Chapter 2
Types of Malicious Messages
Abstract
A malicious message is any message in electronic form, sent through an automated information processing systems, which has been crafted or designed to assist in the achievement of a goal that is, in one or more ways, dangerous to the best interests of the recipient. In simpler terms, it is an electronic message that can cause you, or the systems you are connected to, harm. Herein lays the danger of malicious email: if simply opening an email can cause problems for you, how can you possibly know which emails are safe to open and which ones are not? Further, how can you know whether an attachment is safe to open or not? It is important to realize that there are no 100% solutions. Types of malicious messages range from phishing attacks, which are designed to get recipients to reveal sensitive information, to messaging with embedded malicious software. Understanding the characteristics of malicious messages can help you answer the question, “is this email legitimate and is it safe to open?”
Keywords
Phishing
Spam
Unsolicited Commercial Email
The introduction serves to illustrate the space of the problem. However, to understand what malicious messaging is, and what it is not, it is important to start with a specific definition. The definition offered here is the broadest possible, so that our explorations of the topic can include all possible dangers.
Malicious Message: A message in electronic form, mediated by automated information processing systems, that has been crafted or designed to assist in the achievement of a goal that is, in one or more ways, dangerous to the best interests of the recipient.
In simpler terms, it is an electronic message that can cause you, or the systems you are connected to, harm. There you have it: a short and to the point definition, that makes the point clear: you need to defend yourself against someone who intends to harm you. A tricky follow-on to that definition is figuring out what the potential scope of harm is. Can email harm you physically? Well, not by itself, since an email is nothing but a string of electrons. A properly crafted email may harm your computer, your data, or your network or any network to which you are connected. Additionally, a malicious email may possibly lead you into a situation in which physical harm is a possibility.1
Herein lays the danger of malicious email: if simply opening an email can cause problems for you, how can you possibly know which emails are safe to open and which ones are not? Further, how can you know whether an attachment is safe to open or not? It is important to realize that there are no 100% solutions. In this book, we are going to review methods and techniques to give you a fighting chance in the ever escalating war between the senders and the receivers of malicious email.
We have set the stage for developing the skills to identify and combat quickly most malicious emails. Why only “most”? That is part of the problem, and is why education is so important: the attackers are constantly learning and refining their techniques to improve their chances of success. That is why the last chapter in this book covers what to do if one-or-more malicious emails successfully find their target. The target might not be you—it might be a colleague or a loved one, it may be a group you belong to, or it may be the resources and/or systems of your company. In any event, good preparations include not only preventing problems but also being ready to react should a problem occur.
A word closely associated with malicious messaging is “phishing.” This word is pronounced the same as the word “fishing” and it refers to a set of actions done to get victims to reveal sensitive information, such as bank account details, login credentials, passwords, or detailed personal information. In other words, the attacker is fishing for information. Phishing is closely associated with malicious messaging because the easiest way for attackers to execute this type of attack is by the use of messaging technologies, primarily email.
Recognizing that phishing is one of the great threats to an individual or institution, many researchers have set out to find an answer or create a tool that will prevent phishing attacks. Others have studied how the users can be better prepared to defend against such attacks, but nobody has done the research that ties it together into a holistic defense strategy. Some of this work brings together the research and practical knowledge assembled by many other sources, creating a unified framework for defending against phishing attacks. Through the fusion of various studies, a more robust and complete defense strategy can be created, and that through its implementation, individuals and organization will reduce the number of successful phishing attacks experienced annually. Until that work is completed and solutions are deployed, it is up to the individual user to understand and take steps to guard against these types of attacks.
In order to discuss malicious messages, I have divided the types into several categories of features. It is important to point out that these feature types are not exclusive: a malicious message can have several of the type features embedded in one message. However, in order to discuss the problem space, it is easier to separate and consider the problems individually. Once you know what the types of problems are, you are better able to recognize and avoid the problems.
It is important to point out that malicious messaging is not always spam, formally known as Unsolicited Commercial Email (UCE). UCE can clog your inbox, be very annoying, and steal time from more productive activities, but may not be malicious per se. Email and other forms of electronic messaging stray into the malicious zone when the purpose of the message goes beyond the simple advertising of a product. It can be very difficult indeed to differentiate annoying-but-legitimate unsolicited messages from malicious messaging. In fact, malicious email sometimes can even disguise itself as legitimate unsolicited messages in order to trick you into opening the email.2
Here are some examples of malicious email:
• invitations to participate in some activity, such as an employment scheme, that can result in theft of money (usually from the recipient);
• requests or demands to click on an embedded link, which results in your unwitting participation in fraudulent activity, such as traffic driving or click fraud, or your unknowing download of unwanted software or material, including viruses or pornographic material;
• requests or demands that attachments to the email be reviewed, where the attachment is malicious software that is executed when opened, embedding software in your computer.
These are but a few of the types of malicious email behavior seen. Rather than cataloging all types, we can generalize certain characteristics that can assist you in making the judgment call: “Is this email legitimate and is it safe to open?”
Feature types of malicious messages
The feature types of malicious messages are all intended to accomplish substantially the same purpose: to get the recipient to do something. The something can be responding to the email, clicking on an embedded link, or opening an attachment. Thus, we can quickly focus in on four primary feature types: appeals to emotion, trickery, subversive links, and subversive attachments. After describing the feature types, I have included real examples of actual emails that illustrate one or more of the feature types.
Appeals to Emotion
Emotion is a powerful motivator for human beings. Research has shown that emotional states can affect physical and mental health and can be responsible for hormonal changes in the body3. The sender hopes to get a recipient to act without considering if their emotions are being manipulated. Emotions that are common targets for bad guys to exploit include (but are not limited to) the following:
• emotions associated with comparative success, such as ambition, envy, narcissism, and greed;
• those associated with authority, such as intimidation, obligation, or pride;
• those associated with compassion, such as sympathy or kindness;
• those associated with paranoia, such as anger, bitterness, and fear; and
• those associated with community, such as courage and love.
Trickery
Disguising an electronic message to appear to be legitimate is an appallingly effective way to get recipients to do something they may not normally do. This approach is particularly effective when combined with an appeal to emotion. Often, these electronic messages include precise copies of official logos, images, and other symbols of authenticity, such as trademark or copyright logos. The entire design of these types of messages is to convey an overwhelming sense of authenticity to the recipient so that trust will be implied. In addition, when that trust is effectively established through such trickery, the recipient’s defenses are reduced, thus increasing the probability that the goal of the sender will be accomplished.
Subversive Links
It is common to receive an electronic message with an embedded link to a website, a document, or some other asset. The problem is that these links are not always what they appear to be. It is possible to disguise a link to hide its true nature. For example, using appearance coding, a link to http://www.exampleofmaliciouslink.com could be disguised to look like something innocuous, like http://www.funwithpuppies.org. This is quite dangerous, as it can be difficult to discover what the actual link in the message is, depending on what platform the recipient is using to read messages. Some platforms, such as fully functioning desktop computers, provide enough functionality that users are able to look behind the curtain to discover the truth. Other platforms, such as some phones, have limited support to users to discover the true content of links. The purpose of subversive links is to get the recipient to load a website that then unleashes the attack on the recipient. Typically, this consists of downloading malicious software automatically. Because of this, a first order recommendation is never to click on a link in an electronic message. Instead, if you really feel like you need to find out what is at the link, use the various tricks at your disposal to discover the actual content. A few of these will be discussed later in the book, but a caveat remains that there are so many platforms, no discussion can possibly be complete and you should take a few minutes to find out how to do this on each of your devices. It is not difficult, as we will see, and can save you a world of pain.
Subversive Attachments
In a similar fashion, it is possible to disguise attachments to look quite legitimate. One common technique is to hide attachment file extensions (such as.doc or.txt) so that the recipient cannot easily detect that the attachment is actually an executable program. Double-clicking on the attachment in the electronic message launches the file via the default application for that file type. Again, the first order recommendation is never to launch an attachment from within an electronic message. If you feel like you need to examine an attachment, you can save it to a protected area in your storage area and then use the directory listing to examine the file naming structure. To examine the contents of the file, you can use the File Open With command on your computer to look at the contents with a text editor, such as a note pad application. If you were expecting it to be a word processing document and all you see is a bunch of symbols or what appear to be hieroglyphs, then you know immediately that the file may not be what you expected it to be. If you are not able to ascertain to a reasonable level of certainty that it is a legitimate file, you should delete it. Alternatively, if you are in an enterprise environment, your network security people might want to examine the file.
A Further Complication
Rarely does the electronic mail have the return address of [email protected]. Instead, the sender identification will be designed to appear legitimate, innocuous, authoritative, or a combination of all those elements. A favorite trick is to use common names, so that the recipient will assume it is an acquaintance. In these days of social networks, where we have contact lists that number in the thousands, this type of disguise works fairly well to deceive the recipient. Another trick is to use the name of a celebrity or a slight variation on the name of a celebrity. The commonality of the name is such that the defenses of the recipient are reduced simply because the brain is tricked into a sense of normalcy. Electronic messages that are disguised to appear to come from authoritative sources, such as banks or government agencies, naturally have the sender identification modified to appear to be legitimate elements of the source.
All of these elements combine to create what can be an amazing array of tricks to deal with. The knowledge needed is simple, through awareness of the problem, a basic understanding of electronic messaging, and the development of a suspicious approach to electronic messaging. Then simply being cautious can provide an enormous amount of protection against these types of attacks.
Examples of malicious messages
The following examples are all real; they are copied verbatim from received emails. The message content itself is presented, with an analysis of the types of issues that are easily noted that provide evidence that the message is problematic. Some of the elements are obvious: poor grammar, misspellings, or punctuation mistakes. Other elements are more subtle, until you get used to picking them out in messages. Each of these includes one or more of the feature types discussed earlier.
An Appeal to Emotion
Probably the best known of all malicious emails is the email that invites the recipient to participate in a shady activity with the promise of an enormous payout at the end. There are endless varieties of this type of email: the Nigerian 419 scam, the stranded passenger scam, the lonely-hearts scam, the unlucky inheritor scam, and others. A common version of this type of email is a plea for help combined with an offer to share in good fortune, as noted in the following example:
My Name is Miss Hanna Gaddafi,I growed up and found that i am an adopted daughter of Late Muammar Gaddafi,former president of Libya who died on October 20, 2011
I hope you will not find my message offensive since we have not met before and coupled with lots of internet scams going on these days on the internet.
Due to the critical situation I found myself in Libya, I have managed to sneak into united kingdom as the new government is looking out for all our family members for prosecution or be killed as they killed my father. Am looking for an honest/trusted person to whom i shall hand over deposits my late father deposited on my behalf to be used when am matured enough to handle such enormous treasures (funds including gold and diamonds)if you are the honest/trusted person,kindly get back to me so i can furnish you with the contact information of our family lawyer for the process to kick off immediately as this letter need an urgent attention because the new government is searching for the hidden treasures of my late father therefore treat this as highly confidential and urgent.Waiting to hear from you.
Miss Hanna Gaddafi
A variation on the scheme exploits religious values to try to get the recipient to respond, as illustrated by the following text of an email (spelling and grammar from original):
From Mother Asetou
My name is Mother Asetou kosta. nationality of Syria’s. I am married to late. Mr James kosta. who worked with Ivory Coast embassy in Syria’s for nine years before he died in the year October 2009. We were married for twenty years with a two kids. He died after the hilliness that lasted for long last four day.
Before his death we were both born again Christians. When my late husband and was alive we deposited the sum of $9.2 Million (Nine Million two thousand Euros) with one of good banks here in Malaysia, presently, this money is still with the bank. Recently my Doctor told me that I would not last for the next three months due to my cancer problem. Though what disturbs me most is my stroke, Having known my condition I decided to donate this fund to church or better still a Christian individual that will utilize this money the way I am going to instruct here in, I want a person or church that will use this fund to churches, orphanages, research canters and widows propagating the word of God and to ensure that the house of God is maintained.
The Bible made us to understand that blessed is the hand that grivet. I took this decision because I have a child that will inherit this money but my son can not carry out this work only because i and my late husband decide to use some of the money to work for God and live some f or our son to have a better live, our son is just 14year old with his elder sister 16 now and been grow up in Africa, he have low mentality and my husband’s relatives are not Christians and I don’t want my family hard earned money t o be misused by unbelievers. I don’t want a situation where this money will be used in an ungodly manner. Hence the reason for taking this bold decision, I am not afraid of death hence I know where I am going to. I know that I am going to be in the bosom of the Lord. Exodus 14 VS 14says that the lord will fight my case and I shall hold my peace. I want your t telephone communication in this regard because of my health because of the presence of my family relatives around me always; I don’t want any of my husband family relatives to receive this money. With God all things are possible.
As soon as I receive your reply I shall give you the contact of the Finance/bank. I will also issue you a letter of authority that will empower you as the new beneficiary of this fund. I want you and the church to always pray for me because the lord is my shepherd. My happiness is that I live a life of a worthy Christian. Whoever that wants to serve the Lord must serve him in spirit and truth. Please always be prayerful all through your life. Any delay in your reply will give me room in sourcing for a church or Christian individual for this same purpose.
Please assure me that you will act accordingly as I stated here.
Remain blessed in the name of the Lord.
Mother Asetou kosta.
What these messages attempt to do is establish contact with a person, who will then be systematically exploited for as much money as the scammers can get.
At first, a trusting person might well be persuaded by the content of these messages. She is merely a poor young girl on the run from people who want to kill her. Of course, the first instinct is to help! A pious elderly woman who simply wants to spread the religion that has given her so much peace? An adherent of the same religion might feel obligated to assist, even blessed to have been the one chosen. It is in these details that the dangers lay but also where the truth can be revealed.
In the first email, the sender claims to have only recently discovered that she is an adopted daughter of Gaddafi. The first question that springs to mind is, “how did the adoption work, if she was abandoned to the point of being ignorant of the fact?” The second question that follows quickly is, “Was she really adopted or not?” If she had truly managed to grow up ignorant of being an adopted daughter of the most powerful person in the country, then why would she be in danger? Furthermore, if she were an abandoned adopted daughter, then how on earth would she have access to all that wealth? Moreover, it is when one starts critically considering the plausibility of the story that it indeed starts to fall apart.
The same is true with the second email, although it is slightly more subtle than the first. In this one, the sender claims to be an older woman with an enormous amount of money that she wants to be used to spread her religion. Taking the message as truth, it is clear that the woman is poorly educated in English and lost her husband approximately 5 years ago (the email was received in 2013). Her husband had worked at the Ivory Coast Embassy in Syria, and she claims to be of Syrian nationality, but later in the email implies that she resides in Malaysia. That is strange. This poor woman says she only has months to live and needs to find a trustworthy person to carry on the good works of the church, which she cannot trust her children to do, since they are in their teens and the son is not very smart. No word on the daughter’s intelligence. Moreover, the two children live in Africa someplace, not in Malaysia with her. Therefore, for a strongly religious person of a religion that values family relationships, her family structure is quite strange. Then there is the question of where did she and her husband gets 9.2 million euros? Euros are not the currency of Syria, the Ivory Coast, or Malaysia, so there must have been a currency exchange to convert the money from its original form to euros. It is indeed possible to have a foreign currency account in some banks in Malaysia, but the question lingers—how did two people in Syria manage to open a foreign currency account in Malaysia with that much money?
Both emails are also not addressed to anyone in particular. If you had a large amount of money that you were trying to do something with, would you not research possible assistants to gauge their ability to be of real assistance? Not everyone knows how to manage millions—how does one even keep track of that much money? Furthermore, the second email claims to want the money to be used for religious purposes, but she does not even ask if the recipient shares her religion; much less verify the sanctity of the recipient.
It is in this level of critical analysis that the messages shed any semblance of legitimacy and actually become comical to read. The more you reread the messages, the more ludicrous they become. This then is a critical part of being able to defend yourself against these types of malicious messages: developing the ability to recognize something as illegitimate simply by reading the content. If you read a message over and over again, asking critical questions about each detail, more questions than answers suggest themselves until the scam becomes apparent.
The Invitation
In this type of malicious email, the recipient is invited to participate in some activity. The invitation seems exclusive or very special, and may include a time component, which adds to the incentive for the recipient to act. For example, the following message offering discounted Apple products implores quick action, since the stock is small.
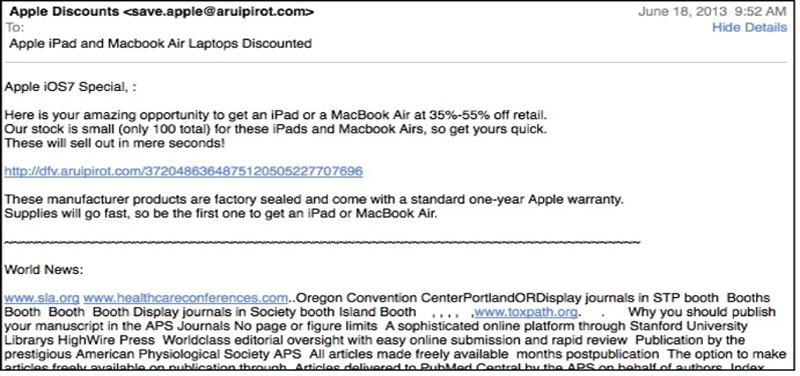
Since Apple products are in great demand and are expensive compared with its alternatives, an unwary recipient might be tempted by this invitation. There are several troubling aspects of this email offer.
First, the date of the email is June 18, 2013 and the lead in sentence of the email is Apple iOS7 Special, with some interesting punctuation. The use of a comma and a colon is different. However, the MacBook Air does not run iOS: that is strictly for the mobile platforms in the Apple family, such as the iPhone and iPad. Further, iOS7 had not yet been released in June, with a scheduled fall 2013 release date. These discrepancies raise serious questions about the validity of this email.
Enticingly, the email offers a very large discount, but the discount is variable from 35% to 55%. So which is it: 35%, 55%, or something in between? The email author(s) might think this range lends credibility to the offer, since it implies that they have legitimately purchased iPads or MacBook Air computers at varying prices, which is why the discount off of retail might vary. A reader might be tempted to interpret the range the same way. But, here is the thing: the legitimate supply chain does not sell these products at varying prices, so this range of discounts just seems strange in this context.
Finally, the email states that the supply is quite small. This is probably one of the most telling elements of the email: if the offer were legitimate, even with knock-off reproductions of the products, why would the offer be emailed to millions of recipients over large geographic areas? Someone who really had 100 iPads to sell would be better off to find local buyers. That would increase the probability of verified payment, eliminate shipping costs, and avoid customs and other tariffs.
An important point to note in examining this email message is the random text at the bottom of the message: this text, scrapped off news feeds, is designed to confuse the spam-detection software systems. By greatly increasing the number and complexity of the words included in the message and by increasing the variation of the content, automated detection of spam is reduced in accuracy. However, a quick visual inspection of the email reveals the random text and alerts the recipient to this trick, which would not be needed for a valid email. Interestingly, sometimes the random text can be placed well below the actual text of the message to reduce the chance that the person receiving the email will actually see the text.
A variation on the Invitation Message is to urge the recipient to take his or her place of recognition in exclusive societies. For example, the following invitation message combines an appeal to vanity with a warning about it being a final notice:

This message is probably the most unprofessional looking email one could ever imagine, particularly for one that claims to be from a prestigious source of professional individuals. There are odd spaces in words, the name of the “Managing Director” is not capitalized, and the formatting is simply ugly. The return address of “refi-isnow.us” is suspect as well, since it bears little resemblance to a publishing company. But it uses words that can entice the unwary: “exclusive,” “final notice,” and “premier source.” Further, it includes a presumably prestigious New York City address, on the 15th floor as well, leading those not familiar with New York City to potentially be impressed. Those who take the time to look up the address discover that it is six story building, making the 15th floor an extravagant detail indeed.
It is clearly a scam—and a quick search on the internet confirms that status—but the interesting inclusion of links makes it dangerous. The first “Click Here” in light blue is a hot link: it is a clickable link that, if selected, would take you to a website. You cannot tell simply by looking at the “Click Here” words where the link might take you, and therein lies the danger. Then, there is the entire (run-on) sentence in light blue: “Be 100% Up to Date in your Industry Get noticed today be happy you did it tomorrow !,” which is also enabled as a hot link. Again, you have no way by simply looking at it to see where it would take you. And finally, there is the hot link after the words “To unsubscribe,” helpfully labeled “click here:” Again you have no way of knowing where that link would take you. The range of options is endless: it could take you to a terrorist recruitment site, a site that would launch malicious software (such as viruses) into your computer, or other equally inappropriate places. Later in the book, we will go into how to see what the actual link is, but for now, you just need to know that you should not click on any link you do not understand completely.
The Offer of Money
In this type of malicious email, the recipient is directly offered money. Typically, the details are very sparse, as in the example shown below, but the offer sounds sincere and urges the recipient to act quickly in order to take advantage of the offer.
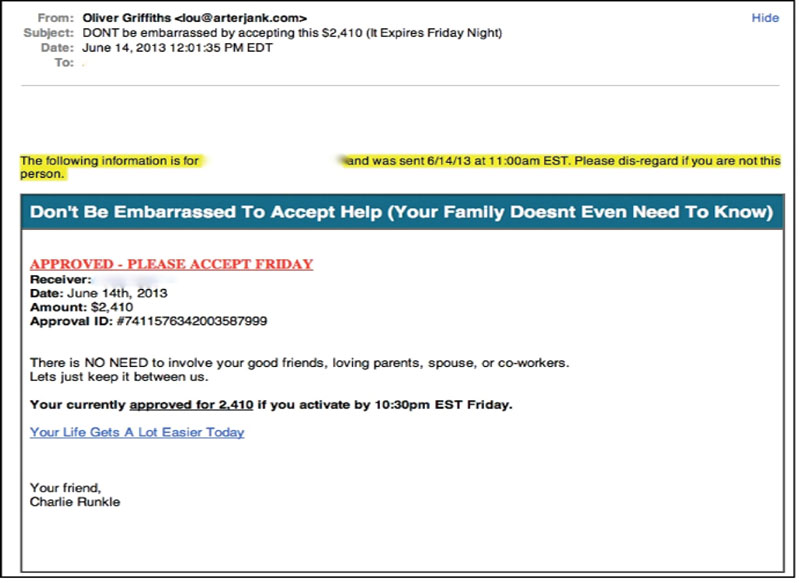
The first element in this email that draws our attention is the subject line, which contains several interesting features. The subject line reads: “Don’t be embarrassed by accepting this $2,410 (It Expires Friday Night).” There are three action elements in this subject: emotion, a lure or attraction, and time.
The emotional element is evoked by the use of the phrase, “Don’t be embarrassed.” A gut level reaction from a normal person would be indignation, followed closely by a desire to prove the implication wrong. This is the same emotional response that is triggered in adolescents when they dare each other to do something. The use of the word “embarrass” casts an aspersion on the reader, implying that the reader is so insecure that he or she might be embarrassed at their state of being or worth. Without thinking, an immediate response is to react in order to counter that implication, to prove that the recipient is not at all embarrassed. This emotional aspect is powerful enough that one sees it often in malicious emails.
There is also an element of conspiracy: no one else needs to know, it can be a secret. This enticement is followed by the promise that the recipient is already approved, with an officious looking approval id, and an underscored point that it will make the recipient’s life a lot easier, almost immediately.
The lure or attraction in this case is the money. It is not a huge amount but it is not trivial either. It is enough to get the recipient’s attention. The wording is obscure as well: the use of the phrasing “accepting this $2,410” sounds like the money might be offered by a wealthy donor or grant agency. There is no implication that this might be a loan or other type of credit—it just sounds like someone is offering to give away $2,410. And who would turn away from free money? Money is very useful in this life and the average person can find a lot of ways to spend an extra two thousand dollars.
The time component is a deadline that reinforces the emotional impact of the message. The deadline screams at the person to act fast before the good luck evaporates. The day that this message was received was, not coincidentally, Friday. The pressure created by this deadline increases the emotional imperative to act on the message.4
All of these elements are duplicated and reinforced by the content of the email. The emotional aspect is reinforced by the parenthetical comment “Your Family Doesnt Even Need To Know.” This also speaks directly to those who might be working themselves to death to keep their family in food and clothing: a chance for a windfall would be very attractive. The official looking structure of the email reinforces the lure in two places while adding some impressive details, such as the Approval ID, an impressive looking 19 digit number. The time component is reinforced several times as well, most notably in the capitalized, red lettered, underlined exhortation: “APPROVED - PLEASE ACCEPT FRIDAY.”
Clues that this email might not be entirely legitimate also abound. For example, the name and email address in the From line do not match. One might wonder how an “Oliver Griffiths” came to have an email address of “Lou.” Then there is the name of the person who signed the email, “Charlie Runkle.” Three different names in this email are definitely questionable.
Another clue is in the numerous grammatical oddities. These include a hyphen in the word disregard, even though one is not needed, the lack of an apostrophe in the words “doesn’t” and “let’s,” the misspelling of the word “you’re” as “your,” and the use in closing of “Your Friend.”
And, finally, there is the question about the terms: is this a loan, a grant, free money, or what? Would the recipient be required to do work for the money? All these things are left unclear, a point which an unwary reader may not even notice.
The Alert
In The Alert, a recipient is warned that her account has been compromised and needs to immediately change their passwords and possibly other login credentials to keep their account information safe. An example is shown below, purportedly from Capital One. It looks very authentic, even using official Capital One logos. And it is very scary indeed, with the subject line of “Account Locked Notification” guaranteed to spike a recipient’s blood pressure. Close analysis, however, reveals it to be an entire fraud.

This example is much more carefully constructed than the previous examples. The use of the official logos, the structure of the email, the inclusion of the Log In button—all of these design elements come together to reassure the recipient that the email is legitimate. Thus, it takes a little extra effort to determine whether it is legitimate or not.
Let us start with the concept of the email. I do not have a Capital One account, so why would Capital One be sending me an email warning me about “unusual activity” in my account? It would be unusual to have any activity at all, considering that there is no account. Unless there was a problem with identity theft, which is a very real issue, there should be no account. Assuming we can rule out identity theft, the very concept of the email is a clue that it is not legitimate.
Moving on to the From line: it looks legitimate on its face, with the sender being identified as [email protected]. Just because it looks legitimate does not mean it is. Looking into the internals of the email, it turns out that the real From email address is from cafe24.com, which is a Chinese language website (how to actually do this will be covered later in the book). This discovery reinforces the most important element of detecting and combatting malicious email: do not believe what you see at first glance. Always dig deeper to find out what the truth of the matter is.
The email itself contains only a few suspect features. The links in the upper right hand corner lend an air of authenticity to the email, as does the body structure. However, there are some clues that all is not as it might seem. The use of the ® symbol in the subject line at the end of the “Account Locked Notification” is strange—why should a symbol that means something is registered, such as a trademark or slogan, be used next to a generic notification? This same strange use of official looking notation continues in the email body, with SM symbol appended to Capital One Online. While Capital One does indeed offer online banking, much like most other banks today, their Service Marked offering is called Capital One 360, not Capital One Online. This is fairly esoteric knowledge that not everyone would have, but it is still worth keeping in mind.
The body of the message is not poorly constructed. There is really only one grammatical error that leaps out, but it is associated with a word that would be highly unusual to be included in this type of message, if it is to be legitimate. That is the word “kindly,” which in this email is not capitalized even though it begins a sentence. Also, the use of “kindly” in this context is not normal usage and just seems off. If this was a legitimate email, it should not be necessary to beg with someone to kindly perform an action, particularly if online access to their funds had been suspended.
The sentence then concludes with, “so we can complete your security update.” This sentence is contextually different. The email first states that access to the account has been suspended due to unusual activity, but then changes to a security update process. These are two completely different processes and combining them in one very short email really raises suspicions. But it is a clever construction: by first raising the fear level of the recipient and then by offering a quick fix, the probability that a recipient will actually click on the link to “fix the security” increases.
The use of links embedded in the email seems like something a reasonable sender would do, and in fact, legitimate emails include them all the time. They are dangerous though, simply because what you see in a formatted message is only and exactly what the sender wants you to see. In this case, the sender has configured the presentation of the link to make it look like it goes to www.capitalone.com, which in fact is the legitimate website for Capital One, although they prefer users to go to the https version, which has encryption services enabled to protect the communications. Looking inside the email, we discover that the link does not in fact go to Capital One, but directs the person who clicks on the link to the website adinship.ch.
The term “phishing,” which is pronounced “fishing” (as in with a rod and bait), was introduced earlier. This email is a prime example of a phishing email: it is intended to lure the catch, which is the recipient, with the bait, which is the fear of losing money, to bite the hook, which is clicking on the link that will prompt the recipient to enter in all kinds of personal information, which will then allow the malicious sender to indeed compromise the recipient’s bank accounts.
Another example of a phishing email is the one pictured below. This variation is also very common. In this variant, the scare tactic is loss of email access and the bait is the ability to restore full access immediately by clicking on the link.

Again, this email looks at first glance like it might be authentic. That is a key to its success as a way to gather personal information from actual users. Effective organizations continually remind customers and users that these types of communications are never authentic and that users should never either believe the email or respond, either by replying or clicking on the link.
A particularly problematic version of this type of malicious message is illustrated by the following email that purports to be from Wells Fargo, another well-known financial institution.
This email does not include all the graphics and professional layout of the fraudulent Capital One email, but still it manages to look official enough, with a plausible return address, signature block, and lots of legal disclaimers. The danger here lies in the attachment. The text of the message is quite simple and direct: it asks the recipient, nicely, to “check the attached documents.”
This request is tempting from at least two perspectives. If the recipient is indeed a customer of Wells Fargo, the recipient may be tempted to open the attachment to see what information is being sent. On the other hand, if the recipient is not a customer, then the recipient may think that the information has been sent to the wrong email address by mistake. In that case, the recipient may be tempted to open the attachment out of curiosity, to see what the intended recipient’s financial situation might be, or altruistically, in an attempt to determine the correct end address for the material.
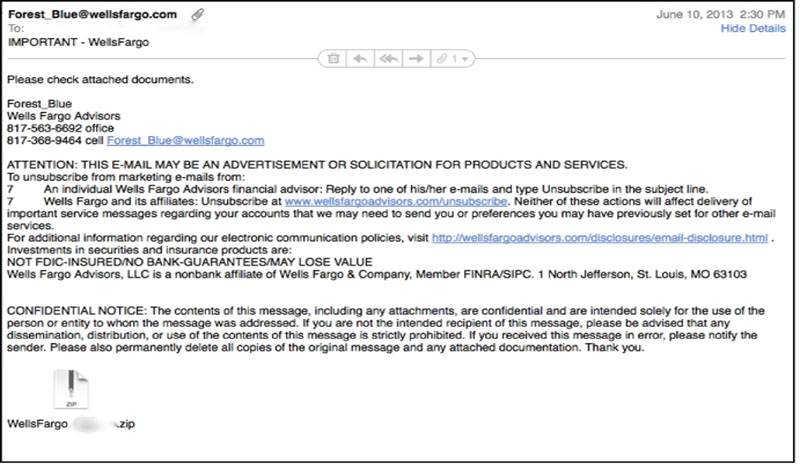
Opening the attachment is a very, very bad idea. In this particular case, the attachment contains malicious software which, when unzipped, would execute to install on the recipient’s computer. The use of a zipped file is particularly clever, as the compression assists in bypassing some protection software. In this instance, it was easy to see, simply by examination, that the file was a zipped file. This alone was enough to raise suspicions regarding the content of the actual attachment. In some instances of malicious attachments, it can be very difficult to identify the actual file type of the attachment. We will cover how to examine attachment types safely later in the book.
The Inside Scoop
In this type of malicious email, the sender offers to share special or secret information with the recipient that will help with health issues, financial issues, or other common problems. An example of this type of email is shown below, which offers to share with you a secret cure for high blood pressure and high cholesterol that the medical establishment does not want you to know about.

The typical telltales exist: a return address of “god,” abuse of bold and capitalization, fear tactics, and the appeal of hidden knowledge that the establishment does not want you to know. Many of these emails do not provide details: you have to click through to get the secret. And once they have your email, they can then make money selling it to other email marketers. Of course, they can also entice you to purchase alternative medicines, some of which are extremely dangerous. Some of the remedies being sold may even seem healthy and safe, since they are herbs. What some potential customers do not realize is that not all herbs are safe and that some herbs are only safe in certain circumstances. For example, a herb called yohimbe5 actually causes high blood pressure, so taking it would make a problem with hypertension worse, not better.
The Masked Email
Certain emails look legitimate because they seem to come from well-known sources. The email shown below claims to be from Match.com, a well-known online dating site. It is not however. It is fake, pretending to be from Match.com, trying to get you to click on the embedded links. The entirety of the email is shown: the only thing there is the link. But again, you do not know just by looking what is behind the link.

The Big Lie
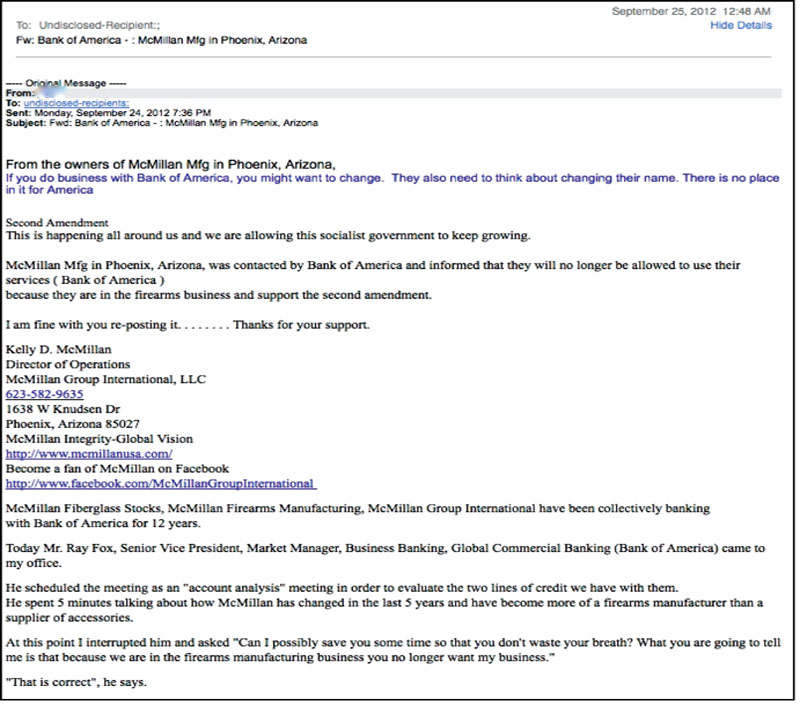
Chain emails sent and resent amongst people who know and trust each other can promulgate falsehoods into effects of staggering proportion. Typically, these emails take some situation, recast it in an overtly political tone, and play to the emotional sympathies associated with patriotism, religion, or family love. The email shown below is an example of a blatant falsehood being promulgated with a great deal of plausibility through trusted networks of friends and relatives. The interesting thing about this is the nature of the falsehood: the email blames the “socialist government” for a business decision that may (or may not) have occurred: the details are disputed.6 Independent of the veracity of the actual cancellation of the account, and the reasons for that if it indeed occurred, which is really none of our business, Bank of America is not a government organization, much less a socialist government organization. The entire purpose of this message can be interpreted as a subtle attack upon support for the government at the very real expense of Bank of America. It received enough publicity that the National Rifle Association investigated the story, including a statement from the Bank that it does “not have a policy that would deny banking services to entities because they are in the firearms industry. Bank of America has banking relationships with retailers, manufacturers and other related companies.”7 A search for similar stories on Google revealed “about 6300 results,” many of them with exactly the same language. The story reached an astonishing number of people, simply through the mechanism of sharing.
The Little Lie
Chain mails can also promulgate information that, while not nearly as malicious, can cause harm or at least potential for harm. The following email is an example of this type of nonsense.

This email passes along information purporting to be truth, but which in fact false. So what is the danger? Imagine being at an ATM and being held at gunpoint. How easy is it to remember your real PIN? Now imagine entering it in reverse. For many people, entering a PIN is a matter of muscle memory—you do not actually think about the numbers, but enter the PIN through memory of placement of numbers on the pad: top left, top right, middle middle, and bottom left for a PIN of 1359. Trying to enter that in reverse, particularly under pressure, would cause a normal person to have to pause and figure it out slowly, which would provide a clue to the robber that there was something amiss. Furthermore, if the robber was actually aware that no ATM in the United States currently employs this technology, then all the robber would have to do is watch the laboriously entered PIN fail and reverse it for a successful next attempt. Sure, in the scheme of things, this is probably not the worst thing in the world, but passing such small lies around wastes bandwidth and at the very least cause confusion.
Like Farming: In social media, a particularly noxious form of messaging is known as “like bait” or “like farming.” A typical “like bait” message contains some emotional appeal, such as for a lost child, a sick child, or some innocuous message such as “share if you hate cancer” or “I bet you won’t share this.” These messages are blatant attempts to drive up the number of people that are reached by certain pages. Social media companies, such as Facebook, counter these tactics with filtering technologies, but it is certain that with money from advertising at risk, the people engaging in these types of tactics will simply find new ways to spam.
Some of these like-farming efforts are potentially dangerous, simply because they abuse real images of people without consent, thereby exposing those people to potential harm. A particularly appalling example of this was the theft of a photo of a young girl named Katie, who was repackaged as “Mallory.” The post showed the photo along with the request: “This is my sister Mallory. She has Down syndrome and doesn’t think she’s beautiful. Please like this photo so I can show her later that she truly is beautiful.” The family discovered this abuse when people started emailing them about their daughter, after having discovered the connection online.8
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
