Once communication protocols are established, conversations can commence. The basic assumption of communication is that both a sender and a receiver exist and agree to an extent on protocol, proper grammar and syntax, and processing capability. The essential ingredient of communication, however, is the message itself. Without the message, there can be no semantic agreement; with the message, understanding can begin.
Internet protocols provide the basis for NDC applications communication, as we saw in Chapter 5. But it takes more than protocols to facilitate the meaningful sharing of information. While protocols give some form to datacom capabilities, it is the purpose of communication that ultimately gives shape to the design of semantics and the desire for conversation.
Within a competitive, ceaselessly innovative fitscape, the nature of conversations and the semantic milieu in which they are conveyed may be in a state of constant flux. Some general communication models seem to be long-lived, however, and may therefore be universal, at least insofar as NDC is concerned. Some, too, transcend the protocols upon which they are built, giving credence to the original design principles and motivations behind the OSI 7-layer conceptual model.
What is the purpose of software? Beyond the broadest and most general sense, this question must be answered for each case, despite the risk of intellectual marginalization. Software does indeed have a purpose, though that purpose is served only through market or design requirements specific to the individual projects.
Although a larger software teleology may escape our view, we know that software is a player within various fitscapes—economically, socially, and technically—and must obey any common rule set governing these dynamic positive feedback systems, to the extent that such rules can be discerned. If we can say that software evolves, it must be constrained by the forces inherent in the system in which it evolves.
If we view the three metatrends—Moore's, Metcalfe's, and Gilders's laws—as forces that shape the software fitscape and are made manifest in specific terms, we might also speculate that any larger teleological vector for NDC software is directed by these three laws. Opportunities explored through NDC innovation can be considered as a function of the interaction of these three forces.
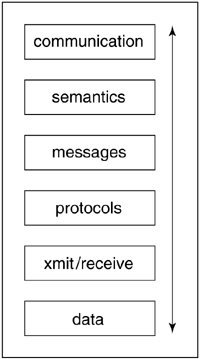
In essence, the NDC fitscape has given rise to several forms of messaging that are based on standardized protocols that are universally applicable in application development. Communication, which represents not only the transmission of information but the receipt and ultimate understanding of it as well, can be viewed in a manner akin to the OSI 7 conceptual model, as shown in Figure 6.1.
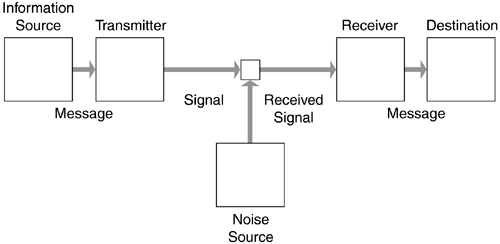
The point above cannot be overemphasized: communication represents both transmission and receipt (and understanding) of information. This may seem obvious, but the point needs be made precisely, if only because the theories of information upon which we rely for modern datacom—which tend not to include transmitter and receiver in the same equation—are descriptive of an approach that could be classified as a “transmission model” for communication. Shannon's information theory gives rise to a conduit metaphor for communication: the source translates thoughts into words and sends the words to a receiver, which then translates them into thoughts.
The notion of transmission and receipt, and the underlying metaphor of placing an object in a container and sending it through a conduit of sorts, may be misleading, however. Even after a message is sent, I presumably still have it; the receiver, who removes the object from the container, has in fact received a copy. This model also raises a question it was never intended to address: how does the object get into the container, and get out? More precisely, how do we put meaning into words, and how does someone else extract that same meaning from those words?
This semantic puzzle is as inherent in node-to-node communication as in head-to-head communication. By design, a transmission model does not deal with meaning, but communication represents receipt and understanding of information as well as transmission. Ironically, Shannon's The Mathematical Theory of Communication[1] therefore leaves the question of communication itself out of the equations, even while the ability to transmit messages is essentially enabled—another paradox of the Network Age.
Shannon's brilliant work provided the means to quantify and facilitate data communication in real-world environments that regularly include noise, signal decay, and erroneous attributes, a foundation upon which higher-level protocols could be built. Given these protocols and the necessary message transmission capabilities, patterns of messaging grew, eventually giving rise to something in the way of genuine communication. Several winners in the messaging fitscape bear examination—patterns of messaging that are useful, common, and universal.
From the genesis of the ARPANET through the modern Internet and wireless, mobile nodes, the one common thread has been message passing. Even during the dramatic growth of the Internet since the mid-1990s, the single most popular slice of the programming pie has been the essential passing of messages. The very notion of interoperability, the battle cry of Web Services models, is based on the simple concept of putting the object in a container so as to make it a message. That, in fact, is the essence of Web Services model: converting human-readable Web pages into messages. Once data is objectified and transformed into messages, the successful transmission of those messages to one or more receivers (which may also include routing at or above the OSI 7 transport layer) can be undertaken.
Message passing is the basis for all data transfer, which includes RPC as well as executable objects. Once a node decides to access or share data that is not in memory but physically within reach (that is, outside a high-speed bus or proprietary data link mechanism), a message must be passed. While there are many interesting and useful variations, that simple concept is the fundamental constituent of NDC. (Formalization of message passing has been one of the key enablers of parallel processing systems as well, though not necessarily those tied to NDC communication protocols.)
It should be clear that the approach provided by Shannon's simple model is not as robust or useful as those that drive datacom today. Indeed, as we've seen in the discussions of protocols, there is much in the way of error correction, stochastic analysis, and protocol-laden work that takes place on behalf of the message, with more to come as new Internet standards emerge. But message passing will remain NDC's essence, our anchor in a sea of NDC change.
The passing of NDC messages can take many forms. Just as the type of data that is transmitted is germane to the operation, so is the form of transfer. Broadcasting a message, for example, is a much different implementation than a one-to-one transfer. And timing naturally affects the nature of messages. A complex set of implementations arises from the simple transmission model, based on three general message considerations:
Data transformation
Synchrony
Routing
These three considerations tend to differentiate the various flavors of message passing patterns that are commonly used today.
In general, NDC messages are used in one of two ways, as shown in Figure 6.2: a node sees either a shared memory, the access semantics for which are not significantly different from those used for local memory, or various “cookings”—manipulations and transformations—of the messages themselves; which become the means of creating a shared memory. Within each of these general patterns are further specializations with respect to the message considerations listed above.
The reification of messages at each point along the way is essential, from a conceptual perspective, as a function of the cooking points at which message transformation operations occur. In general terms, the flow of messages over time is not bound to a specific or solitary operation or ordering at any of the potential cooking points. Nor is there any specific limit on cooking-point operations. As such, data-type classification or transformation, for example, can theoretically take place at a number of stops along the way, even in a synchronous message passing environment. The same can be said of potential routing operations.
Recall that the Transport level can provide a number of protocol-level options, including levels of message reliability, nonrepudiation, trustworthiness, and security. Operations can be glued atomically and often can be executed asynchronously, that is, if causality is not implied or required, two similar operations can transform an arbitrary message at two completely different stops along the message conduit. The exercise of such choices is both the art of NDC programming and the bane of framework providers who would sugar Deutsch's Fallacies with interface candy.
Paradoxically, XML is the culture in which we now grow framework-independent data, and in which we can implement operations specific to frameworks dependent on document types. The concept of data-type transformation is probably more accurately described as document-type transformation; data-typing on a language level is orthogonally germane to the data transformation that occurs in message passing, and RPC alludes operationally to that relationship. But the transformation of data on a per-document basis is operationally essential to message passing on the Internet and the nodes that feed it. For example, the encryption and decryption of a message requires sophisticated data transformations that must occur in a reliable, trustworthy, ordered manner. That cooking will, by definition, occur at multiple points distributed over time and resources. Some of these transformations may be more reliable than others, and that in turn affects overall application performance.
Regardless of whether a distributed shared memory view is available, interoperable data may require transformation in order to facilitate processing within a given framework. Beyond encryption, other examples of document transformation include Java-to-XML processing, metadata wrappers and containers, and style sheet transformations with approaches like XSLT.
Custom document generators benefit many NDC projects. (The term document in the context of NDC may include various artifacts.) The wide variety of activities in any software development effort leads to the production of documents in many forms. Whether it be a source programming language file, the compiled version of the source, the control files that facilitate compilation, or the messages generated by the running program, the concept of document transformation is essential. From the perspective of developing code alone, document transformation allows a higher degree of automation. The benefits of this approach can include enhanced provisioning, model-driven programming, and a higher degree of consistency driven by systematic document generation enforced at key points.
With ongoing XML extension, standardization efforts, and the growing availability of tools supporting those standards, it has now become possible to generate multiple types of documents. For example, XML document-transformation technology has made it easier to develop custom code generators in application development projects. As such, the interoperability of platforms and frameworks is theoretically enhanced.
Different types of computers handle data in different ways. One of the most common transformations of network data is from the representation used by the application into a form suitable for transmission over a network, and vice versa. Encoding/decoding data for transmission is sometimes called marshalling/unmarshalling. This terminology comes from the RPC world, in which the client node invokes a procedure with a set of arguments that must then be brought together and appropriately ordered (marshalled) to form a network message.
The big-endian and little-endian transformations—named for a tale from Gulliver's Travels, in which two communities were in conflict over which end of an egg to broach for effective consumption—are a good example of the kinds of data transformations that must occur if interoperability among heterogeneous networked nodes is to be possible. The Motorola 680x0 is an example of big-endian architecture, the Intel 80x86 an example of little-endian architecture; internal storage and processing of data is different on the two different architectures. Take, for example the hexidecimal integer value 0x12345678. The Motorola's big-endian architecture sends that value as 12.34.56.78., whereas the Intel's little-endian architecture sends it as 78.56.34.12. Both are “correct,” depending on the assumptions made; as with the communities in Swift's novel, it is a religious matter and neither approach is sacred.
Another reason for marshalling is that application programs are written in different languages, and—even more insidious—there may be more than one compiler for a given language. Since compilers may have a fair amount of latitude in how structures are represented in memory, such as how much padding they put between fields, the simple transmission of a structure from one node to another requires marshalling; even if both nodes are of the same architectural family and the programs are written in the same language, the compiler on the destination node might align the structure's fields differently.
In addition to marshalling and unmarshalling, other forms of message transformation are required in NDC. To the extent that a message consists of an assembly of structured symbols, document transformation is synonymous with message transformation; the absolute structure of a message is arguably a proper subset of all possible document types, depending on document taxonomy. But it is safe to say that a message can enjoin transformation as can a document. As such, document-transformation technologies can be viewed as message filters as much as processing and storage options.
The instantiations of NDC messaging constitute an active, evolving fitscape. For example, from a Java perspective, relevant document-transformation/messaging technologies include those provided by the Java XML Pack from Sun among which are the following:
Java API for XML Messaging enables NDC developers to send and receive XML messages based on SOAP 1.1 with attachments.
Java API for XML Processing enables developers to process XML documents by providing support for the XML processing standards SAX, DOM, and XSLT.
Java API for XML Registries provides a uniform and standard Java API for interacting with XML registries such as UDDI and ebXML Registry/Repository.
Java API for XML-based RPC enables Java technology developers to build Web applications and Web Services incorporating XML-based remote procedure call (RPC) functionality according to the SOAP 1.1 specification.
Java API for XML Binding will provide for Java-to-XML and XML-to-Java document transformations.
The Java XML Pack provides an essential bridge between portable behavior (as exemplified by Java objects) and portable data (as encoded by XML). This combination is essential for NDC interoperability going forward, and is one of the cornerstones of next generation NDC development, whether it be Web Services, the Semantic Web, or other organic approaches covered later in this book.
As discussed in previous chapters, NDC message passing employs two basic forms of synchrony: synchronous and asynchronous. An asynchronous message-passing model has traditionally been applied to loosely coupled nodes, generally found in WANs, whereas a synchronous message passing model is more of an idealization in which some amount of timing information about the network is assumed to be known (such as the upper bounds of message delay). Strictly speaking, an asynchronous model is less realistic in modern NDC environments. Synchronous message passing has a long list of implementations and is somewhat easier from a programming standpoint, giving rise to less complexity. But asynchronous message passing may offer advantages that can make the extra implementation effort worthwhile.
The RPC mechanism, long the message passing modality of choice in NDC, serves as one of the simplest and best examples of synchronous message passing. With XML-RPC, the forerunner of SOAP, much in the way of NDC development can be facilitated with what has to be one of the simplest interface approaches currently available. XML-RPC is a specification and a set of implementations that allow software running on disparate operating systems on nodes running in various environments to make procedure calls over the Internet. Using HTTP for transport and XML for encoding, designers made XML-RPC as simple as possible while still allowing complex data structures to be packaged as synchronous messages.
An XML-RPC message is an HTTP-POST request; the body of the request is in XML. A procedure executes on the server; the value it returns is also encoded in XML. Procedure parameters can be a number of data types, including scalars, numbers, strings, and dates, and can also be complex record. List structures are also supported. An XML-RPC request might appear as follows:[2]
POST /RPC2 HTTP/1.0 User-Agent: Frontier/5.1.2 (WinNT) Host: betty.userland.com Content-Type: text/xml Content-length: 181 <?xml version="1.0"?> <methodCall> <methodName>examples.getStateName</methodName> <params> <param> <value><i4>41</i4></value> </param> </params> </methodCall>
The first five lines in the example are the header. The format of the URI in line 1 is not specified. (In the example, the URI is /RPC2, which tells the server to route the request to the RPC2 responder). The URI line might be empty (a single slash) if the server handles only XML-RPC calls. If the server handles a mix of incoming HTTP requests, the URI helps route the request to the program on the server node that handles XML-RPC requests. A User-Agent and Host must be specified; in the example, these are Frontier/5.1.2 and betty.userland.com. The Content-Type is text/xml. The Content-Length must be specified and must be correct.
The balance of the XML-RPC message is the payload, which is encoded in XML and consists of a single <methodCall> structure. The <methodCall> must contain a <methodName> subitem, which is a string containing the name of the method to be called. The string may only contain identifier characters, upper- and lower-case A–Z, the numeric characters, 0–9, underscore, dot, colon, and slash.
It's entirely up to the server to decide how to interpret the characters in a methodName. For example, the methodName could be the name of a file containing an executable script, the name of a cell in a database table, or the path to a file contained within a hierarchy of folders and files. If the procedure call has parameters, the <methodCall> must contain a <params> subitem. The <params> subitem can contain any number of <param> entries, each of which has a <value>. A <value> can be scalars. Types are indicated by nesting the value inside one of a set of tags, which includes the <i4> tag, which indicates a four-byte, signed integral value.
The response format is just as simple. An example of a response to an XML-RPC request follows:
HTTP/1.1 200 OK Connection: close Content-Length: 158 Content-Type: text/xml Date: Fri, 17 Jul 1998 19:55:08 GMT Server: UserLand Frontier/5.1.2-WinNT <?xml version="1.0"?> <methodResponse> <params> <param> <value><string>South Dakota</string></value> </param> </params> </methodResponse>
Unless a lower-level error occurs, the response header will always return 200 OK. The Content-Type is text/xml. Content-Length must be present and correct.
The body of the response is a single XML structure, a <methodResponse>, which can contain a single <params>, which contains a single <param>, which contains a single <value>. The <methodResponse> could also contain a <fault>, which contains a <value>, which is a <struct> containing two elements: one named <faultCode> (an <int>) and one named <faultString> (a <string>). A <methodResponse> cannot contain both a <fault> and a <params>.
XML-RPC is a simple, extensible technology that provides for synchronous message passing in a heterogenous networked environement. Note that marshalling and unmarshalling for XML-RPC are assumed to occur as a function of transmission and receipt of messages.
From the simplicity of XML-RPC, NDC messaging runs the gamut to the complextities of problems addressed by interfaces like JAXM. JAXM messages also use XML, conforming to the SOAP 1.1 and SOAP with Attachments specifications, which prescribe the format for messages and also specify some things that are required, optional, or not allowed. With the JAXM API, developers can create XML messages that conform to the SOAP specifications by making Java API calls.
An XML document has a hierarchical structure with elements, subelements, sub-subelements, and so on. Many JAXM classes and interfaces represent XML elements in a SOAP message and have the word “element” or “SOAP” or both in their names.[3] There are two main types of SOAP messages: those that have attachments and those that do not. The parts of the SOAP message are referred to as just that.
A SOAP message may include one or more attachment parts in addition to the SOAP part. The SOAP part may contain only XML content; if any of the content of a message is not in XML format, it must occur in an attachment part. If a SOAP message is intended to contain an image file, for example, the message must have an attachment part for it. Note than an attachment part can contain any kind of content, including data in XML format.
The following outline shows the high-level structure of a SOAP message that has two attachments, one containing plain text and one containing an image.
I. SOAP message
A. SOAP part
1. SOAP envelope
a. SOAP header (optional)
b. SOAP body
B. Attachment part (content is plain text)
C. Attachment part (content is an image file)
JAXM provides the AttachmentPart class to represent the attachment part of a SOAP message. A SOAPMessage object automatically has a SOAPPart object and its required subelements, but because Attachment Part objects are optional, they must be created and added accordingly.
So far, JAXM is just a tad more complex than XML-RPC. But one of the distinct features JAXM provides is asynchronous messaging opportunities, which brings messaging providers into the discussion. All JAXM messages are sent and received over a connection, which can go directly to a particular destination or to a messaging provider. A messaging provider is a service that handles the transmission and routing of messages and provides features not available to direct connectors to the ultimate destination; the service works behind the scenes to keep track of messages and see that they are sent to the proper destination or destinations.
One of the most frequently touted benefits of using a messaging provider is that an application need not be aware of it. NDC developers can write applications that conform to the JAXM APIs, and the right things happen. For example, when a message is sent by a call to the ProviderConnection.send method, the messaging provider receives the message and works with other parts of the communication infrastructure to perform various tasks, depending on what the message's header contains and how the messaging provider itself has been implemented. The result is that the message arrives at its final destination without the NDC application being aware of any of the details involved in accomplishing the delivery.
JAXM also enables programmers to plug in additional protocols that are built on top of SOAP. A JAXM provider implementation is not required to implement features beyond those required by SOAP 1.1 and SOAP with Attachments, but it is free to incorporate other standard protocols, called profiles, that are implemented on top of SOAP. The ebXML Transport, Routing, and Packaging V1.0—Message Service Specification, (ebXML TR&P), for example, defines levels of service that are not included in the two SOAP specifications. A messaging provider that is implemented to include ebXML capabilities on top of SOAP capabilities is said to support an ebXML profile. A messaging provider may support multiple profiles, but an application can use only one at a time and must have a prior agreement with each of the parties to whom it sends messages about what profile is being used.
A messaging provider works continuously. A JAXM client may make a connection with its provider, send one or more messages, and then close the connection; the provider stores each message and then sends it, perhaps resending a failed transmission until it is successfully delivered or until the threshold for the number of resends is reached. The provider also stays in a waiting state, ready to receive any messages that are intended for the client, and it stores them for forwarding when the client connects again. In addition, the provider generates error messages as needed and maintains a log in which messages and their related error messages are stored.
Clearly, the messaging provider approach gives rise to an asynchronous message-passing model in NDC environments. When a messaging provider is used, a message can be sent to one or more intermediate destinations before going to the final recipient; the delay in passing the message can be indeterminate. These intermediate destinations, called actors, are specified in the message's SOAPHeader object. Assume, for example, that a message is an incoming Purchase Order. The header might route the message to the order input desk, the order confirmation desk, the shipping desk, and the billing department. Each of these destinations is an actor that will take the appropriate action, remove the header information relevant to it, and send the message to the next actor. The default actor is the final destination, so if no actors are specified, the message is routed to the final recipient. If intermediate actors are specified, time considerations may be implicit—for example, a service-level agreement for input of an order may be implicit for the business in question—but the asynchronous nature of the message is a given.
As we have seen, asynchronous messaging is inherently more complex than synchronous messaging. With synchronous messaging, an atomic success/failure model is implied: either the message was transmitted successfully or it was not, and that information is known immediately upon completion of the exercise. Not so with an asynchronous messaging model. But the asynchronous model also provides opportunities for document transformation that are not available with the synchronous approach.
The message provider approach also creates the opportunity for greater reliability in message passing, depending on the characteristics of the nodes involved. If, for example, an intermittently connected mobile node is the originator of a given message, a message provider approach would be much more reliable than XML-RPC.
Routing is one of the most interesting aspects of NDC messaging. Recall from the OSI 7-layer conceptual model that routing is the job of the Network layer. Navigating the dynamic pathways of the modern Internet is still functionally addressed in the lower datacom protocols of OSI 7. Beyond the network layer, routing is what is also meant in the context of message passing.
In the specific case of ebXML TR&P, routing functions beyond those offered by TCP/IP are provided by the ebXML framework (Electronic Business using eXtensible Markup Language), is sponsored by the United Nations (UN/CEFACT) and OASIS, is a modular suite of specifications designed to enable global enterprises of any size in any country to conduct business over the Internet.[4] OASIS is an international, not-for-profit consortium that designs and develops industry standards specifications for interoperability based on XML.[5] Routing at the network protocol layer provides the bedrock for message passing by identifying pathways wherein two (or more) nodes can be connected by a virtual circuit. The routing articulated by ebXML TR&P, which layers well above the OSI 7 Network layer, provides a more application-level flavor of routing, designed for more sophisticated NDC applications.
Consider a “Publish and Subscribe” class of applications. OSI 7 Network layer protocols do not generally provide a means wherein messages may be distributed to members of a list of parties, nor is anonymity necessarily an optional mechanism. By extending the routing metaphor above the OSI 7 stack, ebXML TR&P describes a means for message routing that is extensible for such purposes. Based on interoperability sensibilities and existing in tandem with legacy routing technologies, ebXML provides a more application-oriented set of interfaces that allow developers to implement Publish-and-Subscribe applications.
The earlier example of simple message passing with XML-RPC requires less intellectual investment on the part of the developer than does ebXML. But implementing something like Publish and Subscribe using XMP-RPC would be considerably more difficult because the developer would be required to not only provide a dynamic attachment capability à la SOAP but to implement something in the way of asynchronous message passing capabilities as well. (Publish and Subscribe, by definition, requires more than a simple RPC mechanism in order to function.) At its core, ebXML is based on XMP-RPC, as is SOAP, but using only unextended XML-RPC as the basis for NDC programming would be a limiting choice, depending on the type of application being developed. It's the classic “pay me now or pay me later” question; avoiding the initial cost of learning ebXML, for example, in favor of the less challenging option of XML-RPC, may result in a faster prototype, but will likely result in a longer and more difficult development cycle. Goff's axiom applies here—it all depends on the context.
Most often we think of messages as having one sender and one receiver. The bulk of messages do not fall into that category, however, if we include broadcast communication. In the past two decades the number of broadcasters has increased a hundredfold, if cable television (and satellite) options are any measure. While not NDC communications per se, these digital signals nevertheless betray a clear indication of the growth and penetration of NDC-capable technologies and also serve as an example of message transmission: one sender, multiple receivers.
In NDC, broadcast and multicast can provide flexible one-to-many transmission options. Strictly speaking, three types of transmission options are available on the Internet:
Unicast: typical one-to-one
Broadcast: global one-to-many (passed on by the router)
Multicast: local one-to-many (stops at the router)
Think of broadcast as one amplified voice that everyone in the world hears, whereas multicast is more like a private party, where only those sitting at a particular table hear what is said. Broadcast NDC systems present many unique challenges for network management. These systems generally have both high bandwidth requirements (up to 20 Mbps per channel) and stringent QoS requirements for reliable, guaranteed delivery; some transmissions can be worth millions of dollars an hour. Some proprietary (that is, nonstandard) solutions exist in this space, but generally speaking, a standardized, reliable broadcast mechanism does not yet exist on the Internet.
TCP/IP based multicast has been utilized by some standard application frameworks such as Jini network technology and, to some extent, Project JXTA. For the most part, however, the standards communities have yet to meaningfully address the general problem of broadcast on the Internet.
One useful perspective on any arbitrary network can be gained by examining the nature of its message passing and the opportunities for message transformations, or cooking points, it provides. The Web Services approach to NDC applications is, at its heart, a set of message passing specifications. To the extent that messages are marshalled and serialized, document transformation technologies can also be viewed as message transformation entities.
A transmission model serves as the presumptive mechanism for NDC message passing, implying both a sender and a receiver who share some semblance of shared processing capability. NDC message passing can be very simple or very complex, depending on the needs of the application and the preference of the developer. Regardless of the developer's messaging choice, a standardized, reliable broadcast specification is not currently available for implementation.
| 1. | C. E. Shannon, The Mathematical Theory of Communication (Urbana: University of Illinois Press, 1948). |
| 2. | Source: www.xmlrpc.com, the home page for the XML-RPC community. |
| 3. | An element is also referred to as a node, not to be confused with an NDC node. |
| 4. | See www.ebxml.org for more information. |
| 5. | See www.oasis-open.org for more information. |