Chapter Six
Putting It All Together
Abstract
Examples of how to make simple effective visuals to explain complex technical issues are explained in this chapter, as well as a presentation from a real case.
Keywords
Compousssnd file; Court; Disk image; Expert testimony; Jury; Presentation; Technical illustration
• A real-case example of complicated technical issues explained in plain language
• How illustrations can be used to build on one another to aid in explaining complex technical issues
Introduction
Now that we have laid the foundation of how useful graphics can be when explaining a technical concepts to laypersons, let’s see what it is like when the rubber hits the road. This chapter is an example of a couple of graphics I have used to explain technical concepts, and then we will examine a presentation I have used to explain the digital evidence in a highly complex case using plain language and graphics.
Before we go any further through a disclaimer is needed. To my technical friends, it is important to remember that a graphic is similar to an analogy in a critical way; an analogy is very useful to explain something in plain language, but if you squeeze any analogy hard enough, it breaks down.
A graphic is the same. It can be used to explain something in our context at a high level, to get the main points across. If a graphic was used in an attempt to explain a technical concept on a computer system in its entirety, it would be huge, bloated, convoluted, and imminently confusing.
Example Graphics With Explanation
Let’s warm up with a couple of examples where a graphic is used to explain a single technical concept.
Explanation: How Browser Caching Works
As you surf the Internet, the Web browser you are using saves information to your computer in temporary storage. This process of saving Web pages and documents in temporary storage is called Internet browser caching or Web caching. The purpose of Web caching is to improve the experience of the computer user as he or she browses the Internet. When you visit a website, your Web browser will begin to save the information that you are viewing to your computer and also parts of a website that you are not viewing. So while you are at the home

page of a website, your browser might be temporarily saving the other pages also. The browser is anticipating that you will look at the other pages and images on the website, and it saves this information so that it will load faster when you navigate to them. The browser is attempting to make your experience better by downloading information you have not seen so that it loads very quickly when you navigate the website. However, information now exists on your computer that you may have never seen before.
Explanation: LNK (Link Files)
Link files are files that exist for the sole purpose of pointing to another file. For example, the icons on your desktop are Link files. Your software applications live inside of the folder Program Files, the Link files just allows you to access the program easily from the “Shortcut” (Link file) on your desktop. From your start menu, if you select “Recent Files,” the listed files are also Link files, allowing you to quickly get back to a file you were working on without having to navigate into your documents or other folders to find it.

Before the digital age, when library books had checkout cards in the back, those paper cards were used to keep track of certain information about the book they were associated with. When a book was checked out, the checkout card would be filed away so that the library could know who checked that book out, and when they did so.
The purpose of the checkout card is to store information about something else. You can think of a Link file in much the same way. A library card is used to store information about where the book is located, who is in possession of the book, when the book was checked out, and other information. A Link file is the digital equivalent to a library card, storing information such as the location of the file it is associated with, the time that file was created, when it was last accessed, when it was last modified, and to which user account that file belongs.
However, there will be instances where you need to explain something more complicated with a level of detail that is not suited to a single graphic. In these instances, it is best to include a series of graphics in a presentation that build on one another to explain the concept or evidence in a case. We will look at examples of explaining more technically complicated explanations, aided by graphics, in this chapter.
Case Example: Complex Technical Explanation
The following presentation in this example was used with great success in a case I worked on, and this presentation was created specifically for this particular case. I was hired as an independent expert by the attorney who was representing the defendant. According to the opposing experts in this case, the defendant was in possession of contraband files.
In many cases, the mere existence of files on a computer that someone should not possess is enough for the opposing side to make a case. However, the attorney in my case understood that there is a difference between having something on your computer, and knowingly possessing that item on your computer.
Think of it this way; do you know all the files on your computer at this very moment? How about every single item in your house?
Do you know, with absolute certainty, that the last house guest you had made sure to collect every single piece of clothing, phone charger, candy wrapper, or other items they brought in with them? Probably not. Think of that same scenario, and then complicate it many, many times over and it would then be consistent with the case we are about to examine.
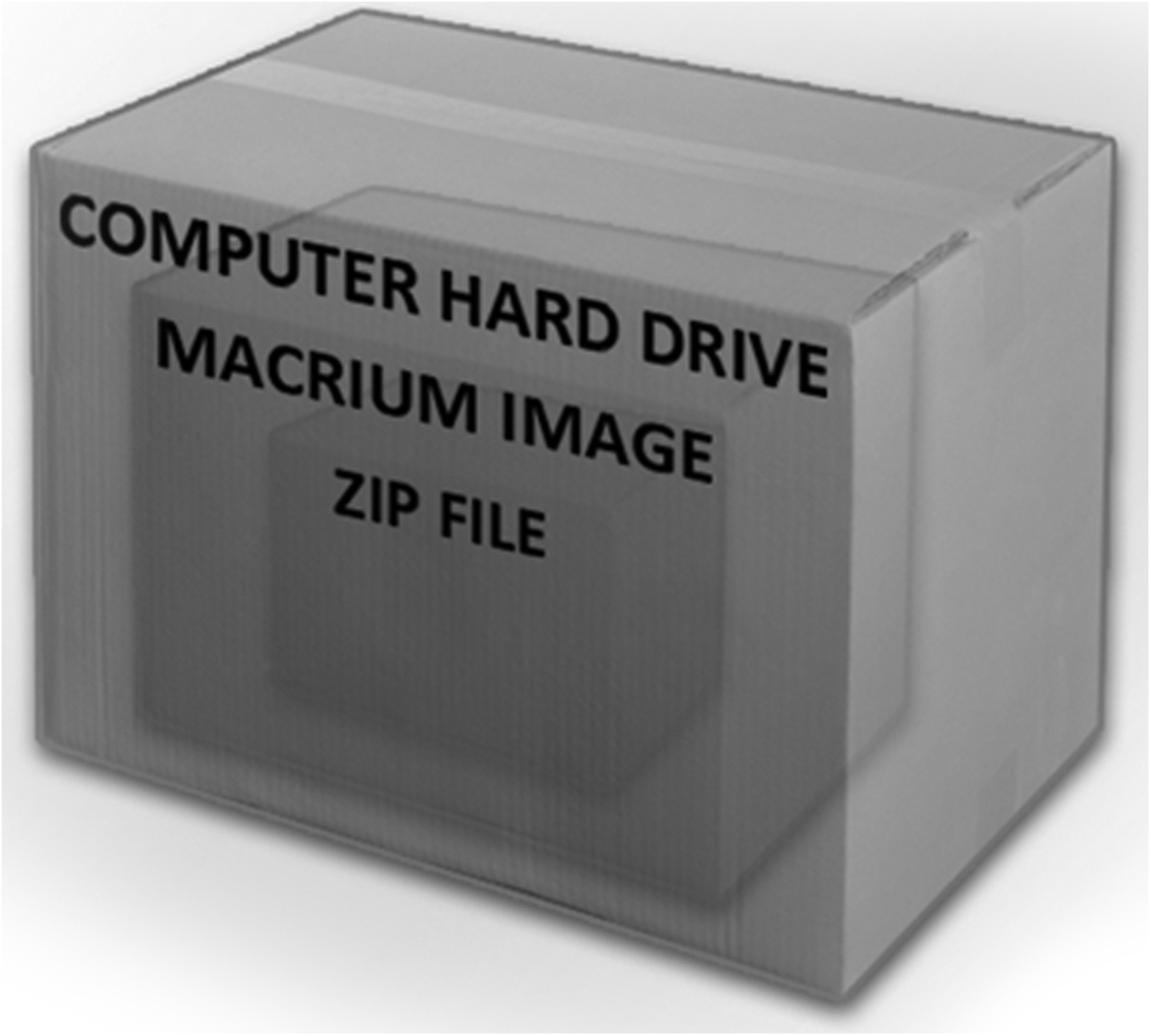
Computers contain many thousands of files. In this case, the contraband files only existed inside of one single file. On the computer hard drive running the Windows Vista operating system, there was a Macrium disk image, and buried inside of that Macrium disk image was a ZIP file, which is a compound file that can contain other files in a compressed format. Inside of that ZIP file were the handful of contraband files.
Explaining this scenario to a technical person with words alone can be complicated enough; now imagine trying to explain this with words only to laypeople on a jury. Well, this is where the power of illustrations comes in. We will examine the graphics slide by slide in the following presentation, and I am confident you will recognize how much easier it is to translate the complicated technical concepts efficiently and simply with graphics.
This example is where we will truly see why multiple graphics are often needed to explain more technical concepts. When dealing with laypersons, it is important to explain everything you need (without adding unnecessary complexity), with individual blocks of information building into the whole.
We have seen the following graphic before, and that is not by accident. The filing cabinet as file system is extremely helpful in my experience in aiding laypeople with the understanding of how data is generally organized on computer systems.
Plain Language Slide Explanation: On the computer hard drive is an operating system. The operating system on this particular computer is Windows XP. You can think of the data on your hard drive as a filing cabinet. Your operating system is the filing cabinet. Inside of that filing cabinet are partitions, such as C partition and D partition. These are the individual drawers of the filing cabinet. Inside of these drawers are individual folders. For example, your folders such as “My Documents,” “My Pictures,” and “My Music” would be inside of the C partition. Inside of the folders, such as “My Music,” would be individual files. The files inside of the “My Music” folder would be the individual song files of your favorite artists.

Now that we have explained how data is organized on a hard drive, we need to explain the next technical issue in this case, compound files. There are a number of points we need to make when explaining compound files, including their purpose, which is to compress numerous files into a single file both for convenient archiving and transmission. We also need to explain that unless browsed, a user cannot determine what is inside of a ZIP file. Of particular interest from this case example was the fact that the ZIP file was never decompressed, or extracted, on any of the computers (virtual or otherwise) in this case.
We are going to use our slide to convey the main point. We do not need the slide to explain every aspect of compression ratios and types related to compound files. The only pertinent information we need to transfer to our audience is that you cannot see the files inside of a ZIP file unless you do something with it.
Plain Language Slide Explanation: If I brought a backpack into your home and set it down, you would know that a backpack was now there, but you would not know what was inside of it. There could be one item inside, a dozen, or even hundreds of items. This is because the purpose of the backpack is to carry many things inside of one thing, the backpack. A ZIP does the same thing digitally. It allows for many files to be placed into a single container and moved all at once in a convenient package.
You would not know what was inside of my backpack unless you unzipped the compartments and browsed through its contents. Once again, this is the same with the ZIP file. Unless the files inside of the ZIP file are looked at individually, a computer user does not know what is inside.
With my backpack, I could have a patch on the outside that says “Backpack full of cookies,” but the inside could actually be filled with rat poison. With a ZIP file, the file could be named anything, “Pictures of Puppies,” for instance, but all of the picture files inside could actually be of cats.

We then need to explain what a disk image is. In this case, the program used to make the disk images was Macrium Reflect. The way the program was used in this case was to create Macrium. MRIMG (Mirror Image) files of entire hard drives for backup purposes. Macrium develops tools for complete disaster recovery in case of catastrophic hardware failure. Once again we want to keep the explanation as simple and concise as possible, so we are going to explain to the court the main issue as it relates to the case; this disk image is basically an entire computer contained inside of a single file.
Plain Language Slide Explanation: If you could take your entire home and everything inside of it, make an exact copy, and shrink it down to fit inside of a single box that would do great in case if there was ever a disaster and your home was damaged or destroyed. You could then just unpack your magic box, and your home and all of your things would be there just as if the disaster had never happened.
That is the point of creating a disk image. If your computer stops working because the hard drive begins to have problems or you get a particularly nasty virus, you can use the disk image to restore your computer back to its original condition. All your digital “home and property” are safely duplicated and saved inside of a single file.
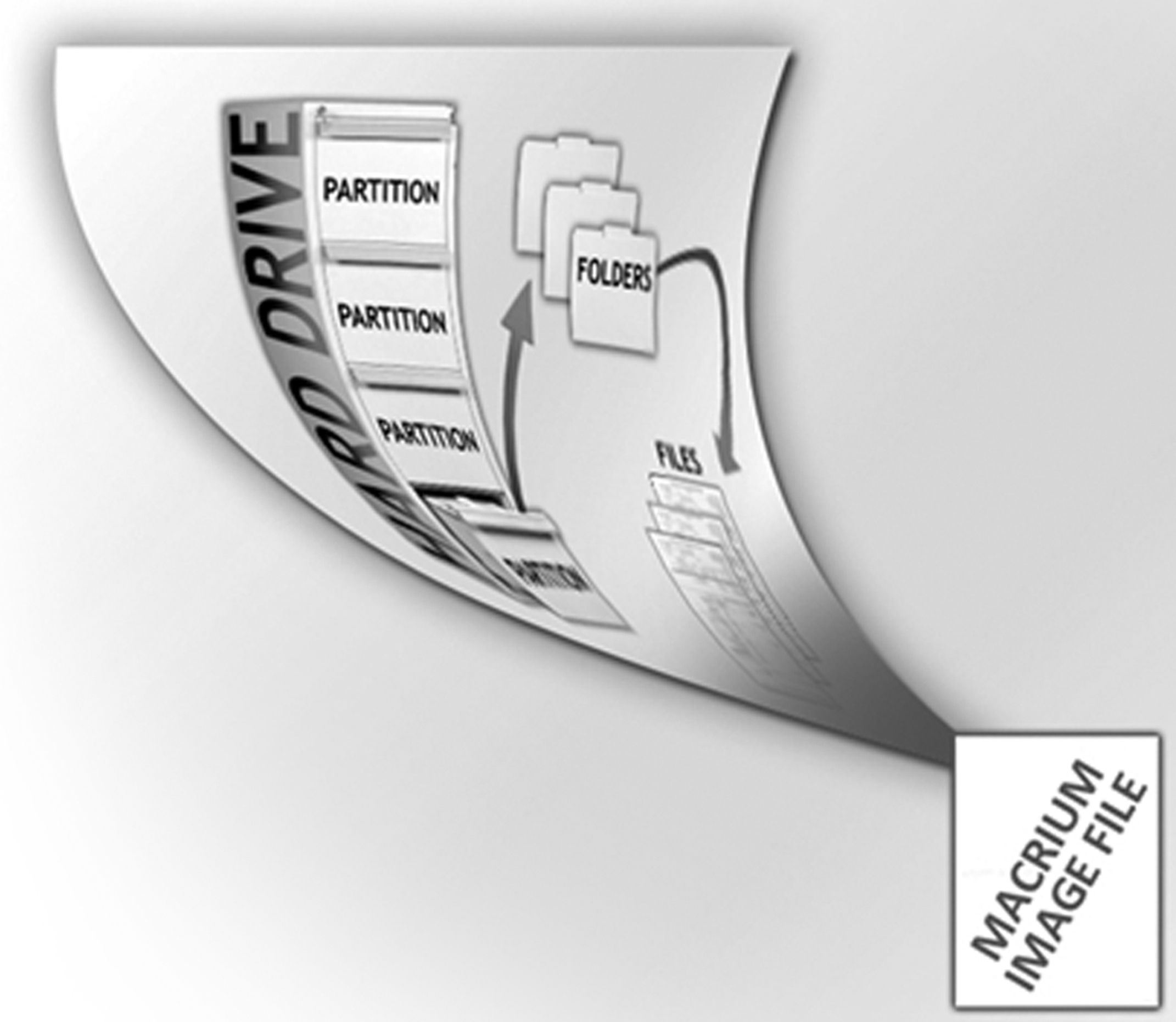
We then need to go back to the filing cabinet example we saw earlier, but this time, the files contained in the folders are of the Macrium disk images. In this case, there were multiple disk images inside of a folder. Only one of the multiple disk images contained the ZIP file with contraband in it. The rest were completely empty.
It was important in this case to note that there were numerous disk image files because inside of each image was a computer, further increasing the difficulty of actually knowing everything that was contained inside of each one. In reality, we may only have one computer that is of interest, but that one computer holds inside of it numerous other computers contained in disk images.

Plain Language Slide Explanation: Returning to our filing cabinet, we can see that inside of a folder are Macrium disk image files. Remember, each Macrium image file contains the contents of an entire computer.
We then need to explain what it would actually take for someone to be able to even get access to the data contained inside of the disk image file containing the ZIP file with the contraband images inside of it. It was claimed by the opposing side that the disk image file could be opened as a virtual machine as it existed on the defendant’s computer. This was incorrect, as the disk image would have to be converted to a virtual machine first.

Plain Language Slide Explanation: When you have a virtual machine, you are able to open a computer inside of a computer using special software. Many technology professionals use virtual machines as a part of their work. It allows for them to have a single computer that can open many other computers contained inside of single virtual machine files on that one computer. The benefit being that you could have one computer that has virtual machines of Windows XP, Windows Vista, and Windows 7 to test your software products or websites you are developing.
In this case, however, the files are disk images. While they are a computer contained inside of a single file, similar to a virtual machine, they are different. And the main difference as it relates to this case is that they cannot be opened using virtual machine software without having another special program to convert the disk image into a virtual machine.
There is no program on the defendant’s computer that would allow him/her to convert the disk image into a virtual machine, so he/she could not open the disk image containing the ZIP file with the contraband files inside on this computer at all.
We have made it clear that the disk image could not have been accessed by the defendant using virtual machine software. Instead, he/she would have to actually restore that disk image onto a new hard drive. Anyone with even a modicum of information technology experience will know that restoring a disk image to a hard drive is harder than just copying that data over to a new hard drive and installing it into a new computer. Issues related to the hardware in the computer, drivers for all of that hardware, and many other compatibility issues come into play. But as we have tried with every slide, we are going to keep the main thing the main thing and not delve into the rest.
The main thing for this slide is simple. The defendant did not have any other computer to restore the disk image onto in the first place.

Plain Language Slide Explanation: The way the disk image was made in this case means that it could not be opened with virtual machine software. In other words, the “computer” contained within the disk image file could not be opened with special software inside of the defendant’s computer. Instead, this disk image would have to be restored onto an entirely new hard drive. This means that he/she would either have to buy a new hard drive, or have one available, restore the disk image onto that hard drive, and place that hard drive inside of a computer that he/she had available or purchased. The data inside of this disk image is not something he/she, or anyone else, would have been able to access whenever they wanted to, as the process to even get access to the contraband files contained in the ZIP file on the disk image would require hours of work to access them.
At this point we have gotten through much of the technical information that it is critical to explain. Now we need to give our audience more perspective on how deeply buried within the computer’s file system these contraband files actually were. In my experience, having testified dozens of times as an expert witness in digital forensics, even the information we have given so far, which has been clearly explained, will be fuzzy in the minds of some. This is not a criticism on the intelligence of a jury, but simply an understanding that some people are not engaged with or not interested in technology. The information we are trying to explain is so far outside of their normal experience that it needs to be explained in multiple ways using real-life examples that they can easily grasp.
We have laid the technical framework, explaining compound files, disk images, and file systems. Now it is time to bring it down to the lowest level we can, and making sure that the audience understands the main point; the contraband files were buried deep and there is no evidence the defendant even knew about them, let alone opened or accessed them.
This slide is our different layers at the 10,000 foot level. We explain our computer and files as containers (boxes) this time, using this metaphor to drive to our final slides when we introduce the warehouse to drive the point home.

Plain Language Slide Explanation: A computer contains data, and so does a disk image file. As we have discussed, a disk image is a file containing an entire computer. A Zip file is also a container, which holds individual files. We can think of each one of these as a box. The contents of the box will be the data stored inside of the computer, disk image, and Zip file, respectively.
We need the audience to understand at this point that the ZIP file is buried deep in the file system, so let’s stack them inside one another.
Plain Language Slide Explanation: The ZIP file with the contraband files contained inside of it is buried deep on the computer system. Think of Matryoshka dolls, often called Russian nesting dolls, where we have a series of wooden dolls of decreasing size nested inside of each other. Each time you remove a doll, there is another inside, just smaller. The contraband files in this case would be inside of the smallest doll so to speak, they would not be on the outside for everyone to see. Looking at our slide, the contraband would be inside of the smallest box, the ZIP file, but this does not adequately explain how buried the contraband files are.
Continuing with our boxes, we are now going to enter the warehouse. I am confident all of our previous slides will make sense in the grand scheme now that we have gotten near the end of our presentation.
We need to explain that there are hundreds of thousands, if not millions, of individual files on a computer in this slide, as we will be introducing the disk image and ZIP files following this graphic.

Plain Language Slide Explanation: Think of your computer as a warehouse. Inside of that warehouse are boxes, and these boxes represent the files on your computer. If the warehouse in this slide was yours, would you feel that you truly knew the contents of each box? I know I would not. To know the contents of each box and be held accountable for those contents would be daunting, but the number of boxes in this warehouse is tiny compared to the number of files on your computer.
We then need to introduce the disk image file into our warehouse.

Plain Language Slide Explanation: In our warehouse of boxes, there is one particular box that is the disk image file. It is the glowing box left of center in the slide. Only one box inside of the warehouse of files contains contraband. But then we need to account for the ZIP file box, inside of that box.
Now we include the ZIP file as the smaller glowing box inside of the glowing box to drive home the “nesting” of that ZIP file containing the contraband as we previously described, just this time inside the “warehouse of files.”

Plain Language Slide Explanation: You see, the ZIP file box is inside of the disk image file box, which is inside of the warehouse. If you are unsure of your ability to identify all of the boxes inside of a warehouse this size, how about the boxes nested inside of each of the boxes inside of the warehouse? These nested boxes could increase the total number of boxes you could be held accountable for “knowing about” by a dramatic amount.
But even the example from our last slide does not do justice to the scenario in this case, and now we get to what the entire presentation has been leading to. We have to explain that the contraband files, contained in a ZIP file, are inside of a computer file system, contained in a single disk image file, which is itself contained on the defendant’s laptop’s file system. We have a handful of contraband files, contained in a box, contained in a warehouse inside of a single box, which is contained inside of another warehouse.

Plain Language Slide Explanation: Working from the outside in, we have our warehouse first. This represents the defendant’s computer. This is a warehouse with tens of thousands of files inside of it. Only one of those files is the disk image file in question. What we need to make sure to understand is that the disk image file is another entire warehouse of tens of thousands of files. Inside of the disk image warehouse is a single ZIP file. Inside of that ZIP file are a handful of contraband files.
Summary
At this point we have explained to the jury that the defendant would have to go through many steps to access the contraband files; it is clearly understood by all who would view such a presentation that these files were not in plain sight, not readily searchable, or otherwise easy to locate or access. These facts, coupled with other technical information in the case, show that there was no evidence of the contraband ever being opened or accessed was used by his/her attorney to aid in a good outcome for the defendant.
In this chapter we have looked at a complicated example from a real case that benefited greatly from illustrations in explaining technical issues in plain language to laypersons in a way that understands that they may lack the technical background to readily understand the material, but also respects their intelligence. With our explanations, it is important to remember that when acting as a subject–matter expert we must explain things as clearly and as simply as possible. If our audience is unable to understand the concept we are attempting to convey, we have likely failed at communicating in the most beneficial form. A good idea of how to explain a technical concept in plain language, a great metaphor or analogy, is really able to shine in many instances with the inclusion of an excellent illustration.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
