Chapter 8
Securing the Network Infrastructure
CERTIFICATION OBJECTIVES
8.02 Using Intrusion Detection Systems
Abig part of security within organizations today comes from securing the network infrastructure. This involves making sure that the network used to connect an employee’s computer to the servers is as secure as possible against threats from outside or inside the network.
The last few chapters have been focused on what you can do to secure individual systems, which is very important, but you also want to be sure that the network you connect those systems to is as secure as possible. In order to create a secure network infrastructure for those systems, you must take a layered security approach (also known as defense in depth), which involves protecting the network infrastructure with firewalls, but also ensuring you use intrusion detection systems to identify suspicious network traffic.
This chapter will introduce you to topics such as firewalls, intrusion detection systems, and network access control. You will be tested on these technologies on your Security+ certification exam, so be sure you are comfortable with the content of this chapter.
CERTIFICATION OBJECTIVE 8.01
Understanding Firewalls
In this section you learn about firewalls, proxy servers, and other types of security devices used to create a secure network infrastructure. Firewalls and proxy servers are two of the most common devices found in network environments today because they are responsible for ensuring that unauthorized persons outside the network (such as on the Internet) cannot gain access to your network.
Firewalls
Firewalls are designed to protect systems on one side of the firewall from systems on the other side by analyzing packets that reach the firewall and determining whether each packet is allowed to pass through. You will configure rules on the firewall that indicate to the firewall which traffic is to pass through and which is to be blocked.

For the Security+ exam, know that firewalls are examples of protective controls, as they have rules configured to control what type of traffic can enter the network. This chapter also discusses the intrusion detection system (IDS), which in general is considered a detective control— unless it is an active IDS, in which case it is known as an intrusion prevention system (IPS), but more on that later!
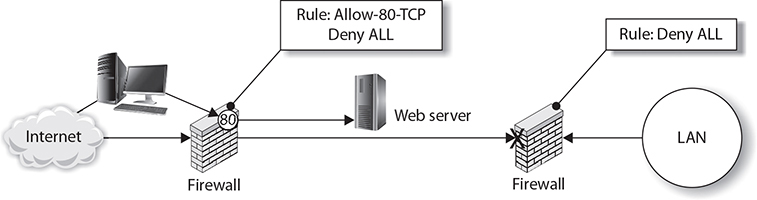
For example, as a general rule you should configure the firewall to block all traffic, meaning that no traffic can pass through. Once you have configured the “default” rule of blocking all traffic, you can configure exceptions to the rule, allowing select traffic to pass through. For example, if you have a web server that you want to expose to the Internet, you would block all traffic except TCP port 80, the port on which web server traffic runs (as shown in Figure 8-1).
FIGURE 8-1
Firewalls allow selected traffic to pass through the firewall.
Before we go any further into the firewall discussion, I should stress that there are two major classes of firewalls. A host-based firewall is a piece of software you install on a system that is used to protect that one system. A network-based firewall is placed at the edge of the network and controls what traffic is allowed to enter and leave the network. This chapter focuses on network-based firewalls.
Types of Firewalls
Firewalls have progressed over time, and for the Security+ certification exam, it is important to understand the different types of firewalls that have emerged over the years.
Packet-Filtering Firewall (Stateless) The first type of firewall is a packet-filtering firewall, also known as a stateless firewall. A packet-filtering firewall can block or allow traffic (known as filtering traffic) based on the source or destination IP address and the source or destination port number, as shown in Figure 8-2.
FIGURE 8-2
A packet-filtering firewall filters traffic based on the layer-3 and layer-4 headers.
When configuring the packet-filtering firewall, you specify rules that control what type of traffic is allowed to pass through the firewall and what traffic is to be blocked. With packet-filtering firewalls, the rules can filter traffic based on source address, destination address, protocol, and source and destination port address.
For example, if you intend to allow all incoming traffic from any system that is destined for port 80 on your web server’s IP address of 24.15.34.89 while disabling all other inbound traffic, you may configure a packet-filtering rule such as the following:
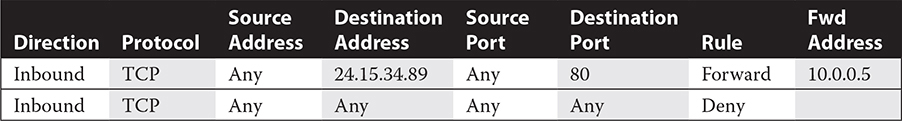
Typically, with most firewalls, the first rule that applies to the packet is the rule that the packet follows. For example, with the foregoing rule, if you have any inbound traffic destined for port 80 on IP address 24.15.34.89, the traffic is forwarded to the web server inside the company at IP address 10.0.0.5 (see Figure 8-3). Based on the ACL, any other traffic would be denied at the firewall.
FIGURE 8-3
Firewalls forward traffic to a system inside the network.

A packet-filtering firewall filters traffic based on fields in the header of the packet, such as the source and destination IP address and the source and destination port number.
A packet-filtering firewall is known as a stateless inspection firewall because it simply allows or denies traffic based on the header of the packet (source/destination IP address or source/destination port number). The attacker could alter the addresses in the header of the packet to fit into the rule placed on the firewall, and then the firewall would allow the packet into the network.
Stateful Packet Inspection Firewall Packet-filtering firewalls look like a great type of firewall at first, but they are not all that intelligent because it is easy for a hacker to spoof a packet so that it meets the rules of the firewall. For example, if you open port 80 on a packet-filtering firewall, any packets destined for port 80 will bypass the firewall.
Like packet-filtering firewalls, a stateful packet inspection firewall can filter traffic based on the source and destination IP address or port number, but can also look at the context of the conversation and determine if the packet is supposed to be received at that point in the conversation. If the firewall receives a packet in the correct context of the conversation and the packet follows one of the rules, it allows the packet into the network. Stateful packet inspection firewalls use rules to filter traffic as well, but they also are smart enough to know the context of the conversation.
An example of a stateful packet inspection firewall knowing about the context of a conversation is that if a hacker tries to send malicious commands to the firewall with a destination port of 80 and the hacker has not performed a three-way handshake first, the firewall says, “Nope, sorry, you are not allowed in because I don’t see that we have established a connection.” Stateful packet inspection firewalls know that before TCP communication can occur, there needs to be a three-way handshake.

A stateful packet inspection firewall filters traffic by the layer-3 and layer-4 headers (like a packet-filtering firewall, also known as stateless), but in addition can filter traffic by knowing what packets are expected during certain phases of the conversation.
Application-Layer Firewall The next type of firewall, the application-layer firewall, implements features of both the packet-filtering firewall and the stateful packet inspection firewall, but also can filter traffic based on the payload data of the packet.
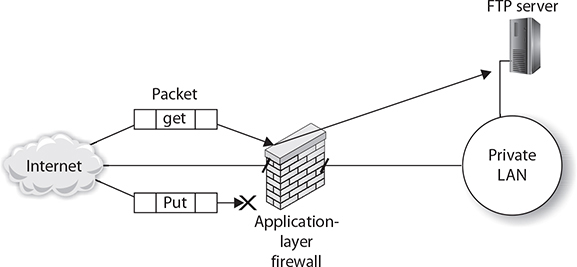
Not only does an application-layer firewall implement packet-filtering and stateful packet inspection features, but it also can inspect the application data in the packet, known as the payload. This means that an application-layer firewall can deny packets containing suspicious commands. For example, the application-layer firewall can check that the destination port is 80, but also ensure that there is no HTTP put command being executed. Or the firewall could ensure that data is downloaded (get) from an FTP server, but not uploaded (put) to the server (see Figure 8-4).
FIGURE 8-4
Application-layer firewall checking the payload of a packet

An application-layer firewall can filter traffic based on the data portion of the packet, known as the payload data. This allows the firewall to control what types of actions, or commands, can be passed through the firewall in the payload of the packet.
Other Firewall Types The world of firewalls has evolved over the last number of years. The following is a listing of other important key points to remember of firewalls and firewall types for the Security+ exam:
■ Web application firewall A web application firewall (WAF) is an application-layer firewall that allows you to control which HTTP messages can reach your web server or web service. Controlling the HTTP messages allows you to protect against common attacks targeting web servers. The difference between a WAF and a regular network firewall is that the WAF is focused on analyzing HTTP traffic, while the network firewall analyzes all network traffic.
■ Next-generation firewall A next-generation firewall (NGFW) performs packet filtering functions like a stateful packet inspection firewall, but also performs deep packet inspection (DPI), which allows the firewall to inspect the data portion of the packet and take actions based on the data of the packet. The NGFW also has intrusion prevention capabilities, which allow it to block suspicious traffic based on the header and data found in the packet.
■ Unified threat management Look to unified threat management (UTM) systems to provide an all-in-one security solution for the organization. UTM systems are multifunctional devices that have firewall features, intrusion detection and prevention, anti-spam, antivirus, and content filtering, to name a few features.
■ Open source vs. proprietary When looking at firewall solutions, you can go with an open-source solution that is supported on many different platforms or you can go with a company’s proprietary solution.
■ Hardware vs. software Firewalls can be hardware devices connected to different network segments that allow it to filter traffic from one segment to another, or they can be software running on a system that filters traffic that can pass through the system.
■ Appliance vs. host-based vs. virtual You can use a firewall that is an appliance device, a host-based firewall, or a virtual firewall. The benefit of the appliance is that it is a separate device with multiple interfaces and typically comes with other security features such as intrusion prevention features. The host-based firewall is software that can run on systems with different hardware configurations, which may not be possible with the appliance device. A virtual firewall is firewall software installed in a virtual machine that can be used to protect a network or group of virtual machines.

For the Security+ exam, know the differences between WAF, NGFW, and UTM firewall devices.
Using IPTables as a Firewall
An important example of a firewall is IPTables, a very powerful firewall feature found in Linux that has replaced the older IPChains feature. IPTables gets its name from tables of rules that control what traffic is allowed to enter or leave the system or to be forwarded on to another system.
Three main tables are used with IPTables:
■ Input This table controls what traffic is allowed to pass through the network card into the Linux system.
■ Output This table controls what traffic is allowed to pass through the network card out of the Linux system.
■ Forward This table is used if you want to forward a packet from the Linux system on to another system.
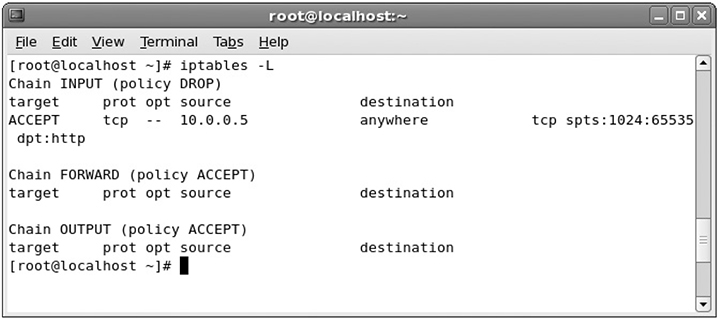
To view a list of the tables, you can use the iptables -L command in Linux. Notice in Figure 8-5 that I have the three tables and that each table has a default policy of ACCEPT. This means that, by default, Linux allows all traffic to enter or leave the system.
FIGURE 8-5
Looking at IPTables in Linux
If you wanted to change the default policy of the INPUT table, you could use the iptables command with the -P switch and then specify the default rule. The following command is used to change the default policy on the INPUT table to DROP all traffic:
![]()
After you change the default rule (known as a policy) of a table, you can then start adding exceptions by appending rules to the table. In the following example, iptables is used with -A to append a rule to the INPUT table. The rule allows any TCP traffic with a source IP address of 10.0.0.1, any destination address with a source port ranging from 1024 to 65535, and a destination port address of 80 to pass through the firewall. The following commands show how to add a rule to the firewall (note that -j is how you specify the action of either ACCEPT or DROP):
![]()
EXERCISE 8-1

Configuring IPTables in Linux
In this exercise, you work with IPTables, the firewall feature built into Linux. This exercise requires a Linux system that has the FTP service and the web server software installed. Note that in this exercise, I use Fedora with an IP address of 10.0.0.150.
1. Ensure that the Linux, Windows 10, and ServerA VMs are running.
2. Go to the Linux VM and start a terminal.
3. To flush any previous rules out of the input table, type the following:
![]()
4. List all tables by typing iptables –L in a terminal session. What are the three default tables? __________________________________________________

5. Notice that the policy for the INPUT table is ACCEPT, meaning that the system will accept all inbound traffic.
6. Go to the Windows 10 VM and ensure that you can navigate to the web site located on the Linux system by typing http://<IP_Of_Linux> (for example, http://10.0.0.150) in the web browser address.
7. Go back to the Linux VM.
8. To change the INPUT table to deny all incoming traffic, type
![]()
9. To view your change by listing all tables again, type
![]()
10. What is the default policy for the INPUT table? _______________
11. What is the default policy of the OUTPUT table: ACCEPT or DROP? _______________
12. Go to the Windows 10 VM and navigate to the web site located on the Linux system by typing http://<IP_Of_Linux> (for example, http://10.0.0.150) in the web browser address again.
13. Can you view the site? Why or why not?
_______________________________________________________________________
_______________________________________________________________________
14. Go back to the Linux VM.
15. You want to allow only the Windows 10 system to view the web site, so you will create an INPUT rule that allows traffic to the web site if the source IP address is 10.0.0.5. Type the following:
![]()
16. What does this rule do?
_______________________________________________________________________
_______________________________________________________________________
17. To view the new rule in the INPUT table, type iptables –L.
18. Go to the Windows 10 VM and verify that you can surf the Linux web site. Were you successful? _______________
19. Go to the ServerA VM and verify that you cannot surf the Linux web site. Were you successful? _______________
Using Firewall Features on a Home Router
Most home users and small businesses use what is known as a “home router” to establish a high-speed connection between their network and the Internet. The nice thing about these home routers is that they are multifunctional devices in the sense that they are NAT devices and firewall devices that offer URL-filtering features to limit what web sites users on the network can visit.
By default, the home routers typically block all traffic that originates from the Internet, so if you want to host your own web site inside the network, you would have to open its port on the firewall of the home router. For your guidance, here are the steps I used on my D-Link DIR-615 router:
1. Launch a web browser and navigate to the internal IP address of the router (which is typically 192.168.0.1).
2. Choose the Advanced link at the top of the page.
3. Choose the Port Forwarding link on the left side of the screen.
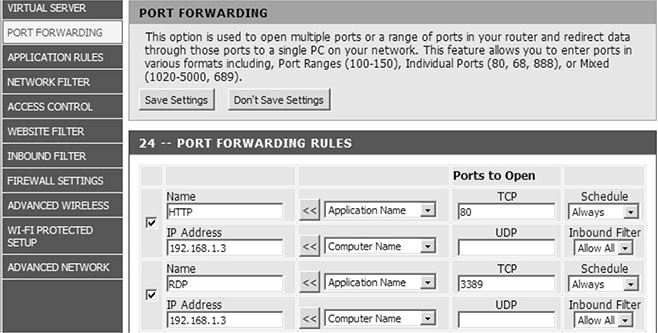
4. Once on the Port Forwarding screen, you can configure rules on the firewall to forward packets destined for a particular port to a system inside the network. To allow inbound web traffic to your web server, type the following information into the appropriate fields (see Figure 8-6):
FIGURE 8-6
Configuring a port-forwarding rule
■ Name: HTTP.
■ IP Address: 192.168.1.3 (the IP address of the internal system to which you want to have the traffic forwarded).
■ TCP: 80 (the port the traffic is destined for; you could also specify a UDP port instead if the traffic was UDP based).
5. Once all the information for the rule has been inputted, click the Apply button to apply the change.
Firewall Topologies
Let’s move on to firewall topologies. Popular configurations for firewalls include dual-homed, screened-host, and screened-subnet firewalls.
Dual-Homed Host Firewalls A dual-homed host firewall consists of a single computer with two physical network interfaces that acts as a gateway between the two networks. The server’s routing capability is disabled so that the firewall software installed on the system can handle all traffic management. Firewall software or proxy server software is typically run on this system to pass packets from one side of the dual-homed system to the other. You must be careful not to enable routing within the network operating system that will be used as the dual-homed system; otherwise, you will bypass your firewall software and simply be routing data. Figure 8-7 shows a dual-homed host firewall configuration.
FIGURE 8-7
A dual-homed system acting as a firewall has two network interfaces.
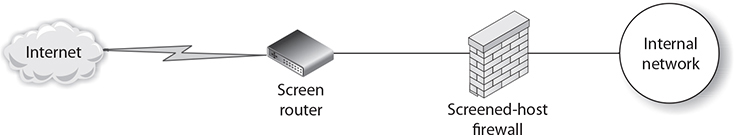
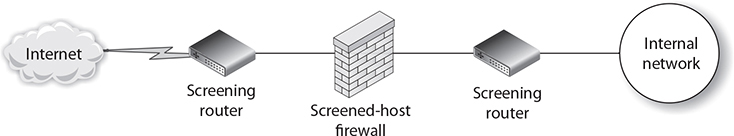
Screened-Host Firewalls Screened-host firewall configurations are considered by many to be more secure than dual-homed firewalls. In this configuration, you place a screening router between the dual-homed host and the public network. This enables you to provide packet filtering before the packets reach the dual-homed firewall, thereby adding an extra layer of network security. The dual-homed system can then run firewall software or proxy server software to provide additional security to this configuration. Figure 8-8 shows a screened-host configuration.
FIGURE 8-8
A screened-host firewall configuration provides an extra layer of security by adding a packet-filtering router in front of the firewall.
Screened-Subnet Firewalls A screened-subnet firewall configuration takes security to the next level by further isolating the internal network from the public network. An additional screening router is placed between the internal network and the dual-homed firewall. This provides two additional levels of security. First, by adding a screening router internally, you can protect the dual-homed firewall host from an attack by an internal source. Second, it makes an external attack much more difficult because the number of layers an attacker must go through is increased. Normally, the outside screening router will be configured to send any data that has passed the filter rule to the dual-homed firewall, which will perform more tests on the incoming traffic. Once the incoming traffic has passed the test performed by the dual-homed system, the traffic may then be sent to the internal screening router, where additional tests on the packet are performed. The internal screening router is typically configured to accept only data from the dual-homed firewall, ensuring that hackers can’t skip past the outside firewall layers. Figure 8-9 shows the screened-subnet firewall configuration.
FIGURE 8-9
A screened subnet uses two screened routers and a firewall.

For the Security+ certification exam, know the different types of firewall topologies such as dual-homed, screened host, and screened subnet.
Security Zones
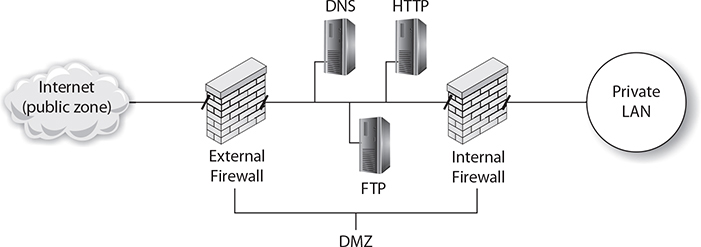
Firewalls allow the network administrator to divide the network into different network segments known as zones. As shown in Figure 8-10, when creating your firewall plan, you will typically create three zones:
FIGURE 8-10
Firewalls divide networks into different zones.
■ Private LAN/intranet The firewall placed in front of the private LAN ensures that no traffic from any other network is sent through the firewall to the private LAN. Note that this zone could be called the private zone, private LAN, or intranet zone.
■ DMZ The DMZ is an area between two firewalls (typically referred to as external and internal firewalls) that allows selected traffic from the Internet to pass through the external firewall into systems within the DMZ. The purpose of the internal firewall is to not allow any traffic originating from the Internet to pass through it. The DMZ is where you place any servers that need to be reached by the general public, such as a web server, SMTP server, FTP server, or DNS server.
■ Public zone The public zone is any network not controlled by the network administrator. The best and most popular example of a public zone is the Internet. As a firewall administrator, you will control which traffic comes from the public zone to the intranet zone.
Organizations are now looking to expand on the number of zones within their network to create different network segments for different types of users on the network. For example, many companies are creating a guest network segment (a guest zone) that allows a visitor to get Internet access, but anyone on the guest zone cannot communicate with systems on the private LAN. The following are some other common zones created on networks today:
■ Extranet An extranet zone includes servers you want to make accessible to selected organizations via the Internet or other public zones.
■ Wireless The wireless network could be placed in a network zone of its own, which gives the firewall administrator the opportunity to control which zones the wireless client can access. For example, you may not want the wireless network to access the intranet and extranet zones.
■ Guest The guest zone is designed for visitors to your office location. Visitors typically do not need access to the private network or even the extranet zone; they typically just need Internet access to check e-mail and access Internet resources. You can create a guest zone that has access to the public Internet zone but does not have access to any of the other zones.
One last concept or Security+ term related to designing security within your organization is the concept of zero trust, also known as the zero trust security model. Zero trust is the principle that when you’re designing the network, network devices and systems that are connecting to the network should not be trusted by default. Because today’s networks have a number of network segments, and a large number of types of devices connecting to those segments, it is important to implement mutual authentication and health checks of systems before granting them access to the network. End-user devices are a classic example of devices that should fall into the zero trust security model.

For the Security+ exam, know that the purpose of segmenting your network into different zones is so you can control communication between the zones. For example, you wouldn’t want a system in the Internet zone or the guest zone to access resources in the intranet zone.
INSIDE THE EXAM
Understanding DMZs
For the Security+ certification exam, know that the demilitarized zone (DMZ) is an area between two firewalls: an external firewall and an internal firewall. The DMZ is an area on the network that you allow selected traffic from the Internet to reach. You normally place DNS servers, web servers, FTP servers, and SMTP servers in the DMZ.
The following ports are opened on the external firewall to allow communication to the appropriate services inside the DMZ:
■ DNS UDP port 53
■ HTTP TCP port 80
■ FTP TCP port 21 (control port) and port 20 (data port)
■ SMTP TCP port 25
■ SSH TCP port 22
 To see a demonstration of how to configure separate zones on a Watchguard UTM security device, watch the video included in the online resources that accompany this book.
To see a demonstration of how to configure separate zones on a Watchguard UTM security device, watch the video included in the online resources that accompany this book.
NAT and Ad Hoc Networking
Many firewall solutions provide network address translation (NAT), which allows you to use a private address range on the inside of the network that is then translated to a public address used on the NAT device. This is accomplished by the NAT device having one of its interfaces connected to the Internet (known as the public interface), while the other interfaces are connected to the private network (known as private interfaces). The public interface is connected to the Internet and gets an IP address (a public IP address). The other interfaces on the NAT device are assigned private addresses, and all systems inside the network have a private address in that same range. When someone on the private network tries to surf the Internet, for example, the packet first goes from the client computer to the NAT device, which switches the private source IP address of the packet to the IP address of the public interface on the NAT device. The packet is then sent out on the Internet so that as far as anyone on the Internet is concerned, it is the NAT device surfing the Internet. The rest of the systems remain hidden on the private network.
Ad hoc networking involves a topology with no central server or device to create the network; you simply connect two devices together, such as two laptops on the fly, to create a network. A good example of this is an ad hoc wireless network where there is no wireless access point, just two laptops with wireless network cards that connect directly with one another so that the laptop users can share information.
Proxy Servers
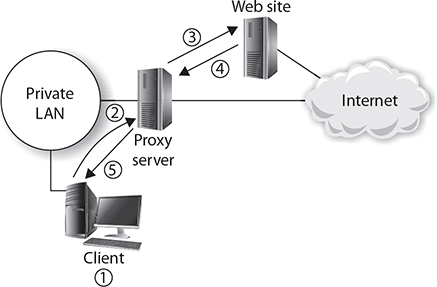
By definition, a proxy server is a server that performs a function on behalf of another system. A proxy server is responsible for making requests for Internet resources on behalf of the systems within the organization (because it is using NAT technology). Figure 8-11 and the following list detail how a proxy server works:
FIGURE 8-11
How a proxy server works
1. The workstations (clients) on the network are configured to send Internet requests to the proxy server.
2. A workstation submits a request for a web page on the Internet to the proxy server.
3. The proxy server then connects to the Internet site on behalf of the user and transmits the request on to the Internet web server.
4. The Internet web site sends the reply to the proxy server.
5. The proxy server sends the reply to the original workstation that made the request.
The benefit of a proxy is that from the outside world’s point of view, the request came from the proxy server (which it actually did). If someone looks at the source IP address of the request and decides to attack that source IP address, then they are attacking the proxy server and not the internal system. At no point did the workstation inside the network make a connection to the Internet resource!
Some proxy servers implement a caching feature as well, which stores the web page that was requested by the client on the proxy server. The benefit of this is that the next client that requests the same web page can receive the page more quickly because the proxy server already has the content and does not need to retrieve it from the Internet.
Proxy servers also allow the administrator to have a central point where they can log and filter what web sites users are allowed to visit. Most proxy servers have reporting features so that the administrator can view a list of the most-visited web sites. The administrator can then choose whether to continue to allow access to a site or, if it is not of a business nature, to deny access to the site.
One of the key features of proxy servers is that users typically authenticate to the proxy server so that the proxy server can then control access to what web sites the user can visit or what Internet applications the user can employ.

For the Security+ certification exam, know the purpose of a proxy server and that it offers caching and filtering capabilities.
There are different types of proxy servers, or different functionality that is offered by your proxy server. For the Security+ exam, be sure to know these proxy functions:
■ Forward and reverse proxy A forward proxy is what was describe earlier—the client sends the request to the proxy server, and the proxy server retrieves the resource out on the Internet and sends the response to the client. With a forward proxy, the internal system does not talk to a system on the Internet directly. A reverse proxy is used in a scenario where you want a system on the Internet to be able to send a request to one of your internal systems, such as a web server or mail server. In this situation, the direction of communication is reversed, but all communication still goes through the proxy (reverse proxy in this case). The system on the Internet sends the request to the reverse proxy server, which then forwards the request to the internal server after checking that the request is not malicious.
■ Transparent proxy A transparent proxy is a proxy solution that does not require any software or additional configuration on the client. For example, nontransparent proxy solutions require you to install a proxy client, or agent, and configure the applications to point to the proxy server for outbound requests. With a transparent proxy, you do not need to install or configure client software; you simply configure the IP default gateway setting to point to the proxy server. The user has no idea they are configured for a proxy; they simply think the IP address of the default gateway is referring to the router address.
■ Application/multipurpose Proxy servers are known as application-layer firewalls and can inspect many different areas of the packet, such as the header and data portion of the packet. This means that you can filter packets by source and destination IP address and source and destination port number like you can with a packet-filtering firewall, but with an application-layer proxy you can also filter by the data portion of the packet. For example, the proxy stops FTP put commands but allows FTP get commands to pass through the proxy/firewall.
■ Content/URL filter Proxy servers have the capability to block user access to different web sites based on the URL of the web site or by keywords found in the URL.
Routers and ACLs
Enterprise devices such as routers by vendors such as Cisco have many security features built into them. For example, on a Cisco router you can create access control lists (ACLs) that configure the router to inspect each packet as it arrives and analyze the layer-3 (IP) and layer-4 (TCP/UDP) addresses in the packet to determine whether it is allowed to pass through the router.
Routers also have many security features built in that can protect from known security vulnerabilities, such as DDoS protection features that block traffic that appears to be a DDoS attack, and anti-spoofing features that block packets that appear to be spoofed (someone altered their source address) in order to trick the router into allowing the packets to pass through the ACL.
Other Security Devices and Technologies
The Security+ exam objectives expect you to know other types of security devices for the certification exam. The following is a list of other security devices to be familiar with:
■ Web security gateway A web security gateway is a device or software that protects your network from malicious content on the Internet. Web security gateways not only protect your employees from inappropriate content such as pornography on the Web but also scan the content for malicious code, and they can provide data loss prevention (DLP) for your company by ensuring that employees are not posting sensitive information on the Web.
■ VPN aggregator You can centralize your virtual private network (VPN) access by having all employees go through a VPN aggregator in order to access the network. The VPN aggregator is where you configure the authentication and encryption protocols. The VPN aggregator also supports high availability so that it is always available to answer VPN requests from clients. When implementing your VPN solution, you can configure the VPN aggregator to allow clients to connect remotely to the network. Or you could implement remote access, where VPN aggregators are used to connect from one site to another site (known as a site-to-site VPN) to allow entire offices to communicate over a secure connection. In this scenario, the client computers would not need to establish the VPN connection manually like they would in a client access scenario.
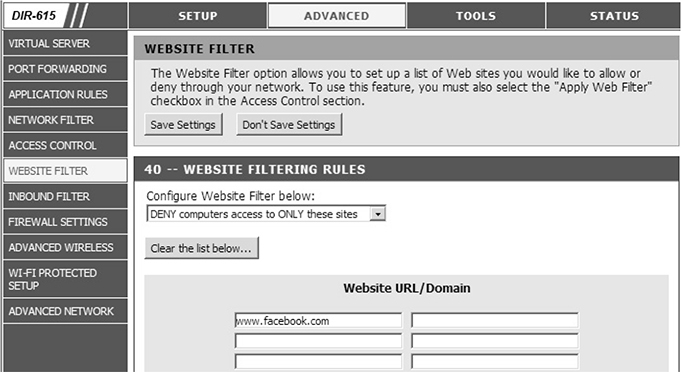
■ URL filter Most proxy servers, Internet gateway products, and even your home routers allow you to configure URL filters (see Figure 8-12), which are listings of web sites that you want to allow or deny access to.
FIGURE 8-12
URL filters limit what web sites can be visited.
■ Content filter Again, most proxy servers and Internet gateway devices can inspect the content of a page and, based on the type of content the user has requested, either deny or allow the content to enter the network.
■ Malware inspection As mentioned earlier in the list, a number of Internet gateway products not only inspect web page content to see whether it is inappropriate but also check for malware in the content.
CERTIFICATION OBJECTIVE 8.02
Using Intrusion Detection Systems
Having a firewall protect your network from unwanted traffic is definitely a must, but network security involves a lot more than just implementing a firewall solution. You want to be sure to configure your system to monitor internal network activity so that you can identify potential threats before they get out of hand.
In this section you learn about intrusion detection systems and how to do basic configuration of Snort—a very popular network-based intrusion detection system.
IDS Overview
An intrusion detection system (IDS) is responsible for monitoring activity on a system or network and then logging or notifying the administrator of any suspicious activity.
Analysis Methods
How the IDS determines that there is suspicious traffic depends on the type of analysis the IDS performs. The following sections outline the different methods an IDS uses to determine if there is suspicious traffic.
Signature-Based Systems With a signature-based IDS, the IDS has a signature file that lists what is considered suspicious activity. When the IDS captures activity, it compares the activity against the signature database, and if there is a match, it sends out notification of an intrusion.
For example, you may have a system that notifies when a number of SYN messages are sent from a single IP address to a number of ports on the same target system within a short period of time. This is a classic signature of a port scan.
The benefit of a signature-based system is that it has few false positives—meaning minimal false alarms—because a signature-based system bases everything on the signatures that you configured on the system. Because you are looking for specific activity, you will have a limited number of false alarms.
Anomaly-Based Systems An anomaly-based system understands what is considered normal activity (a baseline) and then considers anything outside that normal activity to be “suspicious” activity. The anomaly-based monitoring system typically determines the baseline from the behavior of the person using the system. This is known as a behavior-based anomaly monitoring system.
The benefit of the behavior-based anomaly system is that you do not need to configure a definition file of known suspicious activity; the system learns what is normal based on the users’ activity. The drawback of a behavior-based system is that anything outside the norm is considered suspicious, which results in a large number of false alarms (false positives).
Heuristic/Behavior Analysis Heuristic analysis is an analysis type that identifies malicious activity based on vendor-generated rules that are stored in a database and then used by the detection software. The vendor rules are created based on past experiences with malicious activity. Heuristic analysis is a popular approach with antivirus software. With virus detection, the goal of heuristic analysis is to detect new viruses that are unknown. The virus protection software typically runs the program in an isolated area known as a virtual machine (VM). The virus protection software then analyzes everything the program does when it executes and compares the activity to past experiences. For example, the antivirus software may look for malicious activity such as file overwrites or signs the program is replicating itself or trying to hide itself.

For the Security+ exam, remember that a signature-based system determines suspicious activity based on the signatures in a file that you would need to program or keep up to date. An anomaly-based system determines malicious activity based on the activity being abnormal. Heuristic analysis monitors the activity and knows what is suspicious based on past events.
Types of IDS
When implementing your intrusion detection system, you have a choice of implementing a host-based IDS or a network-based IDS. The following is an overview of the difference between the two types of IDSs.
Host-Based IDS You learned in Chapter 7 that a host-based IDS (HIDS) is installed on a single system and monitors activity on that system. The HIDS identifies suspicious activity by monitoring areas such as memory, system files, log files, and network connections, to name only a few.
Implementing an HIDS has the limitation that it can monitor only activity on the system the software is installed on. If you wanted to monitor for suspicious activity on multiple systems, you would have to install the HIDS software on multiple systems.
Network-Based IDS A network-based IDS (NIDS) can be installed as its own network device or as software on a system. Either way, the NIDS analyzes all traffic that travels across the network. The NIDS analyzes the network traffic and looks for suspicious activity, logs the details of the activity, and sends out an administrative alert.
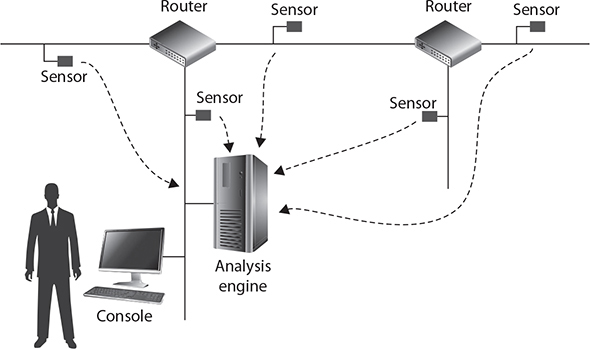
As shown in Figure 8-13, the NIDS is made up of a few components that work together to identify the suspicious traffic:
FIGURE 8-13
Components of a network-based IDS
■ Sensors A sensor is a piece of software or hardware that is placed on each network segment and is responsible for collecting traffic from that segment and then forwarding the traffic to the analysis engine—or to a collector if your infrastructure has one. A collector is a component that collects all the traffic from the sensors and sends it to the analysis engine.
■ Analysis engine Also known as a correlation engine, the analysis engine is responsible for receiving the packets from the sensor (or collector) and then performing the analysis on the packets to determine if they are considered suspicious. For example, if the NIDS in this case is a signature-based IDS, then the analysis engine compares the packets against a database of known-suspicious traffic.
■ Console The console is also known as the administrative console and is where the alerts and notifications are typically sent. The administrator configures the NIDS from the console.

For the Security+ certification exam, know that a network-based IDS monitors network traffic to identify suspicious activity. Also note that if the traffic is encrypted, the network-based IDS will be unable to monitor the traffic.
Classes of IDSs
You need to be familiar with different classes of IDSs for the Security+ certification exam. The class of IDS indicates how the IDS responds to suspicious activity—does it simply log the activity or also take some form of corrective action?
Passive vs. Inline IDS A passive IDS monitors for suspicious activity, and when it detects activity it considers suspicious, it simply logs the activity to a log file and sends notification to the administrator. It is important to understand that a passive IDS does nothing to try to protect the network from further suspicious activity. Note that a passive IDS configured this way is typically connected to a monitoring port or a network tap to allow the IDS to receive all network traffic.
An inline IDS is an IDS that is placed in the pathway of the packets so that the packets pass through the IDS to reach the destination. The benefit of this is that the IDS can take action (which technically makes it an IPS, but more on that in a second) such as blocking the traffic if it is suspicious. Another benefit of an inline IDS is that if the IDS fails, no packets can make it through the system until the IDS is fixed. With a passive IDS that is simply receiving a copy of all data and monitoring the data, if the IDS fails, the traffic still reaches the destination but isn’t inspected.
Active IDS and IPS An active IDS monitors for suspicious activity, and when it detects any activity it considers suspicious, it may log the activity to a file and send notification to the administrator, but it will also take action to protect the environment. For example, if the active IDS notices that a system is performing a ping sweep, it may disconnect that system from the network so that the suspicious system cannot send any more traffic.
It is important to note that the term “active IDS” has been phased out, and now an active IDS is referred to as a network intrusion prevention system (IPS) because it takes steps to prevent the suspicious activity from continuing.

For the Security+ certification exam, know that a passive IDS only sends out notifications or logs the suspicious activity, and as a result it is considered a detective control. An intrusion prevention system (IPS) will take corrective action. As an example, the IPS may disconnect the suspicious system from the network in order to prevent any other activity from the suspect system. An “active IDS” is now known as an IPS and is considered a prevention control.
HIPS vs. NIPS There are two major categories of intrusion prevention systems. A host-based intrusion prevention system (HIPS) is responsible for monitoring activity on a single system, typically by looking at logs, identifying suspicious activity on that system, and then taking corrective action. A network-based intrusion prevention system (NIPS) is responsible for monitoring all network activity (not just activity on one system) and identifying suspicious network traffic before taking corrective actions.
In-Band vs. Out-of-Band In the IDS and IPS context, in-band refers to an IPS that is placed inline, which means that the traffic must pass through it to make it to the destination systems. This allows the IPS to not only monitor but also block the traffic if it is suspicious. Out-of-band refers to an IDS/IPS that simply monitors traffic that travels through the network by having a copy of the traffic sent to it. In this scenario, the IDS can only trigger alerts or send notification to the administrator of the suspicious traffic.
Rules When configuring the IDS, you configure rules to indicate the type of traffic that is considered suspicious and what action to take when that traffic is detected. For example, the following code generates a rule that logs ICMP type 8 packets (echo request messages) that have a source IP address that is not from our internal network of 192.168.1.0 and a destination address that is for any system on the 192.168.1.0 network. In the log file, we record the display text of “ICMP Traffic Detected” along with the packet details.
![]()

For the Security+ exam, know that an intrusion prevention system can be a host-based intrusion prevention system (HIPS) or a network-based intrusion prevention system (NIPS). The HIPS detects and helps prevent intrusion attempts against a single system, whereas the NIPS detects and prevents intrusions against the network.
Analytics The analytics engine is the component of the IDS that does the analysis of the traffic collected. The analytics engine uses the rules you have configured on the IDS to determine what is considered suspicious traffic. The action in the rule tells the IDS how to respond to the suspicious traffic.
False Positive vs. False Negative When evaluating IDSs, be sure to verify the likelihood of false positives and false negatives with the product. Having an IDS that reports a high number of false statements is bad news because it means the IDS triggers alarms when it shouldn’t or doesn’t trigger alarms when it should. Know the following false results for the Security+ exam:
■ False positive A false positive is when the IDS states there was suspicious activity (positive), but in reality, there was not (a false assumption). In simple terms, the IDS reports suspicious activity but none occurred.
■ False negative A false negative is when the IDS does not see any suspicious activity, and again that was incorrect—there really was some! In simple terms, the IDS fails to detect suspicious activity that actually occurred and thus doesn’t report it.
EXERCISE 8-2

Using Snort: A Network-Based IDS
In this exercise, you learn how to use Snort, a popular network-based intrusion detection system. Keep in mind that Snort is complicated software, and the goal here is to simply introduce you to an example of a network-based IDS.
1. Ensure that the Linux, Windows 10, and ServerA VMs are running.
2. Download and install Snort from the Internet onto the ServerA VM. After installing Snort, be sure to install WinPcap, which is the packet-sniffing driver used by Snort.
3. After installing WinPcap and Snort, launch a command prompt (be sure to run as administrator) and type the following:
4. List three of the folders that you see there: _______________
5. To start Snort, go to the bin directory by typing cd bin.
6. To view the version of Snort you are using, type snort -V.
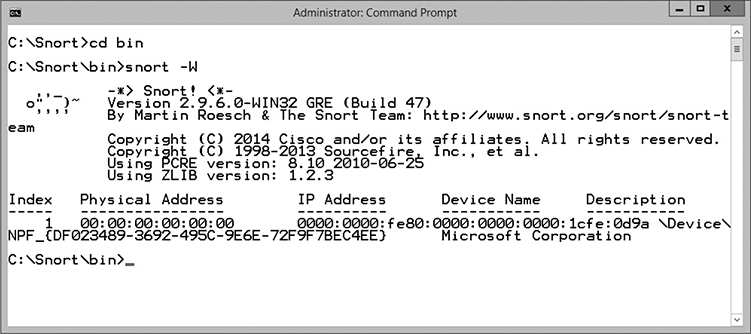
7. To view a list of network adapters that Snort can use, type snort –W. What interface number is your network card? ______
Notice in the following illustration that my network card has an index/interface number of 1 (in the index column):
Monitor Traffic with Snort
8. To use Snort to monitor traffic on the screen, type snort –i# -v (where # is your interface number) and press enter.
9. Go to one of the other virtual machines and create some traffic, such as FTP, HTTP, or Ping traffic.
10. Switch back to the ServerA VM and then press ctrl-c to stop Snort.
11. Review the output by scrolling to the top and navigating down.
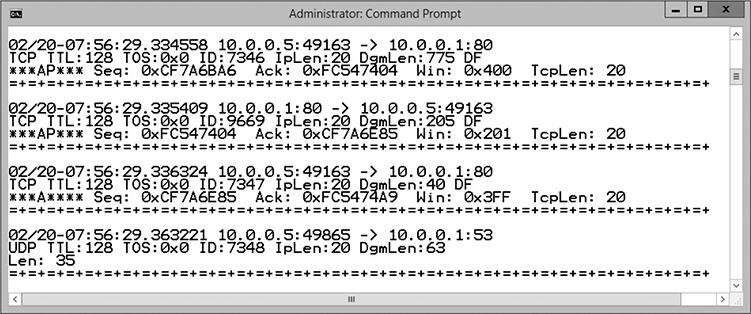
12. Can you see the traffic you created? _______________
Notice in the preceding illustration that I have a packet destined for port 80 on the 10.0.0.1 system that came from 10.0.0.5.
Logging with Snort
13. Ensure you are on the ServerA VM.
14. At the command prompt, you will use Snort to capture the payload data (-d) and log traffic (-l) to the snortlog folder by typing
![]()
where # is your network interface number.
15. Go to another VM and generate network traffic with Ping, FTP, or HTTP.
16. Switch back to ServerA and then press ctrl-c to stop Snort.
17. Through My Computer, navigate to c:snortlog.
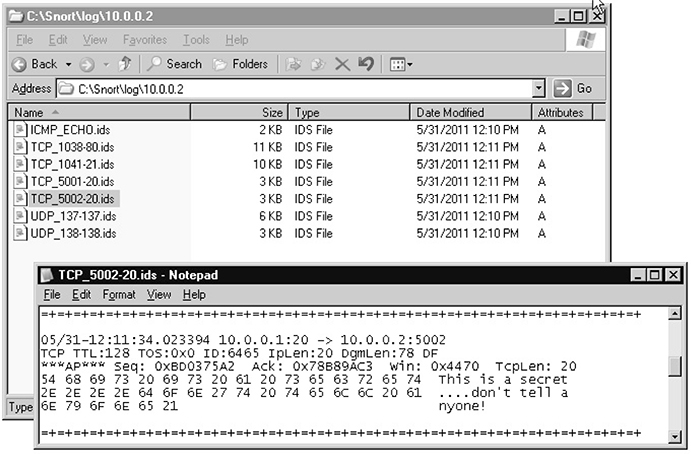
18. Do you see a subfolder for each IP address involved in network traffic? _______________
19. Open each of the log files and view the details.
Rules with Snort
20. Ensure you are on the ServerA VM.
21. With Snort, you can program rules that are signatures of the types of traffic you wish to be notified of. Each rule starts with an action such as “alert,” indicating that you want Snort to store any traffic that matches the rule to an alert file. Then you have the protocol such as TCP, UDP, IP, or ICMP. Then you have the source IP and port address with an arrow pointing to the destination IP address and port number. Finally, in brackets you can specify options that are different fields in the headers you can look for. Start Notepad and type the following rules (watch for typos):

22. The following outlines what each rule does:
■ The first rule identifies any web traffic with the word “facebook” in it.
■ The second rule watches for ICMP echo request messages.
■ The third rule watches for the word “password” being transmitted to help identify any potential unencrypted passwords.
23. Save the file as c:snort uleslab.rules and change the file type to “all files” while in the Save As dialog box.
24. To use the Snort rules, go to the snort folder at a command prompt and type
![]()
25. Once Snort has started, go to another system and create some traffic such as Ping or FTP, and if you have Internet access in the VM, surf the Facebook site.
26. Go back to the ServerA VM and stop Snort with ctrl-c.
27. Open My Computer and navigate to the c:snortlog folder.
28. Do you have an alert.ids file? _______________
29. Open the alert.ids file and review the contents. You should see your Ping traffic and FTP traffic.

![]() Snort is a very powerful, open-source, network-based intrusion detection system well worth spending some time with. And it’s free! You can download it from www.snort.org.
Snort is a very powerful, open-source, network-based intrusion detection system well worth spending some time with. And it’s free! You can download it from www.snort.org.
Deception and Disruption
Another method of detecting intrusions is by using a bit of trickery to catch the attacker red-handed, collect information about them, and slow down their attack against production systems. You can use a combination of technologies such as honeypots, honeynets, and honeyfiles to capture the attention of the hacker to lure them into your trap!
Honeypots and Honeynets
A honeypot is a system that is placed on the private network, or in a DMZ, and is designed to lure the hacker away from production systems and to the honeypot. The hacker spends time trying to hack into the honeypot, but all the while, you are logging the activity and having the host-based IDS installed on the honeypot send you notification of the hacker’s existence.
Most companies make the mistake of not securing the honeypot because they want the hacker to break into it, but if you make it too easy for the hacker to compromise the honeypot, the hacker may walk away, sensing a trap. It is critical that you challenge the hacker by hardening the honeypot and that you implement security controls to make the system appear as if it may have value.
Another common security term is honeynet, which is an entire network designed to appear as a production network but is solely there to lure the hacker away from the real production network.
Honeyfiles
A honeyfile is a file you place on a system to get the hacker to open it. When the file is opened, you can have an alert sent out that informs you of this fact so that you are aware there is someone on the system. For example, you could place a file on the desktop called passwords.txt that tricks the attacker into thinking you have a file with all your passwords in it. When the hacker opens the file, an alert is sent out informing you that the file has been opened.
DNS Sinkhole
A DNS sinkhole is when the DNS server responds with fake IP address information for known-malicious URLs or domain names. These fake IP addresses are sent to the clients so that the clients do not connect to known-malicious addresses.
Fake Telemetry
Telemetry is data that is collected for monitoring purposes. Some applications allow you to generate fake telemetry data, which could be information about the infrastructure, servers, and clients. Fake telemetry data can be generated to test solutions that use telemetry data.

For the Security+ certification exam, know deception and disruption techniques such as honeypots, honeyfiles, and DNS sinkholes. Remember that a text file on the desktop called passwords.txt is a classic example of a honeyfile.
Protocol Analyzers
Intrusion detection systems and honeypots deal with monitoring the hacker’s activities and discovering malicious activity on the network or system. Another common tool you can use to discover suspicious activity is a protocol analyzer (also called a packet sniffer). The protocol analyzer, or packet sniffer, can capture all traffic on the network segment and can be used to identify suspicious traffic.
For example, you may use a packet sniffer such as Wireshark (see Figure 8-14) to capture network traffic and realize that there are a number of TCP SYN messages coming from the same system that are destined for different ports on the same target system. This is a great indication that someone is doing a port scan on the network.
FIGURE 8-14
Packet sniffers can help identify abnormal traffic.
Monitoring traffic today is a little harder than in the past due to the security features of a network switch. Remember that a switch only forwards the traffic to the port that the destination system resides on, so having the packet-capturing software is not enough today. To capture traffic today, you must be running your network card in promiscuous mode, which means that your network card will receive all traffic. Normally, systems receive and process only traffic that has a destination MAC address in the header of the packet with its own MAC address or the broadcast address.
Not only do you need to have a card that can be placed in promiscuous mode, but you need to be able to bypass the filtering feature of the switch. Here are two common methods that administrators use to do this:
■ Port spanning/port mirroring If you configure port spanning, also known as port mirroring, your switch will send a copy of all traffic to whatever port you configure as the mirrored port. You would then connect your monitoring station, or IDS, to that mirrored port so that the system can receive a copy of the traffic.
■ Network tap/port tap You can also use a network tap device, also known as a port tap, which is a piece of hardware that can be connected to the network and has ports available to connect a monitoring system to the device.
CERTIFICATION OBJECTIVE 8.03
Network Design and Administration Principles
Core network design elements such as subnetting, segments, and VLANs make up a big part of the security infrastructure for the network. In this section you learn about the importance of core network technologies and how they relate to security.
Network Segmentation
Network segmentation is a big part of network security and involves creating different smaller networks, known as segments, within your network. The benefit is that you can place routers or firewalls between each of the network segments that allow you to control what traffic is allowed to pass between the network segments. The term we use for traffic traveling within the network is east-west traffic. For highly secure environments, you can decide to not connect some network segments together—thus isolating a segment from the rest of the network to ensure communication to the segment cannot occur. As a reference, north-south traffic represents traffic from outside your network, such as the Internet coming into the network. When you are diagraming this, the external networks such as the Internet are at the top of the diagram, while your network is south of the external networks. Once in your network, the segments are considered east-west traffic.
Subnetting for Segmentation
Each network segment will require its own IP block so that the routers can route traffic throughout the network segments. Subnetting is the logical division of IP address blocks into smaller network blocks. Network administrators normally subnet in order to match the physical network structure. For example, if your company has one network address, such as 216.83.11.0, but two different physical networks connected by routers, you will need to break the one network address into two different network addresses, known as subnets.
To break the network address into two (or more) subnets, you need to manipulate the subnet mask of that network ID. In my example, the default subnet mask is 255.255.255.0. To subnet into two networks, I will need to convert the first bit of the last octet in the subnet mask to a 1. This gives me a new subnet mask of 255.255.255.128 and two subnets known as the 216.83.11.0 subnet and the 216.83.11.128 subnet.
I know that is a quick review of subnetting from your Network+ days, but the key point is that subnetting has a bit of a security benefit, because once you assign someone to a logical subnet (IP address range), they are able to communicate only with other systems in that IP address range unless you have a router to route between the networks.
Physical Segmentation
Another method of implementing control on communication is to break your network up into multiple physical network segments. A network segment can be created in a few different ways, depending on what your goals are:
■ Multiple collision domains If your goal is to have multiple collision domains, then you can segment the traffic by using a bridge, switch, or router. Each interface on each of these devices creates a collision domain, which is a group of systems that can have their data collide with one another. Each of these collision domains is also known as a network segment, with the security benefit being that a hacker monitoring traffic while on a network segment by default can capture only traffic on that segment.
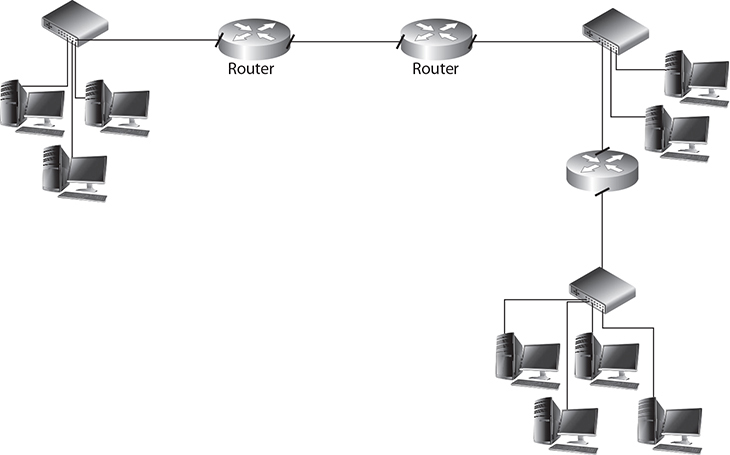
■ Multiple broadcast domains If you want to control how far your broadcast messages go on the network, you can use routers to break the network into multiple broadcast domains. The benefit of breaking the network into multiple broadcast domains with routers is that you can then use access control lists on the routers to control what traffic can enter or leave each of the broadcast domains (see Figure 8-15).
FIGURE 8-15
Using routers to segment the network into broadcast domains
Virtual LANs
If you wanted to create communication boundaries by dividing your network into different broadcast domains without using multiple routers, you could do so by using virtual LANs (VLANs) on a network switch. You learned in Chapter 1 that once a system is connected to a port on a switch that is part of a particular VLAN, the system cannot communicate with systems in other VLANs unless a router is used to route the data from one VLAN to another VLAN.

For the Security+ exam, be familiar with the fact that you should secure areas of your network by segmenting networks into communication boundaries. You can do that by breaking the network into multiple networks and using access lists, or you can create communication boundaries with VLANs on a switch.
Virtualization
Virtualization products nowadays allow you to segment traffic using virtual networks. With virtual networking, you can place virtual machines on different network segments and control which VMs can talk to one another.
Air Gaps
Air gap in the context of network segmentation is a conceptual term meaning a network has no connection point with another network. For example, in highly secure environments, there may be a secret network and a nonsecret network. Due to the sensitivity of the secret network, there is to be no physical connection linking the two networks, thus creating an air gap.
Network Switches
Network switches provide great security to the network environment. First off, the network switch is designed to filter traffic and only send data to the destination port of the switch. This means that using a switch prevents someone from easily monitoring network communication. There are a number of other features that switches have to increase the security of the network:
■ Layer 2 vs. layer 3 A switch can be a layer-2 switch or a layer-3 switch. A layer-2 switch does not have any routing functionality; it simply is a switch that is designed to send traffic only to the destination MAC address contained in the layer-2 header of the frame. This is known as media access control (MAC) filtering. A layer-3 switch is essentially a switch and a router all in one. The layer-3 switch has switch ports on it, but also has a few router ports designed to send the data to another network.
■ Port security You can control which systems can connect to ports on a switch by configuring port security. With port security, you enable a port but then associate the MAC address of a particular system with that port. Only the system with that MAC address can connect to the port.
■ Loop protection Loops can cause the network to crash, so it is critical that you have methods of preventing loops on the network. Routers use the time-to-live (TTL) value of a packet to determine when a packet is to be removed from the network. Switches prevent loops at layer 2 by implementing loop prevention protocols such as Spanning Tree Protocol (STP). When you connect switches together, which results in a network loop, STP dynamically selects one of the ports involved in the loop and places it in a blocking state to disarm the loop.
■ Flood guards A flood guard is typically a feature on a firewall or router that allows you to control and block malicious traffic such as flood attacks being sent to your network. A common example of flood traffic is the SYN flood attack, where the hacker sends a number of SYN messages to ports on your network. The flood guard would identify this traffic, stop the traffic from entering the network, and prevent the denial of service (DoS) attack.
■ Broadcast storm prevention With a switch, you can use VLANs to create different network segments, also known as broadcast domains. By doing this, you are limiting the effects of a broadcast storm because broadcast messages are kept within the VLAN.
■ Bridge Protocol Data Unit (BPDU) guard Switches use a protocol known as Spanning Tree Protocol to prevent loops on the network. They do this by sending BPDU frames on the network every 2 seconds to discover any loops that may exist. A hacker connected to the network could perform a man-in-the-middle attack by issuing out their own BPDU frames. To countermeasure this, you can enable BPDU guard on ports so that if the switch sees a BPDU message, it will place the port into an “err-disabled state.” This feature should be enabled on all ports that user stations are connecting to.
■ Dynamic Host Configuration protocol (DHCP) snooping DHCP snooping is a feature you can enable on your switch that allows your switch to detect rogue DHCP servers that have been connected to your network without authorization.

For the Security+ certification exam, remember key security features of a switch, such as VLANs for segmentation, BPDU guard, and DHCP snooping. Remember that with BPDU guard, the switch places the port in an err-disabled state if a BPDU message is sent to the port (likely a hacker performing a man-in-the-middle attack).
Network Address Translation
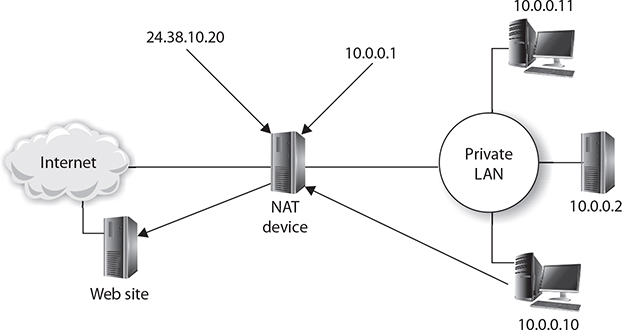
Network address translation, or NAT, is a network technology used for years that allows you to use a private address range on the inside of the network that is then translated to a public address used on the NAT gateway (see Figure 8-16). The security benefit is that you hide the internal IP addresses used by systems surfing the Internet because all outbound traffic has the source IP address translated to that of the NAT gateway.
FIGURE 8-16
NAT is used to hide the internal network and share a public address.
As mentioned, the internal network typically uses what is known as a private address range, which is not usable on the Internet. This means that any outbound traffic has to have the source IP address in the packet converted from the private IP address to a public, routable address by the NAT device. The following are the three private IP address ranges used by the internal network:
■ 10.0.0.0 to 10.255.255.255
■ 172.16.0.0 to 172.31.255.255
■ 192.168.0.0 to 192.168.255.255
There are two major types of NAT: NAT overloading and static NAT. With NAT overloading, all clients inside the network access the Internet using one public address assigned to the public interface of the NAT device. The NAT device not only translates the private IP address to a public IP address, but it translates the port address information as well. This is known as port address translation (PAT) and is used so that the NAT device can track each different client request over the one public address.

For the Security+ exam, remember that NAT is used to hide the internal IP address scheme by having all systems send traffic out the NAT device, which replaces the source IP address in the packet with the public IP address of the NAT device.
Static NAT is when a single public IP address on the NAT device is mapped to a single private address inside the network. This is typically used to handle inbound requests to a server in the DMZ that the company is publishing to the Internet, such as a web site or FTP site.
Network Access Control
Network access control (NAC) is a very hot technology today and allows you to control who gains access to a wired or wireless network based on the state of the connecting system. With network access control, you can specify conditions that a system must meet to gain access to the network. If those conditions are not met, you can then redirect the user to a restricted network from which they can remedy their system.
For example, you may require that in order for a system to connect to the network, it must have antivirus software installed, with the antivirus definitions up to date. You may also require that the system have a personal firewall enabled. If any of these conditions are not met, the NAC system then places the client on a restricted network where they can typically apply patches, or in this case, perform an update of the virus definitions.
When connected to the restricted network, the client has no access to network resources because communication to the private company network from the restricted network is controlled. Figure 8-17 displays a network access control environment.
FIGURE 8-17
Network access control is used to place health requirements on systems connecting to the network.

For the Security+ exam, be sure to be familiar with network access control (NAC) and be able to identify scenarios where NAC is being used.
There are many scenarios where NAC is being used today. The following are some scenarios you should be familiar with and some NAC concepts to be aware of for the Security+ exam:
■ Connecting to wireless When connecting to a wireless network, the NAC system may require the client to accept the terms of wireless network usage before they are given access to the network.
■ Patch status When a client attempts to connect to a network, either locally or through a VPN, its health is checked to ensure antivirus software is installed, virus definitions are up to date, and the system is current with patches before being allowed to connect.
■ Connecting to a switch If the switch is 802.1X compliant, it can be configured to ensure that the connecting client is authenticated by an authentication service (such as RADIUS) before client access to the network is allowed.
■ Agent vs. agentless Network access control solutions can be agent-based or agentless solutions. An agent-based solution requires the clients have client software (the agent) installed that allows the client to authenticate to the system and NAC to determine the health of the system. An agentless solution does not require the client systems to have agent software installed. In this situation, the NAC checks are typically performed by the authentication server as part of the logon process.
■ Dissolvable vs. permanent If you install the agent software on the client system or device, it is known as a permanent (or persistent) agent, because the NAC system can continuously monitor the health of the system. A dissolvable agent is one that is not permanently installed. It is a piece of software that is run to check the current status of the system, but it’s not installed.
■ Host health checks A key feature of the NAC solution is that it has the capability to check the health status of the system trying to connect to the network. As part of the health check, the NAC solution can verify that the operating system is up to date, has antivirus software installed with up-to-date definitions, and has a firewall installed and enabled.
Data Protection
Part of securing the network infrastructure is ensuring that you place protection controls on data to ensure that unauthorized individuals do not get access to sensitive data. There are a number of protection methods you can use to help protect data, such as data loss prevention, encryption, and features such as tokenization and masking.
Data Loss Prevention
Organizations today are looking for ways to implement data loss prevention (DLP) solutions, which are designed to prevent data leaking outside the organization. DLP involves a number of security controls to ensure that data is not leaked outside the organization either intentionally or accidentally. The following are some key areas to implement DLP security controls:
■ USB blocking You can disable the use of USB devices on a system so that users cannot copy data to a USB drive and take the data outside the organization. You can disable the USB devices via software configuration or even disable them at the hardware level within the BIOS settings.
■ Cloud-based solutions Many cloud-based solutions offer the capability to create DLP policies to prevent the sharing of sensitive data. For example, Office 365 offers the capability to create DLP rules for different types of sensitive information such as financial data and health information. These rules can prevent users from e-mailing sensitive information, storing information in the cloud, or even sharing the information on the organization’s intranet.
■ E-mail An e-mail system represents the classic scenario for applying DLP. To prevent users from sending sensitive information in an e-mail message, you can either use an e-mail system that has DLP policy features or purchase or subscribe to a service that provides DLP functionality for e-mail systems.
Masking
Data masking is a common technique within applications to protect sensitive data by replacing the data with a masking character, such as an asterisk (*). A common example where this is used is when displaying customer data on the screen, having the credit card masked out so that the employee looking at the customer record does not know the credit card number of the customer.
Encryption
If working with sensitive data such as PII data, health information, or financial data, you typically look to encrypt the data so that unauthorized individuals cannot get access to this sensitive data. You will learn more about encryption in Chapters 12 and 13, but for now know that sensitive data should be encrypted in the following situations:
■ At rest Sensitive data should be encrypted in storage, whether it’s on disk or stored in a database.
■ In transit/motion As sensitive data is transmitted from one system to another, it should travel in an encrypted format.
■ In processing Data may also be encrypted while being processed until the information is actually being read and needs to be decrypted.
Tokenization
You learned in Chapter 7 about tokenization, but let’s review it here. Tokenization is when sensitive data is stored with a token service instead of with the application data that the sensitive data is used with. The token service also provides a substitute value for that sensitive data that is nonrelevant. The token service then stores the mapping of the sensitive data and the nonrelevant value for future reference so that it can be looked up when needed.
Rights Management
Rights management involves putting protective controls on the data itself to manage the types of actions that can be performed on the data. For example, an e-mail system may put rights management protection on an e-mail message that prevents the user from forwarding the message to someone else. Or a movie rental company may put rights management protection on a movie that allows you to view it for two days, but not after that.

For the Security+ exam, remember the difference between data protection mechanisms such as DLP, masking, encryption, tokenization, and hashing.
Hashing
As you learned in Chapter 2, hashing is a method for ensuring the integrity of data. You can run the data through a hashing algorithm to generate a hash value. If at a later time you wish to verify the file has not been modified, you can run the file through the hashing algorithm again and see if the same hash value is calculated (different content creates a different hash value).
Data Sovereignty
Data sovereignty is the concept that data is governed by the laws of the country that the data resides in. This is a big concern with cloud computing, as companies want to ensure that their data is located within their country so that they understand the laws that govern that data.
Mail Gateway
A mail gateway is a device or server placed in your DMZ that sends and receives e-mail for your organization. When people on the Internet send e-mail to employees within your organization, the mail is directed to the mail gateway within the DMZ. At this point, the mail gateway should do a virus scan and spam filter check on the message to ensure the message is a valid message clean of any viruses. Once the message passes the virus check and the spam filter, the mail gateway then forwards the message to your internal mail server. Keep in mind there is typically a firewall between the DMZ and the internal network, so you will need to configure a rule on this firewall to allow mail traffic from the mail gateway to the internal mail server only.
The following are features you should look for in your mail gateways:
■ Spam filter A spam filter should be configured to check that the message is not a spam message polluting your users’ mailboxes.
■ DLP Data loss prevention should be a feature that can be implemented on the mail gateway so that the mail gateway can ensure that outbound e-mail does not contain sensitive information such as financial or health records or any company secrets.
■ Encryption The mail gateway may implement server-to-server encryption with another mail server at another location within your company, or with a partnering company, so that messages to that company sent across the Internet are not sent in clear text. Also, products such as Cisco IronPort support user-to-user encryption by hosting the encrypted mail on the device until the remote user connects to read it.
Network Communication Encryption
A big part of network security is determining if you want to encrypt network communication. A number of different technologies can be used to encrypt network communication. Let’s take a look at some of our options.
IPSec
IP Security, typically called IPSec, is a protocol that provides different security features depending on how it is configured. IPSec can provide three different security services:
■ Authentication Ensures that the IP packet is actually from the person the packet says it is coming from (the source)
■ Integrity Ensures that the packet has not been altered in transit
■ Confidentiality Ensures that the data in the packet is kept secret by encrypting the packet
The Security+ exam expects you to know the different protocols within IPSec that provide these three different security services:
■ ESP The Encapsulating Security Payload protocol can provide all three services of authentication, integrity, and confidentiality.
■ AH The Authentication Header protocol only provides authentication and integrity services. It cannot be used to encrypt the IP packet.
■ IKE The Internet Key Exchange protocol is used to set up a security association (SA) between two parties. The SA is a unidirectional secure channel, so if the two parties want to send data to each other, typically two SAs are established—one for each direction. The IKE protocol is also the key management protocol for IPSec that allows the parties to exchange encryption keys.

For the Security+ exam, remember the difference between IPSec protocols such as ESP, AH, and IKE.
IPSec can be configured to run in either transport mode or tunnel mode. Transport mode is used for host-to-host encryption, meaning that if two systems want to encrypt communication between them, they run in transport mode. If you wish to encrypt communication from all systems on one network with all systems on another network, you can configure IPSec for tunnel mode. The benefit of tunnel mode is that each client system, or host, does not need to have IPSec configured; you simply configure IPSec on the gateways to each of the networks.
SSL/TLS Encryption
Transport Layer Security (TLS) encryption is the successor to Secure Sockets Layer (SSL) encryption and is used in many scenarios, such as encrypting web traffic, mail traffic, or VoIP traffic. TLS provides confidentiality by encrypting the communication between the two parties using a symmetric key, and it provides data integrity by ensuring the data has not been altered in transit. Authentication services can be configured as well using asymmetric encryption. You will learn more about symmetric and asymmetric encryption in Chapters 12 and 13.
Secure Sockets Layer (SSL)/Transport Layer Security (TLS) inspection is a common topic today when discussing network security because SSL inspection (or TLS inspection) allows security professionals to intercept SSL/TLS traffic as it travels from sender to receiver and decrypt the data for monitoring or inspection purposes. You may want to do this if your security solution needs to inspect encrypted traffic for malicious content, as hackers are using encryption as a method to hide the malicious content.
VPN to Secure Communication
VPN technology enables you to encrypt communication between two parties across an untrusted network such as the Internet. When implementing your VPN solution, you can configure it for remote access, where the clients create the encrypted tunnel with the VPN server. If you need to secure all communication across the Internet between two networks, you can configure a site-to-site VPN. With a site-to-site VPN, the secure tunnel is created by a central device at each office location. All clients on each network send data through the central encrypted tunnel, which gives the benefit of not needing to configure VPN software on each client system.
Another scenario where VPN can be used is with wireless networks. Because wireless security protocols are known to have flaws, you can treat the wireless network as an untrusted network and have a wireless client create a VPN connection to the server before allowing the wireless client to access the corporate network.
Always-On There is a new craze in the VPN world known as always-on VPN. With traditional VPN solutions, the user has to initiate the secure VPN connection by launching the VPN software on their system any time they want to communicate with the corporate network. With always-on VPN, the computer is configured to always establish a secure connection with the company network once the Internet connection is detected (typically when the system starts up). The benefit of always-on VPN is that there is no reliance on the user; the system automatically makes the connection and the feature is transparent to the user.
Split Tunnel vs. Full Tunnel Another VPN option is whether to implement the VPN as full tunnel or split tunnel.
Full tunnel is the traditional implementation in which a user launches VPN software from a remote network, such as their home network, to create an encrypted tunnel between their system and the corporate network VPN server. One of the problems users experience with full tunnel is that they cannot access any resources on the LAN they are connected to (in this case, the home network); for example, if they want to print to their home printer, they cannot because technically once the VPN connection is made, the user is on the corporate network and can access only those resources.
Split tunnel is a VPN feature that allows the user to access the corporate network through the secure VPN tunnel after the VPN software has been launched, but retain the capability to access LAN resources. The split tunnel feature can specify which destination systems are to have their traffic delivered through the tunnel and which traffic stays on the LAN. This is known as split-include tunnel.
Remote Access vs. Site-to-Site When looking at VPN solutions, you should decide if you need a remote access solution or a site-to-site solution. A remote access solution involves an employee using VPN software on their laptop. When they want to connect to the network, they launch the VPN software, log in, and then get connected to the network. As mentioned earlier, a site-to-site solution saves you from needing to install VPN software on each employee’s system, because when a user sends data off the network, the router creates a VPN tunnel to the other location and sends all employee data through that connection. This is a common scenario when a satellite office needs to connect to the head office.
VPN Protocols You will learn more details about security protocols used to perform encryption in Chapters 12 and 13, but in order to complete the VPN discussion, we must discuss the protocols that are used by VPN solutions:
■ IPSec Internet Protocol Security (IPSec) is a protocol that can be used to encrypt all IP traffic and can be used to encrypt your VPN traffic.
■ SSL/TLS Many vendors have VPN solutions that encrypt the traffic with SSL/TLS, much like web traffic is encrypted with digital certificates (again, you learn about this in Chapters 12 and 13).
■ HTML5 HTML5 VPN is based on SSL/TLS encryption and gives us a method to use a clientless VPN connection through the web browser to remotely access a system on the internal network.
■ Layer 2 Tunneling Protocol (L2TP) The L2TP VPN protocol uses IPSec to perform the encryption of data within the VPN tunnel.
API Considerations
An application programming interface (API) is a library of functions that software developers can call upon from their applications. Part of security is ensuring that any third-party libraries that are called upon by your in-house applications are following security best practices. You can ensure that your developers are following secure coding practices, but you should also test third-party components as well.
Network Administration Principles
To create a secure network environment, it is critical that the network administrators follow common, secure network administration principles. The following outlines some fundamental principles or security technologies that network administrators should follow and use when looking to create a more secure environment:
■ Rule-based management Implement rules with technologies that support rule-based management, including routers, firewalls, and proxy servers. Be sure to test the rules that allow or deny traffic, and ensure your rules work as expected.
■ Firewall rules Manage the rules on the firewall in such a way as to allow only required traffic to pass through the firewall. Configure the firewall with a default rule of deny all and then add exceptions for the traffic that is allowed to pass through the firewall.
■ VLAN management Be sure to create communication boundaries on the network with the use of VLANs. By default, systems can only communicate with other systems in the same VLAN unless you configure a router to route between the VLANs.
■ Secure router configuration Ensure that you configure the router in a secure way. This includes creating access control lists, setting passwords for local access to the device, setting passwords for remote access, and only using secure remote access protocols such as SSH.
■ Access control lists Implement ACLs where possible. ACLs are commonly applied to file and folder permissions and to routers and firewalls.
■ 802.1X Implement this common authentication protocol that controls who gains access to a wired or wireless network by requiring the client to authenticate against a central authentication database such as a RADIUS server.
■ Implicit deny When possible, configure routers and firewalls for implicit deny. This means that unless you have a rule specifically added to the device to allow traffic into the network, the router and firewall will automatically deny the traffic. Permissions on folders and files should also have an implicit deny rule.
■ Network segmentation/separation As mentioned earlier, it is critical that you divide the network into smaller network segments and then work on controlling traffic from one network segment to another.
■ Log analysis An overlooked aspect of security is the reviewing of log files on a regular basis. It is important to ensure that you implement logging on all critical systems and devices, and review the logs on a regular basis.
■ Bridge Bridging technology enables systems on one network to connect to systems on another network. An example of a bridge is a wireless bridge, where two networks are connected together over a wireless link. From a security standpoint, keep track of any bridging technologies that are being used so that you are aware of all communication channels that exist.
■ SSL accelerators/TLS accelerators In environments where cryptography is heavily used, you can avoid bogging down your system processor by using an SSL/TLS accelerator, which is a card installed into the system that has its own processor to handle the cryptography functions of the system.
■ SSL decryptors SSL and TLS decryptors are devices on enterprise networks used to decrypt a message so that DLP policies can review the contents. They are also used so malware detection features can scan the message after it is decrypted, or to allow cloud monitoring services to scan the message.
■ Media gateway A media gateway device is a component that is used to translate data streams from one form of communication to another. For example, the media gateway can translate data on your network to a format used by 3G radio networks.
■ HSM A hardware security module (HSM) is a device, typically a card, that can be installed in a server that is used to perform cryptography functions and manage keys for those cryptography functions.
■ Load balancers A load balancer is a device that is used to split the load across a number of servers so that one server is not bogged down with work.
■ DDoS mitigator A DDoS mitigator would be placed between the Internet and your public Internet resources such as web servers and e-mail servers. The DDoS mitigator is a device that monitors network traffic coming from the Internet to your public servers and identifies traffic that may be designed to overburden your servers. The mitigator checks characteristics of the packet, including the source IP address and the HTTP header, to determine if the traffic is coming from a bot. If so, the mitigator blocks that traffic so that it does not reach your public server.
■ Aggregation switches In most organizations, each floor has a switch in a wiring closet that the users on that floor connect to. The switch for each floor is then connected to an aggregation switch within the data center. That aggregation switch acts as a connectivity point for all switches, but also may be a layer-3 switch and be able to route the traffic out to the Internet. If it is not a layer-3 switch, then it would connect to a router, which would then be connected to the Internet.
■ Taps and port mirror Network switches can be configured to send a copy of all network traffic to a port that you can run your monitoring software or IDS on. This is critical because switches filter traffic, preventing anyone but the destination from seeing that traffic. You can also install a network tap device, which would contain multiple ports, plus a monitor port, and receives a copy of all traffic.
■ Out-of-band management Out-of-band management involves connecting to a management port on a network device in order to administer that device (for example, connecting to the console port on a switch in order to configure the device). When securing the device, be sure to lock down management interfaces by configuring a password on them to be used for authentication.
■ DNS When implementing security on DNS servers, be sure to limit what systems can receive zone transfers and look to DNSSec to protect the integrity of DNS zone data.
■ Route security Route security involves protecting your routing devices from attack, including allowing a hacker to gain access and manipulate the routing table. Look to harden your routing device by limiting the protocols running on the device and locking down the running protocols.
■ Quality of service You should monitor the performance of the network and measure the quality of service (QoS) that users are receiving with telephony and cloud-based services.
■ Monitoring services Be sure to lock down any monitoring services and protocols so that hackers cannot gain access to monitored data. For example, ensure devices are using SNMP version 3, which supports authentication and encryption of data.
■ File integrity monitors You can implement file integrity monitors, which allow you to monitor changes to files on the network. If a file is changed, you can have alerts sent to you.
■ SDN Software-defined networking is a feature that can be configured within your virtualization environment that allows you to create virtual networks and segment network traffic.
Business Connectivity Considerations
When looking at enterprise security for your organization, you also want to take into account geographical considerations of your business locations, as the location of your offices can affect the types of natural disasters you can expect and response time of emergency personnel.
You should also consider incident response procedures and the types of recovery controls that your business will rely on in case of a security incident. You will learn more about disaster recovery and business connectivity in Chapter 18, whereas Chapter 21 discusses incident response.
Placement of Security Devices and Network Appliances
When you’re designing the network, it is important to place the different security devices and network appliances at the right locations. The following list identifies key security devices and network appliances as well as where they should be placed:
■ Sensors Sensors should be placed on each network segment so that they can capture network traffic for that network segment and send it to a collector or analysis engine.
■ Collectors You can place a single collector on any network segment and have each of the sensors send captured traffic to that collector.
■ Correlation engines The correlation engine should be running on a system that has access to the data on the collector, and it should be placed on a secure network segment.
■ Filters These components filter different types of traffic and should be placed on the edge of the network. For example, you can use URL filters on your proxy server to block specific sites from users. The proxy server is placed between the Internet connection and your users so that it can review each web site being visited and filter out web sites that have been disallowed.
■ Proxy servers A forward proxy is a device that is placed on the edge of the network between your Internet connection and the users. All requests from the users to Internet resources are passed through the proxy so that it can filter out any unauthorized content. A reverse proxy is placed in the DMZ and is used to publish servers within the network (such as a web server) out to the Internet. When a system on the Internet tries to access your server, it first contacts the reverse proxy (which has the DNS name assigned to it), and then the reverse proxy sends the traffic to the internal system.
■ Jump servers A jump server is a system that is used to access or manage devices in another security zone. The jump server is hardened and configured for secure communication protocols such as SSH, and it’s placed in the zone that contains devices that need to be accessed. The firewalls have strict rules on what protocols and systems can be used to communicate with the jump server.
■ Firewalls Firewalls should be placed at the edge of the network to protect the network from unauthorized traffic coming in from the Internet. You can also place a firewall between different network segments to control traffic between segments.
■ VPN aggregators The VPN aggregator is placed at the edge of the network as well, but behind the firewall so that the firewall can block malicious traffic that may be headed toward the VPN aggregator. The firewall will need to open ports to allow VPN traffic to reach the VPN aggregator.
■ SSL accelerators SSL accelerators can be placed inside any system or server that performs a large number of cryptographic functions.
■ Load balancers Load balancers are typically placed in the DMZ and are generally used to load-balance requests to web applications. You can also place load balancers inside the network for network services that may require multiple servers to split the load.
■ DDoS mitigator The DDoS mitigator is placed between the Internet and your public Internet resources, such as web sites and e-mail servers, so that it can protect those resources from DDoS attacks.
■ Taps and port mirror You can place a network tap device on each network segment so that it sends a copy of all data to your monitoring system. The monitoring system is connected to the port mirror and runs software to monitor network traffic.
Configuration Management
Part of creating a secure network infrastructure is ensuring that your company has a configuration management policy in place that dictates the change management process that needs to be followed in order for changes to be implemented on the network. This includes deploying the change in a test environment before making the change in production.
Change management also involves having up-to-date network diagrams of the network environment and ensuring that there is a baseline configuration that can be applied to new devices. The baseline configuration is a tool that is used to ensure consistent configuration across all devices, thus preventing configuration errors from occurring. You should also ensure standardized naming conventions are used for systems and devices on the network to aid in the understanding of what the names of devices are. You should also document the Internet Protocol (IP) address scheme that is used on the network, especially if you are using multiple network segments with different IP blocks on each segment.
CERTIFICATION OBJECTIVE 8.04
Securing Devices
The last topic in this chapter reviews some common practices for securing network devices. Over the last few chapters, you have read that common steps should be taken to secure systems and devices. Let’s review some of these points as they relate to network devices:
■ Privilege escalation Be sure to keep up to date on how someone connecting to a system or device can raise their privileges on the system and gain administrative access to it. This typically happens due to a vulnerability in the product, so be sure to apply updates to the system or device. Applying updates to a device involves upgrading the firmware on the device as revisions to the firmware come out.
■ Weak passwords I cannot believe how many administrators are still using weak, obvious passwords. During an assessment on a company’s Cisco router, I viewed the running configuration and noticed that the company administrator configured Telnet access to the router with a password of “telnet.” I also gained administrative access to the router by typing a password of “cisco.” Not only are these not strong passwords, they are also common passwords that a hacker would attempt to use to gain access. Another security issue in this example is that I should not have been able to view the passwords because they should have been encrypted in the configuration. With Cisco devices, you can use the service password-encryption command to encrypt passwords in the configuration files.
■ Back doors Review network devices for potential back doors. A good example that I find is that network administrators configure passwords on the console port of a router but do not set a password on the auxiliary port of a router (if one is present). The auxiliary port is like another console port, and someone who has physical access to the router can connect to it to administer the device. Be sure to password-protect all ports on these devices!
■ Default accounts Watch out for default accounts that exist on a system or device, and be sure to guard those accounts with strong passwords. If at all possible, you should rename the default accounts to something that’s not so obvious.
■ DoS A variety of denial of service attacks can be performed against network systems and devices. Implementing a flood guard on your firewall should protect your system from most DoS attacks, because most involve the hacker attempting to flood your system with so much information that it crashes your system. A flood guard blocks the flood messages from entering your network.
CERTIFICATION SUMMARY
In this chapter you learned about common network components that can be used to help increase security in your network environment. Be sure to know the content of this chapter well because you are sure to get questions on firewalls, NAT, NAC, and other security devices on the Security+ exam. The following are some key points to remember regarding this chapter:
■ Know the difference between a packet-filtering firewall (stateless), a stateful packet inspection firewall, and an application-layer firewall.
■ Different firewall topologies include a dual-homed firewall, screened-host firewall, and screened-subnet firewall. Your firewall design should create different zones on the network, such as the private zone and the public zone.
■ Proxy servers are popular devices that allow you to control the type of content and applications users on the network can use when accessing the Internet.
■ Know the difference between a host-based IDS and a network-based IDS. Also know that an IDS detects an intrusion, whereas an IPS detects and prevents an intrusion.
■ Use network design principles to help create a secure network environment, such as creating multiple network segments and controlling what traffic can pass from one segment to another.
■ Don’t confuse NAT and NAC. NAT is a feature that is used for Internet access and translates the private address information to a public address. NAC is used to check the state of the system connecting to the network, and if it does not pass the requirements, then the system is not connected to the network.
■ Common security practices with regard to network devices include ensuring that complex passwords are used, renaming or disabling default accounts, and keeping the system up to date with patches, to name a few.
✓ TWO-MINUTE DRILL
Understanding Firewalls
![]() A packet-filtering firewall allows you to filter traffic by the layer-3 header (IP) and the layer-4 header (TCP or UDP). A stateful packet inspection firewall can do packet filtering, but also knows about the context of the conversation. An application-layer firewall can look at the application data in the packet and make decisions.
A packet-filtering firewall allows you to filter traffic by the layer-3 header (IP) and the layer-4 header (TCP or UDP). A stateful packet inspection firewall can do packet filtering, but also knows about the context of the conversation. An application-layer firewall can look at the application data in the packet and make decisions.
![]() The DMZ is a zone that allows selected traffic from the Internet to reach public servers such as DNS, FTP, and HTTP servers.
The DMZ is a zone that allows selected traffic from the Internet to reach public servers such as DNS, FTP, and HTTP servers.
![]() A proxy server typically incorporates firewall features with content control features. For example, you can restrict what sites a user can visit or the types of applications they can use to access the Internet.
A proxy server typically incorporates firewall features with content control features. For example, you can restrict what sites a user can visit or the types of applications they can use to access the Internet.
Using Intrusion Detection Systems
![]() A network-based intrusion detection system analyzes network traffic to identify suspicious activity.
A network-based intrusion detection system analyzes network traffic to identify suspicious activity.
![]() An intrusion detection system (IDS) logs suspicious activity and notifies the administrator, but an intrusion prevention system (IPS) takes corrective action. For example, an IPS may disconnect the person responsible for the suspicious traffic from the network.
An intrusion detection system (IDS) logs suspicious activity and notifies the administrator, but an intrusion prevention system (IPS) takes corrective action. For example, an IPS may disconnect the person responsible for the suspicious traffic from the network.
![]() For the exam, know that IDSs can detect suspicious traffic based on signatures (signature-based IDS) or can identify suspicious traffic based on the traffic being outside the parameters of normal activity (anomaly-based IDS). Also know that heuristic monitoring involves detecting suspicious traffic based on past experience.
For the exam, know that IDSs can detect suspicious traffic based on signatures (signature-based IDS) or can identify suspicious traffic based on the traffic being outside the parameters of normal activity (anomaly-based IDS). Also know that heuristic monitoring involves detecting suspicious traffic based on past experience.
Network Design and Administration Principles
![]() Create communication boundaries within the network by using VLANs on a network switch.
Create communication boundaries within the network by using VLANs on a network switch.
![]() You can also create different network segments by placing routers on the network and controlling what traffic can enter different network segments using access control lists on the router (for example, separating your wireless network for visitors from the corporate network).
You can also create different network segments by placing routers on the network and controlling what traffic can enter different network segments using access control lists on the router (for example, separating your wireless network for visitors from the corporate network).
![]() Data loss prevention (DLP) technologies can be used to prevent someone from stealing or sharing sensitive company data.
Data loss prevention (DLP) technologies can be used to prevent someone from stealing or sharing sensitive company data.
![]() Network access control (NAC) allows you to check the state of the system before a system is granted access to the wired or wireless network.
Network access control (NAC) allows you to check the state of the system before a system is granted access to the wired or wireless network.
![]() Implement spam filtering features and antivirus software on your mail gateway to keep employee mailboxes clean of spam messages and messages containing viruses.
Implement spam filtering features and antivirus software on your mail gateway to keep employee mailboxes clean of spam messages and messages containing viruses.
Securing Devices
![]() Ensure that network devices have strong passwords.
Ensure that network devices have strong passwords.
![]() Be sure to patch devices to eliminate vulnerabilities on them.
Be sure to patch devices to eliminate vulnerabilities on them.
![]() Rename or disable default accounts on the devices if possible.
Rename or disable default accounts on the devices if possible.
SELF TEST
The following questions will help you measure your understanding of the material presented in this chapter. As indicated, some questions may have more than one correct answer, so be sure to read all the answer choices carefully.
Understanding Firewalls
1. Which of the following identifies the benefit of a stateful packet inspection firewall?
A. Can filter traffic based on the source and destination IP address
B. Can filter traffic based on the source and destination port number
C. Can filter traffic based on the application data
D. Can filter traffic based on the context of the conversation
2. Which type of firewall has the capabilities to inspect the payload of a packet to determine if the content is allowed to pass through the firewall?
A. Packet-filtering firewall
B. Application-layer firewall
C. Stateful packet inspection firewall
D. Screened-host firewall
3. What firewall topology typically involves having a router placed between the firewall and the Internet?
A. Packet-filtering firewall
B. Application-layer firewall
C. Dual-homed firewall
D. Screened-host firewall
4. Emily, a senior security officer for Company XYZ, is responsible for ensuring systems meet certain security requirements. Emily needs to ensure the security of the accounting systems by making sure that any systems running the accounting software have specific ports closed down. Which of the following should Emily use?
A. A host-based IDS
B. A host-based firewall
C. A network firewall
D. A host-based IPS
5. You are the firewall administrator for Company XYZ and need to ensure that DNS zone transfers are blocked at the firewall. Which of the following rules would you use?
A. deny ip any any
B. deny udp any any port 53
C. deny tcp any any port 25
D. deny tcp any any port 53
6. Your manager approaches you and is concerned that customers who visit and connect to the wireless guests SSID will be able to access corporate data and assets. What security solution would you recommend?
A. Implement network access control.
B. Segment into different zones.
C. Install network address translation.
D. Use data loss prevention policies.
Using Intrusion Detection Systems
7. Which network-based IDS component is responsible for analyzing the traffic against the signatures?
A. Sensor
B. Notification
C. Engine
D. Signature database
8. You have intrusion detection software that can monitor activity and identify suspicious activity based on past experience. What type of analysis is being performed?
A. Anomaly
B. Heuristic
C. Passive
D. Signature
9. Your intrusion detection software uses a baseline, and any activity outside that baseline is considered suspicious traffic. What type of analysis is being performed?
A. Anomaly
B. Heuristic
C. Passive
D. Signature
10. John has implemented an intrusion detection system that has identified suspicious traffic without the use of signatures. While responding to the event, John notices that the IDS has falsely identified the traffic as being suspicious. Which of the following devices does John need to configure to prevent additional false alarms?
A. Signature-based IDS
B. Anomaly-based IDS
C. Anomaly-based IPS
D. Host-based IDS
11. The information system security officer (ISSO) for the organization is concerned that attacks against the web server will be successful if the hacker has an unlimited number of attempts. Which of the following is designed to stop attacks on a specific server?
A. HIDS
B. NIDS
C. NIPS
D. HIPS
Network Design and Administration Principles
12. You have a small network with all servers and workstations connected to a single switch. Your manager would like to ensure that no system outside the systems in the accounting department can communicate with the accounting server. What would you do?
A. Get another switch and connect the accounting systems to that switch.
B. Get a router and create two networks.
C. Get a proxy server to control communication.
D. Use VLANs on the switch.
13. When a system tries to connect to a network, the system is checked to ensure that it has recent patches and virus definitions before being allowed to communicate on the network. What service can be used to do this?
A. NAT
B. Proxy
C. NAC
D. VLAN
14. What type of system is typically used to monitor and control which web sites a user visits and can block content based on information in the content being accessed?
A. NAT
B. Proxy
C. NAC
D. VLAN
15. You are monitoring network traffic on the LAN and notice a large number of packets that use the SIP and RTP protocols. Which of the following actions would you take to segment that traffic on the LAN?
A. Create a DMZ.
B. Configure NAT.
C. Implement an NIPS.
D. Create a voice VLAN.
16. You are looking to use IPSec to provide encryption, authentication, and data integrity services. Which IPSec protocol would you use?
A. AH
B. IKE
C. ESP
D. PPTP
17. Your manager would like to implement a VPN solution that encrypts all communication that travels across the Internet between the two office locations with minimal configuration on each client. What would you recommend?
A. Full tunnel
B. Site-to-site VPN
C. Remote access VPN
D. Split tunnel
18. You are the security administrator for your company and you would like to prevent employees from e-mailing sensitive data to their personal e-mail accounts. How would you do this?
A. DLP
B. NAC
C. VPN
D. NAT
Securing Devices
19. Which of the following represents the first thing you should do after purchasing a wireless router?
A. Disable DHCP.
B. Configure proxy rules.
C. Configure VLANs.
D. Set a password on the device.
20. Your manager is concerned about the vulnerabilities that may exist with a specific switch that was purchased for the office network. What can you do to ensure that you are protected from known vulnerabilities?
A. Enable the firewall.
B. Configure logon hours.
C. Update the firmware.
D. Configure VLANs.
Performance-Based Questions
21. You are responsible for configuring the company firewall. Using the network diagram as a guide, choose the firewall rules you would configure using these requirements:
■ Only accounting systems can communicate with 12.0.0.10 using HTTPS.
■ Only accounting systems can communicate with 12.0.0.10 using SMTP.
■ All systems can communicate with 12.0.0.11 with any type of traffic.
22. Match the term on the left with the description on the right.

SELF TEST ANSWERS
Understanding Firewalls
1. ![]() D. A stateful packet inspection firewall understands the state of the conversation and what packets it should expect to receive. If a packet is received that is out of the context of the conversation, then the firewall does not allow the packet, even though it may be destined for a port that is open on the firewall.
D. A stateful packet inspection firewall understands the state of the conversation and what packets it should expect to receive. If a packet is received that is out of the context of the conversation, then the firewall does not allow the packet, even though it may be destined for a port that is open on the firewall.
![]() A, B, and C are incorrect. Although a stateful packet inspection firewall can filter traffic based on source/destination IP address and source/destination port number (packet-filtering firewalls can do that as well), what makes it unique is understanding the context of the conversation. An application-layer firewall can filter traffic based on the application data (also known as the payload).
A, B, and C are incorrect. Although a stateful packet inspection firewall can filter traffic based on source/destination IP address and source/destination port number (packet-filtering firewalls can do that as well), what makes it unique is understanding the context of the conversation. An application-layer firewall can filter traffic based on the application data (also known as the payload).
2. ![]() B. An application-layer firewall can inspect the application data and allow or disallow certain functions of an application through the firewall. This is more advanced than simply opening a port. For example, port 80 may be opened on the firewall, but the application firewall can also restrict the traffic to allow only HTTP get commands and not HTTP put commands.
B. An application-layer firewall can inspect the application data and allow or disallow certain functions of an application through the firewall. This is more advanced than simply opening a port. For example, port 80 may be opened on the firewall, but the application firewall can also restrict the traffic to allow only HTTP get commands and not HTTP put commands.
![]() A, C, and D are incorrect. A packet-filtering router filters traffic based on the source/destination IP address and the source/destination port number. A stateful packet inspection firewall can filter traffic based on the IP address and port information, but it also understands if a packet is received out of context. A screened-host firewall is a topology and not a type of firewall.
A, C, and D are incorrect. A packet-filtering router filters traffic based on the source/destination IP address and the source/destination port number. A stateful packet inspection firewall can filter traffic based on the IP address and port information, but it also understands if a packet is received out of context. A screened-host firewall is a topology and not a type of firewall.
3. ![]() D. A screened-host firewall is a firewall that has a packet-filtering router placed in front of it that filters the traffic based on the layer-3 header or layer-4 header. The information that passes through the packet-filtering router then hits the firewall and must meet the firewall rules in order to reach the internal network.
D. A screened-host firewall is a firewall that has a packet-filtering router placed in front of it that filters the traffic based on the layer-3 header or layer-4 header. The information that passes through the packet-filtering router then hits the firewall and must meet the firewall rules in order to reach the internal network.
![]() A, B, and C are incorrect. Packet-filtering and application-layer firewalls are types of firewalls and not topologies. A dual-homed firewall is a system that has two network cards installed and firewall software installed on the system.
A, B, and C are incorrect. Packet-filtering and application-layer firewalls are types of firewalls and not topologies. A dual-homed firewall is a system that has two network cards installed and firewall software installed on the system.
4. ![]() B. In order to control traffic to a specific system, Emily should use a host-based firewall. A host-based firewall is typically software installed on a system that allows you to control traffic to that specific system.
B. In order to control traffic to a specific system, Emily should use a host-based firewall. A host-based firewall is typically software installed on a system that allows you to control traffic to that specific system.
![]() A, C, and D are incorrect. A network firewall can control communication, but it controls communication to the network, not a specific system. In this case, an IDS and IPS are not used, as the goal is to control communication, not monitor it.
A, C, and D are incorrect. A network firewall can control communication, but it controls communication to the network, not a specific system. In this case, an IDS and IPS are not used, as the goal is to control communication, not monitor it.
5. ![]() D. In order to block DNS zone transfers, you will deny TCP 53 traffic.
D. In order to block DNS zone transfers, you will deny TCP 53 traffic.
![]() A, B, and C are incorrect. Answer A is a rule that would block all TCP/IP traffic, whereas answer B would block DNS queries from clients. Answer C would block SMTP traffic.
A, B, and C are incorrect. Answer A is a rule that would block all TCP/IP traffic, whereas answer B would block DNS queries from clients. Answer C would block SMTP traffic.
6. ![]() B. In this scenario you should recommend that the wireless guest network be in a separate zone from the corporate network, which would be the intranet zone. Using a firewall to create zones allows you to control whether communication can occur between the two zones, which in this case you do not want to occur.
B. In this scenario you should recommend that the wireless guest network be in a separate zone from the corporate network, which would be the intranet zone. Using a firewall to create zones allows you to control whether communication can occur between the two zones, which in this case you do not want to occur.
![]() A, C, and D are incorrect. NAC would be used to check the health of a system before it is allowed to connect to the network. NAT would be used to hide the internal address scheme of the network, and DLP policies would be used to ensure that employees are not leaking sensitive data.
A, C, and D are incorrect. NAC would be used to check the health of a system before it is allowed to connect to the network. NAT would be used to hide the internal address scheme of the network, and DLP policies would be used to ensure that employees are not leaking sensitive data.
Using Intrusion Detection Systems
7. ![]() C. The IDS engine, also known as the analysis engine, is responsible for comparing the traffic against signatures of known attacks.
C. The IDS engine, also known as the analysis engine, is responsible for comparing the traffic against signatures of known attacks.
![]() A, B, and D are incorrect. A sensor is responsible for capturing the traffic and sending it to the analysis engine. Notification may be the result of the engine identifying suspicious traffic. The signature database is a database of known attacks and is used to identify suspicious traffic.
A, B, and D are incorrect. A sensor is responsible for capturing the traffic and sending it to the analysis engine. Notification may be the result of the engine identifying suspicious traffic. The signature database is a database of known attacks and is used to identify suspicious traffic.
8. ![]() B. Heuristic analysis is when the IDS identifies suspicious events based on past experience. For example, virus protection software that uses heuristic analysis can identify new, unknown viruses by analyzing the actions of the unknown software and, based on actions of past viruses, be able to flag the software as a virus.
B. Heuristic analysis is when the IDS identifies suspicious events based on past experience. For example, virus protection software that uses heuristic analysis can identify new, unknown viruses by analyzing the actions of the unknown software and, based on actions of past viruses, be able to flag the software as a virus.
![]() A, C, and D are incorrect. Anomaly-based analysis is when a baseline of normal activity is determined, and anything outside that normal activity is considered suspicious. Passive is not an analysis method. Signature-based analysis uses a database of known-suspicious activity to identify suspicious traffic.
A, C, and D are incorrect. Anomaly-based analysis is when a baseline of normal activity is determined, and anything outside that normal activity is considered suspicious. Passive is not an analysis method. Signature-based analysis uses a database of known-suspicious activity to identify suspicious traffic.
9. ![]() A. Anomaly-based analysis is when a baseline of normal activity is determined, and anything outside that normal activity is considered suspicious.
A. Anomaly-based analysis is when a baseline of normal activity is determined, and anything outside that normal activity is considered suspicious.
![]() B, C, and D are incorrect. Heuristic analysis is when the IDS identifies suspicious events based on past experience. Passive is not an analysis method. Signature-based analysis uses a database of known-suspicious activity to identify suspicious traffic.
B, C, and D are incorrect. Heuristic analysis is when the IDS identifies suspicious events based on past experience. Passive is not an analysis method. Signature-based analysis uses a database of known-suspicious activity to identify suspicious traffic.
10. ![]() A. A signature-based IDS can reduce the number of false alarms because it is programmed specifically for the type of traffic that is to be considered suspicious traffic. Unless the traffic meets the conditions that the IDS has been programmed for, it does not consider the traffic suspicious.
A. A signature-based IDS can reduce the number of false alarms because it is programmed specifically for the type of traffic that is to be considered suspicious traffic. Unless the traffic meets the conditions that the IDS has been programmed for, it does not consider the traffic suspicious.
![]() B, C, and D are incorrect. Signature-based IDSs are less likely to have false positives because they identify suspicious traffic based on the signatures programmed into the product.
B, C, and D are incorrect. Signature-based IDSs are less likely to have false positives because they identify suspicious traffic based on the signatures programmed into the product.
11. ![]() D. A host-based intrusion prevention system (HIPS) is designed to prevent attacks against a specific system.
D. A host-based intrusion prevention system (HIPS) is designed to prevent attacks against a specific system.
![]() A, B, and C are incorrect. A host-based intrusion detection system (HIDS) will identify suspicious activity against a specific system but will not take corrective action to prevent the attack. Network-based intrusion detection and prevention systems are not designed to prevent attacks against a specific system.
A, B, and C are incorrect. A host-based intrusion detection system (HIDS) will identify suspicious activity against a specific system but will not take corrective action to prevent the attack. Network-based intrusion detection and prevention systems are not designed to prevent attacks against a specific system.
Network Design and Administration Principles
12. ![]() D. You can use VLANs on a switch to break the network down into multiple virtual LANs. Systems in one VLAN are, by default, unable to communicate with systems in another VLAN.
D. You can use VLANs on a switch to break the network down into multiple virtual LANs. Systems in one VLAN are, by default, unable to communicate with systems in another VLAN.
![]() A, B, and C are incorrect. Answer A is close to the correct answer because getting separate switches for the accounting systems will work, but unfortunately you are spending money when the goal can be accomplished with VLANs. The same point can be made about the router (answer B)—although it will work, it comes with the expense of purchasing more hardware. Finally, this question has nothing to do with proxy servers (answer C).
A, B, and C are incorrect. Answer A is close to the correct answer because getting separate switches for the accounting systems will work, but unfortunately you are spending money when the goal can be accomplished with VLANs. The same point can be made about the router (answer B)—although it will work, it comes with the expense of purchasing more hardware. Finally, this question has nothing to do with proxy servers (answer C).
13. ![]() C. Network access control (NAC) is a feature of networking that allows you to control which systems can connect to the wired or wireless network. You can put conditions on the state of the system (known as the health of the system) before allowing the client to connect.
C. Network access control (NAC) is a feature of networking that allows you to control which systems can connect to the wired or wireless network. You can put conditions on the state of the system (known as the health of the system) before allowing the client to connect.
![]() A, B, and D are incorrect. Network address translation (NAT) is used to hide the systems on the private network behind the NAT device by sharing a single public address. A proxy server can be used to send requests to the Internet on behalf of the user, while the administrator monitors and filters requests at the proxy server. VLANs are a feature of a switch that allow you to create communication boundaries on the switch.
A, B, and D are incorrect. Network address translation (NAT) is used to hide the systems on the private network behind the NAT device by sharing a single public address. A proxy server can be used to send requests to the Internet on behalf of the user, while the administrator monitors and filters requests at the proxy server. VLANs are a feature of a switch that allow you to create communication boundaries on the switch.
14. ![]() B. A proxy server can be used to send requests to the Internet on behalf of the user while the administrator monitors and filters requests at the proxy server.
B. A proxy server can be used to send requests to the Internet on behalf of the user while the administrator monitors and filters requests at the proxy server.
![]() A, C, and D are incorrect. Network address translation (NAT) is used to hide the systems on the private network behind the NAT device by sharing a single public address. Network access control (NAC) is a feature of networking that allows you to control which systems can connect to the wired or wireless network. VLANs are a feature of a switch that allow you to create communication boundaries on the switch.
A, C, and D are incorrect. Network address translation (NAT) is used to hide the systems on the private network behind the NAT device by sharing a single public address. Network access control (NAC) is a feature of networking that allows you to control which systems can connect to the wired or wireless network. VLANs are a feature of a switch that allow you to create communication boundaries on the switch.
15. ![]() D. Session Initiation Protocol (SIP) and Real-time Transport Protocol (RTP) are protocols used by Voice over IP (VoIP). It is a common security practice to create a separate VLAN for the VoIP traffic on the network in order to partition that traffic from other network traffic.
D. Session Initiation Protocol (SIP) and Real-time Transport Protocol (RTP) are protocols used by Voice over IP (VoIP). It is a common security practice to create a separate VLAN for the VoIP traffic on the network in order to partition that traffic from other network traffic.
![]() A, B, and C are incorrect. These are not common practices to deal with VoIP traffic.
A, B, and C are incorrect. These are not common practices to deal with VoIP traffic.
16. ![]() C. Encapsulating Security Payload (ESP) is the only IPSec protocol that provides all three—encryption, authentication, and data integrity.
C. Encapsulating Security Payload (ESP) is the only IPSec protocol that provides all three—encryption, authentication, and data integrity.
![]() A, B, and D are incorrect. AH can provide authentication and data integrity, IKE is the key exchange protocol, and PPTP is not an IPSec protocol.
A, B, and D are incorrect. AH can provide authentication and data integrity, IKE is the key exchange protocol, and PPTP is not an IPSec protocol.
17. ![]() B. A site-to-site VPN would involve having a central device on the network encrypt all communication to the remote office location and not require you to configure each client.
B. A site-to-site VPN would involve having a central device on the network encrypt all communication to the remote office location and not require you to configure each client.
![]() A, C, and D are incorrect. Full tunnel is when the client cannot access network resources while the VPN client software is running. Split tunnel is when the client can access the Internet through the LAN but can also access corporate resources through the VPN. Remote access VPN is the opposite of site-to-site VPN and would require each client to have VPN software to create their own encrypted tunnel to the destination.
A, C, and D are incorrect. Full tunnel is when the client cannot access network resources while the VPN client software is running. Split tunnel is when the client can access the Internet through the LAN but can also access corporate resources through the VPN. Remote access VPN is the opposite of site-to-site VPN and would require each client to have VPN software to create their own encrypted tunnel to the destination.
18. ![]() A. DLP, or data loss prevention, is a group of technologies that can prevent data from being leaked out of the organization.
A. DLP, or data loss prevention, is a group of technologies that can prevent data from being leaked out of the organization.
![]() B, C, and D are incorrect. NAC would be used to check the health of a system before it is allowed to connect to the network. NAT would be used to hide the internal address scheme of the network. A VPN would be used to encrypt communication across an untrusted network.
B, C, and D are incorrect. NAC would be used to check the health of a system before it is allowed to connect to the network. NAT would be used to hide the internal address scheme of the network. A VPN would be used to encrypt communication across an untrusted network.
Securing Devices
19. ![]() D. The first thing you should do with any network device is to ensure you have set a password for the administrator account so that unauthorized individuals cannot make changes to the configuration.
D. The first thing you should do with any network device is to ensure you have set a password for the administrator account so that unauthorized individuals cannot make changes to the configuration.
![]() A, B, and C are incorrect. None of these represents the first thing you should do with a new device.
A, B, and C are incorrect. None of these represents the first thing you should do with a new device.
20. ![]() C. It is critical that you update the firmware on hardware devices, just as you would update a system with patches.
C. It is critical that you update the firmware on hardware devices, just as you would update a system with patches.
![]() A, B, and D are incorrect. These actions will not necessarily help against vulnerabilities that the firmware is exposing the device to.
A, B, and D are incorrect. These actions will not necessarily help against vulnerabilities that the firmware is exposing the device to.
Performance-Based Questions
21. The Security+ exam may present to you a network diagram and expect you to identify rules that need to be configured on the firewall based on criteria presented in the question. The exam will most likely ask you to choose the rules from a list of available rules. The following illustration identifies the rules for this scenario:
22. The following is the correct matching of security terms to their descriptions.