Chapter 3
Domain 3: Cyber Incident Response
EXAM OBJECTIVES COVERED IN THIS CHAPTER:
 3.1 Given a scenario, distinguish threat data or behavior to determine the impact of an incident.
3.1 Given a scenario, distinguish threat data or behavior to determine the impact of an incident.- Threat classification
- Factors contributing to incident severity and prioritization
 3.2 Given a scenario, prepare a toolkit and use appropriate forensics tools during an investigation.
3.2 Given a scenario, prepare a toolkit and use appropriate forensics tools during an investigation.- Forensics kit
- Forensic investigation suite
 3.3 Explain the importance of communication during the incident response process.
3.3 Explain the importance of communication during the incident response process.- Stakeholders
- Purpose of communication processes
- Role-based responsibilities
 3.4 Given a scenario, analyze common symptoms to select the best course of action to support incident response.
3.4 Given a scenario, analyze common symptoms to select the best course of action to support incident response.- Common network-related symptoms
- Common host-related symptoms
- Common application-related symptoms
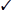 3.5 Summarize the incident recovery and post-incident response process.
3.5 Summarize the incident recovery and post-incident response process.- Containment techniques
- Eradication techniques
- Validation
- Corrective actions
- Incident summary report
-
If Lucca wants to validate the application files he has downloaded from the vendor of his application, what information should he request from them?
- File size and file creation date
- MD5 hash
- Private key and cryptographic hash
- Public key and cryptographic hash
-
Jeff discovers multiple .jpg photos during his forensic investigation of a computer involved in an incident. When he runs exiftool to gather file metadata, which information is not likely to be part of the images even if they have complete metadata intact?
- GPS location
- Camera type
- Number of copies made
- Correct date/timestamp
-
Chris wants to run John the Ripper against a Linux system’s passwords. What does he need to attempt password recovery on the system?
- Both /etc/passwd and /etc/shadow
- /etc/shadow
- /etc/passwd
- Chris cannot recover passwords; only hashes are stored.
-
Charles needs to review the permissions set on a directory structure on a Window system he is investigating. Which Sysinternals tool will provide him with this functionality?
- DiskView
- AccessEnum
- du
- AccessChk
-
John has designed his network as shown here and places untrusted systems that want to connect to the network into the Guests network segment. What is this type of segmentation called?

- Proactive network segmentation
- Isolation
- Quarantine
- Removal
-
The organization that Alex works for classifies security related events using NIST’s standard definitions. Which classification should he use when he discovers key logging software on one of his frequent business traveler’s laptop?
- An event
- An adverse event
- A security incident
- A policy violation
-
Jennifer is planning to deploy rogue access point detection capabilities for her network. If she wants to deploy the most effective detection capability she can, which of the following detection types should she deploy first?
- Authorized MAC
- Authorized SSID
- Authorized channel
- Authorized vendor
-
Dan is designing a segmented network that places systems with different levels of security requirements into different subnets with firewalls and other network security devices between them. What phase of the incident response process is Dan in?
- Post-incident activity
- Detection and analysis
- Preparation
- Containment, eradication, and recovery
-
The company that Brian works for processes credit cards and is required to be compliant with PCI-DSS. If Brian’s company experiences a breach of card data, what type of disclosure will they be required to provide?
- Notification to local law enforcement
- Notification to their acquiring bank
- Notification to federal law enforcement
- Notification to Visa and MasterCard
-
Lauren wants to create a backup of Linux permissions before making changes to the Linux workstation she is attempting to remediate. What Linux tool can she use to back up the permissions of an entire directory on the system?
- chbkup
- getfacl
- aclman
- There is not a common Linux permission backup tool.
-
While working to restore systems to their original configuration after a long-term APT compromise, Charles has three options.
- He can restore from a backup and then update patches on the system.
- He can rebuild and patch the system using original installation media and application software using his organization’s build documentation.
He can remove the compromised accounts and rootkit tools and then fix the issues that allowed the attackers to access the systems.
Which option should Charles choose in this scenario?
- Option A
- Option B
- Option C
- None of the above. Charles should hire a third party to assess the systems before proceeding.
-
Jessica wants to access a macOS FileVault 2–encrypted drive. Which of the following methods is not a possible means of unlocking the volume?
- Change the FileVault key using a trusted user account.
- Retrieve the key from memory while the volume is mounted.
- Acquire the recovery key.
- Extract the keys from iCloud.
-
Susan discovers the following log entries that occurred within seconds of each other in her Squert (a Sguil web interface) console. What have her network sensors most likely detected?
- A failed database connection from a server
- A denial-of-service attack
- A port scan
- A misconfigured log source
-
Frank wants to log the creation of user accounts on a Windows 7 workstation. What tool should he use to enable this logging?
- secpol.msc
- auditpol.msc
- regedit
- Frank does not need to make a change; this is a default setting.
-
If Danielle wants to purge a drive, which of the following options will accomplish her goal?
- Cryptographic erase
- Reformat
- Overwrite
- Repartition
-
Cynthia wants to build scripts to detect malware beaconing behavior. Which of the following is not a typical means of identifying malware beaconing behavior on a network?
- Persistence of the beaconing
- Beacon protocol
- Beaconing interval
- Removal of known traffic
-
While performing post-rebuild validation efforts, Scott scans a server from a remote network and sees no vulnerabilities. Joanna, the administrator of the machine, runs a scan and discovers two critical vulnerabilities and five moderate issues. What is most likely causing the difference in their reports?
- Different patch levels during the scans
- They are scanning through a load balancer.
- There is a firewall between the remote network and the server.
- Scott or Joanna ran the vulnerability scan with different settings.
-
As part of his organization’s cooperation in a large criminal case, Adam’s forensic team has been asked to send a forensic image of a highly sensitive compromised system in RAW format to an external forensic examiner. What steps should Adam’s team take prior to sending a drive containing the forensic image?
- Encode in EO1 format and provide a hash of the original file on the drive.
- Encode in FTK format and provide a hash of the new file on the drive.
- Encrypt the RAW file and transfer a hash and key under separate cover.
- Decrypt the RAW file and transfer a hash under separate cover.
-
Mika wants to analyze the contents of a drive without causing any changes to the drive. What method is best suited to ensuring this?
- Set the “read-only” jumper on the drive.
- Use a write blocker.
- Use a read blocker.
- Use a forensic software package.

-
What type of forensic investigation–related form is shown here?
- Chain of custody
- Report of examination
- Forensic discovery log
- Policy custody release
-
Lisa is following the CompTIA process for validation after a compromise. Which of the following actions should be included in this phase?
- Sanitization
- Re-imaging
- Setting permissions
- Secure disposal
-
Eric has access to a full suite of network monitoring tools and wants to use appropriate tools to monitor network bandwidth consumption. Which of the following is not a common method of monitoring network bandwidth usage?
- SNMP
- Portmon
- Packet sniffing
- Netflow
-
James wants to determine whether other Windows systems on his network are infected with the same malware package that he has discovered on the workstation he is analyzing. He has removed the system from his network by unplugging its network cable, as required by corporate policy. He knows that the system has previously exhibited beaconing behavior and wants to use that behavior to identify other infected systems. How can he safely create a fingerprint for this beaconing without modifying the infected system?
- Plug the system in to the network and capture the traffic quickly at the firewall using Wireshark.
- Plug the system into an isolated switch and use a span port or tap and Wireshark to capture traffic.
- Review the ARP cache for outbound traffic.
- Review the Windows firewall log for traffic logs.
-
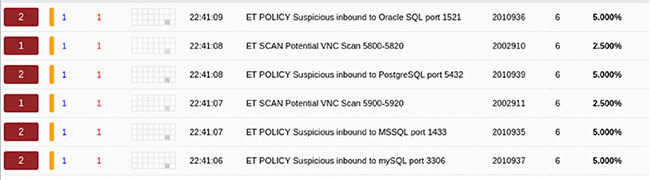
Fred is attempting to determine whether a user account is accessing other systems on his network and uses lsof to determine what files the user account has open. What information should he identify when faced with the following lsof output?
- The user account demo is connected from remote.host.com to a local system.
- The user demo has replaced the /bash executable with one they control.
- The user demo has an outbound connection to remote.host.com.
- The user demo has an inbound ssh connection and has replaced the bash binary.
-
After completing an incident response process and providing a final report to management, what step should Casey use to identify improvement to her incident response plan?
- Update system documentation.
- Conduct a lessons-learned session.
- Review patching status and vulnerability scans.
- Engage third-party consultants.
-
The senior management at the company that Kathleen works for is concerned about rogue devices on the network. If Kathleen wants to identify rogue devices on her wired network, which of the following solutions will quickly provide the most accurate information?
- A discovery scan using a port scanner.
- Router and switch-based MAC address reporting.
- A physical survey.
- Reviewing a central administration tool like SCCM.
-
While investigating a system error, Lauren runs the df command on a Linux box that she is the administrator for. What problem and likely cause should she identify based on this listing?
# df -h /var/
Filesystem Size Used Avail Use% Mounted on
/dev/sda1 40G 11.2G 28.8 28% /
/dev/sda2 3.9G 3.9G 0 100% /var
- The var partition is full and needs to be wiped.
- Slack space has filled up and needs to be purged.
- The var partition is full, and logs should be checked.
- The system is operating normally and will fix the problem after a reboot.
-
In order, which set of Linux permissions are least permissive to most permissive?
- 777, 444, 111
- 544, 444, 545
- 711, 717, 117
- 111, 734, 747
-
As Lauren prepares her organization’s security practices and policies, she wants to address as many threat vectors as she can using an awareness program. Which of the following threats can be most effectively dealt with via awareness?
- Attrition
- Impersonation
- Improper usage
- Web
-
Scott wants to recover user passwords for systems as part of a forensic analysis effort. If he wants to test for the broadest range of passwords, which of the following modes should he run John the Ripper in?
- Single crack mode
- Wordlist mode
- Incremental mode
- External mode
-
During a forensic investigation, Charles discovers that he needs to capture a virtual machine that is part of the critical operations of his company’s website. If he cannot suspend or shut down the machine for business reasons, what imaging process should he follow?
- Perform a snapshot of the system, boot it, suspend the copied version, and copy the directory it resides in.
- Copy the virtual disk files and then use a memory capture tool.
- Escalate to management to get permission to suspend the system to allow a true forensic copy.
- Use a tool like the Volatility Framework to capture the live machine completely.
-
Mika, a computer forensic examiner, receives a PC and its peripherals that were seized as forensic evidence during an investigation. After she signs off on the chain of custody log and starts to prepare for her investigation, one of the first things she notes is that each cable and port was labeled with a color-coded sticker by the on-site team. Why are the items labeled like this?
- To ensure chain of custody
- To ensure correct re-assembly
- To allow for easier documentation of acquisition
- To tamper-proof the system
-
Laura needs to create a secure messaging capability for her incident response team. Which of the following methods will provide her with a secure messaging tool?
- Text messaging
- A Jabber server with TLS enabled
- Email with TLS enabled
- A messaging application that uses the Signal protocol
-
While reviewing her Nagios logs, Selah discovers the error message shown here. What should she do about this error?

- Check for evidence of a port scan.
- Review the Apache error log.
- Reboot the server to restore the service.
- Restart the Apache service.
-
Alex needs to sanitize hard drives that will be leaving his organization after a lease is over. The drives contained information that his organization classifies as sensitive data that competitors would find valuable if they could obtain it. Which choice is the most appropriate to ensure that data exposure does not occur during this process?
- Clear, validate, and document.
- Purge the drives.
- Purge, validate, and document.
- The drives must be destroyed to ensure no data loss.
-
Selah is preparing to collect a forensic image for a Macintosh computer. What hard drive format is she most likely to encounter?
- FAT32
- MacFAT
- HFS+
- NTFS
-
During a forensic analysis of an employee’s computer as part of a human resources investigation into misuse of company resources, Tim discovers a program called Eraser installed on the PC. What should Tim expect to find as part of his investigation?
- A wiped C: drive
- Antiforensic activities
- All slack space cleared
- Temporary files and Internet history wiped
-
Jessica wants to recover deleted files from slack space and needs to identify where the files begin and end. What is this process called?
- Slacking
- Data carving
- Disk recovery
- Header manipulation
-
Lauren is the IT manager for a small company and occasionally serves as the organization’s information security officer. Which of the following roles should she include as the leader of her organization’s CSIRT?
- Her lead IT support staff technician
- Her organization’s legal counsel
- A third-party IR team lead
- She should select herself.
-
During her forensic analysis of a Windows system, Cynthia accesses the registry and checks \HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsNTCurrentVersionWinlogin. What domain was the system connected to, and what was the username that would appear at login?

- Admin, administrator
- No domain, admin
- Legal, admin
- Corporate, no default username
-
Lauren wants to ensure that the two most commonly used methods for preventing Linux buffer overflow attacks are enabled for the operating system she is installing on her servers. What two related technologies should she investigate to help protect her systems?
- The NX bit and ASLR
- StackAntismash and DEP
- Position-independent variables and ASLR
- DEP and the position-independent variables
-
Angela is attempting to determine when a user account was created on a Windows 10 workstation. What method is her best option if she believes the account was created recently?
- Check the System log.
- Check the user profile creation date.
- Check the Security log.
- Query the registry for the user ID creation date.
-
Alex suspects that an attacker has modified a Linux executable using static libraries. Which of the following Linux commands is best suited to determining whether this has occurred?
- file
- stat
- strings
- grep
-
Lauren wants to detect administrative account abuse on a Windows server that she is responsible for. What type of auditing permissions should she enable to determine whether users with administrative rights are making changes?
- Success
- Fail
- Full control
- All
-
Cameron believes that the Ubuntu Linux system that he is restoring to service has already been fully updated. What command can he use to check for new updates, and where can he check for the history of updates on his system?
- apt-get -u upgrade, /var/log/apt
- rpm -i upgrade, /var/log/rpm
- upgrade -l, /var/log/upgrades
- apt-get install -u; Ubuntu Linux does not provide a history of updates
-
Adam wants to quickly crack passwords from a Windows 7 system. Which of the following tools will provide the fastest results in most circumstances?
- John the Ripper
- Cain and Abel
- Ophcrack
- Hashcat
-
Because of external factors, Eric has only a limited time period to collect an image from a workstation. If he collects only specific files of interest, what type of acquisition has he performed?
- Logical
- Bit-by-bit
- Sparse
- None of the above
-
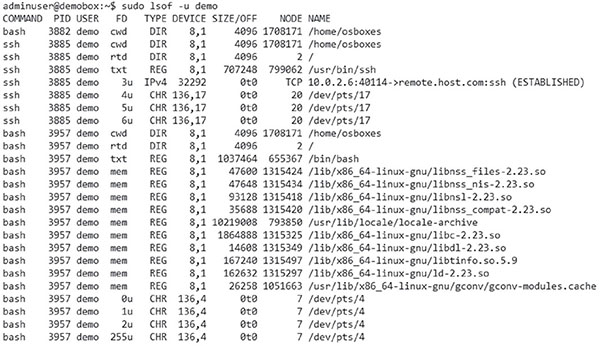
Kelly sees high CPU utilization in the Windows Task Manager, as shown here, while reviewing a system’s performance issues. If she wants to get a detailed view of the CPU usage by application, with PIDs and average CPU usage, what native Windows tool can she use to gather that detail?
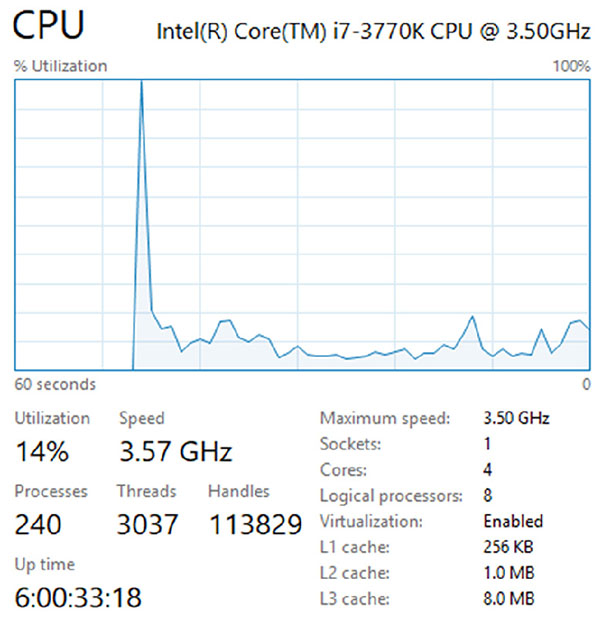
- Resource Monitor
- Task Manager
- iperf
- Perfmon
-
During a forensic investigation, Steve records information about each drive, including where it was acquired, who made the forensic copy, the MD5 hash of the drive, and other details. What term describes the process Steve is using as he labels evidence with details of who acquired and validated it?
- Direct evidence
- Circumstantial evidence
- Incident logging
- Chain of custody
-
Roger’s SolarWinds monitoring system provides Windows memory utilization reporting. Use the chart shown here to determine what actions Roger should take based on his monitoring.

- The memory usage is stable and can be left as it is.
- The memory usage is high and must be addressed.
- Roger should enable automatic memory management.
- There is not enough information to make a decision.
-
NIST defines five major types of threat information types in NIST SP 800-150, “Guide to Cyber Threat Information Sharing.”
- Indicators, which are technical artifacts or observables that suggest an attack is imminent, currently underway, or compromise may have already occurred
- Tactics, techniques, and procedures that describe the behavior of an actor
- Security alerts like advisories and bulletins
- Threat intelligence reports that describe actors, systems, and information being targeted and the methods being used
- Tool configurations that support collection, exchange, analysis, and use of threat information
Which of these should Frank seek out to help him best protect the midsize organization he works for against unknown threats?
- 1, 2, and 5
- 1, 3, and 5
- 2, 4, and 5
- 1, 2, and 4
-
Alex wants to determine whether the user of a company-owned laptop accessed a malicious wireless access point. Where can he find the list of wireless networks that the system knows about?
- The registry
- The user profile directory
- The wireless adapter cache
- Wireless network lists are not stored after use.
-
Fred wants to prevent buffer overflows from succeeding against his organization’s web applications. What technique is best suited to preventing this type of attack from succeeding?
- User input canonicalization
- User input size checking
- Format string validation
- Buffer overwriting
-
Susan needs to perform forensics on a virtual machine. What process should she use to ensure she gets all of the forensic data she may need?
- Suspend the machine and copy the contents of the directory it resides in.
- Perform a live image of the machine.
- Suspend the machine and make a forensic copy of the drive it resides on.
- Turn the virtual machine off and make a forensic copy of it.
-
Allison wants to access Chrome logs as part of a forensic investigation. What format is information about cookies, history, and saved form fill information saved in?
- SQLite
- Plain text
- Base64 encoded text
- NoSQL
-
While Chris is attempting to image a device, he encounters write issues and cannot write the image as currently set. What issue is he most likely encountering?

- The files need to be compressed.
- The destination drive is formatted FAT32.
- The destination drive is formatted NTFS.
- The files are encrypted.
-
Christina is configuring her SolarWinds alerts for rogue devices and wants to select an appropriate reset condition for rogue MAC address alerts. Which of the options shown here is best suited to handling rogue devices if she wants to avoid creating additional work for her team?
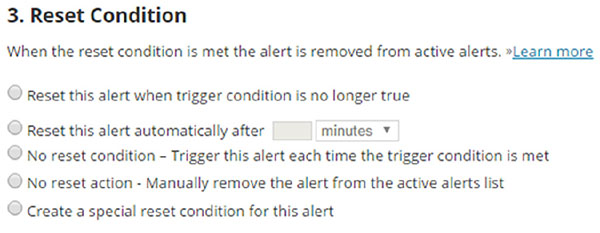
- Reset when no longer true.
- Reset after a time period.
- No reset condition; trigger each time condition is met.
- No reset action; manually remove the alert from the active alerts list.
-
Fred needs to validate the MD5 checksum of a file on a Windows system but is not allowed to install any programs and cannot run files from external media or drives. What Windows utility can he use to get the MD5 hash of the file?
- md5sum
- certutil
- sha1sum
- hashcheck
-
Which of the following is not an important part of the incident response communication process?
- Limiting communication to trusted parties
- Disclosure based on public feedback
- Using a secure method of communication
- Preventing accidental release of incident-related information
-
Alex is diagnosing major network issues at a large organization and sees the following graph in her PRTG console on the “outside” interface of her border router. What can Alex presume has occurred?
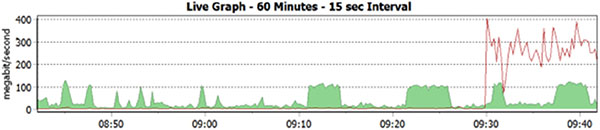
- The network link has failed.
- A DDoS is in progress.
- An internal system is transferring a large volume of data.
- The network link has been restored.
-
Which of the following commands is not useful for determining the list of network interfaces on a Linux system?
- ifconfig
- netstat -i
- ip link show
- intf -q
-
What Windows memory protection methodology is shown here?

- DEP
- ASLR
- StackProtect
- MemShuffle
-
Forensic investigation shows that the target of the investigation used the Windows Quick Format command to attempt to destroy evidence on a USB thumb drive. Which of the NIST sanitization techniques has the target of the investigation used in their attempt to conceal evidence?
- Clear
- Purge
- Destroy
- None of the above
-
Angela wants to use her network security device to detect potential beaconing behavior. Which of the following options is best suited to detecting beaconing using her network security device?
- Antivirus definitions
- File reputation
- IP reputation
- Static file analysis
-
During an incident response process Susan plugs a system back into the network, allowing it normal network access. What phase of the incident response process is Susan performing?
- Preparation
- Detection and analysis
- Containment, eradication, and recovery
- Post-incident activity
-
A server in the data center that Chris is responsible for monitoring unexpectedly connects to an off-site IP address and transfers 9GB of data to the remote system. What type of monitoring should Chris enable to best assist him in detecting future events of this type?
- Flow logs with heuristic analysis
- SNMP monitoring with heuristic analysis
- Flow logs with signature based detection
- SNMP monitoring with signature-based detection
-
Jennifer’s team has completed the initial phases of their incident response process and is assessing the time required to recover from the incident. Using the NIST recoverability effort categories, the team has determined that they can predict the time to recover but will require additional resources. How should she categorize this using the NIST model?
- Regular
- Supplemented
- Extended
- Not recoverable
-
Which of the following mobile device forensic techniques is not a valid method of isolation during forensic examination?
- Use a forensic SIM.
- Buy and use a forensic isolation appliance.
- Place the device in an antistatic bag.
- Put the device in airplane mode.
-
Rick wants to monitor permissions and ownership changes of critical files on the Red Hat Linux system he is responsible for. What Linux tool can he use to do this?
- watchdog
- auditctl
- dirwatch
- monitord
-
Janet is attempting to conceal her actions on a company-owned computer. As part of her cleanup attempts, she deletes all of the files she downloaded from a corporate file server using a browser in incognito mode. How can a forensic investigator determine what files she downloaded?
- Network flows
- SMB logs
- Browser cache
- Drive analysis
-
Joe is aware that an attacker has compromised a system on his network but wants to continue to observe the attacker’s efforts as they continue their attack. If Joe wants to prevent additional impact on his network while watching what the attacker does, what containment method should he use?
- Removal
- Isolation
- Segmentation
- Detection
-
When Charles arrived at work this morning, he found an email in his inbox that read, “Your systems are weak; we will own your network by the end of the week.” How would he categorize this sign of a potential incident if he was using the NIST SP 800-61 descriptions of incident signs?
- An indicator
- A threat
- A risk
- A precursor
-
During an incident response process, Cynthia conducts a lessons-learned review. What phase of the incident response process is she in?
- Preparation
- Detection and analysis
- Containment, eradication, and recovery
- Post-incident recovery
-
As part of his incident response program, Allan is designing a playbook for zero-day threats. Which of the following should not be in his plan to handle them?
- Segmentation
- Patching
- Using threat intelligence
- Whitelisting
-
As the CISO of her organization, Jennifer is working on an incident classification scheme and wants to base her design on NIST’s definitions. Which of the following options should she use to best describe a user accessing a file that they are not authorized to view?
- An incident
- An event
- An adverse event
- A security incident
-
Fred wants to identify digital evidence that can place an individual in a specific place at a specific time. Which of the following types of digital forensic data is not commonly used to attempt to document physical location at specific times?
- Cell phone GPS logs
- Photograph metadata
- Cell phone tower logs
- Microsoft Office document metadata
-
Cynthia has completed the validation process of her media sanitization efforts and has checked a sample of the drives she had purged using a built-in cryptographic wipe utility. What is her next step?
- Resample to validate her testing.
- Destroy the drives.
- Documentation
- She is done and can send the drives on for disposition.
-
In his role as a small company’s information security manager, Mike has a limited budget for hiring permanent staff. While his team can handle simple virus infections, he does not currently have a way to handle significant information security incidents. Which of the following options should Mike investigate to ensure that his company is prepared for security incidents?
- Outsource to a third-party SOC.
- Create an internal SOC.
- Hire an internal incident response team.
- Outsource to an incident response provider.
-
The Stuxnet attack relied on engineers who transported malware with them, crossing the air gap between networks. What type of threat is most likely to cross an air-gapped network?
- Web
- Removable media
- Attrition
-
While reviewing his network for rogue devices, Dan notes that a system with MAC address D4:BE:D9:E5:F9:18 has been connected to a switch in one of the offices in his building for three days. What information can this provide Dan that may be helpful if he conducts a physical survey of the office?
- The operating system of the device
- The user of the system
- The vendor who built the system
- The type of device that is connected
-
Frank wants to ensure that media has been properly sanitized. Which of the following options properly lists sanitization descriptions from least to most effective?
- Purge, clear, destroy
- Eliminate, eradicate, destroy
- Clear, purge, destroy
- Eradicate, eliminate, destroy
-
Degaussing is an example of what form of media sanitization?
- Clearing
- Purging
- Destruction
- It is not a form of media sanitization.
-
While reviewing storage usage on a Windows system, Brian checks the volume shadow copy storage as shown here:
C:WINDOWSsystem32>vssadmin list Shadowstorage
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2013 Microsoft Corp.
Shadow Copy Storage association
For volume: (C:)\?Volume{c3b53dae-0e54-13e3-97ab-806e6f6e69633}
Shadow Copy Storage volume: (C:)\?Volume{c3b53dae-0e54-13e3-97ab-806e6f6e6963}
Used Shadow Copy Storage space: 25.6 GB (2%)
Allocated Shadow Copy Storage space: 26.0 GB (2%)
Maximum Shadow Copy Storage space: 89.4 GB (10%)
What purpose does this storage serve, and can he safely delete it?
- It provides a block-level snapshot and can be safely deleted.
- It provides secure hidden storage and can be safely deleted.
- It provides secure hidden storage and cannot be safely deleted.
- It provides a block-level snapshot and cannot be safely deleted.
-
Near the end of a typical business day, Danielle is notified that her organization’s email servers have been blacklisted because of email that appears to originate from her domain. What information does she need to start investigating the source of the spam emails?
- Firewall logs showing SMTP connections
- The SMTP audit log from her email server
- The full headers of one of the spam messages
- Network flows for her network
-
Lauren recovers a number of 16GB and 32GB microSD cards during a forensic investigation. Without checking them manually, what filesystem type is she most likely to find them formatted in as if they were used with a digital camera?
- RAW
- FAT16
- FAT32
- HFS+
-
While checking for bandwidth consumption issues, Alex uses the ifconfig command on the Linux box that he is reviewing. He sees that the device has sent less than 4Gb of data, but his network flow logs show that the system has sent over 20Gb. What problem has Alex encountered?
- A rootkit is concealing traffic from the Linux kernel.
- Flow logs show traffic that does not reach the system.
- ifconfig resets traffic counters at 4Gb.
- ifconfig only samples outbound traffic and will not provide accurate information.
-
After arriving at an investigation site, Brian determines that three powered-on computers need to be taken for forensic examination. What steps should he take before removing the PCs?
- Power them down, take pictures of how each is connected, and log each system in as evidence.
- Take photos of each system, power them down, and attach a tamper-evident seal to each PC.
- Collect live forensic information, take photos of each system, and power them down.
- Collect a static drive image, validate the hash of the image, and securely transport each system.
-
In his role as a forensic examiner, Lucas has been asked to produce forensic evidence related to a civil case. What is this process called?
- Criminal forensics
- E-discovery
- Cyber production
- Civil tort
-
During their organization’s incident response preparation, Charles and Linda are identifying critical information assets that the company uses. Included in their organizational data sets is a list of customer names, addresses, phone numbers, and demographic information. How should Charles and Linda classify this information?
- PII
- Intellectual property
- PHI
- PCI-DSS
-
As Lauren studies her company’s computer forensics playbook, she notices that forensic investigators are required to use a chain of custody form. What information would she record on that form if she was conducting a forensic investigation?
- The list of individuals who made contact with files leading to the investigation
- The list of former owners or operators of the PC involved in the investigation
- All individuals who work with evidence in the investigation
- The police officers who take possession of the evidence
-
Scott needs to ensure that the system he just rebuilt after an incident is secure. Which type of scan will provide him with the most useful information to meet his goal?
- An authenticated vulnerability scan from a trusted internal network
- An unauthenticated vulnerability scan from a trusted internal network
- An authenticated scan from an untrusted external network
- An unauthenticated scan from an untrusted external network
-
What is the primary role of management in the incident response process?
- Leading the CSIRT
- Acting as the primary interface with law enforcement
- Providing authority and resources
- Assessing impact on stakeholders
-
While reviewing his OSSEC SIEM logs, Chris notices the following entries. What should his next action be if he wants to quickly identify the new user’s creation date and time?
![Table shows examples for [OSSEC] New group added to system (5901, 5902).](http://images-20200215.ebookreading.net/9/2/2/9781119433200/9781119433200__comptia-cysa-practice__9781119433200__images__c03uf013.jpg)
- Check the user.log for a new user.
- Check syslog for a new user.
- Check /etc/passwd for a new user.
- Check auth.log for a new user.
-
Jessica wants to track the changes made to the registry and filesystem while running a suspect executable on a Windows system. Which Sysinternals tool will allow her to do this?
- App Monitor
- Resource Tracker
- Process Monitor
- There is not a Sysinternals tool with this capability.
-
Frank wants to improve the effectiveness of the incident analysis process he is responsible for as the leader of his organization’s CSIRT. Which of the following is not a commonly recommended best practice based on NIST’s guidelines?
- Profile networks and systems to measure the characteristics of expected activity.
- Perform event correlation to combine information from multiple sources.
- Maintain backups of every system and device.
- Capture network traffic as soon as an incident is suspected.
-
NIST describes four major phases in the incident response cycle. Which of the following is not one of the four?
- Containment, eradication, and recovery
- Notification and communication
- Detection and analysis
- Preparation
-
Charles wants to perform memory forensics on a Windows system and wants to access pagefile.sys. When he attempts to copy it, he receives the following error. What access method is required to access the page file?
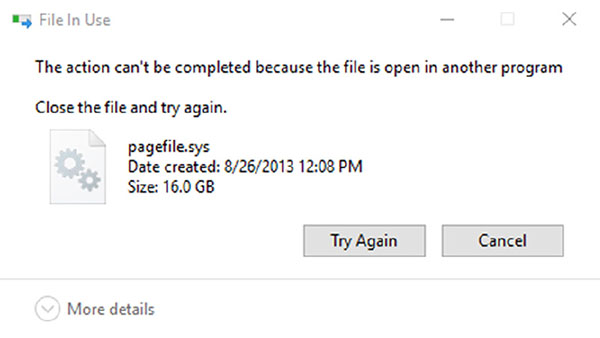
- Run Windows Explorer as an administrator and repeat the copy.
- Open the file using fmem.
- Run cmd.exe as an administrator and repeat the copy.
- Shut the system down, remove the drive, and copy it from another system.
-
Chris wants to prevent evil twin attacks from working on his wireless network. Which of the following is not a useful method for detecting evil twins?
- Check for BSSID.
- Check the SSID.
- Check the attributes (channel, cipher, authentication method).
- Check for tagged parameters like the organizational unique identifier.
-
Where is slack space found in the following Windows partition map?

- The System Reserved partition
- The System Reserved and Unallocated partitions
- The System Reserved and C: partitions
- The C: and unallocated partitions
-
Luke needs to verify settings on a macOS computer to ensure that the configuration items he expects are set properly. What type of file is commonly used to store configuration settings for macOS systems?
- The registry
- .profile files
- Plists
- .config files
-
Adam needs to determine the proper retention policy for his organization’s incident data. If he wants to follow common industry practices and does not have specific legal or contractual obligations that he needs to meet, what time frame should he select?
- 30 days
- 90 days
- 1 to 2 years
- 7 years
-
The system that Alice has identified as the source of beaconing traffic is one of her organization’s critical e-commerce servers. To maintain her organization’s operations, she needs to quickly restore the server to its original, uncompromised state. What criteria is most likely to be impacted the most by this action?
- Damage to the system or service
- Service availability
- Ability to preserve evidence
- Time and resources needed to implement the strategy
-
After law enforcement was called because of potential criminal activity discovered as part of a forensic investigation, the officers on the scene seized three servers. When can Joe expect his servers to be returned?
- After 30 days, which provides enough time for a reasonable imaging process.
- After 6 months, as required by law.
- After 1 year, as most cases resolve in that amount of time.
- Joe should not plan on a time frame for return.
-
Lauren wants to create a forensic image that third-party investigators can use but does not know what tool the third-party investigation team that her company intends to engage will use. Which of the following forensic formats should she choose if she wants almost any forensic tool to be able to access the image?
- E01
- AFF
- RAW
- AD1
-
After Janet’s attempts to conceal her downloads of important corporate information were discovered, forensic investigators learned that she frequently copied work files to a USB drive. Which of the following is not a possible way to manually check her Windows workstation for a list of previously connected USB drives?
- Check the security audit logs.
- Check the setupapi log file.
- Search the registry.
- Check the user’s profile.
-
As part of his forensic investigation, Scott intends to make a forensic image of a network share that is mounted by the PC that is the focus of his investigation. What information will he be unable to capture?
- File creation dates
- Deleted files
- File permission data
- File metadata
-
NIST SP 800-61 identifies six outside parties that an incident response team will typically communicate with. Which of the following is not one of those parties?
- Customers, constituents, and media
- Internet service providers
- Law enforcement agencies
- Legal counsel
-
What common incident response follow-up activity includes asking questions like “What additional tools or resources are needed to detect or analyze future events?”
- Preparation
- Lessons-learned review
- Evidence gathering
- Procedural analysis
-
Susan has been asked to capture forensic data from a Windows PC and needs to ensure that she captures the data in their order of volatility. Which order is correct from most volatile to least volatile?
- Network traffic, CPU cache, disk drives, optical media
- CPU cache, network traffic, disk drives, optical media
- Optical media, disk drives, network traffic, CPU cache
- Network traffic, CPU cache, optical media, disk drives
-
During an incident response process, Susan heads to a compromised system and pulls its network cable. What phase of the incident response process is Susan performing?
- Preparation
- Detection and analysis
- Containment, eradication, and recovery
- Post-incident activity
-
Scott needs to verify that the forensic image he has created is an exact duplicate of the original drive. Which of the following methods is considered forensically sound?
- Create a MD5 hash
- Create a SHA-1 hash
- Create a SHA-2 hash
- All of the above
-
What strategy does NIST suggest for identifying attackers during an incident response process?
- Use geographic IP tracking to identify the attacker’s location.
- Contact upstream ISPs for assistance in tracking down the attacker.
- Contact local law enforcement so that they can use law enforcement–specific tools.
- Identifying attackers is not an important part of the incident response process.
-
Rick is conducting a forensic investigation of a compromised system. He knows from user reports that issues started at approximately 3:30 p.m. on June 12. Using the SANS SIFT open source forensic tool, what process should he use to determine what occurred?
- Search the drive for all files that were changed between 3 and 4 p.m.
- Create a Super Timeline.
- Run anti-malware and search for newly installed malware tools during that time frame.
- Search system logs for events between 3 and 4 p.m.
-
Charles believes that an attacker may have added accounts and attempted to obtain extra rights on a Linux workstation. Which of the following is not a common way to check for unexpected accounts like this?
- Review /etc/passwd and /etc/shadow for unexpected accounts.
- Check /home/ for new user directories.
- Review /etc/sudoers for unexpected accounts.
- Check /etc/groups for group membership issues.
-
Ben wants to coordinate with other organizations in the information security community to share data and current events as well as warnings of new security issues. What type of organization should he join?
- An ISAC
- A CSIRT
- A VPAC
- An IRT
-
While investigating a spam email, Adam is able to capture headers from one of the email messages that was received. He notes that the sender was Carmen Victoria Garci. What facts can he gather from the headers shown here?

- Victoria Garci’s email address is [email protected].
- The sender sent via Yahoo.
- The sender sent via a system in Japan.
- The sender sent via Gmail.
-
Lauren needs to access a macOS system but does not have the user’s password. If the system is not FileVaulted, which of the following options is not a valid recovery method?
- Use Single User mode to reset the password.
- Use Recovery mode to recover the password.
- Use Target Disk mode to delete the Keychain.
- Reset the password from another privileged user account.
-
While performing forensic analysis of an iPhone backup, Cynthia discovers that she has only some of the information that she expects the phone to contain. What is the most likely scenario that would result in the backup she is using having partial information?
- The backup was interrupted.
- The backup is encrypted.
- The backup is a differential backup.
- The backup is stored in iCloud.
-
Chris wants to ensure that his chain of custody documentation will stand up to examination in court. Which of the following options will provide him with the best documentary proof of his actions?
- A second examiner acting as a witness and countersigning all actions
- A complete forensic log book signed and sealed by a notary public
- A documented forensic process with required sign-off
- Taking pictures of all independent forensic actions
-
Cynthia is reviewing her organization’s incident response recovery process, which is outlined here. Which of the following recommendations should she make to ensure that further issues do not occur during the restoration process?

- Change passwords before restoring from backup.
- Isolate the system before restoring from backups.
- Securely wipe the drive before restoration.
- Vulnerability scan before patching.
-
After zero wiping a system’s hard drive and rebuilding it with all security patches and trusted accounts, Lauren is notified that the system is once again showing signs of compromise. Which of the following types of malware package cannot survive this type of eradication effort?
- An MBR-resident malware tool
- A UEFI-resident malware
- A BIOS-resident malware
- A slack space–resident malware package
-
Patents, copyrights, trademarks, and trade secrets are all related to what type of data?
- PII
- PHI
- Corporate confidential
- Intellectual property
-
Which of the following issues is not commonly associated with BYOD devices?
- Increased network utilization
- Increased device costs
- Increased support tickets
- Increased security risk
-
Saria is reviewing the contents of a drive as part of a forensic effort and notes that the file she is reviewing takes up more space on the disk than its actual size, as shown here. What has she discovered?
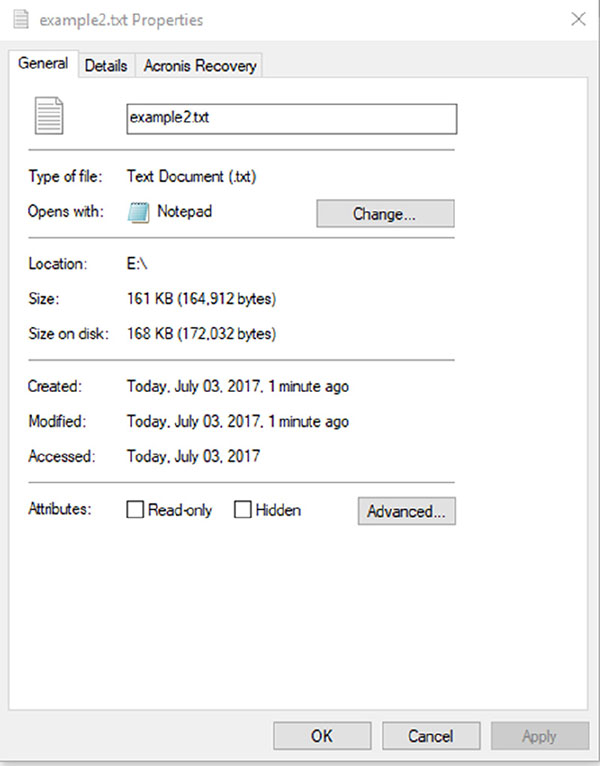
- Slack space
- Hidden content
- Sparse files
- Encryption overhead
-
What is the minimum retention period for incident data for U.S. federal government agencies?
- 90 days
- 1 year
- 3 years
- 7 years
-
Kathleen is restoring a critical business system to operation after a major compromise and needs to validate that the operating system and application files are legitimate and do not have any malicious code included in them. What type of tool should she use to validate this?
- A trusted system binary kit
- Dynamic code analysis
- Static code analysis
- File rainbow tables
-
Charles wants to verify that authentication to a Linux service has two-factor authentication settings set as a requirement. Which common Linux directory can he check for this type of setting, listed by application, if the application supports it?
- /etc/pam.d
- /etc/passwd
- /etc/auth.d
- /etc/tfa
-
Charles is creating the evidence log for a computer that was part of an attack on an external third-party system. What network-related information should he include in that log if he wants to follow NIST’s recommendations?
- Subnet mask, DHCP server, hostname, MAC address
- IP addresses, MAC addresses, host name
- Domain, hostname, MAC addresses, IP addresses
- NIC manufacturer, MAC addresses, IP addresses, DHCP configuration
-
Chris believes that systems on his network have been compromised by an advanced persistent threat actor. He has observed a number of large file transfers outbound to remote sites via TLS-protected HTTP sessions from systems that do not typically send data to those locations. Which of the following techniques is most likely to detect the APT infections?
- Network traffic analysis
- Network forensics
- Endpoint behavior analysis
- Endpoint forensics
-
After submitting a suspected malware package to VirusTotal, Alex receives the following results. What does this tell Alex?
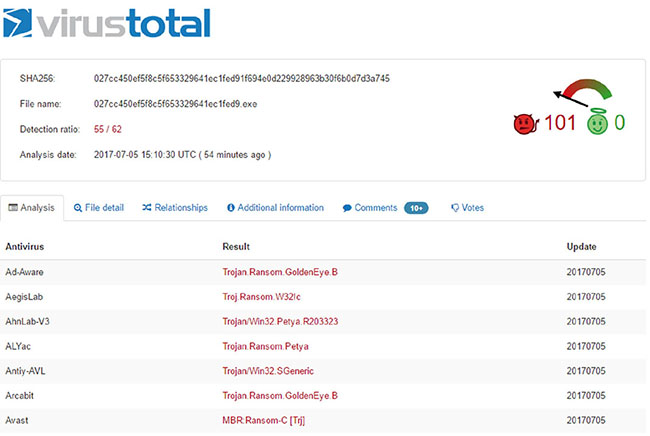 [https://drive.google.com/open?id=0B4u5n3PsqCBjcXNOVmtROEZFUFE]
[https://drive.google.com/open?id=0B4u5n3PsqCBjcXNOVmtROEZFUFE]- The submitted file contains more than one malware package.
- Antivirus vendors use different names for the same malware.
- VirusTotal was unable to specifically identify the malware.
- The malware package is polymorphic, and matches will be incorrect.
-
Ben is investigating a potential malware infection of a laptop belonging to a senior manager in the company he works for. When the manager opens a document, website, or other application that takes user input, words start to appear as though they are being typed. What is the first step that Ben should take in his investigation?
- Run an antivirus scan.
- Disconnect the system from the network.
- Wipe the system and reinstall.
- Observe and record what is being typed.
-
Kathleen’s forensic analysis of a laptop that is believed to have been used to access sensitive corporate data shows that the suspect tried to overwrite the data they downloaded as part of antiforensic activities by deleting the original files and then copying other files to the drive. Where is Kathleen most likely to find evidence of the original files?
- The MBR
- Unallocated space
- Slack space
- The FAT
-
As part of a test of her network’s monitoring infrastructure, Kelly uses snmpwalk to validate her router SNMP settings. She executes snmpwalk as shown here:
snmpwalk -c public 10.1.10.1 -v1
iso.3.6.1.2.1.1.0 = STRING: "RouterOS 3.6"
iso.3.6.1.2.1.2.0 = OID: iso.3.6.1.4.1.30800
iso.3.6.1.2.1.1.3.0 = Timeticks: (1927523) 08:09:11
iso.3.6.1.2.1.1.4.0 = STRING: "root"
iso.3.6.1.2.1.1.5.0 = STRING: "RouterOS"
...
Which of the following pieces of information is not something she can discover from this query?
- SNMP v1 is enabled.
- The community string is public.
- The community string is root.
- The contact name is root.
-
Laura needs to check on memory, CPU, disk, network, and power usage on a Mac. What GUI tool can she use to check these?
- Resource Monitor
- System Monitor
- Activity Monitor
- Sysradar
-
Angela wants to access the decryption key for a BitLocker-encrypted system, but the system is currently turned off. Which of the following methods is a viable method if a Windows system is turned off?
- Hibernation file analysis
- Memory analysis
- Boot-sector analysis
- Brute-force cracking
-
Adam believes that a system on his network is infected but does not know which system. To detect it, he creates a query for his network monitoring software based on the following pseudocode. What type of traffic is he most likely trying to detect?
destip: [*] and duration < 10 packets and destbytes < 3000 and flowcompleted = true
and application = http or https or tcp or unknown and content != uripath:* and content
!= contentencoding:*
- Users browsing malicious sites
- Adware
- Beaconing
- Outbound port scanning
-
Casey’s search for a possible Linux backdoor account during a forensic investigation has led her to check through the filesystem for issues. Where should she look for back doors associated with services?
- /etc/passwd
- /etc/xinetd.conf
- /etc/shadow
- $HOME/.ssh/
-
As an employee of the U.S. government, Megan is required to use NIST’s information impact categories to classify security incidents. During a recent incident, proprietary information was changed. How should she classify this incident?
- As a privacy breach
- As an integrity loss
- As a proprietary breach
- As an availability breach
-
During what stage of an event is preservation of evidence typically handled?
- Preparation
- Detection and analysis
- Containment, eradication, and recovery
- Post-incident activity
-
Susan is reviewing event logs to determine who has accessed a workstation after business hours. When she runs secpol.msc on the Windows system she is reviewing, she sees the following settings. What important information will be missing from her logs?

- Login failures
- User IDs from logins
- Successful logins
- Times from logins
-
Cynthia runs the command shown here while checking usage of her Linux system. Which of the following statements is true based on the information shown?
![Image shows programing code with commands such as [user1@demo~] dollar netstat -at, et cetera, and table shows columns for proto, recv-Q, send-Q, local address, foreign address, and state.](http://images-20200215.ebookreading.net/9/2/2/9781119433200/9781119433200__comptia-cysa-practice__9781119433200__images__c03uf021.jpg)
- There are two users logged in remotely via ssh.
- There is an active exploit in progress using the Monkeycom exploit.
- The local system is part of the demo.com domain.
- The system is not providing any UDP services.
-
Lucas wants to purge a drive to ensure that data cannot be extracted from it when it is sent off-site. Which of the following is not a valid option for purging hard drives on a Windows system?
- Use the built-in Windows sdelete command line.
- Use Eraser.
- Use DBAN.
- Encrypt the drive and then delete the key.
-
The company that Charleen works for has been preparing for a merger, and during a quiet phase she discovers that the corporate secure file server that contained the details of the merger has been compromised. As she works on her report, how should she most accurately categorize the data that was breached?
- PII
- PHI
- Intellectual property
- Corporate confidential data
-
Which of the following is not a valid use case for live forensic imaging?
- Malware analysis
- Encrypted drives
- Postmortem forensics
- Nonsupported filesystems
-
Which of the following commands is the standard way to determine how old a user account is on a Linux system if [username] is replaced by the user ID that you are checking?
- userstat [username]
- ls -ld /home/[username]
- aureport -auth | grep [username]
- None of the above
-
Profiling networks and systems can help to identify unexpected activity. What type of detection can be used once a profile has been created?
- Dynamic analysis
- Anomaly analysis
- Static analysis
- Behavioral analysis
-
While reviewing the actions taken during an incident response process, Jennifer is informed by the local desktop support staff person that the infected machine was returned to service by using a Windows system restore point. Which of the following items will a Windows system restore return to a previous state?
- Personal files
- Malware
- Windows system files
- All installed apps
-
During a major incident response effort, Ben discovers evidence that a critical application server may have been the data repository and egress point in the compromise he is investigating. If he is unable to take the system offline, which of the following options will provide him with the best forensic data?
- Reboot the server and mount the system drive using a USB-bootable forensic suite.
- Create an image using a tool like FTK Imager Lite.
- Capture the system memory using a tool like Volatility.
- Install and run an imaging tool on the live server.
-
Charles wants to monitor file permission changes on a Windows system he is responsible for. What audit category should he enable to allow this?
- File Permissions
- User Rights
- Filesystem
- Audit Objects
-
Charles finds the following entries on a Linux system in /var/log/auth.log. If he is the only user with root privileges, requires two-factor authentication to log in as root, and did not take the actions shown, what should he check for?
![Sheet shows text which reads Jun 20, 21:44:02 kali useradd[1433]: new group: name equals demo, GID equals 1000, et cetera.](http://images-20200215.ebookreading.net/9/2/2/9781119433200/9781119433200__comptia-cysa-practice__9781119433200__images__c03uf022.jpg)
[https://drive.google.com/open?id=0B4u5n3PsqCBjTDViWHhycjhhSzQ]
- A hacked root account
- A privilege escalation attack from a lower privileged account or service
- A malware infection
- A RAT
-
A disgruntled former employee uses the systems she was responsible for to slow down the network that Chris is responsible for protecting during a critical business event. What NIST threat classification best fits this type of attack?
- Impersonation
- Attrition
- Improper usage
- Web
-
As part of his forensic analysis of a series of photos, John runs exiftool for each photo. He receives the following listing from one photo. What useful forensic information can he gather from this photo?

- The original creation date, the device type, the GPS location, and the creator’s name
- The endian order of the file, the file type, the GPS location, and the scene type
- The original creation date, the device type, the GPS location, and the manufacturer of the device
- The MIME type, the GPS time, the GPS location, and the creator’s name
-
During the preparation phase of his organization’s incident response process, Ben gathers a laptop with useful software including a sniffer and forensics tools, thumb drives and external hard drives, networking equipment, and a variety of cables. What is this type of pre-prepared equipment commonly called?
- A grab bag
- A jump kit
- A crash cart
- A first responder kit
-
Chris is analyzing Chrome browsing information as part of a forensic investigation. After querying the visits table that Chrome stores, he discovers a 64-bit integer value stored as “visit time” listed with a value of 131355792940000000. What conversion does he need to perform on this data to make it useful?
- The value is in seconds since January 1, 1970.
- The value is in seconds since January 1, 1601.
- The value is a Microsoft timestamp and can be converted using the time utility.
- The value is an ISO 8601–formatted date and can be converted with any ISO time utility.
-
Cynthia needs to ensure that the workstations she is responsible for have received a critical Windows patch. Which of the following methods should she avoid using to validate patch status for Windows 10 systems?
- Check the Update History manually.
- Run the Microsoft Baseline Security Analyzer.
- Create and run a PowerShell script to search for the specific patch she needs to check.
- Use SCCM to validate patch status for each machine on her domain.
-
As John proceeds with a forensic investigation involving numerous images, he finds a directory labeled Downloaded from Facebook. The images appear relevant to his investigation, so he processes them for metadata using exiftool. The following image shows the data provided. What forensically useful information can John gather from this output?
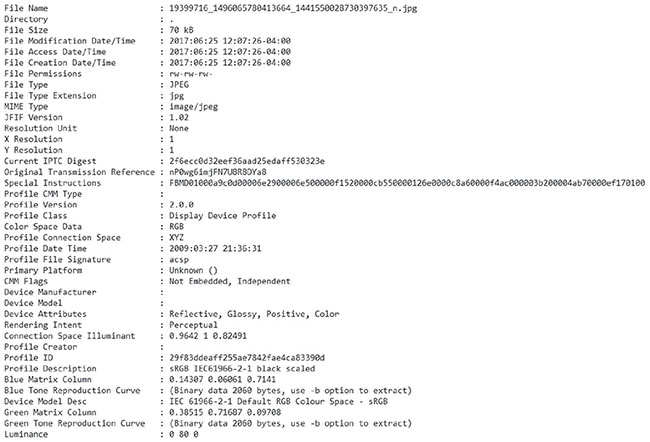
- The original file creation date and time
- The device used to capture the image
- The original digest (hash) of the file, allowing comparison to the original
- None; Facebook strips almost all useful metadata from images.
-
The hospital that Ben works at is required to be HIPAA compliant and needs to protect HIPAA data. Which of the following is not an example of PHI?
- Names of individuals
- Records of health care provided
- Records of payment for healthcare
- Individual educational records
-
Ben works at a U.S. federal agency that has experienced a data breach. Under FISMA, which organization does he have to report this incident to?
- US-CERT
- The National Cyber Security Authority
- The National Cyber Security Center
- CERT/CC
-
Which of the following properly lists the order of volatility from least volatile to most volatile?
- Printouts, swap files, CPU cache, RAM
- Hard drives, USB media, DVDs, CD-RWs
- DVDs, hard drives, virtual memory, caches
- RAM, swap files, SSDs, printouts
-
Joe wants to recovery the passwords for local Windows users on a Windows 7 workstation. Where are the password hashes stored?
- C:WindowsSystem32passwords
- C:WindowsSystem32config
- C:WindowsSecureconfig
- C:WindowsSecureaccounts
-
While conducting a forensic review of a system involved in a data breach, Alex discovers a number of Microsoft Word files including files with filenames like critical_data.docx and sales_estimates_2017.docx. When he attempts to review the files using a text editor for any useful information, he finds only unreadable data. What has occurred?
- Microsoft Word files are stored in .zip format.
- Microsoft Word files are encrypted.
- Microsoft Word files can be opened only by Microsoft Word.
- The user has used antiforensic techniques to scramble the data.
-
Rick is attempting to diagnose high memory utilization issues on a macOS system and notices a chart showing memory pressure. What does memory pressure indicate for macOS when the graph is yellow and looks like the following image?
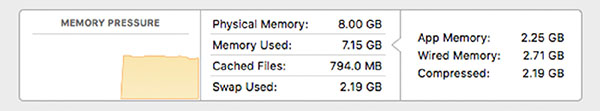
- Memory resources are available.
- Memory resources are available but being tasked by memory management processes.
- Memory resources are in danger, and applications will be terminated to free up memory.
- Memory resources are depleted, and the disk has begun to swap.
-
Lucas believes that one of his users has attempted to use built-in Windows commands to probe servers on the network he is responsible for. How can he recover the command history for that user if the system has been rebooted since the reconnaissance has occurred?
- Check the bash history.
- Open a command prompt window and hit F7.
- Manually open the command history from the user’s profile directory.
- The Windows command prompt does not store command history.
-
While conducting a wireless site survey, Susan discovers two wireless access points that are both using the same MAC address. When she attempts to connect to each, she is sent to a login page for her organization. What should she be worried about?
- A misconfigured access point
- A vendor error
- An evil twin attack
- A malicious MAC attack
-
During an incident response process, Alex discovers a running Unix process that shows that it was run using the command nc -k -l 6667. He does not recognize the service and needs assistance in determining what it is. Which of the following would best describe what he has encountered?
- An IRCC server
- A network catalog server
- A user running a shell command
- A netcat server
-
Angela is conducting an incident response exercise and needs to assess the economic impact to her organization of a $500,000 expense related to an information security incident. How should she categorize this?
- Low impact
- Medium impact
- High impact
- Angela cannot assess the impact with the data given.
-
Chris needs to verify that his Linux system is sending system logs to his SIEM. What method can he use to verify that the events he is generating are being sent and received properly?
- Monitor traffic by running Wireshark on the system.
- Configure a unique event ID and send it.
- Monitor traffic by running Wireshark on the SIEM device.
- Generate a known event and monitor for it.
-
Susan wants to protect the Windows workstations in her domain from buffer overflow attacks. What should she recommend to the domain administrators at her company?
- Install an anti-malware tool.
- Install an antivirus tool.
- Enable DEP in Windows.
- Set VirtualAllocProtection to 1 in the registry.
-
What step follows sanitization of media according to NIST guidelines for secure media handling?
- Reuse
- Validation
- Destruction
- Documentation
-
Joe is responding to a ransomware incident that has encrypted financial and business data throughout the organization, including current payroll and HR data. As events currently stand, payroll cannot be run for the current pay period. If Joe uses the NIST functional impact categories shown here, how should Joe rate this incident?

- Critical
- Medium
- High
- Extended recovery
-
Lauren wants to create a documented chain of custody for the systems that she is handling as part of a forensic investigation. Which of the following will provide her with evidence that systems were not tampered with while she is not working with them?
- A chain of custody log
- Tamper-proof seals
- System logs
- None of the above
-
Matt’s incident response team has collected log information and is working on identifying attackers using that information. What two stages of the NIST incident response process is his time working in?
- Preparation and containment, eradication, and recovery
- Preparation and post-incident activity
- Detection and analysis, and containment, eradication, and recovery
- Containment, eradication, and recovery and post-incident activity
-
Angela wants to understand what a malware package does and executes it in a virtual machine that is instrumented using tools that will track what the program does, what changes it makes, and what network traffic it sends while allowing her to make changes on the system or to click files as needed. What type of analysis has Angela performed?
- Manual code reversing
- Interactive behavior analysis
- Static property analysis
- Dynamic code analysis
-
Ben discovers that the forensic image he has attempted to create has failed. What is the most likely reason for this failure?
- Data was modified.
- The source disk is encrypted.
- The destination disk has bad sectors.
- The data cannot be copied in RAW format.
-
Derek sets up a series of virtual machines that are automatically created in a completely isolated environment. Once created, the systems are used to run potentially malicious software and files. The actions taken by those files and programs are recorded and then reported. What technique is Derek using?
- Sandboxing
- Reverse engineering
- Malware disassembly
- Darknet analysis
-
Chris notices the following entries in his Squert web console (a web console for Sguil IDS data). What should he do next to determine what occurred?
![Table shows example for [OSSEC] user missed password more than one time (2502), [OSSEC] SSHD authentication failed (5716), et cetera.](http://images-20200215.ebookreading.net/9/2/2/9781119433200/9781119433200__comptia-cysa-practice__9781119433200__images__c03uf027.jpg)
- Review ssh logs.
- Disable ssh and then investigate further.
- Disconnect the server from the Internet and then investigate.
- Immediately change his password.
-
Lauren wants to avoid running a program installed by a user that she believes is set with a RunOnce key in the Windows registry but needs to boot the system. What can she do to prevent RunOnce from executing the programs listed in the registry key?
- Disable the registry at boot.
- Boot into Safe Mode.
- Boot with the -RunOnce flag.
- RunOnce cannot be disabled; she will need to boot from external media to disable it first.
-
Joseph wants to determine when a USB device was first plugged into a Windows workstation. What file should he check for this information?
- The registry
- The setupapi log file
- The system log
- The data is not kept on a Windows system.
-
A major new botnet infection that uses a peer-to-peer command-and-control process much like 2007’s Storm botnet has been released. Lauren wants to detect infected systems but knows that peer-to-peer communication is irregular and encrypted. If she wants to monitor her entire network for this type of traffic, what method should she use to catch infected systems?
- Build an IPS rule to detect all peer-to-peer communications that match the botnet’s installer signature.
- Use beaconing detection scripts focused on the command-and-control systems.
- Capture network flows for all hosts and use filters to remove normal traffic types.
- Immediately build a network traffic baseline and analyze it for anomalies.
-
Which of the following activities is not part of the containment and restoration process?
- Minimizing loss
- Identifying the attacker
- Limiting service disruption
- Rebuilding compromised systems
-
Angela has recently taken a new position as the first security analyst that her employer has ever had on staff. During her first week, she discovers that there is no information security policy and that the IT staff do not know what to do during a security incident. Angela plans to stand up a CSIRT to handle incident response. What type of documentation should she provide to describe specific procedures that the CSIRT will use during events like malware infections and server compromise?
- An incident response policy
- An operations manual
- An incident response program
- A playbook
-
What type of attack behavior is shown here?
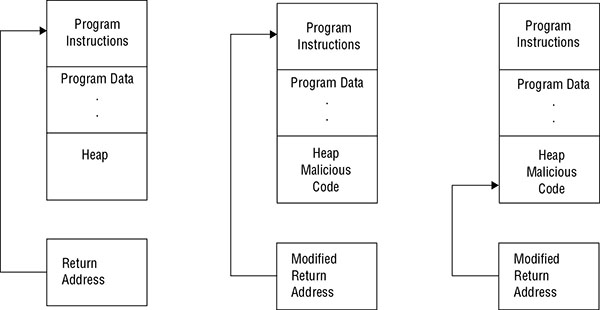
- Kernel override
- RPC rewrite
- Buffer overflow
- Heap hack
-
While investigating a compromise, Jack discovers four files that he does not recognize and believes may be malware. What can he do to quickly and effectively check the files to see whether they are malware?
- Submit them to a site like VirusTotal.
- Open them using a static analysis tool.
- Run strings against each file to identify common malware identifiers.
- Run a local antivirus or anti-malware tool against them.
-
Alex is attempting to determine why a Windows system keeps filling its disk. If she wants to see a graphical view of the contents of the disk that allows her to drill down on each cluster, what Sysinternals tool should she use?
- du
- df
- GraphDisk
- DiskView
-
What useful information cannot be determined from the contents of the $HOME/.ssh folder when conducting forensic investigations of a Linux system?
- Remote hosts that have been connected to
- Private keys used to log in elsewhere
- Public keys used for logins to this system
- Passphrases associated with the keys
-
John believes that the image files he has encountered during a forensic investigation were downloaded from a site on the Internet. What tool can John use to help identify where the files were downloaded from?
- Google reverse image search
- Tineye
- Bing Image Match
- All of the above
-
Brian’s network suddenly stops working at 8:40 AM, interrupting video conferences, streaming, and other services throughout his organization, and then resumes functioning. When Brian logs into his PRTG console and checks his router’s traffic via the primary connection’s redundant network link, he sees the following graph. What should Brian presume occurred based on this information?

- The network failed and is running in cached mode.
- There was a link card failure, and the card recovered.
- His primary link went down, and he should check his secondary link for traffic.
- PRTG stopped receiving flow information and needs to be restarted.
-
Alex needs to create a forensic copy of a BitLocker-encrypted drive. Which of the following is not a method that he could use to acquire the BitLocker key?
- Analyzing the hibernation file
- Analyzing a memory dump file
- Retrieving the key from the MBR
- Performing a FireWire attack on mounted drives
-
Adam works for a large university and sees the following graph in his PRTG console when looking at a year-long view. What behavioral analysis could he leverage based on this pattern?
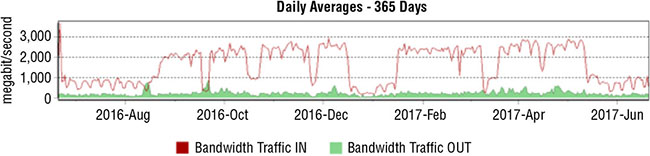
- Identify unexpected traffic during breaks like the low point at Christmas.
- He can determine why major traffic drops happen on weekends.
- He can identify top talkers.
- Adam cannot make any behavioral determinations based on this chart.
-
What is space between the last sector containing logical data and the end of the cluster called?
- Unallocated space
- Ephemeral space
- Slack space
- Unformatted space
-
Frank wants to use netstat to get the process name, the PID, and the username associated with processes that are running on a Linux system he is investigating. What netstat flags will provide him with this information?
- -na
- -pt
- -pe
- -sa
-
Jack is preparing to take a currently running PC back to his forensic lab for analysis. As Jack considers his forensic process, one of his peers recommends that he simply pull the power cable rather than doing a software-based shutdown. Why might Jack choose to follow this advice?
- It will create a crash log, providing useful memory forensic information.
- It will prevent shutdown scripts from running.
- It will create a memory dump, providing useful forensic information.
- It will cause memory-resident malware to be captured, allowing analysis.
-
Amanda has been tasked with acquiring data from an iPhone as part of a mobile forensics effort. At this point, should she remove the SIM (or UICC) card from the device if she receives the device in a powered-on state?
- While powered on, but after logical collection
- While powered on, prior to logical collection
- While powered off, after logical collection
- While powered off, before logical collection
-
Rick wants to validate his recovery efforts and intends to scan a web server he is responsible for with a scanning tool. What tool should he use to get the most useful information about system vulnerabilities?
- Wapiti
- Nmap
- OpenVAS
- ZAP
-
What is the key goal of the containment stage of an incident response process?
- To limit leaks to the press or customers
- To limit further damage from occurring
- To prevent data exfiltration
- To restore systems to normal operation
-
What level of forensic data extraction will most likely be possible and reasonable for a corporate forensic examiner who deals with modern phones that provide filesystem encryption?
- Level 1: Manual extraction
- Level 2: Logical extraction
- Level 3: JTAG or HEX dumping
- Level 4: Chip extraction
-
Angela is performing a forensic analysis of a Windows 10 system and wants to provide an overview of usage of the system using information contained in the Windows registry. Which of the following is not a data element she can pull from the SAM?
- Password expiration setting
- User account type
- Number of logins
- The first time the account logged in
-
Samantha is preparing a report describing the common attack models used by advanced persistent threat actors. Which of the following is a typical characteristic of APT attacks?
- They involve sophisticated DDoS attacks.
- They quietly gather information from compromised systems.
- They rely on worms to spread.
- They use encryption to hold data hostage.
-
During an incident response process, Alice is assigned to gather details about what data was accessed, if it was exfiltrated, and what type of data was exposed. What type of analysis is she doing?
- Information impact analysis
- Economic impact analysis
- Downtime analysis
- Recovery time analysis
-
Angela has discovered an attack that appears to be following the process flow shown here. What type of attack should she identify this as?
- Phishing
- Zero-day exploit
- Whaling
- Advanced persistent threat
Refer to the image shown here for questions 201 to 203.

-
During an e-discovery process, Angela reviews the request from opposing counsel and builds a list of all of the individuals identified. She then contacts the IT staff who support each person to request a list of their IT assets. What phase of the EDRM flow is she in?
- Information governance
- Identification
- Preservation
- Collection
-
During the preservation phase of her work, Angela discovers that information requested as part of the discovery request has been deleted as part of a regularly scheduled data cleanup as required by her organization’s policies. What should Angela do?
- Conduct a forensic recovery of the data.
- Create synthetic data to replace the missing data.
- Report the issue to counsel.
- Purge any other data related to the request based on the same policy.
-
What phase should Angela expect to spend the most person-hours in?
- Identification
- Collection and preservation
- Processing, review, and analysis
- Production
-
The incident response kit that Cassandra is building is based around a powerful laptop so that she can perform on-site drive acquisitions and analysis. If she expects to need to acquire data from both SATA and IDE drives, what item should she include in her kit?
- A write blocker
- A USB hard drive
- A multi-interface drive adapter
- A USB-C cable
-
Which of the following items is not typically found in corporate forensic kits?
- Write blockers
- Crime scene tape
- Label makers
- Decryption tools
-
What incident response tool should Lauren build prior to an incident to ensure that staff can reach critical responders when needed?
- A triage triangle
- A call list
- A call rotation
- A responsibility matrix
-
While performing process analysis on a compromised Linux system, Kathleen discovers a process called “john” that is running. What should she identify as the most likely use of the program?
- Password cracking
- Privilege escalation
- A rootkit
- A user named John’s personal application
-
Which of the following organizations is not typically involved in post-incident communications?
- Developers
- Marketing
- Public relations
- Legal
-
While reviewing system logs, Charles discovers that the processor for the workstation he is reviewing has consistently hit 100% processor utilization by the web browser. After reviewing the rest of the system, no unauthorized software appears to have been installed. What should Charles do next?
- Review the sites visited by the web browser when the CPU utilization issues occur
- Check the browser binary against a known good version
- Reinstall the browser
- Disable TLS
-
Lauren finds that the version of Java installed on her organization’s web server has been replaced. What type of issue is this best categorized as?
- Unauthorized software
- An unauthorized change
- Unexpected input
- A memory overflow
-
Greg finds a series of log entries in his Apache logs showing long strings “AAAAAAAAAAAAAAAAAAAAAAA” followed by strings of characters. What type of attack has he most likely discovered?
- A SQL injection attack
- A denial of service attack
- A memory overflow attack
- A PHP string-ring attack
-
Catherine wants to detect unexpected output from the application she is responsible for managing and monitoring. What type of tool can she use to detect unexpected output effectively?
- A log analysis tool
- A behavior based analysis tool
- A signature based detection tool
- Manual analysis
