Chapter 2
Cybersecurity Basics
While this book does not require the reader to be either a risk expert or cybersecurity expert, given there will be terminology and process discussions on some cybersecurity topics, some time spent on the terminology and the subject matter is warranted.
Cybersecurity has three main pillars: Confidentiality, Integrity and Availability (CIA):
- Confidentiality: Prescribes only authorized users and systems should be able to access or modify data.
- Integrity: Data should be maintained in a correct state and cannot be improperly modified.
- Availability: Authorized users should be able to access data when needed.
This is called the CIA Triad as shown in Figure 2.1.
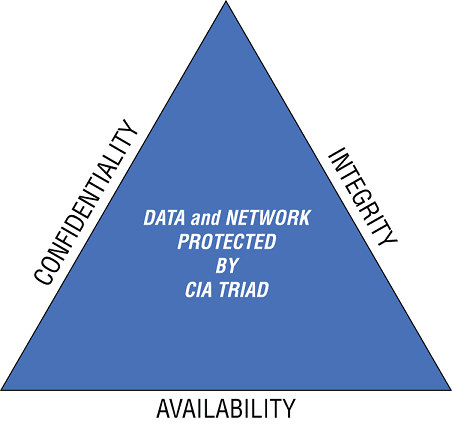
FIGURE 2.1 The CIA Triad
These pillars are designed to break down the complexities of cybersecurity to determine how to best make decisions. For example:
- Does the vendor store our data in ways that make it more secure?
- Will this product ensure the integrity of our data in the cloud?
- Can the vendor ensure that the data will be available when required to those who need it?
Because this book is mainly focused on third parties, references will be aligned with that focus in mind. It is not about what security your organization is performing, but what is going on at the third party, both with the specific services they provide and also how they secure their own enterprise. We include several examples of how a vendor's connection is used to target a company, and how their company‐wide cyber controls directly impact the ability to protect a company's data and any connection to your network (both intermittent and persistent).
Cybersecurity Basics for Third‐Party Risk
Some terminology and a few foundational cybersecurity principles are required for a discussion on vendor risk management. Many of these concepts and components of cybersecurity are reviewed throughout this book. The reader isn't expected to be a cybersecurity expert; however, it's easier to grasp risk, priority, and actions if you have a basic understanding of them. You should keep the following bolded terms, which have simplified explanations, in mind.
Encryption is the process of taking plaintext, like a text message or email, and scrambling it into an unreadable format called cipher text. This text helps protect the confidentiality of data, either stored on computer systems or transmitted through a network like the internet. This capability is at the core of most discussions for securing data. There are subcategories in this area, such as synchronous and asynchronous encryption, but for this book, the discussions revolve mostly around the level of encryption. Advanced Encryption Standard (AES) is the type of encryption most often used by the U.S. government, among others. Most organizations typically leverage the AES‐128 or AES‐256 level of encryption for their enterprise. The trade‐off of higher encryption levels is speed—the higher the number, the more processing power it takes to decrypt—thus, the higher the number, the better.
Another area of encryption to focus on is the three states of encryption. Data consists of three states: at‐rest, in‐motion, and in‐use. At‐rest is as it sounds, meaning when the data is in a database or file. In‐motion refers to when data is traveling over a network or the internet. When a process is using the data, as in the CPU or memory, it is considered to be in‐use. In all three states, it is important to have the data encrypted. As you engage vendors on how they protect the data, ensure that your discussion involves all three states.
In recent years, a new mantra has been born: “Identity is the new perimeter.” This statement refers to how millions of people, especially after the rush to remote work during the COVID‐19 pandemic, are now connecting to work and school away from those places. Their identities, which are used to connect users to organizations, work, or school, and how that access is managed, which is known as access management, is very important when protecting the enterprise (and the data that resides internally at the vendor). It requires entities to focus on several areas for third‐party risk.
First, we cover the access process, which includes three steps: identity, authorization, and access. The identity phase is where a user types in their name and password and the system confirms their identity. Next, the authorization step confirms what access the user has—what that user is permitted to see and do. Lastly, the correct level of access is provided. Once these three steps are completed, the user is permitted to access the data and resources they have authorization to view.
The most common type of access in corporate environments, role‐based access (RBAC), includes predefined job roles with a specific set of access privileges. This implementation is demonstrated by the difference between two examples of types of roles. For example, a human resources (HR) manager will likely have access to payroll and personnel files. However, if they try to log in to a finance server, it will not permit them to connect because they do not have a role in the finance department. If the HR manager requires entry into that server, they must submit a business reason to the access management team for needing access to that server.
Single Sign‐On (SSO) is a mechanism that limits the number of times a user has to submit their identity for access verification. In most larger organizations, users are required to interact with multiple systems. Their SSO enables them to log in once and gives them permission to gain access without reentering their credentials. The different systems pass this credential permission between them silently and provide access to other systems and services without referencing the credentials.
Multi‐factor authentication (MFA), also referred to as two‐factor authentication (2FA), refers to when there is more than one login step required. (Note, two or more factors can be involved in this authentication.) There are four main types of MFA:
- Things you know, like your password or PIN.
- Things you have, such as an employee badge or security token (physical and soft).
- Things you can refer to, such as biometric items like your fingerprints, retinas, or voice.
- Where you are based—your location. Most systems leverage this in the background, so the end user may be unaware of this check. Note, this MFA type is not used as often, but if you are based in the United States and someone attempts to use your login in South America, the system is attuned to this difference and would take appropriate action, such as prompt for additional verification or deny access.
MFA is an important security feature and should be pushed to all account types. At a minimum, MFA must be used for all privileged and elevated accounts. Privileged accounts are those with elevated access and permissions to do things that present a higher risk, such as system administrators, senior executives, and data owners. This important feature ensures that only the authorized user gains data access.
Least‐privilege is a principle where a user has only the privileges (i.e., access) they need to complete the task or job at hand. For example, a database user who only needs access to be able to view data records should not have permission to perform deletions or change any users' rights to the database. Least‐privilege is important for ensuring that the Confidentiality, Integrity and Availability is kept for the data.
As part of the security hygiene, patch management is an important component. It's the process of distributing and applying updates to software and hardware. This process is vital to fixing errors and vulnerabilities. Vendors must focus on what their processes are and how they prioritize them as security vulnerabilities are identified and categorized (high to lower priority), tested, and deployed into production.
An Intrusion Detection System (IDS) is hardware or software that monitors network traffic and computer systems looking for anomalous behavior or known threats. The IDS alerts security personnel, which is why this system is called a detection system—it takes no other action except to detect and alert. While there are several IDS types, what your vendor uses is generally not an issue. The disadvantage of an IDS is that it doesn't take any actions, it merely alerts; if it detects suspicious network traffic, it does not stop the traffic. The general rule of thumb is that most companies do not buy an IDS as a standalone product but as part of a suite or bundled product. This system doesn't take action against the suspicious traffic, but leaves it in place within the enterprise notifying Security so it can be monitored.
An Intrusion Prevention System (IPS) is software or hardware that can both detect and prevent known threats. These systems can also just alert, depending on how their thresholds are configured. These systems continuously evolve, and in recent years, have advanced. Network access controls and firewalls are now available with this feature.
Firewalls inspect network traffic and block or allow traffic based upon rules. Available as hardware and software, these devices have highly evolved from their early days and can now read and inspect encrypted traffic. These Next‐Generation Firewalls (NGFW) can look deep into the data within the network traffic as it passes by, and can provide options to take action, stopping anything that meets its malicious criteria.
An IP address is a string of numbers that identifies a unique computer or network. These unique numbers allow communications within private networks or over the internet. Think of an IP address as an address found on a mailed letter. As the email (or traffic) is passed along on the network, the provided IP address indicates where the email must go in order to get to the intended recipient. IP addresses have three numbers in four sets: 192.168.1.1 or 10.102.201.32 and billions of combinations.
Ports are physical or logical openings that allow connectivity for a specific program or application. An example of a physical port could be to plug in a mouse or a USB stick. On the logical side, an example is normal internet browsing that occurs over port 80. If you are connecting to a secure site, such as your bank, you would connect over port 443. These ports are there so that each side of the connection knows exactly which port to use when communicating. Similar to the IP address, a port enables the traffic to arrive at the intended computer or network; the port specifies which “room” to go to for the conversation.
A domain name server (DNS) is a system of computers that translate human‐friendly names (www.rasner.com) to an IP address, simply because IP addresses can evolve and virtually no one wants to memorize one. Whenever a user types in a website address, a DNS server helps translate it into the correct IP address to ensure that the target resource (i.e., a website, database server, printer, etc.) is found.
Network access control is a method used to restrict access to network resources by ensuring that devices (i.e., laptops, mobile devices, computers, servers, printers, etc.) comply with security policies. It is also known by its protocol name of 802.1x, and is viewed as an essential tool for limiting network access to those devices that meet security criteria and are allowed to connect to a network.
Out of band communications refers to devices that are not the primary connectivity device. For example, many vendors will use a router or VPN concentrator as hardware devices to connect to a customer's network. Some will want to place a modem or an alternate device for connecting to that network if the router is offline. These devices can be problematic for connectivity as they are usually not connected to any monitoring or logging system; hence, they can be a used as a backdoor by hackers.
A shared responsibility model for cloud security is adhered to by Cloud Service Provider (CSPs) and refers to how different solutions shift the responsibility from the CSP to the customer. In a traditional data center owned by a company, that company is responsible for its technology's delivery. When deploying to the cloud, the level of responsibility increases for the customer as they shift from Infrastructure as a Service (IaaS) to Platform as a Service (PaaS). The IaaS model requires the customer to perform more of the security and maintenance than in the PaaS model.
Personally Identifiable Information (PII) is data that is used alone or with other data and enables a viewer to identify an individual. Thousands of combinations of information are possible that make up data PII, but typically it contains name, Social Security numbers, financial info, drivers' licenses, physical address, phone numbers, or more.
Personal Health Information (PHI) is PII that pertains to an individual's medical information, such as smoking status, any illnesses, medications, and other very confidential medical data. PHI is considered more sensitive than PII and as such, requires more security.
Data classification is when data is analyzed and organized into categories based upon its sensitivity to the sorting organization. There are often three or four classes of data for most companies, but there should only be one category that is labeled as public and one labeled private or sensitive.
For the purposes of this book and how cybersecurity third‐party risk approaches this topic, the cloud is defined as any location not inside your own data center, server closet, or laptop hard drive (if you are a small‐business owner). The cloud could be located in a CSP, such as AWS, Google, or Azure, at a co‐location facility provider, or at a data center managed by the vendor directly.
Advanced Persistent Threat (APT) is considered a more superior threat actor because hackers use continuous, clandestine, and advanced techniques to gain access, remain stealthy for longer periods of time, and often leave undetected or with little evidence left behind for forensics. APTs are starting to utilize the supply chain cyber weaknesses.
Cybersecurity Frameworks
The information security field has been around long enough for more than a few standards to be written. Security frameworks are a collection of government cybersecurity policies and guidelines, and best practices set in place protect information systems. They often have specific instructions for organizations to handle PII to lower the risk of a breach or damage. Dozens of them exist globally, but you must be aware of a few top useful ones to understand their scope and focus. Cybersecurity frameworks provide defined structures for people, process, and technology that a company uses as a reference to secure their networks, data, and systems from cyber threats. Some are regulatory guidance (e.g., New York Department of Financial Services [NYDFS] or the Health Insurance Portability and Accountability Act [HIPAA]), which provide a framework's structure. Some companies adopt a framework that is aligned with their industry (e.g., Control Objectives for Information and Related Technologies [COBIT] and Finance, or HIPPA and healthcare providers).
National Institute of Standards and Technology Cybersecurity Framework (NIST‐CSF) was created in response to the U.S. Presidential Executive Order 13636, whose purpose was to enhance the security of the country's critical infrastructure. While aimed at critical infrastructure such as power and water delivery, many private companies have adopted it. NIST‐CSF contains the following five functions that manage the risk to data and systems security: Identify, Protect, Detect, Respond, and Recover. This is shown in Figure 2.2.
The Identify function focuses on identifying physical and software assets as a basis for managing assets. It defines what an organization's supply chain risk management strategy is, according to its priorities, constraints, risk tolerance, and assumptions that support the risk‐based decisions managing their supply chain risks.
The Protect function provides security controls to ensure the security and integrity of an organization's infrastructure systems. Through identity and access management (IAM), an organization seeks to limit and contain any possible damage, thus protecting both its physical and logical access. A data protection program must be aligned with the organization's risk strategy and appetite, and its data protection must align with the cybersecurity core principles of Confidentiality, Integrity and Availability. Its goals are to defend the organization's resources with a patch and vulnerability management programs, and to assist the staff in safeguarding its data and assets with awareness and training in best practices on the safe handling of protected information.
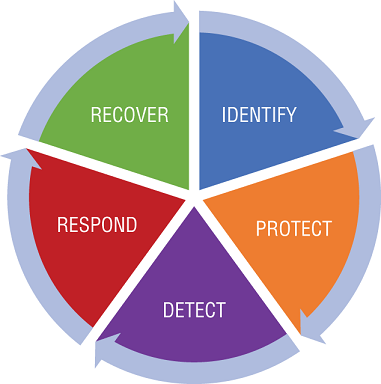
FIGURE 2.2 The NIST Cybersecurity Framework
The Detect function is as it sounds—it refers to the activity taken to discover indications of a security incident. This detection must be timely. Monitoring capabilities must be continuously implemented in order to find and identify anomalous events to catch malicious or suspicious behavior. When we think of an organization's cyber operations teams defending against hackers, we typically think of them as being in detection mode. Some of the capabilities used to detect are Security Information and Event Management (SIEM), Data Loss Prevention (DLP), Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), and the other tools, which are focused on this detection activity.
The Respond function ensures that correct actions are taken when a cybersecurity event is detected. Such activity ensures that cyber Incident Response plans are executed according to an organization's previously established processes. All work done to analyze and support recovery work is performed in a timely manner, and corrective activities are carried out to contain the incident and close the issue.
The Recover function acknowledges any impact, then prioritizes the restoration of services or capabilities in a timely manner to further reduce the event's impact. The execution of a recovery plan as it's designed and implemented ensures the restoration of an organization's systems. A “lessons learned” meeting, or what may be known as a post‐mortem on the incident, must occur to determine if any changes are required in the organization's existing plans. Communications—both inbound and outbound—are coordinated during and post recovery from the event.
What is important about this framework is that it prepares a cybersecurity organization for the inevitable: the breach. Risk is never a zero game, and eventually the vulnerability and threat actors align perfectly. The adoption of this cybersecurity framework forces an organization to best prepare to protect its data, but also for when an event does occur. An organization must have recognized plans in order to limit an attack's impact.
The ISO 27001 cybersecurity framework is an international standard that states a risk‐based process requires an adopting organization to incorporate measures for detecting security threats to information systems. ISO 27001 has a total of 114 controls that are categorized into 14 categories (with the number of controls):
- Information Security Policies (2 controls)
- Information Security Organization (7 controls)
- Human Resources Security (6 controls)
- Asset Management (10 controls)
- Access Controls (14 controls)
- Cryptography (2 controls)
- Physical and Environmental Security (15 controls)
- Operations Security (14 controls)
- Communications Security (7 controls)
- Systems Acquisition, Development, and Maintenance (13 controls)
- Supplier Relationships (5 controls)
- Information Security Incident Management (7 controls)
- Business Continuity Management (4 controls)
- Compliance (8 controls)
Organizations are not required to implement all 114 controls listed. The framework provides an outline for the controls that can be referred back to when performing a gap analysis and risk assessment compared to the ISO 27001. The downside is that the controls are not described in depth. To compensate for this lack of detail, organizations turn to the supplementary ISO 27002, which provides a lot of specificity to the cybersecurity controls. In ISO 27002, each control is given a page to explain how it operates and how to carry out the control.
NIST 800‐53 was created to enable government agencies to have effective cybersecurity controls. This framework specifically describes the requirements for federal government agencies to protect data and information systems. It has over 900 security requirements, which makes it very complex for an organization to implement. The number of requirements and the mandates required to enforce the compliance are focused primarily on any company whose systems interact with a federal agency information system. Also because of this complexity, unless the company is required to follow NIST 800‐53, most private companies will adhere to NIST‐CSF.
The New York Department of Financial Services (NYDFS) framework is a cybersecurity framework that covers nearly any entity performing financial services through the state of New York. The framework originates from NYDFS Cybersecurity Regulation (23 NYCRR 500) and “is designed to promote the protection of customer information as well as the information technology systems or regulated entities.” It requires companies to conduct risk assessments and to implement a program with security controls that detects and responds to cyber events.
The covered entity, a financial institution, must implement the following six items:
- A risk assessment must be conducted periodically to assess the Confidentiality, Integrity and Availability of information systems and protected data.
- An audit trail must record and respond to security incidents and be maintained for five years.
- Limits on data retention must be set in place to ensure that data is disposed of properly when no longer needed.
- Access Privileges must be implemented and limited to protected data, and access records must be periodically reviewed.
- An Incident Response plan must be published to ensure that cybersecurity events are clearly communicated, roles and responsibilities are clear, and remediation takes place.
- Notices to the superintendent (the superintendent is the organization that oversees the regulation) must be provided within 72 hours after a “material” cybersecurity event is detected.
NYDFS is similar to the General Data Protection Regulation (GDPR) and the California Privacy Protection, which have outsized power due to their economic size. Much of the world's finance flows through New York, and so many world finance companies are subjected to this framework. More importantly for this book, the NYDFS has a part that requires covered entities (i.e., those subject to the regulation) to perform due diligence on their third parties at regular intervals.
The Federal Information Systems Management Act (FISMA) is a framework for federal agencies. This standard defines a set of security requirements that the agencies use to improve their cybersecurity. The benchmark requires that third parties to an agency conform to their information security requirements. It contains nine steps for securing government data, operations, and assets:
- Defining the information categories for security levels
- Understanding the minimum security controls for protecting data
- Refining controls through risk assessments
- Documenting controls and developing security plans
- Implementing the required security controls
- Evaluating the effectiveness of implemented controls
- Establishing security risks for federal resources and data
- Authorizing the use of secure information systems
- Continuously monitoring the implemented controls
Several other frameworks are worth describing in high‐level detail. The Australian Signals Directorate (ASD) Essential 8 contains controls and strategies that are a part of the ASD Strategies to Mitigate Cyber Security Incidents. Based upon experience of the Australian government, these controls are considered by them to be the cybersecurity baseline in that country. If implemented correctly, the country reports it can mitigate up to 85 percent of most common cyberattacks.
The Control Objectives for Information and Related Technology (COBIT) framework is a high‐level framework for identifying and mitigating risk. COBIT is primarily used in the finance space to adhere to Sarbanes‐Oxley (SOX). SOX is also known as the Public Company Accounting Reform and Investor Protection Act. Developed by information technology (IT) governance professionals to lower risk, it has evolved to align to business goals.
The Ten Steps to Cybersecurity framework is an initiative of the United Kingdom's Department of Business to provide senior leaders with a cybersecurity overview. This framework acknowledges the urgency of giving executives knowledge about information security issues and risks that impact businesses, along with controls to mitigate them. It provides in business English (i.e., non‐technical, non‐jargon) an explanation in wider terms of the numerous cybersecurity risks, defenses, mitigations, and resolutions.
The Technical Committee on Cyber Security (TC CYBER) framework was developed to improve the telecommunication security in the European Union (EU). It contains a series of requirements for improving privacy for companies and individuals. The focus is to confirm that EU residents and citizens have a high level of privacy protection when communicating on all the various mediums in the zone. Although it's focused on the EU, it has been adopted by other countries worldwide.
These cybersecurity frameworks are important in third‐party risk due diligence work. When engaging with vendors about security due diligence, one of the first questions to ask is what cybersecurity framework they adhere to. Their answer will provide valuable information about how their organization performs its own security activities. Many of the frameworks or standards have similar themes and controls because cybersecurity does not vary industry to industry. However, what is often different is its focus or scope. Understanding which industry a vendor is in or the one you are subject to, can establish which framework is best used or a required fit.
Due Care and Due Diligence
Two of the concepts discussed often in this book, as well as in cybersecurity and third‐party risk, is due care and due diligence. Due care is using a reasonable effort to protect the interests of a company. For due care with vendors, it is ensuring they develop and formalize security policies, standards, baselines, and procedures to ensure the security of their environment. Due diligence is performing a reasonable exam and investigation before taking action. The opposite of due diligence is the ad‐hoc process. An ad‐hoc process is one that is not predefined but is essentially done without guidance. In this book, performing due diligence refers to the efforts of researching the risks of third parties. Due diligence is performing the necessary research to understand risk, while due care is performing the actions identified as needed from due diligence.
Cybercrime and Cybersecurity
The breaches and security incidents described in this book are primarily caused by cybercriminals and other bad actors. Breaches occur when an unauthorized individual gains access to a network and exposes sensitive data. Cybercrime is when such individuals use computers or the internet to perform criminal activities. The following outlines several types of cybercrime:
- Email and internet fraud: A fraudster sends an email enticing the user to a financial gain by offering a scheme, such as you will receive $10,000 or more if you send a portion of that amount to release it.
- Identity fraud: This cybercrime occurs when a cyber bad actor uses stolen identity data to commit a crime (e.g., when they apply for a credit card using a stolen identity).
- Financial and payment card data theft: Just as it sounds, this cybercrime is the stealing of credit/debit card numbers or nefarious direct access to bank accounts.
- Theft and sale of protected corporate data: While the focus is often on PII, there are other types of sensitive data at nearly every company that can be stolen and sold by bad actors, including internal price lists, computer/network information, financial data, and intellectual property.
- Ransomware: This cybercrime includes encrypting (i.e., making it unavailable to read) the target's data—ranging from a single desktop to whole server farms—and demanding money to unlock the encryption.
- Crypto jacking: This cybercrime is stealing your computer's processing power to “mine” for cryptocurrency and does not include targeting data.
- Cyberespionage: Whether done by a state actor (i.e., country), cybercriminals, or a competitor, this cybercrime involves spying on a firm using electronic means (i.e., computer).
The types of bad actors and their motivations can vary just as widely. While the vast majority are out for financial reward, a few other drivers exist:
- Cybercriminal: The modern‐day equivalent of the bank robbers, cybercriminals are electronic thieves. Most often, they deploy ransomware, phishing attacks, spear phishing, fake documentation, or denial‐of‐service attacks. The Home Depot attack in 2014 was the work of cybercriminals to steal payment card information.
- Nation‐state: Many nations have dedicated, highly skilled hackers who're paid to hack and perform espionage. However, some countries are more like cybercriminals, using their resources to become electronic bank robbers, and are known as Advanced Persistent Threats (APTs) because these organizations have nearly unlimited resources and time to focus on their target. Examples include the Sony attack by North Korean hackers in 2014; and Stuxnet (in 2009) whose origin hasn't been confirmed but largely thought to be a collaboration between Israeli and U.S. intelligence services to damage and delay the Iranian nuclear plans. Stuxnet is largely considered the first occurrence of cyberwarfare.
- Disgruntled employee: The insider threat is often not appreciated by business. We like to trust our employees and colleagues; however, there are some who will steal company data or property. For example, in 2018, a Tesla employee sabotaged the computer systems and sent proprietary data to outside parties.
- Professional hacking group: Usually this group consists of a loose confederation of highly skilled hackers who pool their resources to target for a political purpose, financial gain, or on behalf of cybercriminals. This group can also be referred to as APT due their resources and commitment. In 2020, the Philippine Long Distance Telephone (PLDT) company had its customer service Twitter account hacked by the Anonymous Philippines group. The group changed the profile name to “PLDT Doesn't Care.” The first tweet by the hackers was aggressive: “As the pandemic arises, Filipinos need fast internet to communicate with their loved ones. Do your job. The corrupt fear us, the honest support us, the heroic join us. We are Anonymous. We are Legion. We do not forgive. We do not forget. Expect us.”
- Hacktivist: Driven by political or social causes, this bad actor typically steals embarrassing information to cause reputational damage. The 2012 WikiLeaks' leaking of declassified information from the U.S. State Department and other countries is an example of hacktivism.
- Botnet masters: These malware creators create bots, which are an automated collection of internet‐connected devices that an attacker has compromised. These bots are leveraged by the creator to steal data or compromise systems. The botnet Mirai is a prime example. In 2016, the creators of this botnet software launched an attack on a security service company and at its peak infected over 6 million devices.
- Script kiddies: These generally unsophisticated hackers use off‐the‐shelf tools to gain access mostly for bragging rights, but sometimes for financial gain. In 2015, a 15‐year‐old was arrested for hacking into the U.K. telecom carrier TalkTalk Group PLC. While the attack was not sophisticated, it exploited an easy SQL injection method to gain access to a database.
Types of Cyberattacks
A cyberattack is defined as a malicious and deliberate attempt by someone to breach the systems of another. Various types of cyberattacks exist, including the following:
- Phishing: Nearly 100 percent of email users have received phishing emails. Posing as legitimate emails, these fake emails are used to encourage the email recipient to click a link, download a file, or even call a number so that the attacker can steal credentials or data, plant malware, or contact them for another malicious intent. One of the most concerning successful phishing examples is also a third‐party one as well: In January of 2019, there was a report of how Russian state threat actors had gained access to the U.S. power grid. They didn't accomplish this by attacking the hardened sites at the power infrastructure operators, but at their suppliers. A phishing campaign targeted the vendors for the power grid operators, taking advantage of the trust relationship they had with the intended target.
Phishing types can include the following:
- Spear phishing: This type is targeted at a specific individual, and isn't a typical mass email campaign to thousands of targets. Often, these specific targets are researched on LinkedIn and other company websites before being phished. There are only so many ways an email address is created (e.g., grasner@ or greg.rasner@ or Gregory.rasner@ and so on). If an attacker can focus on one (or a few targets) who likely has privileged access (i.e., IT Admin, HR Sys Admin, etc.), then they only have to try a few dozen options before they likely get it right.
- Whale phishing: Where do you go to get the best data? To the top! Whale phishing is when attackers target the big fish, such as C‐level or very senior IT/security staff. This phishing type takes a little more finesse than the first two types as many firms are also likely to focus their countermeasures at this team of privileged access users. However, the extra effort can have a larger reward as the attacker gets a level of elevated access that takes a lot longer to attain (and more likely to discover) in a typical security breach.
- Vishing: Rather than email, this type is performed over the telephone and involves social engineering to convince the target it is a legitimate call. The goal is to attain enough information from the call for the attackers to get their target's credentials directly from the call or gain enough information to make guessing it a lot easier.
- Botnets: This cyberattack type is when a network of private computers are infected with malicious software and controlled as a group without the owner's knowledge (e.g., to send spam messages). Kraken, a botnet first discovered in 2008 and on pace to be one of the most successful, has infected over 10 percent of Fortune 500 systems and sends over 500,000 spam emails a day!
- Man‐in‐the‐middle (MitM) attack: Otherwise known as eavesdropping attacks, MitM attacks occur when an attacker is able to insert themselves into a two‐way conversation. When successful, the attacker is then able to filter and steal data from the connection. The most common attack type is via an unsecure, or weakly secured, Wi‐Fi access point; or by installing malware to redirect traffic to a bad actor.
- Denial‐of‐service (DoS) or distributed denial‐of‐service (DDoS): A DoS attack overwhelms or floods a system or network to the point that it makes it unavailable. A DDoS is a case where multiple attackers are performing a DoS. One of the biggest examples of DDoS attack occurred in February 2020 when Amazon Web Services mitigated the biggest such attack recorded to date.
- Brute‐force: When an attacker systematically submits numerous passwords or passphrases until the correct one is found. In 2016, Alibaba was the victim of a successful brute‐force attack that resulted in the loss of 21 million account data records.
- Malware: A term used to describe malicious software and includes worms, ransomware, viruses, spyware/adware, and trojans:
- Worm: A standalone program that replicates itself to spread to other computers. The most famous worm is the Morris Worm (see Chapter 1).
- Ransomware: A type of malware that uses encryption to remove a data owner's access so that the attacker can hold the data hostage until the data's owner pays the ransom. There has been a large growth of ransomware, and most cyber intelligence sources anticipate this growth to continue as a threat in 2021 and beyond. WannaCry was the biggest ransomware event so far, with over 250,000 systems affected, in 150 countries, with an average of $300,000 paid per system, and over 176 types of encryption used.
- Virus: A type of malicious code (or program) written to alter the way a computer operates, and designed to spread from one computer to another. The Mydoom virus is the biggest known virus to date, with an estimated $38 billion damages in 2014.
- Spyware/adware: These include the annoying pop‐up advertisements on search engines, which redirect your search. Some arrive as browser add‐ons purporting to help save money or time. Other instances include being placed as malware on a system or as spyware performing key logging (i.e., the action of recording the keys struck on a keyboard). CoolWebSearch is a browser add‐on that took advantage of security vulnerabilities in Internet Explorer to hijack it, change settings, and send the browsing history to the software publishers.
- Trojan: The most common type of cyberattack, it typically arrives in the form of a legitimate‐looking email asking the reader to perform an update or click a link for something. The malware is then unknowingly downloaded into the target's computer; hence, the name Trojan. Storm Worm, in 2007, is a well‐known type of trojan horse attack. It tricked victims into clicking an email link to an article that downloaded trojan malware. It affected over 1.5 million systems, and is estimated to have cost $10 billion in damages.
Analysis of a Breach
Now that we've covered all the types of cybercrimes, bad actors, and breach threats, let's discuss how a breach is typically carried out. It can be broken down into five main steps: research, intrusion, lateral movement, privilege escalation, and exfiltration. CEO John Chambers once said, “There are two types of companies: Those that have been hacked, and those who don't know yet that they have been hacked.”
Phase 1: Research This phase can begin months before detection. For most attackers, it begins by finding out as much as possible about their target. Searches on LinkedIn and company websites for possible phishing targets are common. Their reconnaissance may include researching who the third parties and affiliates are, locating buildings and Wi‐Fi networks, and discovering information on security systems and any entry points. Like any good attacker, knowing where the target stores its valuables and how they protect them are key components of planning a hack. Once all this intelligence is gathered, the type of tools and methodology can then be determined, and their intrusion can begin.
Phase 2: Intrusion As in the research phase, intrusion can take months before discovery. This phase involves the attacker being focused on breaking into the perimeter of the target, with a persistent foothold being their ultimate goal. Whether they used a phishing campaign to steal credentials or used hacking tools to crack into the network, attackers usually are able to do this and remain nearly invisible to the victim. Once they are inside the network, the attacker will work to ensure their access is long term in the anticipation of revisiting on a regular basis.
The five steps to a breach are shown in Figure 2.3 below.
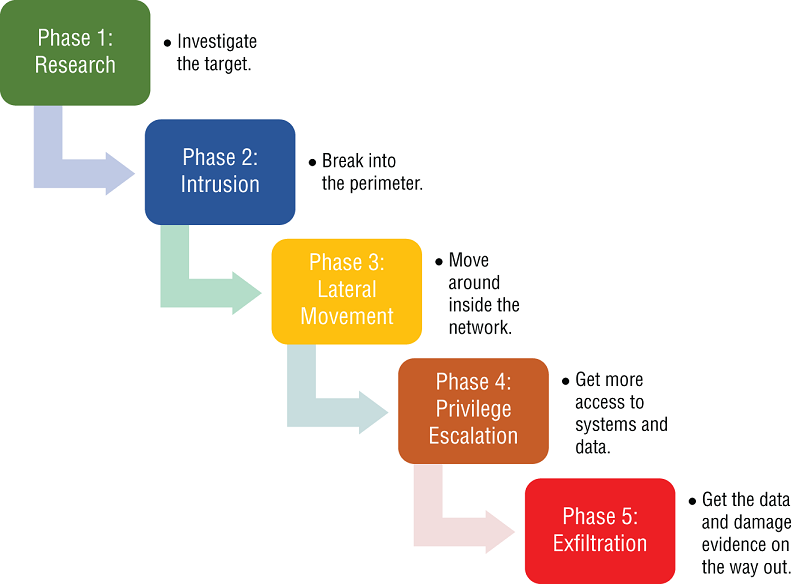
FIGURE 2.3 The Five Steps to a Breach
Phase 3: Lateral Movement After the access becomes more persistent (the attacker has a solid foothold in the target network), the attacker's goal is to find and access more systems within the network. They will search files, databases, password files, sensitive data locations, and network mapping for this work. Most often, the attacker is impersonating an authorized user, so detection is difficult without robust countermeasures such as SIEM and IDS/IPS. This phase generally takes place months or weeks prior to detection.
Phase 4: Privilege Escalation The majority or totality of sensitive information in most company networks is (or should be) protected behind layers of defense that require special access rights. In cases where these user accounts have elevated access, such as in the case of administrators or data owners, this is called Privileged Access. This type of access allows the attacker to get at the data needed, so they must find a way to escalate their initial access. Once this access is obtained, then the attacker will go after their internal targets: sensitive company documents, PII, mail servers, document systems, and other areas.
Phase 5: Exfiltration In this final phase, the attacker is in the home stretch. They have attained the intel necessary, broken into the network, looked around for the stuff to steal, gained access to those systems, and are now ready to steal it. They steal the data, sometimes damaging critical systems used to track their movements and disrupt operations. Some destroy any evidence with a ransomware attack at this point. Some linger in the network, if they think they are not detected, waiting for new opportunities to exploit their access. Once they have reached this stage, it is very difficult to stop the attack and the cost to the company increases the longer it goes undetected.
The Third‐Party Breach Timeline: Target
The discussion of the five phases for a breach can be best demonstrated by using Target as an actual example. In December 2013, it was announced that around 70 million payment card data records for Target's shoppers had been stolen through the point‐of‐sale (POS) system. In addition, over 11 GB of data was exfiltrated. The anatomy of how it occurred illustrates both the vulnerability of third parties and how an attacker goes through the five phases.
Research: HVAC vendors were likely targeted as this third party is used as a backdoor to gain access. An internet search could have produced information about how Target works with its vendors and likely would've shown vendor portals. Also easily found is the Microsoft study done on how Target uses its virtualization software, the MS Domain Name Server (DNS), its software for managing system configurations (Systems Center Configuration Manager [SCCM]), and other important intel about internal systems.
Analysis then shows a phishing email was sent to Target's HVAC vendor, Fazio Mechanical, with malware that was a password‐stealing bot. It is suspected that this software sent stolen credentials to the attackers.
Intrusion: Using the stolen credentials from Fazio Mechanical, attackers logged in to Target's systems via a vendor portal. Because they stole valid credentials, no alarms were sent. This type of credential from the vendor gave them the continuous access to make repeated attempts at the next steps for the breach.
Lateral Movement: Using the valid user credentials and a solid beachhead (i.e., a foothold within the target network), they now could leverage much of their research into what type of systems the target had running internally to the attacker's advantage. Along with their tools for hacking, knowing that they had SCCM and Microsoft's DNS, among other products, would have given them an advantage in looking for vulnerabilities to exploit. In addition, attackers likely would have deployed common network scanning tools to create a map to help them decide the next best steps for the lateral movement.
Privilege Escalation: As attackers moved laterally within the Target environment, the objective would be to find privileges that worked with the POS system. As they exploited these known vulnerabilities on the Microsoft and other systems they had identified in their reconnaissance, intrusion, and lateral movement phases, that data was leveraged to elevate themselves to be able to perform the last step.
Exfiltration: The malware was distributed to the POS machines in such a fashion as to suggest it was an automated update, indicating that the attackers had attained privileged access to the central system that updates those machines. Because the malware was custom written, virus scanners did not have their signature to detect it. As the payment cards were swiped, their data was stored in a system configuration file that was shared over well‐known ports. This data collection from all the different POS machines was then sent to a compromised server internal to Target's network. The data was then retrieved via a number of electronic “drop” locations worldwide. The Target team in India notified the Minneapolis team of the attack, but they took no action on the warning.
The breach itself took place from November 27 to December 15, 2014. Obviously, we do not know how long the research phase took for the attackers. What the timeline does show is how methodical and clever attackers can be when attempting to ambush a victim. In this case, leveraging the available public information not only got attackers access to the vendor portal, but also gave them candidates from the vendors so they could select one with lower access standards. This breach cost Target hundreds of millions of dollars in direct damage, lost revenue, and reputational costs. Many C‐level and lower‐level employees lost their jobs, including the CIO and CEO, while the board of directors was threatened with removal as well.
Inside Look: Home Depot Breach
Occurring in 2014, the attacker in the Home Depot breach used a third‐party's logon credentials to get into that vendor's environment. Once inside the vendor's network, they leveraged a zero‐day exploit for Windows that gained them access to Home Depot's corporate environment. Within the Home Depot network, they deployed memory‐scraping malware to the company's POS systems, resulting in over 50 million credit and debit cards numbers being stolen along with a similar number of email addresses. Valid customer email addresses are a gold mine for phishing attacks. Several studies were done on how Home Depot could have installed IDS/IPS, end‐to‐end encryption, network segmentation, and other technical and process improvements to detect the vulnerabilities exploited by the attackers. Very little is ever mentioned about how a more robust cybersecurity due diligence program would be appropriate for vendors.
This third‐party vendor had a connection to Home Depot. While we have focused most of the discussion on data security, there are vendors who will need to connect to your network to perform their business function. These types of vendors pose risks like the Home Depot incident demonstrates: Their inadequate security controls were the beachhead the hacker needed. Legitimate cases can be made that if Home Depot had better security patterns in its enterprise, the attack might have been either prevented or caught much earlier (they lingered for months). However, if Home Depot had taken our more Cybersecurity Third‐Party Risk approach, the risk of the beachhead being established would have been reduced.
In this updated approach, we want to look at a few items:
- Did Home Depot have language in its contract with this vendor? Did it have:
- Appropriate cybersecurity language in the contract with the vendor who had a direct connection to the Home Depot network?
- Provisions in the contract language allowing Home Depot to perform validation or gain assurance of the vendor security controls?
- A few high‐level questions should have been more diligently reviewed:
- The hardware most vendors maintain at a customer's sites for end‐to‐end connectivity often falls into a no‐man's‐land of who maintains it. If the third party owns it, make sure they do so securely. Did they verify it on a regular basis that is pre‐established with the vendor to set expectations?
- What was their access management policy and how did they enforce it in production? If they had a policy, how did it not catch this activity? Was logging and monitoring insufficient?
- What was the vendor's patch management policy and were they aware of the zero‐day exploit available in the version of Windows?
Notice many of these questions are incident management–type questions a cybersecurity incident management team (CIMT) would typically ask internally. In this case, it is a third‐party risk team asking similar questions of vendors, leveraging language that is written into contracts, and managing their security as an extension of your own.
Conclusion
Cybersecurity, like many technology‐based careers, is complex and typically takes a good deal of training, studying, and immersion in the field to become proficient. The basic cybersecurity triad of Confidentiality, Integrity and Availability can serve as guideposts for any risk discussion around data protection and third parties. Information security focuses on ensuring that data stays restricted to those authorized to access it, protected so it is not altered, and accessible to those permitted to get to access it. Cybersecurity can cover a wide spectrum of activities in most enterprise networks, and will be the basis for how due diligence and due care activities are to be performed in upcoming chapters.
Cybersecurity frameworks provide organizations with guides to how to lower their risk to security incidents. Frameworks to focus on include NIST‐CSF, ISO 27001 and 27002, NIST‐853, Federal Information Security Management Act of 2002 (FISMA), New York Department of Financial Services (NYDFS), and any that are applicable to the industry, country, or region where business is conducted. The adoption and adherence to one or more of these structures informs the customer how the vendor approaches this risk reduction. Speaking to them in their “language” by understanding their framework adoption can ease discussions about gap analysis and remediation steps.
The types of cybercrime and cyber threats are always evolving. Advanced Persistent Threats (APTs) and cybercriminal organizations pose the largest threat to others as they tend to have near infinite time, resources, and energy. The types of attacks are equally varied, but the ones that are most often impactful or seen recently have been phishing and ransomware attacks. Social engineering using fake emails to fool an insider to give away their credentials, or to download malware that encrypts all their files, is often that path of least resistance for a hacker.
Understanding how a breach is performed was broken down into the five steps—research, intrusion, lateral movement, privilege escalation, and exfiltration—and we included a walkthrough of how it was accomplished at Target. The five steps (i.e., phases) illustrated how most of the APTs and cybercriminals approach their work and how the steps are important to when and how a breach can be stopped. If the cybersecurity team's detective work can catch a breach in the intrusion or lateral movement stages, there is a good chance of containing the effects with minimal damage and data loss. However, if their detection isn't until the exfiltration phase (which is often when detection occurs as the damage the hackers have done becomes known), then there's zero chance to stop the loss of data and damage. This is why cybersecurity professionals push tools like as IDS/IPS and DLP, among others, to amp up the detection capability.
