![]()
CHAPTER 1
Ethical Hacking Basics
In this chapter you will learn about
• Identifying basic elements of information security
• Understanding security, functionality, and ease of use
• Defining and profiling an ethical hacker
• Defining classifications of hackers and terms associated with hacking
• The five stages of ethical hacking
• Defining the types of system attacks
• Understanding U.S. federal laws related to cyber crime
• Understanding various international laws related to cyber crime
![]()
In my youth I spent a lot of time working in a body shop owned by a neighbor just down the road. We fixed cars that had been involved in accidents, did plenty of custom work on vehicles at customer request, and painted one bodacious flame job on a 1974 Volkswagen Beetle. I remember how excited I was that first day of work, greatly looking forward to picking up a paint gun and blasting a beautiful scene on someone’s car. I also remember how deflating it was seconds later when my boss held up a paint gun in one hand and some masking tape and a sander in the other. “See this?” he said, holding up the paint gun. “When you learn how to use these correctly,” he said, shaking the tape and sander, “then I’ll teach you how to use the paint gun.”
Sorry to disappoint you, but this chapter is a lot like that tape and sander. I know you’re excited. I know you can’t wait. I can close my eyes and see you there, trembling with excitement and eager to get to the first few keystrokes that will turn you into a hacker—but you’re going to have to learn some of the basics first. And most of it isn’t any more exciting or sexy than masking tape.
This chapter is about all the bedrock and highly essential (but inanely boring and mundane) information you’ll need to know—not only to become a successful ethical hacker, but also to pass the exam. Just as with any certification you attempt, there are any number of definitions and terms you’ll need to know, including just what an ethical hacker is supposed to be. There are also numerous rules, regulations, and laws you’ll need to know—both those applying within the United States and those relevant to international law. Granted, none of this is as exciting as cracking into some high-level network, but it is essential.
Introduction to Ethical Hacking
Ask most people to define the term “hacker,” and they’ll instantly picture a darkened room, several monitors ablaze with green text scrolling across the screen, and a shady character in the corner furiously typing away on a keyboard in an effort to break or steal something. Unfortunately, a lot of that is true, and a lot of people worldwide actively participate in these activities for that very purpose. However, it’s important to realize there are differences between the good guys and the bad guys in this realm. It’s the goal of this section to help define the two groups for you, as well as to help provide some background on the basics.
Whether for noble or bad purposes, the art of hacking remains the same. Using a specialized set of tools, techniques, knowledge, and skills to bypass computer security measures allows someone to “hack” into a computer or network. The purpose behind their use of these tools and techniques is really the only thing in question. Whereas some use these tools and techniques for personal gain or profit, the good guys practice them in order to better defend their systems and, in the process, provide insight on how to catch the bad guys.
Security Basics: CIA
Before we get into what a hacker is and how you become one, let’s take a few moments and talk about some security basics you’ll need to know. First and foremost, ask any true security professional what “CIA” stands for, and they won’t respond with “Central Intelligence Agency,” as you might expect. Instead, you’ll get a knowing smile and a response including the holy trinity of IT security: Confidentiality, Integrity, and Availability. Whether you’re an ethical hacker or not, these three items constitute the hallmarks of security we all strive for. You’ll need to be very familiar with two aspects of each term in order to achieve success as an ethical hacker as well as on the exam: what the term itself means and which attacks are most commonly associated with it.
Confidentiality
Confidentiality, addressing the secrecy and privacy of information, refers to the measures taken to prevent disclosure of information or data to unauthorized individuals or systems. Confidentiality for the individual is a must, considering its loss could result in identity theft, fraud, and loss of money. For a business or government agency, it could be even worse. The use of passwords within some form of authentication is by far the most common logical measure taken to ensure confidentiality, and attacks against passwords are, amazingly enough, the most common confidentiality attacks.
For example, your logon to a network usually consists of a user ID and a password, which is designed to ensure only you have access to that particular device or set of network resources. If another person were to gain your user ID and password, they would have unauthorized access to resources, and could masquerade as you throughout their session. Although authentication (using passwords, for example) is by far the most common method used to enforce confidentiality, numerous other options are available to ensure confidentiality, including options such as encryption, biometrics, and smart cards.
| EXAM TIP Be careful with the terms “confidentiality” and “authentication.” Sometimes these two are used interchangeably, and if you’re only looking for one, you may miss the question altogether. For example, a MAC address spoof (using the MAC address of another machine) is called an authentication attack. Authentication is definitely a major portion of the confidentiality segment of IT security. | |
Integrity
Integrity refers to the methods and actions taken to protect the information from unauthorized alteration or revision—whether the data is at rest or in transit. In other words, integrity measures ensure the data sent from the sender arrives at the recipient with no alteration. For example, imagine a buying agent sending an e-mail to a customer offering the price of $300. If an attacker somehow altered the e-mail and changed the offering price to $3,000, the integrity measures have failed and the transaction will not occur as intended—if at all. Oftentimes, attacks on the integrity of information are designed to cause embarrassment or legitimate damage to the target.
Integrity in information systems is often ensured through the use of a hash. A hash function is a one-way mathematical algorithm (such as MD5 and SHA-1) that generates a specific, fixed-length number (known as a hash value). When a user or system sends a message, it generates a hash value to also send to the recipient. If even a single bit is changed during the transmission of the message, instead of showing the same output, the hash function will calculate and display a greatly different hash value on the recipient system. Depending on the way the controls within the system are designed, this would result in either a retransmission of the message or a complete shutdown of the session.
| EXAM TIP “Bit flipping” is one form of an integrity attack. In bit flipping, the attacker isn’t interested in learning the entirety of the plaintext message. Instead, bits are manipulated in the ciphertext itself to generate a predictable outcome in the plaintext once it is decrypted. | |
Availability
Availability is probably the simplest, easiest to understand segment of the security triad, yet it should not be overlooked. It refers to the communications systems and data being ready for use when legitimate users need them. Many methods are used for availability, depending on whether the discussion is about a system, network resource, or the data itself, but they all attempt to ensure one thing—when the system or data is needed, it can be accessed by appropriate personnel.
Attacks against availability all fall into the “denial of service” realm. Denial of service (DoS) attacks are designed to prevent legitimate users from having access to a computer resource or service, and can take many forms. For example, attackers could attempt to use all available bandwidth to the network resource, or they may actively attempt to destroy a user’s authentication method. DoS attacks can also be much simpler than that—unplugging the power cord is the easiest DoS in history!
 | NOTE Many in the security field add other terms to the security triad. I’ve seen several CEH study guides refer to the term “authenticity” as one of the “four elements of security.” However, it’s not used much outside the certification realm. This is useful to keep in mind, though, come test time. |
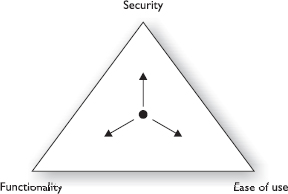
The Security, Functionality, and Ease of Use Triangle
Another important triad to remember in security is the Security, Functionality, and Ease of Use triangle. To effectively understand this topic, consider a common example used in almost every class and book I’ve ever seen on the subject. Suppose a security professional named Joe was charged with securing access to a building. Joe looks at it from a pure security perspective, and wants to do everything he can to restrict access. So, he puts in guard posts. And eyeball scanners. And passcodes with a lockdown feature only the guards can unlock. Voice recognition, smart cards, and a key, cut only from on-site security, round out his plan.
After the first day, Joe would most likely be fired. Why? Imagine working in the building Joe “secured.” You left your key at home? You’re done—you can’t come to work, and will have to wait several days for a new key to be cut. Got an important meeting with customers (assuming they can even get in the building) and you forgot your passcode? You’re done—your delay in the lockdown center waiting on the guards to release you prevented you from making the meeting. Didn’t pass the eyeball scanner? Goodness knows what Joe has in store for you.
The Security, Functionality, and Ease of Use triangle is simply a graphic representation of a problem that has faced security professionals for an eternity—the more secure something is, the less usable and functional it becomes. Want to completely secure a computer? Leave it in the box and never turn it on. Want to make the system easy for Mom to use? Better be prepared for the inevitable security breach when she clicks on the link promising <fill in the blank>.
Why is it represented as a triangle? The objective is simple, as you can see in Figure 1-1. If you start in the middle and move the point toward Security, you’re moving further and further away from Functionality and Ease of Use. Move the point toward Ease of Use, and you’re moving away from Security and Functionality. Simply put, as security increases, the system’s functionality and ease of use decrease. As a security professional, and a student preparing for the CEH exam, you’ll need to remember this axiom and apply as much common sense as possible in your designs.
Figure 1-1 The Security, Functionality, and Ease of Use Triangle
Defining the Ethical Hacker
So what makes someone an “ethical” hacker? Can such a thing even exist? Considering the art of hacking computers and systems is, in and of itself, a covert action, most people might believe the thought of engaging in a near-illegal activity to be significantly unethical. However, the purpose and intention of the act itself has to be taken into account.
For comparison’s sake, law enforcement professionals routinely take part in unethical behaviors and situations in order to better understand, and to catch, their criminal counterparts. Police and FBI agents must learn the lingo, actions, and behaviors of drug cartels and organized crime in order to infiltrate and bust the criminals, and to do so sometimes forces them to engage in criminal acts themselves. Ethical hacking can be thought of in much the same way. In order to find and fix the vulnerabilities and security holes in a computer system or network, you sometimes have to think like a criminal and use the same tactics, tools, and processes they might employ.
In CEH parlance, and as defined by several other entities, there is a distinct difference between a hacker and a cracker. An ethical hacker is someone who employs the same tools and techniques a criminal might use, with the customer’s full support and approval, in order to help secure a network or system. A cracker, also known as a malicious hacker, uses those skills, tools, and techniques for either personal gain or destructive purposes or, in purely technical terms, to achieve a goal outside the interest of the system owner. Ethical hackers are employed by customers to improve security. Crackers either act on their own or, in some cases, act as hired agents to destroy or damage government or corporate reputation.
Espionage Hacking
We would be remiss if we simply counted individuals in the realm of the dark side of hacking. In truth, many state-sponsored groups are actively targeting government and commercial networks and systems in an effort to promote their own nation’s interests and to control political advantage. Although governments around the world still play the spy game the way they always have, there’s no escaping the reality of the modern world. The James Bond-like super-agent has given way to a different kind of spy—one who maneuvers a digital landscape instead of the cloak-and-dagger physical realm, although with the same smoothness, tact, and sleek moves as Mr. Bond.
Examples of attacks against United States government systems are, unfortunately, widespread and easy to discover. Over the past couple of years, attacks on Department of Homeland Security (DHS) systems, Department of Defense (DoD) networks, and several Silicon Valley technology firms have been well documented. The results of a recent congressional investigation showed that the U.S. Department of Homeland Security networks were the victim of cyber attacks initiated by foreign entities, with terabytes of information being ferreted away to “Web hosting services that connect to Chinese Web sites.” Here’s just one article on the subject: http://articles.cnn.com/2007-09-24/us/homelandsecurity .computers_1_dhs-unisys-homeland-security?_s=PM:US.
The truly scary news, though, isn’t the number of attacks every year—easily in the millions—it’s that these millions of attacks are only the ones we know about. In the DHS attacks just referenced, the congressional staff noted incidents were not noticed until months after the initial attacks, and even then it’s only “when hackers are sloppy that you find out.” This one episode alone, among the hundreds reported in the press every year, serves notice that the ethical hacking field is here to stay.
While we’re on the subject, another subset of this community uses its skills and talents to put forward a cause or a political agenda. These people hack servers, deface websites, create viruses, and generally wreak all sorts of havoc in cyberspace under the assumption that their actions will force some societal change or shed light on something they feel to be political injustice. It’s not some new anomaly in human nature—people have been protesting things since the dawn of time—it has just moved from picket signs and marches to bits and bytes. In general, regardless of the intentions, acts of “hactivism” are usually illegal in nature.
Hacker Classification: The Hats
In addition to the definitions already given, the hacking community in general can be categorized into three separate classifications: the good, the bad, and the undecided. In the world of IT security, this designation is given as a hat color, and if you’ve ever watched an old Western movie, you can probably guess where this is going:
• White hats Considered the good guys, these are the ethical hackers, hired by a customer for the specific goal of testing and improving security, or for other defensive purposes. White hats are well respected and don’t use their knowledge and skills without prior consent.
• Black hats Considered the bad guys, these are the crackers, illegally using their skills for either personal gain or malicious intent. They seek to steal or destroy data, and to deny access to resources and systems. Black hats do not ask for permission or consent.
• Gray hats The hardest group to categorize, these hackers are neither good nor bad. Generally speaking, there are two subsets of gray hats—those that are simply curious about hacking tools and techniques, and those that feel like it’s their duty, with or without customer permission, to demonstrate security flaws in systems. In either case, hacking without a customer’s explicit permission and direction is a crime.
 | NOTE Lots of well-meaning hacker types have found employment in the security field by hacking into a system and then informing the victim of the security flaw(s) so that they may be fixed. However, many more have found their way to prison attempting the same thing. Regardless of your intentions, do not practice hacking techniques without approval. You may think your hat is gray, but I guarantee the victim sees only black. |
One final class of hacker borders on the insane. Some hackers are so driven, so intent on completing their task, they are willing to risk everything to pull it off. Whereas we, as ethical hackers, won’t touch anything until we’re given express consent to do so, these hackers are much like hactivists and feel that their reason for hacking outweighs any potential punishment. Even willing to risk jail time for their activities, so-called suicide hackers are the truly scary monsters in the closet.
Ethical Hacking Steps and Stages
You’ve probably noted by now an over-arching thought stated repeatedly throughout this first chapter. And yes, it is that important, so we’ll state it again here: To be an ethical hacker you must work within the confines of an agreement made between you and a customer. This agreement isn’t simply a smile, a conversation, and a handshake just before you flip open a laptop and start hacking away. No, instead it is a carefully laidout plan, meticulously arranged and documented to protect both the ethical hacker and the client.
In general, an ethical hacker will first meet with the client and sign a contract. The contract defines not only the permission and authorization given to the security professional (sometimes called the “get out of jail free card”), but also confidentiality and scope. No client would ever agree to having an ethical hacker attempt to breach security without first ensuring the hacker will not disclose any information found during the test. Usually, this concern results in the creation of a Non-Disclosure Agreement (NDA).
Additionally, clients almost always want the test to proceed to a certain point in the network structure, and no further—“you can try to get through the firewall, but do not touch the file servers on the other side…because you may disturb my MP3 collection.” They may also want to restrict what types of attacks you run. For example, the client may be perfectly okay with you attempting a password hack against their systems, but may not want you to test every DoS attack you know. Oftentimes, however, even though you’re hired to test their security and you know what’s really important in security and hacking circles, the most serious risks to a target are not allowed to be tested due to the “criticality of the resource.” If the test designed to improve security actually blows up a server, it may not be a winning scenario; however, sometimes the data that is actually at risk makes it important enough to proceed. This really boils down to cool and focused minds during the security testing negotiation.
 | NOTE A common term you’ll see referenced in your CEH study is tiger team, which is nothing more than a group of people, gathered together by a business entity, working to address a specific problem or goal. Ethical hackers are sometimes part of a tiger team, set up to thoroughly test all facets of a security system. Whether you’re hired as a part of the team or as an individual, pay attention to the rules of engagement. |
Companies and government agencies ask for penetration tests for a variety of reasons. Sometimes rules and regulations force the issue. For example, many medical facilities need to maintain compliance with the Health Insurance Portability and Accountability Act, and will hire ethical hackers to complete their accreditation. Sometimes the organization’s leadership is simply security conscious and wants to know just how well existing security controls are functioning. And sometimes it’s simply an effort to rebuild trust and reputation after a security breach has already occurred. It’s one thing to tell customers you’ve fixed the security flaw that allowed the theft of all those credit cards in the first place. It’s another thing altogether to show the results of a penetration test against the new controls.
With regard to your exam, and to your future as an ethical hacker, there are two processes you’ll need to know: how to set up and perform a legal penetration test, and how to proceed through the actual hack. A penetration test, also known as a pen test, is a clearly defined, full-scale test of the security controls of a system or network in order to identify security risks and vulnerabilities, and has three major phases. Once the pen test is agreed upon, the ethical hacker begins the “assault” using a variety of tools, methods, and techniques, but generally follows the same five stages to conduct the test. For the CEH exam, you’ll need to be very familiar with the pen test stages and the five stages of a typical hack.
There are three main phases to a pen test—preparation, assessment, and conclusion—and they are fairly easy to define and understand. The preparation phase defines the time period during which the actual contract is hammered out. The scope of the test, the types of attacks allowed, and the individuals assigned to perform the activity are all agreed upon in this phase. The assessment phase (sometimes also known as the security evaluation phase) is exactly what it sounds like—the actual assaults on the security controls are conducted during this time. Lastly, the conclusion (or post-assessment) phase defines the time when final reports are prepared for the customer, detailing the findings of the tests (including the types of tests performed) and many times even providing recommendations to improve security.
Once an ethical hacker is within the assessment phase of the pen test, it’s time to begin the attack. Although there are many different terms for these phases, and some of them run concurrently and continuously throughout a test, EC Council has defined the standard hack as having five separate phases, shown in Figure 1-2. Whether the attacker is ethical or malicious, these five phases capture the full breadth of the attack.
Figure 1-2 Phases of ethical hacking
| EXAM TIP Keep the phases of hacking in mind throughout your study. You’ll most likely see several questions asking you to identify not only what occurs in each step, but which tools are used in each one. | |
Reconnaissance is probably going to be the most difficult phase to understand for the exam—mainly because many people confuse some of its steps as being part of the next phase (scanning and enumeration). Reconnaissance is nothing more than the steps taken to gather evidence and information on the targets you wish to attack. It can be passive in nature or active. Passive reconnaissance involves gathering information about your target without their knowledge, whereas active reconnaissance uses tools and techniques that may or may not be discovered, but put your activities as a hacker at more risk of discovery.
For example, imagine your pen test has just started and you know nothing about the company you are targeting. Passively, you may simply watch the outside of the building for a couple of days to learn employee habits and see what physical security measures are in place. Actively, you may simply walk up to the entrance or guard shack and try to open the door (or gate). In either case, you’re learning valuable information, but with passive reconnaissance you aren’t taking any action to signify to others that you’re watching. Examples of actions that might be taken during this phase are social engineering, dumpster diving, and network sniffing—all of which are addressed throughout the remainder of this study guide.
In phase 2, scanning and enumeration, security professionals take the information they gathered in recon and actively apply tools and techniques to gather more in-depth information on the targets. This can be something as simple as running a ping sweep or a network mapper to see what systems are on the network, or as complex as running a vulnerability scanner to determine which ports may be open on a particular system. For example, whereas recon may have shown the network to have 500 or so machines connected to a single subnet inside a building, scanning and enumeration would tell me which ones are Windows machines and which ones are running FTP.
Not Just by the Book
Sometimes the phases of a test blend into one another. Instead of being held to a book definition, a good pen tester knows when to strike while the iron is hot and opportunity presents itself.
On one test I was a part of long ago, I stationed myself in front of the building, merely to take notes on the physical security measures in place. I noticed, after a few moments, that the great majority of people at the entrance gate would hold the door for others coming through—it was raining, after all, and they wanted to be polite. On a whim, I jumped out of my car and walked across the street, just as an employee was swiping his card at the gate. He not only held the gate open for me, but directed me to the executive’s personal conference room and unlocked the door for me.
Phase 1? I was already well on my way to completion of phase 4 (at least for physical security anyway) and hadn’t even spent 30 minutes on the job.
Phase 3, as they say, is where the magic happens. This is the phase most people delightedly rub their hands together over, reveling in the glee they know they will receive from bypassing a security control. In the gaining access phase, true attacks are leveled against the targets enumerated in phase 2. These attacks can be as simple as accessing an open and nonsecured wireless access point and then manipulating it for whatever purpose, or as complex as writing and delivering a buffer overflow or SQL injection against a web application. The attacks and techniques used in the phase will be discussed throughout the remainder of this study guide.
In phase 4, maintaining access, hackers attempt to ensure they have a way back into the machine or system they’ve already compromised. Back doors are left open by the attacker for future use—especially if the system in question has been turned into a zombie (a machine used to launch further attacks from) or if the system is used for further information gathering—for example, a sniffer can be placed on a compromised machine to watch traffic on a specific subnet. Access can be maintained through the use of Trojans, rootkits, or any number of other methods.
| EXAM TIP Some study guides will also sneak in another phase of hacking called “escalation of privileges” between phases 3 and 4. This defines the actions taken by a hacker to promote his access to root or administrative levels. If you see this on the exam, be prepared—actions taken here span the gap between the gathering access and maintaining access phases. You’ll have to use your best judgment in answering the question. | |
In the final phase, covering tracks, attackers attempt to conceal their success and avoid detection by security professionals. Steps taken here consist of removing or altering log files, hiding files with hidden attributes or directories, and even using tunneling protocols to communicate with the system. If auditing is even turned on and monitored, and often it is not, log files are an indicator of attacks on a machine. Clearing the log file completely is just as big an indicator to the security administrator watching the machine, so sometimes selective editing is your best bet. Another great method to use here is simply corrupting the log file itself—whereas a completely empty log file screams an attack is in progress, files get corrupted all the time and, chances are, the administrator won’t bother to try to rebuild it. In any case, good pen testers are truly defined in this phase.
A couple of insights can, and should, be gained here. First, contrary to popular belief, hackers do not just randomly assault things hoping to find some overlooked vulnerability to exploit. Instead, they normally follow a specific, organized method to thoroughly discover every aspect of the system they’re targeting. Good ethical hackers performing a pen test ensure these steps are very well documented, taking exceptional and detailed notes and keeping items such as screenshots and log files for inclusion in the final report. Second, keep in mind that security professionals performing a pen test do not normally repair or patch any security vulnerabilities they find—it’s simply not their job to do so. The ethical hacker’s job is to discover security flaws for the customer, not to fix them.
 | NOTE Sometimes what CEH covers and what happens in the “real world” are at odds. In this case, you should probably know that a hacker who is after someone in particular may not bother sticking to a set method in getting to what they want. Hackers in the real world will take advantage of the easiest, quickest, simplest path to the end goal, and if that means attacking before enumerating, then so be it. |
Hacking Terminology and Attacks
In this section, we’ll cover some of the more mundane stuff—the definitions, terms, and other notes you’ll need to know to be successful on the exam. Of course, it’s a necessity to know the lingo on the actual job as well, but when you’re itching to put fingers on keyboard to begin hacking, it’s sometimes maddening to read through. Trust me, though, this stuff is essential.
Ethical Hacking Testing Types
In performing a pen test, an ethical hacker must attempt to reflect the criminal world as much as possible. In other words, if the steps taken by the ethical hacker during the pen test don’t adequately mirror what a “real” hacker would do, then the test is doomed to failure. For that reason, most pen tests have individuals acting in various stages of knowledge about the target of evaluation (TOE). These different types of tests are known by three names—black box, white box, and gray box.
In black box testing, the ethical hacker has absolutely no knowledge of the TOE. It’s designed to simulate an outside, unknown attacker, takes the most amount of time to complete and, usually, is by far the most expensive option. For the ethical hacker, black box testing means a thorough romp through the five stages of an attack, and removes any preconceived notions of what to look for. The only true drawback to this type of test is it focuses solely on the threat outside the organization, and does not take into account any trusted users on the inside.
White box testing is, amazingly enough, the exact opposite of black box testing. In this type, pen testers have full knowledge of the network, system, and infrastructure they’re targeting. This, quite obviously, makes the test much quicker, easier, and less expensive, and is designed to simulate a knowledgeable internal threat, such as a disgruntled network admin or other trusted user.
The last type, gray box testing, is also known as partial knowledge testing. What makes this different from black box testing is the assumed level of elevated privileges the tester has. Whereas black box testing is generally done from the network administration level, gray box testing assumes only that the attacker is an insider. Because most attacks do originate from inside a network, this type of testing is very valuable and can demonstrate privilege escalation from a trusted employee.
Attack Types
Once the ethical hacker is engaged, several different categories or labels are placed on the actual type of attack being used. EC Council broadly defines all these in four categories:
• Operating system attacks Generally speaking, these attacks target the common mistake many people make when installing operating systems—accepting and leaving all the defaults. Things like administrator accounts with no passwords, all ports left open, and guest accounts (the list could go on forever) are examples of settings the installer may forget about. Additionally, operating systems are never released fully secure—they can’t be, if you ever plan on releasing them within a timeframe of actual use—so the potential for an old vulnerability in newly installed operating systems is always a plus for the ethical hacker.
• Application-level attacks These are attacks on the actual programming codes of an application. Although most people are very cognizant of securing their OS and network, it’s amazing how often they discount the applications running on their OS and network. Many applications on a network aren’t tested for vulnerabilities as part of their creation and, as such, have many vulnerabilities built into them. Applications on a network are a goldmine for most hackers.
• Shrink-wrap code attacks These attacks take advantage of the built-in code and scripts most off-the-shelf applications come with. The old refrain “Why reinvent the wheel?” is very often used to describe this attack type. Why spend time writing code to attack something when you can buy it already “shrink wrapped”? These scripts and code pieces are designed to make installation and administration easier, but can lead to vulnerabilities if not managed appropriately.
• Misconfiguration attacks These attacks take advantage of systems that are, on purpose or by accident, not configured appropriately for security. Remember the triangle earlier, and the maxim “As security increases, ease of use and functionality decrease”? This type of attack takes advantage of the administrator who simply wants to make things as easy as possible for the users. Perhaps to do so, the admin will leave security settings at the lowest possible level, enable every service, and open all firewall ports. It’s easier for the users, but creates another goldmine for the hacker.
Elements of Risk and More Hacking Terminology
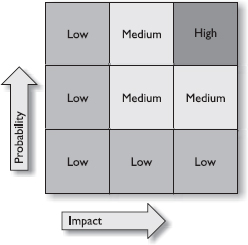
Risk analysis and management are major parts of the IT security career field. Basically the goal is to identify what risks are present, quantify them on a measurement scale (see Figure 1-3 for a sample risk analysis matrix), and then come up with solutions to mitigate, eliminate, or accept the risks. To fully accomplish this task, you’ll need to be aware of the three basic elements of risk—asset, threat, and vulnerability. Combine them with the probability of an attack and what the impact of a successful attack would be, and you’ve got an easy way to identify high, medium, and low risks.
Figure 1-3 Risk analysis matrix example
An asset is an item of economic value owned by an organization or an individual. Identification of assets within the risk analysis world is the first and most important step. After all, if you don’t know what you have, how can you possibly secure it? Assets can be anything from physical devices (such as desktops, servers, printers, switches, and routers) to databases and file shares.
 | NOTE When it comes to assets, don’t neglect the “intangibles.” Public image and reputation are just as important as trade secrets and proprietary information. |
A threat is any agent, circumstance, or situation that could cause harm or loss to an IT asset. Threats can take on many forms, and may not always be readily identifiable. For example, you probably already think of malicious hackers and viruses as threats, but what about bad weather? A hurricane, tornado, flood, or earthquake could cause just as much damage to your assets as a hacker could ever dream of doing. Ethical hackers are, obviously, much more concerned with the virtual threat agent techniques, but security professionals designing an entire program need to be cognizant of as many threats as possible.
A vulnerability is any weakness, such as a software flaw or logic design, that could be exploited by a threat to cause damage to an asset. The goal of pen testers is to discover these vulnerabilities and attempt to exploit them. The key thing to remember about vulnerabilities is that their existence does not necessarily equate to a risk. For example, given physical access to any computer system, a hacker could easily (usually) successfully hack the device—so the vulnerability (physical access) exists. However, if your server is locked in an airtight room, buried in an underground silo, with multiple guards and physical security measures in place, the probability of it being exploited is reduced to near zero.
Other hacking terminology you may run into or read includes the different types and designations of various hackers (including phreakers, script kiddies, and whackers), the differences in attack vectors (an inside attack generates from inside the network boundary, whereas an outside attack comes from outside the border), and things like daisy chaining. To avoid a 100-page chapter of endless definitions, and to attempt to assist you in maintaining your sanity in studying for this exam, I’m going to recommend you peruse the glossary at the end of this book for more information. You’ll see these terms used throughout the book anyway, and most of them are fairly easy to figure out on your own, but don’t discount the definitions you’ll find at the end. Besides, we worked really hard on the glossary—it would be a shame if it went unnoticed.
| EXAM TIP Definition questions should be no-brainers on the exam. Learn the hacker types, the stages of a hack, and other definitions in the chapter—don’t miss the easy ones. | |
Legal Hacking: Laws and Guidelines You Need to Know
So we’ve spent some time defining what an ethical hacker is, how to become one (for one thing, pass the CEH exam!), and learning some of the lingo of the trade. This next section deals with the laws and legality every ethical hacker needs to know and work under. Yes, I know, you didn’t pick this book up as part of your bar examination study to become a lawyer. However, you do need to be very cognizant of the laws regarding cyber crime, both inside the United States and around the world—not only because it will help the subset of our chosen profession that uses statutes against criminals, but also to ensure you stay out of jail yourself.
The good news here is you don’t need to commit this entire section to memory. Laws and legality may not appear on the exam any more—the CEH objectives no longer call for them—but they’re included in this chapter as a reference for you. I know you’re probably wondering, then, why you should bother with reading it—after all, you picked this book up in order to study for an exam. The answer, my friend, is that being an ethical hacker is about a lot more than just passing an exam. Some laws can be confusing in their real-world implementation, and if you don’t pay attention you can wind up in jail. For example, a computer attack could originate in China, be launched from Singapore through a computer in Alabama (yes, there are some there), and exploit a system in England. Whose laws take precedence? Who is liable for the attack? How much culpability do the carriers hold? Who will prosecute? We’ll examine a couple of relevant laws and acts, and do our best to list and describe those others you’ll need to know.
U.S. Cyber Crime Laws
On October 29, 1969, a U.S. Defense Department team successfully established a link between three separate nodes—and the ARPANET was born. From this humble beginning, packet switching technology, a new protocol stack called TCP/IP, and the Internet were born. Early on in computing, most crimes were nothing more than any other—physical theft or destruction of the devices. However, as time moved on and more and more data became available and accessible on networks, it wasn’t long before criminals discovered an entirely new realm in which to play.
For example, in 1978 a group of players at the Flagler Dog Track in Florida found a way to fake winning dog race tickets using a computer system. After more than a few fraudulent tickets made their way past the booth, the owners became suspicious and, finally, caught the cheaters. However, the technology was so new, no one knew what statute to charge them under. As a result, the first law regarding computer use and abuse in the United States was created: the Florida Computer Crimes Act.
 | NOTE All computer crimes fall into one of two major categories: crimes where a computer or network was used in the commission of a crime, and those where the computer or network itself was the target of the crime. In either case, the penalties for computer crimes are getting more and more severe as time, and our understanding, moves on. |
Since that time, computer law has grown and become more specific, just as the use of computers and networking in crimes has become more sophisticated. Although a large number of U.S. statutes and laws need to be learned, we will simply concentrate on the most relevant to your professional future. Hacking specifically is addressed under law in United States Code Title 18: Crimes and Criminal Procedure, Part I: Crimes, Chapter 47: Fraud and False Statements, Sections 1029 and 1030. Other regulations and laws are also described in this section.
18 U.S.C § 1029 and 1030
Section 1029, “Fraud and related activity in connection with access devices,” has several subsections and statutes defined. Basically, the law gives the U.S. government the authority to prosecute criminals who traffic in, or use, counterfeit access devices. In short, the section criminalizes the misuse of any number of credentials, including passwords, PIN numbers, token cards, credit card numbers, and the like. If a person creates or sells devices that fake credentials, or if they traffic the credentials created by the fake machines, Section 1029 provides punishment under the law.
Section 1030, “Fraud and related activity in connection with computers,” is a little different. This statute actually targets hackers themselves, and criminalizes unauthorized access to computer systems or data. Section 1030 also addresses and criminalizes the spread of viruses and malware. Full texts of both sections of the U.S. Code referenced here can be found at the U.S. Department of Justice website at www.justice.gov/criminal/cybercrime/1029NEW.htm and www.justice.gov/criminal/cybercrime/1030NEW.htm.
The SPY Act
In 2007, the Securely Protect Yourself Against Cyber Trespass Act passed the U.S. Congress and became law. Dealing mainly with spyware, the act makes it unlawful for any person who is not the owner, or authorized user, of a computer used for a financial institution, the U.S. government, or in any interstate or foreign commerce or communication to engage in “unfair or deceptive acts,” including the following:
• Taking unsolicited control of the system
• Modifying computer settings
• Collecting personally identifiable information
• Inducing the owner or authorized user to disclose personally identifiable information
• Inducing the unsolicited installation of computer software
• Removing or disabling a security, antispyware, or antivirus technology
In short, the act criminalizes the collection of personal information (through the use of a keystroke logger, or any other means) without the user’s consent. It also prevents an outsider from redirecting a web browser to another site, taking control of a system without authorization, and using a system to send unsolicited information to others (spam). The full text of the SPY Act, in both its original House and Senate versions, can be found at the U.S. Library of Congress site at http://thomas.loc.gov/cgibin/query/z?c109:H.R.29.
Freedom of Information Act (5 U.S.C. § 552) and the Privacy Act of 1974
I once took a U.S. history class in college while I was serving in the military. The instructor was a naturalized citizen who grew up, if memory serves me here, in either Oman or Yemen, and he brought a unique perspective to the history of my nation. I remember one class in particular, he was railing on about how many nations’ citizens have no idea what their governments are up to and how the lack of basic information on government activities could be very dangerous. This served as his lead-in to a discussion of just how open the U.S. government is with its citizens. One instance of that is the Freedom of Information Act (FoIA).
 | NOTE FoIA doesn’t necessarily help you in hacking, but it does provide a cover for a lot of information. Anything you uncover that could have been gathered through FoIA is considered legal. The Privacy Act, though, defines the information that is not available to you. Dissemination and storage of privacy information needs to be very closely controlled to keep you out of hot water. |
FoIA was originally signed in 1966 and serves the people’s right to know certain pieces of information not deemed to be classified. For the most part, FoIA can be used by any U.S. citizen to get any and every piece of information they want from the government. As a matter of fact, the act doesn’t state what information one is allowed to get—it rather states the nine instances in which one can’t ask for it. These instances are generally things such as military and law enforcement information, classified secrets, and information pertaining to trade secrets or inter-agency litigation.
With all the uproar, protest, and eventually celebration over freedom of information, many also began looking at the downside of too much information being made available. What about items of personal information regarding individuals? If government agencies, or other entities, collected this information and made it available to anyone, the individual’s safety—financially or otherwise—may be put at risk. Additionally, citizens of the United States have an expectation of privacy, which has been thoroughly debated and argued in more court cases than we have time to review here. This thought process brought about the Privacy Act of 1974.
The Privacy Act basically states government agencies cannot disclose personal information about an individual without that person’s consent. It also defines what personal information is and lists 12 exemptions for the release of this information (generally with regard to law enforcement issues). Loads of information on FoIA, including its full text, can be found on the U.S. Department of Justice site at www.justice.gov/oip/.
Federal Information Security Management Act (FISMA)
Mention FISMA to a group of security professionals, and you’re liable to get groans of disgust and anguish (from the groups charged with writing the security plan), followed by grumbling of reserved admiration (or at least acceptance). FISMA basically is an effort to ensure the security of government systems by promoting a standardized approach to security controls, implementation, and testing. The act requires government agencies to create security plans for their systems, and to have them “accredited” at least once every three years. It also requires periodic assessments of the security controls in place, which is where the ethical hacker comes into play—somebody has to make sure the controls for authentication on the network actually work the way the security plan says they do.
FISMA is a giant program with far too many facets and details to cover in this book. The key thing to remember is that it creates a framework for government security program creation, maintenance, and testing. In your real-world work as a security testing professional, you’ll need to become very familiar with everything FISMA-related. More information on FISMA can be found on the National Institute of Standards and Technology (NIST) site at http://csrc.nist.gov/groups/SMA/fisma/index.html.
USA PATRIOT Act of 2001
Still one of the more controversial laws in our current system, the USA PATRIOT Act, signed into law in October of 2001, dramatically increased the government’s ability to monitor, intercept, and maintain records on almost every imaginable form of communication (telephone, networking, e-mail, and medical and financial records are all addressed). The original goal of the act, in response to the September 11th terrorist attacks on the United States, was to better equip the government to prevent future terrorist activity. As a side effect, it has also served to increase observation and prevention of hacking attempts on many systems. The things hackers used to be able to do without fear of discovery, hiding behind privacy laws, are now part of history, and it has forced hackers to be much more thorough in hiding their attempts.
More information on the USA PATRIOT Act can be found on the U.S. Department of Justice website at www.justice.gov/archive/ll/highlights.htm.
NOTE I’d be willing to bet, if you were aware of this law already, you probably referred to it as the “Patriot Act,” believing, like most of us, that the term “patriot” in the title was, indeed, a word. You might be interested to know it’s not actually a word, but an acronym. USA PATRIOT stands for Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism. I was unaware any government had that kind of creative prowess.
Other U.S. Laws of Relevance
We could continue romping through the U.S. Code, ferreting out every individual law that might remotely touch on hacking, data, communication, computers, or networks, but you’d lose interest and I would blow my chapter page count before we ever even got to the good stuff. Suffice it to say there are a lot of laws, and although they’re all relevant to your job as an ethical hacker, it’s impossible for you to know them all—unless, of course, you want to be an ethical hacking lawyer. For the rest of us, Table 1-1 lists a few other laws of relevance, with some quick details you need to know about each.
International Cyber Crime Laws
Ethical hackers need to be cognizant that U.S. law isn’t the only legal guideline in our chosen profession. Many times data and systems regarding a crime either can reside physically in foreign countries or may traverse them somehow. Although the prospect of learning all foreign law regarding the subject is daunting, rest assured you won’t need to be an international law expert to fulfill your duties on a pen test team. Some of the more pertinent international laws you may want to at least read are listed here:
| Law Title | Details |
| Federal Managers Financial Integrity Act (1982) | Requires financial institutions to ensure the protection of records and data by mandating ongoing evaluations of their security measures. |
| Computer Fraud and Abuse Act (1984) | Protects systems and data owned by the federal government, defining classified systems and providing punishment for theft and/or malicious code regarding these systems. |
| Electronic Communications Privacy Act 18 U.S.C. § 2510 (1986) | Protects wire, oral, and electronic information while in transit. Later, a second title protected data in storage as well. |
| Cyber Security Enhancement Act (2002) | In addition to various funding and requirements levied by NIST, this act also strengthens sentencing guidelines for hackers whose activities cause death or bodily harm to others. |
| Government Paperwork Elimination Act (GPEA, 2003) | Requires the government to use electronic forms, filing, and signatures as much as possible and practical. |
Table 1-1 Relevant U.S. Laws Regarding Cyber Crime | |
• Cyber Crime Law in Mexico Section 30-45-5: Unauthorized computer use
• Cyber Crime Law in Brazil Art. 313-A: Entry of false data into the information system. Art. 313-B: Unauthorized modification or alteration of the information system
• Cyber Crime Law in Canada Canadian Criminal Code Section 342.1
• Cyber Crime Law in the United Kingdom Computer Misuse Act 1990 and Police and Justice Act 2006
• Cyber Crime Law in Europe Section 1: Substantive Criminal Law
• Cyber Crime Law in Belgium Computer Hacking Article 550(b)
• Cyber Crime Law in Denmark Penal Code Section 263
• Cyber Crime Law in France Chapter III: Attacks on Systems for Automated Data Processing, Article 323-1 and Article 323-2
• Cyber Crime Laws in Germany Penal Code Section 202a: Data Espionage and Penal Code. Section 303a: Alteration of Data
• Cyber Crime Law in Greece Criminal Code Article 370C § 2
• Cyber Crime Law in Italy Penal Code Article 615: Unauthorized access into computer or telecommunication systems. Criminal Code Article 138a
• Cyber Crime Law in Norway Penal Code § 145, § 145b, and § 151b
• Cyber Crime Laws in Switzerland Article 143b and Article 144b
• Cyber Crime Law in Australia The Cybercrime Act 2001
• Cyber Crime Law in India The Information Technology Act, 2000
• Cyber Crime Law in Japan Law No. 128 of 1999
• Cyber Crime Law in Singapore Chapter 50A: Computer Misuse Act
• Cyber Crime Laws in Korea Chapter VI: Stability of the Information and Communications Network: Article 48, Article 49, and Chapter IX Penal Provisions: Article 61
• Cyber Crime Law in Malaysia Computer Crimes Act 1997
• Cyber Crime Law in Hong Kong Telecommunication Law
Don’t fret—you won’t need to memorize every nuance and verse of every foreign law related to cyber crime. The intent of this section is simply to make you aware that as an ethical hacker, you’ll need to know the various laws that may affect your activities. Take note of where you’ll be testing and what you expect to find; then check the laws of that country to ensure you aren’t getting yourself into trouble.
Chapter Review
To be a successful ethical hacker, you don’t just need the knowledge of tools and techniques, but also the background information that provides a secure foundation for your career. Some of the basics include the security triad of Confidentiality, Integrity, and Availability. Confidentiality, addressing the secrecy and privacy of information, refers to the measures taken to prevent disclosure of information or data to unauthorized individuals or systems. The use of passwords is by far the most common logical measure taken to ensure confidentiality, and attacks against passwords are, amazingly enough, the most common confidentiality attacks. Integrity refers to the methods and actions taken to protect the information from unauthorized alteration or revision—whether the data is at rest or in transit. Integrity in information systems is often ensured through the use of a hash (a one-way mathematical algorithm such as MD5 or SHA-1). Availability refers to the communications systems and data being ready for use when legitimate users need it. Denial of service (DoS) attacks are designed to prevent legitimate users from having access to a computer resource or service, and can take many forms.
Another security basic is the Security, Functionality, and Ease of Use triangle, which is simply a graphic representation of a problem that has faced security professionals for an eternity—the more secure something is, the less usable and functional it becomes. As security increases, the system’s functionality and ease of use decrease.
Defining an ethical hacker, as opposed to a cracker (or malicious hacker), basically comes down to the guidelines one works under—an ethical hacker only works with explicit consent and approval from a customer. Ethical hackers are employed by customers to improve security. Crackers either act on their own or, in some cases, are employed by malicious entities to destroy or damage government or corporate reputation. In addition, some hackers who use their knowledge to promote a political cause are referred to as “hactivists.”
Hackers are generally classified into three separate groups. White hats are the ethical hackers hired by a customer for the specific goal of testing and improving security, or for other defensive purposes. Black hats are the crackers illegally using their skills for either personal gain or for malicious intent—and they do not ask for permission or consent. Gray hats are neither good nor bad—they are simply curious about hacking tools and techniques, or feel like it’s their duty, with or without customer permission, to demonstrate security flaws in systems. In any case, hacking without a customer’s explicit permission and direction is a crime.
A penetration test, also known as a pen test, is a clearly defined, full-scale test of the security controls of a system or network in order to identify security risks and vulnerabilities. The three main phases in a pen test are preparation, assessment, and conclusion. The preparation phase defines the time period when the actual contract is hammered out. The scope of the test, the types of attacks allowed, and the individuals assigned to perform the activity are all agreed upon in this phase. The assessment phase (sometimes also known as the security evaluation phase) is when the actual assaults on the security controls are conducted. The conclusion (or post-assessment) phase defines the time when final reports are prepared for the customer, detailing the findings of the test (including the types of tests performed) and many times even providing recommendations to improve security.
The act of hacking itself consists of five main phases. Reconnaissance involves the steps taken to gather evidence and information on the targets you wish to attack. It can be passive in nature or active. Scanning and enumeration takes the information gathered in recon and actively applies tools and techniques to gather more in-depth information on the targets. In the gaining access phase, true attacks are leveled against the targets enumerated in phase 2. In phase 4, maintaining access, hackers attempt to ensure they have a way back into the machine or system they’ve already compromised. Finally, in the final phase, covering tracks, attackers attempt to conceal their success and avoid detection by security professionals.
Three different types of tests are performed by ethical hackers. In black box testing, the ethical hacker has absolutely no knowledge of the target of evaluation (TOE). It’s designed to simulate an outside, unknown attacker. In white box testing, pen testers have full knowledge of the network, system, and infrastructure they are testing and it is designed to simulate a knowledgeable internal threat, such as a disgruntled network admin or other trusted user. In gray box testing, the attacker has limited knowledge about the TOE. It is designed to simulate privilege escalation from a trusted employee.
Lastly, there are multiple laws, both inside and outside the United States, for the ethical hacker to study and be aware of. You should know not only what each law specifically addresses, and what punishments it may levy, but also what each law means to an ethical hacker and how our business is done.
Questions
1. Which element of security ensures a data message arrives at its destination with no alteration?
A. Confidentiality
B. Integrity
C. Availability
D. Authentication
2. A hacker grows frustrated in his attempts against a network server and performs a successful denial of service attack. Which security element is being compromised?
A. Confidentiality
B. Integrity
C. Availability
D. Authentication
3. As security in the enterprise increases,
A. ease of use increases and functionality decreases.
B. functionality increases and ease of use decreases.
C. ease of use decreases and functionality increases.
D. functionality decreases and ease of use decreases.
4. An ethical hacker is hired to test the security of a business network. The CEH is given no prior knowledge of the network and has a specific framework in which to work, defining boundaries, Non-Disclosure Agreements, and the completion date. Which of the following is a true statement?
A. A white hat is attempting a black box test.
B. A white hat is attempting a white box test.
C. A black hat is attempting a black box test.
D. A black hat is attempting a gray box test.
5. When an attack by a hacker is politically motivated, the hacker is said to be participating in
A. black hat hacking.
B. gray box attacks.
C. gray hat attacks.
D. hactivism.
6. Two hackers attempt to crack a company’s network resource security. One is considered an ethical hacker, whereas the other is not. What distinguishes the ethical hacker from the “cracker”?
A. The cracker always attempts white box testing.
B. The ethical hacker always attempts black box testing.
C. The cracker posts results to the company’s security experts.
D. The ethical hacker always obtains written permission before testing.
7. In which stage of an ethical hack would the attacker actively apply tools and techniques to gather more in-depth information on the targets?
A. Active reconnaissance
B. Scanning and enumeration
C. Gaining access
D. Passive reconnaissance
8. Which type of attack is generally conducted as an inside attacker with elevated privileges on the resource(s)?
A. Gray box
B. White box
C. Black box
D. Active reconnaissance
9. Which attacks take advantage of the built-in code and scripts most off-the shelf applications come with?
A. OS attacks
B. Bit-flipping
C. Misconfiguration
D. Shrink-wrap
10. A number of laws are relevant to ethical hacking. Within the United States, which federal statute specifically addresses hacking under U.S. law?
A. United States Code, Title 18
B. SPY Act
C. PATRIOT Act
D. Freedom of Information Act
11 . Which act attempts to ensure a standard level of security in U.S. federal systems?
A. United States Code, Title 18
B. PATRIOT Act
C. FISMA
D. FoIA
12. As part of a pen test, an ethical hacker discovers a file listing government workers’ social security numbers. His dissemination of this document is best governed by which act?
A. Freedom of Information Act
B. Privacy Act
C. PATRIOT Act
D. FISMA
Answers
1. B. The security triad element of integrity ensures data stays in the form it was originally intended—during transit and at rest.
2. C. The security triad element of availability ensures communications systems and data are ready for use when legitimate users need them.
3. D. Per the Security, Functionality, and Ease of Use triangle, as security increases, functionality and ease of use decrease.
4. A. In this example, an ethical hacker was hired under a specific agreement, making him a white hat. The test he was hired to perform is a no-knowledge attack, making it a black box test.
5. D. Hackers who use their skills and talents to forward a cause or a political agenda are practicing hactivism.
6. D. The ethical hacker always obtains written permission before testing, and never performs a test without it!
7. B. The second of the five phases of an ethical hack attempt, scanning and enumeration, is the step where ethical hackers take the information they gathered in recon and actively apply tools and techniques to gather more indepth information on the targets.
8. B. A white box attack is intended to simulate an internal attacker with elevated privileges, such as a network administrator.
9. D. Most software inevitably comes with built-in code and script vulnerabilities, and attacks taking advantage of this are known as shrink-wrap attacks.
10. A. United States Code, Title 18 defines most of the U.S. law concerning hacking and computer crime.
11. C. The Federal Information Security Management Act provides a green light to an ethical hacker with regard to a lot of information, because it makes this information readily available to the public.
12. B. The Privacy Act protects information of a personal nature, including social security numbers.