INTRODUCTION
Computer security has become paramount as the number of security incidents steadily climbs. Many corporations now spend significant portions of their budget on security hardware, software, services, and personnel. They are spending this money not because it increases sales or enhances the product they provide but because of the possible consequences should they not take protective actions.
Why Focus on Security?
Security is not something that we want to have to pay for; it would be nice if we didn’t have to worry about protecting our data from disclosure, modification, or destruction from unauthorized individuals, but that is not the environment we find ourselves in today. Instead, we have seen the cost of recovering from security incidents steadily rise along with the number of incidents themselves. Cyberattacks and information disclosures are occurring so often that one almost ignores them on the news. But with the theft of over 145 million consumers’ credit data from Equifax, with the subsequent resignation of the CSO and CEO, and hearings in Congress over the role of legislative oversight with respect to critical records, a new sense of purpose with regard to securing data may be at hand. The days of paper reports and corporate “lip service” may be waning, and the time to meet the new challenges of even more sophisticated attackers has arrived. This will not be the last data breach, nor will attackers stop attacking our systems, so our only path forward is to have qualified professionals defending our systems.
A Growing Need for Security Specialists
In order to protect our computer systems and networks, we need a significant number of new security professionals trained in the many aspects of computer and network security. This is not an easy task, as the systems connected to the Internet become increasingly complex with software whose lines of code number in the millions. Understanding why this is such a difficult problem to solve is not hard if you consider just how many errors might be present in a piece of software that is several million lines long. When you add the factor of how fast software is being developed—from necessity, as the market is constantly changing—understanding how errors occur is easy.
Not every “bug” in the software will result in a security hole, but it doesn’t take many to have a drastic effect on the Internet community. We can’t just blame the vendors for this situation, because they are reacting to the demands of government and industry. Many vendors are fairly adept at developing patches for flaws found in their software, and patches are constantly being issued to protect systems from bugs that may introduce security problems. This introduces a whole new problem for managers and administrators—patch management. How important this has become is easily illustrated by how many of the most recent security events have occurred as a result of a security bug that was discovered months prior to the security incident, and for which a patch has been available but the community has not correctly installed it, thus making the incident possible. The reasons for these failures are many, but in the end the solution is a matter of trained professionals at multiple levels in an organization working together to resolve these problems.
But the issue of trained people does not stop with security professionals. Every user, from the board room to the mail room, plays a role in the cybersecurity posture of a firm. Training the non-security professional in the enterprise to use the proper level of care when interacting with systems will not make the problem go away either, but it will substantially strengthen the posture of the enterprise. Understanding the needed training and making it a reality is another task on the security professional’s to-do list.
Because of the need for an increasing number of security professionals who are trained to some minimum level of understanding, certifications such as the CompTIA Security+ have been developed. Prospective employers want to know that the individual they are considering hiring knows what to do in terms of security. The prospective employee, in turn, wants to have a way to demonstrate his or her level of understanding, which can enhance the candidate’s chances of being hired. The community as a whole simply wants more trained security professionals.
The goal of taking the CompTIA Security+ exam is to prove that you’ve mastered the worldwide standards for foundation-level security practitioners. The exam gives you a perfect opportunity to validate your knowledge and understanding of the computer security field, and it is an appropriate mechanism for many different individuals, including network and system administrators, analysts, programmers, web designers, application developers, and database specialists, to show proof of professional achievement in security. According to CompTIA, the exam is aimed at individuals who have
• A minimum of two years of experience in IT administration with a focus on security
• Day-to-day technical information security experience
• Broad knowledge of security concerns and implementation, including the topics that are found in the specific CompTIA Security+ domains
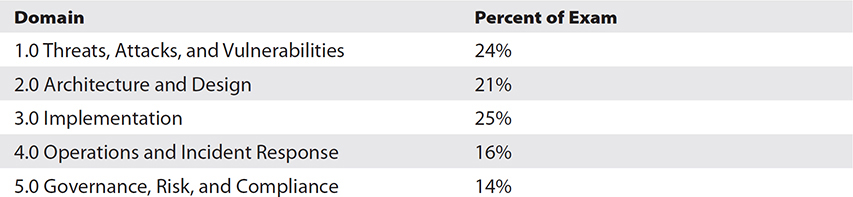
The exam objectives were developed with input and assistance from industry and government agencies. The CompTIA Security+ exam is designed to cover a wide range of security topics—subjects a security practitioner would be expected to know. The test includes information from five knowledge domains:
The exam consists of a series of questions, each designed to have a single best answer or response. The other available choices are designed to provide options that an individual might choose if he or she had an incomplete knowledge or understanding of the security topic represented by the question. The exam will have both multiple-choice and performance-based questions. Performance-based questions present the candidate with a task or a problem in a simulated IT environment. The candidate is given an opportunity to demonstrate his or her ability in performing skills. The exam questions are based on the “CompTIA Security+ Certification Exam Objectives: SY0-601” document obtainable from the CompTIA website at https://certification.comptia.org/certifications/security.
CompTIA recommends that individuals who want to take the CompTIA Security+ exam have the CompTIA Network+ certification and two years of IT administration experience with an emphasis on security. Originally administered only in English, the exam is now offered in testing centers around the world in English, Japanese, Portuguese, and Simplified Chinese. Consult the CompTIA website at www.comptia.org to determine a test center location near you.
The exam consists of a maximum of 90 questions to be completed in 90 minutes. A minimum passing score is considered 750 out of a possible 900 points. Results are available immediately after you complete the exam. An individual who fails to pass the exam the first time will be required to pay the exam fee again to retake the exam, but no mandatory waiting period is required before retaking it the second time. If the individual again fails the exam, a minimum waiting period of 30 days is required for each subsequent retake. For more information on retaking exams, consult CompTIA’s retake policy, which can be found on its website.
Preparing Yourself for the CompTIA Security+ Exam
CompTIA Security+ All-in-One Exam Guide, Sixth Edition, is designed to help prepare you to take CompTIA Security+ certification exam SY0-601.
How This Book Is Organized
The book is divided into sections and chapters to correspond with the objectives of the exam itself. Some of the chapters are more technical than others—reflecting the nature of the security environment, where you will be forced to deal with not only technical details but also other issues such as security policies and procedures as well as training and education. Although many individuals involved in computer and network security have advanced degrees in math, computer science, information systems, or computer or electrical engineering, you do not need this technical background to address security effectively in your organization. You do not need to develop your own cryptographic algorithm, for example; you simply need to be able to understand how cryptography is used, along with its strengths and weaknesses. As you progress in your studies, you will learn that many security problems are caused by the human element. The best technology in the world still ends up being placed in an environment where humans have the opportunity to foul things up—and all too often do.
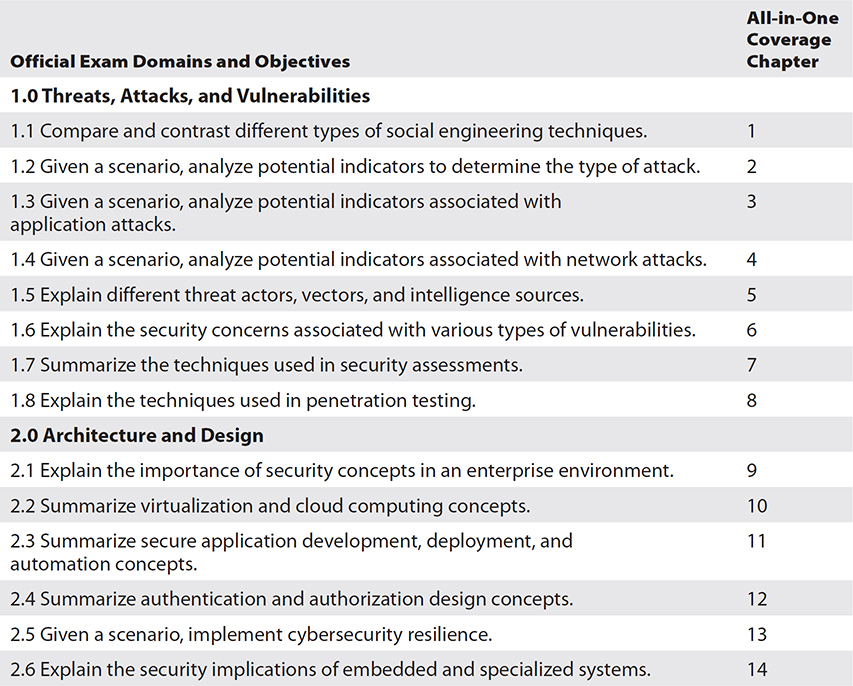
As you can see from the table of contents, the overall structure of the book is designed to mirror the objectives of the CompTIA Security+ exam. The majority of the chapters are designed to match the objectives order as posted by CompTIA. This structure was used to make it easier to search specific content based on the objective. When studying certain topics, you may be required to go to several places in the book to fully cover a topic that has multiple objectives.
In addition, there are two appendixes in this book. Appendix A provides an additional in-depth explanation of the OSI Model and Internet protocols, should this information be new to you, and Appendix B explains how best to use the online materials included with the book.
Located just before the Index, you will find a useful Glossary of security terminology, including many related acronyms and their meanings. We hope that you use the Glossary frequently and find it to be a useful study aid as you work your way through the various topics in this exam guide.
Special Features of the All-in-One Series
To make these exam guides more useful and a pleasure to read, the All-in-One series has been designed to include several features.
Objective Map
The objective map that follows this introduction has been constructed to allow you to cross-reference the official exam objectives with the objectives as they are presented and covered in this book. References have been provided for each objective exactly as CompTIA presents it, along with a chapter reference.
Icons
To alert you to an important bit of advice, a shortcut, or a pitfall, you’ll occasionally see Notes, Tips, Cautions, and Exam Tips peppered throughout the text.
End-of-Chapter Reviews and Questions
An important part of this book comes at the end of each chapter, where you will find a brief review of the high points along with a series of questions followed by the answers to those questions. Each question is in multiple-choice format. The answers provided also include a small discussion explaining why the correct answer actually is the correct answer.
The questions are provided as a study aid to you, the reader and prospective CompTIA Security+ exam taker. We obviously can’t guarantee that if you answer all of our questions correctly you will absolutely pass the certification exam. Instead, what we can guarantee is that the questions will provide you with an idea about how ready you are for the exam.
Security+ Proposed Hardware and Software List
CompTIA provides this sample list of hardware and software in its Exam Objectives description to assist candidates as they prepare for the Security+ exam. Because the material includes elements that require hands-on competency, it is useful to build a lab and practice hands-on skills as part of the study process. The bulleted lists below each topic are sample lists and are not exhaustive.
Hardware
• Laptop with Internet access
• Separate wireless network access card (NIC)
• Wireless access point (WAP)
• Firewall
• Unified threat monitor (UTM)
• Mobile device
• Server/cloud server
• IoT devices
Software
• Virtualization software
• Penetration testing OS/distributions (for example, Kali Linux, Parrot OS)
• Security information and event management (SIEM)
• Wireshark
• Metasploit
• Tcpdump
Other
• Access to a cloud service provider
The Online TotalTester
CompTIA Security+ All-in-One Exam Guide, Sixth Edition, also provides you with a test engine containing even more practice exam questions and their answers to help you prepare for the certification exam. Read more about the companion online TotalTester practice exam software and how to register for and access your exams in Appendix B.
Onward and Upward
At this point, we hope you are now excited about the topic of security, even if you weren’t in the first place. We wish you luck in your endeavors and welcome you to the exciting field of computer and network security.
Objective Map: Exam SY0-601