Alarm Detection and Emerging Video Technologies
Abstract
Chapter 16 includes information on many types of alarm detection technologies including interior and perimeter systems, point systems, volumetric systems, dual technologies, the use of video technologies for detection and emerging detection technologies.
Alarm detection technologies include point detectors, volumetric detectors, and line detectors. Point detectors include magnetic door switches and duress switches. Volumetric detectors include passive and active infrared, microwave, ultrasonic, and acoustic detectors. Dual-technology detectors reduce nuisance alarms. Video systems can also serve as volumetric detectors and as either a security alarm system or a forensic analytic system.
Perimeter detection systems include Leaky Coax Detectors, Capacitance Detectors, Seismic Detectors, Fber-Optic Detectors, Common-Mode Detectors, Pneumatic Weight Detectors, Perimeter Video Detectors, Thermal Video Cameras, Lidar and Ground & Short-Range Radar.
Miscellaneous detectors include 4 to 20-mA current loop detectors and temperature, humidity, and water level detectors.
Introduction
This chapter includes information on different types of alarm detection technologies, including interior and perimeter systems, point systems, volumetric systems, dual technologies, and the use of video technologies for detection and emerging detection technologies.
Alarm Detection Technologies
Alarms are the mainstay of security. The oldest security systems involved a public responsibility of citizens to stay awake all night and patrol in shifts, calling out for help if any threat was discovered.
There are three basic types of detection systems:
• Point detectors (e.g., door position switches, glass-break sensors, duress switches)
• Volumetric detectors (including infrared, microwave, ultrasonic, and video)
• Line detectors (e.g., seismic, pressure, capacitance)
Alarm detectors may be used indoors or outdoors. Indoor applications can be of any type. Outdoor detectors are most commonly used on perimeters, although there is some use of volumetric detectors.
Point Detectors
Magnetic Switches
Simple Magnetic Switches
Simple magnetic switches are used to detect the opening of doors and windows. A basic magnetic switch comprises two parts— the magnet and a magnetically sensitive switch (usually a reed switch enclosed within a glass envelope). Switches may be either normally open (close on alarm) or normally closed (open on alarm). Some are available in a Form-C contact (your choice of normally open or normally closed, both in one switch).
There is a wide variety of magnetic switch form factors for every need. Switches are available both for surface mount and for concealment within the door and its frame.
Economical switches are usually surface mounted and enclosed in a plastic case, whereas better switches may be concealed. Switches are made for unique applications, such as concealment within a wood door or a hollow metal door. These cannot be substituted for each other.
Switches rated for industrial or outdoor use may be fitted with heavy aluminum enclosures, some even with integral conduit fittings.
Balanced Bias Magnetic Switches
One problem with simple magnetic switches is that it may be possible for an intruder to place a magnet next to the switch while opening the door, fooling the system into missing the fact that the door or window has opened.
Balanced bias magnetic switches are designed for high-security applications. By floating the magnetic switch in its case between two magnets oppositely polarized (one horizontal and the other vertical), any disruption in the magnetic field, such as opening of a door or window, will cause a change in state of the magnetic switch. The very act of placing a magnet next to the switch to fool the switch will be seen by the switch as an alarm.
Duress Switches
Duress switches are a class of switches that are intentionally triggered as a call for help by a person who believes that he or she is under threat. Usually, these are in the form of a switch placed under a counter or in the knee-well of a desk that the victim can activate while in his or her normal working position. Duress switches are common in banks, emergency rooms, convenience stores, public counters, and other places where a person might express angry or violent behavior.
There are three factors of concern in the design and use of duress switches:
• The switch must be convenient and quiet so as not to alert the subject of the duress alert.
• The switch must exhibit a positive feedback so that the victim knows that a call for help has gone out.
• The switch must not activate accidentally.
A number of designs have been created to deal with these concerns:
Two-Finger Switches
Two-finger switches are a type of switch that requires two separate pushbutton switches to be pressed simultaneously in order for an alarm to occur. The two switches are best arranged as a finger and thumb squeeze configuration to ensure that they cannot both be triggered accidentally by a knee or object. These switches are very effective but must be custom made.
Pull and Plunger Switches
Pull switches require the victim to pull out a plunger with the thumb and forefinger. This is a positive action and cannot be accidentally triggered. Plunger switches require that a plunger be pushed deep into a ring around the switch that otherwise protects the plunger from accidental triggering.1
Footswitches
Footswitches are common in areas where the victim may be asked to keep his or her hands above a counter, such as in a bank. Footswitches are activated by placing one’s foot under a lever and lifting it with the toe, thus activating the switch.
Bill Traps
For banks and cash counters, a type of duress switch called a bill trap causes an alarm if the last bill in the drawer is removed. The bill is placed in the bill trap and left there constantly, thus separating two contacts of a switch. When the last bill is removed, the switch makes contact, sending a silent alarm. Thus the famous movie line, “I think I hear the silent alarm!”
Resets
All duress alarms should be configured to latch until reset. This is important so that if one of several duress alarms is tripped along a line of cash drawers or service counters, it is possible to determine which one was tripped.
Elegant Duress Switch Implementations
Although simple duress alarms are very helpful, it is not good to send security officers (or even police) into a situation with guns drawn where innocent people could be harmed. These implementations help ensure that the console security officer knows exactly what is going on at the location of the duress switch:
• Audio and video verification: Wherever a duress alarm is used, video and audio verification is appropriate. It is difficult to explain to a courtroom why such verifications were found to be important at a back door but not where an angry, confrontational, possibly gun-toting person was anticipated. A microphone at the counter (you do not want two-way communications here) and video camera with a commanding view of the room are very useful in assessing the situation.
• Ring-back: A ring-back system has been used to assure the victim that his or her duress call was acknowledged and that help is on the way. A simple wrong number to the victim’s phone will keep the subject blissfully unaware that he or she is under observation.
• Visual indicator: Some clients want some kind of visual indicator that the alarm has been acknowledged. This can be in the form of a normal-appearing activity. I have used everything from a momentary and unconcerning telephone ringing across the room (a nonstandard ring tone for the users) to a ceiling fan that switched on in response to a duress alarm. In both cases, those actions were inconsistent with normal operations to the authorized users but would not create an alert to the attacker.
Volumetric Detectors
Volumetric detectors are designed to detect movement within a defined space. All volumetric detectors sense a change in some condition within the space, typically a change in heat signature or motion.
Passive Infrared Field Detectors
Passive infrared (PIR) field detectors sense a change in heat across an infrared photo-transistor. The photo-transistor does not sense motion, but by fabricating a lens in front of the photo-transistor, it is possible to create a series of invisible “fingers” across which a subject might walk or crawl. As the subject moves across the fingers of detection, the photo-transistor senses a change in heat signature from the heat generated by the subject versus the ambient heat in the space. As the change is sensed, the transistor current crosses a predetermined detection threshold, activating a dry-contact relay in the detector.
PIR detectors are most useful in areas where the ambient temperature is below 95.6°F (35°C) because above that temperature the sensor cannot distinguish the difference between the heat generated by a human body and the ambient heat.
PIR detectors are also most useful when configured so that a subject must walk across the fingers of detection. They are least sensitive as a subject walks toward or away from the detector. This is because the detector lens is configured to create temperature differentials between the fingers of detection that the photo-transistor can easily detect. When walking across the fingers, the detection is natural; when walking toward the detector, a subject must transverse an area comprising at least two or three fingers of detection before detection occurs.
PIR detectors are used both for alarm detection and to sense the presence of a person about to exit through an access controlled door. In the latter case, the detector is often configured to unlock the electric lock and to bypass the door alarm to allow the legal exit without an alarm. The former type of detector is configured with detection patterns of from a few degrees to 150 degrees of arc. The latter type of detector is configured to position directly above a door and creates a “curtain” pattern looking down on the door handle. They can often be positioned to look back a few feet to sense a person approaching the door.
Active Infrared Detectors
Reflection Detector
The simplest type of active infrared (IR) detector is one that has an infrared photo-diode coupled with an infrared photo-transistor in the same enclosure. The photo-diode generates infrared light, and the photo-transistor senses the infrared light. These are both visible through lenses on the side of the enclosure. The enclosure is positioned opposite a prism reflector, usually across a door, gate, or other portal. The detector is used to sense an interruption in the beam, typically a person, vehicle, or object moving through the beam.
Reflective detectors are useful for short distances and best used indoors, where ambient light is less likely to overwhelm the photo-transistor. These are commonly used as door alarms to alert a shopkeeper that a customer has entered the shop. They are popular because they are easy to install, having only one active element so wiring is simplified.
Beam Detectors
Infrared beam detectors overcome the inherent problem of reflective IR detectors—that is, the problem of ambient light interfering with the detection. They do this by separating the photo-diode and photo-transistor into separate enclosures. For long-distance detection, the photo-diode may be replaced by an IR laser. This configuration allows the photo-transistor to more precisely sense the IR light.
IR beam detectors are commonly used to detect entry through a perimeter and may be used to surround a property or asset. These are typically high-value assets, including high-end homes, industrial sites, and corporate headquarters. Because of the value of the assets, exploits for early IR beam detectors were developed. These mainly involved replacing the true IR light source with a handheld source in the possession of the intruder. To counter this, manufacturers developed pulsed IR beams. Any attempt to replace the true IR light source with a false source automatically causes alarm detection.
IR beams are most useful on ground that is flat or on a continuous smooth grade without intervening hills and valleys because these create opportunities for the intruder to crawl under the beams. IR beams are available to span distances from 10 to 600 ft.
IR beams are useful wherever a long straight line over level grade must be protected. Exploits for IR beams include the use of ladders, trucks, and even pole vaults—anything that can be used by the subject to go over the top of the beams.
Microwave Detectors
Microwave detectors are made in a variety of types for use indoors and outdoors. Microwave detectors have either an elliptical-shaped detection pattern or a balloon-shaped pattern. Microwave detectors are either monostatic or bistatic. Monostatic detectors have a microwave transmitter and receiver both in one package. Bistatic microwave detectors separate the transmitter and receiver into two units.
Monostatic Detectors
Monostatic detectors are commonly used indoors and in small, contained areas. They are most sensitive to subjects moving toward or away from the detector. Monostatic microwave detectors are essentially small radar units that detect the “echo” of the transmitted signal.
Monostatic detectors operate at such a high frequency2 that they are able to detect the movement of gasses within the space, including gasses within fluorescent fixtures. Many designers have been surprised to discover that their systems false alarm when fluorescent fixtures start flickering. Designers are also sometimes startled to discover that frequent false alarms are in fact caused by the detection of people moving on the other side of a wall. Microwave detectors operate at a frequency high enough to detect movement through walls, particularly gypsum board walls.
Exploits for monostatic detectors include very slow movement (less than 1 ft every 5 minutes) and creating a string of continuous false alarms over a long enough time so that the monitoring center may ignore the alarm when it is real.
Bistatic
Bistatic detectors operate completely differently from monostatic detectors in that they are not detecting an echo signal but more closely resemble the operation of active IR beams. By separating the microwave transmitter and detector, greater definition of the detection zone is possible, as well as greater distances. Bistatic microwave detectors can “reach” distances of up to 1500 ft.
Bistatic microwave detectors operate at a very small wavelength (0.75–3 cm), making detection of any object larger than 3 cm a virtual certainty within their detection field. Bistatic microwave detectors should be overlapped when used to protect a perimeter so that there are no areas where an intruder can step over or between the patterns of any individual detector. Detection patterns can be adjusted from very narrow to up to 40 ft.
Microwave detectors are prone to false alarms when positioned across any body of water (even a small mud puddle) and during weather patterns such as snow, high wind, rain, or fog. Wind is problematic due to the number of small blowing objects, including leaves and debris.
Bistatic microwave detector exploits include transiting during periods of heavy wind and rain, when the detectors are likely to be yielding many nuisance alarms.
Ultrasonic
Ultrasonic detectors use a high-frequency transducer just above the range of human hearing (typically 40–60 kHz). Ultrasonic detectors predate the introduction of monostatic microwave detectors for indoor use and have largely fallen into disuse.
Ultrasonic detectors broadcast a high-frequency audio signal and listen for the same signal. They detect the Doppler shifted wave reflected by a moving object within the field of detection. Ultrasonic detectors are prone to nuisance alarms caused by keys jingling, vacuum cleaners, and numerous other problems.
Acoustic (Glass-Break) Detectors
Acoustic glass-break detectors comprise a microphone and discriminating circuit designed to listen for the specific sound signature of glass breaking. Acoustic glass-break detectors are placed within close acoustic proximity of the glass to be monitored (typically within 15 ft). They must have a clear line of sight to the glass and may not detect reliably if they are obstructed.
Early acoustic glass-break detectors were prone to all of the same problems as ultrasonic volumetric detectors, but these have largely been resolved by use of discriminating audio circuits.
Do not confuse ultrasonic detectors with glass-break detectors that sense in the ultrasonic range. The difference is that glass-break detectors do not transmit an ultrasonic frequency but instead use a microphone to listen for the specific sound of glass breaking within the ultrasonic frequency range.
Dual Technologies
Serious designers always try to design detection systems that complement the weaknesses of each other in order to ensure detection in any circumstances. Recognizing that infrared and monostatic microwave detectors have complementary nuisance detection factors, manufacturers have packaged both together into a single unit, thus ensuring reliable detection in most circumstances. Many can be configured to alarm if either (“or” logic) or both (“and” logic) detectors sense the presence of an aggressor. The infrared and microwave each have different sensing patterns and responses to objects moving in their path. Infrared detectors sense most readily when an aggressor is moving across their pattern,3 and microwave detectors sense most readily when an aggressor is moving toward or away from the detector.4
These detectors can detect objects moving any direction within their field (when set to “or” logic) and are considered more reliable than either infrared or microwave detectors alone.
Emerging Video Technologies
Volumetric Detectors
Video detection systems are somewhat unique in that they combine both detection and assessment into a single process. As the video algorithm detects possible inappropriate behavior, the system makes the video available for further human assessment.
Video Motion Detectors
The simplest form of video volumetric detection is motion detection. Such algorithms are available on even the least expensive of multiplexers, digital video recorders, and other video processing units. In their simplest form, they define an area on the screen using large block pixels. Settings include sensitivity (how many shades of gray each pixel must change in order to cause a detection) and duration.
Intelligent Video Detectors
Anyone looking at a specific video image can easily distinguish motion and certain troubling behaviors. Using advanced digital signal processing image evaluation algorithms, it is possible to detect a number of inappropriate behaviors on many cameras simultaneously without the need to have console officers viewing all those images at all times.
The term the industry uses for this is intelligent video. Although intelligent video still has a long way to go in terms of both accuracy and cost, it shows great promise. Video detection algorithms can be programmed as to the area of detection, the type of detection (e.g., motion, absence of motion, loitering, left objects), and the schedule of detection.
This approach allows for much better utilization of human resources, freeing guards for patrol and response. These solutions are also highly scalable. Where increased video detection tasks quickly overwhelm human resources, computers can efficiently process dozens to hundreds of video images simultaneously. Intelligent video detectors are also much better than their human counterparts at enforcement of security and surveillance policies because they do not rely on the integrity or attention span of the monitoring guard.
Typically, a computer is used to render the images to the detection algorithm. Each computer can typically handle 3–16 cameras.
The systems are also capable of organizing detections into classifications, times, and dates in order to develop trend-tracking reports. They also generally archive the detection video, including a period of pre- and post-alarm activity. Intelligent video detectors typically work one or more algorithms for each camera.
One type of intelligent video detection shows great promise. One company has developed a set of detection algorithms that index their findings so that searches can be made very rapidly (in milliseconds). The system is also capable of rendering alerts, like a normal intelligent video system, and it requires many times less processing power than other systems. This system is especially useful for security analytics and is the first system to make deep video analytics practical for the typical user.5
Some intelligent video systems are better suited for indoor scenes and some are better suited for outdoor scenes, based on the type of algorithm. For example, outdoor systems are often designed to look for human-sized objects moving in a large field and may also be able to identify boats, planes, cars, trucks, busses, and even animals. One current system is able to identify the location of the object in three-dimensional space and whether that object is moving toward, away from, or across or into a zone that has been identified for intrusion detection.6 Such capabilities as plane and bus identification obviously have little use indoors.
Other intelligent video detection systems are especially adept at indoor scene detection. These often include such capabilities as identifying people loitering in a crowd or a crowd developing or dispersing, and they may be able to identify the facial features of a subject for later or real-time identification. Based on facial identification features, the level of certainty can be calculated. Some systems are pretty good at determining if an object has been left or taken. Some systems are capable of ignoring certain types of ongoing activity, such as trees blowing in the wind and mild wave action.7
Finally, video facial recognition systems can create alarms in response to the recognition of a banned individual.
Triangulation Detectors
Another type of video detector that is undergoing testing is quite unique in that it uses three video cameras to triangulate on an area in three-dimensional space to determine if an object is moved, placed, or affected in any way. Each of three cameras is set up to detect the same object from different angles. The combination of the cameras allows for much more accurate detection to determine if an object is targeted in the presence of high traffic. This system has had considerable success in early tests, such as in museum environments.
Perimeter Detection Systems
Line Detectors
Leaky Coax Detectors
Ported coax or “leaky coax” detectors comprise a direct-burial coaxial cable in which the center conductor is continuous and the shield is woven in such a fashion as to allow the signal from the center conductor to leak through the shield by virtue of the fact that the shield has openings in the weave, unlike a normal shielded coaxial cable. A radio frequency signal is sent down the coax, and some of its energy leaks into the atmosphere. The cable is buried so as not to make possible intruders aware of its presence. When the intruder steps into the field of the coax, he or she interrupts the field, causing detection. Advanced systems can pinpoint within a few feet exactly where the detection occurred.
Leaky coax systems are useful wherever there is a long expanse of perimeter to cover and the detection method should be unseen (Fig. 16.1).
Leaky coax systems must be well integrated to their environment. The systems can fail to alarm or to false alarm by virtue of their environment. For example, leaky coax systems will not detect under ponding water and may yield nuisance alarms from larger animal activity. Thus, they should be installed along crest lines (ridge lines) if possible and in areas not prone to animal activity.
Leaky coax exploits are few where they are properly installed. Leaky coax systems can fail to detect if movement is less than approximately 1 ft every 10 minutes. Few intruders have such patience.
Capacitance Detectors
Leaky coax systems are a form of capacitance detector. Other types can be mounted on or above a fence. Capacitance detectors work best if configured so that the intruder must come into close contact with the sensor, such as when used in lieu of barbed wire at the top of a fence, set off the fence fabric by a few inches.
Seismic Detectors
Seismic detectors are basically microphones that are placed into the ground to detect acoustic disturbances. A typical seismic detector is configured as a spike that is driven into the ground. These are arrayed in a line along a perimeter. Usually, the cables can be covered to obscure their presence (Fig. 16.2). Seismic detectors work well in remote areas and areas where there is little adjacent vehicular traffic.
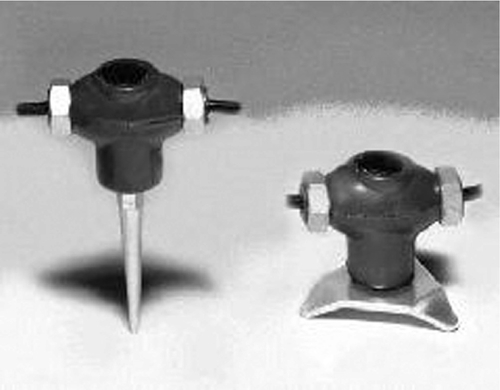
A common seismic detector exploit is to use a large vehicle to mask the sound of foot traffic.
Fiber-Optic Detectors
Fiber-optic cable can be configured to detect either breaking or deflection in the cable. It can also be configured to act as a microphone along a fence line.
A fiber-optic detector injects a pulsed signal down the fiber and monitors it for differences at the receiver, where it is compared to the signal that was sent. Any sudden change in the signal triggers an alarm. Fiber-optic detectors are immune from most environmental effects and operate reliably over a wide range of environmental conditions. The circuitry around fiber-optic perimeter sensors has become very sophisticated in the last few years. Using single-mode fiber at least one long-line perimeter detection system can detect ± 3 m along a fence line of up to 60 km (37 miles). This is useful for securing long borders, such as borders of countries.
A common fiber-optic exploit is to “accidentally” cut or damage the cable, necessitating a repair. An intrusion may occur during the repair interval (Fig. 16.3).
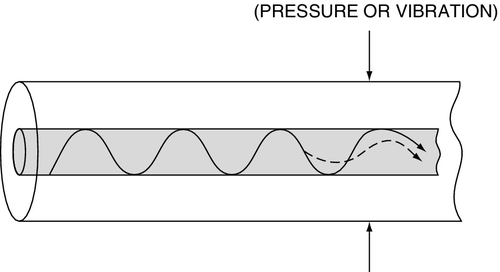
Common-Mode Wire Detectors
Common-mode wire detectors are similar in physical installation to fiber-optic detectors. Common-mode detectors comprise a pair of wires strung within a single insulation jacket. A balanced signal is sent down the cables, and they detect any difference in the signal resulting from a disruption in the cables. Common-mode detectors are typically strung onto a chain-link fence. The detector acts as a microphone, “listening” for the sound of the chain-link mesh being cut or climbed.
Common-mode detectors are subject to their environment, particularly fence condition. Fences that are loose, have large signs loosely attached to the fabric, or are connected to gate posts that might “clang” when a gate closes can all cause false alarms.
Common-mode detectors are best used on expanses of fence that are free from vegetation and animal activity and also on fences that are well maintained.
Exploits for common-mode detectors are the same as for fiber-optic detectors, in addition to the placement of an object that can cause false alarm activity.
Pneumatic Weight Detectors
Pneumatic weight detectors are a variation on the old gas station driveway alert, which was common years ago. They comprise a tube filled with air, plugged at one end, and at the other end there is an atmospheric pressure sensor.
The pneumatic tube is buried just underneath the surface. When an intruder steps onto the ground above the tube, detection occurs. Unlike fiber-optic and capacitance detectors, the area of the detection is imprecise; only the zone is detected, not the location on the zone.
Unlike capacitance and fiber-optic detectors, pneumatic detectors are immune to water, brush, small animals, and other such objects. Only a heavy step will trigger the zone.
Pneumatic detectors are subject to the diets of certain rodents, so the tubes must be maintained with positive pressure so that detection occurs not only on pressure but on the absence of pressure (e.g., when a rodent chews through the tube). When this occurs, the location of the tear is impossible to determine without visual inspection all along the tube until it is located. This can be time-consuming.
If the location of the pneumatic detector is known, it can be exploited by going over the tube with a structure such as a ladder.
Monostatic and Bistatic Perimeter Microwave Detectors
These were described under Volumetric Detectors.
Perimeter Video Detectors
Video can be used as an alarm detector with the addition of either simple video motion detection or complex intelligent video algorithms.
Thermal Video Cameras
Thermal video cameras detect radiant heat rather than reflected visible light. Although they provide a video image like a normal video camera, the image in fact is that of the difference in heat being generated by a heat-radiating object (motor, human, dog, etc.) as compared to the ambient surrounding environment. The images of the environment comprise reflected radiant heat being radiated by the surrounding objects. Due to this, thermal video cameras can be used as detection devices wherever there is a difference in temperature between the detected object or person versus the surrounding environment.
Exploits for thermal video cameras include:
- Move only when the ambient temperature is at or near body temperature. If there is no difference between the body temperature and the ambient temperature, the thermal video camera will not “see” a difference. (This does not work well in actual practice because the flutter of small differences is generally enough to detect movement).
- Utilize a thermal insulating suit made out of a material such as a “space blanket” that effectively isolates the inside and outside temperatures. (Again, doesn’t work so well in practice).
Lidar
Lidar is a sensing technology that beams a laser onto an object and measures the distance of the reflected laser back to its source. The name Lidar is a combination of Light and Radar. A typical Lidar detector uses a fast-moving mirror to “scan” an area (typically definable from a few degrees horizontal all the way up to a 360-degree rotation). Advanced Lidar systems can actually provide a video image of the environment scanned by the Lidar unit. Integral software can detect motion in the area scanned by comparing the reflection time from the ambient environment to that of the moving object. Advanced software can display the ambient environment as an image and highlight the moving object.
Lidar works in any light condition down to absolute zero ambient light because it is its own (typically infrared) light source. Lidar also works well over relatively long distances (some units work up to a distance of several miles). This can make Lidar an economical alternative to costly perimeter detection systems. Lidar is x-ray invisible, so it is not picked up by radar or x-ray detectors. It may, however, be detected by infrared detectors.
There is effectively no practical exploit for Lidar. Even a very slow-moving sniper crawling as slowly as he can cannot beat a well-designed Lidar unit.
Ground and Short-Range Radar
Radar detects movement from the echo of a moving object against its ambient environment. Radar uses radio frequencies to create the echo signature. Short-range and ground radar can be used to protect open terrain such as a harbor or open terrain at the border of a country or large facility. Ground radar is useful for protecting high-security facilities such as research or operations facilities. Wherever an expanse of open unoccupied terrain can be established, ground and short-range radar can be used. Similar to Lidar, radar software can provide an image of movement overlaid onto a video image of the environment, highlighting the moving object (vehicle, boat, human, or animal).
Sonar
Sonar detects movement from the echo of a moving object against its ambient environment. Sonar uses audio frequencies in a water-filled environment to create the echo signature. Sonar can be used in port environments to detect underwater threats near vessels. Like Lidar and radar, sonar creates a detection image showing range and vector (distance, depth and angle).
Miscellaneous Detectors
Most designers believe that the alarm inputs on security systems are binary inputs, sensing open and closed positions. In fact, most alarm inputs are measuring current flow across a constant voltage. Typically, the acceptable range is 4–20 mA. Anything less than 4 mA or greater than 20 mA is an indicator that the alarm loop is in a trouble condition, or that it has been subject to tampering. By using end-of-line resistors, in series with and across the alarm dry-contact switch, an open or closed condition of the switch can be accurately measured because it results in precise 4- or 20-mA conditions on the loop.
A few systems can also use their alarm inputs to measure a current gradient, allowing analog measurements such as temperature and water level.
Other common miscellaneous detectors include water level detectors, humidity detectors, and temperature detectors.
Summary
Alarm detection technologies include point detectors, volumetric detectors, and line detectors. Point detectors include magnetic door switches and duress switches. Volumetric detectors include passive and active infrared, microwave, ultrasonic, and acoustic detectors. Dual-technology detectors reduce nuisance alarms.
Video systems can also serve as volumetric detectors and as either a security alarm system or a forensic analytic system.
Perimeter detection systems include leaky coax detectors, capacitance detectors, seismic detectors, fiber-optic dc ommon-mode detectors, pneumatic weight detectors, perimeter video detectors, thermal video cameras, Lidar, and ground and short-range radar.
Miscellaneous detectors include 4- to 20-mA current loop detectors and temperature, humidity, and water level detectors.
Questions and Answers
1. Which of those listed below are not basic types of detection systems?
b. Volumetric detectors
c. Line detectors
d. Expansion chamber detectors
2. Which of those below are not types of point detectors?
b. Pull-and-plunger switches
c. Electronic line alarms
d. Footswitches
3. Which of the below are valid ways to confirm a duress switch activation?
b. Ring-back
c. Visual indicator
d. All of the above
4. Which below are not types of volumetric detectors?
b. Microwave detectors
c. Acoustic detectors
d. All above are volumetric detectors
5. Which below is not a form of video detector?
b. Triangulation detectors
c. Video motion detection
d. Facial recognition system
6. Which below is not a form of perimeter detector?
b. Capacitance detectors
c. Seismic detectors
d. Fiber-myopic detectors
7. Common-mode detectors are similar in physical installation to:
b. Capacitance detectors
c. Seismic detectors
d. Fiber-optic detectors
8. Pneumatic weight detectors are a variation on the old ________________, which was common years ago.
a. Hair-trigger switch detectors
b. Pneumatic tube cash transfer systems
c. Pneumatic control systems
d. Gas station driveway alert
9. Thermal video cameras detect:
a. Infrared light instead of radiant heat
b. Radiant heat instead of infrared light
c. Radiant heat instead of reflected visible light
d. Visible light and other physical phenomena
10. Lidar is a sensing technology that:
a. Uses radar as its primary detection medium
b. Beams a laser onto an object and measures the distance of the reflected laser back to its source
c. Beams a laser onto an object and measures its lateral but not spherical movement
d. Uses ground and short range radar as the basis for its measurements
Answers: 1: d, 2: c, 3: d, 4: d, 5: a, 6: d, 7: d, 8: d, 9: c, 10: b
