In this chapter, you will learn about the various threats that an attacker can launch against a network. Attacks on a specific protocol or service are attempts to take advantage of a specific feature or to use the protocol or service in a way that was not intended. You will gain an understanding of different types of network attacks and how to use assessment tools to help determine security.
- 1.
Analyze and differentiate among types of network attacks.
- 2.
Analyze and differentiate among types of wireless attacks.
Denial-of-Service Attack
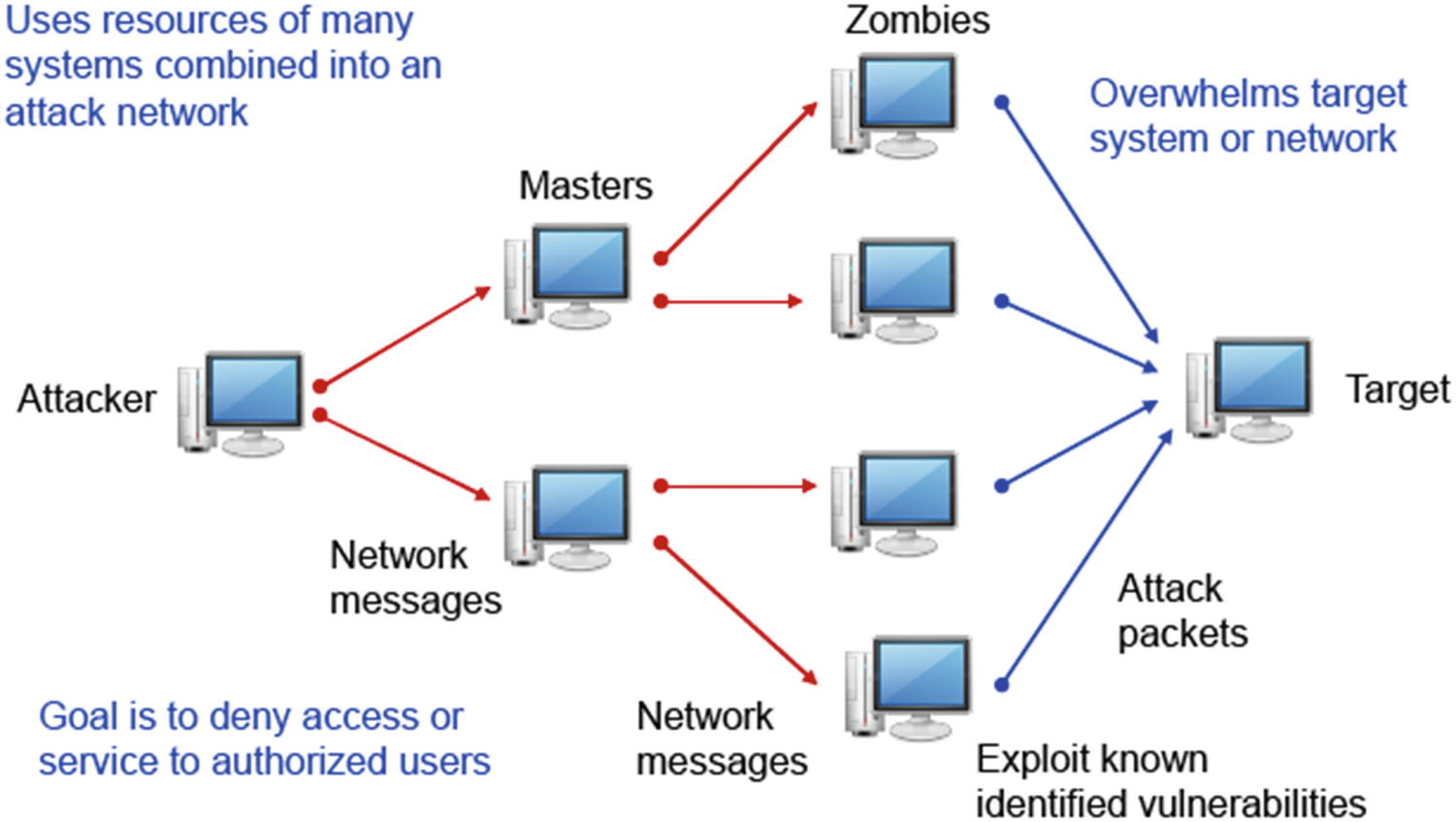
Denial of Service Attack
Three-Way Handshake
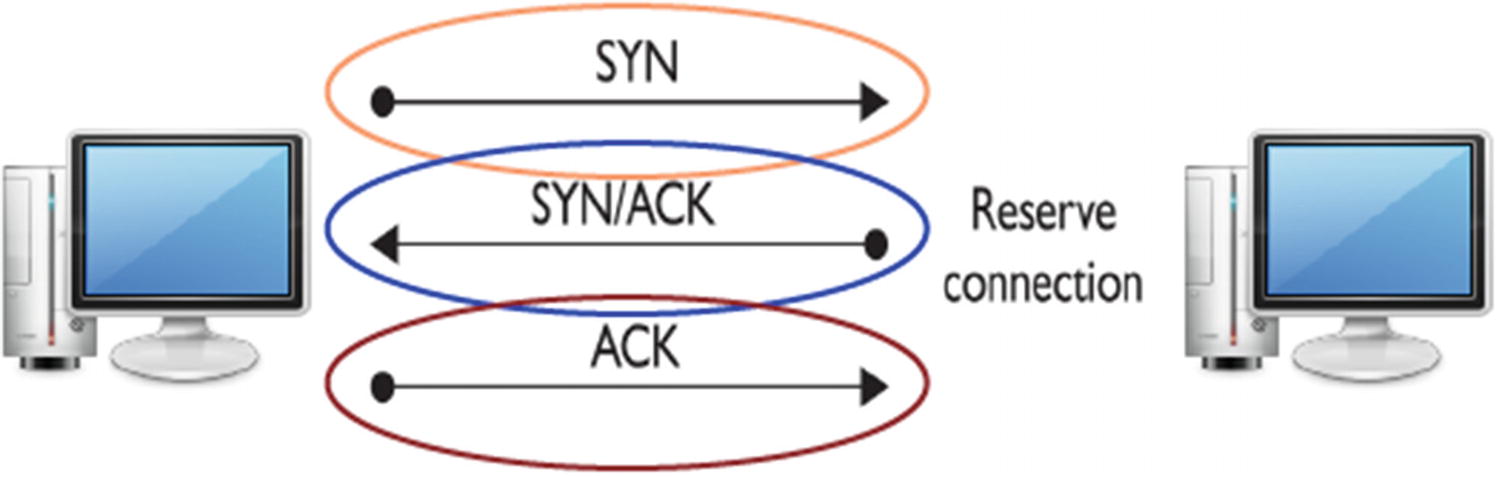
A Three-Way Handshake Process
SYN Flood Attack
- 1.
Communication request sent to target system using a fake IP address. Note that if the attacks outpace the requests timing out, then system’s resources will be exhausted.
- 2.
Target responds to fake IP address.
- 3.
Target waits for nonexistent system response.
- 4.
Request eventually times out.

SYN Flood Attack Using a Three-Way Handshake
Ping of Death (POD)
A Ping-of-Death attack is an example of a DoS attack which targets a specific protocol or operating system. The attacker sends an Internet Control Message Protocol (ICMP) ping packet equal to or greater than 64KB. This type of packet should not occur naturally. Some systems cannot handle the packet and will hang or crash.
Trapdoors and Backdoors
Originally, backdoors referred to efforts by software developers to ensure access to a program that bypassed the normal access methods. Over time, this practice has come to be known as creating a trapdoor into a program. One problem with a trapdoor is that since it is hard-coded into the program, it can be very difficult, if not impossible, to remove. A benefit to software developers and system administrators in using a trapdoor is that it ensures access to a program even if the normal access methods fail. However, this benefit is now a vulnerability. The trapdoor offers full access into the system where an attacker could cause serious harm.
More recently, a backdoor has come to refer to the programs or code introduced by an attacker that has compromised a system. A few common backdoor programs are Netbus and Back Orifice which both allow remote access to unauthorized system users. The purpose of the backdoor is to grant the attacker future access to the system even if the original vulnerability used to attack the system has been fixed. Usually, backdoors are installed on systems by unauthorized users or attackers. However, they can also be installed by authorized users who inadvertently run a Trojan horse program on their machine which then installs the backdoor.
Similar to the backdoor, another method employed by attackers is to install a rootkit on a system that ensures continued root access for the attacker.
Null Sessions
A null session is a connection to a Windows inter-process communication share (IPC$). A vulnerability exists in Microsoft Windows systems prior to the XP and Server 2003 versions of the operating system. The Server Message Block (SMB) system allows users to establish a null session. A wide range of tools and malware use this vulnerability to achieve their aim.
One way to defend against the creation of null sessions is to upgrade the systems to Windows XP, Server 2003, or newer version. You can also limit TCP ports 139 and 445 to only allow trusted user access.
Sniffing
Sniffing occurs when an attacker examines all network traffic as it passes their NIC independent of whether or not the traffic is addressed to them or not. Network sniffing can be accomplished with a software application, hardware device, or a combination of the two. Sniffing can be used to view all network traffic, or it can target a specific protocol, service, or even string of characters such as a log-in or password. Some network sniffers are designed not just to observe all traffic but to modify some or all of the traffic as well. Network administrators may also use sniffers to analyze network traffic, identify bandwidth issues, and troubleshoot other network issues. Physical security is important in preventing the introduction of sniffers on the internal network.
IP Address Spoofing
In a specific DoS attack known as a smurf attack, the attacker sends a spoofed packet to the broadcast address for a network, which distributes the packet to all systems on that network. In the smurf attack, the packet sent by the attacker to the broadcast address is an echo request with the From address forged so that it appears that another system (the target system) has made the echo request.

ID Address Spoofing
Spoofing and Trusted Relationships
Spoofing can also take advantage of a trusted relationship between two systems.
If two systems are configured to accept the authentication accomplished by each other, an individual logged onto one system might not be forced to go through an authentication process again to access the other system. An attacker can take advantage of this arrangement by sending a packet to one system that appears to have come from a trusted system. Since the trusted relationship is in place, the targeted system may perform the requested task without authentication.
Since a reply will often be sent once a packet is received, the system that is being impersonated could interfere with the attack, since it would receive an acknowledgement for a request it never made. The attacker will often initially launch a disk operating system (DoS) attack (such as a SYN flooding attack) to temporarily take out the spoofed system for the period of time that the attacker is exploiting the trusted relationship.
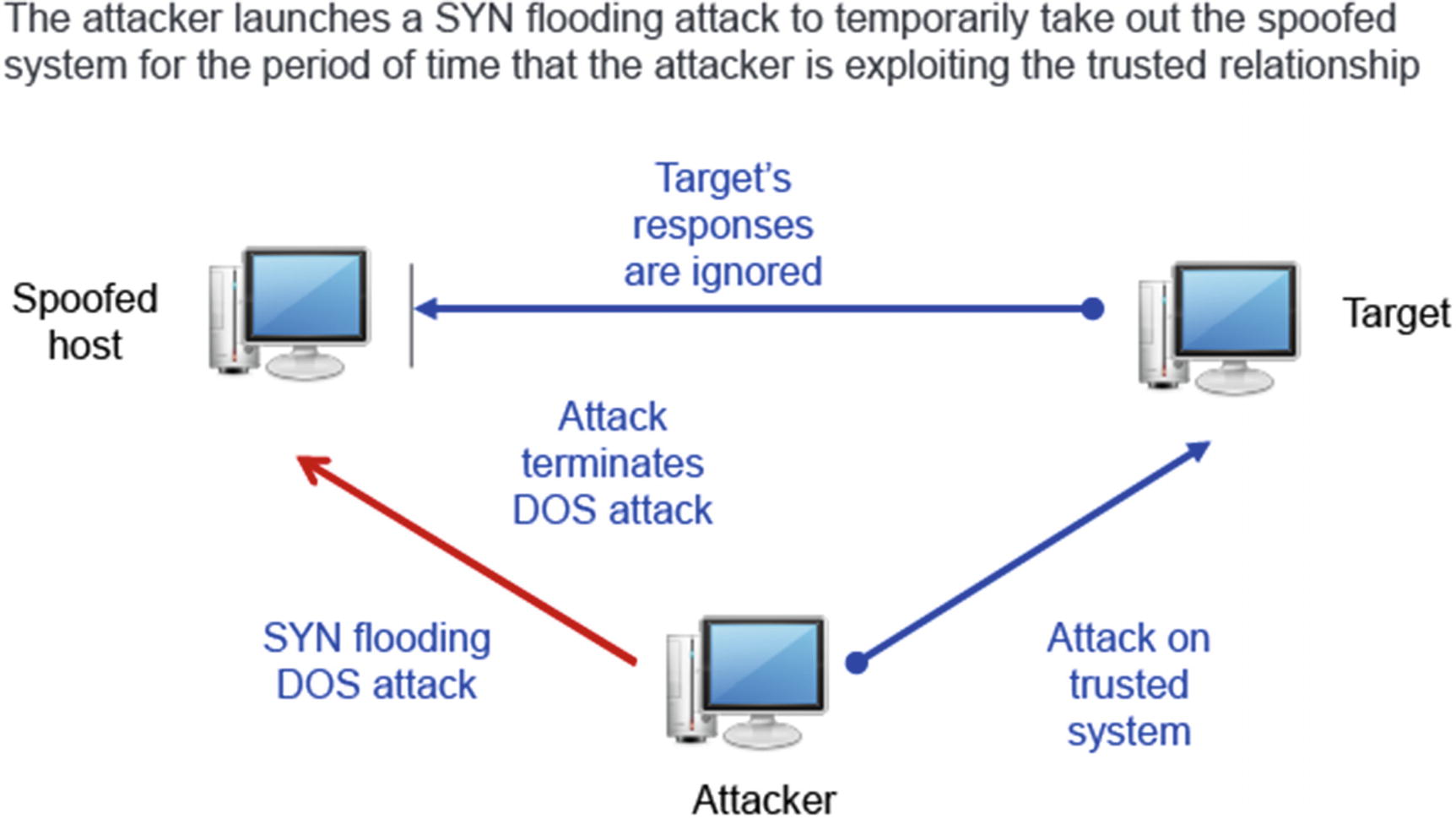
An SYN Flooding Attack
Firewalls should also be configured to discard any packets from outside of the firewall that have From addresses indicating they originated from inside the network. This is a situation that should not occur normally, and it indicates spoofing is being attempted.
Spoofing and Sequence Numbers
In the transmission control protocol (TCP) three-way handshake, two sets of sequence numbers are created. The first system chooses a sequence number to send with the original SYN packet. When the second host responds and sends its own SYN packet, it generates another sequence number.
The second host also sends an ACK packet in response to the first host’s SYN packet. The ACK packet includes the original sequence number incremented by 1. The original host system receives the SYN/ACK with both sequence numbers and then increments the second host’s sequence number by one and passes it back in an ACK packet response.
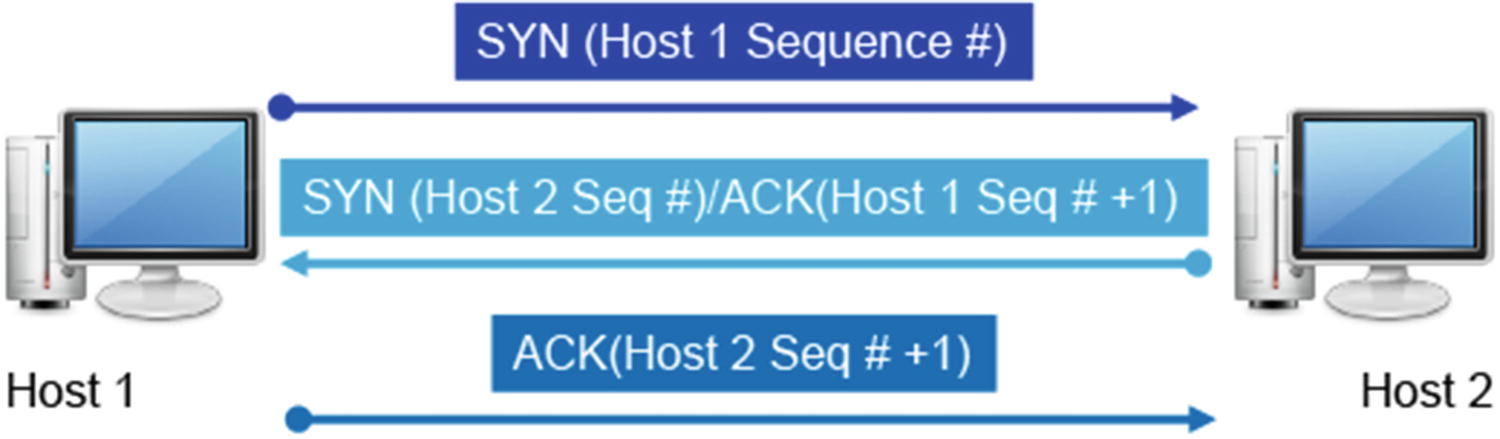
Spoofing and Sequence Process
Man-in-the-Middle Attack
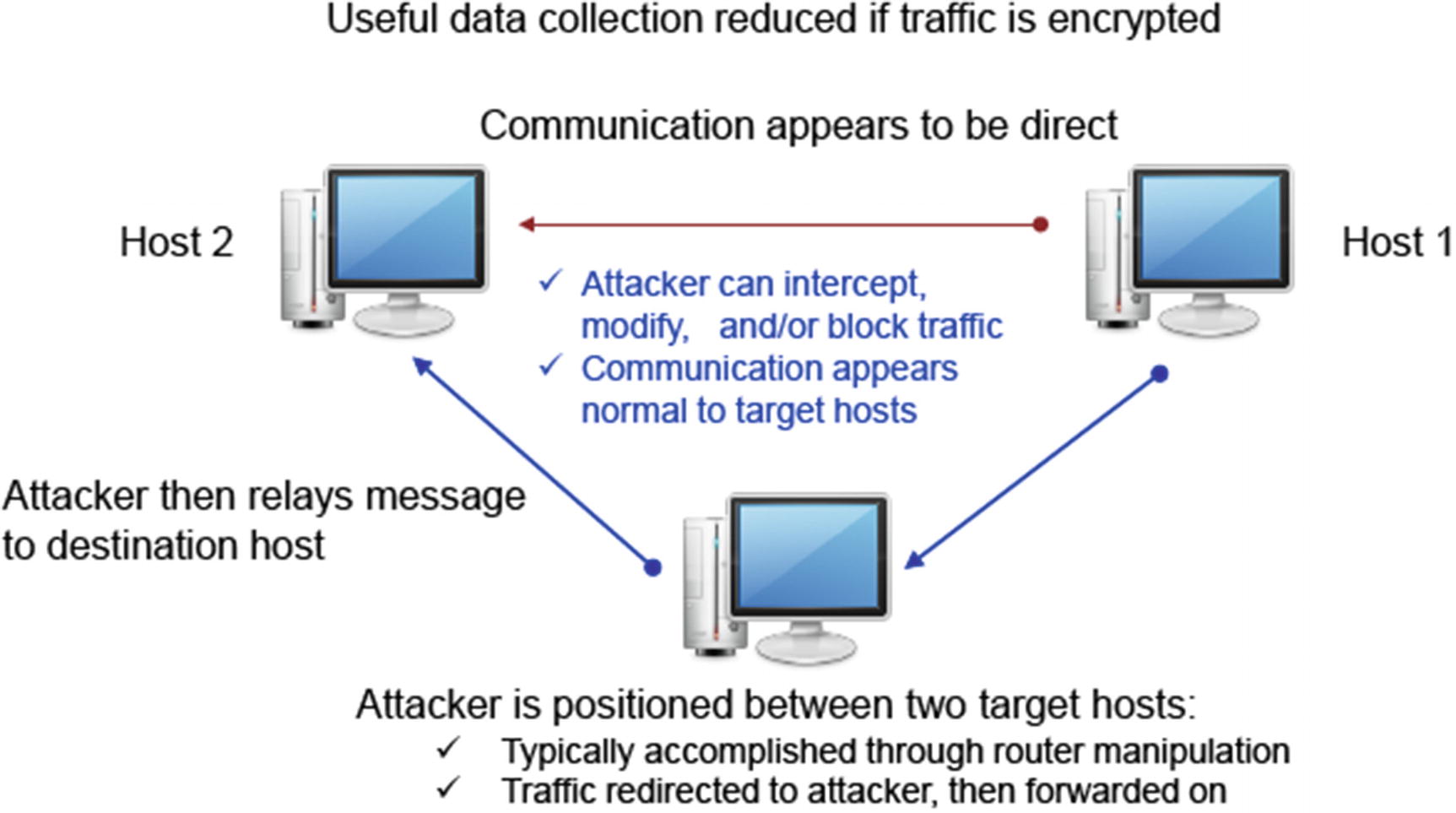
Illustration of Man-in-the-Middle Attack
Replay Attack
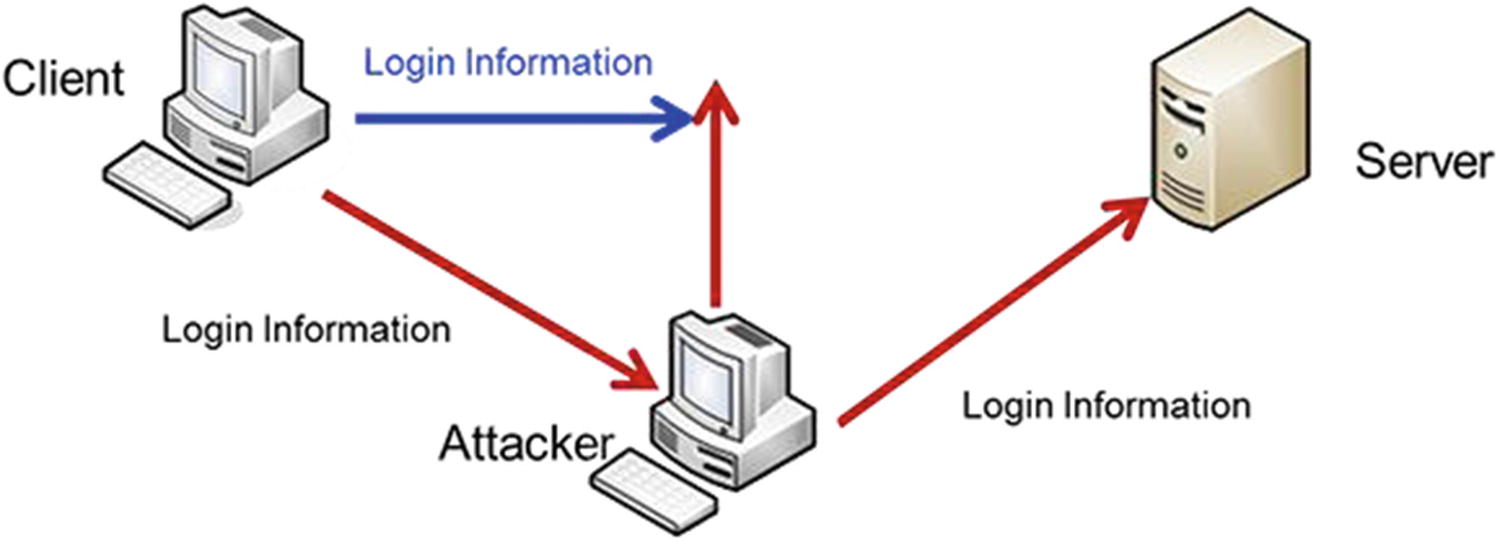
Replay Attack
TCP/IP Hijacking
Transmission Control Protocol/Internet Protocol (TCP/IP) hijacking and session hijacking are terms used to refer to the process of taking control of an already existing session between a client and a server. The advantage to an attacker of hijacking over attempting to penetrate a computer system or network is that the attacker does not have to circumvent any authentication mechanisms.
To prevent the user from noticing anything unusual, the attacker may target the user’s system with a DoS attack, taking it down so that the user, and the system, will not notice the extra traffic that is taking place.

TCP/IP Hijacking
Drive-By Download Attack
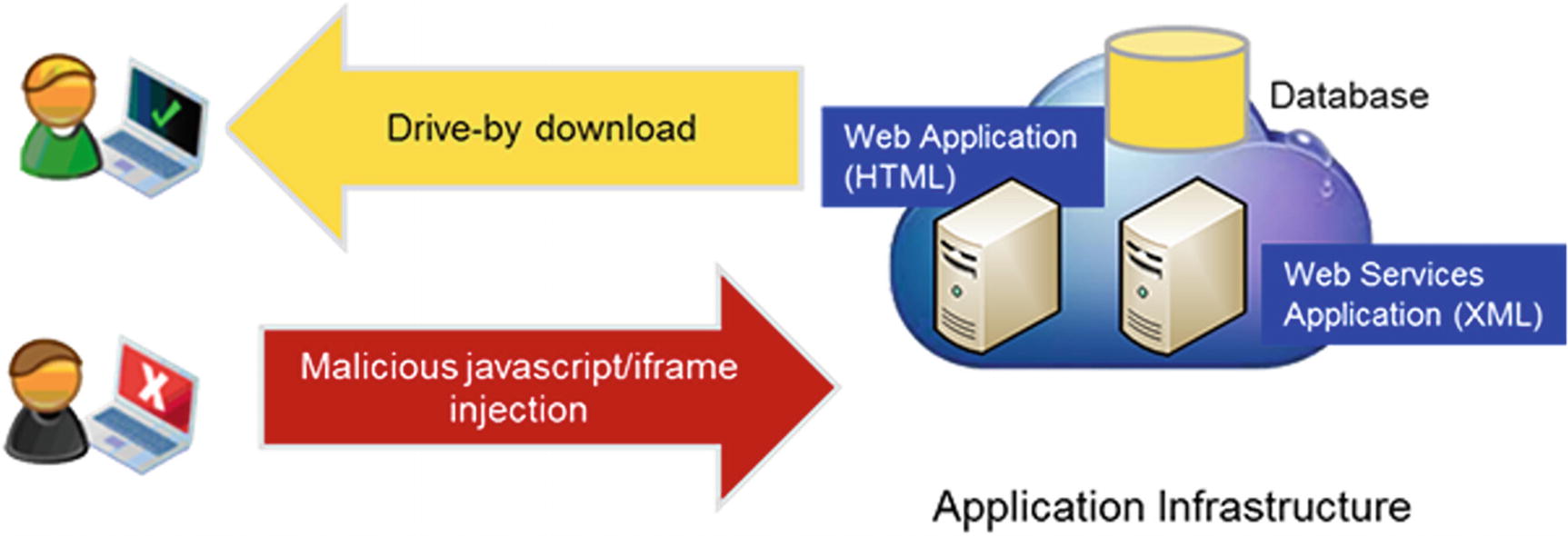
Drive-By Download Attack
Summary
It is important to be aware of the various types of potential threats that an attacker may launch against a network. In this chapter you learned about different types of network attacks and the use of assessment tools that can be applied to determine security threats and vulnerabilities to safeguard against attacks.
