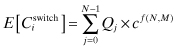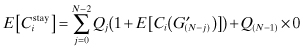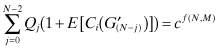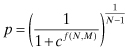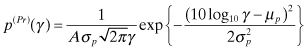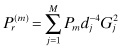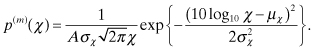13
SELF-COEXISTENCE AND SECURITY IN COGNITIVE RADIO NETWORKS
13.1 INTRODUCTION
Recent experimental studies have demonstrated that wireless spectrum suffers from overutilization in some bands and underutilization in others over different points in time and space [1]. This results in a great amount of white space (unused bands) being available dynamically that can potentially be used for both licensed and unlicensed services. It is then intuitive that static spectrum allocation may not be the optimal solution for efficient spectrum sharing and usage. In static spectrum allocation, a large number of the radio bands are allocated to the television, government, private, and public safety systems. However, the utilization of these bands is significantly low. Often, the usage of spectrum in certain networks is lower than anticipated, while other bands suffer from crisis because the demands of their users exceed the network capacity. Though it might be argued that the implementation and administration of static allocation policy is very easy, the fact remains that the current allocation policy is ineffective and the penalty trickles down as an increased cost to the end users.
Static spectrum allocation often also faces issues due to the modification in existing technologies. For example, in case of VHF and UHF bands reserved for television broadcast in the United States, allocation of 6 MHz per TV channel was based on the old analog NTSC system even though better-quality video can be now broadcast with almost 50% less spectrum per channel [2]. Given the pervasive penetration of cable TV, this spectrum, though allocated and owned, remains unused in most geographical locations, thus leading to underutilization and wastage. This observation underscores the suboptimality of the fixed spectrum assignment policies and has led to the recent spectrum policy reforms by the Federal Communication Commission (FCC) in the sub-900-MHz bands [3]. This new policy would allow unused, licensed spectrum bands (white spaces) to be used by unlicensed users (secondary users) under the provision that they would vacate upon the return of the licensed user (primary user).1 The success of this policy depends on the ability of secondary users to dynamically identify and access unused spectrum bands, detect the return of primary users, and switch to a different band promptly upon sensing the primary user.
The newly proposed cognitive radio (CR) paradigm/networks are anticipated to make dynamic spectrum access (DSA) a reality [4]. Unlike conventional radios, cognitive radios can intelligently adjust their transmission/reception parameters based on interaction with the environment and find the best available spectrum bands to use [5]. The core components of a cognitive radio network are the base stations (BSs) and the consumer premise equipments (CPEs) [6, 7]. A BS typically manages its own cell by controlling on-air activity within the cell, including access to the medium by CPEs, allocations to achieve quality of service (QoS), and admission to the network based on network security mechanisms. The operations of BS/CPEs can be divided into two major categories: sensing and transmitting/receiving data. Sensing and avoiding incumbent transmission is the most prioritized task of all CR-enabled secondary devices. If any of the channels used by CR node/network is accessed by the licensed incumbents, the primary task of CR devices is to vacate the channels within the channel move time (e.g., for IEEE 802.22, the channel move time is 2 s) and switch to some other channel. To get the knowledge of the presence of licensed incumbents and their usage of channels, BS and CPEs periodically perform channel sensing.
To date, a great deal of research work has been done in spectrum sensing [8–12], most of which falls into three categories: matched filter detection, cyclostationary feature detection, and energy detection. Unfortunately, none of these sensing mechanisms can ensure accuracy in the detection outcomes due to the inherent unreliable nature of the wireless medium and varying physical separation between the primary and secondary users. Such uncertainties in the licensed user detection make the spectrum sensing vulnerable to denial-of-service (DoS) threats in the hostile network environment. In this chapter, we discuss a specific class of DoS attacks in cognitive radio networks known as the primary user emulation (PUE) attack. In this type of attack, one or multiple attacking nodes (malicious users) transmit in forbidden timeslots and effectively emulate the primary user to make the protocol compliant secondary users erroneously conclude that the primary user is present. If the attack is successful, the protocol-compliant secondary users will leave the spectrum band, potentially causing a disruption in their network quality of service (QoS).
Another major challenge in the newly proposed CR standard is ensuring quality of service (QoS) among multiple good (rational) CR networks themselves—in other words, maintaining self–coexistence. In areas with significant high primary incumbents (licensed services), open channels will be a commodity of demand. Therefore, dynamic channel access among CR networks will be of utmost importance so that the interference among CR networks themselves can be minimized; else the throughput and Quality of Service (QoS) will be compromised. Thus in this chapter, we also focus on the issue of self–coexistence among multiple good overlapping and competing CR networks in a geographical region. We use the tools from noncooperative game theory and model the competitive environment as a distributed game. We consider the system of multiple overlapping CR networks operated by multiple wireless service providers that compete for the resources and try to seek a spectrum band void of interference from other coexisting CR networks. If interfered by other CR networks at any stage of the game, the networks face a binary choice of whether to stick to the band (assuming the interferers might move away) or move to another band itself.
Unlike other standards where self-coexistence and security issues are only considered after the specification essentially is finalized, it is required for CR networks to take the proactive approach due to the open nature of dynamic spectrum access. However, the current spectrum etiquette policies only emphasize on the primary user–secondary user interaction (primary avoidance policy) and hardly focus on the policy issues regarding the interaction among multiple secondary networks with good or malicious intentions. In light of these new perspectives, this chapter discusses the approaches to investigate the novel self-coexistence and primary user emulation attack issues for enhanced MAC as revision of the initial cognitive radio standard conception and definition [4].
13.2 COGNITIVE RADIO NETWORK SYSTEM OVERVIEW
Before proceeding further, let us briefly discuss the features of the newly proposed cognitive radio networks [4–7].
13.2.1 System Architecture
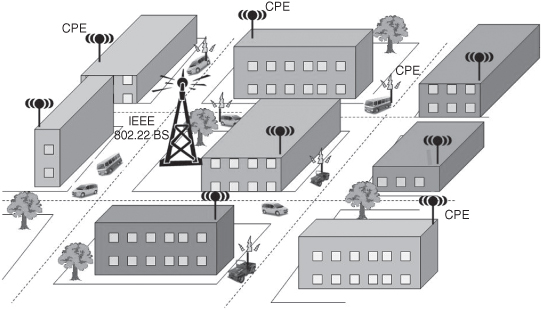
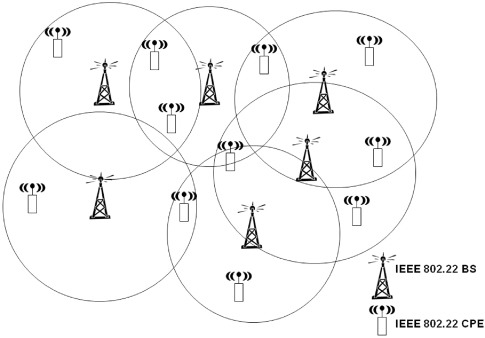
A simple architecture of a cognitive radio network consisting of BS and CPEs is shown in Figure 13.1. The BS transmits control, management, and data packets in the downstream direction to the various CPEs, which in turn respond back to the BS in the upstream direction. Based on the feedback received from the CPEs, if any, the BS decides its next actions. The CR network can be used in point-to-point (P2P) or point-to-multipoint (P2MP) mode, using omnidirectional or directional antennas. BS/CPEs typically use omnidirectional antennas for incumbent sensing and receiving data while sectored/directional antennas for transmission purpose. In the United States, TV bands are spread from 54 to 806 MHz and each TV channel is usually 6 MHz. In the initial standard version, the CR-enabled devices can operate/transmit using the 6-MHz channels. The spectral efficiency ranges from 0.5 bit/s/Hz to 5 bit/s/Hz, thus resulting in an average data rate of 18 Mbit/s and maximum up to 30 Mbit/s in a single 6-MHz TV band.
Figure 13.1. An example of CR network system with BS and CPEs.
13.2.2 MAC Layer Overview
The existing MAC of proposed cognitive radio devices has most of the features similar to the MAC of 802.11 and 802.16. However, few distinguishing features make the newly proposed MAC worth mentioning.
13.2.2.1 Initial Connection Establishment.
Initial connection establishment in CR network differs from that of the previous IEEE 802 standards such as 802.11 or 802.16. Though connection establishment in a true centralized network should be simple, it is not so for the CR paradigm because there is no predefined channel for the CPEs to establish connection with BS as these networks share the spectrum band with licensed devices. Thus there is no way for a CPE to know what channel to use to establish the initial connection with a BS.
In CR network, when a CPE is switched on, it follows the mechanism of listen before talk by scanning all the channels in the licensed TV band to determine the presence of any incumbent in the interfering zone and builds a spectrum usage report of vacant and occupied channels. The BS, on the other hand, also follows the same mechanism of sensing spectrum and periodically broadcasts using an unused frequency channel. If a CPE can locate the broadcast sent from the BS, it then tunes to that frequency and then transmits back in the uplink direction with an unique identifier; BS thus becomes aware of the existence of the CPE. Authentication and connection registration is then done gradually. The spectrum usage report is then sent back to the BS from the CPE in the form of feedback. Upon acceptance of the feedback the BS makes a decision on spectrum usage. When more than one CPE tries to establish an initial connection, then a contention-based connection setup similar to that of the IEEE 802.11 takes place after all the CPEs tune to the broadcasted channel.
13.2.2.2 Incumbent Detection.
Much of the standard of cognitive radio paradigm is dependent on incumbent sensing and detection. At any point of time, a number of incumbents (TV broadcasting, wireless microphones etc.) may be operating in the same region as that of the CR network. To coexist with the incumbents, it is mandatory that incumbent sensing be done by both the BS and CPEs. CPEs send their spectrum usage reports to the BS in the form of feedbacks. Depending on the incumbent detection algorithms proposed and their efficiencies, the general spectrum sensing process in divided into two categories: fast sensing and fine sensing [4]. Fast sensing is done typically before fine sensing and uses a quick and simple detection algorithm such as energy detection. It is carried out primarily over in-band channels, and the outcome of these measurements will determine the need and the duration of the upcoming fine sensing. Fine sensing, on the other hand, is of longer duration (on the order of milliseconds for each single-frequency channel, e.g., 24 ms in the case of field-sync detection for ATSC [4]) as more detailed sensing is performed on the target channels. In other words, the fine sensing could be over three orders of magnitude larger than the fast sensing but provides more accuracy.
13.3 CHALLENGES AND RELATED WORK
Since a secondary CR network shares the spectrum bands dynamically with licensed devices and other secondary CR networks, the devices cannot know a priori what frequency bands other devices would be operating on. This gives birth to two very important challenges: (i) efficient dynamic spectrum access among multiple good CR networks (self-coexistence) and (ii) risk of primary user emulation attack from malicious secondary users/networks.
The advancements in software-defined radio (SDR) technology have led to the development of novel algorithms, architectures, and protocols for cognitive radio-based dynamic spectrum access. As far as dynamic spectrum sensing and access are concerned, there is a recent emerging body of works that deal with different decision-making aspects, issues, and challenges in a cognitive radio network setting. A proactive spectrum access approach is used in reference 13, where secondary users utilize past observations to (a) build predictive models on spectrum availability and (b) minimize disruptions to primary users. Energy detection and interference temperature measurements have been largely used in references 14–16 to monitor primary spectrum usage activity. Spectral correlation-based signal detection for primary spectrum sensing in IEEE 802.22 WRAN systems is presented in reference 17. Signature-based spectrum sensing algorithms are presented in reference 18 to investigate the presence of Advanced Television Systems Committee (ATSC) DTV signals. In a similar effort, sequential pilot sensing of Advanced Television Systems Committee (ATSC) DTV signals is carried out in reference 19 to sense the primary usage in IEEE 802.22 cognitive radio networks. In reference 20, a novel frequency-sensing method is proposed known as dynamic frequency hopping (DFH). In DFH, neighboring WRAN cells form cooperating communities that coordinate their DFH operations where WRAN data transmission is performed in parallel with spectrum sensing without interruptions. The aim here is to minimize interrupts due to quiet sensing and increase QoS. Most of the above-mentioned works focus on primary spectrum usage sensing, but the issue of self-coexistence, sharing, or coordinated dynamic spectrum access to minimize interference and maximize self-coexistence is not considered.
In references 2 and 21–23, novel approaches of dynamic spectrum allocation among secondary users (cognitive radio) through a spectrum broker are investigated where the spectrum broker has the knowledge of dynamic availability of spectrum. With the introduction of auctions and pricing, the spectrum broker determines allocations among the secondary users. In reference 24, “economic behavior” of the network nodes are studied using game theory underlimited and finite channel capacity with pricing and purchasing strategies of the access point, wireless relaying nodes, and clients in wireless mesh networks. However, dynamic spectrum access is not considered in this work. Though the pricing models have potential of generating revenue through commercialized secondary spectrum usage, there are a number of challenges in terms of implementations for the pricing in dynamic spectrum allocation—that is, payment transaction method, best-effort-service nature of opportunistic spectrum access, trustworthiness, authentication, and many more.
In a system where unlicensed devices are sharing the spectrum under the presence of licensed incumbents, the issue of self-coexistence among multiple CR operators in an overlapping region is very significant. In areas with analog/digital TV transmissions and wireless microphone services, unused channels are already commodities of demand. The challenge of self-coexistence becomes even tougher because the networks do not have information about which bands other secondary CR networks will choose. In such a scenario (e.g., Figure 13.2), when multiple CR networks operated by multiple operators (or service providers) overlap, it is highly probable that the operators will try to act greedy and use the entire available bandwidth. Because all the operators will act in the same way, this may result in interference among CR networks themselves. Thus an efficient spectrum access method needs to be used such that the interference is minimized.
Figure 13.2. Multiple geographically co-located CR networks competing.
Although other aspects of cognitive radio networks have been studied in detail, there is not much literature available on the security [25–29]. In the particular case of DSA networks, it can be argued that in order to stage a denial-of-service (DoS) attack at the sensing level, it is necessary to affect the decision on primary activity during the sensing phase. This can be done in one of the following ways: (a) primary user emulation attacks (PUEA), where some malicious nodes emit signals that emulate the activity of the primary [26, 29–31]; (b) a set of nodes can lie about the the spectrum data (Byzantine attack) [27]; (c) by making use of the weaknesses of existing protocols for evacuation [25]; or (d) by modifying messages passed between the sensing nodes and the centralized decision maker [32].
A class of DoS attacks on the secondaries called primary user emulation attack (PUEA) is studied here. In such attacks, a set of “malicious” secondary users could spoof the essential characteristics of the primary signal transmission to make other “good” secondary users believe that the primary user is present. The secondary users following normal spectrum evacuation process (the good users) will vacate the spectrum unnecessarily, resulting in what are known as the primary user emulation attacks (PUEA).
Chen and Park [30] propose two mechanisms to detect PUEA: distance ratio test and distance difference test based on the correlation between the length of wireless link and the received signal strength. In reference 26, Chen et al. discuss defense against PUEA by localization of the malicious transmission using an underlying sensor network and comparing it with the known location of the primary transmitter. A mitigation technique for DoS attacks arising from fraudulent reporting of sensing results by malicious nodes is studied in reference 27. The PUEA methods described thus far do not take into account the fading characteristics of the wireless environment and require estimation of the location of the malicious users either via a dedicated sensor network or via significant enhancement of the secondary nodes themselves.
13.4 SELF-COEXISTENCE AMONG MULTIPLE CR NETWORKS
In this section, we formulate the self–coexistence problem as a dynamic channel2 switching game. We assume that N CR networks (players) operated by N separate wireless service providers in a region are competing for one of M separate orthogonal spectrum bands not used by primary incumbents. The CR networks can have partially or completely overlapped geographical overage area with each other. If one network is in the interference range of another, they cannot use the same spectrum band because the QoS of both the networks will suffer. In this scenario, we model the dynamic channel switching as a noncooperative game where the aim of each network is to capture a spectrum band free of interference. We assume that the only control information needed for participating successfully in the game is the number of overlapping competitors in the region, which can be known from the broadcasting beacons by each of the CR networks in the Foreign Beacon Period (FBP) [4].
13.4.1 Decision Problem of CR Network
We assume that each CR network can dynamically choose one of the M allowable spectrum bands for its operations. If two or more overlapped networks operate using the same spectrum band, then interference will occur and their transmissions will fail. Thus the networks will have to make new decisions for channel switching in the next stage of the game. The game ends when all the networks are successful in capturing a clear spectrum band. The optimization problem is to find the mechanism of achieving minimum number of failed transmission stages from the networks. As far as the decision strategy in this game is concerned, if interfered at any stage of the game, network i has the binary strategy set of switching to another band (expecting to find a free spectrum band) or staying on the current band (assuming the interferers will move away).
When an interfered network i chooses either “switch” or “stay,” it faces one of two possible costs in terms of time units. If the network i chooses to switch, it faces a cost of finding a clear spectrum band in the game. Note that in a game of N networks competing over M spectrum bands, the network i might find the clear channel just after 1 switching, or it might take more than 1 switching as multiple networks might choose the same band chosen by network i resulting in a subgame. Moreover, note that with varying N and M, the average cost of finding a clear band will also vary. We define the expected cost of finding a clear channel, if the network chooses the strategy of switching, as
over all possible resulting subgames, where si and s−i denote the strategies chosen by network i and rest of the networks, respectively. c is the cost of single switching and f(·) is a function that depicts the varying behavior of the cost with N and M. We assume a simple closed form of f(N, M) = NM/(M − N). The intuitive reason behind proposing such a function is that expected cost to find a clear band increases with increasing N but fixed M, while the cost decreases with increasing M but fixed N; however, with both N and M increasing, the cost varies simultaneously with the ratio of M : N and the difference between them. Note that we could choose any other form for f(N, M) as long as the above conditions are satisfied.
At the beginning of the stage, if the network i chooses the strategy of “stay,” it might fall in one of three different scenarios: (i) All the other networks that were attempting to operate using the same band as network i might move away, thus creating a clear band for network i. (ii) All the other networks that were attempting to operate using the same band as network i might also “stay,” thus wasting the stage under consideration and repeating the original game G, which started at the beginning of the stage. (iii) Some of the networks move (“switch”) while some networks end up being in the same band (“stay”), thus wasting the stage under consideration and creating a subgame G′ of the original game G. More detailed explanations for subgame G′ will be presented later. We define the cost functions as
(13.2)
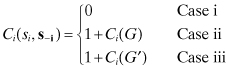
13.4.2 Self-Coexistence Game Analysis
With the strategy set and cost functions defined, the optimization problem in this game is to find a mechanism of switching or staying such that the cost incurred can be minimized and an equilibrium can be achieved. We typically assume that all the players are rational and pick their strategy, keeping only individual cost minimization policy in mind at every stage of the game. We intend to find if there is a set of strategies with the property that no network can benefit by changing its strategy unilaterally while the other networks keep their strategies unchanged (Nash equilibrium) [33].
For this purpose, we study the game with mixed strategy by assigning probabilities to each of the strategies in the binary strategy space. We define the mixed strategy space of network i as ![]() , where network i chooses the strategy “switch” with probability p and chooses the strategy “stay” with probability (1 − p). Since all networks are assumed to behave identically, we assume similar mixed strategy space for all the networks. The question now is, What values of (p, 1 − p) tuple will help us achieve the optimal solution—in other words, if there exists any finite nonzero probability of “switch” and “stay”?
, where network i chooses the strategy “switch” with probability p and chooses the strategy “stay” with probability (1 − p). Since all networks are assumed to behave identically, we assume similar mixed strategy space for all the networks. The question now is, What values of (p, 1 − p) tuple will help us achieve the optimal solution—in other words, if there exists any finite nonzero probability of “switch” and “stay”?
We start the game with all (N − 1) other networks coexisting with network i on one band and choose a strategy from mixed strategy space. Then regardless of the strategy chosen by network i, the resulting subgame will obtain one of the following possible outcomes: All N − 1 networks choose “switch,” or N − 2 networks choose “switch,” · · · , or 0 networks choose “switch.” To find the Nash equilibrium, we then determine the expected cost if network i under consideration chooses to “switch” or “stay.” Following the switching cost for finding a nonoccupied band as indicated previously in Eq (13.1), the expected cost over all possible resulting subgames for network i, if it chooses to switch, is
where j denotes the number of other networks choosing to “switch” and Qj denotes the probability of j networks switching out of other N − 1 networks and is given by ![]() . On the other hand, the expected cost for network i, if it chooses “stay,” can then be given as
. On the other hand, the expected cost for network i, if it chooses “stay,” can then be given as
where ![]() denotes the expected cost incurred in subgame
denotes the expected cost incurred in subgame ![]() . Note that if the expected cost of switching is less than the expected cost of staying, network i will always choose the strategy “switch,” thus going back to the pure strategy and as a result cannot achieve the Nash equilibrium [34]. Again, if the expected cost of staying is less than the expected cost of switching, similar reasoning can be applied for the strategy “stay” and Nash equilibrium can not be achieved. Thus for the existence of mixed strategy Nash equilibrium, network i must be indifferent between “switch” or “stay” regardless of strategies taken by other networks. In other words, the probability tuple (p, 1 − p) helps in choosing the strategy such that network i is never dominated by response from any other networks and thus will not deviate from the mixed strategy space (p, 1 − p) unilaterally to obtain lower cost. To find the optimal values for mixed strategy space, we equate Eqs. (13.3) and (13.4) as
. Note that if the expected cost of switching is less than the expected cost of staying, network i will always choose the strategy “switch,” thus going back to the pure strategy and as a result cannot achieve the Nash equilibrium [34]. Again, if the expected cost of staying is less than the expected cost of switching, similar reasoning can be applied for the strategy “stay” and Nash equilibrium can not be achieved. Thus for the existence of mixed strategy Nash equilibrium, network i must be indifferent between “switch” or “stay” regardless of strategies taken by other networks. In other words, the probability tuple (p, 1 − p) helps in choosing the strategy such that network i is never dominated by response from any other networks and thus will not deviate from the mixed strategy space (p, 1 − p) unilaterally to obtain lower cost. To find the optimal values for mixed strategy space, we equate Eqs. (13.3) and (13.4) as
Note that the expected cost of the game at Nash equilibrium is actually not dependent on j as evident from first part of Eq. (13.5), that is, how many networks are actually switching; rather, the cost varies with N, the number of networks, and M, the number of bands. Thus the expected cost for network i in the subgame ![]() can be deduced to be the same as that in the original game. Using binomial expansion and detailed mathematical derivations, we obtain the closed form for p as
can be deduced to be the same as that in the original game. Using binomial expansion and detailed mathematical derivations, we obtain the closed form for p as
For any values of N and M, p has a nonzero finite value, thus proving the existence of a mixed strategy Nash equilibrium point. In other words, the mixed strategy tuple, (p, 1 − p), presented in Eq. (13.6) constitutes the dominant best response strategy in this game.
13.5 RISK OF PRIMARY USER EMULATION ATTACK
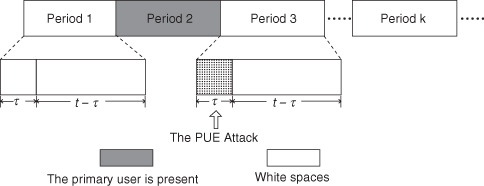
In this section, we discuss in detail the threat due to PUEA in DSA networks. We consider a cognitive radio network with a primary transmitter as well as the secondary and malicious nodes as shown in Figure 13.3. We assume that all secondary and malicious users are distributed in a circular grid of radius R as shown in Figure 13.3. A primary user is located at a distance of at least dp from all other users. We consider energy-based mechanisms to detect the presence of the primary. Typical energy-based detection methods assume that the primary is present if the received signal strength is −93 dBm [35]. We consider the time epochs in this network model to be divided into discrete periods where each period consists of one sensing slot, τ, and one transmission slot, t − τ. Figure 13.4 shows instances of the presence of the primary, the absence of primary, and an instance of a PUE attack.
Figure 13.3. A typical cognitive radio network in a circular grid of radius R consisting of good secondary users and malicious secondary users. No malicious users are present within a radius R0 about each good secondary user. A primary transmitter is located at a distance of at least dp from all other users.
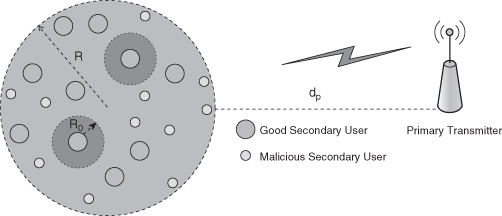
Figure 13.4. Discrete sensing/transmission periods. In each period, τ and t − τ represent the sensing slot and transmission slot, respectively. Note that the shaded period indicates that the primary user is using the spectrum band and the grid filled sensing slot indicates that the attack has been launched.
In each period, the secondary user measures the received signal power during the sensing slot. Also, we assume that secondary users are not naive, that is, they are aware of the existence of malicious users around the network. However, they know neither the locations of malicious nodes nor the slots when the attacks will be launched. Hence, identifying the presence of the primary user is a challenging task for the secondary user because the received energy might be from the primary user or the malicious user or both.
In order to mitigate this threat, we devise two hypothesis-based testing mechanisms to decide if the primary is transmitting or if an attack is in progress. We consider a system where there is no cooperation between the secondary users. Thus, the probability of PUEA on any user is the same as that on any other user. Hence, without loss of generality, we analyze the probability density function (pdf) of the received signal at one secondary user located at the origin (0, 0). All malicious nodes are then uniformly distributed in the annular region with radii R0 and R.
The first step to obtain a hypothesis test is to determine the probability density function (pdf) of the received signal at the secondary user due to transmission by the primary and the malicious users. Consider M malicious users located at coordinates (rj , θj) 1 ≤ j ≤ M. The position of the jth malicious user is uniformly distributed in the annular region between R0 and R. Also, rj and θj are statistically independent ∀ j. The received power at the secondary user from the primary transmitter, ![]() , is given by
, is given by
(13.7)
![]()
where Pt is the primary transmit power, ![]() , and
, and ![]() . Since Pt and dp are fixed, the pdf of
. Since Pt and dp are fixed, the pdf of ![]() , p(pr)(γ), follows a log-normal distribution and can be written as
, p(pr)(γ), follows a log-normal distribution and can be written as
where A = ln10/10 and
(13.9)
![]()
The total received power at the secondary node from all M malicious users is given by
where Pm is the transmit power of each malicious user, dj is the distance between the jth malicious user and the secondary user, and ![]() is the shadowing between the jth malicious user and the secondary user.
is the shadowing between the jth malicious user and the secondary user. ![]() , where
, where ![]() . Conditioned on the positions of all the malicious users, each term in the summation on the right-handside of Eq. (13.10) is a log-normally distributed random variable of the form
. Conditioned on the positions of all the malicious users, each term in the summation on the right-handside of Eq. (13.10) is a log-normally distributed random variable of the form ![]() , where
, where ![]() , where
, where
(13.11)
![]()
Conditioned on the positions of all the malicious users, ![]() can be approximated as a log-normally distributed random variable whose mean and variance can be obtained by using Fenton’s method. Applying Fenton’s approximation for the weighted sum, the expression for the pdf p(m)(χ) can be approximated as a log-normal distribution with parameters μχ and
can be approximated as a log-normally distributed random variable whose mean and variance can be obtained by using Fenton’s method. Applying Fenton’s approximation for the weighted sum, the expression for the pdf p(m)(χ) can be approximated as a log-normal distribution with parameters μχ and ![]() of the form
of the form
The details of the derivation of ![]() and μχ can be found in reference 31. The NPCHT can be used to distinguish between two hypotheses, namely,
and μχ can be found in reference 31. The NPCHT can be used to distinguish between two hypotheses, namely,
(13.13)
![]()
The observation space is the sample space of received power measured at the secondary user. It is observed that there are two kinds of risks incurred by a secondary user in this hypothesis test.
- False Alarm: When the actual transmission is made by malicious users but the secondary decides that the transmission is due to the primary. In our case, this is also the probability of a successful PUEA.
- Miss: When the actual transmission is made by the primary transmitter but the secondary decides that the transmission is due to the malicious users. This is a serious concern if the good secondary does not wish to violate the spectrum etiquette.
The Neyman–Pearson criterion allows the secondary to minimize the probability of successful PUEA while fixing the probability of missing the primary user at a desired threshold, α. The decision variable, Λ, is given by
(13.14)
![]()
where x is the measured power of the received signal. In the above, p(Pr)(x) and p(m)(x) are given by Eqs. (13.8) and (13.12), respectively. The decision is then made based on the following criterion:
(13.15)
![]()
where λ satisfies the constraint that miss probability, Pr{D2|H1}, is fixed at α.
The WSPRT allows us to specify desired thresholds (α1 and α2, respectively) for both the false alarm and the miss probabilities. The decision variable after n sequential tests, Λn, is given by
(13.16)
![]()
where xi is the measured power at the ith stage. In the above equation, p(Pr)(xi) and p(m)(xi) are given by Eqs. (13.8) and (13.12), respectively. The decision is then made based on the following criterion:
(13.17)

The average number of observations required to arrive at a decision is given by
(13.18)
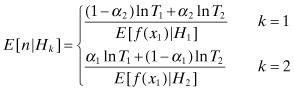
where the function f(x1) = ln Λ1.
13.6 SIMULATION MODEL AND RESULTS
We conducted simulation experiments to evaluate the improvements achieved by the proposed strategies. Source code for the experiment has been written in C under Linux environment.
13.6.1 Self-Coexistence Strategy Evaluation
We assumed that N secondary networks, operated by N separate wireless service providers, compete for one of M available spectrum bands. Each of the networks is associated with a mixed strategy space of “switch” and “stay.” The system converges when all the networks capture a spectrum band free of interference from other CR networks. N and M are given as inputs to the experiment.
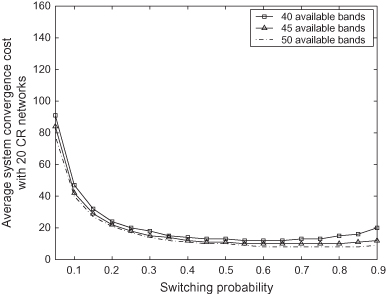
In Figure 13.5, we present the average system convergence cost with 20 competing cognitive radio (CR) networks. Switching strategy (probability) is varied for this simulation experiment. With increase in number of available bands, the convergence cost decreases. The convex nature of the curves in Figure 13.5, proves that a point of minima exists for each of the curve. This minima corresponds to the Nash equilibrium strategy (p).
Figure 13.5. Average system convergence cost with 20 CR networks and varying number of bands.
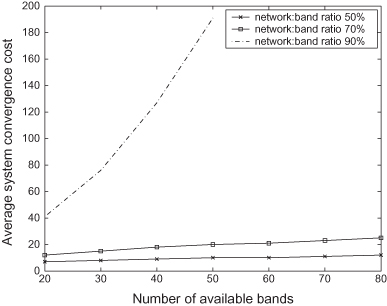
We also present different system convergence costs following mixed strategy space for a varying network : band ratio (50−90%) in Figure 13.6. We find that with an increase in the network : band ratio the system convergence cost increases almost exponentially, justifying the proposed cost function.
Figure 13.6. Average system convergence cost with varying network : band ratio.
13.6.2 Primary User Emulation Attack
The risk of PUEA is measured in terms of the probability of a successful attack. We run numerical simulations in Linux to perform the computations. We consider the following values of the system parameters for our numerical simulations. The variances for the primary and malicious transmissions are assumed to be σp = 8 and σm = 5.5. A primary transmitter (a TV tower), located at a distance of dp = 100 km to the secondary user, has a transmit power of Pt = 100 kW. The transmit power of the malicious users, Pm, is taken to be 4 W. The exclusive distance from the secondary user, R0, is fixed at 30 m. The number of malicious users is assumed to be a geometrically distributed random variable with E[M] = 25.
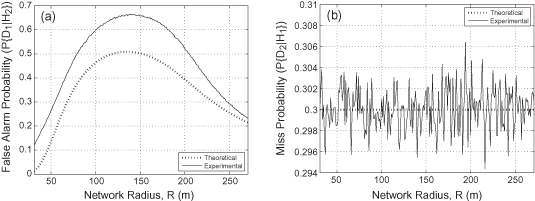
Figure 13.7 presents the probability of successful PUEA (Figure 13.7a) and the probability of missing the primary transmitter (Figure 13.7b) for the NPCHT with the theoretical probability of missing the primary user set to α = 0.3. It is observed from Figure 13.7a that the probability of false alarm rises and then falls down with increasing value of R. This is because, for a given R0, if R is small (i.e., malicious users are closer to the secondary user), the total received power from all malicious users is likely to be larger than that received from the primary transmitter, thus decreasing the probability of successful PUEA. Similarly, for large R, the total received power from the malicious users may not be enough to successfully launch a PUEA. Figure 13.7b shows that the experimental probability of missing the primary user is always close to the required value (within ± 0.04 of the desired value).
Figure 13.7. NPCHT with theoretical probability of missing primary user α = 0.3. (a) Probability of successful PUEA using the NPCHT. The average number of malicious users is fixed at 25. (b) Probability of missing primary user using the NPCHT.
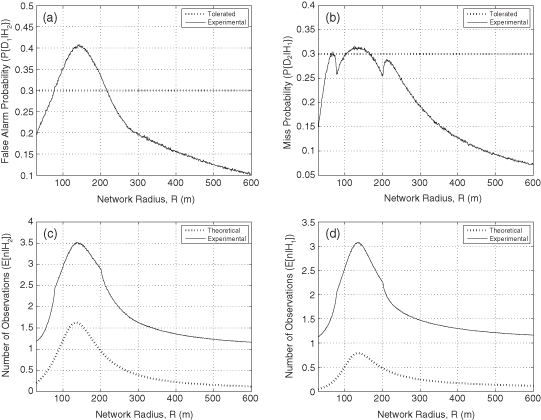
The performance of WSPRT is shown in Figure 13.8. The thresholds for the probability of successful PUEA and the probability of missing primary user are set to 0.3 each. Although the experimental curve in Figure 13.8a goes above the theoretical one, we achieve much lower probabilities of successful PUEA compared to Figure 13.7a. In fact, the maximum probability of successful PUEA in the NP test can go as high as 0.7, whereas in the Wald’s test we can limit this to 0.4. The lower probabilities of successful PUEA are achieved at the cost of more observations as shown in Figure 13.8c and Figure 13.8d. It is observed that number of observation behaves similar to the probability curves. This is because more observations are always taken if a decision cannot be made easily, where decision error probabilities also tend to be relatively high. Note that it is almost always possible to make sure that the probability of missing primary user stays strictly below the required threshold. This is particularly important in CRN to ensure that the secondaries still obey the spectrum-sharing etiquette.
Figure 13.8. WSPRT with theoretical probability of successful PUEA α1 = 0.3 and theoretical probability of missing primary user α2 = 0.3. (a) Probability of successful PUEA. (b) Probability of missing primary user. (c) Average number of observations when malicious users are transmitting. (d) Average number of observations when primary user is transmitting.
13.7 CONCLUSIONS
In this research, we investigated the spectrum etiquettes from secondary networks’ interaction perspectives. We focused on the issues of self-coexistence and primary user emulation attacks in such networks. We discussed how multiple overlapped CR networks controlled by different service providers can operate on the available spectrum and coexist. We used a noncooperative game to model this problem and presented mixed strategy for the CR networks. In order to mitigate PUEA, we proposed a Neyman–Pearson composite hypothesis test (NPCHT) and a Wald’s sequential probability ratio test (WSPRT). Simulation experiments showed that both WSPRT and NPCHT resulted in a range of radii in which PUEA were most successful. For a desired threshold on the probability of missing the primary, WSPRT was found to achieve about 50% reduction in the probability of successful PUEA compared to NPCHT. The extension of our analysis to include power control at the malicious users is a topic for further investigation.
Notes
1 Throughout the chapter, we use the terms “user” and “node” interchangeably.
2 Throughout this chapter, we use the words “channel,” “band,” and “chunk” interchangeably unless explicitly mentioned otherwise.
REFERENCES
1. [Online]. Available: http://www.sharedspectrum.com/inc/content/measurements/nsf/NY_Creport.pdf
2. M. Buddhikot, P. Kolodzy, S. Miller, K. Ryan, and J. Evans, DIMSUMnet: New directions in wireless networking using coordinated dynamic spectrum access, in IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, 2005, pp. 78–85.
3. Federal Communications Commission (fcc), Notice of proposed rule making, ET Docket no. 04-113, May 2004.
4. IEEE P802.22/D0.1, Draft Standard for Wireless Regional Area Networks Part 22: Cognitive Wireless RAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications: Policies and Procedures for Operation in the TV Bands, 2006. [Online]. Available: http://www.ieee802.org/22/
5. I. Akyildiz, W. Lee, M. Vuran, and S. Mohanty, Next generation/dynamic spectrum access/cognitive radio wireless networks: a survey, Computer Networks, Vol. 50, No. 13, pp. 2127–2159, 2006.
6. C. Cordeiro, K. Challapali, D. Birru, and S. Shankar, IEEE 802.22: The first worldwide wireless standard based on cognitive radios, IEEE International Symposium on Dynamic Spectrum Access Networks, November 2005, pp. 328–337.
7. S. Sengupta, S. Brahma, M. Chatterjee, and N. Sai Shankar, Enhancements to cognitive radio based ieee 802.22 air-interface, in Proceedings of IEEE International Conference on Communications (ICC), June 2007, pp. 5155–5160.
8. G. Ganesan and Y. Li, Cooperative spectrum sensing in cognitive radio networks, part i: Two user networks and part ii: Multiuser networks, IEEE Trans. Wireless Commun. Vol. 6, No. 6, June 2007.
9. Z. Quan, S. Cui, A. H. Sayed, and H. V. Poor, Optimal multiband joint detection for spectrum sensing in cognitive radio networks, IEEE Trans. Signal Processing, Vol. 57, No. 3, pp. 1128–1140, March 2009.
10. A. Ghasemi and E. Sousa, Interference aggregation in spectrum-sensing cognitive wireless networks, IEEE J. Sel. Top. Signal Processing, Vol. 2, No. 1, pp. 41–56, February 2008.
11. Z. Ye, G. Memik, and J. Grosspietsch, Energy detection using estimated noise variance for spectrum sensing in cognitive radio networks, in IEEE Wireless Communications and Networking Conference (WCNC), April 2008, pp. 711–716.
12. K. Kim, I. Akbar, K. Bae, J. sun Urn, C. Spooner, and J. Reed, Cyclostationary approaches to signal detection and classification in cognitive radio, in 2nd IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks (DySPAN), April 2007, pp. 212–215.
13. P. Acharya, S. Singh, and H. Zheng, Reliable open spectrum communications through proactive spectrum access, ACM Int. Conf. Proc. Ser., Vol. 222, 2006.
14. G. Ganesan and Y. Li, Cooperative spectrum sensing in cognitive radio networks, in Proceeding of IEEE DySPAN, 2005.
15. A. Ghasemi and E. Sousa, Collaborative spectrum sensing for opportunistic access in fading environments, in First IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks (DySPAN), November 2005, pp. 131–136.
16. A. Sahai, N. Hoven, and R. Tandra, Some fundamental limits on cognitive radio, in Forty-Second Allerton Conference on Communication, Control and Computing, 2004.
17. N. Han, S. Shon, J. Chung, and J. Kim, Spectral correlation based signal detection method for spectrum sensing in IEEE 802.22 WRAN systems, in Proceedings of 8th International Conference on Advanced Communication Technology (ICACT), Vol. 3, February 2006.
18. H. Chen, W. Gao, and D. Daut, Signature based spectrum sensing algorithms for IEEE 802.22 WRAN, in Proceedings of IEEE International Conference on Communications (ICC), June.
19. N. Kundargi and A. Tewfik, Sequential pilot sensing of atsc signals in ieee 802.22 cognitive radio networks, in IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), 2008, pp. 2789–2792.
20. W. Hu, D. Willkomm, M. Abusubaih, J. Gross, G. Vlantis, M. Gerla, and A. Wolisz, Cognitive radios for dynamic spectrum access—Dynamic frequency hopping communities for efficient IEEE 802.22 operation, IEEE Commun. Mag., Vol. 45, No. 5, pp. 80–87, May 2007.
21. L. Cao and H. Zheng, Spectrum allocation in ad hoc networks via local bargaining, in Proceeding of SECON, 2005.
22. O. Ileri, D. Samardzija, and N. Mandayam, Demand responsive pricing and competitive spectrum allocation via spectrum server, in Proceedings of IEEE DySPAN, November 2005.
23. S. Sengupta, M. Chatterjee, and S. Ganguly, An economic framework for spectrum allocation and service pricing with competitive wireless service providers, in IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), 2007, pp. 89–98.
24. R. Lam, D. Chiu, and J. Lui, On the access pricing and network scaling issues of wireless mesh networks, IEEE Trans. Computers, Vol. 56, No. 11, pp. 1456–1469, November 2007.
25. G. Jakimoski and K. Subbalakshmi, Denial-of-service attacks on dynamic spectrum access networks, in IEEE CogNets Workshop, IEEE International Conference on Communications (ICC), May 2008, pp. 524–528.
26. R. Chen, J. M. Park, and J. H. Reed, Defense against primary user emulation attacks in cognitive radio networks, IEEE J. Sel. Areas Commun.: Special. Issue on Cognitive Radio Theory and Applications, Vol. 26, No. 1, pp. 25–37, 2008.
27. R. Chen, J. M. Park, and K. Bian, Robust distributed spectrum sensing in cognitive radio networks, in Proceedings of IEEE Conference on Computing and Communication (INFOCOM’2008), April 2008, pp. 1876–1884.
28. A. Sethi and T. X. Brown, Hammer model threat assessment of cognitive radio denial of service attacks, in Proceedings of IEEE Symposium of New Frontiers in Dynamic Spectrum Access Networks (DySPAN’2008), October 2008.
29. Z. Jin, S. Anand, and K. P. Subbalakshmi, Detecting primary user emulation attacks in dynamic spectrum access networks, in Proceedings of IEEE Int. Conference on Communication (ICC’2009), June 2009.
30. R. Chen and J. M. Park, Ensuring trustworthy spectrum sensing in cognitive radio networks, in Proceedings IEEE Workshop on Networking Technol. for Software Defined Radio Networks (SDR’2006), September 2006, pp. 110–119.
31. Z. Jin, S. Anand, and K. P. Subbalakshmi, Mitigating primary user emulation attacks in dynamic spectrum access networks using hypothesis testing, ACM Mobile Computing Commun. Rev. (MC2R): Special Issue on Cognitive Radio Networks, 2009.
32. G. Jakimoski and K. P. Subbalakshmi, Towards secure spectrum decision, in Proceedings IEEE Intl. Conference on Communication. (ICC’2009), June 2009.
33. J. Nash, Equilibrium points in N-person games, Proc. Natl. Acad. Sci., Vol. 36, pp. 48–49, 1950.
34. S. Sengupta, R. Chandramouli, S. Brahma, and M. Chatterjee, A game theoretic framework for distributed self-coexistence among ieee 802.22 networks, in Proceedings of IEEE Global Communications Conference (GLOBECOM), December 2008, pp. 1–6.
35. IEEE Standards for Information Technology, Telecommunications and Information Exchange Between Systems; Wireless Regional Area Networks—Specific Requirements, Part 22; Cognitive Wireless RAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications: Policies and Procedures for Operation in the TV Bands, June 2006.