Chapter 5
Steps in Detection
Abstract
Detection is an important foundation for other technical mitigation strategies. Detection helps us develop the knowledge to prevent pending attacks and warn others. Detection is more than the act of catching an attack in progress. There are two major components to detecting and combatting malicious email: first, use the technology to help you as much as it can, and second, use your brain. Scientists and researchers are continually applying every trick possible to combat malicious email and significant advances have been made. But the bad guys continue to react to those measures and modify how they operate, in order to avoid detection. Your brain, therefore, is a critical part of your defense. Further, when you understand the detection process, you also develop an intuition as well as detailed understanding of how problems potentially occur and that gives you the ammunition to actually prevent many problems from occurring and to quickly contain what problems sneaked through your defenses.
Keywords
Detection
Situational Awareness
There are two major components to detecting and combatting malicious email: first, use the technology to help you as much as it can, and second, use your brain. Scientists and researchers are continually applying every trick possible to combat malicious email and significant advances have been made. But the bad guys continue to react to those measures and modify how they operate, in order to avoid detection. Your brain, therefore, is a critical part of your defense.
As noted in Chapter 1, the basic approach is:
1. do not trust that any message you receive is legitimate: treat it with suspicion!;
2. use your eyes: look at messages for content, misspellings, and other anomalies;
3. do not click on any embedded links;
4. do not open any attachments;
5. do not believe in fairy tales, get-rich-quick schemes, or conspiracy theories;
6. keep your antivirus software up to date.
We have discussed most of these points, but some discussion is in order. A critical point about detection is that you would rather not rely on detection to protect you from problems. The reason for this is that by the time you detect a problem, it has already either begun to happen or has happened. It would be better to not let the problem occur in the first place. In a perfect world, you would have enough information and foreknowledge so that you could prevent problems from occurring before they became problems. However, this is not a perfect world. Because of that, problems do occur and it is important to understand how to think about the detection process in order to most effectively recognize when a problem has occurred and to contain the problem in a timely manner. There is a side benefit from this, as when you understand the detection process, you also develop an intuition as well as detailed understanding of how problems potentially occur and that gives you the ammunition to actually prevent many problems from occurring and to quickly contain what problems sneaked through your defenses. In this section, we will start with discussing the detection timeline, which includes all the elements that go into detecting and containing a problem, and then go back to discussing what can be done prior to an event occurring in order to mitigate problems before they become problems.
A good defense from the human element should begin with some element of situational awareness. Situational awareness simply means being aware of what is going on around you. For example, when you drive, you are (or should be) aware of all the other cars in your driving zone and what they are doing. You are aware of cars that are being driven by people who are talking on their phones, cars that are weaving in and out of traffic, and cars that have turn signals illuminated. Each of these cars is a potential threat and being aware of their behavior patterns is a critical part of defensive driving. Similarly, while you are “driving” through cyberspace, you should have some level of situational awareness. This does not necessarily mean that you need to be a security professional but that it is useful to be aware of the threats and strategies used by attackers. Thinking about what can go wrong is a great first step in creating and maintaining situational awareness.
Detection is an important foundation for other technical mitigation strategies. Detection helps us develop the knowledge to prevent pending attacks and warn others. Detection is more than the act of catching an attack in progress. It can be thought of as including three general stages: pre-, mid-, and post-attack detection activities. This is useful in distinguishing the three distinct opportunistic time frames in which threats of an attack or a problem can be identified, analyzed, and understood.
When we talk about recognizing a malicious message, what we are really talking about is detecting the probability that something might be wrong with a message and then taking the appropriate steps to verify, characterize, and neutralize the problem. Actually, this process is true for every detection problem, but we will limit our discussion to the challenge at hand. So let us walk through the process.
We talk about the detection challenge in terms of a timeline. Certain events precede other events in absolute time, but the steps taken in detecting and reacting to a problem only partially follow that timeline. The goals of the detection process should be to minimize the time between steps, so that the aggregate time from problem occurrence to solution is as fast as possible. This can help minimize the damage overall and it certainly helps you get back to normal faster.
In the “pre-attack” stage, there may be few indicators that a problem is about to happen. If you have robust network monitoring tools, which is typical of large organizations, some analytics reports may indicate that some form of reconnaissance has transpired. These reports can be hard to interpret and are not always completely accurate. In this stage, it is important to recognize that detection is not as much about detecting active attackers as it is about detecting the probability that problems might be building and then considering them against the known vulnerabilities in your environment.
It is in the “mid-attack” phase of detection that technology can be most helpful. In this phase, technology can be used to great effect to discover and filter out suspect or problematic activities, such as filtering computer viruses. A lot of work has been done in this phase to more efficiently and effectively discover and report malicious messaging. This can include automatically analyzing the contents of messages, including links and attachments.
The final “post-attack” phase of detection is done primarily through analysis. Analysis is nothing more than examining what happened and seeing what evidence can be recovered. For example, a computer forensics investigation can reveal how a network attack happened, why it happened, and what could be done to prevent a similar attack in the future. Look at systems logs and traffic logs, if they exist, might also reveal elements of a previously unknown attack. This type of post-mortem review can provide great detail about threats and vulnerabilities that can help you close the doors to future attacks. Of course, all of this is predicated on capabilities and resources: large firms can afford to do a lot of investigation while individuals can only do what they can do. You have to manage your problem to your scale.
While we talk about pre-, mid-, and post-attack phases, it is important to realize that the detection of a new attack or problem does not follow these phases chronologically. Instead, detection generally starts mid-attack and then splits into two analytical phases that encompass the pre- and post-attack phases. The lessons learned can then be integrated into your overall defensive posture so that detection of future attacks or problems can occur earlier and faster.
Typically, the first indicators that something has happened or that something might be wrong can be best characterized as symptoms or clues. This first step is the discovery that something is wrong. Looking at the depiction in the following figure, you can see that the indicators occur after the problem event: this can be a tricky issue, especially if there are very few indicators that something might be wrong or if the indicators are misleading.

The “something wrong” could range from noticing a weird subject line on an email to getting complaints from your Facebook friends about links you have been posting to their timelines. Acting on the indicator is the first step towards defeating potential malicious activity. If you notice a weird subject line and treat the subject email with caution, you might well avert a larger problem from happening. This, of course, is the best outcome: stopping malicious activity before it becomes a real problem, as it clearly has become in the second example. This second sample indicator, the complaints from friends, tells you that the problem, whatever it might be, has already gotten beyond your immediate control. For the rest of this discussion on the detection timeline, we will use that example to illustrate.
This leads to the second step in the detection process: characterizing the event. In this step, you take the clues that you are provided and try to figure out what happened, when it happened, and if the problem is ongoing.

When you start this process, you have several facts at hand, which are the immediate observables. For our example, you start with two facts: first, that your Facebook profile has been used to post links that you were unaware of, and that you did not in fact post those links so therefore someone else must have. This very small set of facts gives you at least a starting point in discovering what exactly happened. It also helps you collect data on two very important other questions, namely when exactly did the problem occur or begin occurring, and is it still occurring or has it stopped. Each of these questions is important know for you to understand in order to proceed on to the next step in the detection timeline.

Once you have gathered the information on what is going on, when it probably began occurring, and whether it is still occurring or has stopped, you have to determine how to react. You now know what has happened, probably, you have a small set of facts from which to work with, and you are faced with a series of decisions on how to respond. Your response, of course, is going to directly reflect the nature of the problem and the extent of the problem.
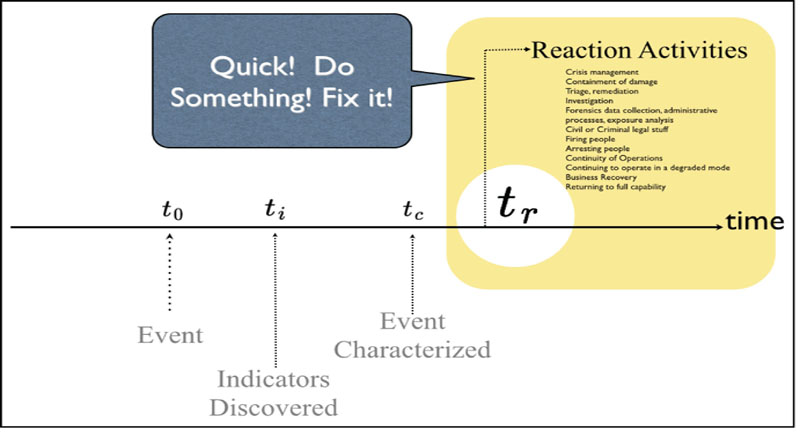
Your reaction activities will, of course, be commensurate with the nature of the problem. If it is a very large problem, then a lot of reaction activities will need to occur. If it is a very small problem, then fewer reaction activities will need to be launched.
Types of reaction activities that may need to be considered include things such as crisis management, containment of damage, investigation, perhaps forensics data collection, perhaps making criminal complaints with the police, possibly suing negligent parties, and continuity of operations in degraded modes. Obviously, for a single individual, the reaction is simpler than for a large organization. For a single individual, reaction may be limited to a cursory investigation, with indefinite results, an apology or explanation to other affected contacts, a password reset, and moving on. For groups of individuals, reaction may encompass much more coordinated response options, such as collecting and comparing information on when and where problems occurred. For large enterprises, frequently more intense investigation is warranted, both to characterize what the extent of the problem and to devise approaches to contain it.

Once you have figured out what the damage might be and whether the damage has stopped occurring—a very tricky issue if your identity has been stolen or your financial credentials have been compromised—you are then faced with the question of whether you should notify anyone. For individuals, that answer is usually “no.” The answer turns to “yes” when there is potential for cascading effects, such as if your email account has been compromised and malicious messages are being sent under your name from your account. The answer is also “yes” if your computer has been compromised and you need help fixing the problem. For larger organizations or for enterprises in regulated industries, there may well be a mandated reporting requirement. Organizational policy will be of assistance in this case, even if the problem occurred on a home computer, since trusted access to an enterprise network has the potential for causing wide spread issues.

Once everything has been handled, then you have the opportunity to ask the most important question of all: what the heck happened and why did it happen to me? As illustrated in the following figure, before any attack is actually executed, the bad guys need to figure out who to target and how to target. These activities are known as pre-attack activities.

For untargeted malicious messaging, the answer to this question may simply be “Because I exist.” Phishing schemes may be sent to every person that the attacker can find with an address or destination on social media. As the attack becomes more individualized, the pre-attack activities become more significant and sometimes even detectable. These are important elements to consider: did something weird happen before the attack? Was something introduced to my environment, like a USB stick that someone found on the ground? Did I get strange phone calls? Did I sign up for a new service? Asking these types of questions can provide a great deal of insight into potentially avoiding problems in the future and help you provide guidance to friends, family, and colleagues.
Technology assistance
The blinking lights and sophisticated toolsets that have been glamorized by authors and Hollywood alike are not always the sensational products they are portrayed to be, and yet major advances in security tools are making it easier to use technologies to provide help. Today’s collection of tools include fairly exotic technologies like dynamic training interfaces, machine learning detection algorithms, continuously monitored environments that present vulnerabilities to threats in near real time, and big data techniques that pour through massive amounts of data finding useful trends for the analyst, but they also include consumer grade technologies that are user-friendly and readily available. Today’s tools are faster, more robust, and produce better indicators across a much larger volume of information than has ever been accomplished in human history. Even better, we can expect that defense toolsets will continue to advance and become more efficient and accurate through time in an effort to keep pace with our adversaries.
Technology can also be your friend. Tools can assist in protecting you and understanding configuration issues can help you avoid problems. When planned and configured correctly, technological solutions offer the benefits of being scrupulous in their methods, reliable over time, and predictable in their results. To be clear, there is not a single tool in existence that has proven to be 100% successful in defending a system or network of systems over time. Even when multiple tools are deployed the success rate is high but not foolproof. What should be taken from this knowledge is that such tools, while highly successful, are still just tools and not answers. Notwithstanding its limitations, technology still provides an important and highly beneficial role in protecting yourself while online. So let us talk about the role of technology.
“Why don’t they DO something about all this spam?” asks one user. “What can I do about this? Who do I need to complain to?” asks another. In this particular case, “They” are the unsung heroes of IT: the poor slogs who set up, administer, and maintain the functionality of information systems. For all of the talk about how glamorous a career in information security is, the reality of the case is that the vast majority of the time is spent configuring users’ systems, helping people who have fallen victim to problems of various sorts, and working within an enterprise to recover from the effects of attacks. It is not particularly glamorous, but it is extremely important. While most of the problems and attacks go unnoticed by the average user, when it comes to malicious email, everyone notices. This is because the point of entry is extremely personal: your inbox.
The good news is that “they” actually are doing something about the problem. The amount of malicious email intercepted by service providers is astonishing compared with the amount that actually gets through to end users. And yet, the amount that gets through to end users is enough to drive people crazy, especially those who have had the same email address for years. There are benefits to having the same email address for years: your contacts know how to send you email and tend not to send it to a wrong email address. But there is a downside: the longer you keep and use an email address, the more likely it will end up on a list of email address that are bought and sold for purposes such as fraud, spam, and worse. There is a direct correlation between age of email address and amount of un-useful email received: the oldest existing email address gets the most annoying email by a very large margin, while the newer ones can blessedly free from spam. Unfortunately changing email addresses every six months is not a viable option in a world where your email address may be the only way to contact you.
This annoying email situation persists because of simple market dynamics: the rewards of getting malicious emails through are sufficiently lucrative that the bad guys work very hard to find ways around the automated detection and filtering of unwanted email. Understanding this phenomenon is a key to combatting the problem on an individual level.
Malicious email is email, so the first defense is being aware of your email patterns. Being able to glance at email and make a first judgment about what is likely legitimate and what is likely malicious is a very important capability. Before it gets to that, however, you can use the power of your email software to help you remove some unwanted emails from your inbox without you even having to look at it.
Researchers have been working on providing automated tools for identifying and filtering emails. Their goals are to help enterprises manage the enormous volume of email received, assist users in eliminating unwanted emails from their inboxes, and reduce the ability of spammers to successfully infiltrate email systems. Depending on who your email provider is, your email may be subject to one or more of the tools that have been developed. For example, your provider may have implemented the sender policy framework (SPF), which was specifically developed to combat the problem of forged sender addresses.1 Or your provider may participate in reputation services, which provide a listing of addresses that should be blocked. Or your enterprise may use technology to support threat detection, such as anti-spam systems. If you want to find out which capabilities are in place in your enterprise or used by your provider, you can find out by looking through the email headers, as discussed in Chapter 3.
These tools and capabilities have really helped in the malicious email wars. But they are not perfect. Furthermore, the bad guys have a strong incentive to figure out how to work around the technologies and protections so they can accomplish their goals. This means, unfortunately, that the wars continue and malicious email will eventually end up in your inbox. When that happens, you need to know what to do.
In some email systems, a spam blocker or junk mail capability is automatically included. In other email systems, you will need to set up such filtering. To find out whether your system is set up with spam or junk mail filtering, go to the help function and see what it says. For example, most large free email service providers, such as Google and Yahoo, not only automatically filter for spam or junk mail but they also allow you to identify unwanted email as spam to improve performance. If your provider does not automatically provide filtering, find out how to activate filtering by looking through the help function. If your provider does not provide any filtering, you might want to consider using an email software system that has filtering embedded. There are many email client software applications for all platforms, most of which are free.
Configuration counts
Independent of your access to sophisticated spam or junk mail filtering, you can accomplish a lot by simply configuring your email preferences to help you be more secure. The point of this is to reduce some of the trickery used in malicious email. This includes activating any included technologies, such as filtering, but also includes deselecting certain options, such as auto-loading of images. The downside of doing this is that your email will appear less attractive, but that is really a temporary aspect that can be manually over-ridden for emails from trusted sources.
The important configuration aspects all revolve around display options. Three important aspects of display options that should be considered carefully are HTML formatted message content, address display options, and automatic loading of images.
HTML Formatted Emails: HTML stands for Hyper Text Markup Language. It is a way of embedding instructions to the computer on how to display information. For example, an embedded command might tell the computer to display the selected text as bolded text. Alternatively, it may tell the computer to associate an internet link with a set of text. In the example shown, two emails are shown. The one on the left is the HTML-formatted email, whereas the one on the right is the same email with the formatting disabled so you can see the embedded commands. The arrow points from the embedded link, allegedly to the Chase Online Banking site, to the actual URL that is embedded in the text. As anyone can see, now that it is revealed, the link is not in fact to the Chase Online Banking site at all, but to some site that has no relationship with Chase Bank at all.
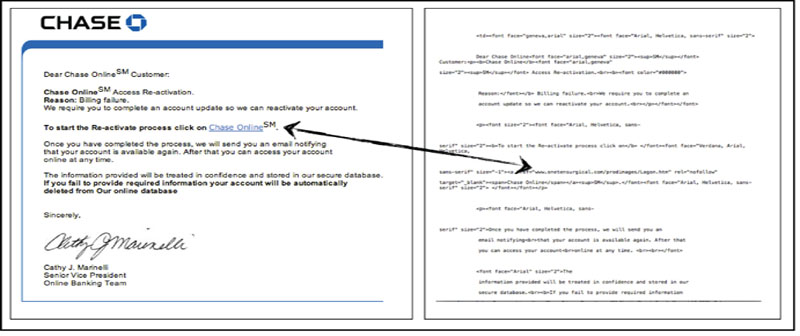
The downside to not displaying HTML formatted email is that you have to wade through all those commands to find out what is being communicated to you. But it turns out that for emails that are more on the legitimate side, disabling HTML formatting may not obscure the content very much, depending on the sender. In fact, for some emails sent by people who are somewhat design challenged, disabling HTML may actually enhance the readability of the message.
Not all email applications will allow you to disable viewing the HTML formatted emails. Some will only allow you to not automatically load images in HTML-formatted images. If your email application does allow you to disable HTML formatting, you should consider doing so. If it does not, you can always use the controls to view the raw message source to examine the actual contents of the HTML content to make sure that it is not hiding something sneaky behind the formatting. Since there are so many email applications, it is not possible to provide comprehensive instructions
If possible, configure your email client to not automatically download and display images in HTML formatted emails. Why? Because when images embedded in messages are displayed with all content, you are actually downloading and opening files from a distant computer. The HTML format allows the distant end computer to actually collect information from your computer when you do this. In fact, one of the more devious ways of collecting information is by including a single pixel image: it is not noticeable, but invokes the power of images to collect information. This particular trick is called variously a clear gif, a web beacon, or a web bug.2
Similarly, you should configure your email client to not display HTML-formatted messages. This choice has consequences: HTML-formatted messages are designed to be easy to read and attractive. When you turn off HTML formatting, you get the HTML commands along with the text, which can be annoying to read through. However, the benefit is that you can easily see if the text contains evil elements, such as hotlinks to fraudulent websites. (This was discussed in detail previously, but it bears repeating.) “Smart” addressing: some email clients will use contact names in place of the actual names and addresses in the headers of emails. This may obscure forged information. You want to be able to see as much of the email data as possible, so turn off “smart” addressing.
Antivirus software is an absolute must have on your computer. But it is not enough to simply have the software—you have to update it often. How often? Every single day is a good rule of thumb. You can set it up to automatically update, so you do not even have to think about it. Despite repeated news stories predicting the end of anti-virus software, it is still a must-have tool. It is inexpensive, easy to use, and will alert you to many different types of common problems.
Finally, a word about passwords. Yes, this is a flawed approach to system security but we are stuck with it for now. Make sure you have a good password and change your passwords regularly (particularly for high value systems, like your bank). Do not use the same password for many different systems: each account you have should have its own unique password. You will not be able to remember them all, so invest in a password safe. A password safe is an application that uses cryptography to hide your sensitive data: you open it, enter your password information, and then close it. Then when you cannot remember your password, you can look it up. Alternatively, you can write your passwords down and store the written version in a real safe.
Educating and training others around you is important. If you are a parent, your children need to understand these issues. If you are in a company, your fellow employees need to understand them as well. Everyone does not necessarily need the same level of education and training, but everyone does need to understand the nature of the problem and how to both protect themselves and others who might rely on them. In the next chapter, an approach to this is presented.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
