Cybersecurity for Commercial Advantage
J.M. Kaplan, McKinsey and Company, New York, NY, United States
Abstract
Many elements of the work required for a business’s offerings are viewed as noncommercial, such as cybersecurity. They are regarded by business management as simply an additional cost that cannot be passed onto customer and that therefore are not recoverable. Many of these elements, and in particular cybersecurity, differ in a critical way from the other concerns that business has. Uneven adoption, including adoption by current or potential business partners, can be a cause of delay in achieving cross-business agreements and can make it much more difficult and costly to achieve and follow your own business’s policies regarding those concerns.
In this chapter we will discuss cybersecurity for business in this regard and describe how its policies and implementation can be turned into a commercial advantage.
Keywords
Cybersecurity; business; customers; Chief Information and Chief Information Security Officer; policies; investment
Most senior management teams and board of directors are starting to understand how damaging cyberattacks can be to their business. On-line fraud and crime can cost a company tens or hundreds of millions of dollars. Loss of sensitive personal information upsets customers, and in some cases, can depress revenues and create massive legal and regulatory exposure. Exfiltration of intellectual property can diminish the value of billions of dollars’ worth of investment in research and development. Theft of sensitive business plans can upend critical pricing or negotiation strategies. And, given that most companies cannot operate without access to core systems, destructive attacks can threaten the viability of the business itself.
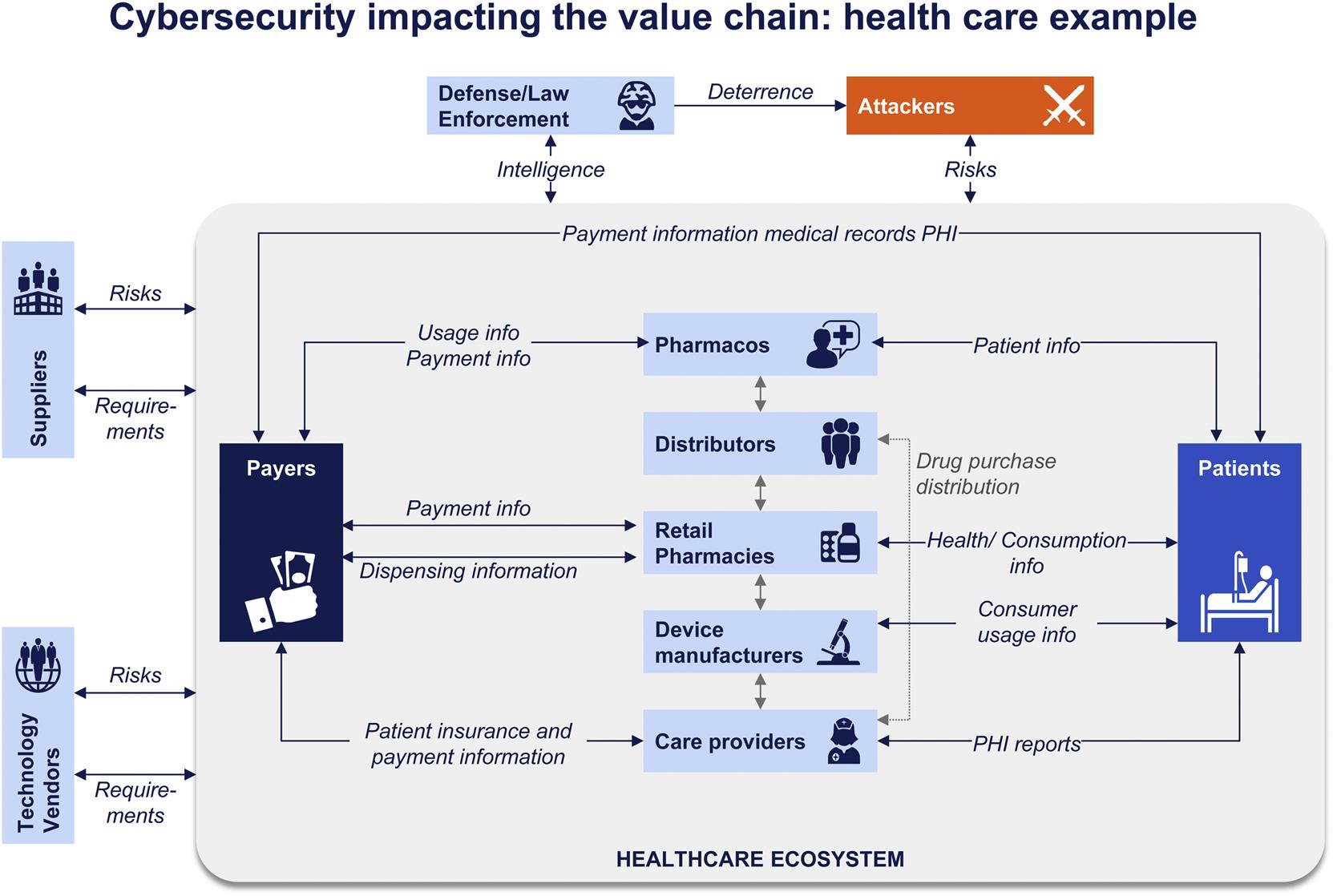
No company is an island in dealing with these risks. Companies share sensitive data like production plans and product specifications with their vendors, and they accept sensitive data from their customers. Everyone understands that banks have sensitive personal financial data and hospital networks have sensitive patient medical records, but almost every type of company receives sensitive data from its customers. IT service provides have critical details about their customers’ networks and technology environments. Commercial insurance carriers collect sensitive data about manufacturing facilities to perform underwriting. Many types of manufacturers receive sensitive product or operational information from their customers.
Moreover, in an increasingly digital world, companies are interconnecting their technology environments with suppliers and customers to create business processes that collect, analyze, and act on massive amounts of data in real time. Already medical device and industrial equipment manufacturers install products that maintain real-time connections to aggregate performance and maintenance information.1
Given this, cybersecurity concerns are starting to reshape value chains, sometimes for better, sometimes for worse. As companies exchange sensitive data and interconnect their technology environments, cybersecurity necessarily becomes a commercial and contractual issue—companies are making cybersecurity capabilities an important criterion in sourcing decisions and conducting complex negotiations over the contractual terms and conditions mandating how their data will be handled. In some cases, this has been an enormously positive development. Commercial pressure can be a more compelling, and more surgically precise, incentive for improved cybersecurity capabilities than any regulatory mandate.
However, given that most companies still treat cybersecurity as a “backoffice” or “control” functional, they have not yet been able to integrate cybersecurity into their commercial interactions either with suppliers or with customers. As a result, cybersecurity is already creating a significant turbulence in the value chain, slowing down collaboration between companies and, potentially, reducing competitiveness and innovation in some markets.
Companies need to place an explicitly commercial lens on cybersecurity, coolly assessing business risks and incorporating these risks’ implications deeply into procurement, product development, sales, service, and procurement processes. The companies that do this most aggressively will not only reduce their risk but also increase their operating efficiency and improve their value proposition with customers.
6.1 Turbulence Along the Value Chain
It would slightly unfair to say that nobody cared about cybersecurity a decade ago, but only by a little bit. Outside of a few sectors like aerospace and defense, even Chief Information Officers (CIOs) devoted little time and attention to protecting information assets from attackers. Not only did many organizations not have Chief Information Security Officers (CISOs), but for them “IT security” meant the tech support staff who ran the antivirus or remote access environment. Basic protections for the network perimeter might be in place, but, insecure application architectures and infrastructure configurations were pervasive—and consequences for flouting security policies all but nonexistent. Threats and risks that followed legitimate entry across the network perimeter or asynchronous attacks were all but ignored. Needless to say, senior business managers considered security to be a “back office” function—requiring far less of their time than other IT issues.2
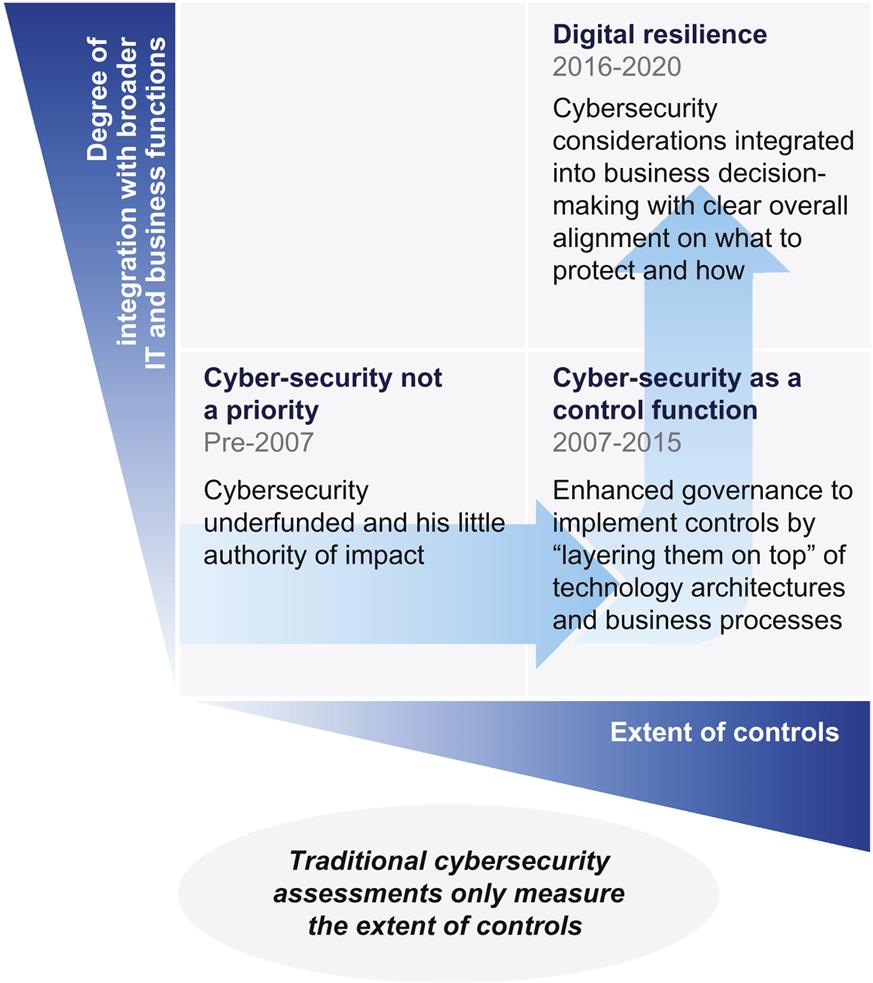
Over time, increasingly aggressive cyberattackers forced companies to revise their model. They vastly expanded the extent of controls, even if they failed to integrate security considerations more deeply into business processes and technology environments. Companies hired CISOs and enhanced the governance and oversight authority for the cybersecurity team. At their CISOs’ direction, they disseminated policies, locked down end-user environments, and put in security architecture reviews for new applications. All this was necessary—without these steps there would have been many more breaches on the front pages of major newspapers. However these steps most often involved the security team saying “No” to certain initiatives and layering sometimes clunky and end-user-experience-detrimental security elements on top of new and existing applications. This has slowed innovation, reduced end-user productivity, and reduced resources available for business projects. It has also created turbulence in commercial interactions by slowing contracting processes, reducing vendor leverage, and attenuating customer experiences.
6.1.1 Slower Contracting Processes
Businesses entrust their vendors with tremendous amounts of sensitive data that could be extremely valuable to attackers, for example
• Employee data to payroll processes and other HR providers
• Customer data to ad agencies and marketing analytics companies
• Financial data to accountancies and investment banks
• Technology configuration information outsourced to service providers
• Product specifications and release dates to engineering or manufacturing partners
Some of the sensitive data may not be immediately obvious. Who thinks about the sensitive data concerned with facilities, for example, that companies provide to insurance carriers as part of the underwriting process. Large companies will often maintain relationships with thousands of vendors who have access to sensitive corporate data in one way or another.
Companies have responded with mechanisms they believe will reduce their exposure to vendor risks. They require new suppliers to fill out surveys with hundreds of questions, participate in architectural reviews, and submit to site visits. They also demand very specific terms and conditions for how data will be protected.
While necessary, all of this is not only resource and time consuming, but it also slows down the contracting processes both because of the time required to evaluate vendors and because of the time required for suppliers and customers to agree on such terms. For example, when we convened a group of entrepreneurial software companies’ CEOs to talk about security, they told us that their sales cycle had doubled in length over the past 2 years because they first had to sell to the CIO or business owner and then conduct an equally involved process with the CISO. In some cases commitments of unlimited liability for the impact of data breaches they had made to get critical, early sales were complicating funding transactions—as venture capitalist or private equity firms discovered unlimited liability commitments in their due diligence processes. Likewise, executives at application services firms told us that commitments about liability for data breaches were often one of the “long poles in the tent” in coming to terms in for an outsourcing deal.
These types of impacts are not limited to the technology sector. In some cases investment banking transactions can get held up by data security concerns. One bank saw a large derivatives transaction held up for months because nobody fully understand all the parties who would receive the personal information associated with servicing the underlying mortgages and how that data would be protected. Sometimes customer demands about data protection conflict with regulatory mandates, creating further churn and delay. In negotiations, one bank demanded that its potential provider of mortgage insurance purge underlying customer data after 90 days. However, some (but not all) states required mortgage insurance providers to retain underlying personal data for the life of the mortgage.
6.1.2 Reducing Vendor Leverage and Reshaping Markets
In addition, mechanisms that companies have put in place to manage vendor risks can reduce vendor leverage and reshape markets.
In most companies, CISOs and security teams have succeeded in convincing procurement organizations that contracting processes have to take security requirements into account. However relatively simplistic and siloed interaction models between security and procurement teams can reduce vendor leverage and, may, over time reshape markets in ways the reduce competitiveness and slow the pace of innovation.
How does this happen? In drafting a request for proposal, the procurement organization will look to the security organization for “requirements” to be included in the document, just as they ask for requirements from the “business owner,” who will use the product or service and other functional stakeholders, like the legal and compliance organizations. In this type of model, it is very easy for the CISO to throw all sorts of requirements “over the wall” to procurement for inclusion into an RFP based on a theoretical perspective on “best practices” (e.g., data can never be shared with subcontractors under any circumstances), without a practical discussion between security and procurement about what requirements really matter given the service in question, what vendors are likely to be able to do and how to make tradeoffs between requirements and ultimate cost impacts.
As a result, RFPs can get loaded up with noncritical security requirements that eliminate some vendors, reducing negotiating leverage, and bring others to increase their estimates of what it would cost to fulfill the contract. One large company saw 9 of 11 potential bidders disqualified for security reasons, dramatically attenuating its negotiating position and causing the ultimate contract to cost tens of millions of dollars more than expected.
However the impacts of security on procurement processes could become far more pernicious over time. Large companies can better bear the cost of security requirements because they can amortize them over a broader set of customers. They can invest in dedicated teams to respond to extensive security questionnaires. Incumbent vendors have an advantage in that they have already demonstrated their security capabilities to a company already.
As a company considers a new type software that it wants to implement quickly, say it can choose between an offering from one of its incumbent vendors and a relatively new attacker. Given the desire for speed, there could well be an organizational inclination to say “We have got to do this quickly. We understand the incumbent vendor’s security model. It will take us a couple of months to get this startup to answer the hundreds of questions our security assessment requirements. Let us just go with the company we know.” That is a perfectly rational decision, but over time, hundreds of perfectly rational decisions like that can harden markets, making it more difficult for new and innovative companies to gain traction.
6.1.3 Attenuating Customer Experiences
One capital markets CIO we know is fond of saying “In the past, for our customers, the API to our company was a phone call. In the future, the API for us will be an API.” As companies seek to become digital businesses, more and more of their interactions with customers will take place on-line, either via a web portal, a mobile app or machine-to-machine communications. This on-line interaction includes everything from a consumer checking her bank balance to a jet engine “phoning home” so it can transmit usage and performance data to facilitate proactive maintenance.
However, any on-line process depends on authentication (validating that the user is who he, or it, claims to be) and authorization (checking that the user has the rights to access the data or undertake the transaction requested). Unfortunately, in the face of ever more sophisticated attackers the authentication model built up over the first two decades of the on-line economy is increasingly less tenable. Most companies realize that simple, static passwords that customers share across many sites provide little protection against sophisticated attackers—is utterly meaningless in a world where the “user” may be an automobile, a thermostat, a refrigerator, a jet engine, or a medical device.
Unfortunately, organizational silos between the marketing, product development, customer care, application development, and security functions often result in frustrating customer experiences as companies seek to better protect their customer interactions. As with procurement, the security team can load up a consumer-facing process with a list of “requirements,” resulting in more complicated password rules, confusing interfaces, repeated requests for credentials and bewildering “challenge questions.” Take just the last of these. Even if a customer remembers what he said was his favorite course when he opened the account, would he remember whether he entered the course name, the course number, or both together. This causes many customers to say, “This is too hard. Let me just dial the call center,” slowing the adoption of digital processes and loading many companies with excess costs.
The same dynamic applies in business-to-business markets. CISOs at hospital networks will often express frustration at how medical device manufacturers address device security. They say that device manufacturers have not fully acknowledged that hospitals are highly sophisticated and integrated technology environments in their own right. As a result, the security model for many medical devices assumes that they will be deployed atomistically, rather than as part of a hospital network, making both authentication to the hospital network and connection to the manufacturers’ network more complicated. As a result, many hospital network CISOs say that they often have to delay the introduction of connected medical devices by a year or more while they determine how to implement them securely.
6.2 Resilience for Commercial Advantage
If managing cybersecurity as a control function results in slower contracting processes, reduced vendor leverage, and more friction with customers, what can companies do to put in place a cybersecurity model that protects sensitive information while minimizing negative commercial impacts for their interactions with suppliers and customers? How can they turn protection of business information from a source of frustration to a source of commercial advantage?
The experience of the US auto manufacturers with quality management may provide something of an example and a direction. In the 1970s auto manufacturers tried to ensure quality by “inspecting it in.” They examined shipments they received from vendors for flaws, and they placed quality inspectors at the end of production lines to check if, for example, the suspension had been appropriately attached to the chassis. This proved to be phenomenally ineffective and expensive. Even the most diligent inspector missed many problems, meaning that the average car had at least one production defect. Defects inspectors did find were equally problematic: they resulted in lots full of cars behind factories waiting for remediation—and tying up expensive working capital.
Eventually the auto manufacturers realized that to meet customer expectations about quality and cost, they would have to build quality into their business model. They started connecting plant managers with product engineers in order to design cars that were easier to manufacturer well. They started very interactive dialogs with their suppliers about how to collaborate in order to reduce defects. They started to redesign front-line activities so that it was difficult to attach a suspension to the chassis incorrectly. And they created a culture of quality throughout the organization, so that any worker was able to stop the line if he or she saw a problem.
Companies need to do the same thing in protecting their sensitive data. They need to move from layering security on top to achieving resilience by building security into their business model. In McKinsey’s joint research with the World Economic Forum, we identified 7 levers for achieving Digital Resilience.
1. Prioritize information assets and related risks in a way that helps engage business leaders
2. Enlist front-line personnel—helping them understand value of information assets
3. Integrate cyberresilience into enterprise-wide management and governance processes
4. Integrated incident response across business functions, enhanced by realistic testing
5. Develop deep integration of security into the technology environment to drive scalability
6. Provide differentiated protection for most important assets
7. Deploy active defenses to be proactive in uncovering attacks early3
Interviews with executives at more than 100 institutions made it clear that collectively these levers would result in a step change improvement in companies’ ability to protect critical information. More recently, our Digital Resilience assessment has made it clear that most companies are not progressing quickly enough in adopting these levers—the average company scores two points out of four in terms of overall maturity.
All of these levers are helpful for using cybersecurity for commercial advantage, but one more so than all of the others—integrate cyberresilience into enterprise-wide management and governance processes. This means conducting discussions across organizational silos to integrate considerations related to protecting information deeply, but also flexibly, into business processes like product development, marketing, sales, customer care, operations and procurement.
There are three places the companies can start to focus in doing this: in managing relationships with consumers, in managing relationships with enterprise customers, and in managing relations with suppliers.
6.2.1 Managing Relationships With Consumers
Most cybersecurity professionals believe that it is hard to communicate effectively with consumers about protecting information because any publically available advertising that speaks to a company’s security capabilities immediately makes it a target for hackers looking to make name for themselves. There has also been a historic belief, among some executives, that consumers have not been particularly worried about protecting their information—that they are cheap and cheerful in this regard.
That said, there are still some very important actions that companies can take to make sure that they provide compelling experiences while also fulfilling their responsibilities to protect customer data.
6.2.1.1 Discover Consumer Preferences
Most companies have little information about how sensitive customers are to risks of information loss or disclosure. However there is at least anecdotal evidence that different customer segments have very different attitudes toward disclosure of information—for example, in financial services, mass affluent customers seem to be far more sensitized to the issue than customers in some other segments. Different types of customers also have very different perspectives on what constitutes an inconvenient security control. Getting real data from market surveys and focus groups enables organizations to understand what customers value and what frustrates them and incorporate those insights into customer-facing processes.
6.2.1.2 Apply Design Thinking to Security-Related Processes
Traditionally, many on-line experiences have been confusing and clunky, with complicated interfaces, vague instructions, requests for superfluous information and frustrating delays between what feels like an endless succession of screens. Increasingly, companies are using the discipline of “design thinking”—which truly requires business managers to take the view of what customers value in creating an experience—to many of their on-line processes. This should be no less true for security-related processes like authentication. In fact, one financial institution applied design thinking to their consumer authentication process. This allowed them to create a much smoother and less time-consuming customer experience. For example, customers told them they were much more concerned about fraud than the risk that someone might see their balance, so the bank delayed additional levels of authentication until the customer started to conduct transactions.
6.2.1.3 Allow Users to Customize Their Own Experiences
Once companies start to gather data on the impact of security controls, they find wide variations in what customers find to be inconvenient. One customer might have no objection to a complex passwords, but balk at changing it once a quarter. Another might prefer a simpler password, but find no inconvenience in entering a PIN texted to him on his phone every time he wants to log in. Several financial institutions are examining deploying portals that allow customers to pick from a menu of authentication-related controls—so long as they, in aggregate, combine to provide a sufficient level of protection. Over time, that minimum level of protection may vary by customer as well—with customers using products that are more “in the cross-hairs” for cybercriminals required to selected controls that provider a higher level of protections.
6.2.2 Managing Relationships With Enterprise Customers
Protection of critical data and cybersecurity considerations are an increasingly important part of relationships between companies and their enterprise customers. While marketing departments cannot create ad campaigns touting their cybersecurity capabilities, client discussions and RFP responses hit very directly on cybersecurity capabilities in industries as diverse as business process outsourcing, enterprise software, wholesale financial services, contract manufacturing, medicals devices, group health insurance, and pharmacy benefits management. As a result, there are a number of actions companies must be taking to improve their collaboration with enterprise customers in protecting critical information.
6.2.2.1 Treat the CISO and Team as Part of the Sales Channel
When security matters a lot, responses to a questionnaire only help so much. Customers feel more comfortable when they can spend time with the CISO and team to gauge their level of competence, test ideas, and problem solving on how to address thorny security issues that may exist at the seams between the two organizations. Some CISOs say they spend as much as 30% of their time with customers.
Others are not so effective in working with their sales teams and may spend almost no time with customers. Sometimes this is the result of CISO feeling that she just lacks the managerial bandwidth given other pressing responsibilities. Sometimes sales teams fail to recognize the importance of the issue. Sometimes there is an absence of trust between the sales and security functions, so account executives hesitate to pick up the phone and invite the CISO to a meeting. In any event, these are missed opportunities—in the absence of real dialog, questions about security get channeled into surveys and questionnaires that can bog down contracting processes.
6.2.2.2 Invest in Capabilities to Facilitate Vendor Security Assessments
For the foreseeable future, enterprise customers will require their suppliers to undergo vendor security assessments. They are painful, and they are inefficient, but until sectors can start to sort out standards for warranting the protection of information, they are also necessary. However, companies can make choices and investments that will dramatically improve their ability to address these assessments effectively. Instead of treating each assessment as a one-off, they can start to analyze them for patterns in order to build the most important customer requirements into their security programs. They can create databases of information typically required for customer assessments, minimizing the grunt work of collecting data. And they can create a center of excellence to consolidate all activity required to respond to customer requests in one place.
6.2.2.3 Build Tight Connections Between Product Security and Cybersecurity
Not too long ago, product security and cybersecurity (or IT security or information security) were very distinct disciplines, with limited interaction in many companies. Specialists in engineering tried to make sure microcode in medical devices or other sophisticated equipment would not be compromised, and information security managers protected data on the company’s internal systems.
Then the lines between products and enterprise networks started to blur. Customers integrated products into their own enterprise networks. Products started connecting to their manufacturers’ enterprise networks to transmit diagnostic information—in effect they became endpoints on those networks. Customers started using applications running in manufacturers’ data centers to configure products running in their facilities.
All of this creates new types of vectors for cyberattackers and makes it critical to take a holistic view across product security and IT security. Some companies have done this by unifying the responsibilities under one executive; others by cross-staffing teams and creating governance structures.
6.2.3 Managing Relationships With Suppliers
Just as companies must integrate cybersecurity considerations into their relationships with customers, when they are on the other side of the commercial transaction, they must integrate cybersecurity considerations into their relationships with suppliers.
6.2.3.1 Bring Together Vendor Security and Vendor Rationalization Programs
The only vendor that does not create cybersecurity risks is the vendor you do not do business with. Now, that does not mean that companies should jettison vendors who have a compelling proposition just because the security team thinks that there are too many vendors.
However, some companies have thousands of duplicative and subscale vendors who handle sensitive information. Yes, it is probably impossible to ascertain whether many vendors are treating sensitive data appropriately—a sourcing pattern like that may well represent an economically suboptimal vendor portfolio. In those cases, there is an opportunity for the CISO and the Chief Procurement Officer to join forces and make that case that vendor rationalization—while politically challenging—would have twin benefits of an improved cost structured and an enhanced security posture.
6.2.3.2 Improve Collaboration Between Security and Procurement
As notedearlier, security teams can easily load impractical requirements into procurement transactions. Avoiding this requires a very collaborative relationship between the security and the procurement teams. It starts with the CISO and team being willing to spend the time to educate procurement managers in each category about security implications associated with, for example, analytic services, accountancy, traditional IT outsourcing, or software-as-a-service. It continues with the security and procurement teams’ problem solving on how to tier vendor relationships and types of procurement—so that both teams can focus their efforts on the highest risk relationships and transactions.
6.2.3.3 Examining Shared Standards and Utilities for Vendor Assessment
As many have noted, as necessary as they are, there is an element of insanity to vendor security assessments. A software or services vendor will spend weeks filling out an assessment survey and then, for its next sale, will receive another assessment survey that covers all the same topics—but just differently enough to require a wholly separate and substantial effort to complete.
From an enterprise customer’s point of view they have to complete an assessment even they know an industry peer—with much the same risk posture—may have spent weeks looking at the same vendor very recently.
As a result, coalitions of companies—defined by sector or sometimes geography—are started to band together around common assessments. For example, a group of leading healthcare companies is launching a cybersecurity utility that will include a shared assessment capability. Members will be able to see vendor responses to a common set of questions and make an independent decision about comfort with that vendor based on a common, robust fact bases. As a result, they can repurpose scarce cybersecurity talent to higher value activities and introduce new products and services without waiting weeks or months for the completion of a custom questionnaire.
6.2.3.4 Establish Operational Linkages With Vendor Security Teams
For many types of commercial interactions, managing vendor risk does not stop with the vendor assessment or the signed contract. New types of information are share. New technology connections get provisioned. Adherence to agreed procedures for sharing data has to be managed—on both side of the transaction. Therefore maintaining day-to-day linkages with vendor’s cybersecurity personnel becomes critical. It starts with having current contact information, but goes far beyond that. Some organizations conduct periodic checkpoints with key vendors to assess how they are jointly managing a deal against commitments and expectations. As few even incorporate vendor personnel in cybersecurity war games, they use to enhance their ability to respond to cyberattacks.
Given the amount of sensitive information shared in conducting business with customers and suppliers, cybersecurity is arguably a commercial issue. Already it is impacting contracting timelines, altering customer experience, and affecting which vendors win and lose business. When companies treat cybersecurity as a back office function that governs and places controls on the flow of information, and that creates commercial disadvantage, both in terms of reduced ability to leverage vendors and less intimate relationships with customers.
However, by building enhancing collaboration between the security team and the rest of the organization and building cybersecurity deeply into business processes, companies can source in a way that is secure and efficient and create customer relationships that both protect critical data and provide compelling experiences.