to help fix the issue but not to diagnose the problem. Debugging Mode is another option. In this scenario, you don’t necessarily need to debug the system, but you should repair the individual driver that failed to load.
15. Answer: D
Explanation: chkdsk /F allows you to fix errors on a disk. It does not fix all errors, but it checks for disk integrity, bad sectors, and similar issues.
Incorrect answers: robocopy copies files and directory trees. tracert /w analyzes the path to another computer with a specific timeout per reply. diskpart is the command-line tool that enables you to make changes to the operating system’s partition table.
16. Answer: A
Explanation: The first thing you should do is install anti-malware software. It would be surprising if the computer doesn’t have any, but it’s a possibility.
Incorrect answers: This could be a virus issue or another malware issue; you won’t know until you investigate further. So, anti-malware is a better solution than just antivirus. After installing the software, you should scan the system for malware, update that software, and then reboot the computer. Use the CompTIA A+ malware removal process to aid in this process. A pop-up blocker is good for ads but not necessarily for full pages that open by themselves. Plus, because the system is running slowly, the problem appears to be more than just pop-ups and is probably malware related.
17. Answer: C
Explanation: The Application log is the location for all events concerning Windows applications and third-party programs.
Incorrect answers: The System log contains information about drivers, system files, and stop errors but not application crashes. The Security log contains information regarding auditing events. The Setup log stores information on events that occurred during the installation of Windows.
18. Answer: C
Explanation: msconfig is the only option listed with which you can disable services. The key in the question is the phrase “bring up a window.” msconfig runs in a window, whereas the rest of the answers run as text at the command line. msconfig can also be used to modify how the system boots. (The Services console window can also be used to disable services, as well as start and stop them.)
Incorrect answers: sfc is the System File Checker; it scans the integrity of protected system files and repairs problems, if necessary and if possible. Contrast this with chkdsk, which can locate and repair errors on the disk but not within system files. gpupdate can update user and computer policy settings on the local computer or on remote computers.
19. Answer: A
Explanation: Use the asset ID and MAC address naming convention to help track and identify laptops while in use. An asset ID is an identification code that helps track computers or other assets in the organization. Many asset management systems use them. However, the system still needs to find the computer in this scenario. Because they are laptops and they could move from place to place, one good option is to locate the laptops by their MAC addresses. A MAC address is a physical address that is programmed into a chip on a network interface card; it is outside of, and not affected by, the operating system. Normally, the MAC address does not change, making it a good way to locate laptops that might move from place to place. The MAC address can be linked to the asset ID in the asset management system. This way, a technician can search for a particular computer by asset ID, and the system will cross-reference the MAC address and be able to find and report on that particular device. (Is this the only way to do this? No, but it is one way of making devices easier to track and identify.)
Incorrect answers: The problem with domain names and location information is that they are operating system based. They can change over time and do not necessarily provide actual identity of the system. IP addresses are also subject to change. If the systems are laptops, then they most likely obtain their IP addresses from a DHCP server, or more than one DHCP server if the laptops move from one location to another. If the DHCP server scope is modified, or if a new DHCP server is introduced to the network, or if the laptop moves to a new location, then the IP address of the system can change, making it more difficult to identify. Again, IP addresses are software based, whereas MAC addresses are hardware based. If at all possible, stick with hardware-based information for identification purposes.
20. Answer: A
Explanation: The best solution is to upgrade the wireless network from WPA to at least WPA2, and preferably WPA3.
Incorrect answers: MAC address filtering does not increase the level of data encryption, but it does filter out unwanted computers when they attempt to connect to the wireless access point. Modifying a wireless encryption key every week is not a good idea because all systems would have to reconnect to the wireless network, supplying that new key. In short, that is not efficient for the organization. Disabling the SSID broadcast deters new computers from making initial connections to the wireless access point. WEP is a deprecated wireless encryption protocol and should be updated to a newer and more powerful protocol if at all possible.
21. Answer: B
Explanation: dir /a can be used to display hidden files. Specifically, dir /ah can be used to show hidden files only.
Incorrect answers: dir /o deals with various sort orders of files (for example, alphabetical). dir /d sorts files by column in wide format, and dir /? displays the help file for the dir command.
22. Answer: A
Explanation: Try accessing Safe Mode first (by using WinRE) and see if the problem continues. It probably won’t, and you will need to roll back the driver and locate, download, and install the correct one. Remember to get your drivers from the manufacturer’s website and don’t forget to download the correct driver for your particular operating system.
Incorrect answers: chkdsk checks the integrity of files and fixes them, if necessary. The System Configuration utility (MSConfig) is used to boot the computer in different ways. Although you normally could select Safe Boot here, it is not possible in this scenario because the system won’t boot into Windows properly. You could check the System log while in Safe Mode, but it won’t explain much except that the system shut down improperly and rebooted continuously.
23. Answers: B, D, and F
Explanation: First, you should configure some kind of remote backup. This way, if the device is compromised, you have the confidential data backed up outside of the device at another location. The other half of this solution (not mentioned in the answers) is remote wipe. If you are positive that the device is stolen or lost, and you know the data was backed up at some point, trigger a remote wipe to remove all data from the device. Also, enable GPS on the device so that it can be tracked if it is lost or stolen. In addition, configure a screenlock of some sort, whether it is a pattern that is drawn on the display, a PIN, or a password. A strong password is usually the best form of screenlock and the hardest to crack.
Incorrect answers: It doesn’t make a difference how Bluetooth and Wi-Fi are configured: They won’t help protect confidential data in the event of theft. Instead of having Wi-Fi encryption configured, a mobile device should be prepared with a file encryption or full drive encryption tool.
24. Answer: D
Explanation: Most likely User B moved the file to another location outside of the current partition, made the changes (which is possible since User B is the one who moved it), and then moved it back to the original location. Whenever a file is moved to another partition or volume, the file takes on the permissions of the parent folder. However, if the file had been moved within the volume, the permissions would have been retained. Tricky. Remember this: If the file is moved within the same volume, it retains permissions, so the permissions don’t change. But if a file is moved to another volume, it takes on the permissions of the folder it is moved into. As for copying, the file’s copy always takes on the permissions of the parent, regardless of where that copy is placed.
Incorrect answers: If NTFS permissions were changed to allow execute, User A should have been able to open the file. If the file was set with the hidden attribute, User A should not have been able to see the file. Accounts receivable might or might not set a file to read-only. However, User A should still be able to open the file, but in read-only mode.
25. Answer: B
Explanation: Use the Event Viewer in Windows to further analyze the issues described in the question—especially the one about intermittent BSODs.
Incorrect answers: The Task Manager is a great analysis program for monitoring processes and system resource usage, but it is not as useful for problems such as BSODs and random screensaver activation. Top is a process analysis tool in Linux. Performance Monitor is another analysis program; it is similar to Task Manager but can monitor every single “object” in the computer, so it is much more in-depth.
26. Answers: B and E
Explanation: The badge reader and biometric lock are the best of the listed answers (although all kinds of other security methods are possible). This scenario is an example of multifactor authentication (MFA). An RFID-based badge reader relies on something a person has, and the biometric lock system relies on something the user is. MFA systems are more secure because they layer security.
Incorrect answers: A bollard is a physical obstacle, often seen in parking lots; it is used to block cars from driving onto a sidewalk or into a building. Cable locks are a good idea for servers and other equipment in a server room or data center, but they don’t secure a data center itself. A USB token is used for authentication to a computer, but not to the data center. Privacy (window) shades work well for blocking people from seeing what is inside a room, but they don’t do much to actually secure the room. Plus, I haven’t seen too many windows in the data centers and server rooms I have worked in!
27. Answer: A
Explanation: Windows PowerShell enables administrators to perform administrative tasks that integrate scripts and executables and can be run over a network. For even more power and flexibility, use Visual Studio Code (VSC) or the older PowerShell Integrated Scripting Environment (PowerShell ISE).
Incorrect answers: The Command Prompt is the basic version of a command line in Windows. It is not as functional as PowerShell. Mission Control is a macOS application that gives a bird’s-eye view of all open windows. Bash is the default shell used by Linux/Unix. You work with it in a command-line tool. For example, in Ubuntu Linux, the default program for working in a Bash shell is the Terminal program.
28. Answer: C
Explanation: Use the df -T command to find out what file systems are used by each of the storage drive partitions. Note that the -T option is needed to see the file system types. The console is simply the name of the command line (terminal) in Linux if you are working on the server locally.
Incorrect answers: diskpart is a Windows tool for analyzing and configuring storage drives and partitions. rm in Linux will remove files or directories. pwd in Linux will show you the current directory path that you are working in.
29. Answer: B
Explanation: exFAT (also known as FAT64) is suited specifically for USB flash drives and many other mobile storage solutions. It is the successor to FAT32 and can format media that is larger than 32 GB with a single partition.
Incorrect answers: Older file systems such as FAT32 are very limited in terms of the partition size. NTFS can be a good solution for USB flash drives, but exFAT was developed specifically for USB flash drives and is a better solution with an operating system that supports it. ext4 is a commonly used file system in Linux-based systems.
30. Answer: A
Explanation: Spyware is a type of malicious software that is usually downloaded unwittingly by a user or is installed by third-party software. It collects information about the user and the user’s computer without the user’s consent.
Incorrect answers: A virus is code that runs on a computer without the user’s knowledge; it infects a computer when the code is accessed and executed. A rootkit is software designed to gain administrator-level control over a computer system without being detected. Spam is the abuse of electronic messaging systems such as email.
31. Answers: B, D, and G
Explanation: You can stop a service in a variety of ways. One way is to go to the Services console window. You can do this by typing services.msc at the Run prompt. You can also stop services in the Task Manager by accessing the Services tab and right-clicking the service in question. But in the Task Manager, you have to know the executable name of the service. The name of the Windows Defender Firewall service is mpssvc. So, the third way (of the listed answers) is to use the net stop mpssvc command in PowerShell or the Command Prompt.
Incorrect answers: Performance Monitor, System Information, and gpedit.exe do not allow you to stop services. MSConfig (System Configuration Utility) can enable or disable services but not start or stop them.
32. Answer: C
Explanation: If the chemical spill is not life threatening, consult the material safety data sheet (MSDS) to determine the proper first aid (if any).
Incorrect answers: If it is an emergency, call 911. If you cannot get access to the MSDS, contact the facilities department of your organization or try your building supervisor. Never ignore a chemical spill. Take action before it becomes a problem.
33. Answer: D
Explanation: The chmod command allows a user to modify file and folder permissions at the Linux command line.
Incorrect answers: The chown command allows a user to change the ownership settings for a file. passwd enables a user to change the password at the command line. ls displays the contents of a directory in Linux. These commands can also be used in macOS.
34. Answer: C
Explanation: Whenever you’re working in someone’s home, make sure that an adult is available.
Incorrect answers: You cannot take on the responsibility for watching a child; there could be legal consequences for doing so. Plus, there is no point in discussing the matter. Most companies have policies that simply state the terms of your visit to a customer. It is not your responsibility to watch over children, nor should any service company agree to have its consultants do this. If the person insists on leaving, and you can pack up your things before that happens, do so, and then call your supervisor to inform him or her of the event.
35. Answer: B
Explanation: You should access the knowledge base (KB) so that you can document your findings. This is especially important because the problem has never been seen before (or at least documented in your organization). By entering your findings and solution into the KB, you help your team by providing information for anyone who needs to troubleshoot the same problem in the future.
Incorrect answers: A Bluetooth PAN is an ad hoc network of Bluetooth-enabled devices such as smartphones, headsets, printers, wireless access points, and so on. An asset management system is used to track and identify assets on a network, such as PCs, laptops, and other devices. Devices that are part of the Internet of Things (IoT) may or may not be part of a screened subnet. A screened subnet (or DMZ) is a good idea, though, especially for IoT devices in the home, as it creates a layer of separation between the IoT devices that usually communicate directly with the Internet and the more personal home devices. Another good option is to put these devices on the guest wireless network.
36. Answer: C
Explanation: An open license means that the software can be downloaded and used for free. It refers to open source software. An example of software with an open license is Linux. Know the difference between open source and closed source software!
Incorrect answers: Often, anti-malware suites offer advanced versions of the software for a fee. At that point, it would become a personal license. Corporate and enterprise licenses are not for home users; they are often bulk discount licenses for multiple users.
37. Answer: A
Explanation: Stay calm and do the job as efficiently as possible. There isn’t much you can do when a customer is upset except fix the problem.
Incorrect answers: I’d be interested to see what would happen if a person asked the owner of the server out for a cup of coffee, but I’m pretty sure the reaction would be negative (at that particular moment at least). You don’t want to avoid the customer, but you don’t have to engage in anything except fixing the problem. You should refer the customer to your supervisor only if the person gets in the way of you doing your work. People being upset about tech… well, it’s common, so be ready.
38. Answer: D
Explanation: You should provide written documentation to the customer to provide proof of everything that you performed and why.
Incorrect answers: Once again, stay calm. Don’t let the complaint bother you. Remember that most customers (especially business customers) want things fixed immediately and don’t really care about (and may not understand) what it takes to effectively troubleshoot a problem. Recording the customer’s concerns is a good idea. Posting them to social media? Well, I think it goes without saying that that’s a bad idea—and one that could possibly get you fired. Informing the customer that the job has been completed is redundant. You already completed the job and left the job site, so an answer like that is non-responsive; it doesn’t provide the customer with anything valuable. In the end, you might need to refer the customer to a supervisor, but you should most definitely provide some kind of documentation first and answer any questions you can (within reason). Verbally defending what you did is not a good idea because there are no facts to back it up. Here’s a saying for you that can extend to many other things in this world: Always provide proof of work!
39. Answer: B
Explanation: There isn’t much you can do in a situation like this, especially if you already saw what was printed on the document. The best thing is to ignore it and act as if it never happened. It’s not your place to take action based on a document that is lying around. Without intense scrutiny, it is hard to know exactly what a document is. The purported list might be real, but it might not be. It isn’t your call to make. However, when working at a customer site, you should ask that all confidential materials be removed before you begin work. If something is left out in plain sight, you could let a manager know that there could be confidential data lying around.
Incorrect answers: Technicians must be security minded. Any documents owned by the company and printed by another user are not your property or your concern; they should not be handled or shredded. It could be a bad situation, but the right course of action is to not discuss it. As mentioned, the list could be real, or it could be a draft or a prank; either way, telling everyone about it could cost you your job. It is, however, something that you could bring up to a member of human resources, if necessary. Yelling is never a recommended course of action at the office. Save that for construction zones, demolition derbies, and heavy metal bands; or just avoid it altogether.
40. Answer: D
Explanation: The force quit option in Apple’s macOS is most like the “end task” feature in the Windows Task Manager. It helps when an application is not functioning as intended and is either frozen or intermittently slows down the system.
Incorrect answers: Time Machine is the macOS backup utility, and it is similar to Windows File History and Windows System Restore. Finder is the macOS file and application exploration tool, and it is similar to the Windows File Explorer. In macOS and Linux systems, kill 3035 is a command that terminates the process with the ID 3035. But that is done at the command line and not in a graphical utility.
41. Answers: A, B, and D
Explanation: To reduce the chance of electrostatic discharge (ESD), use an antistatic wrist strap and mat. If connected properly, they provide suitable self-grounding. Also, consider raising the humidity. The more humidity there is, the less friction and, ultimately, the less ESD there is.
Incorrect answers: Raising the temperature has no effect. Lowering the humidity increases the chance of ESD. Working in a carpeted area also increases the chance of ESD; try to work in a noncarpeted area. You should also touch the chassis of the computer before handling any components; this is a basic form of self-grounding. In addition, place components in antistatic bags when they are not in use.
42. Answer: B
Explanation: Make the customer truly feel comfortable by sitting down next to the person and taking the time to explain the technical concept simply and concisely. The less jargon, the better.
Incorrect answers: Recommending a training class is tantamount to dismissing the customer out of hand. Telling the customer to read the manual is just downright rude. I know, I say this often to you; however, you are a tech, so reading the manual is what you do. The customer is not supposed to be super technically oriented. The acronym RTM should be kept within technical circles!
43. Answer: C
Explanation: If you see the name dpro42.com toward the beginning of the results of an ipconfig /all command, the computer is most likely a part of the dpro42.com domain. This would be listed in the Primary DNS Suffix entry, which is usually directly after the Host Name entry. The .com is the giveaway. Some kind of DNS extension (such as .com or .net) is necessary with a domain.
Incorrect answers: If the computer were simply part of a workgroup, the Primary DNS Suffix entry would be left blank (by default). A Windows computer won’t usually be part of a storage area network (SAN). SANs are usually made up of NAS devices, RAID devices, and Fibre Channel connections. If the computer were connected to a VPN, you would see IP configuration details for a “Tunnel adapter” connection farther down in the ipconfig /all command output.
44. Answer: C
Explanation: If you are not sure about what to clean a screen with, use water. Water will most likely not damage a screen.
Incorrect answers: If the user manual for the monitor calls for it, you might see that you can use a half-and-half mixture of water and isopropyl alcohol. Do not use detergents on a screen; they are okay for the outside of a computer case but not for a display. And boric acid could be quite dangerous.
45. Answer: C
Explanation: A password manager is a program that stores passwords in an encrypted format. It can be integrated into a web browser or can run independently. The important part is for the customer to set up and memorize a complex, lengthy password that allows access to the password manager program.
Incorrect answers: The rest of the answers are all good ideas when surfing the web, but they don’t help with the credentials memorization issue the customer is having. Trusted sources are websites that a web browser is allowed to download content from. Hashing is a way of verifying the validity of a file that is to be downloaded from the Internet. Secure certificates are used whenever a web browser connects to an HTTPS (TLS)-based site.
46. Answer: A
Explanation: The best option here is to create alerts to let any and all administrators know if a backup failure occurs. These alerts would either be created at the network-attached storage (NAS) device or at the individual servers to be backed up. If an admin receives an alert, that person will know to either rerun the backup or (more likely) fix the backup task and then run it. One of the issues here is that, without the alerts, you might not know if a backup fails.
Incorrect answers: Setting up scripts is a good idea for the backup processes themselves, but you first need to be alerted about an issue before you can script a rerun of the failed backup jobs. In this case, the backups are being stored to a NAS device locally (on the LAN), so they are not being stored offsite. You should always test a backup the first time it runs and periodically afterward; however, frequent restoration tests are very time-consuming, not to mention hardware intensive for the NAS device. Restoring to a VM is a good way to test, but it’s not a good way to ensure rapid recovery, nor is it where the backups are supposed to be restored to; the question says “physical servers.”
47. Answer: D
Explanation: If your system’s motherboard is equipped with a UEFI BIOS, you should definitely take advantage of the GUID Partitioning Table (GPT). It is superior to the older MBR technology. GPT allows for up to 128 partitions, is not limited to the 2 TB maximum partition size of MBR, and it stores multiple copies of itself on the system.
Incorrect answers: As mentioned, MBR is inferior to GPT and should be avoided; however, you might service older systems that require it. FAT32 is not really a partitioning scheme but rather a type of file system—and an older one at that. NTFS or exFAT is preferable. A dynamic drive is a drive in Windows that has been upgraded from basic; it allows a user to change the size of the volumes on the drive.
48. Answer: B
Explanation: You should disable System Restore on a Windows system just before attempting to remediate the system of malware. This is step 3 of the CompTIA A+ best practices/procedure for malware removal. The entire procedure is as follows:
1. Investigate and verify malware symptoms.
2. Quarantine infected systems.
3. Disable System Restore in Windows.
4. Remediate infected systems.
a. Update anti-malware software.
b. Scan and removal techniques (safe mode, pre-installation environment).
5. Schedule scans and run updates.
6. Enable System Restore and create a restore point in Windows.
7. Educate the end user.
Incorrect answers: As you can see, the rest of the answers listed in the question occur after (or during) “remediate infected systems.”
49. Answers: A, D, and E
Explanation: If a mobile device cannot connect to the network, you should attempt to power cycle the device, forget and reconnect to the Wi-Fi network, and ensure that the correct SSID was entered in the first place. Perhaps the number-one method would be to power cycle Wi-Fi (which is not listed in the answers).
Incorrect answers: Re-pairing has to do with Bluetooth, not Wi-Fi. Re-pairing means that you remove the paired Bluetooth device and then reconnect it. A hard reset wipes a device of its data and returns it to factory condition. This is a very last resort; there are plenty of other things you can try before that. Changing the IP address is possible but usually not necessary because most mobile devices obtain their IP addresses dynamically.
50. Answer: A
Explanation: Sync Center is a Windows feature that enables you to keep information synchronized between your computer and network servers. You can still access the files and modify them even if you don’t have physical access to the server; in this case, they are modified “offline” and are synchronized automatically when you return to the network. Some mobile devices are also compatible with Sync Center. Sync Center can be configured within the Control Panel.
Incorrect answers: PowerShell is a command-line and scripting environment in Windows. Windows Defender Firewall is the built-in firewall tool in Windows; it provides protection to the operating system against external attacks. Resource Monitor is a Windows tool that allows you to analyze your system resources such as CPU, RAM, and network card in a condensed, easy-to-read fashion.
51. Answer: A
Explanation: The technician should repeat the problem back to the customer to make sure that everyone is talking about the same thing and that both parties understand each other. Always clarify.
Incorrect answers: Having the customer call back later is just delaying the problem. Asking a person with an accent to stop speaking with an accent is like telling a dog to stop wagging its tail: It is probably futile. A technician needs to be culturally sensitive. If you seriously cannot understand the customer even after attempting to listen several times and repeating the problem back, you will have to involve someone else who can help you or attempt to communicate with the person through email.
52. Answers: A and E
Explanation: The hardware for the lab computers should support Preboot eXecution Environment and have Wake-on-LAN capability. To run the virtual desktops, they need PXE to automatically boot to the network server. Wake-on-LAN (also known as WOL) should be enabled so that the lab computers can be started remotely and can wake up when pinged on the network.
Incorrect answers: Image deployment isn’t needed because you are not installing an entire operating system on the lab computers; they will be running virtual desktops that will have to be preconfigured at a server. USB isn’t required here; the lab computers will be getting their virtual desktops over the network (via fiber-optic, Ethernet, or wireless connections). You don’t want a multiboot system here; that would mean that two operating systems are installed to the same drive of a lab computer. An unattended installation means that you are installing an operating system (such as Windows) to a system using an answer file to automate the installation. Again, you don’t want an installation of an OS or an image deployment here; rather, you want to end up with virtual desktops on the lab computers.
53. Answer: C
Explanation: Entering %temp% at the Run prompt displays a folder with the current user’s temporary files. For example, in Windows, this would show the path C:Users\%username%AppDataLocalTemp.
Incorrect answers: Nothing will be added, changed, or deleted. The folder will simply be displayed in a File Explorer window. The operating system’s temporary folder is located at C:WindowsTemp.
54. Answer: D
Explanation: A standard user cannot install software or make changes to the system without knowing an administrative login.
Incorrect answers: Administrators have full control over a system. Power users (way back in the Windows XP days) were able to install programs and device drivers and are found in newer versions of Windows only for backward compatibility with older applications. A Remote Desktop user can remote into another machine to control it from another location.
55. Answer: A
Explanation: chkdsk /R locates bad sectors and recovers the information from them.
Incorrect answers: /F fixes errors but doesn’t locate bad sectors and recover the information from them. /C and /I skip certain checks of the volume (in this case, C:), which ultimately reduces the time it takes to check the volume.
56. Answer: D
Explanation: Of the listed answers, a fingerprint is the best option for securing the smartphone. If the smartphone is lost or stolen, another person would have a difficult time unlocking the device (though it would not be impossible). For a device that cannot be remotely wiped (for various reasons), the best alternative is the use of biometric authentication in combination with a strong password (for MFA) plus encryption.
Incorrect answers: Passcodes and PINs can be cracked, given enough time. Even a lengthy and complex password can be cracked eventually. “Swipe” simply means a user swipes on the screen to unlock it; no actual authentication is happening here, which means swiping is not a secure option.
57. Answer: A
Explanation: Of the listed answers, you should attempt to rebuild the user’s mail profile. If the email program worked for you but doesn’t work for the user, then chances are that the email application is fine, but the user profile needs to be repaired. It is likely that Microsoft Outlook is being used in this scenario. See the following link for information about rebuilding Outlook profiles for Outlook 2010 through 2016: https://support.microsoft.com/en-us/office/fix-your-outlook-email-connection-by-repairing-your-profile-4d5febf6-7623-486b-9a9f-d5cfc4264af3. Also, Microsoft 365 has fewer of these types of issues (though it can auto-rebuild profiles if needed). Consider recommending Microsoft 365 to the user.
Incorrect answers: Applying software updates is always a good idea, and it is probably done automatically by your security team. However, it shouldn’t affect this scenario because other people are able to use the email application without issue. Never add a typical user to the administrators group. Remember the principle of least privilege! You could possibly attempt a repair installation of the email application—but you should do so only after you have tried rebuilding the user’s profile. If you reinstall the email application, you risk having data issues with other user profiles. Again, the email application should be okay because other users are able to use it.
58. Answers: A and D
Explanation: If a user cannot print to a brand-new printer but everyone else can print to it, you should check whether the printer is installed on that user’s computer and whether it is set as the default printer.
Incorrect answers: If the printer has not yet been installed, there will be no print queue to clear. However, if the printer has been installed, the next thing to check would be whether the print queue has failed. You could also check the print spooler. If the user can print to an older printer that is also shared by other users in the workgroup, you should not have to change the user’s password or permissions.
59. Answer: D
Explanation: The best option in this scenario would be to deny read access to the Accounting folder for Bill through shared access security.
Incorrect answers: You would not use local access security because the folder is shared from a network server within your Active Directory domain. Also, if you remove Bill from all domain groups that have access to the Accounting folder, Bill will probably lose access to other folders as well. If you deny read access to the Accounting folder for any group that Bill is a member of, you will probably impact other users on the network negatively.
60. Answer: B
Explanation: The Disk Management component of Computer Management is displayed in the figure. You can tell because it shows each disk and the volumes within each disk.
Incorrect answers: The Event Viewer houses log information for the system, applications, and security auditing events. gnome-disks is a partitioning tool used with Linux. diskpart is the command-line tool used to create and modify partitions on the storage drive.
61. Answer: C
Explanation: System Restore is a feature that creates and saves data about the computer’s system files and settings. It does this by creating restore points. You access it by going to the System Properties dialog box and clicking the System Protection tab. External storage is not necessary for these restore points; they are automatically stored in the system volume.
Incorrect answers: MSConfig is used to modify the way Windows boots and the services that are loaded at startup. The Task Manager is used to view system performance, enable/disable applications, stop services, and kill processes. robocopy is an advanced file copying tool that can be used to copy entire directory trees of data, but it doesn’t copy settings.
62. Answer: A
Explanation: BitLocker is a type of whole-disk encryption (WDE). It encrypts all of the contents that are created on it or copied to it in real time. It requires a Trusted Platform Module (TPM) chip on the motherboard or an encrypted USB flash drive. Only select editions of Windows support BitLocker when used in this manner. Other lesser versions of Windows are compatible with BitLocker To Go for reading encrypted documents from USB flash drives.
Incorrect answers: PKI, which stands for public key infrastructure, is an entire system of technologies and users dealing with encryption. The TPM chip can be required for this scenario, but it is not the encryption itself. Kerberos is an authentication protocol.
63. Answer: B
Explanation: The first thing you should do is investigate and verify malware symptoms. (By the way, if the computer is on the network, disconnect it first.) Then, if there is malware present, you can research that malware and any possible cures by searching the Internet and accessing your AV provider’s website.
Incorrect answers: Rolling back drivers should not be necessary, especially if you find it necessary to run a System Restore at some point. Remember your best practices procedure for malware removal!
64. Answer: A
Explanation: User A will end up having the Read-Only level of access to the share. Generally, a user gets the more restrictive level of access. The only thing that is different between the share’s permissions and the parent directory’s permissions is the level of control for the Users group. Normally, a share obtains its permissions from the parent folder—that is, unless that option is unchecked in the properties of the folder. Then the folder can be reconfigured for whatever permissions an admin wants to set for it. That must be what happened in this scenario.
Incorrect answers: Administrators get Full Control access to almost everything by default. Guests get No Access to just about everything by default. So the only possibilities for this question are Change and Read-Only. Again, in general, the typical Standard User account receives the more restrictive level of permissions.
65. Answer: A
Explanation: Before implementing the BitLocker solution in Windows, you should enable the Trusted Platform Module (TPM) chip in the BIOS/UEFI. This is the chip on the motherboard that includes the encryption code.
Incorrect answers: UAC, which stands for User Account Control, is a separate security option in Windows that checks whether users have administrative permissions before allowing them to carry out administrative tasks. Defragmenting the hard drive is not necessary, but it can’t hurt to at least analyze the drive and see if it needs to be defragged. Defragging a drive that requires it can increase performance. BitLocker works on FAT16, FAT32, NTFS, and exFAT partitions, so you do not need to convert the file system.
66. Answer: D
Explanation: Use the File Explorer Options utility in the Control Panel of Windows. From there, you go to the View tab and then deselect the checkbox labeled Hide Protected Operating System Files (Recommended). You might also deselect the Hide Extensions for Known File Types checkbox to see which ones are .dll files. You can also access these settings from the File Explorer program by choosing View > Options > Change Folder and Search Options (in which case the dialog box will be named Folder Options). Or you can go to Run and type control folders.
Incorrect answers: The other Control Panel utilities do not apply here.
67. Answers: C and D
Explanation: This situation is more common than you might think. It seems as if no one is safe today from email threats and scams. We must be vigilant and make all users aware of the murky email waters ahead. Did the CEO attend user training and sign an AUP? Sometimes user education works; sometimes it doesn’t. One way to make user education more effective is to have a technical trainer educate your users instead of doing it yourself. This can provide for a more engaging learning environment. During this training, you might opt to define the organization’s acceptable use policy (AUP). This is a document that stipulates constraints and practices that a user must agree to before being granted access to a corporate network or the Internet.
Incorrect answers: Advanced Encryption Standard (AES) is the strongest form of wireless encryption commonly used with WPA2/WPA3. You can access Windows Defender Firewall by going to Run > firewall.cpl. However, neither AES nor Windows Defender Firewall will protect against clicking on malicious email links.
68. Answer: A
Explanation: You should first verify that the installation is allowed under the company’s licensing agreement. It probably isn’t, but you should check. Most organizations do not allow purchased software to be installed on an employee’s home computer. If doing so is against organization policy, you should notify your supervisor. There are many types of licenses that you should be aware of, including end-user licensing agreements (EULA), digital rights management (DRM), commercial and enterprise licenses (such as client access licenses or CALs), open source versus closed source (that is, Android versus iOS), personal licenses, and so on. Again, be sure to follow and incorporate corporate end-user policies and security best practices when it comes to these types of licenses.
Incorrect answers: You would notify your supervisor/manager, not the company owner, unless it was a very small company. Verify whether the license is valid or allowed before advising any individuals. Calling law enforcement is premature because you have not yet verified the nature and validity of the license.
69. Answer: A
Explanation: If you see video issues such as pausing during game play, upgrade the video drivers. Make sure that you download the latest video driver from the manufacturer’s website. Gamers cannot rely on Microsoft drivers.
Incorrect answers: Sometimes reinstalling a game is necessary, but it shouldn’t be in this scenario. Replacing the NVMe drive can be expensive, and reinstalling the OS is time-consuming. Both are most likely drastic and unnecessary measures in this scenario.
70. Answer: B
Explanation: The first thing you should do is export the user’s certificate from the first laptop to the second laptop. You can do this by clicking Start and typing certmgr.msc in the Search box; then locate and export the correct personal certificate. The Certificates console window can also be added to the MMC. Encrypting File System (EFS) is the standard single-file encryption method for Windows (in editions of Windows that support it).
Incorrect answers: Administrative privileges won’t help immediately because the encryption will still be in effect, but an administrator can deal with the importing and exporting of certificates from one computer to another, and a typical user cannot. Networking need not be disabled, and you aren’t sure which user is being referred to in the answers, but if the certificate has been exported, that user should be able to read the files. Partitions can be converted from FAT32 to NTFS but not vice versa.
71. Answer: B
Explanation: Authentication can be carried out by utilizing something a user is, such as a fingerprint; something a user knows, such as a password or PIN; something a user has, such as a smart card or token; and something a user does, such as writing a signature or speaking words.
Incorrect answers: A smart card is something the user has (a possession factor), not something the user knows. A PIN and a password are something the user knows (a knowledge factor), not something the user does. A signature is something the user does, not something the user has.
72. Answer: B
Explanation: This scenario is based on a Windows system. You should configure the enforce password history policy and set it to a number higher than zero. This way, when a user is prompted to change his or her password every 42 days (which is the default maximum password age), that user will not be able to use the same password. Password policies can be accessed in Windows within the Local Security Policy window > Security Settings > Account Policies > Password Policy.
Incorrect answers: Minimum password length is the policy that states the fewest characters a password must contain. Eight is a decent setting, but to be full-on secure, many organizations require at least 16 characters. There are several technical reasons for this, but the A+ exam does not go into that kind of depth. Minimum password age won’t stop a user from reusing a password; it is usually set to zero by default. Complexity requirements policy, if enabled, forces a user to select a password that meets three of the following five categories: uppercase characters, lowercase characters, numbers, special characters (such as ! or #), and Unicode characters (not often implemented). Since 2017, the National Institute of Standards and Technology (NIST) has leaned toward lengthy passwords as opposed to complex passwords.
73. Answer: B
Explanation: When you add a second drive to a system that already has Windows installed, you will probably have to initialize the drive and format it in the Disk Management utility.
Incorrect answers: Rebooting the computer does not help the system see the drive. You can configure the drive in the BIOS/UEFI to a certain extent, but that won’t help Windows see the drive. When you format the drive, Disk Management asks you to assign a drive letter. You don’t need to set the drive to active because this drive does not have an OS to be booted to.
74. Answer: D
Explanation: The most practical way to prevent intrusion to the network is to install a firewall. In fact, if this is a SOHO network, chances are the network is controlled by a multifunction network device that already acts as a switch and a router and probably has built-in firewall technology; it just has to be enabled. Usually, the firewall on such a device is enabled by default, but perhaps someone inadvertently disabled this feature, and that’s one of the reasons an attacker keeps trying to get into the network.
Incorrect answers: An intrusion detection system (IDS) is usually more elaborate and costs more money, but it would help to prevent network intrusion. (Some devices combine IDS and firewall technologies, but SOHO multifunction network devices usually do not.) Disabling the SSID helps to discourage the average user from accessing the wireless network, but any hacker worth his or her salt can get right past that; plus, the attacker could be trying to connect directly through the Internet connection. Antivirus software, regardless of where it is installed, does not repel attackers; it locates and quarantines malware. Disconnecting the Internet connection would work; the hacker wouldn’t be able to get in, but none of the employees would be able to use the Internet. That’s not a good compromise.
75. Answers: A and C
Explanation: The most likely reasons the users cannot connect are denied permissions and mapped drives. If the data was moved to another computer, the folders will inherit new permissions from the parent (by default). That will most likely eliminate the current user access. Also, the path to the share will change (again by default). Either the server name/IP address, the sharename, or both will be different when the data is moved to another server. So, to fix the problem, the user and group permissions will have to be modified for the new share, and new mapped drives will need to be configured.
Incorrect answers: There is no evidence that the time of day restrictions have been changed for any users. Administrative shares (such as C$) are for admins only; the users are not trying to access these shares in the scenario. Disabling proxy settings is done at the client computer. It might make sense that these settings have been disabled if this happened to one system, but because multiple users are affected, it is unlikely.
76. Answer: C
Explanation: Use the FAT32 file system to format a drive that needs to be accessed by both Linux and Windows operating systems.
Incorrect answers: exFAT works well for USB drive, and while a USB drive is external, these drives are not available in 8 TB sizes. The drive being worked with is most likely using some other technology, such as a NAS device or something similar. The Network File System (NFS) works well to store data on servers, and while both Windows and Linux systems can access NFS over the network, NFS is not the proper option for a drive that is being accessed directly. ext4 is used by Linux but is not compatible with Windows.
77. Answers: A and D
Explanation: Use the stop-computer cmdlet or the shutdown command. Either of these can be used to turn off a local or remote computer. They can be used directly in PowerShell or within a script. For more information about stop-computer, see https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.management/stop-computer?view=powershell-7.2#parameters. For more information on shutdown, see https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/shutdown.
Incorrect answers: poweroff is used to turn off Linux systems. kill is used to terminate processes in Linux. restart-computer is a cmdlet in PowerShell that reboots the Windows system.
78. Answer: C
Explanation: /S copies subdirectories but skips any empty ones.
Incorrect answers: /E copies all subdirectories, including empty ones. /B copies files in backup mode. /DCOPY:T also copies timestamps of files and folders.
79. Answers: A, C, and D
Explanation: When dealing with prohibited content, there will always be a first responder who is required to identify the issue, report through proper channels, and preserve data and possibly devices used. This person will be in charge of starting the documentation process, which includes maintaining a chain of custody, tracking evidence, and maintaining a chronological log of that evidence.
Incorrect answers: You should always maintain a positive attitude and avoid distractions, but those concepts concern professional behavior, not first response and prohibited content.
80. Answers: C and D
Explanation: The HVAC system’s primary responsibilities are to provide an appropriate ambient temperature for the equipment and to maintain appropriate humidity levels. This keeps the equipment from overheating and prevents electrostatic discharge (ESD).
Incorrect answers: HVAC equipment, by its very nature, is a producer of electromagnetic interference (EMI); it does not shield equipment from EMI—quite the reverse. HVAC equipment often needs to be shielded to reduce EMI after it is installed. Isolation can be provided by other methods, such as the material used in the perimeter of the room. A separate ventilation system can be installed to vent fumes away from the server room; however, there shouldn’t be any fumes. Products that contain fumes should be stored in a separate and specially secured area. And if a fire were to occur, the sprinkler system or special hazards system should end that threat, eliminating any fumes that were a result of the fire.
That Was a Lot of Fun!
This is the end of Exam C, which is the last practice exam in the book. I hope you have enjoyed reading it as much as I enjoyed writing it.
If you scored 90% or higher on this 220-1102 practice exam, you are in pretty good shape. Now complete the book and access the companion website for more content.
