Finalizing the Installation
Abstract
This chapter contains information on setting up a finalization and commissioning checklist, special implementations, custom system reports implementation, and securing the security system. System finalization includes commissioning, training, and acceptance. Steps include device IP addressing and startup, device communications and programming, and securing the security system.
It is the responsibility of the designer to ensure that the security system design includes securing the security system. Security measures should be taken at all seven layers of the OSI networking model, where possible. RF systems in particular should be secured because their infrastructure has no physical security. Common RF attacks include
• Denial of service attacks
• Surveillance
• Impersonation
• Client-to-client intrusion
• Client-to-network intrusion
• Rogue APs and ad hoc networks
Archived data must also be secured, and a business continuity program should be developed for the security system. User classes and authorities should be set up, and logon/logoff security should be considered. System cutover should be well planned so as to occur smoothly. System maps should be created that allow the security console officer to easily control the system and get a full situational view of what is going on in the facility.
Introduction
This chapter contains information on setting up a finalization and commissioning checklist, special implementations, custom system reports implementation, and securing the security system.
Finalization and Commissioning Checklist
The following steps should be taken in commissioning the system and its software. Each of these items is explained in detail following this list:
• Connect each field device to power and its digital switch as its installation is completed in the field.
• Load and commission the server and workstation operating systems.
• Set up the security system master clock.
• Set up the security system network infrastructure (primary switches, wireless nodes, servers, and workstations), get all devices communicating (backup servers will be set up later), and secure the security system information technology network.
• Load alarm/access control system primary server and workstation software and set up the access control system databases.
• Configure connections to all of the alarm/access control system field controller panels, reader interface boards, alarm input boards, and output control boards.
• Load digital video system primary server and workstation software (including the archive server software) and set up the digital video system archive databases.
• Configure connections to all of the digital video system cameras and intercoms.
• Commission the alarm/access control system field devices.
• Commission the digital video system cameras and intercoms.
• Set up higher system functions (e.g., video guard tours, video pursuit).
• Set up PSIM configurations, if applicable.
• Set up alarm/access control system and digital video system integration.
• Implement Homeland Security threat level system policies and rules.
• Implement the organization’s security system policies and rules.
• Implement backup servers.
• Configure the system for remote monitoring.
• Present the system for acceptance testing.
Set up the Security System Master Clock
After the devices are hung and powered, the server(s) is installed, the workstations are in place, and all the wiring is run in conduit and the racks are built, the system must be commissioned (put into operation). Included in this basic preparation is system server/workstation configuration, which may include ensuring that there is one master clock for the entire system and that all other servers and workstations take their time stamp from that one server. Ideally, that clock will be synchronized with an atomic clock.
Connect Each Field Device to Power and Its Digital Switch as Its Installation Is Completed in the Field
As the field devices (e.g., cameras, card readers, intercoms) are installed, connect each to its power source and the digital edge switch through which all devices will communicate. Also connect the network infrastructure elements together in the field (edge switches to distribution switches, distribution switches to core switches, and so on) and document each completion step.
Load and Commission the Server and Workstation Operating Systems
Load the server and main workstation operating systems, including any required support programs (antivirus, antispyware, and registry maintenance program), and delete any automatically preinstalled programs that could be harmful to the system, including preinstalled Web links.
Set Up the Security System Network Infrastructure
After the primary server and workstations are operating, get the primary server and all workstations communicating together on the core network. Next, connect the edge switches and any wireless nodes so that the entire network infrastructure is operating. Configure the infrastructure to support the communications rules sets that will be required on the network. This may include establishing IGMP querying on the main core switch to support multicasting (often also on a backup core switch) and IGMP snooping on it and all the other the switches.
If the system is being blended with the organization’s information technology (IT) local area network (LAN) or wide area network (WAN), the system may require a virtual local area network (VLAN) or subnet configuration and the establishment of VLAN or subnet rules in order to segregate the two logical networks on the same physical infrastructure.
Finally, establish group policies on the server and switches to enforce basic network user-level security. A complete discussion on securing networks at all seven layers of the Open Systems Interconnection (OSI) network model is provided later. I recommend that all network-based security systems should be secured at all seven layers of the OSI network model.
Load Alarm/Access Control System Primary Server and Workstation Software
I am not sure if it matters whether the alarm/access control or digital video software is loaded first, but it seems to be an industry convention to load the Access Control System first, perhaps because the network configuration is simpler. Once the alarm/access control system server and workstation software is loaded, it is time to set up the access control system database. There are a number of types of system databases, but two are most common: MS Access (for smaller systems) and structured query language (SQL) for larger systems. SQL databases are powerful and robust, and they can easily operate an enterprise access control system comprising thousands of sites and hundreds of thousands of authorized users. Access databases are adequate for small systems only.
Configure Alarm/Access System Field Connections
After the alarm/access control system software and database are established, connect the field hardware devices to the network by coding their TCP/IP addresses into the network and configure each device, including the system controllers, reader interface panels, alarm input panels, and output relay panels. At this point, we are only concerned with connectivity, not programming of the individual devices.
Load Digital Video System Primary Server and Workstation Software
In the same manner in which the alarm/access control system server/workstation software was loaded and its database configured, so now the digital video system server/workstation software is loaded and its databases are configured.
Configure Connections to All of the Digital Video System Cameras and Intercoms
Following the loading of the digital video server/workstation software, use the software to find and connect to all available digital video cameras and intercoms. You should be able to see images on every camera. You will also need to configure the system for multicast operation if more than one workstation or server will be in the system. For simplicity and reliability, I suggest that you configure the cameras and intercoms to communicate by unicast protocol to the primary server and then configure the server to communicate by multicast to its workstations and backup server.
For networks that are especially sensitive to multicast, such as blended corporate/security networks, it is recommended to separate the field components network from the workstation/backup server network by means of a subnet or VLAN. This can be done by installing two network interface cards (NICs) in the primary server, one for the cameras and intercoms and one for the workstations and backup server. This approach creates multiple logical networks in the same physical network architecture, as though they were in fact separate physical networks. Typically, the security system will already be configured on its own VLAN in a blended network. This approach can help ensure that multicast signals never interfere with normal system operation.
Commission the Alarm/Access Control System Field Devices
After configuring the software of both main security systems, begin commissioning of the alarm/access control system field devices.
Set up Access Control Groups
This involves first setting up the devices into groups and then setting alarm/access control system schedules of operation to the groups. For example, in a multitenant building, you might set floor access to each tenant (in this case, each tenant forms a group). For a corporate environment, this will normally involve setting groups to correlate with buildings, departments, divisions, or others.
Schedules and Time Zones
Once groups are established, you can set up the system schedules. These will include time zones (e.g., 24/7, working hours) and holidays.
Then correlate the device groups to their normal operating schedules. For example, you may want the front lobby doors to be on alarm bypass and unlocked automatically during working hours but locked on access control at other times and on holidays.
Next, begin entering the system’s user database. For a new system in a new facility, this is fairly straightforward. Simply input the data and take photos in the photo ID segment of the software. For existing systems, you will need to transport the existing user database to the new system. This can be a relatively simple process if the system is simply an upgrade of an earlier version of the same manufacturer’s software, or it can be quite complicated if an entirely new system is being imported. The manufacturer will have explicit instructions on how to make this conversion, which should be followed exactly to achieve a successful database conversion.
Set Up Higher System Functions (e.g., Video Guard Tours, Video Pursuit)
Video Guard Tour Implementations
A video guard tour is a compilation of individual video guard tour stops. A video guard tour stop is a group of individual camera scenes that are brought up on screen together that convey an overall view of a contiguous area, such as at an airport security checkpoint. A video guard tour is a consecutive sequence of individual video guard tour stops that allows the console operator to tour the entire facility in a coordinated fashion using groups of video cameras to get a good look at each stop on the tour. Video guard tours are a basic element of successful integrated security system functions and should be included in every monitored system.
The ultimate expression of video guard tours is the video pursuit function. In video pursuit, each camera tile on the screen is an alarm button. By pressing on the tile of a video camera, that camera becomes the focus camera of a new video guard tour stop. The console operator can follow a subject simply by pressing on the video tiles into which the subject walks. This function is especially useful in large public venues, such as airports, casinos, convention centers, malls, and parking structures. Video pursuit allows a console security officer to “follow” a subject of interest through a facility using available video cameras as though he or she were walking along with them.
PSIM Software Implementation
Physical Security Information Management Systems (PSIM) are an especially elegant form of Graphical User Interface (GUI) that includes information that places the alarm information in the context of a map or aerial or satellite photo of a facility and provides the console operator with additional useful information about the alarm incident or event. Situational Awareness Software (SAS) also may update the movements of subjects based upon emerging sensor data, such as radar data. Situational awareness software is one of the most effective means of managing a security system from a console operator’s point of view. The SAS (or PSIM) provides a “top-level” view of the system and how it relates to its overall physical environment. The SAS/PSIM should have as a minimum the following basic elements:
• Camera icons
• Intercom icons
• Nested maps (to “drill down” into maps with greater detail)
• Linked maps (to move from area to area—east/west/north/south)
In addition, all alarm points should display a GUI screen.
In an ideal PSIM implementation, each camera should also be a “pseudo-alarm” point that links to a PSIM screen (as well as to nearby cameras), so that when an operator double-clicks on a camera, it becomes the new focus camera and related cameras around it also display (video guard tour); in addition, a PSIM map shows the area of the selected camera. This facilitates the video pursuit function.
Set up Alarm/Access Control System and Digital Video System Integration
After setting up both the alarm/access control and the digital video system, the real work begins. Set a camera link for each individual alarm in the system. Typically, the link should call up a guard tour stop from which the console officer can then follow the subject in question using video pursuit.
Similarly, link every intercom in the system to the nearest video camera so that the console officer can see the image of the person on the intercom during the conversation. Also, the GUI screen showing that intercom (and its related access controlled door or gate) should be displayed on the screen.
Access controlled doors can also be tied to the photo ID lookup function so that the console officer can look up the access control record of the person at the intercom and then let the system approve access for that person by dragging his or her photo over the door icon on the GUI screen.
In reverse, anytime a focus camera is selected, the intercom associated with that camera should be queued automatically, as should the GUI map on which that camera is shown.
Implement Homeland Security Threat Level System Policies and Rules
After all this, you can implement Homeland Security threat level policies and rules. Homeland Security threat levels1 are as follows:
• Red—Severe: A terrorist attack has occurred, or credible and corroborated intelligence indicates one is imminent. Normally, this threat condition is declared for a specific location or critical facility.
• Orange—High: Credible intelligence indicates that there is a high risk of a local terrorist attack but a specific target has not been identified.
• Yellow—Elevated: Elevated risk of terrorist attack but a specific region or target has not been identified.
• Blue—Guarded: General risk with no credible threat to any specific targets.
• Green—Low: Low risk of terrorism. Routine security is implemented to preclude routine criminal threats.
You may set up the system to operate differently at each threat level. For example, when the threat level is changed from yellow to orange, you might put two consoles online and dedicate one entirely to continuous video guard tours. At the same time, a high threat level policy would be implemented; for example, no one would be allowed to loiter near a suspension bridge anchorage building. This would be enforced by implementing intelligent video motion detection, looking for loiterers on the camera viewing the area surrounding the anchorage building, and then notifying the loiterers by bullhorn intercom to leave the area.
Implement the Organization’s System Policies and Rules
The previous example illustrates one type of security policy implementation. The entire security system can and should be designed to facilitate the organization’s security policies. For example, if company laptops are issued to certain employees, you can install asset tracking tags on the laptops and then track them as they leave through building exits against the employee access credential. By using Boolean algebra logic cells, you can compare the laptop asset tag to the authorized employee list. If the computer is in the hands of an authorized employee, no action will be taken by the system. If, however, it is in the hands of an unauthorized employee or a non-credentialed person, an alarm will sound, allowing a nearby security officer to quiz the person when the laptop is sensed passing through an exit.
A thorough review of the entire organization’s security policies should be implemented in order to fully exploit the power of the security system.
Implement Backup Servers
After implementing the primary servers, workstations, and the security application programs, backup servers may be implemented. The backup server(s) will provide two main services: archiving system activities in real time and providing a fail-over function to manage the system in the event of failure of the primary server.
Configure the System for Remote Monitoring
Following implementation of the backup server, remote monitoring can be implemented. There are two common ways to achieve remote monitoring: through an independent connection to the Internet or through the organization’s WAN. Generally, for independent Internet connections, this is best handled only via a virtual private network (VPN) connection to ensure the security of the connection and vital security data. Remember that remote monitoring could theoretically expose the organization to a “takeover” attack in which an outsider can open doors and gates for accomplices using the alarm/access control system and may know the activities of the security force via use of the digital video system. Thus, the security of the connection is at all times vital.
For connections through the organization’s WAN, permission must be obtained from the organization’s IT department. Understand that the security system and its architecture, configuration, and management rules must necessarily then comply with the IT department’s standards.
The main issues of concern are bandwidth usage and network security. Bandwidth to a remote monitoring location can easily exceed the maximum network capacity from a remote site. A typical site may be served by one or more T-1 connections.2 A security system can easily require 3 Mbps to monitor unless it is well managed. Management is accomplished by controlling the amount of video to be sent, its image resolution, and its frame rate. For slow connections, it is advisable to use 2CIF or lower resolution and slow frame rates, perhaps one frame per second. I have designed around connections that would not support more than one frame every 20 seconds.
Network security can be ensured with proper system hardware and network configurations. Basic methods include the use of a stateful firewall.3 Many large organizations use managed firewalls.4 Managed firewalls are very expensive but provide the best possible protection.
Secure the Security System
The security system must itself be secure. The best way to do that is to secure the system at all seven layers of the OSI network model. A basic discussion of that is provided at the end of this chapter. Other important security methods covered include basic data encryption, IPSec, and wireless security.
Integrate the System to the Information Technology System
Where it is required to share the IT infrastructure for logistical or architectural reasons, there are three main concerns:
• Network security (for both the organization’s LAN/WAN and the security system)
• Multicast compatibility
Bandwidth preservation involves a simple number. No network infrastructure should ever be utilized to more than 45% of its rated capacity. If the connection is a 100Base-T connection, no more than 45 Mbps should be used. For gigabit links, no more than 450 Mbps should be used. These are absolute worst-case figures. Less utilization is better. Utilization over that amount will result in dropped UDP packets and lost camera image pixels. The worst-case utilization of both networks should be calculated in order to ensure that the infrastructure can accommodate the demands of both systems.
The best way to accommodate this requirement and to accommodate network security is to segregate the security system on its own VLAN. Each network operates in its own VLAN, even if none are implemented. The native VLAN is VLAN 0. You will implement a separate VLAN for the security system, which will both ensure bandwidth segregation and isolate the two networks so that the security system is not accessible from the organization’s LAN users.
Additionally, it is important to implement IGMP querying and snooping on the data switches in order to isolate multicast traffic. Multicast traffic is also isolated automatically by the VLAN.
Integrate the System to Other Building Systems
Integrated security systems are often integrated to other building systems, including elevators, building automation systems, parking control systems, irrigation systems, lighting control systems, public address systems, and telephone systems. There are two basic types of interfaces to other systems: dry-contact relay interfaces and data interfaces between system computers.
Dry-contact interfaces are basic but powerful. They also have the advantage that changes in system software versions of either system will not likely affect the interface as long as the logic elements remain in effect. Their downside is space and capital cost. I am very fond of dry-contact interfaces because of their dependability and durability.
The best argument in favor of data interfaces is that the physical interface is very simple. Often, the physical interface is affected just by plugging both systems into switches (sometimes on opposite ends of the building). However, for the interface to work, both manufacturers must
• Agree to the interface and its attributes and functions.
• Coordinate an application programming interface or other method.
• Coordinate the databases of both systems so that information can be exchanged.
Many manufacturers have cooperated to create useful functions. However, if the function you need has not been previously agreed upon by the two manufacturers that you are considering using, it is best either to consider other manufacturers that have cooperated or create the function in relay logic.
Relays can be combined to perform almost any function. They can count, set timers, create “and” or “or” functions, and even create “exclusive or” functions. Although this may seem hardware intensive, the results can be excellent. I and other consultants have been asking the security system manufacturers for many years for products that can perform Boolean algebra logic cells. Finally, they are being developed. New alarm/access control and digital video systems are being developed that have counters, timers, and addressable memory and can perform all manner of logic functions. Many higher functions can be performed with these tools, as described next.
One of the best arguments in favor of relays and against data connections is that relays are fixed and are not subject to disconnection when a new software update is installed in one system that does not contain the necessary programming elements to communicate with the other software in the system, as did the original software version. Such unplanned obsolescence can occur if both manufacturers are not fully committed to maintaining interoperability through software version changes, or if the alarm/access control software manufacturer issues a version update or patch but has not yet gotten around to updating the interface related to that version update or patch.
Special Implementations
System Maps
Virtually every integrated security system should be equipped with a GUI that includes response maps. Response maps show the locations of security system devices within the structures and around the site and provide the security console officers with information from and control over those devices in a graphical environment.
A software map should be developed for the overall campus site and for each level of every building on the campus that contains security system equipment. For a site with two four-story buildings, this would require one map for the site and eight floor maps. Software map backgrounds can usually be obtained from the architect (on new construction) or from the owner. It may be necessary to develop original maps for retrofit installations. Fire egress plans can be used as a template for this.
For the site map, locate an icon for each controlled gate and for every perimeter detector (as a zone) and every gate intercom. Also configure an icon on the image of each building that links the map to a “riser” diagram of that building, showing each floor (where there is an icon on each floor linking the riser to that floor plan of that building.
For each floor plan, show an icon representing every alarm detector and every access-controlled door and intercom.
There are two schools of thought on how to show video cameras:
- Show an icon for each individual video camera (showing the field of view for fixed cameras).
- Show a “layout icon” for each area of the building or site, where the layout icon will call up a “salvo” of video cameras that are all geographically related to the same area.
The second approach is much more useful for a console guard because it gives him or her a complete idea of what is happening in a contiguous geographical area.
Configure video layouts of every geographical area and create a layout icon on every map that can link to the video layouts related to those geographical areas.
Finally, create a video guard tour that “walks” the console officer throughout the facility, using the video layouts created above. Video guard tours can be conducted several times per hour, but they should not take the place of physical guard tours where the guard walks the areas at least once per hour.
Boolean Algebra Logic Cell Implementation
Boolean algebra logic cells are the key to amazing integrated security system functions as well as to truly cost-effective installations. You can achieve virtually any function you can imagine with a combination of counters, timers, input and output points, memory, and Boolean algebra logic cells. This section presents only four examples developed by me for various projects. Your imagination will undoubtedly develop an endless array of others.
“And” Gate Alarms
A petrochemical terminal had a perimeter alarm system that comprised 52 microwave zones just inside its outer fence line. These microwave alarms occasionally caused nuisance alarms, which the firm wished to reduce. I designed a system of 35 fixed video cameras on existing camera towers to view the microwave alarm zones. The fixed cameras were configured with video motion detection to detect movement within the areas of the microwave alarms. The triggering of a motion alarm by either the microwave detectors or the video motion detectors would cause an alert, whereas the triggering of motion detection by both systems simultaneously within the same zone would cause an alarm.
With an alarm/access control system with Boolean algebra logic cells, this can be accomplished by only 52 hardware-based alarm inputs for the microwave detectors. The video motion alarms are in the video software, and they are transmitted to the alarm/access control system via software. The alarm/access control system compares the inputs and causes either an alert or an alarm, based on the Boolean algebra logic cell formula.
In a conventional alarm/access control system without Boolean algebra logic cells, this same result requires (now this will not be easy to follow, so stay with me) 52 hardware alarm outputs for the video motion alarms from the video system to the alarm/access control system from the 35 video cameras, 104 hardware alarm inputs (52 for the microwave detectors and 52 for the video motion alarm inputs from the 35 cameras), and an additional 104 outputs to reflect the condition of the alarm inputs are then hardwired together to create the 52 “and” gates, which are then wired back into an additional 52 alarm inputs in the alarm/access control system as “and” gate alarm inputs. The total hardware count is 156 outputs and 156 inputs. Understand why Boolean algebra logic cells are so popular with designers who understand them and with the clients who would otherwise have to pay thousands of dollars for all those extra inputs and outputs? It is easy to understand why.
Local Alarms
Suppose we have a door that gets a lot of traffic during the day and that some people occasionally prop open (e.g., a stairwell door). We do not want it propped because this would violate fire code. In a system with Boolean algebra logic cells, we simply use the single door alarm input and a single output control near the door, two timers, and a logic cell. During the day, if the door is propped open, a timer is engaged when the door opens and it counts to perhaps 45 seconds. If the door is still open at 45 seconds, we engage the output control, which is connected to a local alarm at the door. This tells people in the vicinity of the door to close the door. If they do not close it within perhaps an additional 30 seconds, we send an alarm to the security console stating that the door is propped open so that the console operator can dispatch a patrol officer to close the door. At night, the door does not act as a propped door alarm but, rather, activates an alarm immediately upon opening, based on a software schedule. In a conventional system without Boolean algebra logic cells, this same function can be achieved by means of a hardware-based prop-door alarm, which has a key that a patrol officer turns on and off.
Lighted Paths
As a convenience to late-working employees, a client asked me to design a system that would turn on lights and air-conditioning for any employee who arrived late at night to work (these were IT workers who often had to come in to work in the wee hours of the morning when something did not work correctly in the system). I established a database of workers and where they worked, and I designed a lighted-path algorithm to turn on the lights in the parking structure and all the way to their offices or cubicles, specific to each employee, as well as to the snack room and the bathrooms. The lights stayed on until the employees logged out of their computers.
Lights/HVAC After-Hours System Billing
In response to a client request, I designed a system that provided lights, heating/air-conditioning, and plug power for employees who worked late or on weekends. Each elevator lobby had a card reader on a panel with three buttons (lights, heat–A/C, and reset). Upon entering the workspace to work late, an employee would present his or her access card to the reader and press one or both service request buttons. This would energize lights, heat–A/C, and plug power for 2 hours. Ten minutes before the end of the 2-hour period, the lights would flash once so that the employee could request more time if needed. If the employee left during the 2-hour period, he or she could present his or her card once again and press the reset button, ending the timing cycle. At the end of each month, a report (custom written for this purpose) presented a bill to each tenant for its usage, with a full audit trail of who made the requests, the date and time of the requests, and the time outs or resets. The system was popular with the tenants. Although commercial products exist for this purpose, they cost tens of thousands of dollars. This system was installed in a small four-story building for only the cost of the readers and pushbuttons, plus a small cost for the creation of the Boolean algebra logic cells and the monthly report. The alarm/access control system had an additional user-defined field for each cardholder that defined what lighting zone the employee sat in so that it knew what lights and A/C to turn on.
You can probably imagine dozens of other applications for Boolean algebra logic cells.
Custom System Reports Implementation
In addition to the dozens of useful reports each access control system has available today, it is also possible to write custom reports that are very useful. One example was mentioned previously with regard to the after-hours lighting report. This section discusses a few more examples.
Exclusion Reports
It is important to know which employees entered and left the site each month. However, it is perhaps more important to know which cardholders did not use their cards within the past month. These may be terminated employees whose cards are still in the system. At a minimum, all such employee cards should automatically be suspended until the employees return. However, a good report is one that will list all active cardholders who did not use their cards. This can be done with an exclusion report comparing active cardholders against card usage.
Nesting Reports
In a parking structure that had little room for both visitors and employees, the first two floors were set aside for visitors, and the upper floors were segregated for employees by reading a toll tag-type card on the employees’ windshields from an overhead reader, coupled with a vehicle gate. The old employee toll tag readers and gates at the ground-level entrances were set to “open” so that visitors could freely enter the parking structure and access the first two floors. The problem was that employees felt free to park in visitor spaces, leaving no spaces for visitors. The solution was to reengage the toll tag readers on the ground floor and have visitors check in via intercoms at the ground floor. The console officer would open the gate for each visitor and the gate would open automatically for employees, having read their employee toll tag cards on their windshields. A custom report was prepared that compared employee usage at the ground floor with the reader that granted upper floor access. If an employee parked in the first two levels instead of on the upper employee levels (if an employee did not clear past the upper tag reader within 5 minutes), the custom report identified the employee as a visitor area parking offender and the employee was counseled by his or her supervisor with a warning. If the employee reoffended, parking privileges to the structure were suspended for 30 days, requiring the employee to find parking in the surrounding neighborhood and walk to the building. For those few employees who tried to fool the system by stating that they were visitors, the toll tag gave them away as employees, and they were turned away. The system proved to be very effective at making spaces available for visitors in an area with very few outside parking spaces.
Securing the Security System
This frankly is the reason that I wrote this book. As a designer, I have been astonished at the number of integrated security installations I was asked to look at that were totally unsecured. While this was not a big problem when security systems were on totally proprietary communication architectures, the advent of TCP/IP network infrastructures for security systems makes this a top priority. It makes no sense whatsoever to spend hundreds of thousands (sometimes millions) of dollars on an electronic security system to secure a facility if the security system itself is not secure! Simply put, it is utterly irresponsible to design a security system that does not secure its TCP/IP network, data, and programs.
Many TCP/IP-based security systems are installed without encryption or any other type of network security. I am fascinated by a security industry that does not secure its own systems. This could be the height of technical incompetence and moral (and possibly legal) irresponsibility.
Device and Transmission Security
Architectural Security
The OSI reference model (OSI seven-layer network model) has many opportunities to both secure and exploit weaknesses in data communications. The OSI levels have been discussed previously; here, I discuss how those layers affect the security of the system and the organization.
OSI layer 1 is the physical layer. It is imperative to prevent physical access to network switches, routers, firewalls, and servers if the security system is to be secure. All these devices should be behind locked doors and in alarmed rooms.
OSI layer 2 is defined as the data link layer. This is the layer on which switches operate. Each TCP/IP device has a physical address called a media access control (MAC) address. This address is unique for every device that is hard coded into the network interface card of every TCP/IP device. The MAC addresses of the devices within the system should be stored in a table, and those addresses should be reserved such that they are the only authorized devices on the network, allowing no other devices on the network. Additionally, network switches should be programmed to detect whether a device reporting a given approved MAC address is in fact the real device, or if the MAC address is being “spoofed” by a rogue device.
OSI layer 3 is the network layer. This is the layer on which routers operate. This is often called the protocol layer. Layer 3 manages the IP protocol. Subnets, supernets, VLANs, and VPNs are all managed using OSI layer 3.
OSI layer 4 is the transport layer. Layer 4 manages TCP, UDP, RTP, and other protocols. Better network switches provide for prioritizing of certain packet types (e.g., intercom traffic over video traffic). Layer 4 devices include firewalls and layer 4 session switches.
OSI layer 5 is the session layer. Layer 5 opens and closes network sessions, controls the establishment and termination of links between network devices and users, and reports any upper layer errors. Secure Socket Layer security operates on layers 5–7. Layer 5 data management can also optimize network data traffic by establishing a TCP proxy that reduces the amount of outside network traffic allowed to see the host.
OSI layer 6 is the presentation layer. Layer 6 performs network encryption and compresses and decompresses data.
OSI layer 7 is the application layer. Layer 7 manages application usernames and passwords.
A good network designer secures his or her system at all seven layers of the OSI network model. Any layer that is not secured is vulnerable to an internal or external system hacker.
Data Encryption
Encryption is essential for any wireless network traffic and is a good idea for all data on a security system, especially alarm/access control data, which if hacked could unlock doors, open gates, and bypass alarms.
Encryption Basics5
Encryption is the process of converting a readable message into something that is unreadable by anyone who is not in possession of the appropriate encryption key (Fig. 18.1).
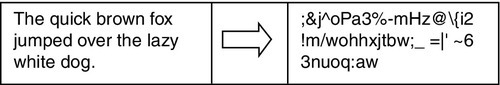
There are two common techniques of encryption: secret key and public key cryptography. These are also known as symmetric key and asymmetric key cryptography, respectively. Secret key cryptography involves using the same key for both encryption and decryption. Public key cryptography uses only one key (a public key) for encryption and its mate (a secret one—private key) for decryption.
Public key encryption permits one to publish the public key, allowing many people to know and use the key to create messages that can only be decrypted by someone with the secret (private) key. Once encrypted, the public key will not open the message, making it secure from everyone with the public key. Public key encryption is best used with devices such as a smart card that holds the private key. One of the best public key systems uses a smart card that continuously displays a rotating number that must be input and matched to the private key. After a few seconds, the number changes, making the last number useless to anyone who has captured it on a sniffer.
Secret (private) key encryption is best used as a single-use encryption method.
Encryption keys can be any length, from a few characters to many. Most commercial and governmental keys are from 40 to 256 bits. The longer the key, the longer it takes a hacker to conduct a “brute force attack” in which the attacker tries all possible combinations until he or she finds one that works. Encryption specialist Kevin Henson has developed a 40-kilobit encryption key that can encrypt or decrypt a megabyte of data in less than one-quarter of a second.
Internet Protocol Security
Internet Protocol Security (IPSec) is a set of protocols defined by the Internet Engineering Task Force to provide IP security at the network layer (OSI layer 3). IPSec is highly recommended if the security system is to be run on the organization’s WAN, even if it is on its own VLAN.
Radio Frequency Security
When a designer specifies a radio frequency (RF) infrastructure, there are two major security concerns. I call them the CNN factor and the Volkswagen Bus factor. No client wants video from its cameras showing up on CNN, and no client wants an 18-year-old sitting in an old Chevy Vega with a laptop computer attaching to the wireless network security system. Other concerns include the following6:
• Denial of service (DoS) attacks
• Surveillance
• Impersonation (man-in-the-middle)
• Client-to-client intrusion
• Client-to-network intrusion
• Rogue APs (access points) and ad hoc networks
Countermeasures
The following measures help secure RF infrastructures:
• Probing/network discovery: Encrypt the SSID connection. There is little that a network designer can do to prevent probing and network discovery other than to turn off the SSID message. However, that does not prevent a determined hacker. I suggest using 802.11a or another less used frequency for backhaul traffic. The network cannot be probed if the hacker does not possess equipment that can see the network. Encrypting the SSID helps to prevent entry.
• DoS attacks: DoS attacks can take several forms, but all of them are carried out with the intent to deny access to the appropriate user. A common DoS method is RF jamming.
• RF jamming: RF jamming involves flooding the airwaves with 802.11 frequency energy. There is little that can be done about this. I recommend using either 802.11a or another less used frequency for backhaul (there is less equipment in use and, therefore, less chance of jamming).
• Deauthentication attacks: In a deauthentication attack, the attacker floods the airwaves with spoofed MAC addresses. Eventually, the system loses track of what devices it is connected to and will try to search for another AP. There are several effective means to prevent this type of attack, including detection of MAC address spoofing. Other countermeasures can log the attempts and approximate the physical location of the attacker based on signal strength in proximity to his or her nearest wireless node.
• Surveillance: Encrypt all data on the RF system using a strong encryption algorithm. This helps prevent your video from being illegally exported to other systems. I recommend the use of IPSec for this purpose.
• Impersonation: Often, solving the surveillance problem also solves the impersonation problem. Another type of impersonation attack is the man-in-the-middle attack. This type of attack allows the hacker to add, delete, and modify data. An intrusion detection system can be effective in preventing man-in-the-middle attacks.
• Client-to-client intrusion: Many designers make their servers nearly impervious to outside attacks but fail to protect client devices. Diligent maintenance of network authorizations can prevent this type of attack. I strongly recommend against allowing business user clients onto the security system wireless backbone, even if a VLAN is used.
• Client-to-network intrusion: Multilayer security as described previously is effective in preventing this type of attack.
• Rogue APs and ad hoc networks: Diligent network management can prevent a client from setting up a rogue access point.
Archived Data Security
Archiving Principles
Data archiving is the process of storing the record of events within the system for future retrieval and analysis. As data flows into the server for the system to process, an archive file captures a copy of the data and stores it in a fashion that is indexed for retrieval. Data are typically stored for alarm/access control, system status change events, video streams, and audio streams. These will likely be stored on separate disk volumes or libraries.
Backups and Recoveries
Data can be stored either in its native form or as a backup for a recovery. Typically, both may be used, with native data stored for recent history on disk within the primary server and backup files being used to store older data on disk or tape on extended storage.
For extended storage beyond the capacity of the disks within the server, an extension box is created that includes a backup server and disk and/or tape storage. For large storage requirements, a tape carousel is appropriate. These should be attached to the server with a separate NIC in the server and connected directly to the backup server or, if several servers are involved, through a backup switch, separate from the primary backhaul network. This is to minimize the effect of archiving data traffic on the primary backhaul network. This architecture is called a storage area network (SAN). It is the best choice for large video archives. If the archive server is connected onto the backhaul network (network attached storage), the additional traffic caused by the archive data may cause the backhaul network to begin losing video packets, which has a negative effect on the quality of both live and archived video images.
Business Continuity Management Servers
Large enterprises value archives and often place their archive servers in a separate physical location. Such servers are called business continuity management (BCM) servers. It is common in large enterprises to have both live and archive servers locally, or in a primary data center, and BCM servers in a separate data center. In such cases, these will be an entire duplicate set of servers, usually configured as fail-over servers, ready to take over on a moment’s notice. This requires a high-speed connection capable of supporting all the data.
User Classes and Authorities
Users are not all alike in terms of their access privileges. They are categorized into several major classes:
• Administrators: Administrators have all rights on the system, including the right to add, modify, and delete data and programs.
• Managers: Managers have all rights on the system except to add or delete programs or to delete data. However, a manager is permitted to issue authorizations to lower level users and to manage how they can use the system. Typically, some system reports are also reserved for managers.
• Supervisors: Supervisors can manage all live activities in the system, including screen configurations and access to high-security areas.
• Guards: Guards may be permitted access to view certain classes of cameras and not others, and they may be permitted to lock and unlock or open certain gates. Typically, guards can see and respond to all alarms.
• Roving guards: Roving guards may be issued wireless tablets or PDAs that may grant access only to the region of their patrol.
Login/Logout Security (Card Controls Operating System)
One of the most important and most often overlooked elements of security system data integrity is solid proof of who was logged onto a guard workstation when an event took place. It is stunningly common to discover that the person who the system records as having been logged in was in fact not even at work at the time of a security event. In the hands of a skilled defense attorney, this can be argued to void the validity of the rest of the data security in the system.
The most effective way to verify that the logged operator is in fact the operator on the console is to use a presence reading card reader tied to the workstation login. Using this method, login to the guard workstation is automatic when the guard places his or her proximity access card in a reader slot. With keys on the same ring as an access card, logout is ensured whenever the guard leaves the console for a restroom break or at the end of a shift.
Cutting-Edge System Security
For extremely high-security systems, special additional security measures can be taken that can effectively make the security system invisible on the network. In the simplest method, the security system is programmed onto its own VLAN on the organization’s WAN. More sophisticated methods also exist that are suspected of being used by intelligence agencies of certain governments. These are accomplished with the use of nonstandard protocol data encapsulation. Clever encapsulation configurations can create a security system that is virtually invisible on the business network. One reported method even includes a “protocol diode” that could theoretically be configured to allow a “one-way mirror,” meaning that the system can look into the common data architecture without being seen by that WAN.
System Cutover Day
On the day on which the new security system is to be cut over to replace an older one, nerves can be frazzled. The setting up of a temporary data infrastructure to run the system can help ensure that all elements of the new system are in good working order and communicating properly prior to actual placement of the system on the primary data network. Bench testing is also a recommended option.
Summary
System finalization includes commissioning, training, and acceptance. Steps include device IP addressing and startup, device communications and programming, and securing the security system.
It is the responsibility of the designer to ensure that the security system design includes securing the security system. Security measures should be taken at all seven layers of the OSI networking model, where possible.
RF systems in particular should be secured because their infrastructure has no physical security. Common RF attacks include
• Denial of service attacks
• Surveillance
• Impersonation
• Client-to-client intrusion
• Client-to-network intrusion
• Rogue APs and ad hoc networks
Archived data must also be secured, and a business continuity program should be developed for the security system.
User classes and authorities should be set up, and logon/logoff security should be considered. System cutover should be well planned so as to occur smoothly.
System maps should be created that allow the security console officer to easily control the system and get a full situational view of what is going on in the facility.
Questions and Answers
1. Which of the following is not appropriate for a finalization and commissioning checklist?
a. Train the operators how to use the system
b. Connect each field device to power and its digital switch as its installation is completed in the field
c. Load and commission the server and workstation operating systems
d. Configure connections to all of the digital video system cameras and intercoms
2. Which of the following is not part of commissioning alarm/access control system field devices?
a. Set up access control groups
b. Set up schedules and time zones
c. Set up the video system
3. A video guard tour is:
a. A consecutive sequence of individual video guard tour stops.
b. Individual cameras
c. Individual guard tour stop and check-in buttons along a physical guard tour
d. Stop-and-frisk stop points
4. Video guard tours are:
a. Used with intercom stations to complete a garage safety package
b. A part of every video camera, usually included in its packaging
c. A basic element of successful integrated security system functions and should be included in every monitored system
d. None of the above.
5. The ultimate expression of video guard tours is the:
a. Managed guard tour software
b. Video pursuit function
c. Professionally managed guard tours
d. Pursuit of happiness
6. Physical Security Information Management Systems (PSIMs):
a. Are an especially elegant form of GUI
b. Are useful to watch for migrating species
c. Are useful to watch dangerous surrounding facilities
d. None of the above
7. Video pursuit allows a console security officer to:
a. Pursue intruders where there are no video cameras
b. Follow vehicles leaving the facility
c. Follow employees into the restroom
d. “Follow” a subject of interest through a facility using available video cameras as though he or she were walking along with them
8. The entire security system can and should be designed to:
a. Facilitate easy operation by untrained individuals
b. Facilitate the organization’s security policies
c. Facilitate a comfortable chair
d. None of the above
9. You can achieve virtually any function you can imagine with a combination of
a. Boolean algebra logic cells
b. Counters, timers, input and output points, memory, and Boolean algebra logic cells
c. Keystrokes
d. None of the above
10. It makes no sense whatsoever to spend hundreds of thousands (sometimes millions) of dollars on an electronic security system to secure a facility:
a. When guards and dogs can do the job
b. When there are no policies and procedures
c. If the security system itself is not secure!
d. None of the above
Answers: 1: a, 2: c, 3: a, 4: c, 5: b, 6: a, 7: d, 8: b, 9: b, 10: c
