This section deals with binary files that contain malware samples. For this purpose, we may need to isolate the environment of the malware once again.
- Please repeat adding the Host-only Adapter
vboxnet0and set it just the way we did in Chapter 1, Getting Started with Automated Malware Analysis using Cuckoo Sandbox. - Start the windows-cuckoo from VirtualBox, set the IP, and save the snapshot of it.
- Remember to turn it off, change the Cuckoo configuration, and restart it.
- You can start to analyze the binary file using the following command:
$ python utils/submit.py --platform windows shares/Sality.G.exe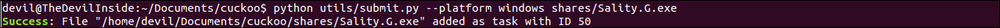
- Also remember that the
.exefile was named asSality.G.exein order to warn the user that this file is a virus namedSality.G.exe. This file disguises itself as a keygen and activator for certain software. - Please make sure you have a Success message as shown in the preceding screenshot with task with ID 50.
Windows will open the binary file.
- We do not need to add the
--packageargument because the default package that Cuckoo will execute first contains.exefiles. And actually we do not need to add the- -platform windowsargument because by default we have configured it in.conffiles. But just to make sure it works, as we hope for, we just add it.Windows will open the
.exefile and a pop-up window will appear as shown in the following screenshot: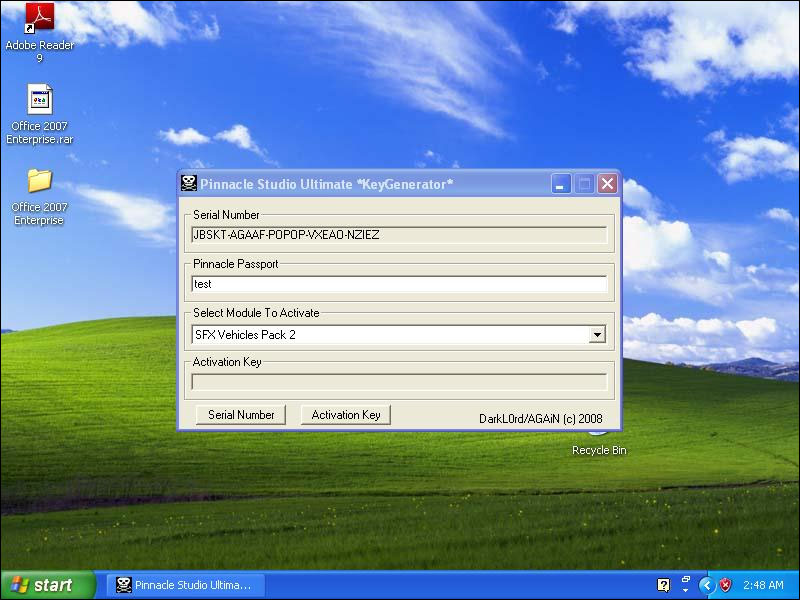
The malware binary disguises itself as a key generator for some software. The reason behind this is because people intend to have free software, so they must have this kind of software. They will not care whether some antivirus is warning them. It will run because people needed it the most.
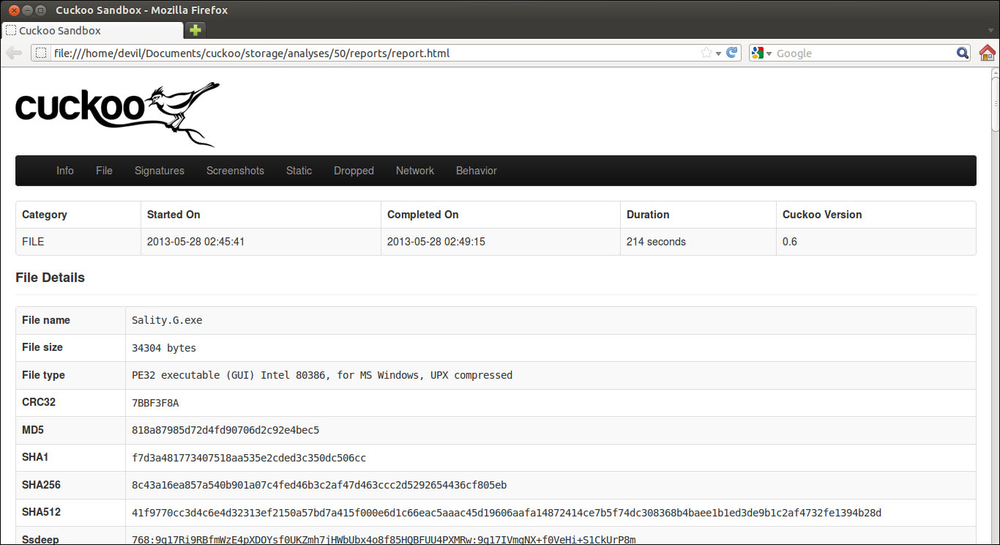
Let's see the report.html from Cuckoo Sandbox. Based on the ID, we will find it at storage/analyses/50/reports.
Open the report.html in your web browser:
Please take a look at the VirusTotal section:
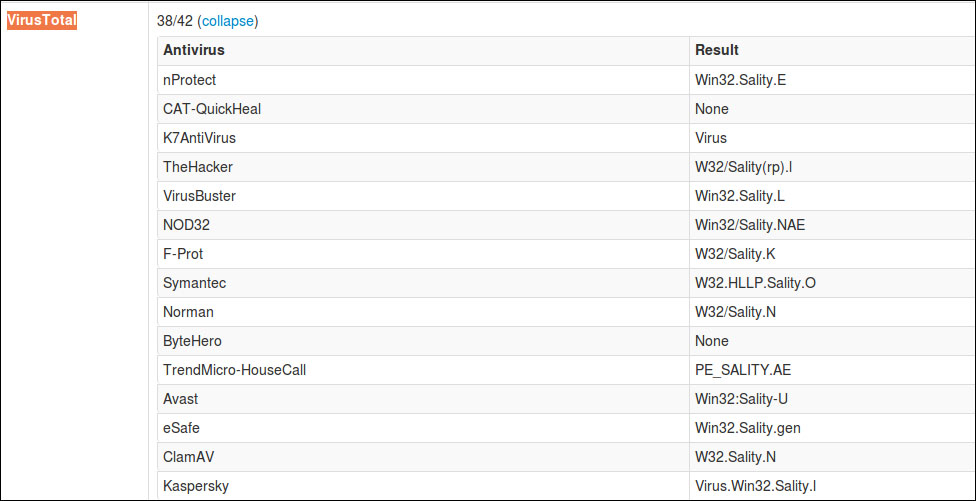
That .exe file was identified as a virus named Sality. Now continue to the Static Analysis section:

It will import some library form KERNEL32.DLL.
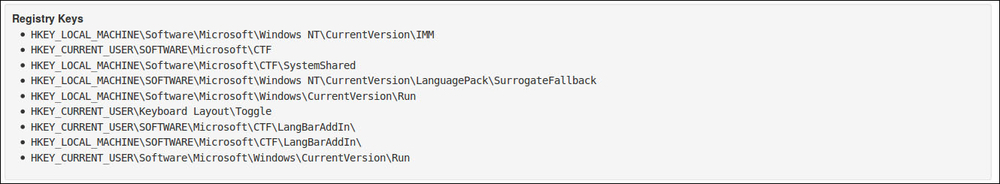
The malware binary then will access and put some entry into the registry. As you may see, it will access the registry entry, such as HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun that defines the programs that can run at startup. This is typical of common virus activity to maintain their access to the victim's computer.
Now let's see what the virus is doing in the host machine in detail. In the Processes section, we will see an entry like the following screenshot:

Click on Sality.G.exe and we will see its details in the following screenshot:

As we can see , the binary malware tried to make a file in C:WINDOWSsystem32. A lot of activities like that may occur as you may have seen in the report.
Note
More about utils option can be found in this page:
(https://cuckoo.readthedocs.org/en/latest/usage/utilities.html)
If you want to repeat the above process. Just use the following command:
$ python utils/process.py [task ID]
For example, you may use command:
$ python utils/process.py 50
From this example, you are running again the process engine for analysis number 50.
Or, if you just want to re-generate the report please use command:
$ python utils/process.py --report [task ID]
