As VMware’s preferred public cloud provider, AVS supports vSphere workloads in the Azure Cloud. In VMware and Microsoft’s hybrid cloud solution, customers can move to the cloud and modernize their applications quickly and easily, enabling faster time-to-market and innovation.
AVS solutions enable cloud consumers to accelerate adoption of the cloud without the burden of having to reformat existing assets for the cloud. The Azure VMware Solution makes it possible to run cloud consumers’ VMware technology stacks on Azure as if it were on-premises, so no app refactoring or different skillsets are needed.
AVS delivers scalable processing and high throughput networking with low latency. Cloud consumers can migrate datacenters to the cloud to easily deploy rapid data center evacuation, disaster recovery, and application modernization.
Overview of AVS
Key elements of AVS
Compute overview of Azure VMware Solutions
Storage overview of Azure VMware Solutions
Network overview of Azure VMware Solutions
AVS workload and application mobility
AVS management and operations
AVS security
Overview of Azure VMware Solutions
The Microsoft Azure VMware solution combines VMware’s proven enterprise-grade software defined datacenter with elasticity, flexibility, and the global presence of the Azure Cloud. Combining these technologies allows users to standardize on-premises and on-cloud infrastructures. Cloud consumers do not need to make modifications or refactor workloads to migrate.

An illustration depicts an overview of Azure V M ware solution which is a low cost of Microsoft Applications in terms of business view, Simplified Multi Environment Operations for administrator, and Faster delivery of modern applications which helps developers.
Overview of Azure VMware Solution
If an organization utilizes Windows Server or SQL Server, Microsoft has specific cost savings for AVS to incentivize businesses to adopt the technology. These include free security updates for Windows Server 2008 r2 and SQL Server 2008 r2 for four years beyond the end-of-the-extended-support date for these products. Extended security updates typically cost around 75-125% of the base software license cost per year, making running legacy Microsoft platforms on the cloud prohibitively expensive.
VMware on-premises does not receive the same service. It does not provide free security updates. If IT organizations want to stay as secure as possible, they must update security. According to Microsoft, the extended security updates for SQL Server 2012 r2 and Windows Server 2012 r2 will be provided free of charge by Azure and AVS. The Azure hybrid benefit program also allows customers to bring their existing Windows Server and SQL Server licenses with software insurance to Azure and AVS after their extended support dates in 2022 and 2023. Microsoft licensing costs are reduced by 40% due to this. For Windows and SQL Server licenses purchased after October 2019, no other VMware hyperscale service lets you bring your own licensing options.
As part of AVS, Microsoft also allows the deployment of downloadable Office 365 and VDI desktops. Other non-Microsoft VMware hyperscale services cannot run downloadable Office 365 applications that integrate Microsoft tools. AVS subscriptions are managed by the Azure portal, which uses Azure credits to purchase AVS. The portal also simplifies initial and day-to-day operations for administrators. The Azure portal provides integrated audit logging alerting, metrics management, and a unified Azure services bill included as an Azure Resource Manager template.
With Azure Monitor for application developers, developers can also modernize existing vSphere applications with Azure’s IoT services and develop and deploy applications via Azure APIs. Developers have access to all Azure services, including AVS, through a single pane of glass because of VMware’s SDDC and vCenter integration with Azure. Utilizing Azure services from within the AVS SDDC environment is also more accessible and secure by integrating VMware and Azure identity management.
You might be asking yourself, well, that’s all great information, but what is Azure VMware Solution?

An illustration depicts the workings of Azure in terms of On Premises Datacenter and Azure cloud. On Premises Datacenter has elements, v Center, v m, v Sphere, v S A N, N S X, and third party D R. Cloud has Azure portal and Azure resource manager, classified into Azure private cloud infra, Azure backbone network, and Azure native services.
Azure VMware Solution logical view
With vSAN storage, AVS hosts can scale performance and reliability as they add more hosts. NSX-T offers software-defined networking in the AVS private cloud for easy interoperability with on-premises networks. The AVS private cloud hosts vCenter, which is used to manage VMware components.
Cloud datacenters with VMware AVS are located in more countries than any other cloud service offered by VMware. At the time of writing, 20 of the more than 60 regions of Azure offer Microsoft’s AVS service.
Azure is continually adding new AVS regions. AVS’s broad geographic coverage is essential for cloud consumers to ensure compliance with data sovereignty regulations. Microsoft and VMware have committed to delivering cloud services that follow industry best practices for security and compliance. In addition to adhering to rigorous security standards, each company also extends its coverage to specific industries.
In Azure Cloud, VMware Solutions offers bare metal and hypervisor access and administrative access to vCenter, NSX-T, and many more add-on services. The VMware environment deployed in Azure Cloud possesses the same control, security, and functionality as its on-premises counterpart. As an entirely native VMware environment, AVS does not require any modifications to existing tools or processes. It is only accessed through the cloud.
Microsoft and VMware have created solutions based on VMware Cloud foundation solutions to address the concern that security is one of the biggest reasons for hesitation in cloud adoption. AVS VCF runs in a single, dedicated environment, eliminating “noisy neighbors” and data corruption.
The VMware hardware attestation for Microsoft Azure enables workloads to run on trusted servers with role-based access and Intel TXT, which provides encryption at the chip level. The Azure Virtual Compute Facility includes leading-edge security solutions. Clients who access hypervisors and bare metal can use the technical, business, and personnel controls to meet compliance and auditing requirements.
Take advantage of the global Azure infrastructure to get continuity, speed, and scale for VMware workloads
Utilize their existing VMware investments, skills, and tools, including VMware VCF, vSphere, vSAN, vCenter, and other providers’ tools
Take advantage of the data locality in the Azure cloud to seamlessly migrate apps to Azure-native management, security, and services
Enjoy unmatched Windows and SQL Server pricing

An illustration of Azure V M ware solution use cases indicates application modernization, cloud migration, data center extension, cloud virtual desktops, and disaster recovery. Each element has its respective icon representations at the top.
Azure VMware Solution use cases
Use case 1: Modernizing applications is simplified if migrated to AVS. Workloads can be incrementally refactored to cloud-native standards using SaaS, PaaS, the Azure Kubernetes service, or directly on AVS with its support. You can enable True Hybrid capabilities, such as streamlining DevOps across VMware and Azure. You can optimize and standardize VMware administration for Azure services and solutions applicable to all cloud customers’ workloads. You can access public cloud services without expanding cloud consumers’ datacenters or reengineering cloud consumers’ applications. Azure VMware Solution helps cloud consumers identify and access control policies and log and monitor them.
Use case 2: Cloud customers who need to move to the cloud from CapEx to OpEx or aging hardware. In the past, IT expenses were primarily CapEx, including outright purchases of hardware and software and maintenance equipment. Business owners who buy these items outright have total ownership of their systems, but this comes at a cost. The problem with CapEx purchases in IT is that they often become outdated before they have time to pay for themselves, so the initial investment isn’t always recouped before the further expense is incurred.
Over the last decade, businesses have steadily reduced their IT CapEx in favor of operating expenses such as cloud services.
Use case 3: The data center extension needs extra capacity or retains Windows Server and SQL Server software beyond the end-of-support dates. Customers would need to pay prohibitive prices to Microsoft to receive security updates to stay on premises.
Use case 4: Desktop virtualization in the cloud was a significant use case for AVS during the COVID 19 pandemic when customers needed to rapidly expand support for remote workers. AVS came to the rescue with its support for VMware horizon virtual desktops that customers could run on a native VMware platform and manage as an extension of their on-premises horizon infrastructure horizon on AVS.
Use case 5: AVS supports DR solutions to protect customers’ on-premises workloads. AVS gives customers the option of replacing their off-premises DR sites with Azure VMware Solution. This solution provides the same level of reliability and testability as VMware on-premises solutions. Increasing cyber threats and natural disasters have made maintaining uptime a necessity for cloud consumers. It is now imperative that Microsoft and VMware have a resiliency strategy. Customers can reduce downtime with three resiliency tools: VMware HCX, JetStream Disaster Recovery, and Zerto (disaster recovery).
Key Elements of Azure VMware Solutions
Let’s discuss a deployment overview for AVS and what is deployed in a private cloud. The steps for deploying Azure VMWare Solutions to deliver VMWare-based private clouds within Microsoft Azure will be described in this section. Microsoft Azure’s private cloud hardware and software deployments are fully integrated and automated.

An illustration of private cloud integrated view of Azure V M ware solution. It has Microsoft Azure subscriptions of Microsoft Azure Region and Microsoft Azure Resource Group where the components of A V S Private Cloud connect to D M S E E, to E R Gateway, then to Cloud Consumers Resource Group.
Azure VMware Solution private cloud integrated view
The Azure VMware Solution combines VMware compute, networking, and storage running on bare metal hosts within Microsoft Azure.
Here’s a quick view of Azure core components.
Azure subscriptions: Subscriptions are a billing boundary in Azure. To deploy any Azure resource, a user needs a valid subscription. Subscriptions associated with Microsoft Enterprise Agreements or Cloud Solution Provider Azure plans support Azure VMware Solution.
Azure regions: Azure regions are collections of datacenters linked by a dedicated, low-latency network that hosts Azure services. Azure services are not available in all regions.
Azure resource groups: The purpose of a resource group is to simplify the management of multiple Azure resources by grouping them into one container object. All resources within the group can be affected by policies and lifecycle actions.
Azure VNets and virtual network gateway: Private networks within Azure are built using Azure virtual networks. Azure VNets allow resources to securely communicate with each other, the Internet, and on-premises resources. Virtual network gateways allow routes to be exchanged between VNets.
Azure ExpressRoute: Microsoft Azure ExpressRoute circuits enable private connections to its global backbone. Through an ExpressRoute connectivity provider, a customer can connect to an ExpressRoute location and access all regions within a particular geopolitical region.
VMware vSphere
VMware vSAN
VMware NSX-T
VMware HCX

An illustration depicts the core components of the V M ware solution which are V N ware v Sphere, V M ware v S A N, V M ware N S X T, and V M ware H C X. Each component has its respective logos at the top.
Azure VMware Solution – VMware core components
AVS core capabilities are provided by VMware vSphere, VMware vCenter, VMware vSAN, VMware NSX-T, and VMware HCX. The core capabilities of VMware products that have been certified with AVS can be extended with VMware services. Virtual machines can be migrated to AVS using VMware HCX.
vRealize portfolio products can manage, monitor, and automate AVS, VMware SD-WAN and NSX Advanced Load Balancer. Tanzu Kubernetes Grid, Tanzu Mission Control, and VMware Tanzu Standard provide a platform for application modernization, presenting consistent Kubernetes runtime and management capabilities.
The virtual desktop solution supported by AVS is VMware Horizon. The primary disaster recovery solution for the cloud is VMware Site Recovery Manager. Horizon Cloud on Azure is another option, a separate solution that offers Horizon as a service SaaS on Azure.
In AVS, the CloudAdmin role is assigned to a local user called CloudAdmin. This role provides access to manage the environment. It does not have access to Microsoft-specific management components, such as ESXi hosts, clusters, and datastores. Active Directory users and groups can be assigned the CloudAdmin role using the CloudAdmin user.
HCX Advanced is deployed by default for no additional charge. HCX Enterprise can be upgraded through a support ticket with Microsoft. HCX offers many benefits over HCX Advanced, such as scheduled bulk migrations between on-premises and AVS.
When the AVS private cloud is provisioned, an ExpressRoute circuit is created, connecting it to the Microsoft dedicated Enterprise Edge routers, allowing access to Azure services. An ExpressRoute gateway enables AVS to connect to existing Azure VNets. AVS private clouds should be connected to on-premises datacenters via ExpressRoute Global Reach. Site-to-site VPN connections can be used without an ExpressRoute connection between the datacenter on-premises and Azure.
Subscription
Resource group
Subscription contributor
Network
An illustration of pre requisites of cloud deployment which are subscription, resource group, subscription contributor, and networks. Each element has its respective icons at the top.
Azure VMware Solution private cloud deployment prerequisites
It is necessary to identify several things before deploying the private cloud object in Microsoft AVS Solution. Cloud consumers must place a subscription into which they want AVS to be deployed; they can use an existing subscription if that subscription is associated with an enterprise agreement (EA) or cloud solution provider plan (CSP), or create a new one.
Next, they must identify a resource group. Generally, AVS administrators can create a new resource group for AVS and related resources. Alternatively, AVS administrators can use an existing resource group. It is also necessary for AVS administrators to identify the administrator who will enable and deploy the private cloud. They should assign this individual the role of Contributor.
AVS architects need to think about network requirements. AVS administrators require a slash 22 network for AVS deployment, divided into smaller subnets for vCenter Next, VMotion, and HCX. This block should not overlap with any existing cloud consumers’ network segment on-premises. Azure, and a VNet defined connect AVS into if cloud consumers generally want to connect to Azure native services.
AVS administrators must create a virtual network that hosts the jump box to access the private cloud from Azure. For workload VMs defined in NSX-T post-deployment, AVS administrators also need to identify one or more network segments.
HCX might need some on-premises segments to be created after deployment if cloud consumers want to use HCX for migrations and network extension.
In addition, AVS administrators should determine whether cloud consumers are connecting via a VPN or an Express route and adjust the configuration accordingly. Most enterprise customers will use the Express route, but a VPN is also supported. Administrators must also configure firewall rules to access on-premises resources from AVS or to access AVS from on-premises.
Compute Overview of Azure VMware Solutions
Azure is a platform of choice for companies because of its computing services. Applications and services can be hosted on Azure. Azure compute provides the infrastructure needed to run cloud consumer applications. You can take advantage of compute capacity in the cloud and scale as needed. Cloud consumer applications can be containerized, Windows and Linux VMs can be deployed, and VMs can be migrated to Azure with flexibility. Cloud consumers can deploy where and how they want with comprehensive support for hybrid environments. In addition, Azure compute includes a full-featured identity solution, so cloud consumers can benefit from managed end-point protection and Active Directory support to secure access to on-premises and cloud applications. Pay-as-you-go and Azure Hybrid Benefits enable you to deploy apps and save.
Computing Services Provided by Azure
Name of Services | Service Function |
|---|---|
Azure Virtual Machine | Windows or Linux VM hosted in Azure |
Azure Virtual Machine Scale Sets | With autoscaling, cloud consumers can create thousands of VMs in minutes while maintaining high availability. |
Azure Spot Instances | Provision unused compute capacity for cloud consumers workloads to get deep discounts |
Azure Functions | An event-driven and serverless compute service |
VM Hosted on Azure VMware Solution | VMs running in dedicated host provisioned and isolated from other tenants running in Azure VMware Solution |
App Services | Providing managed hosting services for web applications, mobile apps, REST APIs, or automated business processes |
Azure Spring Cloud | Host Spring Boot apps with a managed service |
Azure Kubernetes Services | Containerized applications running on Kubernetes |
Batch | The execution of large-scale parallel and high-performance computing applications (HPC) via a managed service |
Container Instances | This is the most straightforward way to run a container in Azure without creating any virtual machines and without having to adopt a higher-level service. |
Azure Dedicated Host | Using physical servers only for cloud consumers to deploy virtual machines or containers for cloud consumers |
Physical servers that the Azure Dedicated Host provides host Azure virtual machines. Azure’s physical cloud servers are dedicated to each organization and workload, and capacity isn’t shared with other tenants. Compliance requirements are met as a result of this host-level isolation. In provisioning the host, cloud consumers gain visibility into and control over the placement of their VMs and can define the host’s maintenance policies.
The AVS administrator should deploy at least three virtual machines on various hosts to ensure high availability. Cloud consumers can choose from several Azure Dedicated Host options to customize their fault isolation boundaries with cloud infrastructure.
Within an Azure region, availability zones are unique physical locations, and datacenters within each zone are outfitted with independent power, cooling, and networking. All hosts in a host group will be placed within a single availability zone once the group is created. Cloud consumers need to create multiple host groups (one per zone) and spread their hosts accordingly to achieve high availability across zones.
All VMs created on that host must be created in the same availability zone if a cloud consumer assigns a host group to a zone. It is possible to create hosts in specific fault domains. Hosts in different fault domains will be placed on other physical racks in the data center as they are with VMs in a scale set or availability set. Cloud consumers must specify the fault domain count when creating host groups. When creating hosts within a host group, a cloud consumer assigns a fault domain to each host. A fault domain is not assigned to VMs.
Fault domains are not the same as colocation, and two hosts sharing the same fault domain do not necessarily mean they are near each other. A fault domain is scoped to a host group. The cloud consumer should avoid assuming anti-affinity between two host groups (unless they are in different availability zones). A VM running on a host with a different fault domain will have its managed disk services deployed on multiple storage stamps to increase fault isolation.
The cloud consumer can combine both capabilities to achieve even more fault isolation. Cloud consumers specify the availability zones and fault domains for each group of hosts, assign a fault domain to each host in the group, and assign availability zones to each VM.
A hosted Azure Dedicated Host supports Azure standard HDDs, standard SSDs, and premium SSDs at the time of writing this book.
AVS compute perspective: Resources made up of physical hosts and clusters with processors, memory, and I/O interfaces.

An illustration depicts the core computers of V M ware solutions which are V M ware v Center Server, E S X i, and V M. Each element has its respective icons at the top.
Azure VMware Solution – core compute
A host, where a VMware ESXi hypervisor is installed on bare metal
Private clouds can be provisioned or reserved on the host.
Azure provides the service in the region.
From provisioned nodes, cloud consumers create their own private cloud. The minimum number of nodes needed for a private cloud is three of the same SKU. Adding additional nodes expands the private cloud. Administrators can add nodes to an existing cluster through the Azure portal or create a new cluster.
By paying with a credit card, cloud consumers subscribe to Azure immediately.
They will be billed for Azure the following month.
In addition to bare-metal server hosts for the vSphere clusters, vCenter Server, NSX-T, and vSAN, AVS private clouds offer various Azure underlay resources that are required for connectivity/operation. There is a default limit of one AVS private cloud per subscription, but this can be scaled through a support ticket.
AV36 Host Configuration
Components | Configuration |
|---|---|
Instance size | AV36 |
Processor type | Dual Intel Xeon Gold 6140 @2.3 GHZ | 18 Cores, HT enabled |
Core(s) | 36 |
RAM | 576GB (50.15GB reserved) |
ESXi minimum version | 6.7 U3 P05 |
ESXi edition | Enterprise Plus |
vCenter minimum version | 6.7 U3 |
Clusters per private cloud | 12 |
Minimum hosts per cluster | 3 |
Maximum hosts per cluster | 16 |
Maximum hosts per private cloud | 96 |
vCenter per private cloud | 1 |
vSAN capacity limit | 75% of total usable space |
Cache | 2 *1.6 TB NVMe |
Capacity | 8 *1.92 TB SSD |
All flash storage | 15.36 TB |
NVMe cache | 3.2 TB |
vSAN minimum version | 6.7 P05 |
vSAN minimum edition | Enterprise |
Network interface card (uplink) | 2 x Dual port 25 GbE |
Host Max Configuration for CPU, RAM, and Storage
Host | CPU | RAM | Storage |
|---|---|---|---|
3 | 108 | 1.5 TB | 46 TB |
8 | 288 | 4 TB | 122 TB |
16 | 576 | 8 TB | 245 TB |
32 | 1,152 | 16 TB | 491 TB |
64 | 2,304 | 32 TB | 983 TB |
96 | 3,456 | 49 TB | 1.4 TB |
Storage Overview of Azure VMware Solutions
Durability: In a hardware failure, redundancy will ensure the safety of cloud consumers’ data. Cloud consumers can also replicate data across datacenters or geographical regions to protect against local catastrophes or natural disasters. If a disaster hits, the replicated data will remain reliable.
Secure: Azure Storage accounts are encrypted when data is written to them. Azure Storage lets cloud consumers control who can access their data at fine-grained levels.
Scalable: Azure Storage is designed to be massively scalable to meet today’s performance and data storage needs.
Managed: Cloud consumers can rely on Azure for hardware maintenance, updates, and critical issues.
Accessible: Over HTTP or HTTPS, Azure Storage data can be accessed from anywhere globally. .NET, Java, Node.js, Python, PHP, Ruby, Go, and others provide Azure Storage client libraries, as well as a mature REST API. Azure Storage supports scripting in Azure PowerShell or Azure CLI. And the Azure portal and Azure Storage Explorer provide easy visual solutions to work with data in the cloud.
VMware vSAN is used by default as cluster-wide storage in Azure VMware Solutions private clouds by AVS. Host storage is used in a vSAN datastore, and information at rest is encrypted by default. Azure Storage resources can be utilized to extend the storage capabilities of cloud consumers’ private clouds.
Azure Storage resource such as Blob Storage, File Sync, Azure Files, Azure Netapp Files, and Azure Disk Poo can be integrated with AVS as well.
AVS Storage perspective: Resources made up of high-performance local disks based on the best RAID configuration.

An illustration depicts the core storage of V M ware which are V M ware v S A N, Blob Storage, Azure Files, Azure Net App Files, File Syncs, and Azure Disk Pool.
Azure VMware Solution – core storage
Azure Storage Functions
Name of Services | Service Function |
|---|---|
Blob Storage | A massively scalable object store for binary and text data. Blob Storage's archive tier has the lowest possible cost. Offline data might need to be copied to a Cool, Hot, or Premium tier to enable access. A Cool tier provides low-cost, instant access to offline data. |
Azure Files | Using Azure Files, users can manage native SMB file shares without running virtual machines. Any Azure virtual machine or on-premises computer can mount an Azure Files share as a network drive. |
Azure NetApp Files | Metered Azure NetApp Files is a high-performance service that offers enterprise-class performance. Across all workload types, Azure NetApp Files is highly available by default. Service and performance levels can be selected, and this service can set up snapshots. |
File Sync | File Sync in Azure Files allows cloud consumers to centralize their file shares. File Sync from Azure offers the same flexibility, performance, and compatibility as an on-premises file server. |
Azure Disk Pool | Azure disk storage offers high-performance, persistent block storage to power Azure VMs. Azure Disk Pool provides the industry's only single-instance service-level agreement (SLA) for virtual machines running on Premium SSD or Ultra Disk Storage. Customers can have high availability using Azure disks with availability zones and Azure VM fault domains. |
Azure Databox | Applications and solutions for transferring data to Azure and edge computing |
Azure Data Lake Storage | For high-performance analytics workloads, a scalable and secure data lake |

An illustration depicts the architecture of the v S A N storage platform. The elements in the blocks are labeled as A V 36, N V M e, S S D, and Capacity respectively.
Azure VMware Solution – vSAN storage
Virtual storage area networks (vSANs) are hypervisor-converged, meaning storage, compute, and management are delivered from the same x86 server platform running the hypervisor. The VMware stack is fully integrated. Provisioning of VM storage and management of storage SLAs can be controlled by VM-level policies that can be set and modified on demand. Cluster-wide vSAN datastores use local storage in each host, and data-at-rest encryption is enabled by default.
vSAN datastores are built using local storage on each cluster host. With a raw, SSD-based capacity of 15.4TB per host, all disk groups include an NVMe cache tier of 1.6TB. A cluster’s raw capacity tier equals the per-host capacity multiplied by the number of hosts. For example, in the vSAN capacity tier, four hosts provide 61.6TB of raw capacity.
Datastore.AllocateSpace
Datastore.Browse
Datastore.Config
Datastore.DeleteFile
Datastore.file management
Datastore.UpdateVirtualMachineMetadata
VMware vSAN is used as storage in Azure VMware Solution. VMware vSAN is a distributed, object-based file system software layer that runs natively in the ESXi hypervisor. vSAN aggregates a host cluster’s local or direct-attached capacity devices into a unified storage pool shared by all hosts in the cluster.
Virtual machines are stored according to storage policies in vSAN. These policies determine how virtual machine storage objects within a datastore are provisioned and allocated to guarantee a certain level of service.
On a host cluster, vSAN is enabled by creating a single vSAN datastore using disks from all participating hosts, and it is assigned a default storage policy.
Default storage policies for the private cloud cluster include RAID-1 (mirroring), FTT-1 (failure to tolerate), and thick provisioning. With this configuration, the cluster continues to grow unless the storage policy is changed. FTT-1 accommodates a single host failure in a three-host cluster.
The FTT-1 protocol accommodates the failure of a single host in a cluster of three hosts. Microsoft monitors failures regularly and replaces hardware when necessary from an architecture perspective.
Administrators who are uncertain if the cluster will expand to four or more should deploy using the default policy. Microsoft recommends expanding a cluster after initial deployment if you are certain that the cluster will grow. In the VM settings, change the disk’s storage policy to either RAID-5 FTT-1 or RAID-6 FTT-2 when the VMs are deployed to the cluster.
vSAN storage policies determine the performance and availability of the provisioned storage. RAID-1 FTT1-1 is the fastest but uses the most storage and RAID 5 FTT-1 is fast and more space efficient while RAID-6 FTT-2 is the most available and space efficient but can be slower in large sequential reads from disk.
Azure VMware Solution provisioning types are classified into two categories:
Thick: Space that has been assigned, fully provisioned, or reserved in advance. The system is protected because the space on the vSAN datastore is already reserved, even if it is full. An AVS administrator can create a 10GB virtual disk with thick provisioning. A virtual disk’s total storage capacity is preallocated on its physical storage, which consumes all of the datastore’s space. A VM can’t share the datastore space with another VM.
Thin: Consumes the space it needs initially and then grows to match the data space demand used by its datastore. AVS administrators can create VMs instead of thick provisioning (outside of the default). The cloud consumer’s VM template should use thin provisioning for a deduplication setup. This can be used when capacity growth projections are uncertain.
Data-at-rest encryption : Data-at-rest encryption is enabled by default in vSAN datastores using keys stored in Azure Key Vault. For key management, the encryption solution utilizes Azure KMS. The data on SSDs is invalidated immediately when a host is removed from a cluster.
Cloud administrators can use Azure Storage services within their private clouds. Storage accounts, table storage, and blob storage are among the storage services. Azure Storage services aren’t connected via the Internet to the workloads. Cloud consumers can use SLA-based Azure storage services on their private clouds with this connectivity.
VMs deployed in AVS can access native Azure Storage services such as storage accounts and blob storage.
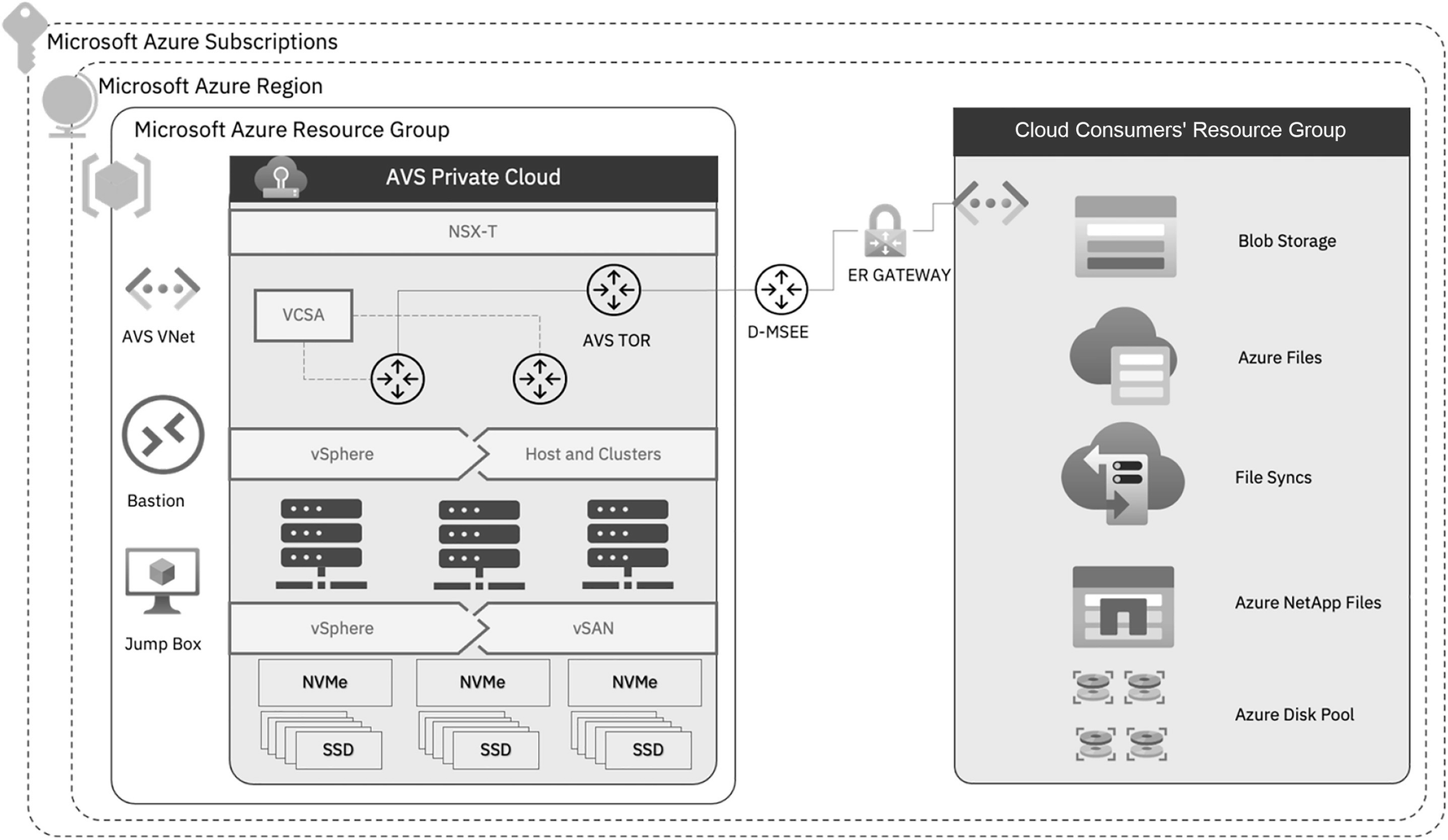
An illustration of private cloud integrated view of Azure V M ware solution. It has Microsoft Azure subscriptions of Microsoft Azure Region and Microsoft Azure Resource Group where the components of A V S Private Cloud connect to D M S E E, to E R Gateway, then to Cloud Consumers Resource Group.
Azure VMware Solution – native storage intgrated view
The Azure backbone provides high-speed, low-latency private and secure connectivity and enables cloud consumers to use SLA-based Azure Storage services in their private cloud workloads.
Microsoft has a cloud-based object storage solution called Azure Blob Storage. Massive amounts of unstructured data are best stored in blob storage. Unstructured data, such as text or binary data, does not conform to a particular model or definition.
VMs and data can be stored in Azure Blob Storage, enabling enterprise-grade DR at a reduced cost of operation.
Azure Blob Storage is more than just a journal or “cold data tier” and can be used as a repository for all VMs, data, configuration metadata, and recovery policies.
Azure Files provides cloud-hosted file shares accessible with the Server Message Block (SMB) or Network File System (NFS) protocols. Using an AVS private cloud, Azure Files file shares can be mounted concurrently. NFS shares can be mapped to VMs within AVS.
Windows, Linux, and macOS clients can access SMB Azure file shares. NFS files can be accessed using Linux or macOS clients. Moreover, SMB Azure file shares can be cached on Windows Servers using Azure File Sync for fast data access near where the data is needed.
Using Azure VMware Solutions and Azure Files simultaneously, users can realize a vSphere-based cloud solution without replatforming, changing IP addresses, or changing architecture. Furthermore, the vSphere storage footprint will shrink, but the file server hierarchy, security, and available files will remain the same.
Syncing all files to Azure File Storage is accomplished by installing Azure FileSync on the file servers before migrating to AVS. When files are needed, they are pulled down to the file server and kept there for a predetermined period, after which they are removed so that space is freed.
Azure NetApp Files is an Azure service for migration and running enterprise file systems in the cloud: databases, SAP, and high-performance computing applications without modifying code. Azure VMware Solution workloads can access an Azure NetApp Files volume using the NFS protocol. VMs run the guest operating system and access Azure NetApp Files volumes.
You can attach Azure VMware Solution disk pools to AVS ESXi hosts. AVS administrators can utilize disk storage for Azure VMware Solutions for optimal performance and cost; at the time of writing, this is in preview.
Applications and workloads backed by Azure Disks can access persistent block storage through Azure disk pools. Whenever the capacity consumption reaches 75%, Microsoft sends an alert. Moreover, AVS administrators have access to capacity consumption metrics that are integrated with Azure Monitor.
Network Overview of Azure VMware Solutions
With Azure virtual networks, Azure resources such as virtual machines, web apps, and databases can communicate with each other and with users on the Internet and with cloud clients on-premises. Azure networks are resources that are used to link Azure resources.
Consumers of cloud services can create multiple isolated virtual networks by using virtual networks. Cloud consumers can use public or private IP address ranges to define a private IP address space. Cloud consumers can allocate each subnet part of the defined address space.
For name resolution, cloud consumers can use the name resolution service built into Azure. Users of the cloud can also configure their virtual networks to use either an internal or external DNS server.
Azure VMs are automatically connected to the Internet. Incoming connections to the cloud can be enabled via public IP addresses or public load balancers. Cloud consumers can connect via the Azure CLI, Remote Desktop Protocol, or Secure Shell for VM management.
Azure virtual networks connect VMs and other Azure resources, including Azure Kubernetes Service, App Service Environment for Power Apps, and Azure virtual machine scale sets.
Connecting to other Azure resource types, including Azure SQL databases and storage accounts, is also possible via service endpoints. Users can use this approach to link multiple Azure resources to virtual networks to improve security and optimize routing between resources.
Point-to-site VPN: A typical virtual private network connection is from a PC outside the cloud consumer’s organization back into the cloud consumer’s corporate network. Connecting the client computer to the Azure virtual network is achieved by initiating an encrypted VPN connection.
Site-to-site VPN: A site-to-site VPN links your on-premises VPN device or gateway to the Azure VPN gateway as part of a virtual network. A device in Azure can appear as if it is on a local network. Connectivity over the Internet is encrypted.
ExpressRoute: Azure ExpressRoute is the perfect solution for environments where cloud consumers require higher bandwidth and increased security. Azure ExpressRoute provides dedicated private connectivity without going over the Internet.
Route table: Defining routes in a route table allows cloud consumers to control how traffic should be directed. Cloud consumers can create their own route tables that control how packets are routed between subnets.
Border Gateway Protocol (BGP): With the BGP, on-premises BGP routes can be propagated to Azure virtual networks using Azure VPN gateways or ExpressRoute.
Network security groups: Azure network security groups contain multiple security rules for inbound and outbound connections. The cloud consumer can define rules based on source and destination IP addresses, ports, and protocols to allow or block traffic.
Network virtual appliances: Compared to a hardened network appliance, a network virtual appliance is a specialized VM. A network virtual appliance performs a specific network function, such as managing a firewall or optimizing wide area networks (WANs).
Virtual network peering allows cloud consumers to connect virtual networks. Peering allows resources within virtual networks to communicate with one another. With Azure, cloud consumers can create a global interconnected network with these virtual networks located in different regions.
Users can define routing using UDR, and UDR is a major upgrade to Azure’s virtual networks. Administrators can control routing tables between subnets within a VNet and between VNets, allowing them to better control network traffic.
Networks are provided as a service, but they are not free. Public IP addresses, global/regional peering, and inbound/outbound data transfers between availability zones cost money. Although nominal, the cost is not free. However, transferring data between resources within the same virtual network is free. Managing, planning, and calculating subscription costs are essential for operating an Azure subscription.
When cloud consumers deploy to Azure, they must consider some significant configuration activities. The basic capabilities deployed in an Azure datacenter are provided by network connectivity, firewalls, DMZs, and other networking devices and configurations.
A lot depends on the solution’s requirements being created or migrated to Azure. In a typical design, the following components are present: inbound and outbound port/firewall rules, network security groups, enabling security via Azure Security Center, and other load balancing rules.
Azure’s Key Networking Services
Name of Service | Service Function |
|---|---|
Azure Protection Services | Protects cloud-based applications using Azure’s network services: load balancing, private links, DDoS protection, firewalls, group security policies, web application firewalls, and virtual network endpoints |
Azure Connectivity Services | The following Azure networking services can be used with on-premises resources: virtual networks (VNets), virtual WANs, ExpressRoute, VPN gateways, virtual network NAT gateways, Azure DNS, peering services, and Azure Bastion. |
Azure Delivery Services | Using any of these or a combination of these Azure networking services, cloud consumers can deliver applications in the cloud: Content Delivery Network (CDN), Azure Front Door Service, Traffic Manager, Application Gateway, Internet Analyzer, and Load Balancer. |
Azure Networking Services | Utilize any of these networking services in Azure to monitor cloud consumers’ network resources: Network Watcher, ExpressRoute Monitor, Azure Monitor, and VNet Terminal Access Point (TAP). |
Network: Resources made up of physical and logical network connectivity, including virtualized security solutions based on VMware NSX-T.
Key Networking Terminologies
Terminologies | Descriptions |
|---|---|
Subscription | Microsoft subscriptions entitle users to use one or more cloud platforms or services. |
Virtual network (VNet) | Fundamental building block for a cloud consumer’s private network in Azure. Connects VMs to an incoming VPN connection. |
ExpressRoute | Private connections between Azure datacenters and infrastructure on cloud consumers’ premises or in a colocation environment |
Microsoft Enterprise Edge (MSEE) | High availability with two routers in an Active/Active configuration. Routers that connect directly to a datacenter allow connectivity providers to connect their circuits. |
Virtual network gateways – VPN or ER | VPN connection between an Azure virtual network and an on-premises network Connects Azure virtual networks to on-premises networks via ExpressRoute |
Azure Firewall | Deploys a high-security, high-availability firewall with unlimited scalability |
Azure Virtual WAN | Develops a unified WAN, connecting local and remote sites |
Azure Network Watcher | Monitors and diagnoses conditions on a network scenario basis |
An illustration depicts Azure network connectivity components. The components are Azure Express Route, Site to Site V P N, and Azure Virtual W A N.
Azure VMware Solution – core network connectivity
AVS private clouds come preconfigured with NSX-T networking and connectivity. The on-premises deployment of NSX-T is not required. Active-Active is the mode used by the t0 gateway, and the t1 gateway uses Active-Standby. Cloud gateways let cloud consumers connect network segments with logical virtual switches and provide east-west and north-south connectivity.
The NSX-T objects can then be configured within the Azure portal once the AVS cloud is deployed. Azure VMware administrators have a simplified view of NSX-T operations that they might use daily.
Component 1: Segments. Azure administrators can create network segments that display in the NSX-T manager and vCenter.
Component 2: DHCP. If the Azure VMware administrator intends to use DHCP to provide addresses to AVS workloads, they can create a DHCP server or DHCP relay.
Component 3: A VMware administrator can set up port mirroring in Azure to help troubleshoot network problems.
Component 4: A DNS VMware administrator can create and manage DNS forwarders to send DNS requests to designated DNS servers for resolution.
In addition, Azure VMware administrators retain access to the NSX-T management console to use advanced settings and other NSX-T features such as configuring routing firewalls and micro-segmentation.

An illustration depicts the backbone integrated view of Azure Subscriptions. It has Azure Services with different tools, Azure backbone, and A V S with Azure V M ware Solution, N S X T Network Segments of v Center, H C X, N S X, E S X i, and v S A N, and Azure Bare Metal dedicated infrastructure.
Azure VMware Solution – backbone integrated view
From VMs in cloud consumers’ Azure subscriptions, inbound access to vCenter Server and NSX-T manager is available.
Private clouds can access Azure’s services outbound.
They can also pass workloads inbound to Azure.
Azure VMware Solution can be integrated with on-premises datacenters and Azure virtual networks. Let’s take look at the options. The bare metal hosts used for AVS are different from the server fleet that hosts other Azure services. Each host is in its own zone within Microsoft’s datacenters.
VMs in cloud consumers’ Azure subscriptions have inbound access to vCenter Server and NSX-T manager.
VMs can access Azure services on a private cloud.
Workloads running in the private cloud can be accessed from the outside.

An illustration depicts the Express Route of Azure. The Cloud Consumer On Prem has a customer edge router, on premises data center, connected elements of v Center, Storage, Network, and E S X i. The router is then connected to the Microsoft Azure Subscriptions with Express Global Reach between M S E E and D M S E E of the Azure Region. The M S E E and D M S E E are connected to Azure V Net and A V S N S X T through the E R gateway and cloud respectively.
Azure VMware Solution – ExpressRoute
Through Microsoft ExpressRoute, cloud consumers can connect cloud on-premises networks to the Microsoft cloud through a private connection. Cloud consumers of Microsoft cloud services such as Azure and 365 can connect to ExpressRoute.
An IP VPN (any-to-any) network, an Ethernet point-to-point network, or a cross-connect through a colocation facility can provide connectivity. There is no public Internet connectivity for ExpressRoute. Because of this, ExpressRoute connections offer reliability, higher speeds, and consistent latency than typical shared Internet connections.
With respect to Layer 3 connectivity, Microsoft connects cloud consumers’ on-premises networks, cloud consumers’ instances in Azure, and Microsoft public addresses using BGP, a dynamic routing protocol. Multiple BGP sessions are established between Microsoft and cloud consumers’ networks for different traffic profiles.
Cloud consumers’ AVS private clouds are connected to the dedicated Microsoft Enterprise Edge (MSEE) when they deploy the existing ExpressRoute circuit between on-premises and Microsoft Azure. Cloud consumers can then connect that to an ExpressRoute gateway in their existing Azure VNet to allow resources within that Azure viewer to communicate with AVS.
Connectivity providers and cloud consumers connect to two Microsoft Enterprise Edge routers at an ExpressRoute location via two ExpressRoute connections. From the connectivity provider’s/cloud consumer’s network edge, Microsoft requires a dual BGP connection, one to each MSEE. It is possible that cloud consumers will not deploy redundant devices/Ethernet circuits on their end. More often, connectivity providers will deploy redundant devices to ensure that Microsoft has handed off cloud consumers’ connections in a redundant manner.
A dedicated MSEE connection is created between an Azure VMware Solution private cloud and the Azure global backbone when a private cloud is provisioned. AVS can then access Azure public services if cloud consumers choose the Internet.
Direct connectivity to Microsoft’s global network is made possible through several peering points strategically located worldwide. ExpressRoute Direct supports Active/Active connectivity at scale with dual 100Gbps connections.
MSEE routers provide north/south network connectivity among Azure native services, cloud consumers’ on-premises DCs, and the Internet.
Dedicated MSEEs provide connectivity for cloud consumers’ private clouds based on AVS running in an Azure environment to connect to Azure native services and on-premises via MSEE.
ExpressRoute Azure services provide private, secure, high-speed, low-latency connections among the on-premises network and Microsoft Azure.
Azure resources can communicate with AVS resources through an ExpressRoute gateway configured in an existing VNet, a virtual network gateway that exchanges IP routes among the network and routes network traffic.
To connect to the jump box through the Azure bastion, you usually creates a VNet with a jump box virtual machine and an ExpressRoute gateway connected to an AVS ExpressRoute. Most enterprises already have an ExpressRoute circuit between their on-premises data center and the Azure region. Those ExpressRoute circuits can be peering with the private ExpressRroute circuit supporting AVS to allow connectivity between the on-premises resources connected VNet and AVS.
Global Reach peer ExpressRoute circuits together to avoid hopping over a VNet.
Private networks are created for management, provisioning, and vMotion in an AVS private cloud. NSX-T Manager, vCenter, and vMotion or deployment of virtual machines can be accessed through these private networks. Private clouds can be connected to on-premises environments with ExpressRoute Global Reach. An ExpressRoute circuit to the Azure subscription on-premises is required to connect to the virtual network.
Connectivity From On-Premises to AVS via ExpressRoute

An illustration depicts the Express Route of Azure. The Cloud Consumer On Prem has a customer edge router, on premises data center, connected elements of v Center, Storage, Network, and E S X i. The router is then connected to the Microsoft Azure Subscriptions without Express Global Reach between M S E E and D M S E E of the Azure Region. The M S E E is connected to Azure V Net through the E R gateway whereas, D M S E E is connected to both the E R gateway and the cloud.
Azure VMware Solution – ExpressRoute without Global Reach
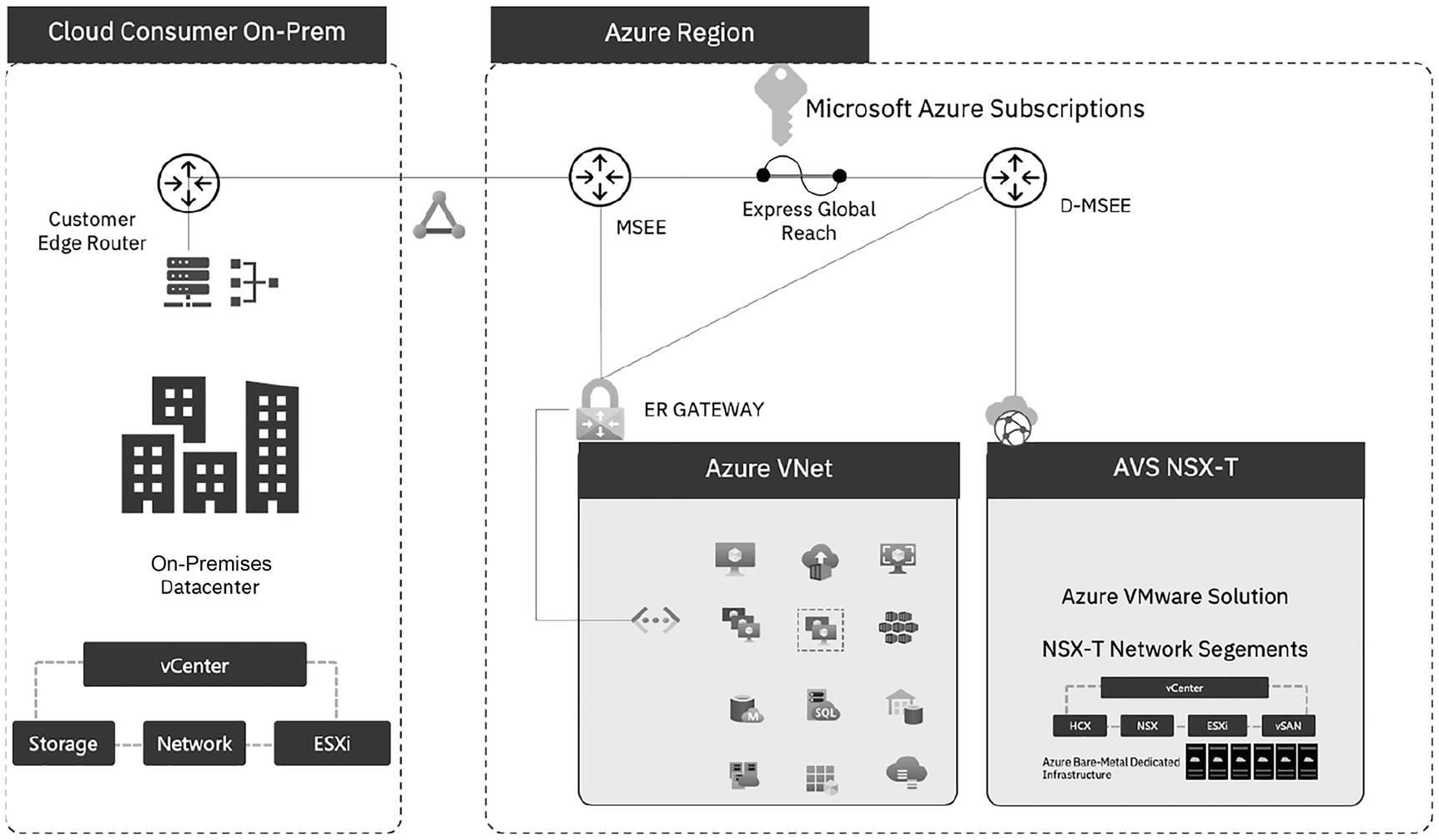
An illustration depicts the Express Route of Azure. The Cloud Consumer On Prem has a customer edge router, on premises data center, connected elements of v Center, Storage, Network, and E S X i. The router is then connected to the Microsoft Azure Subscriptions with Express Global Reach between M S E E and D M S E E of the Azure Region. The M S E E is connected to Azure V Net through the E R gateway whereas, D M S E E is connected to both the E R gateway and the cloud.
Azure VMware Solution – ExpressRoute with Global Reach
The ExpressRoute between AVS D-MSEE and MSEE is part of the AVS service providing backbone connectivity to/from Azure.
Connecting private clouds to on-premises environments is possible with ExpressRoute global reach, and MSEE connects circuits directly. Cloud consumers’ subscriptions must include a virtual network and an ExpressRoute circuit to on-premises. In other words, ExpressRoute gateways (VNet gateways) cannot send traffic from one circuit to another, so the AVS administrator cannot attach two circuits to the same gateway.
Azure VMware Solution environments are ExpressRoute regions (each its own virtual MSEE device), allowing cloud consumers to connect global reach to the “local” peering location. With this feature, multiple Azure VMware Solution instances can be connected to the same peering location in the same region.
In the absence of an ExpressRoute, cloud consumers can use the site-to-site VPN to connect to on-premises. Traffic flows through an Azure VPN tunnel through the Internet and an ExpressRoute gateway to the dedicated Microsoft Edge that VMware and Microsoft recommended for deployments of non-production or POC.

An illustration depicts the Express Route of Azure. The Cloud Consumer On Prem has a customer edge router, on premises data center, connected elements of v Center, Storage, Network, and E S X i. The router is then connected to the Azure v Net through V P N Gateway in the Azure region. The D M S E E is connected to both Azure V Net and A V S N S X T through the E R gateway and the cloud. The E R gateway has two way connections with the V P N gateway.
Azure VMware Solution – VPN connectivity
AVS Supported Configuration for Networking
Components | Configuration |
|---|---|
Azure VMware Solution ExpressRoute maximum linked private clouds | 4 |
Azure VMware Solution ExpressRoute port speed | 10 Gbps |
Public IPs exposed via vWAN | 100 |
Azure virtual WAN public IP addresses provide internet access to virtual machines deployed on a private cloud. By default, internet access is disabled for new private clouds.
AVS Workload and Application Mobility
VMware HCX is an application mobility platform that simplifies application migration, rebalancing workloads, and optimizing disaster recovery across datacenters and clouds.
Cloud migration is dependent on several factors: staff readiness, current processes, IT support, and management. Through AVS, cloud consumers gain access to and manage VMware environments using familiar VMware tools without retraining or even replatforming the hypervisors. As a result, cloud consumers maintain direct administrative access to VMware vSphere interfaces.
Using the VMware HCX Enterprise functionality, organizations can successfully accelerate large-scale, live migrations from on-premises to Azure with little to no downtime. VMs are migrated from on-premises to Azure without any interruption when using VMware vMotion from vCenter.
Migration options include cold and warm replication or live migration without replication,
Perform a bulk migration of live VMs: Schedule the movement of hundreds of VMs in parallel.
Use simple migration planning tools: To quickly identify the application and workload relationships and logically group VMs for efficient migration.
Cloud and data center mobility: VMs can be moved between local datacenters and Azure AVS private clouds or across cloud regions or providers to maximize resource utilization.
Migrate with no downtime: There is no need to rearchitect IP addresses.
Migration of non-vSphere workloads: Migrate KVM and Hyper-V workloads to the current vSphere versions compatible with the entire VMware Cloud, VMware Cloud Foundation, VMware Cloud Provider Program, and IaaS offerings.
Work across the WAN and LAN: Provide a unique infrastructure model based on the workload requirements, mixing public, private, and hybrid clouds.
Extend network and IP space seamlessly for cloud consumers: Reduce complexity and ensure compliance with IP addressing policies, security policies, and administrative boundaries.
To accelerate data center modernization and cloud transformation, VMware HCX enables high-performance, large-scale mobile app deployment across VMware vSphere and non-vSphere environments.
VMware HCX enables interoperability across KVM, Hyper-V, and vSphere 6.0+ to current vSphere versions. Live and bulk migrations can be performed without redesigning the application or rearchitecting the network.
Cloud consumers can modernize existing on-premises datacenters using the complete software-defined data center (SDDC)/VMware Cloud Foundation stack, managed services, or IaaS.
Migrating to a new platform can be driven by the need to move a set of available applications. Cloud adoption is the most common use case for a first wave migration using VMware HCX today, whether it is through a private cloud on-premises using VMware Cloud Foundation or adopting a VMware-based public cloud service such as VMware Cloud on AWS or Azure VMware Service or a combination of these services in support of a multi-cloud strategy.
It is rarely straightforward to move many virtual machines. By replatforming !!is relocating a better word? applications to current vSphere versions as part of the migration process or transforming workloads from KVM and Hyper-V environments, HCX is designed to support these brownfield migrations.
AVS private clouds and on-premises application footprints cannot be rebalanced actively without the ability to connect multiple clouds and become software-centric, service-driven businesses. A secure, high-throughput, WAN-optimized, always-on, secure, hybrid interconnect is at the core of HCX, continuously moving workloads across cloud regions, cloud providers, and on-premises datacenters.
Business continuity and disaster recovery (BC/DR) are optimized through a HCX hybrid interconnect, which offers on-demand migration. The cloud enables consumers to back up virtual workloads and migrate large-scale workloads to avoid disasters on-demand, on a schedule, and through scheduling.
Up to four virtual machines can be transferred simultaneously using HCX bulk migration using the vSphere Replication protocol. Rebooting the virtual machines into the target site can be transformed to the latest VM hardware/tools. Virtual machines can have their vNIC IP addresses updated as part of the migration process by using bulk migration.
HCX vMotion allows you to move virtual machines individually using VMware vMotion. With HCX Network Extension, applications sensitive to downtime can be migrated with zero downtime.
The VMware NFC protocol is used for HCX cold migration. Powered-off virtual machines are automatically transferred using this migration type.
With HCX vMotion with vSphere replication, virtual machines prepared in parallel will fail over with zero downtime (currently in preview with VMware Cloud on AWS).
HCX OS-assisted migration is a migration solution (currently in beta) that enables migrations from non-vSphere (KVM) environments to vSphere using an agent in Windows/Linux VMs.
By replicating data to an HCX-enabled provider or private cloud, VMware HCX helps protect on-premises applications. VMware HCX can restore the networking layer in a disaster. Since traffic routes are kept before the disaster, there is minimal downtime and high-speed disaster recovery. There is no reconfiguration of IPs, eliminating complexity and enabling partial or complete site recovery.

An illustration depicts Azure H C X interconnect. On premises has V M ware H C X connector with V M ware Technology Stack and the Workloads. It is connected to the cloud of V M ware H C X Manager, with the following sub elements, cloud consumers private cloud, Azure backbone, and Azure Services. Both the blocks are connected through H C X Site Pairing, V M, and H C X Interconnect.
Azure VMware Solution – HCX interconnect
Once the cloud consumer’s AVS private cloud is deployed, the HCX cloud manager can be deployed and configured automatically through the Azure portal’s Add-ons tab.
After that, the cloud consumers need to download, activate, and configure the HCX connector in their VMware environments on-premises. They can ensure a secure bi-directional connection between the environments and incorporate several features, including a built-in VPN with Suite B encryption, traffic engineering, LAN optimization, and deduplication and compression.
By extending on-premises networks into the cloud, workload migrations can be facilitated without the need to reconfigure IPs, and WAN optimization between on-premises and AVS can also be achieved, as well as deduplication and compression, which can reduce bandwidth and migration time.
AVS Supported HCX Configuration
Components | Configuration |
|---|---|
HCX | 4.2.2 |
HCX edition minimum | Enterprise/Advanced |
HCX site pairings | 25 (any edition) |
AVS Management and Operations

An illustration has visual tools and code based tools with their respective icons which are the A V S management components.
Azure VMware Solution – management block
Azure’s visual tools make it easy for cloud consumers to visually access all its functionality. Visual tools, however, may not be as helpful when setting up a large deployment of interdependent resources with configuration options.
A code-based tool is usually the better choice for setting up and configuring Azure resources quickly. The correct commands and parameters can be saved into files and used again and again once they have been entered, even though understanding them might take a bit of time. A source code-management tool such as Git allows setup and configuration code to be stored, versioned, and maintained along with application code. This method of managing hardware and cloud resources, which developers use when writing application code, is called Infrastructure as Code.
Infrastructure as Code can be viewed as either imperative code or declarative code. Code that specifies each necessary step to achieve a specific outcome is imperative code. On the other hand, declarative code only defines the desired effect, leaving it up to the interpreter to decide how to do it. A declarative approach is more reliable for deploying dozens or hundreds of resources simultaneously and reliably, so tools based on declarative code are essential.
Azure portal users, Azure PowerShell users, Azure CLI users, and Azure Cloud Shell users must select and use a tooling option.
Microsoft Azure management tools enable administrators, developers, and managers to interact with the cloud environment to perform tasks such as deploying dozens or hundreds of resources at once, configuring individual services programmatically, and viewing detailed reports on usage, health, and costs.
Depending on the situation, Microsoft Azure provides a range of management tooling options. Azure administrators can monitor, manage, and protect VMs using native Azure services in a hybrid environment (Azure, Azure VMware Solution, and on-premises).
It is Azure’s responsibility to manage the lifecycle of the private cloud software stack, while Azure administrators monitor and manage it. Azure is also responsible for providing and configuring the Azure infrastructure. When a failure occurs, or more or fewer resources are needed for cluster scaling, it is responsible for adding or removing hosts and networks. Azure VMware Solution handles the patching and updating of private cloud software.

An illustration depicts monitoring components of Azure software. On the left, it has Cloud consumers Private Cloud with V M ware Technology Stack, with five sub elements such as V M ware v Realize, V M ware v Sphere, and so on, followed by v Net. On the right, it has the Azure Management Operations with the following sub elements, Azure Arc, Azure Monitor, and so on. Azure backbone is in the middle.
Azure VMware Solution – monitoring block
Azure Arc: Microsoft Azure Arc enables the management of any infrastructure, including Azure VMware Solutions, on-premises, or other cloud services. Azure Arc-enabled servers allow cloud customers to manage Windows and Linux servers and virtual machines hosted outside of Azure, on cloud consumers’ corporate network, or in another cloud provider.
Azure Monitor: AVS and on-premises telemetry are collected and analyzed by Azure Monitor. There is no deployment required. Azure VMware Solution or on-premises VMs can be monitored via Azure monitor. Log Analytics workspaces in Azure Monitor enable cloud consumers to collect logs and performance counters using Log Analytics agents and extensions.
The Azure Monitor allows administrators to collect and analyze data from other sources for analysis, visualization, and alerting. The cloud consumer can also create alert rules to detect issues within the AVS environment, including high resource use, missing patches, low disk space, and heartbeats of AVS VMs. By sending an alert to IT Service Management (ITSM) tools, cloud users can automatically respond to detected events. Ops administrators can also receive notifications via email during the detection process.
As part of the Azure VMware Solution, both the VMware components and the underlay are continuously monitored. When Azure VMware Solution detects a failure, it takes action to repair the failed components. Azure VMware Solution initiates host remediation by detecting node degradation or failure.
Host remediation involves replacing the faulty node with a healthy one in a cluster. Whenever possible, the defective host is placed in VMware vSphere maintenance mode. Through VMware vMotion, the VMs can be moved from the faulty host to other available hosts in the cluster, potentially resulting in zero downtime for the live migration of workloads. The host is removed from the cluster if it cannot be placed in maintenance mode.
Processor and memory status
Connection and power state
Hardware fan status
Network connectivity loss
Hardware system board status
Errors on the disk(s) of a vSAN host
Hardware voltage and temperature status
Hardware power status
Storage status and Connection failure
Seamless monitoring
Better infrastructure visibility
Instant notifications
Automatic resolution
Cost efficiency
Microsoft Defender for Cloud: Microsoft Defender for Cloud increases data center security and protects hybrid workloads in the cloud and on-premises against advanced threats. It assesses the vulnerability of Azure VMware Solution VMs, generates alerts when necessary, and forwards them to Azure Monitor for resolution. By way of an example, it estimates the number of missing operating system patches, security misconfigurations, and endpoint protection issues. Customers of Microsoft Defender for Cloud can also define security policies.
File integrity monitoring
Fileless security alerts
Operating system patch assessment
Security misconfigurations assessment
Endpoint protection assessment
Azure Update Management: The Azure Update Management function in Azure Automation allows cloud users to manage operating system updates on Windows and Linux machines. Azure Monitor receives patching deviation alerts and alerts the user to remediate the problem. Cloud consumers’ Log Analytics workspaces must be connected to Azure Update Management to assess the status of updates on their VMs.
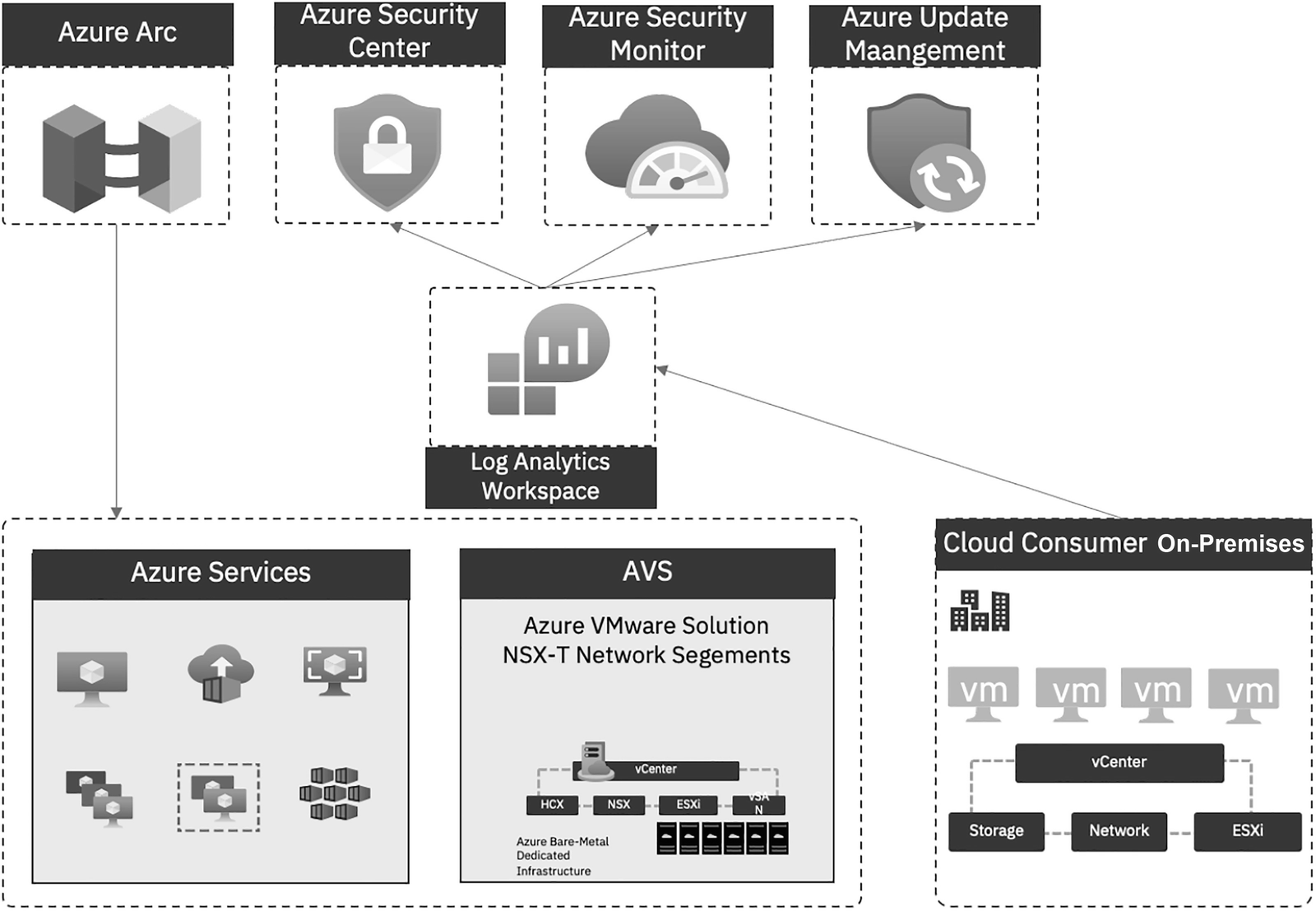
An illustration depicts the integrated view of management and operations. From bottom to top, it has Azure Services, A V S, and Cloud Consumer On Prem. The latter connects to Log Analytics Workspace, then to Azure Security Center, Azure Security Monitor, and Azure Update Management. The Azure Arc connects with Azure Services and A V S.
Azure VMware Solution – management and operations integrated view
Log Analytics agents can be connected to Azure, Azure VMware Solution, and on-premises virtual machines to collect log data. Azure Monitor Logs sends log data to the Log Analytics workspace, where it is stored. For new and existing VMs, cloud consumers can deploy the Log Analytics agent by using Arc-enabled servers.
Log Analytics workspaces collect logs, and cloud consumers can use Log Analytics workspaces with Defender for Cloud to assess the vulnerability status of Azure VMware Solution VMs and raise an alert if a critical vulnerability is found. The system estimates, for example, the number of operating system patches to install, security misconfigurations, and endpoint protections to install.
Microsoft Sentinel can be integrated into the Log Analytics workspace for alert detection, threat visibility, hunting, and threat response.
The Defender for Cloud connector is used to connect Defender for Cloud and Microsoft Sentinel. Microsoft Sentinel receives the vulnerability and creates an incident, which is then mapped with other threats from Defender for Cloud. Cloud consumers can also use the scheduled rules query to detect unwanted activities and report them as incidents.
Backup and Restoration
Backups are performed for vCenter and NSX-T configurations daily, and backups are kept for three days. In the Azure portal, cloud consumers can open a support request via Azure Portal if they need a restore from a backup.
Continuous monitoring is performed on Azure VMware Solution’s VMware and underlay components.
Backup and restoration solutions from Azure backup partners in VMware-based environments are industry-leading. Partners have extended their solutions to include Azure VMware Solution, using Azure as a repository for backups and a storage target for long-term archiving and retention.
In Azure, backup network traffic travels between VMware Solution VMs and a low-latency backup repository. The internal Azure backplane network carries replication traffic between regions at lower bandwidth costs.
Azure Backup Server contributes to a cloud consumer business continuity and disaster recovery (BCDR) strategy. With Azure VMware Solution, cloud consumers can only configure a VM-level backup using Azure Backup Server.
Disk: Azure Backup Server stores short-term backup data in disk pools.
Azure: Data stored in Azure Backup Server disk pools can be backed up to Microsoft Azure using Azure Backup for short-term and long-term storage off-premises.
Use Azure Backup Server to restore data to the source or an alternate location. Cloud consumers can restore data to an alternate location if the original data is unavailable because of planned or unexpected issues.
Ensure regular automated backups
Encrypt backup data
Validate all backups, including customer-managed keys
Mitigate the risk of lost keys
Shared Responsibility
Microsoft Azure VMware Solution is a VMware-validated solution that undergoes ongoing testing and verification related to vSphere upgrades and enhancements. Microsoft manages cloud consumers’ private cloud infrastructures and software. Having Microsoft handle this responsibility allows cloud consumers to focus on developing and running workloads within their private cloud and using Azure native resources. With the Azure VMware Solution private cloud and VMware software upgrades, cloud consumers can ensure their private cloud deployments have the latest security, stability, and features.
The VMware Cloud Infrastructure Services providers all have a shared responsibility model, which defines distinct roles and responsibilities between the VMware Cloud Infrastructure Services provider and the organization that consumes the service.
Cloud consumers and Microsoft are involved in the Azure VMware Solution under the shared responsibility model.
In the Microsoft cloud, ongoing maintenance, security, and management are abstracted, leaving cloud consumers in charge of the most important things, such as guest OS provisioning, applications, and virtual machines. Customers can also consider bringing their lifecycle processes and configuration management techniques to Azure. The Azure VMware Solution infrastructure is more under the control of Microsoft in this model, eliminating specific operational responsibilities.
Azure VMware Solution assumes responsibility for the underlying infrastructure when it deploys in Azure. Unless a support ticket is opened, IT departments cannot gain root access to ESXi hosts or join vCenter to a domain without seeking support. It means that central IT personnel have control over all on-premises VMware environments, changing standard operating procedures and process flow for IT departments.

A table depicts shared security and responsibility view with 4 columns and 16 rows. The column headers are Components, Deployment, Life Cycle, and Configuration. The highlighted labels are for Microsoft responsibility and Cloud Consumer responsibility.
Azure VMware Solution – security shared responsibility view
The cloud consumers’ responsibilities are to deploy and configure their SDDCs, virtual machines, and data. Customers are responsible for configuring network firewalls, ExpressRoute, and VPNs, managing virtual machines (including guest security and encryption), and applying appropriate controls for users using Azure role-based access controls (or Azure Active Directory), along with vCenter roles and permissions.
The Azure VMware Solution service is protected by Microsoft software and systems. Computing, storage, and networking software comprise the SDDC, along with the service consoles used to provision Azure VMware Solution.
The full service’s physical facilities, security, infrastructure, and hardware are under Microsoft’s control.
Microsoft is responsible for managing Azure infrastructure, including physical infrastructure, Azure Regions, Azure Availability Zones, and end-to-end management of compute, network, storage, rack, power bare metal hosts, and network equipment.
Microsoft is responsible for the Azure VMware Solution SDDC lifecycle including ESXi patching and upgrading, vCenter Server patching and upgrading, NSX patching and upgrading, and vSAN patching and upgrading. SDDC Networking (NSX) including Tier-0 Router, connectivity from Tier-0 to Azure Network. SDDC Backup/Restore including Backup and Restore vCenter Server, Backup and Restore NSX Manager. SDDC Health includes replacing failed hosts.
Azure VMware Solution is secured and protected by Microsoft. It consists of the compute, storage, and networking software that makes up the SDDC and the service consoles that enable Azure VMware Solutions to be provisioned.
Microsoft guarantees that Azure VMware Solution will be available at least 99.9% of the time.
Microsoft guarantees that NSX Manager and vCenter Server (management tools for VMware) will be available at least 99.9% of the time.
There is one failure to tolerate for clusters with 3 to 5 hosts and two failures to tolerate for clusters with 6 to 16 hosts.
Cluster storage retains a slack capacity of 25%.
Microsoft has not been prevented from meeting its availability commitment due to consumer actions under the Elevated Privilege mode.
Virtual machines can be started on the cluster since there is enough capacity.
The calculation of total available uptime excludes scheduled maintenance.
Keeping licenses and resources in one place eliminates unnecessary complexity.
The core pack can be licensed on-premises.
Fully utilize existing Windows Server and SQL Server licenses when possible. Azure Reserved Instances and AHUB help you save up to 80%.
Azure offers three years of extended security updates for Windows Server 2008 and 2008 R2. It only upgrades when necessary.
PaYG pricing is available and invoiced as other Azure services based on monthly usage.
Reservations can be discounted programmatically.
Microsoft handles many low-level operational tasks, leaving the customer to manage their workloads.
Cloud consumers are responsible for deploying software-defined data centers (SDDCs), including sizing host count, management network range, and HCX network range.
They are also responsible for configuring the SDDC Network and Security (NSX) including Tier-1 routers, firewall, IPsec VPN, NAT, public IP addresses, network segments, distributed firewalls, and network extensions (via HCX or NSX).
They are also responsible for configuring the SDDC network and Security (VSAN), including defining and maintaining VSAN VM policies and adding hosts to keep adequate “slack space.” Deploying VMs includes installing operating systems, patching operating systems, installing antivirus software, installing backup software, and installing configuration management software.
They are also responsible for migrating VMs including HCX configuration, HCX updates, Live vMotion, cold migration, and content library sync.
They are also responsible for managing VMs including installing software, implementing backup solutions, and implementing antivirus solutions.
AVS Security
Any environment must have security. Workloads deployed in Azure by cloud consumers’ organizations should be secure. Without this, an attacker may be able to use cloud consumers’ Azure resources to mine cryptocurrency at their expense or gain access to sensitive customer information, which would result in massive fines or sanctions for the company. In addition, it could result in reputation damage. Security concerns are increasing, whether using a hybrid cloud or a multi-cloud approach, due to the challenges presented by remote workers and the frequency and sophistication of nation-state attacks. For hybrid cloud planning, security and compliance are viewed as critical and as the first considerations.
With Azure Virtual Services, cloud migrations can access Azure’s built-in security capabilities across all layers and resources of the cloud. It’s easy to turn on throughout every development lifecycle stage, from native controls to scalable security operations.
The security offered by Azure is holistic. The cloud consumer’s organization needs to be protected, not just Azure. Integrating built-in controls and services allows cloud consumers to protect workloads efficiently. AVS workloads are protected against rapidly evolving threats via the Azure Monitoring and Security Center, which makes cloud consumers feel confident during their cloud journey.
Azure VMware Solution security allows cloud consumers to run their VMware-based workloads in a secure and trustable environment.

An illustration depicts the security and compliance of Azure software. They are identity and management, privilege access management, networking, data protection, assets management, logging and threat detection, posture and vulnerability, endpoint security, and backup and recovery.
Azure VMware Solution – security and compliance
As organizations migrate to AVS with Azure, they need to know a new attack vector. Security threats also exist for an AVS workload if it is not protected and secured per industry standards and recommendations.
One of the most daunting tasks for landlords is tenant security. Since Microsoft Azure is a public tenant, Microsoft and its AVS cloud customers share a certain amount of responsibility.
Corporate data used to be protected primarily by network perimeters, firewalls, and physical access controls. With the proliferation of bringing your own device (BYOD), mobile apps, and cloud-based applications, network perimeters have become increasingly porous.
Most cloud-related security breaches begin with a compromised user identity. When attackers gain access to a network through a compromised credential, they can escalate privileges or gather intelligence for further attacks. Secure identity is essential in any discussion about cloud security.
Security is increasingly being determined by identity. As a result, securing AVS solutions and data requires proper authentication and privilege assignment.
The authentication process establishes the identity of a person or service seeking to access a resource. An identity and access control principle is created by challenging a party for legitimate credentials. These credentials prove the person’s identity.
Authenticating a person or service determines what level of access they have. Specifically, it specifies what data they can access and what they can do with it.
Azure AD provides services to manage authentication and authorization.
Standardize Azure AD as the central identity and authentication system.
Manage application identities securely and automatically.
Use Azure AD single sign-on (SSO) for application access.
Eliminate unintended credential exposure.
Cloud consumers can restrict standing administrator access to privileged roles discover and review who has access using Privileged Identity Management (PIM) in Azure AD.
An attacker gaining access to the system
Accidentally affecting a sensitive resource by an authorized user
Users still need to perform privileged operations in Azure AD, Azure, Microsoft 365, or SaaS apps. Cloud consumers can grant users just-in-time privileged access to Azure and Azure AD resources and monitor what they do with their privileged access.
Protect and limit highly privileged users.
Review and reconcile user access regularly.
Use privileged access workstations.
Follow the least privilege principle.
Choose approval process for Microsoft support.
A virtual network is a logically isolated private network that can be created using the Azure cloud platform. Cloud computing services such as IaaS and PaaS use isolated networks, which must be isolated or controlled by customers. The perimeter (the outer boundary between the untrusted public internet and Azure virtual network resources consumed by cloud consumers) is where these private networks are protected from attacks.
Azure Firewall is an intelligent network firewall that protects cloud workloads residing on Azure with a cloud-native approach.
Implement security for internal traffic.
Connect private networks.
Establish private network access to Azure services.
Protect applications and services from external network attacks.
Simplify network security rules.
Secure domain name services (DNSs).
Only allow trusted networks.
Use Azure firewall premium.
Deploy and configure network security groups on a VNet.
Review and implement recommendations within the Azure security baseline for Azure VMware Solution.
The importance of data security is growing. Cloud consumers are obliged to handle their data carefully, including under strict regulations. The data of cloud consumers shouldn’t end up in the wrong hands.
Protect sensitive data.
Encrypt sensitive information in transit.
Encrypt sensitive data at rest.
All assets in a cloud infrastructure can be seen and managed using cloud asset management. This is an automated and secure way to manage cloud infrastructure. Businesses can track their cloud assets while maintaining smooth cloud infrastructure.
Ensure the security team has visibility into risks to the assets.
Ensure the security team has access to asset inventory and metadata.
Use only approved Azure services.
Use only approved applications in compute resources.
Logging and threat detection discusses how to detect threats on Azure and enable, collect, and store audit logs. As part of this process, Azure will enable detection, investigation, and remediation processes with controls that ensure high-quality alerts can be generated with native threat detection; it will also collect logs with Azure Monitor, centralize security analysis with Azure Sentinel, synchronize time, and keep logs for a specified period.
Enable threat detection for Azure resources.
Enable threat detection for Azure identity and access management.
Enable logging for Azure network activities.
Enable logging for Azure resources.
Centralize security log management and analysis.
Configure log storage retention.
Use approved time-synchronization sources.
Controls for evaluating and improving the Azure security posture are included in position and vulnerability management. Azure security configuration tracking, reporting, and correction include vulnerability scanning, penetration testing, and remediation.
Establish secure configurations for Azure services.
Sustain secure configurations for Azure services.
Establish secure configurations for computing resources.
Sustain secure configurations for computing resources.
Securely store the custom operating system and container images.
Perform software vulnerability assessments.
Rapidly and automatically remediate software vulnerabilities.
Conduct regular attack simulation.
An Azure SDK Import module is provided for configuring and enabling anti-malware protection as part of Azure service deployment. Endpoint protection for Azure provides anti-malware protection for Azure services in the cloud running on the Azure OS. During the deployment of Azure role VMs, anti-malware is installed and updated.
An AVS VM is protected from potentially harmful software with Microsoft Endpoint Protection for Azure, including viruses and spyware.
Use endpoint detection and response (EDR).
Use centrally managed modern anti-malware software.
Ensure anti-malware software and signatures are updated.
Summary
In this chapter, you got an overview of AVS, explored key elements of AVS and got a compute overview of Azure VMware Solutions, a storage overview of Azure VMware Solutions, and a network overview of Azure VMware Solutions. You also learned about AVS workload and application mobility, management, operations, and security.
In the next chapter, you will read about the design methodologies of Azure VMware Solution; AVS network topology and connectivity; AVS identity and access management; AVS security, governance, and compliance; AVS management and monitoring; AVS business continuity and disaster recovery; and AVS platform automation.
