Chapter 7
Securing Your Accounts
IN THIS CHAPTER
![]() Understanding that you’re a target
Understanding that you’re a target
![]() Understanding the different types of data that need to be secured
Understanding the different types of data that need to be secured
![]() Securing your accounts from human error
Securing your accounts from human error
![]() Being careful when connecting external storage media
Being careful when connecting external storage media
The weakest link in the cybersecurity chain is almost always people, and the greatest threat to your own cybersecurity is likely yourself, with the members of your family being a close second. As such, all of the technology and technical knowledge in the world won’t deliver much value if you don’t also address various human shortcomings.
Realizing You’re a Target
Perhaps the most significant first step in securing yourself digitally is to understand that you’re a target and that nefarious parties have the desire to breach your computer systems, electronically accessible accounts, and anything else they can get their hands on.
Even if you already realize that you’re a target, it is important that you truly internalize such a notion. People who believe that criminals want to breach their computers and phones act differently than people who do not appreciate this reality, and whose lack of skepticism sometimes leads them into trouble. There is a difference between knowing something in theory and truly believing it. If you want to stay secure you must convince yourself that you really are a target, not just simply understand that in theory you may be.
The threat posed by such attacks is usually not that a criminal will directly steal someone’s money or data, but rather that some party will seek to harm the target in some other manner — a manner that may ultimately translate into some form of financial, military, political, or other benefit to the attacker and (potentially) damage of some sort to the victim. Often the damage is far greater than if the criminal were just seeking to “make a quick buck.”
Securing Your External Accounts
Chapter 4 discusses how you can acquire your own technology products. But using these products isn’t enough to keep you cybersecure as you, no doubt, have digital data of significant value that is stored outside of your own physical possession — that is, outside of data systems and data stores under your control.
In fact, data about every person living in the western world today is likely stored on computer systems belonging to many businesses, organizations, and governmental agencies. Sometimes those systems reside within the facilities of the organizations to which they belong, sometimes they’re located at shared data centers, and, sometimes the systems themselves are virtual machines rented from a third-party provider. Additionally, some such data may reside in cloud-based systems offered by a third party. Not always is the data (or every copy of the data) even located within the same country as the people who are the subjects of the data.
In any event, such data can be broken down and divided into many different categories, depending on which aspects of it a person is interested in. One way of examining the data for the purposes of discovering how to secure it, for example, is to group it according to the following scheme:
- Accounts, and the data within them, that a user established and controls
- Data belonging to organizations that a user has willingly and knowingly interacted with, but the user has no control over the data
- Data in the possession of organizations that the user has never knowingly established a relationship with
Addressing the risks of each type of data requires a different strategy.
Securing Data Associated with User Accounts
When you bank online, shop online, use social media, or even simply browse the web, you provide all sorts of data to the parties that you interact with. When you establish and maintain an account with a bank, store, social media provider, or other online party, you gain control over significant amounts of data related to yourself that the party maintains on your behalf. Obviously, you can’t fully control the security of that data because the data is not in your possession. That said, you should have a strong interest in protecting that data — and, in not undermining the protections for the data that the party hosting your account has established.
While every situation and account has its unique attributes, certain strategies can help keep your data secure at third parties. Obviously, not all the ideas in the following sections apply to every situation, but applying the appropriate items from the menu to your various accounts and online behavior can dramatically improve your odds of remaining cybersecure.
Conduct business with reputable parties
There is nothing wrong with supporting small businesses — in fact, doing so is quite admirable. And, it is certainly true that many large firms have suffered serious security breaches. But if you search for the latest electronic gizmo, for example, and one store that you have never heard of is offering it at a substantial discount from the prices offered at all well-known stores, be wary. There may be a legitimate reason for the discount — or there may be a scam in the works.
Use official apps and websites
Clones of official apps have been found in various app stores. If you install a banking, credit card, or shopping app for a particular company, make sure that you install the official app and not some malicious impersonator. Install apps only from reputable app stores, such as Google Play, Amazon AppStore, and Apple App Store.
Don’t install software from untrusted parties
Malware that infects a computer can capture sensitive information from both other programs and web sessions running on the device. If a website is offering free copies of movies, software, or other items that normally cost money, not only may the offerings be stolen copies, but ask yourself how the operator is making money — it may be by distributing malware.
Don’t root your phone
You may be tempted to root your phone (especially if your phone runs the Android operating system). Rooting is a process that allows you greater control over your device — but rooting also undermines various security capabilities, and may allow malware to capture sensitive information from other apps on the device, leading to account compromises.
Don’t provide unnecessary sensitive information
Don’t provide private information to anyone who doesn’t need that particular data. For example, don’t give your Social Security number to any online stores or doctors. While they often ask for it, they have no need for it.
Use payment services that eliminate the need to share credit card numbers
Services like PayPal, Samsung Pay, Apple Pay, and so on let you make online payments without having to give vendors your actual credit card number. If a vendor is breached, the information about your account that is likely to be stolen is significantly less likely to lead to fraud (and, perhaps, even various forms of identity theft) than if actual credit card data were stored at the vendor. Moreover, major payment sites have armies of skilled information security professionals working to keep them safe that vendors accepting such payments can rarely, if ever, match.
Use one-time, virtual credit card numbers when appropriate
Some financial institutions allow you to use an app (or website) to create disposable, one-time virtual credit card numbers that allow you to make a charge to a real credit card account (associated with the virtual number) without having to give the respective merchant your real credit card number. As seen in Figure 7-1, some virtual credit card systems also allow you to specify the maximum allowable charge size on a particular virtual card number at a figure much lower than it would be on the real corresponding card.
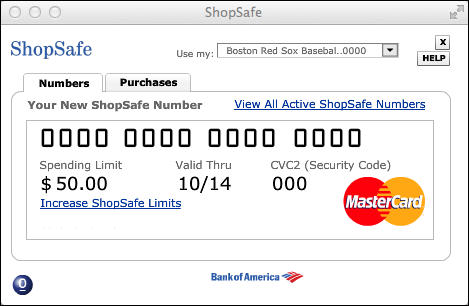
FIGURE 7-1: A (slightly edited image of) a one-time credit card number generator.
While creating one-time numbers takes time and effort, and, in fact, may be overkill when doing repeated deals with a reputable vendor in whose information-security practices you have confidence, virtual credit card numbers do offer benefits for defending against potential fraud and may be appropriately used when dealing with less familiar parties.
Besides minimizing the risk to yourself if a vendor turns out to be corrupt, virtual credit card numbers offer other security benefits. If criminals hack a vendor and steal your virtual credit card number that was previously used, not only can they not make charges with it, their attempts to do so may even help law enforcement track them down, as well as help relevant forensics teams identify the source of the credit card number data leak.
Monitor your accounts
Report suspicious activity ASAP
Employ a proper password strategy
While conventional wisdom may be to require complex passwords for all systems, such a password strategy fails in practice. Be sure to implement a proper password strategy. For more on choosing passwords, see Chapter 8.
Utilize multifactor authentication
Multifactor authentication means authentication that requires a user to authenticate using two or more of the following methods:
- Something that the user knows, such as a password
- Something that the user is, such as a fingerprint
- Something that the user has, such as a hardware token
For extremely sensitive systems, you should use forms of authentication that are stronger than passwords alone. The following forms of authentication all have their places:
- Biometrics, which means using measurements of various human characteristics to identify people. Fingerprints, voiceprints, iris scans, facial structures, the speed at which people type different characters on a keyboard, and the like are all examples of features that differ between people, and that can be compared in order to distinguish between folks and establish someone’s identity.
- Digital certificates, which effectively prove to a system that a particular public key represents the presenter of the certificate. If the presenter of the certificate is able to decrypt messages encrypted with the public key in the certificate, it means that the presenter possesses the corresponding private key, which only the legitimate owner should have.
- One-time passwords, or one-time tokens, generated by apps, read from a list of codes on a sheet of paper, or sent via SMS to your cellphone.
- Hardware tokens, which are typically small electronic devices that either plug into a USB port, display a number that changes every minute or so, or allow users to enter a challenge number and receive a corresponding response number back. Today, smartphone apps perform such functions, allowing, at least theoretically, the smartphone to assume the role of a hardware token. Figure 7-2 shows you an example of using such an app to generate a one-time code for logging into Snapchat. (Note that smartphones can suffer from all sorts of security vulnerabilities that hardware tokens can’t suffer from, so hardware tokens are still likely more appropriate for certain high-risk situations.)
 Knowledge-based authentication, which is based on real knowledge, not simply answering questions with small numbers of possible answers that are often guessable like “What color was your first car?” Note that technically speaking, adding knowledge-based authentication questions to password authentication doesn’t create multifactor authentication since both the password and the knowledge-based answer are examples of things that a user knows. However, doing so certainly does improve security when the questions are chosen properly.
Knowledge-based authentication, which is based on real knowledge, not simply answering questions with small numbers of possible answers that are often guessable like “What color was your first car?” Note that technically speaking, adding knowledge-based authentication questions to password authentication doesn’t create multifactor authentication since both the password and the knowledge-based answer are examples of things that a user knows. However, doing so certainly does improve security when the questions are chosen properly.
Most financial institutions, social media companies, and major online retailers offer multifactor authentication — use it.
Also, note that while sending one-time passwords to users’ smartphones via text messages theoretically verifies that a person logging in possesses the smartphone that the user is supposed to possess (something that the user has), various vulnerabilities undermine that supposition. It is potentially possible, for example, for a sophisticated criminal to intercept text messages even without possessing the relevant phone, or to hack into another chat application used for transmitting such codes.

FIGURE 7-2: One-time password for Snapchat generated by the app Authy — an example of an app-generated multifactor authentication token.
Log out when you’re finished
Don’t rely on automatic timeouts, closing the browser, or shutting down a computer to log you out of accounts. Manually log out every time you’re finished. Don’t leave yourself logged in between sessions unless you’re on a device that you know with — as close as possible to — certainty will remain secure.
Use your own computer or phone
You don’t know how well others have secured any one of more of their devices — a particular computer may, for example, have malware on it that can capture your passwords and other sensitive information or that can hijack sessions and/or perform all sorts of other nefarious activities.
Furthermore, despite the fact that doing so is severely problematic, some applications and websites — to this day — cache data on endpoints that are used for accessing them. You don’t want to leave other people souvenirs consisting of data from your sensitive sessions.
Lock your computer
Lock any computer that you use for accessing sensitive accounts, and keep it physically secure as well.
Use a separate, dedicated computer for sensitive tasks
Consider purchasing a special computer that you use for online banking and other sensitive tasks. For many people, a second computer isn’t practical, but if it is, having such a machine — on which you never read email, access social media, browse the web, and so on — offers security benefits.
Use a separate, dedicated browser for sensitive web-based tasks
If you can’t obtain a separate computer, at least use a separate browser for sensitive tasks. Don’t use the same browser that you use for reading the news, accessing social media, checking out blog posts, and/or most other activities.
Secure your access devices
Every phone, laptop, tablet, and desktop used for accessing secure systems should have security software on it, and that security software should be configured to regularly scan applications when they’re added, as well as to run periodic general scans. Also, make sure to keep the security software up to date — most antivirus technology products perform far better against newer strains of malware when they’re kept up to date than they do when they’re not.
Keep your devices up to date
Besides keeping your security software up to date, be sure to install operating system and program updates to reduce your exposure to vulnerabilities. Windows AutoUpdate and its equivalent on other platforms can simplify this task for you.
Don’t perform sensitive tasks over public Wi-Fi
If you must perform a sensitive task while you’re in a location where you don’t have access to a secure, private network, do what you need to do over the cellular system, not over public Wi-Fi. Public Wi-Fi simply poses too many risks. (To find out more about how to use public Wi-Fi safely, please see Chapter 21.)
Never use public Wi-Fi in high-risk places
Don’t connect any device from which you plan to perform sensitive tasks to a Wi-Fi network in areas that are prone to digital poisoning — that is, to the hacking of, or distribution of malware, to devices that connect to a network.
Hacker conferences and certain countries, such as China, that are known for performing cyberespionage are examples of areas that are likely to experience digital poisoning. Many cybersecurity professionals recommend keeping your primary computer and phone off and using a separate computer and phone when working in such environments. Such advice appeared in the media on a regular basis in the lead-up to the 2022 Winter Olympics in Beijing, during which both journalists covering the games, as well as athletes participating in them, discussed how they planned to address such concerns.
Access your accounts only in safe locations
Even if you’re using a private network, don’t type passwords to sensitive systems or perform other sensitive tasks while in a location where people can easily watch what you type and see your screen.
Use appropriate devices
Don’t try to save money by using dangerous equipment. Do not, for example, purchase electronics directly from sellers overseas and install unbranded networking devices that are not certified by any U.S. authorities. Such devices could have poisoned hardware within them.
Set appropriate limits
Various online venues let you set limits — for example, how much money can be transferred out of a bank account, the largest charge that can be made on a credit card with the card not physically present (as in the case of online purchases), or the maximum amount of goods that you can purchase in one day.
Use alerts
If your bank, credit card provider, or a store that you frequent offers the ability to set up text or email alerts, you should seriously consider taking advantage of those services. Theoretically, it is ideal to have the issuer send you an alert every time activity occurs on your account. From a practical standpoint, however, if doing so would overwhelm you and cause you to ignore all the messages (as is the case for most people), consider asking to be notified when transactions are made over a certain dollar amount (which may be able to be set to different thresholds for different stores or accounts) or otherwise appear to the issuer to be potentially fraudulent.
Periodically check access device lists
Some websites and apps — especially those of financial institutions — allow you to check the list of devices that have accessed your account. Checking this list each time that you log in can help you identify potential security problems quickly.
Check last login info
After you log in to some websites and via some apps — especially those of financial institutions — you may be shown information as to when and from where you last successfully logged in prior to the current session. Whenever any entity shows you such information, take a quick glance. If something is amiss and a criminal recently logged in while pretending to be you, it may stand out like a sore thumb.
Respond appropriately to any fraud alerts
If you receive a phone call from a bank, credit card company, or store about potential fraud on your account, respond quickly. But do not do so by speaking with the party who called you. Instead, contact the outlet at a known valid number that is advertised on its website.
Never send sensitive information over an unencrypted connection
When you access websites, look for the padlock icon (see Figure 7-3), indicating that encrypted HTTPS is being used. Today, HTTPS is ubiquitous; even many websites that do not ask users to submit sensitive data utilize it. If you don’t see the icon, unencrypted HTTP is being used. In such a case, don’t provide sensitive information or log in.
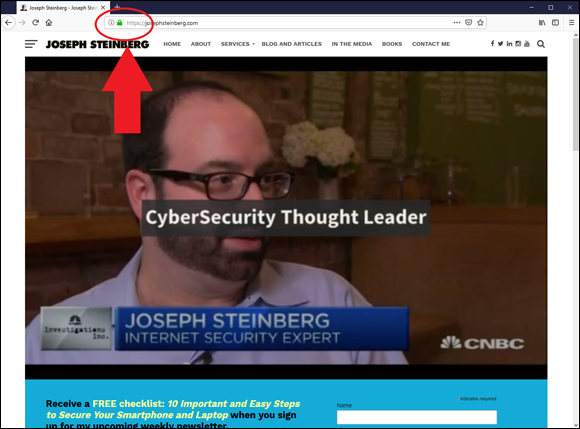
FIGURE 7-3: A secure website.
Beware of social engineering attacks
In the context of cybersecurity, social engineering refers to the psychological manipulation by cyberattackers of their intended victims into performing actions that without such manipulation the targets would not perform or into divulging confidential information that they otherwise would not divulge. A huge portion of successful data breaches begin with social engineering attacks.
To help prevent yourself from falling prey to social engineering attacks, consider any and all emails, text messages, phone calls, or social media communications from all banks, credit card companies, healthcare providers, stores, and so on to be potentially fraudulent.
Establish voice login passwords
Online access isn’t the only path that a criminal can use to breach your accounts. Many crooks do reconnaissance online and subsequently social engineer their ways into people’s accounts using old-fashioned phone calls to the relevant customer service departments at the target organizations.
Protect your cellphone number
If you use strong authentication via text messages, ideally set up a forwarding phone number to your cellphone and use that number when giving out your cell number. Doing so reduces the chances that criminals will be able to intercept one-time passwords that are sent to your phone and also diminishes the chances of various other attacks succeeding.
For example, Google Voice allows you to establish a new phone number that forwards to your cellphone so that you can give out a number other than your real cellphone number and reserve the real number for use within the authentication process.
Don’t click on links in emails or text messages
Clicking on links is one of the primary ways that people get diverted to fraudulent websites. For example, I recently received an email message that contained a link. If I had clicked the link in the message shown in Figure 7-4, I would have been brought to a phony LinkedIn login page that collects LinkedIn username and password combinations and provides them to criminals. Phishing emails and the like are examples of social engineering attacks, which are described earlier.
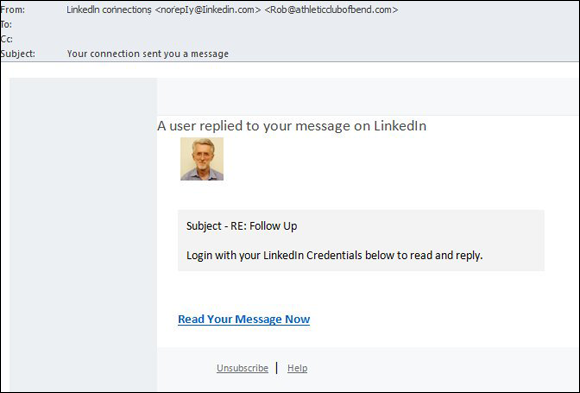
FIGURE 7-4: Email with a link to a phony page.
Securing Data with Parties You’ve Interacted With
When you interact online with a party, not all of the data related to your interaction is under your control. If you browse a website with typical web browser settings, that site may track your activity. Because many sites syndicate content from third parties — for example from advertising networks — sites may even be able to track your behavior on other sites.
To understand how this works, consider two different businesses with two different websites that are using the same advertising network. When the businesses add code to their discrete, separate sites, that code loads advertisements directly from the ad network. When a user visits the first site, the ad network may send a cookie to the user’s device, which the same ad network can read back when the user visits the second site, since both sites cause the user to interact with the same ad network.
If you have an account on any sites that do such tracking and log in, all the sites utilizing the syndicated content may know your true identity and plenty of information about you — even though you never told them anything about yourself. Even if you don’t have such an account or don’t log in, profiles of your behavior may be established and used for marketing purposes, even without knowing who you are. (Of course, if you ever log in in the future to any site using the network, all the sites with the profiles may correlate them to your true identity.)
It is far more difficult to protect data about you that is in the possession of third parties but that is not under your control than it is to protect data in your accounts. That does not mean, however, that you’re powerless. (Ironically, and sadly, most owners of such data likely do a better job protecting data about people than do the people themselves.)
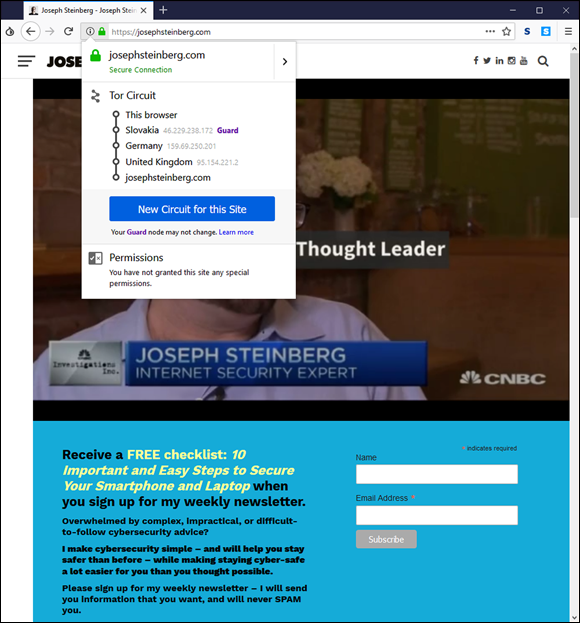
FIGURE 7-5: My website as seen in a Tor browser, with the Tor circuit information button clicked so as to show how Tor is hiding the user’s point of origin. The image was generated using the Tor browser bundle running on a computer in New Jersey, USA, but because of Tor’s security features, appears to the web server as if it were in the United Kingdom.
If Tor seems complicated, you can also utilize a reputable VPN service for similar purposes.
Securing Data at Parties You Haven’t Interacted With
Numerous entities likely maintain significant amounts of data about you, despite the fact that you’ve never knowingly interacted with them or otherwise authorized them to maintain such information.
For example, at least one major social media service builds de facto profiles for people who don’t (yet) have accounts with the service, but who have been mentioned by others or who have interacted with sites that utilize various social widgets or other related technologies. The service can then use these profiles for marketing purposes — even, in some cases, without knowing the person’s true identity, and without the person being aware of what is going on behind the scenes.
Furthermore, various information services that collect information from numerous public databases establish profiles based on such data — containing details that you may not even realize was available to the public.
Some genealogy sites utilize all sorts of public records and also allow people to update the information about other people. This ability can lead to situations in which all sorts of nonpublic information about you may be available to subscribers to the site (or people with free trial subscriptions) without your knowledge or consent. Such sites make finding people’s mothers’ maiden names or mothers’ birthdays easy, which undermines the authentication schemes used by many organizations.
Besides family tree sites, various professional sites maintain information about folks’ professional histories, publications, and so on. And, of course, credit bureaus maintain all sorts of information about your behavior with credit — such information is submitted to them by financial institutions, collection agencies, and so on.
While the Fair Credit Reporting Act may help you manage the information that the bureaus have about you, it can’t help you remove negative information that appears in other venues, such as in old newspaper articles that are online. Besides the privacy implications of such, if any information in those articles provides the answer to challenge questions used for authentication, it can create security risks. In such cases, you may want to reach out to the provider of the data, explain the situation, and ask it to remove the data. In some cases, they will cooperate.
In addition, some businesses, such as insurance companies and pharmacies, maintain medical information about people. Typically, individuals have little control over such data. Of course, this type of data, which isn’t under your complete control, can impact you. The bottom line is that many entities likely maintain significant amounts of data about you, even though you have never directly interacted with them.
It is the duty of such organizations to protect their data stores, but they do not always properly do so. As the Federal Trade Commission notes on its website, a data breach at the credit bureau Equifax, discovered in 2017, exposed the sensitive personal information of 143 million Americans.
The reality is that other than in the cases in which you can manually update records or request that they be updated, you can do little to protect the data in such scenarios.
Securing Data by Not Connecting Hardware with Unknown Pedigrees
While we have graduated from 720 kilobyte floppies to 2 terabyte USB drives, not much has changed conceptually since the 1980s in terms of the general danger of connecting data storage media with a questionable pedigree into a computer. If you connect a USB drive containing malware-infested files to your laptop, you may infect your laptop. Memory cards pose similar risks, as infected contents can lead to serious cybersecurity problems for any device into which the memory cards are inserted.
In addition, any time you connect a piece of hardware to a computer via a USB connection, you potentially enable communications between the two connected devices. Because of the way Plug and Play works, certain code on a USB device executes on a computer whenever the USB drive is first connected — and if that code is poisoned, you could be hacked as well.
The same holds true for other USB devices. Drivers are usually loaded upon connection, so a device with poisoned hardware or flash memory can create serious risk for any computer to which it is attached — and to any devices on the same network as that computer.
Furthermore, there are also dangerous USB devices designed to “fry” computers. Such devices charge themselves via the USB port, store the electricity in a capacitor, and then essentially fire it all out into the USB port in one big burst, permanently damaging electronics within the connected device in under a second.
Even phone chargers and the like can pose problems. Anything that connects to a USB port can potentially seek to communicate with the USB-port-enabled-device, and can potentially try to kill the USB-enabled device by overwhelming it with electricity.

 Because your family members can also impact your digital security, they also need to be aware that they are potential targets. If your children take unwise risks online, they may inadvertently inflict harm not only on themselves, but upon you and other members of the family as well. In some cases, attackers have managed to attack people’s employers via remote connections that were compromised because children misused computers on the same networks as computers that the employees were using for working remotely. Think about how dangerous such attacks can be and how much damage they can cause during an era in which large portions of the population work from home.
Because your family members can also impact your digital security, they also need to be aware that they are potential targets. If your children take unwise risks online, they may inadvertently inflict harm not only on themselves, but upon you and other members of the family as well. In some cases, attackers have managed to attack people’s employers via remote connections that were compromised because children misused computers on the same networks as computers that the employees were using for working remotely. Think about how dangerous such attacks can be and how much damage they can cause during an era in which large portions of the population work from home. Keep in mind that the less information about you that a specific party has, the less data that can be compromised, and correlated, in case of a breach.
Keep in mind that the less information about you that a specific party has, the less data that can be compromised, and correlated, in case of a breach.