Chapter 2
Introduction to Security Terminology
CERTIFICATION OBJECTIVES
2.01 Using Threat Intelligence
2.02 Identifying Threat Actors
2.03 Identifying Threat Vectors
2.04 Understanding Data Roles
QUESTIONS
Threat actors are the entities that enact malicious activities. Identifying threat actor types and their motivations is the first step in planning threat countermeasures.
Information is power. Sharing cybersecurity intelligence helps organizations craft meaningful security policies, and it enhances the efficacy of security monitoring and reporting tools. This includes identifying threat vectors such as e-mail systems, removable media, or cloud services. The protection of data assets is undertaken by a variety of roles, such as data custodians, data controllers, data processors, and data owners.
1. Your manager, Wayne, is concerned about malicious users who might compromise servers and remain undetected for a period of time. What type of threat is Wayne concerned about?
A. Insider threat
B. Hacktivist
C. Advanced persistent threat
D. State actor
2. Which type of malicious users or groups attempt to promote a political or ideological view?
A. Hacktivist
B. Advanced persistent threat
C. State actor
D. Insider threat
3. Your organization has begun quarterly lunch-and-learn sessions to educate employees about current scams and computer security threats to increase their awareness and help prevent security issues such as data leaks. To which of the following items does this initiative best apply?
A. Hacktivist
B. Advanced persistent threat
C. State actor
D. Insider threat
4. Which type of malicious entity is most likely to launder the proceeds of illegal activities through online gambling sites?
A. State actor
B. Criminal syndicate
C. Hacktivists
D. Script kiddie
5. You are part of a team that has been hired to conduct penetration tests. Which term best describes your team?
A. Unauthorized hackers
B. Semi-authorized hackers
C. Script kiddies
D. Authorized hackers
6. You are an IT technician responsible for defining and implementing IT solutions throughout the organization. You have discovered that users in a remote branch office have configured a Wi-Fi network for use only in their location without approval from headquarters. Which term best describes this scenario?
A. Authorized hacking
B. Hacktivists
C. Hardening
D. Shadow IT
7. Which type of malicious actor is the most likely to have the most resources and funding?
A. Hacktivist
B. Criminal syndicate
C. State actor
D. Script kiddie
8. You have enabled firewall rules to allow only HTTPS connections to a web server that resides in your company’s server room. The company’s web site stores sensitive customer data in a backend database stored on the same host. Which types of potential security problems do company IT technicians present in this scenario? (Choose two.)
A. On-path attacks
B. Direct physical access
C. Phishing
D. Insider threat
9. Your organization has deployed mission-critical applications to a public cloud service provider (CSP) platform. The CSP recently disclosed a security flaw in the underlying network switches that was exploited by malicious users. The network switches were missing a firmware update that addressed security vulnerabilities. From your organization’s perspective, what is the source of this security issue?
A. Update management
B. Network switch vendor
C. CSP organizational security policies
D. Supply chain
10. You manage an air-gapped secure network named NET1 for a utility provider. NET1 does not connect in any way to any other network. You have scheduled the automatic scanning of the network for unauthorized network devices. Recently, new malware that is active on the Internet was discovered on NET1. What is the most likely explanation for how the malware made its way to NET1?
A. A rogue Wi-Fi router introduced the malware.
B. Users on NET1 downloaded infected files from the Internet.
C. Users on NET1 clicked a malicious link on a social media site.
D. Removable media was infected.
11. After running a vulnerability scan of your entire network because of newly reported vulnerabilities on the Internet, you notice that Linux-based honeypots on your network that are intentionally configured to appear vulnerable were not reported as vulnerable. What is the most likely cause of this behavior?
A. A credentialed scan was not run.
B. The honeypots have an OS-level firewall enabled.
C. Vulnerability scanners cannot identify vulnerabilities on Linux hosts.
D. The vulnerability database is not up-to-date.
12. You are reviewing network analysis reports for signs that could suggest malicious activity. What are you looking for?
A. Threat map
B. Automated indicator sharing (AIS)
C. Indicators of compromise
D. Predictive analysis
13. You are researching potential vulnerabilities with the way that Session Initiation Protocol (SIP) Voice over IP (VoIP) calls are established over the network. Which documentation source explains the standardized inner workings of SIP VoIP calls?
A. Open source intelligence
B. RFCs
C. Vendor documentation
D. Automated indicator sharing
14. What is the primary purpose of the Tor web browser?
A. Accessing media content in foreign countries
B. Downloading music
C. Web application vulnerability scanning
D. Accessing the Web anonymously
15. Which role is responsible for managing data in alignment with policies set forth by data owners?
A. Data owner
B. Data custodian
C. Data analyst
D. Data privacy officer
16. Which role is ultimately responsible for a data asset?
A. Data owner
B. Data custodian
C. Data analyst
D. Data privacy officer
17. Your organization collects, processes, and stores EU customer data. As a result, a Data Privacy Officer (DPO) role has been established to ensure regulatory compliance. To which European digital privacy legislation does this role apply?
A. PCI DSS
B. HIPAA
C. PIPEDA
D. GDPR
18. An online retailer legally collects and stores sensitive customer data that it then sells to marketing firms. Which data role is the online retailer partaking in?
A. Data processor
B. Data privacy officer
C. Data custodian
D. Data controller
19. A marketing firm legally purchases sensitive customer data from a data collection agency. Which data role is the marketing firm partaking in?
A. Data processor
B. Data privacy officer
C. Data custodian
D. Data controller
20. Which phrase best encompasses the mapping out of specific malicious user activity from beginning to end?
A. Automated indicator sharing
B. Adversary tactics, techniques, and procedures
C. Indicator of compromise
D. Predictive analysis
21. You are researching the potential of an employee e-mail account breach. You suspect these accounts may have been used to sign up to a variety of social media sites. After searching and viewing multiple web pages related to this issue, you become overwhelmed with information. What type of public-sourced security intelligence tool should you use to facilitate further testing of your suspicions?
A. Open source intelligence
B. Academic journals
C. File and code repositories
D. Conferences
22. Which of the following are standards related to the sharing of threat intelligence information? (Choose two.)
A. TAXII
B. OSINT
C. STIX
D. RFC
23. Which statements regarding the usage of the Tor web browser are correct? (Choose two.)
A. The Tor network is an Internet overlay network.
B. The Tor network requires the use of IPv6 addresses.
C. The Tor browser host IP address is hidden.
D. Usage of the Tor network requires signing up with an account.
24. Which of the following are normally considered potential insider threats? (Choose two.)
A. Port scanning of firewall interfaces
B. Contractors
C. Infected e-mail file attachments
D. Brute-force username and password web site attacks
25. Which type of hacker may discover and exploit vulnerabilities, yet lacks malicious intent?
A. Authorized
B. Red hat
C. Semi-authorized
D. Unauthorized
26. Which type of hacker has malicious intent and attempts to discover and exploit vulnerabilities?
A. Authorized
B. Red hat
C. Semi-authorized
D. Unauthorized
27. Which type of active security testing attempts to exploit discovered vulnerabilities?
A. Penetration testing
B. Vulnerability scanning
C. Port scanning
D. Network scanning
28. Which of the following wireless cryptographic protocols are the most vulnerable? (Choose two.)
A. WEP
B. WPA
C. WPA2
D. Default Wi-Fi router credentials
29. Refer to Figure 2-1. You are reviewing the configuration of a wireless router used in an executive boardroom. Which items should be changed to harden the wireless network? (Choose two.)
A. Do not use WEP.
B. Change the wireless network name.
C. Change the wireless channel to a different value.
D. Enable extended range mode.

FIGURE 2-1
Wireless router configuration
30. Refer to Figure 2-2. You are configuring notifications on a company mobile device app. To which of the following terms does this configuration best apply?
A. Device hardening
B. Shadow IT
C. TAXII
D. STIX
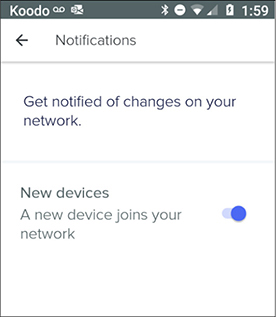
FIGURE 2-2
Mobile device network change notifications
31. Refer to Figure 2-3. To which of the following terms does the display message apply?
A. Anonymous web browsing
B. Shadow IT
C. TAXII
D. STIX

FIGURE 2-3
Tor web browser connection reset
32. Refer to Figure 2-4. To which of the following terms does the display message apply?
A. Data processor
B. Data custodian
C. Data controller
D. Data analyst
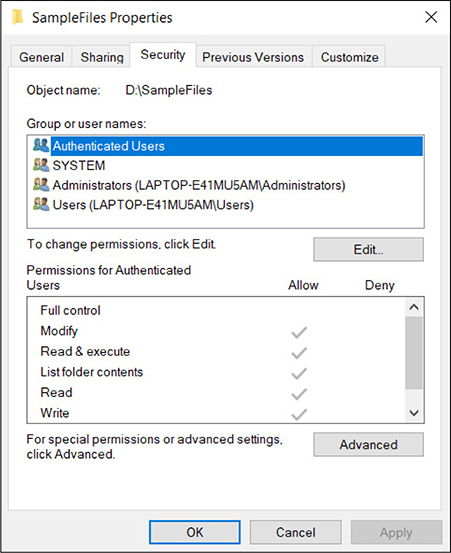
FIGURE 2-4
Windows NTFS file system security permissions
QUICK ANSWER KEY
1. C
2. A
3. D
4. B
5. D
6. D
7. C
8. B, D
9. D
10. D
11. D
12. C
13. B
14. D
15. B
16. A
17. D
18. D
19. A
20. B
21. A
22. A, C
23. A, C
24. B, C
25. C
26. D
27. A
28. A, D
29. A, B
30. B
31. A
32. B
IN-DEPTH ANSWERS
1. ![]() C. An advanced persistent threat (APT) implies a compromised network or device, whereby malicious actors, such as competitors or hacking groups, retain control of the compromised system for a period time before being detected.
C. An advanced persistent threat (APT) implies a compromised network or device, whereby malicious actors, such as competitors or hacking groups, retain control of the compromised system for a period time before being detected.
![]() A, B, and D are incorrect. Insider threats result from an actor within the organization who has knowledge of internal procedures, configurations, or details that would be unknown to external users. Hacktivists exploit vulnerable systems with the intention of promoting awareness of social, political, or ideological views. State actors are hacking groups supported by nations for the purposes of intelligence gathering or computer system disruption of other nations. State actors have considerable resources and sophisticated capabilities for hacking.
A, B, and D are incorrect. Insider threats result from an actor within the organization who has knowledge of internal procedures, configurations, or details that would be unknown to external users. Hacktivists exploit vulnerable systems with the intention of promoting awareness of social, political, or ideological views. State actors are hacking groups supported by nations for the purposes of intelligence gathering or computer system disruption of other nations. State actors have considerable resources and sophisticated capabilities for hacking.
2. ![]() A. Hacktivists exploit vulnerable systems with the intention of promoting awareness of social, political, or ideological views.
A. Hacktivists exploit vulnerable systems with the intention of promoting awareness of social, political, or ideological views.
![]() B, C, and D are incorrect. An APT implies a compromised network or device, whereby malicious actors, such as competitors or hacking groups, retain control of the compromised system for a period of time before being detected. State actors are hacking groups supported by nations for the purposes of intelligence gathering or computer system disruption of other nations. Insider threats result from an actor within the organization who has knowledge of internal procedures, configurations, or details that would be unknown to external users.
B, C, and D are incorrect. An APT implies a compromised network or device, whereby malicious actors, such as competitors or hacking groups, retain control of the compromised system for a period of time before being detected. State actors are hacking groups supported by nations for the purposes of intelligence gathering or computer system disruption of other nations. Insider threats result from an actor within the organization who has knowledge of internal procedures, configurations, or details that would be unknown to external users.
3. ![]() D. Insider threats result from an actor within the organization who has knowledge of internal procedures, configurations, or details that would be unknown to external users. Internal user training and awareness help protect digital assets from unintentional security breaches.
D. Insider threats result from an actor within the organization who has knowledge of internal procedures, configurations, or details that would be unknown to external users. Internal user training and awareness help protect digital assets from unintentional security breaches.
![]() A, B, and C are incorrect. Hacktivists exploit vulnerable systems with the intention of promoting awareness of social, political, or ideological views. An APT implies a compromised network or device, whereby malicious actors, such as competitors or hacking groups, retain control of the compromised system for a period time before being detected. State actors are hacking groups supported by nations for the purposes of intelligence gathering or computer system disruption of other nations.
A, B, and C are incorrect. Hacktivists exploit vulnerable systems with the intention of promoting awareness of social, political, or ideological views. An APT implies a compromised network or device, whereby malicious actors, such as competitors or hacking groups, retain control of the compromised system for a period time before being detected. State actors are hacking groups supported by nations for the purposes of intelligence gathering or computer system disruption of other nations.
4. ![]() B. A criminal syndicate is related to organized crime, which is likely to profit through illegal means and therefore must “clean” the proceeds through laundering.
B. A criminal syndicate is related to organized crime, which is likely to profit through illegal means and therefore must “clean” the proceeds through laundering.
![]() A, C, and D are incorrect. State actors are hacking groups supported by nations for the purposes of intelligence gathering or computer system disruption of other nations. Hacktivists exploit vulnerable systems with the intention of promoting awareness of social, political, or ideological views. Script kiddies have limited technical sophistication, and as opposed to creating their own exploit tools, they use exploit tools created by others.
A, C, and D are incorrect. State actors are hacking groups supported by nations for the purposes of intelligence gathering or computer system disruption of other nations. Hacktivists exploit vulnerable systems with the intention of promoting awareness of social, political, or ideological views. Script kiddies have limited technical sophistication, and as opposed to creating their own exploit tools, they use exploit tools created by others.
5. ![]() D. Authorized hackers are the “good guys”; they are hired to perform penetration tests to identify exploitable security weaknesses.
D. Authorized hackers are the “good guys”; they are hired to perform penetration tests to identify exploitable security weaknesses.
![]() A, B, and C are incorrect. Unauthorized hackers steal sensitive data or break into systems and are usually motivated by profit, revenge, or other nefarious motives. Semi-authorized hackers sit between Authorized and Unauthorized; they do not have malicious intent but may cross legal or ethical boundaries, such as breaking into computer systems at an airport and then notifying officials that their systems are vulnerable. Script kiddies have limited technical sophistication, and as opposed to creating their own exploit tools, they use exploit tools created by others.
A, B, and C are incorrect. Unauthorized hackers steal sensitive data or break into systems and are usually motivated by profit, revenge, or other nefarious motives. Semi-authorized hackers sit between Authorized and Unauthorized; they do not have malicious intent but may cross legal or ethical boundaries, such as breaking into computer systems at an airport and then notifying officials that their systems are vulnerable. Script kiddies have limited technical sophistication, and as opposed to creating their own exploit tools, they use exploit tools created by others.
6. ![]() D. The term “shadow IT” refers to non-IT staff who install or configure networked devices without central approval from the IT department; this would include adding a Wi-Fi router to a network without approval.
D. The term “shadow IT” refers to non-IT staff who install or configure networked devices without central approval from the IT department; this would include adding a Wi-Fi router to a network without approval.
![]() A, B, and C are incorrect. Authorized hackers are the “good guys”; they are hired to perform penetration tests to identify exploitable security weaknesses. Hacktivists exploit vulnerable systems with the intention of promoting awareness of social, political, or ideological views. Hardening is the process of securing a network or device by applying updates, removing unnecessary features, changing default settings, and so on.
A, B, and C are incorrect. Authorized hackers are the “good guys”; they are hired to perform penetration tests to identify exploitable security weaknesses. Hacktivists exploit vulnerable systems with the intention of promoting awareness of social, political, or ideological views. Hardening is the process of securing a network or device by applying updates, removing unnecessary features, changing default settings, and so on.
7. ![]() C. State actors are likely to have ample funding for their activities. These hacking groups are supported by nations for the purposes of intelligence gathering or computer system disruption of other nations.
C. State actors are likely to have ample funding for their activities. These hacking groups are supported by nations for the purposes of intelligence gathering or computer system disruption of other nations.
![]() A, B, and D are incorrect. Hacktivists exploit vulnerable systems with the intention of promoting awareness of social, political, or ideological views. A criminal syndicate is related to organized crime, which often generates profits through illegal means, and would have plenty of resources and funding available for malicious activities. Script kiddies have limited technical sophistication and are often individuals who are hacking a system for fun; they are not likely to be funded.
A, B, and D are incorrect. Hacktivists exploit vulnerable systems with the intention of promoting awareness of social, political, or ideological views. A criminal syndicate is related to organized crime, which often generates profits through illegal means, and would have plenty of resources and funding available for malicious activities. Script kiddies have limited technical sophistication and are often individuals who are hacking a system for fun; they are not likely to be funded.
8. ![]() B and D. Technicians who can gain access to the server room have direct access to the physical server and storage arrays, and physical access bypasses firewall rules. This is considered a potential insider threat.
B and D. Technicians who can gain access to the server room have direct access to the physical server and storage arrays, and physical access bypasses firewall rules. This is considered a potential insider threat.
![]() A and C are incorrect. On-path attacks involve a malicious user inserting themselves in network conversation between two unsuspecting victims. Phishing involves the attempt to acquire sensitive data from unsuspecting victims, usually through deception, such as by sending an SMS text message or e-mail message that looks legitimate but is not.
A and C are incorrect. On-path attacks involve a malicious user inserting themselves in network conversation between two unsuspecting victims. Phishing involves the attempt to acquire sensitive data from unsuspecting victims, usually through deception, such as by sending an SMS text message or e-mail message that looks legitimate but is not.
9. ![]() D. In this case, the cloud service provider (CSP) is a part of the supply chain, or service delivery platform (SDP), in the sense that the CSP supplies the IT services infrastructure used by the cloud customer.
D. In this case, the cloud service provider (CSP) is a part of the supply chain, or service delivery platform (SDP), in the sense that the CSP supplies the IT services infrastructure used by the cloud customer.
![]() A, B, and C are incorrect. Applying updates and reading security documentation from vendor web sites for network switches are activities specific to the CSP, not you as the cloud customer. Cloud customers have no detailed knowledge of CSP organizational security policies and whether those policies mention applying updates nor would customers know if this is a case in which policies were not adhered to.
A, B, and C are incorrect. Applying updates and reading security documentation from vendor web sites for network switches are activities specific to the CSP, not you as the cloud customer. Cloud customers have no detailed knowledge of CSP organizational security policies and whether those policies mention applying updates nor would customers know if this is a case in which policies were not adhered to.
10. ![]() D. Since NET1 has no connections to other networks, the most likely explanation is that the malware was transmitted through infected files on removable media.
D. Since NET1 has no connections to other networks, the most likely explanation is that the malware was transmitted through infected files on removable media.
![]() A, B, and C are incorrect. Since automatic network scanning is in place, a rogue Wi-Fi router would get detected. Users on NET1 do not have access to the Internet or social media sites.
A, B, and C are incorrect. Since automatic network scanning is in place, a rogue Wi-Fi router would get detected. Users on NET1 do not have access to the Internet or social media sites.
11. ![]() D. Vulnerability scanning tools use a database of known vulnerabilities as a comparison mechanism when scanning hosts and apps. Scanning tools can be configured to subscribe to vulnerability and threat feeds for automatic updating. If this database is not kept up-to-date, newer vulnerabilities may not be detected during scanning.
D. Vulnerability scanning tools use a database of known vulnerabilities as a comparison mechanism when scanning hosts and apps. Scanning tools can be configured to subscribe to vulnerability and threat feeds for automatic updating. If this database is not kept up-to-date, newer vulnerabilities may not be detected during scanning.
![]() A, B, and C are incorrect. A credentialed scan will provide a more in-depth scan of hosts that use those credentials, and OS-level firewalls can block some scanning traffic, but since the scan was initiated because of a newly reported vulnerability, these are not as likely as an out-of-date vulnerability database. Vulnerability scanners normally support many different OS platforms, including Linux.
A, B, and C are incorrect. A credentialed scan will provide a more in-depth scan of hosts that use those credentials, and OS-level firewalls can block some scanning traffic, but since the scan was initiated because of a newly reported vulnerability, these are not as likely as an out-of-date vulnerability database. Vulnerability scanners normally support many different OS platforms, including Linux.
12. ![]() C. Indicators of compromise (IoCs) suggest that malicious activity may be taking place or has taken place.
C. Indicators of compromise (IoCs) suggest that malicious activity may be taking place or has taken place.
![]() A, B, and D are incorrect. Threat maps allow for the visualization of active threats geographically. Automated indicator sharing (AIS) allows for the exchange of cybersecurity intelligence information between entities. Predictive analysis is used to analyze vast amounts of network and host activity logs to determine if a security incident is imminent.
A, B, and D are incorrect. Threat maps allow for the visualization of active threats geographically. Automated indicator sharing (AIS) allows for the exchange of cybersecurity intelligence information between entities. Predictive analysis is used to analyze vast amounts of network and host activity logs to determine if a security incident is imminent.
13. ![]() B. Requests for comment (RFCs) are publicly available technical standardization documents stemming from various international technical bodies that detail how specific types of technologies such as HTTP, DNS, or the ASCII character set work. Vendors building software and hardware products generally adhere to RFCs.
B. Requests for comment (RFCs) are publicly available technical standardization documents stemming from various international technical bodies that detail how specific types of technologies such as HTTP, DNS, or the ASCII character set work. Vendors building software and hardware products generally adhere to RFCs.
![]() A, C, and D are incorrect. Open source intelligence (OSINT) tools ingest cybersecurity intelligence data from various public sources to facilitate cybersecurity hardening activities. Vendor documentation is proprietary and will not provide as much standardized information about network protocols as RFCs will; vendor documentation will focus on how that vendor implemented RFC standards. Paying customers will often acquire access to closed source intelligence, such as after purchasing IT security solutions. Automated indicator sharing (AIS) uses information that can stem from open source as well as closed source, or proprietary origins, as well as local industry groups that focus on identifying suspicious activity. AIS focuses on the exchange of cybersecurity intelligence information between entities.
A, C, and D are incorrect. Open source intelligence (OSINT) tools ingest cybersecurity intelligence data from various public sources to facilitate cybersecurity hardening activities. Vendor documentation is proprietary and will not provide as much standardized information about network protocols as RFCs will; vendor documentation will focus on how that vendor implemented RFC standards. Paying customers will often acquire access to closed source intelligence, such as after purchasing IT security solutions. Automated indicator sharing (AIS) uses information that can stem from open source as well as closed source, or proprietary origins, as well as local industry groups that focus on identifying suspicious activity. AIS focuses on the exchange of cybersecurity intelligence information between entities.
14. ![]() D. The Tor web browser enables anonymous connectivity to the Web.
D. The Tor web browser enables anonymous connectivity to the Web.
![]() A, B, and C are incorrect. While the Tor browser can be used to access media and download music, this is not its primary purpose. Tor is not a web app vulnerability scanning tool.
A, B, and C are incorrect. While the Tor browser can be used to access media and download music, this is not its primary purpose. Tor is not a web app vulnerability scanning tool.
15. ![]() B. The data custodian, or data steward, role involves managing data assets in accordance with policies set forth by data owners. An example of a data custodian is a file server administrator that can set file system permissions.
B. The data custodian, or data steward, role involves managing data assets in accordance with policies set forth by data owners. An example of a data custodian is a file server administrator that can set file system permissions.
![]() A, C, and D are incorrect. Data owners set policies on how data will be managed; they are ultimately responsible for the data. Data analysts collect data from multiple sources in order to gain meaningful insights that may not otherwise be derived. A data privacy officer (DPO), also referred to as a data protection officer, is a role put in place to ensure compliance, such as with the European Union (EU) General Data Protection Regulation (GDPR) to protect sensitive EU citizen data.
A, C, and D are incorrect. Data owners set policies on how data will be managed; they are ultimately responsible for the data. Data analysts collect data from multiple sources in order to gain meaningful insights that may not otherwise be derived. A data privacy officer (DPO), also referred to as a data protection officer, is a role put in place to ensure compliance, such as with the European Union (EU) General Data Protection Regulation (GDPR) to protect sensitive EU citizen data.
16. ![]() A. Data owners set policies on how data will be managed; they are ultimately responsible for the data.
A. Data owners set policies on how data will be managed; they are ultimately responsible for the data.
![]() B, C, and D are incorrect. The data custodian, or data steward, role involves managing data assets in accordance with policies set forth by data owners. Data analysts collect data from multiple sources to gain meaningful insights that might otherwise not be derived. A data privacy officer (DPO) ensures compliance with the EU General Data Protection Regulation (GDPR) to protect sensitive EU citizen data.
B, C, and D are incorrect. The data custodian, or data steward, role involves managing data assets in accordance with policies set forth by data owners. Data analysts collect data from multiple sources to gain meaningful insights that might otherwise not be derived. A data privacy officer (DPO) ensures compliance with the EU General Data Protection Regulation (GDPR) to protect sensitive EU citizen data.
17. ![]() D. The EU GDPR is an act of legislation designed to protect sensitive EU citizen data. A data privacy officer ensures compliance with regulations such as the GDPR.
D. The EU GDPR is an act of legislation designed to protect sensitive EU citizen data. A data privacy officer ensures compliance with regulations such as the GDPR.
![]() A, B, and C are incorrect. The Payment Card Industry Data Security Standard (PCI DSS) provides guidance on securing environments where credit card information is processed. The Health Insurance Portability and Accountability Act (HIPAA) is an American act of legislation designed to protect sensitive medical patient information. The Personal Information Protection and Electronic Documents Act (PIPEDA) is a Canadian data privacy act of legislation.
A, B, and C are incorrect. The Payment Card Industry Data Security Standard (PCI DSS) provides guidance on securing environments where credit card information is processed. The Health Insurance Portability and Accountability Act (HIPAA) is an American act of legislation designed to protect sensitive medical patient information. The Personal Information Protection and Electronic Documents Act (PIPEDA) is a Canadian data privacy act of legislation.
18. ![]() D. The data controller determines how data can be used, such as providing it to other parties.
D. The data controller determines how data can be used, such as providing it to other parties.
![]() A, B, and C are incorrect. The data processor role, in this example, is assumed by the marketing firm that purchases data for processing purposes, such as to enhance targeted marketing campaigns. A data privacy officer (DPO) ensures compliance with security standards and regulations such as the EU GDPR to protect sensitive EU citizen data. The data custodian manages data assets in accordance with policies set forth by data owners.
A, B, and C are incorrect. The data processor role, in this example, is assumed by the marketing firm that purchases data for processing purposes, such as to enhance targeted marketing campaigns. A data privacy officer (DPO) ensures compliance with security standards and regulations such as the EU GDPR to protect sensitive EU citizen data. The data custodian manages data assets in accordance with policies set forth by data owners.
19. ![]() A. The data processor role, in this example, is assumed by the marketing firm that purchases data for processing purposes, such as to enhance targeted marketing campaigns.
A. The data processor role, in this example, is assumed by the marketing firm that purchases data for processing purposes, such as to enhance targeted marketing campaigns.
![]() B, C, and D are incorrect. A data privacy officer ensures compliance with security and regulatory standards such as the EU GDPR to protect sensitive EU citizen data. The data custodian manages data assets in accordance with policies set forth by data owners. The data controller role determines how data can be used, such as providing it to other parties.
B, C, and D are incorrect. A data privacy officer ensures compliance with security and regulatory standards such as the EU GDPR to protect sensitive EU citizen data. The data custodian manages data assets in accordance with policies set forth by data owners. The data controller role determines how data can be used, such as providing it to other parties.
20. ![]() B. Adversary tactics, techniques, and procedures (TTP) is used to define how malicious attacks are carried out.
B. Adversary tactics, techniques, and procedures (TTP) is used to define how malicious attacks are carried out.
![]() A, C, and D are incorrect. Automated indicator sharing (AIS) uses information that can stem from open source, closed source, or proprietary origins, as well as local industry groups that focus on identifying suspicious activity. AIS focuses on the exchange of cybersecurity intelligence information between entities. Indicators of compromise (IoCs) suggest that malicious activity may be taking place, or has taken place. Predictive analysis is used to analyze vast amounts of network and host activity logs to determine if a security incident is imminent.
A, C, and D are incorrect. Automated indicator sharing (AIS) uses information that can stem from open source, closed source, or proprietary origins, as well as local industry groups that focus on identifying suspicious activity. AIS focuses on the exchange of cybersecurity intelligence information between entities. Indicators of compromise (IoCs) suggest that malicious activity may be taking place, or has taken place. Predictive analysis is used to analyze vast amounts of network and host activity logs to determine if a security incident is imminent.
21. ![]() A. Open source intelligence (OSINT) tools ingest cybersecurity intelligence data from various public sources to facilitate cybersecurity activities.
A. Open source intelligence (OSINT) tools ingest cybersecurity intelligence data from various public sources to facilitate cybersecurity activities.
![]() B, C, and D are incorrect. Academic journals and conferences can provide valuable security information, but they are not security intelligence tools that can be used for testing. File and code repositories such as GitHub and Bitbucket serve as centralized programming code repositories and can provide security tools, but OSINT is more specific to gathering security information from many sources and using it for security purposes.
B, C, and D are incorrect. Academic journals and conferences can provide valuable security information, but they are not security intelligence tools that can be used for testing. File and code repositories such as GitHub and Bitbucket serve as centralized programming code repositories and can provide security tools, but OSINT is more specific to gathering security information from many sources and using it for security purposes.
22. ![]() A and C. The Trusted Automated Exchange of Indicator Information (TAXII) standard defines how cybersecurity intelligence information is shared among entities. The Structured Threat Information eXpression (STIX) standard defines the data exchange format for cybersecurity information.
A and C. The Trusted Automated Exchange of Indicator Information (TAXII) standard defines how cybersecurity intelligence information is shared among entities. The Structured Threat Information eXpression (STIX) standard defines the data exchange format for cybersecurity information.
![]() B and D are incorrect. Open source intelligence (OSINT) tools ingest cybersecurity intelligence data from various public sources to facilitate cybersecurity hardening activities. Requests for comment (RFCs) are publicly available technical standardization documents stemming from various international technical bodies that detail how specific types of technologies such as HTTP, DNS, or the ASCII character set work.
B and D are incorrect. Open source intelligence (OSINT) tools ingest cybersecurity intelligence data from various public sources to facilitate cybersecurity hardening activities. Requests for comment (RFCs) are publicly available technical standardization documents stemming from various international technical bodies that detail how specific types of technologies such as HTTP, DNS, or the ASCII character set work.
23. ![]() A and C. The Tor network is considered an overlay network in that it sits on the existing public Internet infrastructure; it is designed to use encryption and multiple global relay points to protect user activity from traffic analysis. As a result, using the Tor web browser for Tor network connectivity hides the IP address of the machine running the Tor web browser.
A and C. The Tor network is considered an overlay network in that it sits on the existing public Internet infrastructure; it is designed to use encryption and multiple global relay points to protect user activity from traffic analysis. As a result, using the Tor web browser for Tor network connectivity hides the IP address of the machine running the Tor web browser.
![]() B and D are incorrect. IPv6 is not required on the Tor network, and there is no requirement for setting up a user account.
B and D are incorrect. IPv6 is not required on the Tor network, and there is no requirement for setting up a user account.
24. ![]() B and C. Contractors working for an organization may have knowledge of or access to company processes and systems. Users opening infected file attachments from e-mail messages means the infection would then be on the inside. Both of these present potential insider threats.
B and C. Contractors working for an organization may have knowledge of or access to company processes and systems. Users opening infected file attachments from e-mail messages means the infection would then be on the inside. Both of these present potential insider threats.
![]() A and D are incorrect. Port scanning of firewall interfaces is commonplace and is not specifically conducted from internal networks, but is normally conducted from outside the network by external users. Using brute-force techniques in an attempt to compromise user accounts can be conducted internally but it can also involve an external perspective, such as against a public-facing web site by malicious users.
A and D are incorrect. Port scanning of firewall interfaces is commonplace and is not specifically conducted from internal networks, but is normally conducted from outside the network by external users. Using brute-force techniques in an attempt to compromise user accounts can be conducted internally but it can also involve an external perspective, such as against a public-facing web site by malicious users.
25. ![]() C. Semi-authorized hackers discover vulnerabilities and can compromise systems, which could cross legal or ethical boundaries, but their intent is not malicious. Often Semi-authorized hackers will compromise systems and let the system owners know about the vulnerabilities.
C. Semi-authorized hackers discover vulnerabilities and can compromise systems, which could cross legal or ethical boundaries, but their intent is not malicious. Often Semi-authorized hackers will compromise systems and let the system owners know about the vulnerabilities.
![]() A, B, and D are incorrect. Authorized hackers attempt to identify and sometimes exploit vulnerabilities as part of security testing, such as when teams are hired to conduct penetration tests. “Red-hat hackers” is not a valid security term. Unauthorized hackers are users with malicious intent who attempt to exploit systems.
A, B, and D are incorrect. Authorized hackers attempt to identify and sometimes exploit vulnerabilities as part of security testing, such as when teams are hired to conduct penetration tests. “Red-hat hackers” is not a valid security term. Unauthorized hackers are users with malicious intent who attempt to exploit systems.
26. ![]() D. Unauthorized hackers are individuals with malicious intent that attempt to exploit systems.
D. Unauthorized hackers are individuals with malicious intent that attempt to exploit systems.
![]() A, B, and C are incorrect. Authorized hackers attempt to identify and sometimes exploit vulnerabilities as part of security testing, such as when teams are hired to conduct penetration tests. “Red-hat hackers” is not a valid security term. Semi-authorized hackers discover vulnerabilities and can compromise systems, which could cross legal or ethical boundaries, but their intent is not malicious.
A, B, and C are incorrect. Authorized hackers attempt to identify and sometimes exploit vulnerabilities as part of security testing, such as when teams are hired to conduct penetration tests. “Red-hat hackers” is not a valid security term. Semi-authorized hackers discover vulnerabilities and can compromise systems, which could cross legal or ethical boundaries, but their intent is not malicious.
27. ![]() A. Penetration tests (pen tests) identify and attempt to exploit vulnerabilities.
A. Penetration tests (pen tests) identify and attempt to exploit vulnerabilities.
![]() B, C, and D are incorrect. Vulnerability scans only identify vulnerabilities; no attempt is made to exploit discovered weaknesses. Port scanning is a reconnaissance technique used to learn which network services are running on hosts. Network scanning is used to identify which devices are up and running on a network, and also to identify any services they may be running.
B, C, and D are incorrect. Vulnerability scans only identify vulnerabilities; no attempt is made to exploit discovered weaknesses. Port scanning is a reconnaissance technique used to learn which network services are running on hosts. Network scanning is used to identify which devices are up and running on a network, and also to identify any services they may be running.
28. ![]() A and D. Wired Equivalent Privacy (WEP) is an older, deprecated wireless encryption protocol and should not be used, because many freely available tools can compromise WEP. Using default credentials always presents a security risk because these are widely known.
A and D. Wired Equivalent Privacy (WEP) is an older, deprecated wireless encryption protocol and should not be used, because many freely available tools can compromise WEP. Using default credentials always presents a security risk because these are widely known.
![]() B and C are incorrect. Wi-Fi Protected Access (WPA) and its successor, WPA2, are wireless encryption protocols that succeed WEP. Although they can be compromised, this is not done as quickly or as easily as it is with WEP or with the use of default Wi-Fi router credentials.
B and C are incorrect. Wi-Fi Protected Access (WPA) and its successor, WPA2, are wireless encryption protocols that succeed WEP. Although they can be compromised, this is not done as quickly or as easily as it is with WEP or with the use of default Wi-Fi router credentials.
29. ![]() A and B. Wired Equivalent Privacy (WEP) should not be used because of its many known security flaws; instead, use WPA2 or, if supported by the device, WPA3. Wireless network names, or service set identifiers (SSIDs), should never truly reflect the location in which they are used, because this provides malicious users with more details they can use for nefarious purposes.
A and B. Wired Equivalent Privacy (WEP) should not be used because of its many known security flaws; instead, use WPA2 or, if supported by the device, WPA3. Wireless network names, or service set identifiers (SSIDs), should never truly reflect the location in which they are used, because this provides malicious users with more details they can use for nefarious purposes.
![]() C and D are incorrect. Changing a wireless channel can reduce interference but does not increase security. Extending wireless range could decrease security, such as in the case of allowing wireless signals to propagate beyond an office space.
C and D are incorrect. Changing a wireless channel can reduce interference but does not increase security. Extending wireless range could decrease security, such as in the case of allowing wireless signals to propagate beyond an office space.
30. ![]() B. Shadow IT relates to the non-IT staff implementation of network devices and configurations without centralized IT department approval, such as adding unauthorized devices to the network. Many available tools can notify IT staff when new devices are added to a network.
B. Shadow IT relates to the non-IT staff implementation of network devices and configurations without centralized IT department approval, such as adding unauthorized devices to the network. Many available tools can notify IT staff when new devices are added to a network.
![]() A, C, and D are incorrect. Device hardening involves reducing the device’s attack service with activities such as applying updates, removing unnecessary components, and changing default settings. The Trusted Automated Exchange of Indication Information (TAXII) standard defines how cybersecurity intelligence information is shared among entities. The Structured Threat Information EXpression (STIX) standard defines the data exchange format for cybersecurity information.
A, C, and D are incorrect. Device hardening involves reducing the device’s attack service with activities such as applying updates, removing unnecessary components, and changing default settings. The Trusted Automated Exchange of Indication Information (TAXII) standard defines how cybersecurity intelligence information is shared among entities. The Structured Threat Information EXpression (STIX) standard defines the data exchange format for cybersecurity information.
31. ![]() A. The Tor web browser is used to connect to the Dark Web and the Internet anonymously by routing browsing traffic through a variety of servers in different geographical regions.
A. The Tor web browser is used to connect to the Dark Web and the Internet anonymously by routing browsing traffic through a variety of servers in different geographical regions.
![]() B, C, and D are incorrect. Shadow IT relates to the non-IT staff implementation of network devices and configurations without centralized IT department approval, such as adding unauthorized devices to the network. The TAXII standard defines how cybersecurity intelligence information is shared among entities. The STIX standard defines the data exchange format for cybersecurity information.
B, C, and D are incorrect. Shadow IT relates to the non-IT staff implementation of network devices and configurations without centralized IT department approval, such as adding unauthorized devices to the network. The TAXII standard defines how cybersecurity intelligence information is shared among entities. The STIX standard defines the data exchange format for cybersecurity information.
32. ![]() B. The data custodian, or data steward, role involves managing data assets in accordance with policies set forth by data owners. In this case, setting file system permissions is a responsibility of the data custodian. The listed file system permissions are applied locally on the machine as well as over the network via the server message block (SMB) protocol when the folder is shared.
B. The data custodian, or data steward, role involves managing data assets in accordance with policies set forth by data owners. In this case, setting file system permissions is a responsibility of the data custodian. The listed file system permissions are applied locally on the machine as well as over the network via the server message block (SMB) protocol when the folder is shared.
![]() A, C, and D are incorrect. The data processor role applies actions to data within the confines of parameters specified by the data controller, such as data transformations between file formats, the secure use and storage of data, data versioning and archiving. The data controller role determines how data can be used, such as providing it to other parties. Data analysts collect data from multiple sources to gain meaningful insights that may not otherwise be derived.
A, C, and D are incorrect. The data processor role applies actions to data within the confines of parameters specified by the data controller, such as data transformations between file formats, the secure use and storage of data, data versioning and archiving. The data controller role determines how data can be used, such as providing it to other parties. Data analysts collect data from multiple sources to gain meaningful insights that may not otherwise be derived.
