Chapter 5
Domain 5.0: Compliance and Assessment
EXAM OBJECTIVES COVERED IN THIS CHAPTER:
- 5.1 Understand the importance of data privacy and protection.
- Privacy vs. security
- Non-technical controls
- Technical controls
- 5.2 Given a scenario, apply security concepts in support of organizational risk mitigation.
- Business impact analysis
- Risk identification process
- Risk calculation
- Communication of risk factors
- Risk prioritization
- Systems assessment
- Documented compensating controls
- Training and exercises
- Supply chain assessment
- 5.3 Explain the importance of frameworks, policies, procedures, and controls.
- Frameworks
- Policies and procedures
- Category
- Control type
- Audits and assessments
- Victoria's organization is concerned that end users do not understand the levels of security protection that apply to each type of information that they handle. What security control would best address this need?
- Ownership
- Classification
- Retention
- Confidentiality
- Ken learns that an APT group is targeting his organization. What term best describes this situation?
- Risk
- Threat
- Countermeasure
- Vulnerability
- Walt is assessing his organization against the HIPAA security framework. The HIPAA security rule allows the organization to select controls that are appropriate for the organization's business environment. What term best describes this approach?
- Prescriptive
- Minimal
- Optional
- Risk-based
- Which one of the following activities is least likely to occur during the risk identification process?
- Network segmentation
- Threat intelligence
- Vulnerability scanning
- System assessments
- What two factors are weighted most heavily when determining the severity of a risk?
- Probability and magnitude
- Likelihood and probability
- Magnitude and impact
- Impact and control
- Preemployment background screening is an example of what type of security control?
- Detective
- Preventive
- Corrective
- Compensating
- Roland received a security assessment report from a third-party assessor, and it indicated that one of the organization's web applications is susceptible to an OAuth redirect attack. What type of attack would this vulnerability allow an attacker to wage?
- Privilege escalation
- Cross-site scripting
- SQL injection
- Impersonation
- Manish recently verified that the cash registers in his retail stores are printing only the last four digits of credit card numbers on receipts, replacing all of the other digits with asterisks. The receipt does contain the customer's name and signature. What type of control has he implemented?
- Tokenization
- Purging
- Masking
- Deidentification
- Renee is conducting due diligence on a potential vendor. Which one of the following information sources would be most useful to her?
- Marketing brochure
- Conversation with the vendor's security team
- Independent audit results
- List of security standards in use
- Which one of the following objectives is least relevant to HIPAA compliance programs?
- Confidentiality
- Privacy
- Nonrepudiation
- Availability
Questions 11–13 refer to the following scenario.
Gary recently conducted a comprehensive security review of his organization. He identified the 25 top risks to the organization and is pursuing different risk management strategies for each of these risks. In some cases, he is using multiple strategies to address a single risk. His goal is to reduce the overall level of risk so that it lies within his organization's risk tolerance.
- Gary decides that the organization should integrate a threat intelligence feed with the firewall. What type of risk management strategy is this?
- Risk mitigation
- Risk acceptance
- Risk transference
- Risk avoidance
- Gary discovers that his organization is storing some old files in a cloud service that are exposed to the world. He deletes those files. What type of risk management strategy is this?
- Risk mitigation
- Risk acceptance
- Risk transference
- Risk avoidance
- Gary is working with his financial team to purchase a cyber-liability insurance policy to cover the financial impact of a data breach. What type of risk management strategy is he using?
- Risk mitigation
- Risk acceptance
- Risk transference
- Risk avoidance
- Sadiq is the CIO of a midsized company and is concerned that someone on the IT team may be embezzling funds from the organization by modifying database contents in an unauthorized fashion. What group could investigate this providing the best balance between cost, effectiveness, and independence?
- Internal assessment by the IT manager
- Internal audit
- External audit
- Law enforcement
- Deepa recently accepted a new position as a cybersecurity analyst for a privately held bank. Which one of the following regulations will have the greatest impact on her cybersecurity program?
- HIPAA
- GLBA
- FERPA
- SOX
- Alfonso is reviewing the ways that his organization uses personal information and ensuring that they are compliant with the disclosures made in their privacy policy. What term best describes this activity?
- Data retention
- Data disposal
- Data minimization
- Purpose limitation
- Florian is designing an encryption strategy for his organization. He is choosing an encryption key length and decides that he will choose a shorter key to minimize processor consumption. The key length is within his organization's security standards, but it is not the maximum key length supported by the device. The organization is a HIPAA-covered entity. Which one of the following statements best describes this approach?
- This introduces an unnecessary level of security risk because it is not using the full security capabilities of the device.
- This is an acceptable engineering trade-off.
- This approach likely violates the organization's security policies.
- Regardless of whether the approach violates the organization's internal policies, it is likely a HIPAA violation.
- Brandy works in an organization that is adopting the ITIL service management strategy. Which ITIL core activity includes security management as a process?
- Service strategy
- Service design
- Service transition
- Service operation
- What type of exercise gathers teams together to plan a response to a hypothetical situation without actually activating an incident response effort?
- Checklist review
- Tabletop exercise
- Full interruption test
- Parallel test
- Oskar uses an infrastructure-as-a-service (IaaS) provider and faces limits on the regions that he may use within that service. His organization is concerned that placing data in datacenters located within the European Union would subject it to the EU's General Data Protection Regulation (GDPR). What type of concern does this policy address?
- Data minimization
- Data sovereignty
- Purpose limitation
- Data retention
- Which one of the following events is least likely to trigger the review of an organization's information security program?
- Security incident
- Changes in compliance obligations
- Changes in team members
- Changes in business processes
- Which one of the following risk management strategies is most likely to limit the probability of a risk occurring?
- Risk acceptance
- Risk avoidance
- Risk transference
- Risk mitigation
- Roger is the CISO for a midsized manufacturing firm. His boss, the CIO, recently returned from a meeting of the board of directors where she had an in-depth discussion about cybersecurity. One member of the board, familiar with International Organization for Standardization (ISO) standards in manufacturing quality control, asked if there was an ISO standard covering cybersecurity. Which standard is most relevant to the director's question?
- ISO 9000
- ISO 17799
- ISO 27001
- ISO 30170
Questions 24–26 refer to the following scenario:
Martin is developing the security infrastructure for a new business venture that his organization is launching. The business will be developing new products that are considered trade secrets, and it is of the utmost importance that the plans for those products not fall into the hands of competitors.
- Martin would like to take steps to confirm the reliability of employees and avoid situations where employees might be susceptible to blackmail attempts to obtain the plans. Which one of the following controls would be most effective to achieve that goal?
- Firewall
- DLP system
- Background investigation
- Nondisclosure agreement
- Martin would like to install a network control that would block the potential exfiltration of sensitive information from the venture's facility. Which one of the following controls would be most effective to achieve that goal?
- IPS
- DLP system
- Firewall
- IDS
- Several employees will need to travel with sensitive information on their laptops. Martin is concerned that one of those laptops may be lost or stolen. Which one of the following controls would best protect the data on stolen devices?
- FDE
- Strong passwords
- Cable lock
- IPS
- Saanvi would like to reduce the probability of a data breach that affects sensitive personal information. Which one of the following controls is most likely to achieve that objective?
- Minimizing the amount of data retained and the number of places where it is stored
- Limiting the purposes for which data may be used
- Purchasing cyber-risk insurance
- Installing a new firewall
- Kwame recently completed a risk assessment and is concerned that the level of residual risk exceeds his organization's risk tolerance. What should he do next?
- Have a discussion with his manager
- Implement new security controls
- Modify business processes to lower risk
- Purge data from systems
- Which one of the following is not one of the four domains of COBIT control objectives?
- Plan and Organize
- Acquire and Implement
- Design and Secure
- Deliver and Support
- Mia discovers that an employee is running a side business from his office, using company technology resources. What policy would most likely contain information relevant to this situation?
- NDA
- AUP
- Data ownership
- Data classification
Questions 31–36 refer to the following scenario.
Alan is a risk manager for Acme University, a higher education institution located in the western United States. He is concerned about the threat that an earthquake will damage his organization's primary datacenter. He recently undertook a replacement cost analysis and determined that the datacenter is valued at $10 million.
After consulting with seismologists, Alan determined that an earthquake is expected in the area of the datacenter once every 200 years. Datacenter specialists and architects helped him determine that an earthquake would likely cause $5 million in damage to the facility.
- Based on the information in this scenario, what is the exposure factor (EF) for the effect of an earthquake on Acme University's datacenter?
- 10%
- 25%
- 50%
- 75%
- Based on the information in this scenario, what is the annualized rate of occurrence (ARO) for an earthquake at the datacenter?
- 0.0025
- 0.005
- 0.01
- 0.015
- Based on the information in this scenario, what is the annualized loss expectancy (ALE) for an earthquake at the datacenter?
- $25,000
- $50,000
- $250,000
- $500,000
- Referring to the previous scenario, if Alan's organization decides to move the datacenter to a location where earthquakes are not a risk, what risk management strategy are they using?
- Risk mitigation
- Risk avoidance
- Risk acceptance
- Risk transference
- Referring to the previous scenario, if the organization decides not to relocate the datacenter but instead purchases an insurance policy to cover the replacement cost of the datacenter, what risk management strategy are they using?
- Risk mitigation
- Risk avoidance
- Risk acceptance
- Risk transference
- Referring to the previous scenario, assume that the organization decides that relocation is too difficult and the insurance is too expensive. They instead decide that they will carry on despite the risk of earthquake and handle the impact if it occurs. What risk management strategy are they using?
- Risk mitigation
- Risk avoidance
- Risk acceptance
- Risk transference
- Under the U.S. government's data classification scheme, which one of the following is the lowest level of classified information?
- Private
- Top Secret
- Confidential
- Secret
- When using a data loss prevention (DLP) system, which of the following statements best describes the purpose of labeling data with classifications?
- DLP systems can adjust classifications dynamically as needs change.
- DLP systems can use labels to apply appropriate security policies.
- DLP systems can use labels to perform file access control.
- DLP systems can use labels to perform data minimization tasks.
- Carlos is preparing a password policy for his organization and would like it to be fully compliant with Payment Card Industry Data Security Standard (PCI DSS) requirements. What is the minimum password length required by PCI DSS?
- 7 characters
- 8 characters
- 10 characters
- 12 characters
- Colin would like to implement a security control in his accounting department which is specifically designed to detect cases of fraud that are able to occur despite the presence of other security controls. Which one of the following controls is best suited to meet Colin's need?
- Separation of duties
- Least privilege
- Dual control
- Mandatory vacations
- Singh would like to apply encryption to protect data in transit from his web server to remote users. What technology would best fulfill this need?
- SSL
- DLP
- FDE
- TLS
- Rob is an auditor reviewing the payment process used by a company to issue checks to vendors. He notices that Helen, a staff accountant, is the person responsible for creating new vendors. Norm, another accountant, is responsible for issuing payments to vendors. Helen and Norm are cross-trained to provide backup for each other. What security issue, if any, exists in this situation?
- Least privilege violation
- Separation of duties violation
- Dual control violation
- No issue
- Mei recently completed a risk management review and identified that the organization is susceptible to a man-in-the-middle attack. After review with her manager, they jointly decided that accepting the risk is the most appropriate strategy. What should Mei do next?
- Implement additional security controls
- Design a remediation plan
- Repeat the business impact assessment
- Document the decision
- Robin is planning to conduct a risk assessment in her organization. She is concerned that it will be difficult to perform the assessment because she needs to include information about both tangible and intangible assets. What would be the most effective risk assessment strategy for her to use?
- Quantitative risk assessment
- Qualitative risk assessment
- Combination of quantitative and qualitative risk assessment
- Neither quantitative nor qualitative risk assessment
- Barry's organization is running a security exercise and Barry was assigned to conduct offensive operations. What term best describes Barry's role in the process?
- Red team
- Black team
- Blue team
- White team
- Vlad's organization recently suffered an attack where a senior system administrator executed some malicious commands and then deleted the log files that recorded his activity. Which one of the following controls would best mitigate the risk of this activity recurring in the future?
- Separation of duties
- Two-person control
- Job rotation
- Security awareness
- Vlad's organization recently underwent a security audit that resulted in a finding that the organization fails to promptly remove the accounts associated with users who have left the organization. This resulted in at least one security incident where a terminated user logged into a corporate system and took sensitive information. What identity and access management control would best protect against this risk?
- Automated deprovisioning
- Quarterly user account reviews
- Separation of duties
- Two-person control
- Jay is the CISO for his organization and is responsible for conducting periodic reviews of the organization's information security policy. The policy was written three years ago and has undergone several minor revisions after audits and assessments. Which one of the following would be the most reasonable frequency to conduct formal reviews of the policy?
- Monthly
- Quarterly
- Annually
- Every five years
- Terri is undertaking a risk assessment for her organization. Which one of the following activities would normally occur first?
- Risk identification
- Risk calculation
- Risk mitigation
- Risk management
- Ang is selecting an encryption technology for use in encrypting the contents of a USB drive. Which one of the following technologies would best meet his needs?
- TLS
- DES
- AES
- SSL
- Suki's organization has a policy that restricts them from doing any business with any customer that would subject them to the terms of the General Data Protection Regulation (GDPR). Which one of the following controls would best help them achieve this objective?
- Encryption
- Tokenization
- Geographic access requirements
- Data sovereignty
- Vivian would like to be able to identify files that originated in her organization but were later copied. What security control would best achieve this objective?
- Encryption
- Data masking
- Watermarking
- Tokenization
- Kai is attempting to determine whether he can destroy a cache of old records that he discovered. What type of policy would most directly answer his question?
- Data ownership
- Data classification
- Data minimization
- Data retention
- Fences are a widely used security control that can be described by several different control types. Which one of the following control types would least describe a fence?
- Deterrent
- Corrective
- Preventive
- Physical
- Ian is designing an authorization scheme for his organization's deployment of a new accounting system. He is considering putting a control in place that would require that two accountants approve any payment request over $100,000. What security principle is Ian seeking to enforce?
- Security through obscurity
- Least privilege
- Separation of duties
- Dual control
- Which one of the following frameworks best helps organizations design IT processes that fit together seamlessly?
- NIST CSF
- ITIL
- COBIT
- ISO 27001
- Carmen is working with a new vendor on the design of a penetration test. She would like to ensure that the vendor does not conduct any physical intrusions as part of their testing. Where should Carmen document this requirement?
- Rules of engagement
- Service level agreement
- Nondisclosure agreement
- Counterparty agreement
- Which one of the following categories best describes information protected by HIPAA?
- PII
- SPI
- PHI
- PCI DSS
- In a data management program, which role bears ultimate responsibility for the safeguarding of sensitive information?
- Data owner
- System owner
- Business owner
- Data custodian
- Lakshman is investigating the data management techniques used to protect sensitive information in his organization's database and comes across the database table shown here. What data management technique is most likely being used?
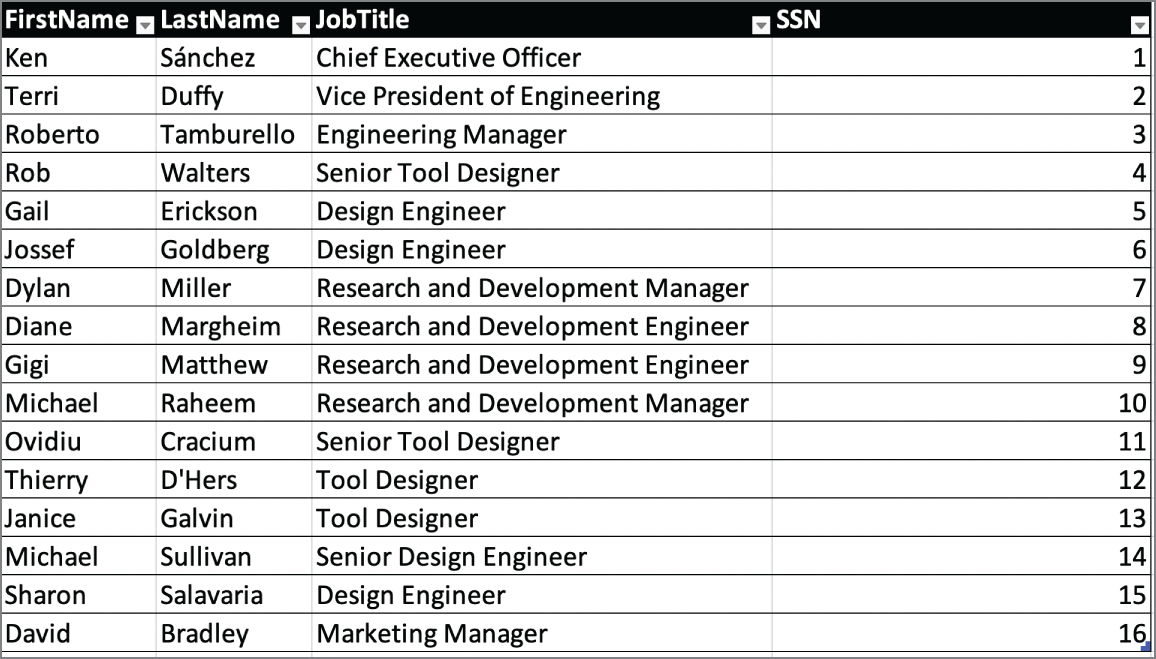
- Masking
- Encryption
- Minimization
- Tokenization
- Lakshman continues to explore the database and finds another copy of the table in a different system that stores information as shown here. What technique was most likely used in this system?
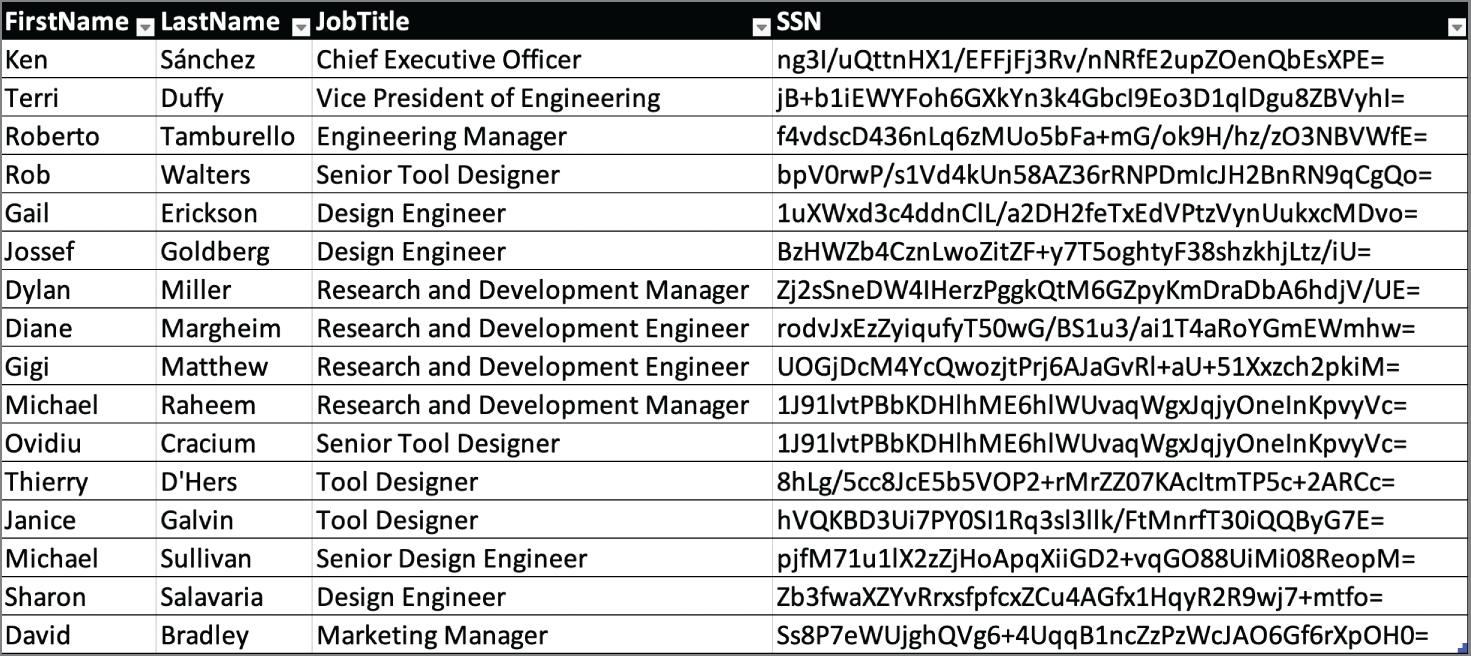
- Masking
- Encryption
- Minimization
- Tokenization
- After reviewing the systems, Lakshman discovers a printed roster of employees that contains the information shown in this image. What type of data protection has most likely been applied to this report?
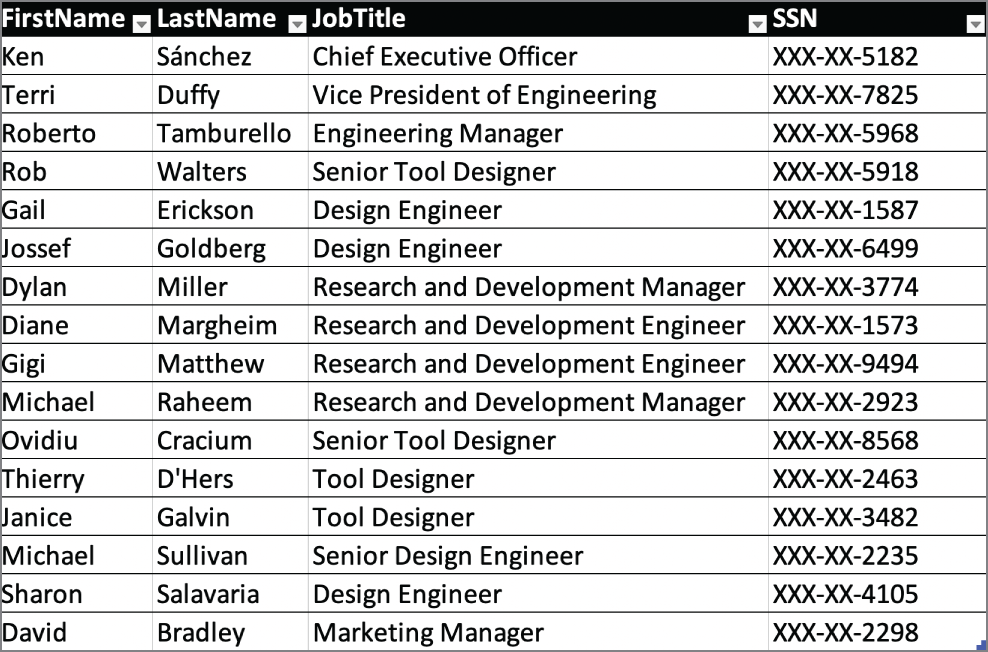
- Masking
- Encryption
- Minimization
- Tokenization
- The board of directors of Kate's company recently hired an independent firm to review the state of the organization's security controls and certify those results to the board. What term best describes this engagement?
- Assessment
- Control review
- Gap analysis
- Audit
- Gavin is drafting a document that provides a detailed step-by-step process that users may follow to connect to the VPN from remote locations. Alternatively, users may ask IT to help them configure the connection. What term best describes this document?
- Policy
- Procedure
- Standard
- Guideline
- Which one of the following is not one of the five core security functions defined by the NIST Cybersecurity Framework?
- Respond
- Recover
- Protect
- Review
- Which one of the following security controls is designed to help provide continuity for security responsibilities?
- Succession planning
- Separation of duties
- Mandatory vacation
- Dual control
- After conducting a security review, Oskar determined that his organization is not conducting regular backups of critical data. What term best describes the type of control gap that exists in Oskar's organization?
- Preventive
- Corrective
- Detective
- Deterrent
- Tim is helping his organization shift resources to the cloud. He is conducting vendor due diligence on the organization's IaaS provider. Which one of the following risks is this effort most likely to reduce?
- Security group misconfiguration
- Operating system misconfiguration
- Data exfiltration
- Provider viability
- Carla is reviewing the cybersecurity policies used by her organization. What policy might she put in place as a failsafe to cover employee behavior situations where no other policy directly applies?
- Data monitoring policy
- Account management policy
- Code of conduct
- Data ownership policy
- Which one of the following items is not normally included in a request for an exception to security policy?
- Description of a compensating control
- Description of the risks associated with the exception
- Proposed revision to the security policy
- Business justification for the exception
- Mike's organization adopted the COBIT standard, and Mike would like to find a way to measure their progress toward implementation. Which one of the following COBIT components is useful as an assessment tool?
- Process descriptions
- Control objectives
- Management guideline
- Maturity models
- What policy should contain provisions for removing user access upon termination?
- Data ownership policy
- Data classification policy
- Data retention policy
- Account management policy
- Suki is the CISO at a major nonprofit hospital group. Which one of the following regulations most directly covers the way that her organization handles medical records?
- HIPAA
- FERPA
- GLBA
- SOX
Questions 74–76 refer to the following scenario:
Karen is the CISO of a major manufacturer of industrial parts. She is currently performing an assessment of the firm's financial controls, with an emphasis on implementing security practices that will reduce the likelihood of theft from the firm.
- Karen would like to ensure that the same individual is not able to both create a new vendor in the system and authorize a payment to that vendor. She is concerned that an individual who could perform both of these actions would be able to send payments to false vendors. What type of control should Karen implement?
- Mandatory vacations
- Separation of duties
- Job rotation
- Two-person control
- The accounting department has a policy that requires the signatures of two individuals on checks valued over $5,000. What type of control do they have in place?
- Mandatory vacations
- Separation of duties
- Job rotation
- Two-person control
- Karen would also like to implement controls that would help detect potential malfeasance by existing employees. Which one of the following controls is least likely to detect malfeasance?
- Mandatory vacations
- Background investigations
- Job rotation
- Privilege use reviews
- Chris is concerned about the possibility that former employees will disclose sensitive personal information about customers to unauthorized individuals. What is the best mechanism that Chris can use to manage this risk?
- NDA
- AUP
- Privacy policy
- Data ownership policy
- Kevin is conducting a security exercise for his organization that uses both offensive and defensive operations. His role is to serve as the moderator of the exercise and to arbitrate disputes. What role is Kevin playing?
- White team
- Red team
- Swiss team
- Blue team
- Dan is the chief information security officer (CISO) for a bank in the United States. What law most directly governs the personal customer information that his bank handles?
- HIPAA
- PCI DSS
- GLBA
- SOX
- Bohai is concerned about access to the master account for a cloud service that his company uses to manage payment transactions. He decides to implement a new process for multifactor authentication to that account where an individual on the IT team has the password to the account, while an individual in the accounting group has the token. What security principle is Bohai using?
- Dual control
- Separation of duties
- Least privilege
- Security through obscurity
- Tina is preparing for a penetration test and is working with a new vendor. She wants to make sure that the vendor understands exactly what technical activities are permitted within the scope of the test. Where should she document these requirements?
- MOA
- Contract
- RoE
- SLA
- Azra is reviewing a draft of the Domer Doodads information security policy and finds that it contains the following statements. Which one of these statements would be more appropriately placed in a different document?
- Domer Doodads designates the Chief Information Security Officer as the individual with primary responsibility for information security.
- The Chief Information Security Officer is granted the authority to create specific requirements that implement this policy.
- All access to financial systems must use multifactor authentication for remote connections.
- Domer Doodads considers cybersecurity and compliance to be of critical importance to the business.
- Ben is conducting an assessment of an organization's cybersecurity program using the NIST Cybersecurity Framework. He is specifically interested in the organization's external participation and determines that the organization has a good understanding of how it relates to customers on cybersecurity matters but does not yet have a good understanding of similar relationships with suppliers. What tier rating is appropriate for this measure?
- Partial
- Risk Informed
- Repeatable
- Adaptive
- Which one of the following security policy framework documents never includes mandatory employee compliance?
- Policy
- Guideline
- Procedure
- Standard
- Kaitlyn is on the red team during a security exercise and she has a question about whether an activity is acceptable under the exercise's rules of engagement. Who would be the most appropriate person to answer her question?
- Red team leader
- White team leader
- Blue team leader
- Kaitlyn should act without external advice.
- Quinn encounters a document that contains information that is not intended for use outside of his company but would generally not cause any serious damage if accidentally disclosed. What data classification would be most appropriate for this document?
- Internal
- Sensitive
- Highly Sensitive
- Public
Questions 87–91 refer to the following scenario.
Seamus is conducting a business impact assessment for his organization. He is attempting to determine the risk associated with a denial-of-service attack against his organization's datacenter.
Seamus consulted with various subject matter experts and determined that the attack would not cause any permanent damage to equipment, applications, or data. The primary damage would come in the form of lost revenue. Seamus believes that the organization would lose $75,000 in revenue during a successful attack.
Seamus also consulted with his threat management vendor, who considered the probability of a successful attack against his organization and determined that there is a 10% chance of a successful attack in the next 12 months.
- What is the ARO for this assessment?
- 0.8%
- 10%
- 12%
- 100%
- What is the SLE for this scenario?
- $625
- $6,250
- $7,500
- $75,000
- What is the ALE for this scenario?
- $625
- $6,250
- $7,500
- $75,000
- Seamus is considering purchasing a DDoS protection system that would reduce the likelihood of a successful attack. What type of control is he considering?
- Detective
- Corrective
- Preventive
- Deterrent
- Seamus wants to make sure that he can accurately describe the category of the DDoS protection service to auditors. Which term best describes the category of this control?
- Compensating
- Physical
- Operational
- Technical
- Piper's organization handles credit card information and is, therefore, subject to the Payment Card Industry Data Security Standard (PCI DSS). What term best describes this standard?
- Prescriptive
- Minimal
- Optional
- Risk-based
- As Piper attempts to implement the PCI DSS requirements, she discovers that she is unable to meet one of the requirements because of a technical limitation in her point-of-sale system. She decides to work with regulators to implement a second layer of logical isolation to protect this system from the Internet to allow its continued operation despite not meeting one of the requirements. What term best describes the type of control Piper has implemented?
- Physical control
- Operational control
- Compensating control
- Deterrent control
- When Piper implements this new isolation technology, what type of risk management action is she taking?
- Risk acceptance
- Risk avoidance
- Risk transference
- Risk mitigation
- What is the proper ordering of the NIST Cybersecurity Framework tiers, from least mature to most mature?
- Partial; Repeatable; Risk Informed; Adaptive
- Risk Informed; Partial; Adaptive; Repeatable
- Risk Informed; Partial; Repeatable; Adaptive
- Partial; Risk Informed; Repeatable; Adaptive
- Ruth is helping a business leader determine the appropriate individuals to consult about sharing information with a third-party organization. Which one of the following policies would likely contain the most relevant guidance for her?
- Data retention policy
- Information security policy
- Data validation policy
- Data ownership policy
- Samantha is investigating a cybersecurity incident where an internal user used his computer to participate in a denial-of-service attack against a third party. What type of policy was most likely violated?
- AUP
- SLA
- BCP
- Information classification policy
- Ryan is compiling a list of allowable encryption algorithms for use in his organization. What type of document would be most appropriate for this list?
- Policy
- Standard
- Guideline
- Procedure
- Julie is refreshing her organization's cybersecurity program using the NIST Cybersecurity Framework. She would like to use a template that describes how a specific organization might approach cybersecurity matters. What element of the NIST Cybersecurity Framework would best meet Julie's needs?
- Framework Scenarios
- Framework Core
- Framework Implementation Tiers
- Framework Profiles
- What types of organizations are required to adopt the ISO 27001 standard for cybersecurity?
- Healthcare organizations
- Financial services firms
- Educational institutions
- None of the above
- During the design of an identity and access management authorization scheme, Katie took steps to ensure that members of the security team who can approve database access requests do not have access to the database themselves. What security principle is Katie most directly enforcing?
- Least privilege
- Separation of duties
- Dual control
- Security through obscurity
- Which one of the following controls is useful to both facilitate the continuity of operations and serve as a deterrent to fraud?
- Succession planning
- Dual control
- Cross-training
- Separation of duties
- Which one of the following requirements is often imposed by organizations as a way to achieve their original control objective when they approve an exception to a security policy?
- Documentation of scope
- Limited duration
- Compensating control
- Business justification
- In the ITIL service life cycle shown here, what core activity is represented by the X?

- Continual service improvement
- Service design
- Service operation
- Service transition
- Berta is reviewing the security procedures surrounding the use of a cloud-based online payment service by her company. She set the access permissions for this service so that the same person cannot add funds to the account and transfer funds out of the account. What security principle is most closely related to Berta's action?
- Least privilege
- Security through obscurity
- Separation of duties
- Dual control
- Thomas found himself in the middle of a dispute between two different units in his business that are arguing over whether one unit may analyze data collected by the other. What type of policy would most likely contain guidance on this issue?
- Data ownership policy
- Data classification policy
- Data retention policy
- Account management policy
- Mara is designing a new data mining system that will analyze access control logs for signs of unusual login attempts. Any suspicious logins will be automatically locked out of the system. What type of control is Mara designing?
- Physical control
- Operational control
- Managerial control
- Technical control
- Which one of the following elements is least likely to be found in a data retention policy?
- Minimum retention period for data
- Maximum retention period for data
- Description of information to retain
- Classification of information elements
- Which one of the following issues would be better classified as a privacy issue, rather than a security issue?
- Use of information for a purpose other than was originally disclosed
- Unpatched vulnerability on a web server
- Improper file permissions for a group of employees
- Accidental destruction of backup media
