APPENDIX B
Mobile Security Penetration Testing Tools

Similar to client/server applications and web applications, mobile applications and HTML sites need to be tested from a security penetration perspective. Penetration testing is a blend of art and science, where each tester brings their unique skills and experience for the art, and manual and automated testing and tools for the science. To help with the latter part, this appendix provides a list of a few free penetrating testing tools helpful with auditing mobile applications, mobile networking, and mobile HTML sites.
This list is not exhaustive, but just a start in providing resources for the new emerging area. An updated list can always be found at www.isecpartners.com/mobile_application_tools.html.
Mobile Platform Attack Tools and Utilities
True mobile-specific security tools are still somewhat rare; however, as of 2009, security research into mobile applications and mobile platforms has increased significantly, resulting in a number of tools dedicated entirely to this area.
Manifest Explorer
![]() Author: Jesse Burns
Author: Jesse Burns
![]() Location: www.isecpartners.com/mobile_application_tools.html
Location: www.isecpartners.com/mobile_application_tools.html
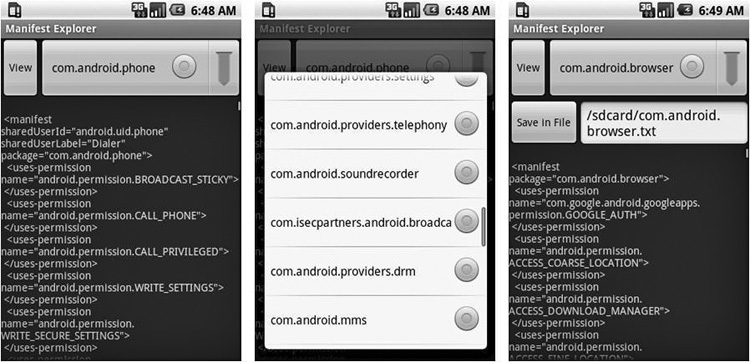
Manifest Explorer is a tool that can be used on any device using the Google Android operating system. On Android, every application must have an AndroidManifest.xml file in its root directory. The AndroidManifest.xml file does a few things, which are all explained at http://developer.android.com/guide/topics/manifest/manifest-intro.html. From a security perspective, the file is most interesting because it defines the permissions the application must have to other applications or protected parts of the API. The Manifest Explorer tool can be used to review the AndroidManifest.xml file, specifically the security permissions of the application, and to give the pen-tester a view of the basic attack surface of the application. The attack surface is a critical starting point to understand the security of the application and how it affects the mobile device itself.
The tool is quite simple to use. As shown in Figure B-1, the tool lists all the system’s applications, allows the user to select one, and then displays the contents of the AndroidManifest.xml file that pertains to the selected application. A menu option enables saving the extracted manifest, so the testers can read it more comfortably on a PC for manual inspection.
Figure B-1 Manifest Explorer main screen, displaying the com.android.phone manifest
Package Play
![]() Author: Jesse Burns
Author: Jesse Burns
![]() Location: www.isecpartners.com/mobile_application_tools.html
Location: www.isecpartners.com/mobile_application_tools.html
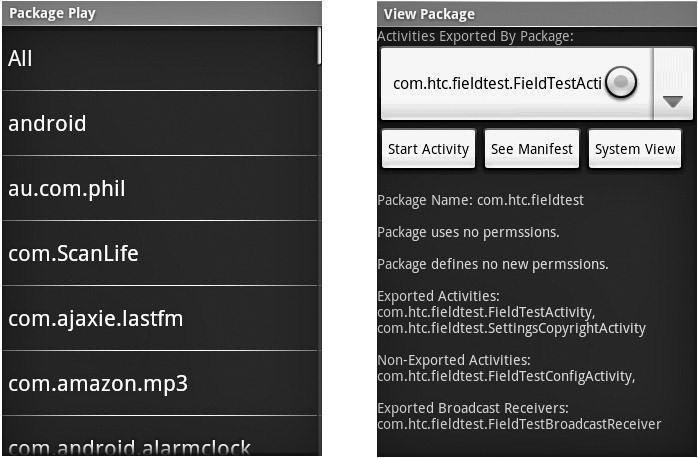
Package Play is a tool that can be used on any device using the Google Android operating system. Package Play shows the user all installed packages on the mobile device. This helps the user in the following ways:
![]() Provides an easy way to start exported Activities
Provides an easy way to start exported Activities
![]() Shows defined and used permissions
Shows defined and used permissions
![]() Shows Activities, Services, Receivers, Providers, and instrumentation, as well as their export and permission status
Shows Activities, Services, Receivers, Providers, and instrumentation, as well as their export and permission status
![]() Switches to Manifest Explorer or the Settings application’s view of the application
Switches to Manifest Explorer or the Settings application’s view of the application
Figure B-2 shows a screenshot of Package Play. The first step with Package Play is to select the package to examine. By reviewing the list, the user may see software they did not originally install, such as software preloaded by the hardware manufacturer but not included in the open-source Android OS.
Figure B-2 Package Play listing packages and exploring package activities
Intent Sniffer
![]() Author: Jesse Burns
Author: Jesse Burns
![]() Location: www.isecpartners.com/mobile_application_tools.html
Location: www.isecpartners.com/mobile_application_tools.html
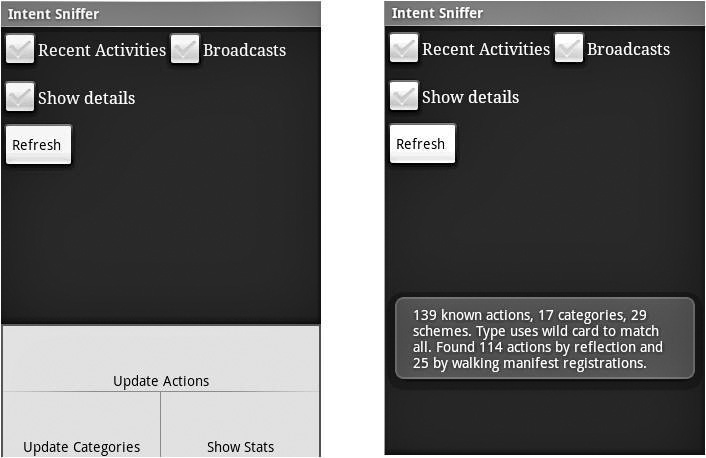
Intent Sniffer is a tool that can be used on any device using the Google Android operating system. On the Android OS, an Intent is a description of an action to be performed, such as startService to start a service. The Intent Sniffer tool performs monitoring of runtime routed broadcasts Intents. It does not see explicit broadcast Intents, but defaults to (mostly) unprivileged broadcasts. There is an option to see recent tasks’ Intents (GET_TASKS). Activities’ Intents are visible when started. The tool can also dynamically update Actions and Categories. Figure B-3 shows a screenshot of Intent Sniffer.
Figure B-3 Intent Sniffer output
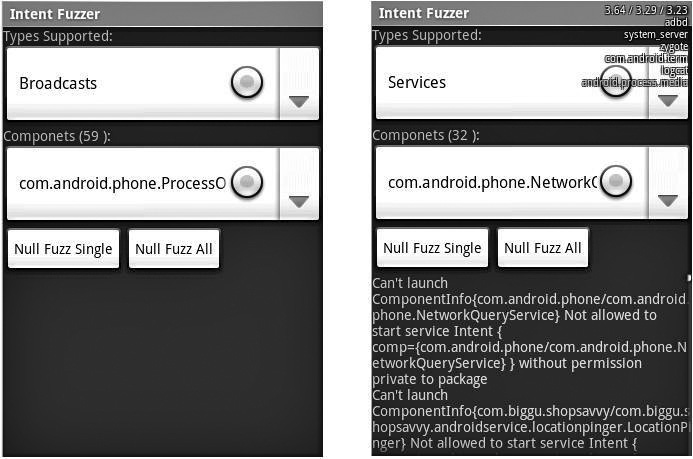
Intent Fuzzer
![]() Author: Jesse Burns
Author: Jesse Burns
![]() Location: www.isecpartners.com/mobile_application_tools.html
Location: www.isecpartners.com/mobile_application_tools.html
Intent Fuzzer is a tool that can be used on any device using the Google Android operating system. Intent Fuzzer is exactly what is seems—it is a fuzzer. It often finds bugs that cause the system to crash as well as performance issues on the device. The tool can either fuzz a single component or all components. It works well on Broadcast receivers, and works average on Services. As for Activities, only single Activities can be fuzzed, not all of them. Instrumentations can also be started using this interface, and Content Providers are listed, but are not an Intent-based interprocess communication (IPC) mechanism. Figure B-4 shows a screenshot of Intent Fuzzer.
pySimReader
![]() Authors: Zane Lackey and Luis Miras
Authors: Zane Lackey and Luis Miras
![]() Location: www.isecpartners.com/mobile_application_tools.html
Location: www.isecpartners.com/mobile_application_tools.html
pySimReader is a tool to write out arbitrary raw SMS PDUs to a SIM card. It is a modified version of Todd Whiteman’s PySimReader code. Additionally, debugging output has been added to allow the user to view all Application Protocol Data Units (APDUs) that are sent between the SIM card and pySimReader. The requirements for this tool are Windows XP with Python 2.5 and the ACS ACR 38t SIM reader. Here’s a sample usage:
# Start the app
python pySimReader.py
# To run with debugging mode enabled
# (This will print out all APDUs sent between the SIM and
pySimReader)
python pySimReader.py -d
Browser Extensions
Several add-ons to the Firefox browser are available that are useful for security testing, web development, and mobile device simulation. Often, we find it easier to do the testing of mobile HTML sites from a desktop browser than from a mobile device or simulator. Here are a few of our favorites.
WMLBrowser
![]() Author: Matthew Wilson
Author: Matthew Wilson
![]() Location: https://addons.mozilla.org/en-US/firefox/addon/62
Location: https://addons.mozilla.org/en-US/firefox/addon/62
The WMLBrowser Firefox add-on simulates WAP browsing by parsing and rendering pages written in the Wireless Markup Language. This is useful for performing testing of mobile sites with a WAP component, because you can leverage all of your existing Firefox tools and network proxies—and of course you use an actual keyboard. Note that some sites will not deliver WML content without detecting the correct User-Agent.
User Agent Switcher
![]() Author: Chris Pederick
Author: Chris Pederick
![]() Location: https://addons.mozilla.org/en-US/firefox/addon/59
Location: https://addons.mozilla.org/en-US/firefox/addon/59
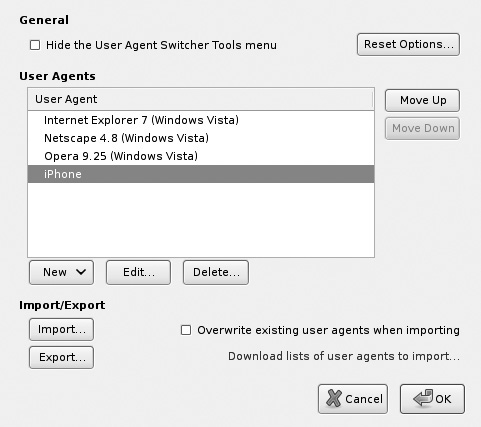
Because some sites make decisions on what content to show you by examining your browser’s “User-Agent” header, you may sometimes want to trick the server into thinking you’re a different browser (such as a WebKit-based mobile browser like on the iPhone, Android, and Symbian). The User Agent Switcher Firefox add-on allows you to change your User-Agent header at will, from a list of User-Agent strings that you define (see Figures B-5 and B-6). This can allow you to interact with mobile sites from the comfort of your own desktop browser.
FoxyProxy
![]() Author: Eric H. Jung
Author: Eric H. Jung
![]() Location: https://addons.mozilla.org/en-US/firefox/addon/2464
Location: https://addons.mozilla.org/en-US/firefox/addon/2464
Figure B-5 Available User-Agent profiles
FoxyProxy is a proxy management tool that can use multiple proxies at one time, and decide which to use based on user-definable rules. For example, if you want to use your regular Internet connection for all sites except one particular mobile site that you want to run through WebScarab, you can create a rule for that site, specifying which proxy to use. This saves time and keeps requests to other sites from cluttering your WebScarab logs. It’s also one of the few proxy extensions for Firefox that receives timely updates.
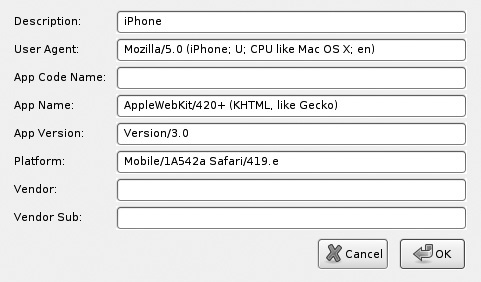
Figure B-6 Details of a User-Agent to simulate an iPhone browser
TamperData
![]() Author: Adam Judson
Author: Adam Judson
![]() Location: https://addons.mozilla.org/en-US/firefox/addon/966
Location: https://addons.mozilla.org/en-US/firefox/addon/966
TamperData is similar in functionality to tools such as WebScarab; the difference is that it runs within the browser itself, obviating the need for changing network settings. Although not as robust as most web application security proxies, it’s a good tool for quickly tampering with or removing POST parameters, or bypassing client-side validation routines. Figure B-7 shows an example of an intercepted request in TamperData.
Live HTTP Headers
![]() Authors: Daniel Savard and Nikolas Coukouma
Authors: Daniel Savard and Nikolas Coukouma
![]() Location: https://addons.mozilla.org/en-US/firefox/addon/3829
Location: https://addons.mozilla.org/en-US/firefox/addon/3829
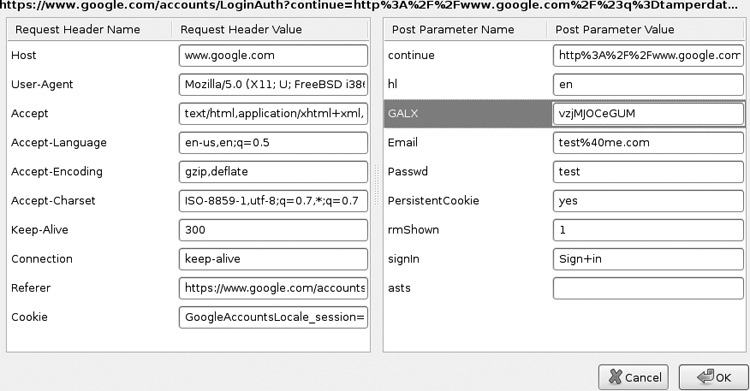
Figure B-7 Editing a request with TamperData
Live HTTP Headers simply shows you the request/response pairs for every request your browser sends, including cookie data, content types, and caching settings—an excellent way to quickly see what’s going on behind the scenes without firing up a proxy or network-sniffing tool. Figure B-8 shows sample HTTP request and response headers.
Web Developer
![]() Author: Chris Pederick
Author: Chris Pederick
![]() Location: https://addons.mozilla.org/en-US/firefox/addon/60
Location: https://addons.mozilla.org/en-US/firefox/addon/60
The Web Developer add-on is one of the most popular extensions for Firefox, and rightfully so. It allows for easily changing form fields from POSTs to GETs, selectively disabling JavaScript, and removing form length limits, as well as provides a number of other tools useful for security testing and web application development.
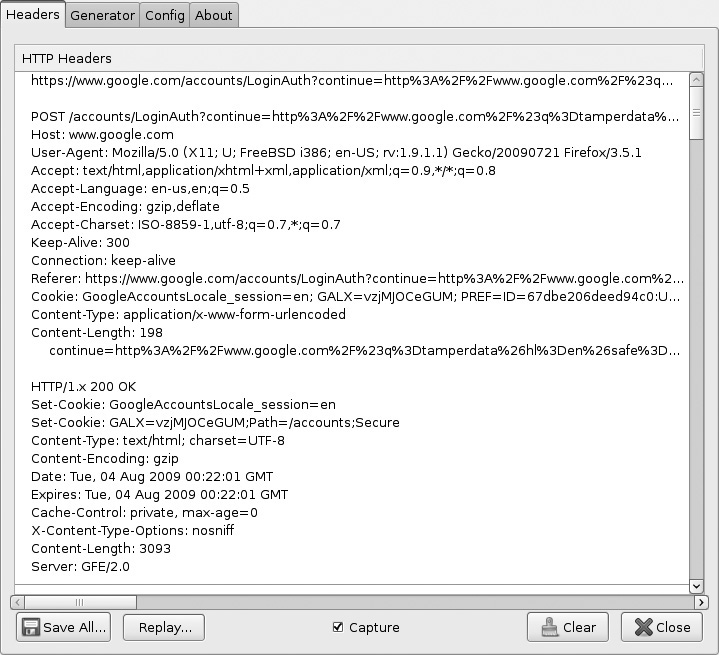
Figure B-8 Examining raw HTTP headers
Firebug
![]() Authors: Joe Hewitt and Rob Campbell
Authors: Joe Hewitt and Rob Campbell
![]() Location: https://addons.mozilla.org/en-US/firefox/addon/1843
Location: https://addons.mozilla.org/en-US/firefox/addon/1843
Firebug allows for the inspection, manipulation, and inline editing of the source of a rendered page. This can be used to remove elements, to delete or change blocks of JavaScript, and to just get a feel for the application’s structure. Another add-on that usefully extends the functionality of Firebug is “Firecookie,” which allows for cookie viewing and editing for the site you’re inspecting (see Figure B-9).
Networking Tools
Similar to web or client/server application testing, mobile application security also benefits from networking tools. The following is a list of the network tools that may assist in a mobile security test.
Wireshark
![]() Authors: Gerald Combs et. al.
Authors: Gerald Combs et. al.
![]() Location: www.wireshark.org
Location: www.wireshark.org
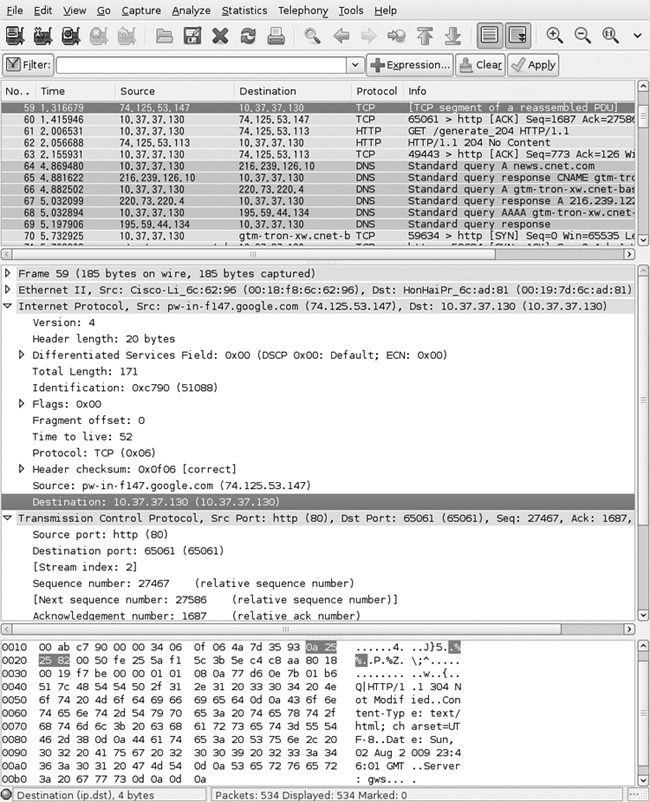
Wireshark is a packet capture and analysis tool widely used in the security, network, and systems administration industries and the software development industry. It can either capture packets live or analyze those stored in standard formats, such as libpcap output files. It analyzes packets from OSI layers 2–7, giving information on Ethernet frames, IP packets, and higher-level protocols such as HTTP. In a mobile development context, tools such as Wireshark are useful for ensuring that clear-text data is not being sent over the network, as well as for debugging when networking code doesn’t behave as you expect.
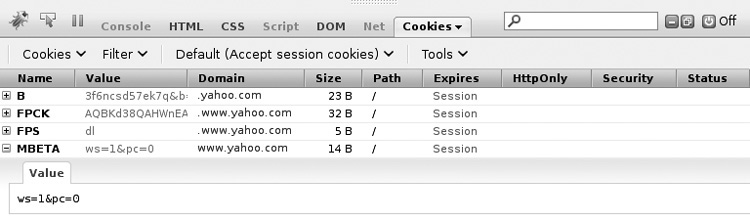
Figure B-9 Editing cookies within Firecookie
Wireshark knows how to parse a great many protocols, including HTTP, various chat services (such as AIM and XMPP), DNS traffic, and voice data (such as that sent over SIP/RTP), displaying detailed information in a tree-structured interface. It is a valuable tool for anyone working with computers to be familiar with—people attacking your software most certainly will be! Figure B-10 shows an example of the types of traffic captured by Wireshark.
Tcpdump
![]() Location: www.tcpdump.org
Location: www.tcpdump.org
An old standard for network packet analysis, tcpdump allows for the capture of network packets using user-defined filters, only capturing traffic matching specific patterns. Whereas tools such as Wireshark give more vivid insight into the content of network packets, tcpdump is lighter weight, available on many systems, and suitable for performing packet capture on systems where a graphical environment isn’t easily available (such as Unix servers). Sometimes, rather than running a tool such as Wireshark on your local network, running tcpdump on the server that you’re trying to test against can be an easier way to capture data, without having to deal with any messiness such as ARP spoofing (http://en.wikipedia.org/wiki/ARP_spoofing). Simply run the tool on the server as follows (you will need root access to do this):
tcpdump –s0 –ni eth0 –w mycapture.pcap tcp and port 80
tcpdump: listening on ath0, link-type EN10MB (Ethernet)
capture size 65535 bytes
^C136 packets captured
240 packets received by filter
0 packets dropped by kernel
This will capture all packets sent and received by the eth0 interface on TCP port 80 (HTTP), listening until interrupted with CTRL-C. Output will be stored in “pcap” format in mycapture.pcap. When finished, you can copy the resulting pcap file to a local desktop system for further analysis or filtering with Wireshark or another parsing tool.
Figure B-10 Wireshark analyzing live network traffic
See the main page for tcpdump for more information on its command-line options and filter expressions (http://www.tcpdump.org/tcpdump_man.html).
Scapy
![]() Author: Philippe Biondi
Author: Philippe Biondi
![]() Location: http://www.secdev.org/projects/scapy/
Location: http://www.secdev.org/projects/scapy/
Scapy also performs packet capture and analysis, but it can also actively generate traffic, encapsulated and transformed in many ways. It is something of a Swiss army knife of packet manipulation, and can be useful for writing tools to send specifically crafted packets or to watch for specific traffic patterns, responding with particular packet transmissions. Knowledge of Python is necessary to work with Scapy; however, Python is a relatively easy language to understand for most experienced developers.
Web Application Tools
The following tools can help test mobile HTML sites by allowing the developer to modify content after it leaves a browser or local application, but before it is sent to a remote server. This approach is very commonly used in penetration testing and QA, and can be quite convenient to a developer as well.
WebScarab
![]() Author: Rogan Dawes
Author: Rogan Dawes
![]() Location: www.owasp.org/index.php/Category:OWASP_WebScarab_Project
Location: www.owasp.org/index.php/Category:OWASP_WebScarab_Project
WebScarab is a free open-source network proxy maintained by OWASP. It performs interception of HTTP traffic, allowing for changing it in transit, replaying it in different ways, fuzzing, and more. This is useful to mobile developers for testing the results of changing traffic in-flight or for simply seeing what HTTP requests a given application makes, along with the content of server replies. Monitoring and altering traffic at the network level can be far more convenient than changing your code or using debugging output. Additionally, for mobile HTML sites, you can use this approach to perform attacks on the server as well—for instance, inserting malicious script into various parameters and removing validation tokens in transit. Several other proxy tools also perform similar functions to WebScarab, all with their different strengths and weaknesses. A few of these are Burp, gizmo-proxy, and Paros.
To use WebScarab, simply run it on a desktop machine, configuring it to listen on a network interface accessible to your mobile device, rather than the default of 127.0.0.1. Then, configure your mobile device’s proxy settings to use the IP of your desktop machine, port 8008. By default, WebScarab only gathers information—by using the Proxy | Manual Edit | Intercept Requests option, you can edit requests before their transmission on the network (see Figure B-11).
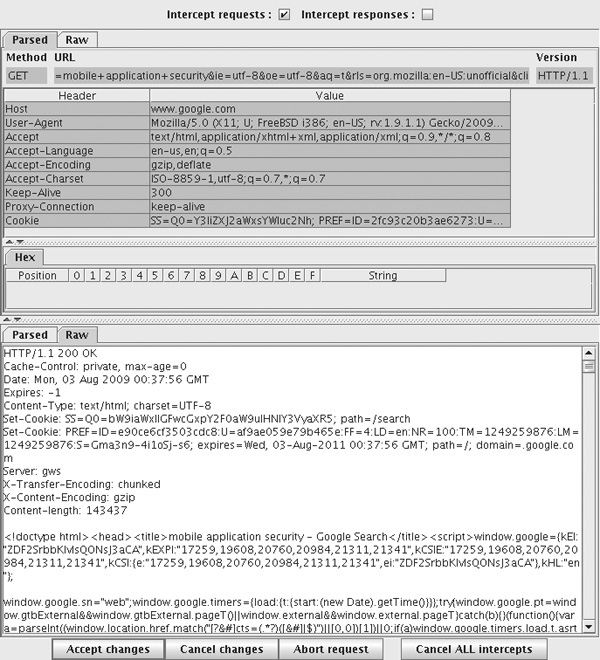
Figure B-11 WebScarab’s traffic interception mode
One caveat with using such tools is that because a primary function of SSL is to prevent middle-person attacks, an error or warning will (or at least, should) be thrown whenever a client tries to access an SSL-enabled URL through the proxy. To solve this, one option is to create your own SSL Certificate Authority, create a new SSL certificate for the HTTPS server that you want to impersonate, and install the Certification Authority (CA) certificate on the mobile device. Note that on the iPhone, new certificate installation can only be done on the mobile device itself, not the emulator.
In the event that you need to do this for multiple servers, you can automate the individual certificate-signing process using CyberVillainsCA (www.isecpartners.com/cybervillainsca.html).
This will dynamically create a new certificate, signed by your Certificate Authority, for every site you visit.
Gizmo
![]() Author: Rachel Engel
Author: Rachel Engel
![]() Location: code.google.com/p/gizmo-proxy/
Location: code.google.com/p/gizmo-proxy/
If WebScarab is a bit heavy for your taste, Gizmo strips down and simplifies the concept. Gizmo includes CyberVillainsCA—it will generate a unique CA certificate upon first use, which you can then import into your browser or other certificate store. Requests are navigated with basic vi editor keybindings: j/k to move up and down in the request list. “e” edits a request, and “s” sends.
One of the useful features Gizmo offers is the ability to send requests directly to commands, or even to your favorite text editor, before sending the request along. This can be done by specifying your default shell and commands to be executed—the request itself will be loaded into a file referred to by the environment variable “BUF”, which can then be sent to another process. The text output of this process (“stdout”) will be returned into the bottom frame. For example, if using a Unix machine, one can enter the following as the parsing commands:
grep –v Cookie: $BUF
to remove the cookie header from the request.
Fuzzing Frameworks
Fuzzing “frameworks” are intended to be general-purpose tools abstract enough to be adapted to apply to fuzzing many protocols or file formats, generally consisting of generators (which create random data), transforms (which convert data in various ways), and logic for writing out or sending fuzzed data. This flexibility can require a greater initial investment to come up to speed; however, if you find yourself having to write fuzzers repeatedly (and as a security-conscious developer, we hope you will), it can be worth the effort to learn a framework rather than write new fuzzers from scratch.
Peach
![]() Author: Michael Eddington
Author: Michael Eddington
![]() Location: http://peachfuzzer.com
Location: http://peachfuzzer.com
Peach is a modular fuzzing framework written in Python, consisting of data models (the structure of the file or protocol to be fuzzed), state models (what to do with the resulting fuzzer output), and publishers (how to make your data interact with an OS or server). Additionally, it contains monitoring components to watch for application crashes, pop-ups, and other events, as well as hooks into debuggers.
Sulley
![]() Authors: Pedram Amini and Aaron Portnoy
Authors: Pedram Amini and Aaron Portnoy
![]() Location: http://code.google.com/p/sulley/
Location: http://code.google.com/p/sulley/
Another Python-based framework, Sulley includes the usual generator and transformation features, as well as detailed log collection methods, monitoring functions, and parallel fuzzing.
Documentation for Sulley can be found at http://www.fuzzing.org/wp-content/SulleyManual.pdf.
General Utilities
Here are a couple odds and ends you may find useful. Of course, it goes without saying that every developer should be familiar with at least one solid text editor and a hex editor.
Hachoir
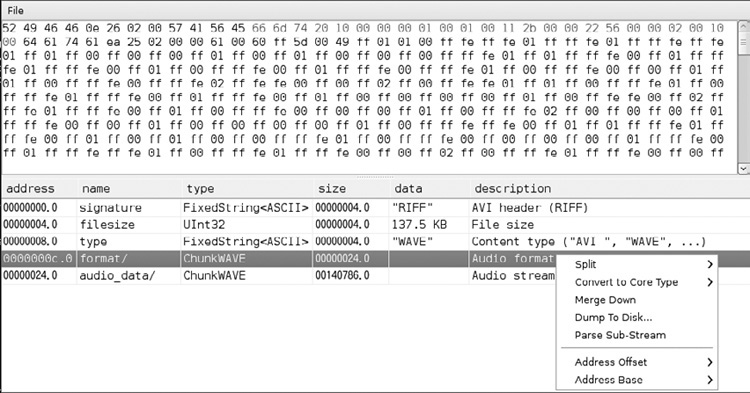
Hachoir is an excellent tool for parsing a variety of file formats, which can be very useful to dig for data inside files, understand their structure, or write fuzzers for them. Additionally, Hachoir can be useful for determining the root cause of bugs, by helping you identify what a program is expecting when parsing a file. See Figures B-12 and B-13 for examples of parsing a WAV audio file.
Hachoir has two main interfaces: hachoir-urwid and hachoir-wx, which are console based and GUI based, respectively. Both have their own strengths, so you may want to experiment.
VBinDiff
![]() Author: Christopher J. Madsen
Author: Christopher J. Madsen
![]() Location: www.cjmweb.net/vbindiff/
Location: www.cjmweb.net/vbindiff/
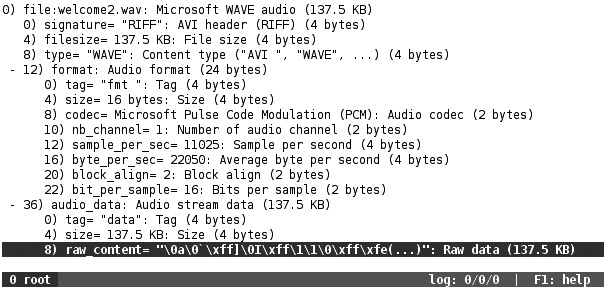
Figure B-12 Hachoir parsing a WAV file
Figure B-13 The same file, using Hachoir-wx
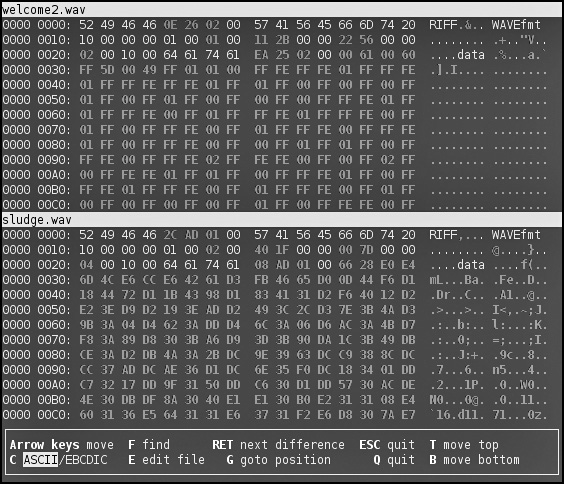
VBinDiff is a simple tool for determining differences between two binary files. The files are loaded side by side, with differences highlighted in red. It can jump between differences, swap bytes between files, and perform a basic search. This can be useful for determining exactly what is broken in a source file (from a fuzzer, for example), in the event it’s causing a crash. Figure B-14 shows a comparison between two different WAV files, highlighting similarities and differences.