Symmetric Algorithms
Symmetric algorithms were explained earlier in this chapter. In this section, we discuss some of the most popular symmetric algorithms. Some of these might no longer be commonly used because there are more secure alternatives.
Security professionals should be familiar with the following symmetric algorithms:
![]() DES/3DES
DES/3DES
![]() AES
AES
![]() IDEA
IDEA
![]() Skipjack
Skipjack
![]() Blowfish
Blowfish
![]() Twofish
Twofish
![]() RC4/RC5/RC6
RC4/RC5/RC6
![]() CAST
CAST
Digital Encryption Standard (DES) and Triple DES (3DES)
Digital Encryption Standard (DES) is a symmetric encryption system created by the National Security Agency (NSA) but based on the 128-bit Lucifer algorithm by IBM. Originally, the algorithm was named Data Encryption Algorithm (DEA), and the DES acronym was used to refer to the standard. But in today’s world, DES is the more common term for both.
Note
Test candidates might see both acronyms used on the CISSP exam.
DES uses a 64-bit key, 8 bits of which are used for parity. Therefore, the effective key length for DES is 56 bits. DES divides the message into 64-bit blocks. Sixteen rounds of transposition and substitution are performed on each block, resulting in a 64-bit block of ciphertext.
DES has mostly been replaced by 3DES and AES, both of which are discussed later in this chapter.
DES-X is a variant of DES that uses multiple 64-bit keys in addition to the 56-bit DES key. The first 64-bit key is XORed to the plaintext, which is then encrypted with DES. The second 64-bit key is XORed to the resulting cipher.
Double-DES, a DES version that used a 112-bit key length, is no longer used. After it was released, a security attack occurred that reduced Double-DES security to the same level as DES.
DES Modes
DES comes in the following five modes:

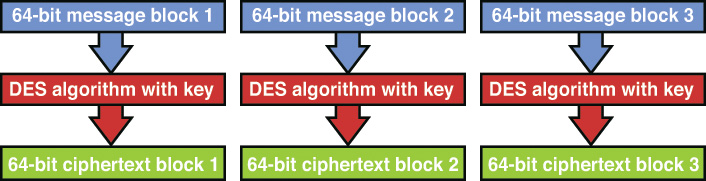
In ECB, 64-bit blocks of data are processed by the algorithm using the key. The ciphertext produced can be padded to ensure that the result is a 64-bit block. If an encryption error occurs, only one block of the message is affected. ECB operations run in parallel, making it a fast method.
Although ECB is the easiest and fastest mode to use, it has security issues because every 64-bit block is encrypted with the same key. If an attacker discovers the key, all the blocks of data can be read. If an attacker discovers both versions of the 64-bit block (plaintext and ciphertext), the key can be determined. For these reasons, the mode should not be used when encrypting a large amount of data because patterns would emerge.
ECB is a good choice if an organization needs encryption for its databases because ECB works well with the encryption of short messages. Figure 3-13 shows the ECB encryption process.
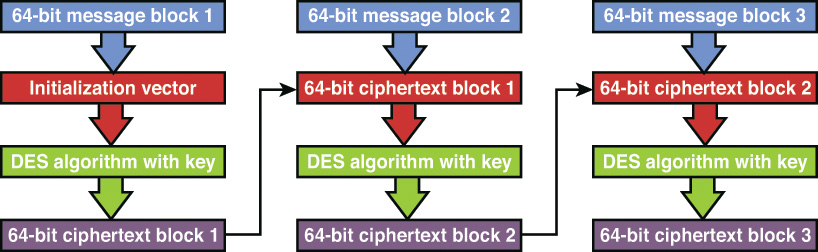
In CBC, each 64-bit block is chained together because each resultant 64-bit ciphertext block is applied to the next block. So plaintext message block 1 is processed by the algorithm using an IV (discussed earlier in this chapter). The resultant ciphertext message block 1 is XORed with plaintext message block 2, resulting in ciphertext message 2. This process continues until the message is complete.
Unlike ECB, CBC encrypts large files without having any patterns within the resulting ciphertext. If a unique IV is used with each message encryption, the resultant ciphertext will be different every time even in cases where the same plaintext message is used. Figure 3-14 shows the CBC encryption process.
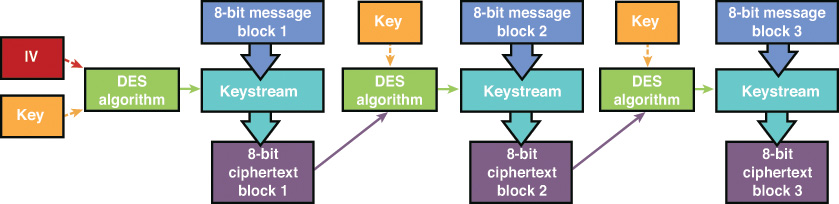
Whereas CBC and ECB require 64-bit blocks, CFB works with 8-bit (or smaller) blocks and uses a combination of stream ciphering and block ciphering. Like CBC, the first 8-bit block of the plaintext message is XORed by the algorithm using a keystream, which is the result of an IV and the key. The resultant ciphertext message is applied to the next plaintext message block. Figure 3-15 shows the CFB encryption process.
The size of the ciphertext block must be the same size as the plaintext block. The method that CFB uses can have issues if any ciphertext result has errors because those errors will affect any future block encryption. For this reason, CFB should not be used to encrypt data that can be affected by this problem, particularly video or voice signals. This problem led to the need for DES OFB mode.
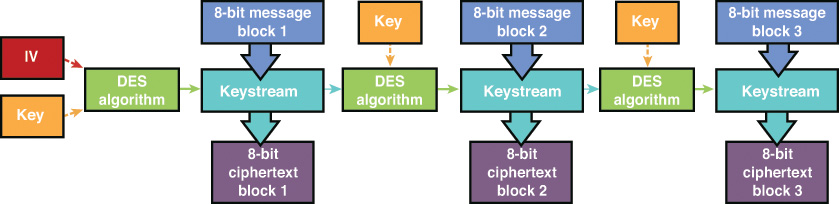
Similar to CFB, OFB works with 8-bit (or smaller) blocks and uses a combination of stream ciphering and block ciphering. However, OFB uses the previous keystream with the key to create the next keystream. Figure 3-16 shows the OFB encryption process.
With OFB, the size of the keystream value must be the same size as the plaintext block. Because of the way in which OFB is implemented, OFB is less susceptible to the error type that CFB has.
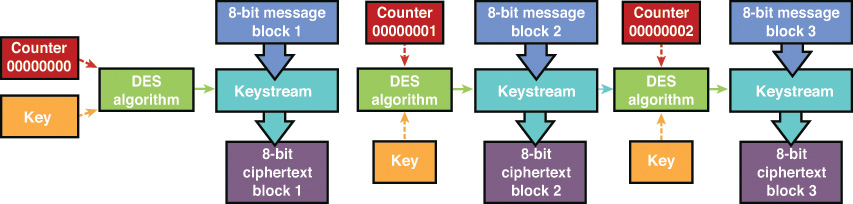
CTR mode is similar to OFB mode. The main difference is that CTR mode uses an incrementing IV counter to ensure that each block is encrypted with a unique keystream. Also, the ciphertext is not chaining into the encryption process. Because this chaining does not occur, CTR performance is much better than the other modes. Figure 3-17 shows the CTR encryption process.
Triple DES (3DES) and Modes
Because of the need to quickly replace DES, Triple DES (3DES), a version of DES that increases security by using three 56-bit keys, was developed. Although 3DES is resistant to attacks, it is up to three times slower than DES. 3DES did serve as a temporary replacement to DES. However, the NIST has actually designated the Advanced Encryption Standard (AES) as the replacement for DES, even though 3DES is still in use today.
3DES comes in the following four modes:

![]() 3DES-EEE3: Each block of data is encrypted three times, each time with a different key.
3DES-EEE3: Each block of data is encrypted three times, each time with a different key.
![]() 3DES-EDE3: Each block of data is encrypted with the first key, decrypted with the second key, and encrypted with the third key.
3DES-EDE3: Each block of data is encrypted with the first key, decrypted with the second key, and encrypted with the third key.
![]() 3DES-EEE2: Each block of data is encrypted with the first key, encrypted with the second key, and finally encrypted again with the first key.
3DES-EEE2: Each block of data is encrypted with the first key, encrypted with the second key, and finally encrypted again with the first key.
![]() 3DES-EDE2: Each block of data is encrypted with the first key, decrypted with the second key, and finally encrypted again with the first key.
3DES-EDE2: Each block of data is encrypted with the first key, decrypted with the second key, and finally encrypted again with the first key.
Advanced Encryption Standard (AES)
AES is the replacement algorithm for DES. When the NIST decided a new standard was needed because DES had been cracked, the NIST was presented with five industry options:
![]() IBM’s MARS
IBM’s MARS
![]() RSA Laboratories’ RC6
RSA Laboratories’ RC6
![]() Anderson, Biham, and Knudsen’s Serpent
Anderson, Biham, and Knudsen’s Serpent
![]() Counterpane Systems’ Twofish
Counterpane Systems’ Twofish
![]() Daemen and Rijmen’s Rijndael
Daemen and Rijmen’s Rijndael
Of these choices, the NIST selected Rijndael. So although AES is considered the standard, the algorithm that is used in the AES standard is the Rijndael algorithm. The AES and Rijndael terms are often used interchangeably.
The three block sizes that are used in the Rijndael algorithm are 128, 192, and 256 bits. A 128-bit key with a 128-bit block size undergoes 10 transformation rounds. A 192-bit key with a 192-bit block size undergoes 12 transformation rounds. Finally, a 256-bit key with a 256-bit block size undergoes 14 transformation rounds.
Rijndael employs transformations comprised of three layers: the non-linear layer, key addition layer, and linear-maxing layer. The Rijndael design is very simple, and its code is compact, which allows it to be used on a variety of platforms. It is the required algorithm for sensitive but unclassified U.S. government data.
IDEA
International Data Encryption Algorithm (IDEA) is a block cipher that uses 64-bit blocks. Each 64-bit block is divided into 16 smaller blocks. IDEA uses a 128-bit key and performs eight rounds of transformations on each of the 16 smaller blocks.
IDEA is faster and harder to break than DES. However, IDEA is not as widely used as DES or AES because it was patented, and licensing fees had to be paid to IDEA’s owner, a Swiss company named Ascom. However, the patent expired in 2012. IDEA is used in PGP, which is discussed later in this chapter.
Skipjack
Skipjack is a block-cipher, symmetric algorithm developed by the U.S. NSA. It uses an 80-bit key to encrypt 64-bit blocks. This is the algorithm that is used in the Clipper chip. Algorithm details are classified.
Blowfish
Blowfish is a block cipher that uses 64-bit data blocks using anywhere from 32- to 448-bit encryption keys. Blowfish performs 16 rounds of transformation. Initially developed with the intention of serving as a replacement to DES, Blowfish is one of the few algorithms that are not patented.
Twofish
Twofish is a version of Blowfish that uses 128-bit data blocks using 128-, 192-, and 256-bit keys. It uses 16 rounds of transformation. Like Blowfish, Twofish is not patented.
RC4/RC5/RC6
A total of six RC algorithms have been developed by Ron Rivest. RC1 was never published, RC2 was a 64-bit block cipher, and RC3 was broken before release. So the main RC implementations that a security professional needs to understand are RC4, RC5, and RC6.
RC4, also called ARC4, is one of the most popular stream ciphers. It is used in SSL and WEP (both of which are discussed in more detail in Chapter 4, “Communication and Network Security”). RC4 uses a variable key size of 40 to 2,048 bits and up to 256 rounds of transformation.
RC5 is a block cipher that uses a key size of up to 2,048 bits and up to 255 rounds of transformation. Block sizes supported are 32, 64, or 128 bits. Because of all the possible variables in RC5, the industry often uses an RC5=w/r/b designation, where w is the block size, r is the number of rounds, and b is the number of 8-bit bytes in the key. For example, RC5-64/16/16 denotes a 64-bit word (or 128-bit data blocks), 16 rounds of transformation, and a 16-byte (128-bit) key.
RC6 is a block cipher based on RC5, and it uses the same key size, rounds, and block size. RC6 was originally developed as an AES solution, but lost the contest to Rijndael. RC6 is faster than RC5.
CAST
CAST, invented by Carlisle Adams and Stafford Tavares, has two versions: CAST-128 and CAST-256. CAST-128 is a block cipher that uses a 40- to 128-bit key that will perform 12 or 16 rounds of transformation on 64-bit blocks. CAST-256 is a block cipher that uses a 128-, 160-, 192-, 224-, or 256-bit key that will perform 48 rounds of transformation on 128-bit blocks.
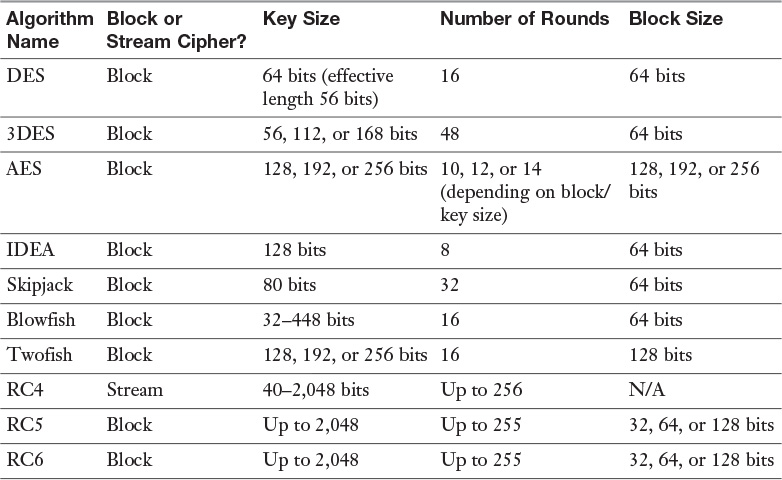
Table 3-6 lists the key facts about each symmetric algorithm.

Asymmetric Algorithms
Asymmetric algorithms were explained earlier in this chapter. In this section, we discuss some of the most popular asymmetric algorithms. Some of these might no longer be commonly used because there are more secure alternatives.
Security professionals should be familiar with the following symmetric algorithms:
![]() Diffie-Hellman
Diffie-Hellman
![]() RSA
RSA
![]() El Gamal
El Gamal
![]() ECC
ECC
![]() Knapsack
Knapsack
![]() Zero Knowledge Proof
Zero Knowledge Proof
Diffie-Hellman
Diffie-Hellman is an asymmetric key agreement algorithm created by Whitfield Diffie and Martin Hellman. Diffie-Hellman is responsible for the key agreement process. The key agreement process includes the following steps:
1. John and Sally need to communicate over an encrypted channel and decide to use Diffie-Hellman.
2. John generates a private and public key, and Sally generates a private and a public key.
3. John and Sally share their public keys with each other.
4. An application on John’s computer takes John’s private key and Sally’s public key and applies the Diffie-Hellman algorithm, and an application on Sally’s computer takes Sally’s private key and John’s public key and applies the Diffie-Hellman algorithm.
5. Through this application, the same shared value is created for John and Sally, which in turn creates the same symmetric key on each system using the asymmetric key agreement algorithm.
Through this process, Diffie-Hellman provides secure key distribution, but not confidentiality, authentication, or non-repudiation. The key to this algorithm is dealing with discrete logarithms. Diffie-Hellman is susceptible to man-in-the-middle attacks unless an organization implements digital signatures or digital certificates for authentication at the beginning of the Diffie-Hellman process.
Note
Man-in-the-middle attacks are discussed later in this chapter.
RSA
RSA is the most popular asymmetric algorithm and was invented by Ron Rivest, Adi Shamir, and Leonard Adleman. RSA can provide key exchange, encryption, and digital signatures. The strength of the RSA algorithm is the difficulty of finding the prime factors of very large numbers. RSA uses a 1,024- to 4,096-bit key and performs one round of transformation.
RSA-768 and RSA-704 have been factored. If factorization of the prime numbers used by an RSA implementation occurs, then the implementation is considered breakable and should not be used. RSA-2048 is the largest RSA number; a cash prize of US$200,000 is being offered for successful factorization. RSA-4096 is also available and has not been broken either.
As a key exchange protocol, RSA encrypts a DES or AES symmetric key for secure distribution. RSA uses a one-way function to provide encryption/decryption and digital signature verification/generation. The public key works with the one-way function to perform encryption and digital signature verification. The private key works with the one-way function to perform decryption and signature generation.
In RSA, the one-way function is a trapdoor. The private key knows the one-way function. The private key is capable of determining the original prime numbers. Finally, the private key knows how to use the one-way function to decrypt the encrypted message.
Attackers can use Number Field Sieve (NFS), a factoring algorithm, to attack RSA.
El Gamal
El Gamal is an asymmetric key algorithm based on the Diffie-Hellman algorithm. Like Diffie-Hellman, El Gamal deals with discrete logarithms. However, whereas Diffie-Hellman can only be used for key agreement, El Gamal can provide key exchange, encryption, and digital signatures.
With El Gamal, any key size can be used. However, a larger key size negatively affects performance. Because El Gamal is the slowest asymmetric algorithm, using a key size of 1,024 bit or less would be wise.
ECC
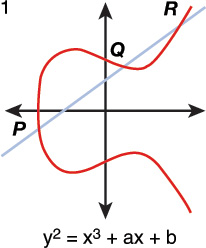
Elliptic Curve Cryptosystem (ECC) provides secure key distribution, encryption, and digital signatures. The elliptic curve’s size defines the difficulty of the problem.
Although ECC can use a key of any size, it can use a much smaller key than RSA or any other asymmetric algorithm and still provide comparable security. Therefore, the primary benefit promised by ECC is a smaller key size, reducing storage and transmission requirements. ECC is more efficient and provides better security than RSA keys of the same size.
Figure 3-18 shows an elliptic curve example with the elliptic curve equation.
Knapsack
Knapsack is a series of asymmetric algorithms that provide encryption and digital signatures. This algorithm family is no longer used due to security issues.
Zero Knowledge Proof
A Zero Knowledge Proof is a technique used to ensure that only the minimum need information is disclosed without giving all the details. An example of this technique occurs when one user encrypts data with his private key and the receiver decrypts with the originator’s public key. The originator has not given his private key to the receiver. But the originator is proving that he has his private key simply because the receiver can read the message.
Public Key Infrastructure
A public key infrastructure (PKI) includes systems, software, and communication protocols that distribute, manage, and control public key cryptography. A PKI publishes digital certificates. Because a PKI establishes trust within an environment, a PKI can certify that a public key is tied to an entity and verify that a public key is valid. Public keys are published through digital certificates.
The X.509 standard is a framework that enables authentication between networks and over the Internet. A PKI includes timestamping and certificate revocation to ensure that certificates are managed properly. A PKI provides confidentiality, message integrity, authentication, and non-repudiation.
The structure of a PKI includes CAs, certificates, registration authorities, certificate revocation lists, cross-certification, and the Online Certificate Status Protocol (OCSP). In this section, we discuss these PKI components as well as a few other PKI concepts.
Certification Authority (CA) and Registration Authority (RA)
Any participant that requests a certificate must first go through the registration authority (RA), which verifies the requestor’s identity and registers the requestor. After the identity is verified, the RA passes the request to the CA.
A certification authority (CA) is the entity that creates and signs digital certificates, maintains the certificates, and revokes them when necessary. Every entity that wants to participate in the PKI must contact the CA and request a digital certificate. It is the ultimate authority for the authenticity for every participant in the PKI by signing each digital certificate. The certificate binds the identity of the participant to the public key.
There are different types of CAs. Organizations exist who provide a PKI as a payable service to companies who need them. An example is Symantec. Some organizations implement their own private CAs so that the organization can control all aspects of the PKI process. If an organization is large enough, it might need to provide a structure of CAs with the root CA being the highest in the hierarchy.
Because more than one entity is often involved in the PKI certification process, certification path validation allows the participants to check the legitimacy of the certificates in the certification path.
OCSP
OCSP is an Internet protocol that obtains the revocation status of an X.509 digital certificate. OCSP is an alternative to the standard certificate revocation list (CRL) that is used by many PKIs. OCSP automatically validates the certificates and reports back the status of the digital certificate by accessing the CRL on the CA.
Certificates
A digital certificate provides an entity, usually a user, with the credentials to prove its identity and associates that identity with a public key. At minimum, a digital certification must provide the serial number, the issuer, the subject (owner), and the public key.
An X.509 certificate complies with the X.509 standard. An X.509 certificate contains the following fields:
![]() Version
Version
![]() Serial Number
Serial Number
![]() Algorithm ID
Algorithm ID
![]() Issuer
Issuer
![]() Validity
Validity
![]() Subject
Subject
![]() Subject Public Key Info
Subject Public Key Info
![]() Public Key Algorithm
Public Key Algorithm
![]() Subject Public Key
Subject Public Key
![]() Issuer Unique Identifier (optional)
Issuer Unique Identifier (optional)
![]() Subject Unique Identifier (optional)
Subject Unique Identifier (optional)
![]() Extensions (optional)
Extensions (optional)
Symantec first introduced the following digital certificate classes:
![]() Class 1: For individuals intended for email. These certificates get saved by web browsers.
Class 1: For individuals intended for email. These certificates get saved by web browsers.
![]() Class 2: For organizations that must provide proof of identity.
Class 2: For organizations that must provide proof of identity.
![]() Class 3: For servers and software signing in which independent verification and identity and authority checking is done by the issuing CA.
Class 3: For servers and software signing in which independent verification and identity and authority checking is done by the issuing CA.
Certificate Revocation List (CRL)
A CRL is a list of digital certificates that a CA has revoked. To find out whether a digital certificate has been revoked, the browser must either check the CRL or the CA must push out the CRL values to clients. This can become quite daunting when you consider that the CRL contains every certificate that has ever been revoked.
One concept to keep in mind is the revocation request grace period. This period is the maximum amount of time between when the revocation request is received by the CA and when the revocation actually occurs. A shorter revocation period provides better security but often results in a higher implementation cost.
PKI Steps

The steps involved in requesting a digital certificate are as follow:
1. A user requests a digital certificate, and the RA receives the request.
2. The RA requests identifying information from the requestor.
3. After the required information is received, the RA forwards the certificate request to the CA.
4. The CA creates a digital certificate for the requestor. The requestor’s public key and identity information are included as part of the certificate.
5. The user receives the certificate.
After the user has a certificate, he is ready to communicate with other trusted entities. The process for communication between entities is as follows:
1. User 1 requests User 2’s public key from the certificate repository.
2. The repository sends User 2’s digital certificate to User 1.
3. User 1 verifies the certificate and extracts User 2’s public key.
4. User 1 encrypts the session key with User 2’s public key and sends the encrypted session key and User 1’s certificate to User 2.
5. User 2 receives User 1’s certificate and verifies the certificate with a trusted CA.
After this certificate exchange and verification process occurs, the two entities are able to communicate using encryption.
Cross-Certification
Cross-certification establishes trust relationships between CAs so that the participating CAs can rely on the other participants’ digital certificates and public keys. It enables users to validate each other’s certificates when they are actually certified under different certification hierarchies. A CA for one organization can validate digital certificates from another organization’s CA when a cross-certification trust relationship exists.
Key Management Practices
A discussion of cryptography would be incomplete without coverage of key management practices. NIST SP 800-57 contains recommendations for key management in three parts:
![]() Part 1: This draft publication covers general recommendations for key management.
Part 1: This draft publication covers general recommendations for key management.
![]() Part 2: This publication covers the best practices for a key management organization.
Part 2: This publication covers the best practices for a key management organization.
![]() Part 3: This publication covers the application-specific key management guidance.
Part 3: This publication covers the application-specific key management guidance.
Security professionals should at least understand the key management principles in Part 1 of SP 800-57. If security professionals are involved in organizations that provide key management services to other organizations, understanding Part 2 is a necessity. Part 3 is needed when an organization implements applications that use keys. In this section, we cover the recommendations in Part 1.
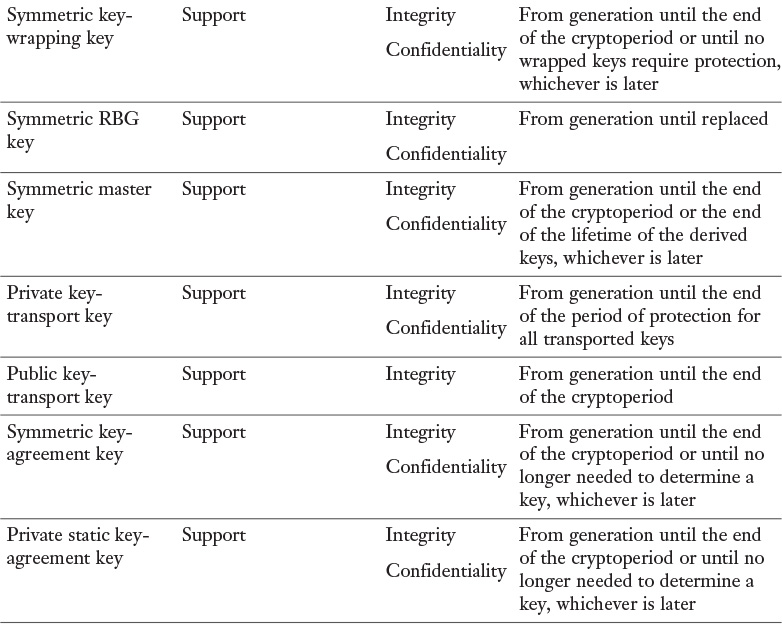
Several different types of keys are defined. The keys are identified according to their classification as public, private, or symmetric keys, as well as according to their use. For public and private key agreement keys, status as static or ephemeral keys is also specified:
![]() Private signature key: These are the private keys of asymmetric (public) key pairs that are used by public-key algorithms to generate digital signatures with possible long-term implications. When properly handled, private signature keys can be used to provide source authentication, provide integrity authentication, and support the non-repudiation of messages, documents, or stored data.
Private signature key: These are the private keys of asymmetric (public) key pairs that are used by public-key algorithms to generate digital signatures with possible long-term implications. When properly handled, private signature keys can be used to provide source authentication, provide integrity authentication, and support the non-repudiation of messages, documents, or stored data.
![]() Public signature-verification key: This is the public key of an asymmetric (public) key pair that is used by a public-key algorithm to verify digital signatures that are intended to provide source authentication, provide integrity authentication, and support the non-repudiation of messages, documents, or stored data.
Public signature-verification key: This is the public key of an asymmetric (public) key pair that is used by a public-key algorithm to verify digital signatures that are intended to provide source authentication, provide integrity authentication, and support the non-repudiation of messages, documents, or stored data.
![]() Symmetric authentication key: This key is used with symmetric-key algorithms to provide source authentication and assurance of the integrity of communication sessions, messages, documents, or stored data (i.e., integrity authentication).
Symmetric authentication key: This key is used with symmetric-key algorithms to provide source authentication and assurance of the integrity of communication sessions, messages, documents, or stored data (i.e., integrity authentication).
![]() Private authentication key: This is the private key of an asymmetric (public) key pair that is used with a public-key algorithm to provide assurance of the identity of an originating entity (i.e., the source) when establishing an authenticated communication session.
Private authentication key: This is the private key of an asymmetric (public) key pair that is used with a public-key algorithm to provide assurance of the identity of an originating entity (i.e., the source) when establishing an authenticated communication session.
![]() Public authentication key: This is the public key of an asymmetric (public) key pair that is used with a public-key algorithm to provide assurance of the identity of an originating entity (i.e., the source) when establishing an authenticated communication session.
Public authentication key: This is the public key of an asymmetric (public) key pair that is used with a public-key algorithm to provide assurance of the identity of an originating entity (i.e., the source) when establishing an authenticated communication session.
![]() Symmetric data-encryption key: This key is used with symmetric-key algorithms to apply confidentiality protection to information (i.e., to encrypt the information). The same key is also used to remove the confidentiality protection (i.e., to decrypt the information).
Symmetric data-encryption key: This key is used with symmetric-key algorithms to apply confidentiality protection to information (i.e., to encrypt the information). The same key is also used to remove the confidentiality protection (i.e., to decrypt the information).
![]() Symmetric key-wrapping key (also called key-encrypting keys): This key is used to encrypt other keys using symmetric-key algorithms. The key-wrapping key used to encrypt a key is also used to reverse the encryption operation (i.e., to decrypt the encrypted key). Depending on the algorithm with which the key is used, the key may also be used to provide integrity protection.
Symmetric key-wrapping key (also called key-encrypting keys): This key is used to encrypt other keys using symmetric-key algorithms. The key-wrapping key used to encrypt a key is also used to reverse the encryption operation (i.e., to decrypt the encrypted key). Depending on the algorithm with which the key is used, the key may also be used to provide integrity protection.
![]() Symmetric random number generation keys: This key is used to generate random numbers or random bits.
Symmetric random number generation keys: This key is used to generate random numbers or random bits.
![]() Symmetric master key: This key is used to derive other symmetric keys (e.g., data-encryption keys, key-wrapping keys, or source authentication keys) using symmetric cryptographic methods. The master key is also known as a key-derivation key.
Symmetric master key: This key is used to derive other symmetric keys (e.g., data-encryption keys, key-wrapping keys, or source authentication keys) using symmetric cryptographic methods. The master key is also known as a key-derivation key.
![]() Private key-transport key: These are the private keys of asymmetric (public) key pairs that are used to decrypt keys that have been encrypted with the corresponding public key using a public-key algorithm. Key-transport keys are usually used to establish keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors).
Private key-transport key: These are the private keys of asymmetric (public) key pairs that are used to decrypt keys that have been encrypted with the corresponding public key using a public-key algorithm. Key-transport keys are usually used to establish keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors).
![]() Public key-transport key: These are the public keys of asymmetric (public) key pairs that are used to encrypt keys using a public-key algorithm. These keys are used to establish keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors). The encrypted form of the established key might be stored for later decryption using the private key-transport key.
Public key-transport key: These are the public keys of asymmetric (public) key pairs that are used to encrypt keys using a public-key algorithm. These keys are used to establish keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors). The encrypted form of the established key might be stored for later decryption using the private key-transport key.
![]() Symmetric key-agreement key: This key is used to establish keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors), using a symmetric key-agreement algorithm.
Symmetric key-agreement key: This key is used to establish keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors), using a symmetric key-agreement algorithm.
![]() Private static key-agreement key: These are the long-term private keys of asymmetric (public) key pairs that are used to establish keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors).
Private static key-agreement key: These are the long-term private keys of asymmetric (public) key pairs that are used to establish keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors).
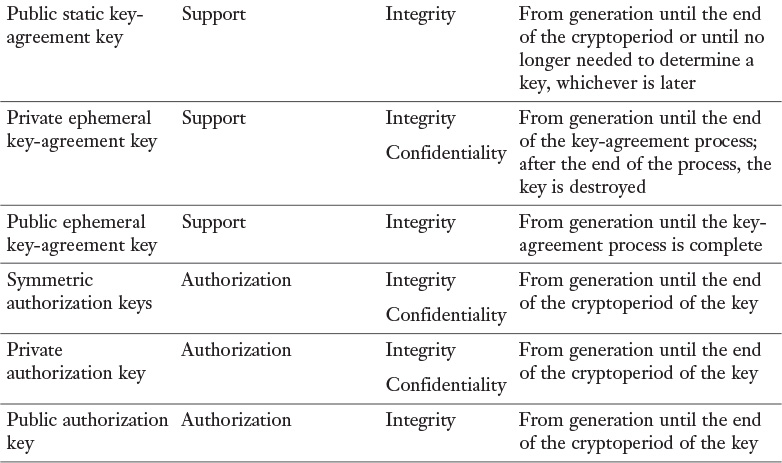
![]() Public static key-agreement key: These are the long-term public keys of asymmetric (public) key pairs that are used to establish keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors).
Public static key-agreement key: These are the long-term public keys of asymmetric (public) key pairs that are used to establish keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors).
![]() Private ephemeral key-agreement key: These are the short-term private keys of asymmetric (public) key pairs that are used only once to establish one or more keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors).
Private ephemeral key-agreement key: These are the short-term private keys of asymmetric (public) key pairs that are used only once to establish one or more keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors).
![]() Public ephemeral key-agreement key: These are the short-term public keys of asymmetric key pairs that are used in a single-key establishment transaction to establish one or more keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors).
Public ephemeral key-agreement key: These are the short-term public keys of asymmetric key pairs that are used in a single-key establishment transaction to establish one or more keys (e.g., key-wrapping keys, data-encryption keys, or MAC keys) and, optionally, other keying material (e.g., initialization vectors).
![]() Symmetric authorization key: This type of key is used to provide privileges to an entity using a symmetric cryptographic method. The authorization key is known by the entity responsible for monitoring and granting access privileges for authorized entities and by the entity seeking access to resources.
Symmetric authorization key: This type of key is used to provide privileges to an entity using a symmetric cryptographic method. The authorization key is known by the entity responsible for monitoring and granting access privileges for authorized entities and by the entity seeking access to resources.
![]() Private authorization key: This is the private key of an asymmetric (public) key pair that is used to provide privileges to an entity.
Private authorization key: This is the private key of an asymmetric (public) key pair that is used to provide privileges to an entity.
![]() Public authorization key: This is the public key of an asymmetric (public) key pair that is used to verify privileges for an entity that knows the associated private authorization key.
Public authorization key: This is the public key of an asymmetric (public) key pair that is used to verify privileges for an entity that knows the associated private authorization key.
In general, a single key is be used for only one purpose (e.g., encryption, integrity, authentication, key wrapping, random bit generation, or digital signatures). A cryptoperiod is the time span during which a specific key is authorized for use by legitimate entities, or the time that the keys for a given system will remain in effect. Among the factors affecting the length of a cryptoperiod are:
![]() The cryptographic strength (e.g., the algorithm, key length, block size, and mode of operation)
The cryptographic strength (e.g., the algorithm, key length, block size, and mode of operation)
![]() The embodiment of the mechanisms (e.g., a [FIPS140] Level 4 implementation or a software implementation on a personal computer)
The embodiment of the mechanisms (e.g., a [FIPS140] Level 4 implementation or a software implementation on a personal computer)
![]() The operating environment (e.g., a secure limited-access facility, open office environment, or publicly accessible terminal)
The operating environment (e.g., a secure limited-access facility, open office environment, or publicly accessible terminal)
![]() The volume of information flow or the number of transactions
The volume of information flow or the number of transactions
![]() The security life of the data
The security life of the data
![]() The security function (e.g., data encryption, digital signature, key derivation, or key protection)
The security function (e.g., data encryption, digital signature, key derivation, or key protection)
![]() The re-keying method (e.g., keyboard entry, re-keying using a key loading device where humans have no direct access to key information, or remote re-keying within a PKI)
The re-keying method (e.g., keyboard entry, re-keying using a key loading device where humans have no direct access to key information, or remote re-keying within a PKI)
![]() The key update or key-derivation process
The key update or key-derivation process
![]() The number of nodes in a network that share a common key
The number of nodes in a network that share a common key
![]() The number of copies of a key and the distribution of those copies
The number of copies of a key and the distribution of those copies
![]() Personnel turnover (e.g., CA system personnel)
Personnel turnover (e.g., CA system personnel)
![]() The threat to the information from adversaries (e.g., from whom the information is protected and their perceived technical capabilities and financial resources to mount an attack)
The threat to the information from adversaries (e.g., from whom the information is protected and their perceived technical capabilities and financial resources to mount an attack)
![]() The threat to the information from new and disruptive technologies (e.g., quantum computers)
The threat to the information from new and disruptive technologies (e.g., quantum computers)
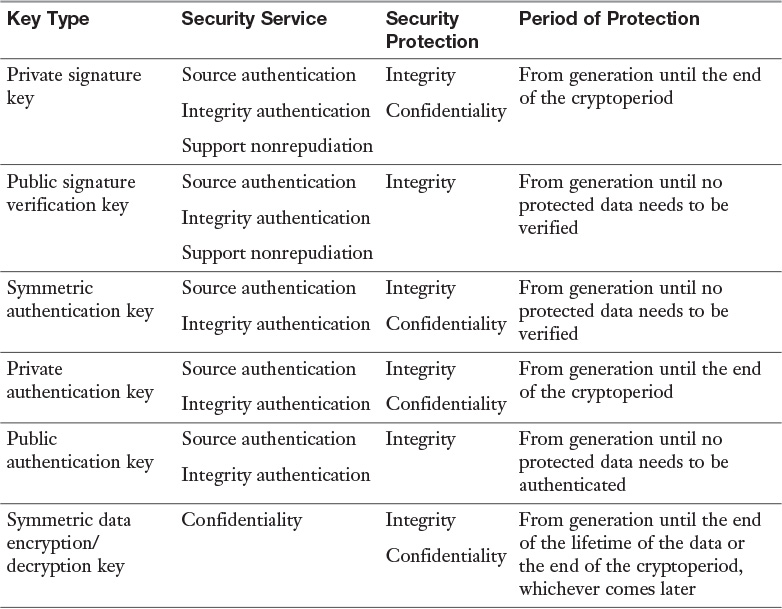
The protection requirements for cryptographic keys are shown in Table 3-7. The Security Service column lists the security service provided by the key. The Security Protection column lists the type of protection required for the key.
A key is used differently, depending on its state in the key’s life cycle. Key states are defined from a system point of view, as opposed to the point of view of a single cryptographic module. The states that an operational or backed-up key may assume are as follows:
![]() Pre-activation state: The key has been generated but has not been authorized for use. In this state, the key may only be used to perform proof-of-possession or key confirmation.
Pre-activation state: The key has been generated but has not been authorized for use. In this state, the key may only be used to perform proof-of-possession or key confirmation.
![]() Active state: The key may be used to cryptographically protect information (e.g., encrypt plaintext or generate a digital signature), to cryptographically process previously protected information (e.g., decrypt ciphertext or verify a digital signature), or both. When a key is active, it may be designated for protection only, processing only, or both protection and processing, depending on its type.
Active state: The key may be used to cryptographically protect information (e.g., encrypt plaintext or generate a digital signature), to cryptographically process previously protected information (e.g., decrypt ciphertext or verify a digital signature), or both. When a key is active, it may be designated for protection only, processing only, or both protection and processing, depending on its type.
![]() Suspended state: The use of a key or key pair may be suspended for several possible reasons; in the case of asymmetric key pairs, both the public and private keys are suspended at the same time. One reason for a suspension might be a possible key compromise, and the suspension has been issued to allow time to investigate the situation. Another reason might be that the entity that owns a digital signature key pair is not available (e.g., is on an extended leave of absence); signatures purportedly signed during the suspension time would be invalid. A suspended key or key pair may be restored to an active state at a later time or may be deactivated or destroyed, or may transition to the compromised state.
Suspended state: The use of a key or key pair may be suspended for several possible reasons; in the case of asymmetric key pairs, both the public and private keys are suspended at the same time. One reason for a suspension might be a possible key compromise, and the suspension has been issued to allow time to investigate the situation. Another reason might be that the entity that owns a digital signature key pair is not available (e.g., is on an extended leave of absence); signatures purportedly signed during the suspension time would be invalid. A suspended key or key pair may be restored to an active state at a later time or may be deactivated or destroyed, or may transition to the compromised state.
![]() Deactivated state: Keys in the deactivated state are not used to apply cryptographic protection, but in some cases, they may be used to process cryptographically protected information. If a key has been revoked (for reasons other than a compromise), then the key may continue to be used for processing. Note that keys retrieved from an archive can be considered to be in the deactivated state unless they are compromised.
Deactivated state: Keys in the deactivated state are not used to apply cryptographic protection, but in some cases, they may be used to process cryptographically protected information. If a key has been revoked (for reasons other than a compromise), then the key may continue to be used for processing. Note that keys retrieved from an archive can be considered to be in the deactivated state unless they are compromised.
![]() Compromised state: Generally, keys are compromised when they are released to or determined by an unauthorized entity. A compromised key shall not be used to apply cryptographic protection to information. However, in some cases, a compromised key or a public key that corresponds to a compromised private key of a key pair may be used to process cryptographically protected information. For example, a signature may be verified to determine the integrity of signed data if its signature has been physically protected since a time before the compromise occurred. This processing shall be done only under very highly controlled conditions, where the users of the information are fully aware of the possible consequences.
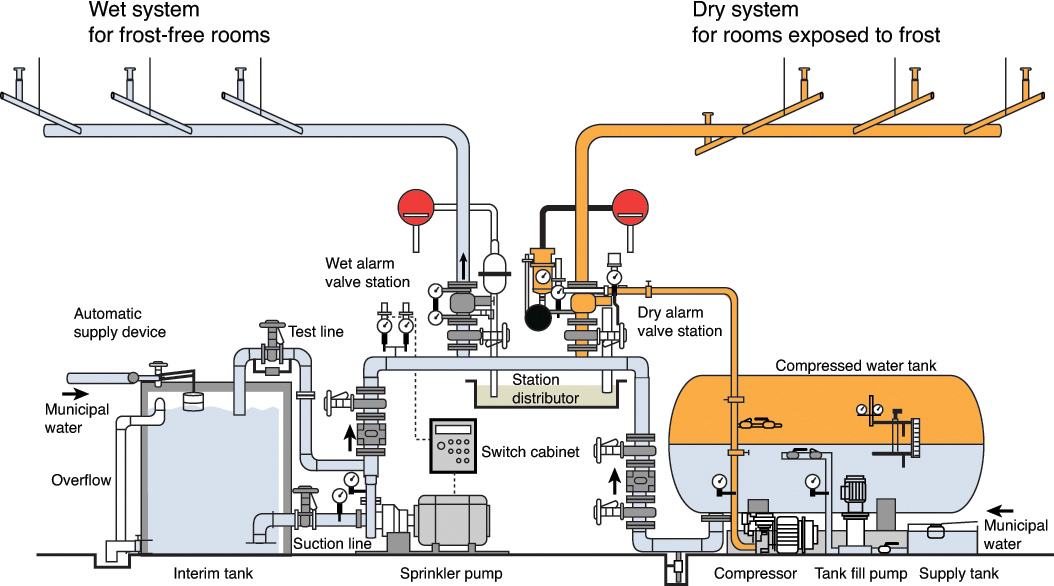
Compromised state: Generally, keys are compromised when they are released to or determined by an unauthorized entity. A compromised key shall not be used to apply cryptographic protection to information. However, in some cases, a compromised key or a public key that corresponds to a compromised private key of a key pair may be used to process cryptographically protected information. For example, a signature may be verified to determine the integrity of signed data if its signature has been physically protected since a time before the compromise occurred. This processing shall be done only under very highly controlled conditions, where the users of the information are fully aware of the possible consequences.
![]() Destroyed state: The key has been destroyed as specified in the destroyed phase, discussed shortly. Even though the key no longer exists when in this state, certain key metadata (e.g., key state transition history, key name, type, cryptoperiod) may be retained.
Destroyed state: The key has been destroyed as specified in the destroyed phase, discussed shortly. Even though the key no longer exists when in this state, certain key metadata (e.g., key state transition history, key name, type, cryptoperiod) may be retained.
The cryptographic key management life cycle can be divided into the following four phases:
1. Pre-operational phase: The keying material is not yet available for normal cryptographic operations. Keys may not yet be generated or are in the pre-activation state. System or enterprise attributes are established during this phase, as well. During this phase, the following functions occur:
a. User registration
b. System initialization
c. User initialization
d. Keying-material installation
e. Key establishment
f. Key registration
2. Operational phase: The keying material is available and in normal use. Keys are in the active, suspended, or deactivated state. Keys in the active state may be designated as protect only, process only, or protect and process; keys in the suspended or deactivated state can be used for processing only. During this phase, the following functions occur:
a. Normal operational storage
b. Continuity of operations
c. Key change
d. Key derivation
3. Post-operational phase: The keying material is no longer in normal use, but access to the keying material is possible, and the keying material may be used for processing only in certain circumstances. Keys are in the deactivated or compromised states. Keys in the post-operational phase may be in an archive when not processing data. During this phase the following functions occur:
a. Archive storage and key recovery
b. Entity de-registration
c. Key de-registration
d. Key destruction
e. Key revocation
4. Destroyed phase: Keys are no longer available. Records of their existence may or may not have been deleted. Keys are in the destroyed states. Although the keys themselves are destroyed, the key metadata (e.g., key name, type, cryptoperiod, usage period) may be retained.
Systems that process valuable information require controls in order to protect the information from unauthorized disclosure and modification. Cryptographic systems that contain keys and other cryptographic information are especially critical. Security professionals should work to ensure that the protection of keying material provides accountability, audit, and survivability.
Accountability involves the identification of entities that have access to, or control of, cryptographic keys throughout their life cycles. Accountability can be an effective tool to help prevent key compromises and to reduce the impact of compromises when they are detected. Although it is preferred that no humans be able to view keys, as a minimum, the key management system should account for all individuals who are able to view plaintext cryptographic keys. In addition, more sophisticated key management systems may account for all individuals authorized to access or control any cryptographic keys, whether in plaintext or ciphertext form.
Two types of audits should be performed on key management systems:
![]() Security: The security plan and the procedures that are developed to support the plan should be periodically audited to ensure that they continue to support the key management policy.
Security: The security plan and the procedures that are developed to support the plan should be periodically audited to ensure that they continue to support the key management policy.
![]() Protective: The protective mechanisms employed should be periodically reassessed with respect to the level of security they currently provide and are expected to provide in the future. They should also be assessed to determine whether the mechanisms correctly and effectively support the appropriate policies. New technology developments and attacks should be considered as part of a protective audit.
Protective: The protective mechanisms employed should be periodically reassessed with respect to the level of security they currently provide and are expected to provide in the future. They should also be assessed to determine whether the mechanisms correctly and effectively support the appropriate policies. New technology developments and attacks should be considered as part of a protective audit.
Key management survivability entails backing up or archiving copies of all keys used. Key backup and recovery procedures must be established to ensure that keys are not lost. System redundancy and contingency planning should also be properly assessed to ensure that all the systems involved in key management are fault tolerant.
Digital Signatures
A digital signature is a hash value encrypted with the sender’s private key. A digital signature provides authentication, non-repudiation, and integrity. A blind signature is a form of digital signature where the contents of the message are masked before it is signed.
Public key cryptography, which is discussed in the next section, is used to create digital signatures. Users register their public keys with a CA, which distributes a certificate containing the user’s public key and the CA’s digital signature. The digital signature is computed by the user’s public key and validity period being combined with the certificate issuer and digital signature algorithm identifier.
The Digital Signature Standard (DSS) is a federal digital security standard that governs the Digital Security Algorithm (DSA). DSA generates a message digest of 160 bits. The U.S. federal government requires the use of DSA, RSA (discussed earlier in this chapter), or Elliptic Curve DSA (ECDSA) and SHA for digital signatures. DSA is slower than RSA and only provides digital signatures. RSA provides digital signatures, encryption, and secure symmetric key distribution.
When considering cryptography, keep the following facts in mind:
![]() Encryption provides confidentiality.
Encryption provides confidentiality.
![]() Hashing provides integrity.
Hashing provides integrity.
![]() Digital signatures provide authentication, non-repudiation, and integrity.
Digital signatures provide authentication, non-repudiation, and integrity.
Digital Rights Management (DRM)
Digital rights management (DRM) is covered in Chapter 1. For security engineering, security professionals must ensure that organizations employ DRM policies and procedures to protect intellectual property, including music, films, ebooks, and software. Today’s DRM implementations include the following:
![]() Directories:
Directories:
![]() Lightweight Directory Access Protocol (LDAP)
Lightweight Directory Access Protocol (LDAP)
![]() Active Directory (AD)
Active Directory (AD)
![]() Custom
Custom
![]() Permissions:
Permissions:
![]() Open
Open
![]() Print
Print
![]() Modify
Modify
![]() Clipboard
Clipboard
![]() Additional controls:
Additional controls:
![]() Expiration (absolute, relative, immediate revocation)
Expiration (absolute, relative, immediate revocation)
![]() Version control
Version control
![]() Change policy on existing documents
Change policy on existing documents
![]() Watermarking
Watermarking
![]() Online/offline
Online/offline
![]() Auditing
Auditing
![]() Ad hoc and structured processes:
Ad hoc and structured processes:
![]() User initiated on desktop
User initiated on desktop
![]() Mapped to system
Mapped to system
![]() Built into workflow process
Built into workflow process
Message Integrity
Integrity is one of the three basic tenets of security. Message integrity ensures that a message has not been altered by using parity bits, cyclic redundancy checks (CRCs), or checksums.
The parity bit method adds an extra bit to the data. This parity bit simply indicates if the number of 1 bits is odd or even. The parity bit is 1 if the number of 1 bits is odd, and the parity bit is 0 if the number of 1 bits is even. The parity bit is set before the data is transmitted. When the data arrives, the parity bit is checked against the other data. If the parity bit doesn’t match the data sent, then an error is sent to the originator.
The CRC method uses polynomial division to determine the CRC value for a file. The CRC value is usually 16- or 32-bits long. Because CRC is very accurate, the CRC value will not match up if a single bit is incorrect.
The checksum method adds up the bytes of data being sent and then transmits that number to be checked later using the same method. The source adds up the values of the bytes and sends the data and its checksum. The receiving end receives the information, adds up the bytes in the same way the source did, and gets the checksum. The receiver then compares his checksum with the source’s checksum. If the values match, message integrity is intact. If the values do not match, the data should be resent or replaced. Checksums are also referred to as hash sums because they typically use hash functions for the computation.
Message integrity is provided by hash functions and message authentication code.
Hashing
Hash functions were explained earlier in this chapter. In this section, we discuss some of the most popular hash functions. Some of these might no longer be commonly used because more secure alternatives are available.
Security professionals should be familiar with the following hash functions:
![]() One-way hash
One-way hash
![]() MD2/MD4/MD5/MD6
MD2/MD4/MD5/MD6
![]() SHA/SHA-2/SHA-3
SHA/SHA-2/SHA-3
![]() HAVAL
HAVAL
![]() Tiger
Tiger
One-Way Hash
A hash function takes a message of variable length and produces a fixed-length hash value. Hash values, also referred to as message digests, are calculated using the original message. If the receiver calculates a hash value that is the same, then the original message is intact. If the receiver calculates a hash value that is different, then the original message has been altered.
Using a given function H, the following equation must be true to ensure that the original message, M1, has not been altered or replaced with a new message, M2:
H(M1) < > H(M2)
For a one-way hash to be effective, creating two different messages with the same hash value must be mathematically impossible. Given a hash value, discovering the original message from which the hash value was obtained must be mathematically impossible. A one-way hash algorithm is collision free if it provides protection against creating the same hash value from different messages.
Unlike symmetric and asymmetric algorithms, the hashing algorithm is publicly known. Hash functions are always performed in one direction. Using it in reverse is unnecessary.
However, one-way hash functions do have limitations. If an attacker intercepts a message that contains a hash value, the attacker can alter the original message to create a second invalid message with a new hash value. If the attacker then sends the second invalid message to the intended recipient, the intended recipient will have no way of knowing that he received an incorrect message. When the receiver performs a hash value calculation, the invalid message will look valid because the invalid message was appended with the attacker’s new hash value, not the original message’s hash value. To prevent this from occurring, the sender should use message authentication code (MAC).
Encrypting the hash function with a symmetric key algorithm generates a keyed MAC. The symmetric key does not encrypt the original message. It is used only to protect the hash value.
Note
The basic types of MAC are discussed later in this chapter.
The basic steps of a hash function are shown in Figure 3-19.
MD2/MD4/MD5/MD6
The MD2 message digest algorithm produces a 128-bit hash value. It performs 18 rounds of computations. Although MD2 is still in use today, it is much slower than MD4, MD5, and MD6.
The MD4 algorithm also produces a 128-bit hash value. However, it performs only three rounds of computations. Although MD4 is faster than MD2, its use has significantly declined because attacks against it have been so successful.
Like the other MD algorithms, the MD5 algorithm produces a 128-bit hash value. It performs four rounds of computations. It was originally created because of the issues with MD4, and it is more complex than MD4. However, MD5 is not collision free. For this reason, it should not be used for SSL certificates or digital signatures. The U.S. government requires the usage of SHA-2 instead of MD5. However, in commercial usage, many software vendors publish the MD5 hash value when they release software patches so customers can verify the software’s integrity after download.
The MD6 algorithm produces a variable hash value, performing a variable number of computations. Although it was originally introduced as a candidate for SHA-3, it was withdrawn because of early issues the algorithm had with differential attacks. MD6 has since been re-released with this issue fixed. However, that release was too late to be accepted as the NIST SHA-3 standard.
SHA/SHA-2/SHA-3
Secure Hash Algorithm (SHA) is a family of four algorithms published by the U.S. NIST. SHA-0, originally referred to as simply SHA because there were no other “family members,” produces a 160-bit hash value after performing 80 rounds of computations on 512-bit blocks. SHA-0 was never very popular because collisions were discovered.
Like SHA-0, SHA-1 produces a 160-bit hash value after performing 80 rounds of computations on 512-bit blocks. SHA-1 corrected the flaw in SHA-0 that made it susceptible to attacks.
SHA-2 is actually a family of hash functions, each of which provides different functional limits. The SHA-2 family is as follows:
![]() SHA-224: Produces a 224-bit hash value after performing 64 rounds of computations on 512-bit blocks.
SHA-224: Produces a 224-bit hash value after performing 64 rounds of computations on 512-bit blocks.
![]() SHA-256: Produces a 256-bit hash value after performing 64 rounds of computations on 512-bit blocks.
SHA-256: Produces a 256-bit hash value after performing 64 rounds of computations on 512-bit blocks.
![]() SHA-384: Produces a 384-bit hash value after performing 80 rounds of computations on 1,024-bit blocks.
SHA-384: Produces a 384-bit hash value after performing 80 rounds of computations on 1,024-bit blocks.
![]() SHA-512: Produces a 512-bit hash value after performing 80 rounds of computations on 1,024-bit blocks.
SHA-512: Produces a 512-bit hash value after performing 80 rounds of computations on 1,024-bit blocks.
![]() SHA-512/224: Produces a 224-bit hash value after performing 80 rounds of computations on 1,024-bit blocks. The 512 designation here indicates the internal state size.
SHA-512/224: Produces a 224-bit hash value after performing 80 rounds of computations on 1,024-bit blocks. The 512 designation here indicates the internal state size.
![]() SHA-512/256: Produces a 256-bit hash value after performing 80 rounds of computations on 1,024-bit blocks. Once again, the 512 designation indicates the internal state size.
SHA-512/256: Produces a 256-bit hash value after performing 80 rounds of computations on 1,024-bit blocks. Once again, the 512 designation indicates the internal state size.
SHA-3, like SHA-2, will be a family of hash functions. SHA-2 has not yet been broken. The hash value sizes for SHA-3 range from 224 to 512 bits. The block sizes range from 576-1,152. SHA-3 performs 120 rounds of computations, by default.
Keep in mind that SHA-1 and SHA-2 are still widely used today. SHA-3 was not developed because of some security flaw with the two previous standards but was instead proposed as an alternative hash function to the others.
HAVAL
HAVAL is a one-way function that produces variable-length hash values, including 128 bits, 160 bits, 192 bits, 224 bits, and 256 bits, and uses 1,024-bit blocks. The number of rounds of computations can be 3, 4, or 5. Collision issues have been discovered if producing a 128-bit hash value with three rounds of computations. All other variations do not have any discovered issues as of this printing.
RIPEMD-160
Although several variations of the RIPEMD hash function exist, security professionals should only worry about RIPEMD-160 for exam purposes. RIPEMD-160 produces a 160-bit hash value after performing 160 rounds of computations on 512-bit blocks.
Tiger
Tiger is a hash function that produces 128-, 160-, or 192-bit hash values after performing 24 rounds of computations on 512-bit blocks, with the most popular version being the one that produces 192-bit hash values. Unlike MD5, RIPEMD, SHA-0, and SHA-1, Tiger is not built on the MD4 architecture.
Message Authentication Code
MAC was explained earlier in this chapter. In this section, we discuss the three types of MACs with which security professionals should be familiar:
![]() HMAC
HMAC
![]() CMAC
CMAC
HMAC
A hash MAC (HMAC) is a keyed-hash MAC that involves a hash function with symmetric key. HMAC provides data integrity and authentication. Any of the previously listed hash functions can be used with HMAC, with the HMAC name being appended with the hash function name, as in HMAC-SHA-1. The strength of HMAC is dependent upon the strength of the hash function, including the hash value size, and the key size.
HMAC’s hash value output size will be the same as the underlying hash function. HMAC can help to reduce the collision rate of the hash function.

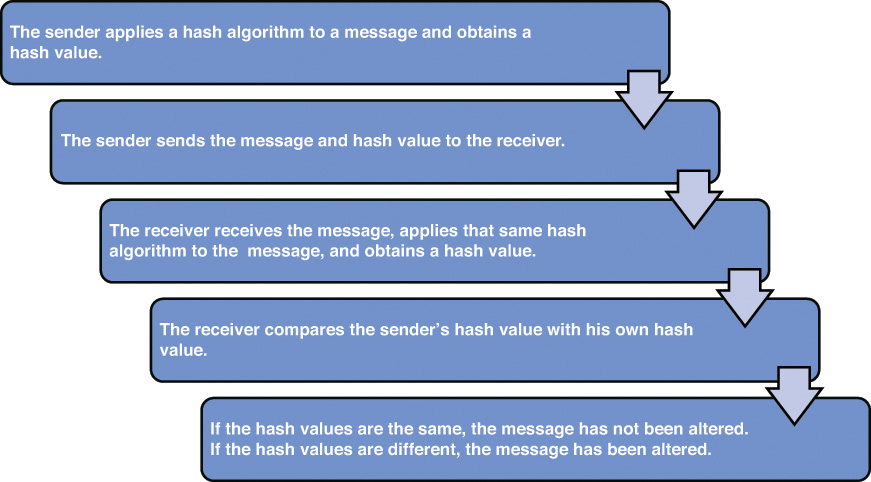
The basic steps of an HMAC process are as follows:
1. The sender and receiver agree on which symmetric key to use.
2. The sender joins the symmetric key to the message.
3. The sender applies a hash algorithm to the message and obtains a hash value.
4. The sender adds a hash value to the original message, and the sender sends the new message to the receiver.
5. The receiver receives the message and joins the symmetric key to the message.
6. The receiver applies the hash algorithm to the message and obtains a hash value.
7. If the hash values are the same, the message has not been altered. If the hash values are different, the message has been altered.
CBC-MAC
Cipher Block Chaining MAC (CBC-MAC) is a block-cipher MAC that operates in CBC mode. CBC-MAC provides data integrity and authentication.

The basic steps of a CBC-MAC process are as follows:
1. The sender and receiver agree on which symmetric block cipher to use.
2. The sender encrypts the message with the symmetric block cipher in CBC mode. The last block is the MAC.
3. The sender adds the MAC to the original message, and the sender sends the new message to the receiver.
4. The receiver receives the message and encrypts the message with the symmetric block cipher in CBC mode.
5. The receiver obtains the MAC and compares it to the sender’s MAC.
6. If the values are the same, the message has not been altered. If the values are different, the message has been altered.
CMAC
Cipher-Based MAC (CMAC) operates in the same manner as CBC-MAC but with much better mathematical functions. CMAC addresses some security issues with CBC-MAC and is approved to work with AES and 3DES.
Salting
Lookup tables and rainbow tables work because each password is hashed exactly the same way. If two users have the same password, their password is the same. To prevent attack, security professionals should ensure that each hash is randomized. Then, when the same password is hashed twice, the hashes are not the same.
Salting means randomly adding data to a one-way function that “hashes” a password or passphrase. The primary function of salting is to defend against dictionary attacks versus a list of password hashes and against precomputed rainbow table attacks.
A security professional should randomize the hashes by appending or prepending a random string, called a salt, to the password before hashing. To check if a password is correct, the attacker needs the salt. The salt is usually stored in the user account database, along with the hash, or as part of the hash string itself.
An attacker does not know in advance what the salt will be, so she cannot precompute a lookup table or rainbow table. If each user’s password is hashed with a different salt, a reverse lookup table attack doesn’t work either.
If salts are used, security professionals must ensure that they are not reused and not too short. A new random salt must be generated each time an administrator creates a user account or a user changes his or her password. A good rule of thumb is to use a salt that is the same size as the output of the hash function. For example, the output of SHA-256 is 256 bits (32 bytes), so the salt should be at least 32 random bytes.
Salts should be generated using a cryptographically secure pseudo-random number generator (CSPRNG). As the name suggests, a CSPRNG is designed to provide a high level of randomness and is completely unpredictable.
Cryptanalytic Attacks
Cryptography attacks are categorized as either passive or active attacks. A passive attack is usually implemented just to discover information and is much harder to detect because it is usually carried out by eavesdropping or packet sniffing. Active attacks involve an attacker actually carrying out steps, like message alteration or file modification. Cryptography is usually attacked via the key, algorithm, execution, data, or people. But most of these attacks are attempting to discover the key used.
Cryptography attacks that are discussed include the following:
![]() Social engineering
Social engineering
![]() Brute force
Brute force
![]() Differential cryptanalysis
Differential cryptanalysis
![]() Linear cryptanalysis
Linear cryptanalysis
![]() Frequency analysis
Frequency analysis
![]() Birthday attack
Birthday attack
![]() Dictionary attack
Dictionary attack
![]() Replay attack
Replay attack
![]() Analytic attack
Analytic attack
![]() Statistical attack
Statistical attack
![]() Factoring attack
Factoring attack
![]() Reverse engineering
Reverse engineering
![]() Meet-in-the-middle attack
Meet-in-the-middle attack
Ciphertext-Only Attack
In a ciphertext-only attack, an attacker uses several encrypted messages (ciphertext) to figure out the key used in the encryption process. Although it is a very common type of attack, it is usually not successful because so little is known about the encryption used.
Known Plaintext Attack
In a known plaintext attack, an attacker uses the plaintext and ciphertext versions of a message to discover the key used. This type of attack implements reverse engineering, frequency analysis, or brute force to determine the key so that all messages can be deciphered.
Chosen Plaintext Attack
In a chosen plaintext attack, an attacker chooses the plaintext to get encrypted to obtain the ciphertext. The attacker sends a message hoping that the user will forward that message as ciphertext to another user. The attacker captures the ciphertext version of the message and tries to determine the key by comparing the plaintext version he originated with the captured ciphertext version. Once again, key discovery is the goal of this attack.
Chosen Ciphertext Attack
A chosen ciphertext attack is the opposite of a chosen plaintext attack. In a chosen ciphertext attack, an attacker chooses the ciphertext to be decrypted to obtain the plaintext. This attack is more difficult because control of the system that implements the algorithm is needed.
Social Engineering
Social engineering attacks against cryptographic algorithms do not differ greatly from social engineering attacks against any other security area. Attackers attempt to trick users into giving the attacker the cryptographic key used. Common social engineering methods include intimidation, enticement, or inducement.
Brute Force
As with a brute-force attack against passwords, a brute-force attack executed against a cryptographic algorithm uses all possible keys until a key is discovered that successfully decrypts the ciphertext. This attack requires considerable time and processing power and is very difficult to complete.
Differential Cryptanalysis
Differential cryptanalysis, also referred to as a side-channel attack, measures the execution times and power required by the cryptographic device. The measurements help the key and algorithm used.
Linear Cryptanalysis
Linear cryptanalysis is a known plaintext attack that uses linear approximation, which describes the behavior of the block cipher. An attacker is more successful with this type of attack when more plaintext and matching ciphertext messages are obtained.
Algebraic Attack
Algebraic attacks rely on the algebra used by cryptographic algorithms. If an attacker exploits known vulnerabilities of the algebra used, looking for those vulnerabilities can help the attacker to determine the key and algorithm used.
Frequency Analysis
Frequency analysis is an attack that relies on the fact that substitution and transposition ciphers will result in repeated patterns in ciphertext. Recognizing the patterns of eight bits and counting them can allow an attacker to use reverse substitution to obtain the plaintext message.
Frequency analysis usually involves the creation of a chart that lists all the letters of the alphabet alongside the number of times that letter occurs. So if the letter Q in the frequency lists has the highest value, a good possibility exists that this letter is actually E in the plaintext message because E is the most used letter in the English language. The ciphertext letter is then replaced in the ciphertext with the plaintext letter.
Today’s algorithms are considered too complex to be susceptible to this type of attack.
Birthday Attack
A birthday attack uses the premise that finding two messages that result in the same hash value is easier than matching a message and its hash value. Most hash algorithms can resist simple birthday attacks.
Dictionary Attack
Similar to a brute-force attack, a dictionary attack uses all the words in a dictionary until a key is discovered that successfully decrypts the ciphertext. This attack requires considerable time and processing power and is very difficult to complete. It also requires a comprehensive dictionary of words.
Replay Attack
In a replay attack, an attacker sends the same data repeatedly in an attempt to trick the receiving device. This data is most commonly authentication information. The best countermeasures against this type of attack are timestamps and sequence numbers.
Analytic Attack
In analytic attacks, attackers use known structural weaknesses or flaws to determine the algorithm used. If a particular weakness or flaw can be exploited, then the possibility of a particular algorithm being used is more likely.
Statistical Attack
Whereas analytic attacks look for structural weaknesses or flaws, statistical attacks use known statistical weaknesses of an algorithm to aid in the attack.
Factoring Attack
A factoring attack is carried out against the RSA algorithm by using the solutions of factoring large numbers.
Reverse Engineering
One of the most popular cryptographic attacks, reverse engineering occurs when an attacker purchases a particular cryptographic product to attempt to reverse engineer the product to discover confidential information about the cryptographic algorithm used.
Meet-in-the-Middle Attack
In a meet-in-the middle attack, an attacker tries to break the algorithm by encrypting from one end and decrypting from the other to determine the mathematical problem used.
Geographical Threats
Many threats are a function of the geographic location of the office or facility. This section discusses a wide variety of threats and issues, some of which only apply to certain areas. The security professional must be prepared to anticipate and mitigate those issues.
Internal Versus External Threats
When talking about threats to the physical security of assets, we can frame the conversation by threats that appear from outside the organization and those that come from within the organization. Many of the mitigation techniques discussed in the following sections are designed to address maintaining perimeter security or access to the building or room, whereas other techniques are designed to address threats from those who might have some access to the room or building.
For example, an electric fence surrounding the facility is designed to prevent access to the building by those who should not have any access (an external threat), whereas a door lock system on the server room that requires a swipe of the employee card is designed to prevent access by those who are already in the building (an internal threat). Keep this in mind as you read the following sections.
Natural Threats
Many of the physical threats that must be addressed and mitigated are caused by the forces of nature. Building all facilities to withstand the strongest hurricanes, tornadoes, and earthquakes is not economically feasible because in many areas these events happen infrequently if ever. What can be done is to make a realistic assessment of the historical weather conditions of an area and perform a prudent cost/benefit analysis to determine which threats should be addressed and which should be accepted. This section discusses some of the major natural threats.
Hurricanes/Tropical Storms
In certain areas, hurricanes and tropical storms are so frequent and unpredictable that all buildings are required to be capable of withstanding the more moderate instances of these storms. In other areas, doing that makes no sense even though these storms do occur from time to time. The location of the facility should dictate how much is spent in mitigating possible damages from these events.
Tornadoes
Although events of the last few years might seem to contradict this, over the long haul certain areas are more prone to tornadoes than others. A study of the rate and severity of tornadoes in an area from a historical perspective can help to determine measures that make sense for a particular location.
Note
In recent tornado outbreaks, many cellphone towers have been knocked out completely. In rural areas especially, communication with loved ones can be next to impossible. But the problem occurs not just in rural areas. In the Dallas–Fort Worth tornado outbreak in December 2015, it took many individuals up to 48 hours to locate loved ones because of lack of communications. You can imagine how this loss of communication would affect a company, school, or hospital.
Earthquakes
Earthquakes should be treated in the same way as hurricanes, tropical storms, and tornadoes; that is, the location of the specific facility should dictate the amount of preparation and the measures to take to address this risk. For example, facilities in California might give this issue more attention than those in the southeastern United States where these events are extremely rare.
Floods
Always take flooding into consideration because it is an event that can occur with the right circumstances just about anywhere. If at all possible, keep computing systems and equipment off the floor, and build server rooms and wiring closets on raised floors to help prevent damage that could occur in even a small flood.
System Threats
Some of the threats that exist are not from the forces of nature but from failures in systems that provide basic services, such as electricity and utilities. Although these problems can sometimes arise from events of nature, in this section we discuss guidelines for preparing and dealing with these events, which can occur in any location and in any type of weather conditions.
Electrical
Electricity is the lifeline of the organization and especially in regard to computing systems; outages are not only an inconvenience, but they can also damage equipment and cause loss of data. Moreover, when the plug is pulled, to a large degree the enterprise grinds to a halt in today’s world.
For this reason, all mission-critical systems should have uninterruptable power supplies (UPSs) that can provide power on a short-term basis until the system can be cleanly shut down. In cases where power must be maintained for longer than a matter of minutes, make onsite generators available to provide the power to keep systems running on a longer term basis until power is restored.
Noise, humidity, and brownouts are also issues that affect the electricity supply. The recommended optimal relative humidity range for computer operations is 40% to 60%. Critical systems must be protected from both power sags and surges. Neither is good for equipment. Line conditioners placed between the system and the power source can help to even out these fluctuations and prevent damage.
Finally, the most prevalent cause of computer center fires is electrical distribution systems. Checking these systems regularly can identify problems before they occur.
Communications
Protecting the physical security of communication, such as email, telephone, and fax systems, is a matter of preventing unauthorized access to the physical communication lines (cables and so on) and physical and logical access to equipment used to manage these systems.
For example, in the case of email, the email servers should be locked away, and access to them over the network must be tightly controlled with usernames and complex passwords.
In the case of fax machines, implementing policies and procedures can prevent sensitive faxes from becoming available to unauthorized persons. In some cases, preventing certain types of information from being transmitted with faxes might be necessary.
Many phone systems now have been merged into the data network using Voice over IP (VoIP). With these systems, routers and switches might be involved in managing the phone system and should be physically locked away and logically protected from network access in the same fashion as email servers. Because email and VoIP both use the data network, ensure that cabling is not exposed to tampering and malicious destruction.
Some additional considerations that can impact disaster recovery are:
![]() Maintain fault-tolerant connections to the Internet, such as T1 as the primary connection and a backup dial-up or satellite connection.
Maintain fault-tolerant connections to the Internet, such as T1 as the primary connection and a backup dial-up or satellite connection.
![]() Establish phone connections to employees besides primary organizational phone connections. Know cellphone and home numbers for employee notification.
Establish phone connections to employees besides primary organizational phone connections. Know cellphone and home numbers for employee notification.
![]() Establish radio communications over the entire campus with repeater antennas to provide communication during emergencies. Many primary forms of communication (such as phone lines and cellphones) can go down.
Establish radio communications over the entire campus with repeater antennas to provide communication during emergencies. Many primary forms of communication (such as phone lines and cellphones) can go down.
Utilities
Some utilities systems, such as gas and water, can be routed into the facility through ducts and tunnels that might provide an unauthorized entry point to the building. Such ducts and tunnels that offer this opportunity should be monitored with sensors and access control mechanisms.
Any critical parts of the systems where cut-off valves and emergency shutdown systems are located should be physically protected from malicious tampering. In some cases covering and protecting these valves and controls using locking cages might be beneficial.
Human-Caused Threats
Although many of the physical threats we face are a function of natural occurrences and random events, some of them are purposeful. This section explores some of the physical threats faced from malicious and careless humans. These threats come from both external forces and internal forces.
Explosions
Explosions can be both intentional and accidental. Intentional explosions can occur as a result of political motivation (covered in more detail in the section “Politically Motivated Threats”) or they can simply be vandalism. Accidental explosions can be the result of a failure to follow procedures and the failure of physical components.
With regard to intentional explosions, the best defense is to prevent access to areas where explosions could do significant damage to the enterprise’s operational components, such as server rooms, wiring closets, and areas where power and utilities enter the building. When an intentional explosion occurs, typically thought has been given to locating the explosive where the most harm can be done, so those areas should get additional physical protection.
Fire
Fires can happen anywhere and thus are a consideration at all times. Later in this chapter, you learn about both fire suppression and fire detection techniques. Address the threat of fire in the contexts of both an accident and an intentional attack. An auxiliary station alarm might be beneficial in many cases. This mechanism automatically causes an alarm originating in a data center to be transmitted over the local municipal fire or police alarm circuits for relaying to both the local police/fire station and the appropriate headquarters.
Fire extinguishers are classified using the standard system shown in Table 3-8. Later in this chapter, we talk more about fire extinguishers and suppression systems for the various types.

With respect to construction materials, according to (ISC)2, all walls must have a two-hour minimum fire rating in an information processing facility. Knowing that the most prevalent cause of computer center fires is electrical distribution systems is also useful. Regardless of the fire source, the first action to take in the event of a fire is evacuating all personnel.
Vandalism
Vandalism in most cases results in defacement of walls, bathrooms, and such, but when critical components are accessible, it can impact operations. Cut cables and smashed devices are reasons stressed in preventing physical access to these components.
Even when all measures have been taken, vandalism can still cause problems. For example, a purposefully plugged toilet can flood a floor and damage equipment if undetected.
Fraud
In the context of physical security, fraud involves gaining access to systems, equipment, or the facility through deception. For example, a person who enters the facility posing as a serviceman or a person who tailgates and follows an employee through the card system are both forms of fraudulent physical access. Physical access control systems become critical to preventing this type of fraud and the damage it can lead to.
Theft
Preventing physical theft of company assets depends on preventing physical access to the facility. Physical theft is the risk that will most likely affect CIA. For assets that leave the facility, such as laptops, give thought to protecting sensitive data that might exist on them through the use of encryption, preferably through encrypted drives.
Collusion
Collusion occurs when two employees work together to accomplish a theft of some sort that could not be accomplished without their combined knowledge or responsibilities. Use proper separation of duties to prevent a single person from controlling enough of a process to hide their actions.
Limiting the specific accesses of operations personnel forces an operator into collusion with an operator of a different category to have access to unauthorized data. Collusion is much less likely to occur from a statistical standpoint than a single person operating alone. When you consider this fact, the tradeoff in exchanging one danger for another is justified.
Politically Motivated Threats
Although it might seem at times like many more politically motivated threats exist today, these threats have always existed. The enterprise is often unwillingly dragged into these confrontations if they are seen as contributing to whatever the issue of the day might be. These threats can be costly in terms of lost productivity, destruction of company assets, and even physical danger to employees and officers of the company. This section covers some of the major ways these threats can manifest themselves along with measures to take that can lessen or mitigate the risk they present.
Strikes
Although strikes might be the least dangerous of the threats in this list, they can still damage the enterprise. In countries like the United States, basic rules of order have been established that prevent the worst of the possible outcomes, but even then an orderly strike can cost productivity and can hurt the image of the company. In other countries, strikes can be much more dangerous, especially when other political issues become intertwined with monetary issues.
Riots
Riots often occur seemingly out of nowhere, although typically an underlying issue explodes at some single incident. These events can be very dangerous as large mobs will often participate in activities that none of the individuals would normally do on their own. Often times the enterprise is seen as a willing participant in some perceived slight or wrong suffered by the rioters. In that case the company and its assets become a large and somewhat easy target.
Civil Disobedience
Civil disobedience is the intentional refusal to obey certain laws, demands, and commands of a government and is commonly, though not always, defined as being nonviolent resistance. One of the typical by-products of this is a disruption of some process to bring attention to the perceived injustice of the law or rule being broken.
It might also manifest itself as an action against some practice by the enterprise that might not be illegal but might be seen by some groups as harmful in some way. When this is the case the physical security of the facility becomes important as in some cases action might be taken to harm the facility.
Terrorist Acts
Increasingly, the threats of terrorist activity have caused a new focus on not only the security of facilities both at home and abroad but also of the physical safety of workers and officers. In many cases certain industries have found it beneficial to include emergency planning designed to address terrorist acts. Reactions to common scenarios are rehearsed to ensure the best possible outcome in the case of an attack.
Bombing
Bombing of facilities or company assets, once a rare occurrence, is no longer so in many parts of the world today. Increasingly, the enterprise is driven to include such considerations as local disturbance levels and general political unrest in an area before company sites are chosen. In many cases the simple threat of a bomb is enough to engage evacuation plans that are both costly and disruptive. Despite this, evacuation plans that address terrorist threats and bombings have become an integral part of any security policy, especially in certain parts of the world.
Site and Facility Design
For many forward-thinking organizations, physical security considerations begin during site selection and design. These companies have learned that building in security is easier than patching the security after the fact. In this section, site selection and site building practices that can lead to increased physical security are covered.
Layered Defense Model
All physical security should be based in a layered defense model. In such a model, reliance should not be based on any single physical security concept but on the use of multiple approaches that support one another. The theory is that if one tier of defense (say, for example, perimeter security) fails that another layer will serve as a backup (such as locks on the server room door). Layering the concepts discussed in this chapter can strengthen the overall physical security.
CPTED
Crime Prevention Through Environmental Design (CPTED) refers to designing a facility from the ground up to support security. It is actually a broad concept that can be applied to any project (housing developments, office buildings, and retail establishments). It addresses the building entrance, landscaping, and interior design. It aims to create behavioral effects that reduce crime. The three main strategies that guide CPTED are covered in this section.
Natural Access Control
The natural access control concept applies to the entrances of the facility. It encompasses the placement of the doors, lights, fences, and even landscaping. It aims to satisfy security goals in the least obtrusive and aesthetically appealing manner. A single object can be designed in many cases to fulfill multiple security objectives.
For example, many buildings have bollards or large posts in the front of the building with lights on them. These objects serve a number of purposes. They protect the building entrance from cars being driven into it. The lights also brighten the entrance and discourage crime, and finally they can guide people to the entrance.
Natural access control also encourages the idea of creating security zones in the building. These areas can be labeled, and then card systems can be used to prevent access to more sensitive areas. This concept also encourages a minimization of entry points and a tight control over those entry points. It also encourages a separate entrance in the back for suppliers that is not available or highly visible to the public.
Natural Surveillance
Natural surveillance is the use of physical environmental features to promote visibility of all areas and thus discourage crime in those areas. The idea is to encourage the flow of people such that the largest possible percentage of the building is always populated, because people in an area discourage crime. It also attempts to maximize the visibility of all areas.
Natural Territorials Reinforcement
The goal of natural territorials reinforcement is to create a feeling of community in the area. It attempts to extend the sense of ownership to the employees. It also attempts to make potential offenders feel that their activities are at risk of being discovered. This is often implemented in the form of walls, fences, landscaping, and light design.
Physical Security Plan
Another important aspect of site and facility design is the proper convergence between the physical layout and the physical security plan. Achieving all the goals of CPTED is not always possible, and in cases where gaps exist, the physical security plan should include policies and/or procedures designed to close any gaps. The plan should address the following issues.
Deter Criminal Activity
Both the layout and supporting policies should deter criminal activity. For example, as many areas as possible should be open and easily seen. There should be a minimum of isolated and darkened areas. Signage that indicates cameras or onsite monitoring and the presence of guards can also serve as deterrents.
Delay Intruders
Another beneficial characteristic of the physical security plan is to add impediments to entry, such as locks, fences, and barriers. Any procedures that slow and monitor the entry of people into the facility can also help. The more delay the intruder encounters, the less likely he is to choose the facility and the more likely he is to be caught.
Detect Intruders
Systems and procedures should be in place that allow for criminal activity to be detected. Motion sensors, cameras, and the like are all forms of intruder detection. Logging all visitors could also be a form of deterrence.
Assess Situation
The plan should identify specific personnel and actions to be taken when an event occurs. Compiling a list of incident types that indicate an acceptable response, response time, and contact names might be beneficial. Written plans developed ahead of time provide a much more effective and consistent response.
Respond to Intrusions and Disruptions
The plan should also attempt to anticipate and develop appropriate responses to intruders and to common disruptions (power outages, utility problems, and so on). Although anticipating every potential event is impossible, creating a list covering possible intrusions and disruptions should be doable. Scripted responses can then be developed to ensure a consistent and predictable response to these events from all personnel.
Facility Selection Issues
When an organization moves to a new facility or enlarges an existing one, it is a great opportunity to include physical security issues in the site selection process or in the expansion plan. In this section, we look at some critical items to consider if this opportunity presents itself.
Visibility
The amount of visibility desired depends on the organization and the processes being carried out at the facility. In some cases having high visibility of the location to help promote the brand or for convenience of customers is beneficial. In other cases a lower profile is desired when sensitive operations are taking place. When this is the case, the likelihood of eavesdropping from outside the facility through windows should be considered. Considering common areas is also important. If possible, these areas should not be isolated or darkened. Place them in visible areas with lighting to discourage crime. This includes hallways, parking lots, and other shared areas.
Note
Perimeter security controls, including lighting, fencing, and perimeter intrusion detection, are covered in more depth in Chapter 7, “Security Operations.”
Surrounding Area and External Entities
Considering the environment in which the facility is located is also important. What type of neighborhood is it? Is it an area that has a high crime rate, or is it isolated? Isolation can be good, but it also invites crime that might go undetected for a longer period of time. Also consider the distance to police stations, medical facilities, and fire stations as well. Finally, consider the nature of the operations of the surrounding businesses. Do they pose any sort of threat to your operations?
Accessibility
The ease with which employees and officers can access the facility is a consideration. What are the traffic conditions that the employees will encounter? If this is a new facility replacing an old one, is it inconvenient for the bulk of the employees? Do you risk losing employees over the commute? Is this location convenient to transportation options, such as train stations and airports? If lots of travel is required by your employees, accessibility could be important. If you often host employees from other locations on a temporary basis or host business partners, are safe accommodations nearby?
Construction
The materials used to construct a facility are another critical issue. But the issues to consider here do not stop at simply the makeup of the walls and ceilings, although that is crucial. The support systems built into the building are also important and include the following:
![]() Walls
Walls
![]() Doors
Doors
![]() Ceilings
Ceilings
![]() Windows
Windows
![]() HVAC
HVAC
![]() Power source
Power source
![]() Utilities
Utilities
![]() Fire detection and suppression
Fire detection and suppression
Some special considerations include the following:
![]() According to (ISC)2, all walls must have a two-hour minimum fire resistant rating.
According to (ISC)2, all walls must have a two-hour minimum fire resistant rating.
![]() Doors must resist forcible entry.
Doors must resist forcible entry.
![]() Location and type of fire suppression systems should be known.
Location and type of fire suppression systems should be known.
![]() Flooring in server rooms and wiring closets should be raised to help mitigate flooding damage.
Flooring in server rooms and wiring closets should be raised to help mitigate flooding damage.
![]() Backup and alternate power sources should exist.
Backup and alternate power sources should exist.
![]() Separate AC units must be dedicated and air quality/humidity should be controlled for data centers and computer rooms.
Separate AC units must be dedicated and air quality/humidity should be controlled for data centers and computer rooms.
Internal Compartments
In many areas of a facility, partitions are used to separate work areas. These partitions although appearing to be walls are not full walls in that that they do not extend all the way to the ceiling. When this construction approach is combined with a drop ceiling, also common in many buildings, an opportunity exists for someone to gain access to an adjoining room through the drop ceiling. All rooms that need to be secured, such as server rooms and wiring closets, should not have these types of walls.
Computer and Equipment Rooms
While we are on the subject of rooms that contain equipment to which physical access should be controlled, such as those that contain sensitive servers and crucial network gear, computer and equipment rooms should be locked at all times and secured and fitted with the following safeguards:
![]() Locate computer and equipment room in the center of the building, when possible.
Locate computer and equipment room in the center of the building, when possible.
![]() Computer and equipment rooms should have a single access door or point of entry.
Computer and equipment rooms should have a single access door or point of entry.
![]() Avoid the top floors of buildings for computer and equipment rooms.
Avoid the top floors of buildings for computer and equipment rooms.
![]() Install and frequently test fire detection and suppression systems.
Install and frequently test fire detection and suppression systems.
![]() Install raised flooring.
Install raised flooring.
![]() Install separate power supplies for computer and equipment rooms when possible.
Install separate power supplies for computer and equipment rooms when possible.
![]() Use only solid doors.
Use only solid doors.
Building and Internal Security
Although perimeter security is important, security within the building is also important as prescribed in the concentric circle model. This section covers issues affecting the interior of the facility.
Doors
A variety of door types and door materials can be used in buildings. They can either be hollow, which are used inside the building, or solid, typically used at the edge of the building and in places where additional security is required. Some door types with which a security professional should be familiar and prepared to select for protection are:
![]() Vault doors: Leading into walk-in safes or security rooms
Vault doors: Leading into walk-in safes or security rooms
![]() Personnel doors: Used by humans to enter the facility
Personnel doors: Used by humans to enter the facility
![]() Industrial doors: Large doors that allow access to larger vehicles
Industrial doors: Large doors that allow access to larger vehicles
![]() Vehicle access doors: Doors to parking building or lots
Vehicle access doors: Doors to parking building or lots
![]() Bullet-resistant doors: Doors designed to withstand firearms
Bullet-resistant doors: Doors designed to withstand firearms
Door Lock Types
Door locks can either be mechanical or electronic. Electric locks or cipher locks use a key pad that require the correct code to open the lock. These are programmable and organizations that use them should change the password frequently. Another type of door security system is a proximity authentication device, with which a programmable card is used to deliver an access code to the device either by swiping the card or in some cases just being in the vicinity of the reader. These devices typically contain the following Electronic Access Control (EAC) components:
![]() An electromagnetic lock
An electromagnetic lock
![]() A credential reader
A credential reader
![]() A closed door sensor
A closed door sensor
Turnstiles and Mantraps
Two special types of physical access control devices, mantraps and turnstiles, require mention as well. Although you might be familiar with a turnstile, which can be opened by scanning or swiping an access card, a mantrap is an unusual system with which you might not be familiar.
A mantrap is a series of two doors with a small room between them. The user is authenticated at the first door and then allowed into the room. At that point, additional verification occurs (such as a guard visually identifying the person) and then she is allowed through the second door. These doors are typically used only in very high security situations. Mantraps also typically require that the first door is closed prior to enabling the second door to open. Figure 3-20 shows a mantrap design.
Locks
Locks are also used in places other than doors, such as protecting cabinets and securing devices. Types of mechanical locks with which you should be familiar are:
![]() Warded locks: These have a spring-loaded bolt with a notch in it. The lock has wards or metal projection inside the lock with which the key will match and enable opening the lock. A warded lock design is shown in Figure 3-21.
Warded locks: These have a spring-loaded bolt with a notch in it. The lock has wards or metal projection inside the lock with which the key will match and enable opening the lock. A warded lock design is shown in Figure 3-21.
![]() Tumbler locks: These have more moving parts than the warded lock, and the key raises the lock metal piece to the correct height. A tumbler lock design is shown in Figure 3-22.
Tumbler locks: These have more moving parts than the warded lock, and the key raises the lock metal piece to the correct height. A tumbler lock design is shown in Figure 3-22.
![]() Combination locks: These require rotating the lock in a pattern that, if correct, lines the tumblers up, opening the lock. A combination lock design is shown in Figure 3-23.
Combination locks: These require rotating the lock in a pattern that, if correct, lines the tumblers up, opening the lock. A combination lock design is shown in Figure 3-23.
In the case of device locks, laptops are the main item that must be protected because they are so easy to steal. Laptops should never be left in the open without being secured to something solid with a cable lock. These are vinyl-coated steel cables that connect to the laptop and then lock around an object.
Biometrics
The highest level of physical access control and the most expensive to deploy is a biometric device. Biometric devices are covered extensively in Chapter 5.
Glass Entries
Glass entryways, which have become common in many facilities, include windows, glass doors, and glass walls. The proper glass must be selected for the situation. A security professional should be familiar with the following types of glass:
![]() Standard: Used in residential area and is easily broken
Standard: Used in residential area and is easily broken
![]() Tempered: Created by heating the glass, which gives it extra strength
Tempered: Created by heating the glass, which gives it extra strength
![]() Acrylic: Made of polycarbonate acrylic; is much stronger than regular glass but produces toxic fumes when burned
Acrylic: Made of polycarbonate acrylic; is much stronger than regular glass but produces toxic fumes when burned
![]() Laminated: Two sheets of glass with a plastic film between, which makes breaking it more difficult
Laminated: Two sheets of glass with a plastic film between, which makes breaking it more difficult
In areas where regular glass must be used but security is a concern, glass can be used that is embedded with wire to reduce the likelihood of breaking and entering. An even stronger option is to supplement the windows with steel bars.
Visitor Control
Some system of identifying visitors and controlling their access to the facility must be in place. The best system is to have a human present to require all visitors to sign in before entering. If that is unfeasible, another option is to provide an entry point at which visitors are presented with a locked door and a phone that can be used to call and request access. Either of these methods helps to prevent unauthorized persons from simply entering the building and going where they please.
Another best practice with regard to visitors is to always accompany a contractor or visitor to their destination to help ensure they are not going where they shouldn’t. In low security situations, this practice might not be necessary but is recommended in high security areas. Finally, log all visits.
Equipment Rooms
Lock any areas where equipment is stored, and control access to them. Having a strict inventory of all equipment so theft can be discovered is also important. For data centers and server rooms, the bar is raised even higher. There will be more on this topic later in this section.
Work Areas
Some system should be in place to separate areas by security. Some specific places where additional security measures might be required are discussed in this section. Most of these measures apply to both visitors and employees. Prohibiting some employees from certain areas might be beneficial.
Secure Data Center
Data centers must be physically secured with lock systems and should not have drop ceilings. Some additional considerations for rooms that contain lots of expensive equipment are
![]() They should not be located on top floors or in basements.
They should not be located on top floors or in basements.
![]() An off switch should be located near the door for easy access.
An off switch should be located near the door for easy access.
![]() Separate HVAC for these rooms is recommended.
Separate HVAC for these rooms is recommended.
![]() Environmental monitoring should be deployed to alert of temperature or humidity problems.
Environmental monitoring should be deployed to alert of temperature or humidity problems.
![]() Floors should be raised to help prevent water damage.
Floors should be raised to help prevent water damage.
![]() All systems should have a UPS with the entire room connected to a generator.
All systems should have a UPS with the entire room connected to a generator.
Restricted Work Area
The facility might have areas that must be restricted to only the workers involved, even from other employees. In these cases physical access systems must be deployed using smart cards, proximity readers, keypads, or any of the other physical access mechanisms described in this book.
Media Storage Facilities
A media storage facility is a building or a secured area within a building where media is stored. Because media can come in a variety of forms, organizations must determine which storage media they will use before selecting a media storage facility. If only tape or optical media is being stored, it might suffice to just install a fire-proof safe in an organization’s existing data center and to store a backup copy at a remote location. However, in some cases, a much larger solution is necessary because of the amount of data that is being protected. If a separate media storage facility is needed, then the organization must ensure that the facility provides the appropriate physical security to protect the media stored there.
Evidence Storage
If an organization has collected evidence that is crucial to an investigation, the organization must ensure that the evidence is protected from being accessed by unauthorized users. Only personnel involved in the investigation should have access to evidence that is stored. Evidence should be stored in a locked room, and access to the evidence should be logged. Evidence should be turned over to law enforcement at the appropriate time. If backup copies of digital evidence are retained during the investigation, the backup copies should also be in a secure storage area with limited personnel access.
Environmental Security
Although most considerations concerning security revolve around preventing mischief, preventing damage to data and equipment from environmental conditions is also the responsibility of the security team because it addresses the availability part of the CIA triad. In this section, some of the most important considerations are covered.
Fire Protection
Fire protection has a longer history than many of the topics discussed in this book, and while the traditional considerations concerning preventing fires and fire damage still hold true, the presence of sensitive computing equipment requires different approaches to detection and prevention, which is the topic of this section.
Fire Detection
Several options are available for fire detection.
You should be familiar with the following basic types of fire detection systems:

![]() Smoke-activated: Operates using a photoelectric device to detect variations in light caused by smoke particles.
Smoke-activated: Operates using a photoelectric device to detect variations in light caused by smoke particles.
![]() Heat-activated (also called heat-sensing): Operates by detecting temperature changes. These can either alert when a predefined temperature is met or alert when the rate of rise is a certain value.
Heat-activated (also called heat-sensing): Operates by detecting temperature changes. These can either alert when a predefined temperature is met or alert when the rate of rise is a certain value.
![]() Flame-actuated: Optical devices that “look at” the protected area. They generally react faster to a fire than non-optical devices do.
Flame-actuated: Optical devices that “look at” the protected area. They generally react faster to a fire than non-optical devices do.
Fire Suppression
Although certainly fire extinguishers (covered earlier in this chapter) are a manual form of fire suppression, other more automated systems also exist.
You should be familiar with the following sprinkler system types:

![]() Wet pipe: Use water contained in pipes to extinguish the fire. In some areas, the water might freeze and burst the pipes, causing damage. These are also not recommended for rooms where equipment will be damaged by the water.
Wet pipe: Use water contained in pipes to extinguish the fire. In some areas, the water might freeze and burst the pipes, causing damage. These are also not recommended for rooms where equipment will be damaged by the water.
![]() Dry pipe: In this system, the water is not held in the pipes but in a holding tank. The pipes hold pressurized air, which is reduced when fire is detected allowing the water to enter the pipe and the sprinklers. This minimizes the chance of an accidental discharge. Figure 3-24 shows a comparison of wet and dry systems.
Dry pipe: In this system, the water is not held in the pipes but in a holding tank. The pipes hold pressurized air, which is reduced when fire is detected allowing the water to enter the pipe and the sprinklers. This minimizes the chance of an accidental discharge. Figure 3-24 shows a comparison of wet and dry systems.
![]() Preaction: Operates like a dry pipe system except that the sprinkler head holds a thermal-fusible link that must be melted before the water is released. This is currently the recommended system for a computer room.
Preaction: Operates like a dry pipe system except that the sprinkler head holds a thermal-fusible link that must be melted before the water is released. This is currently the recommended system for a computer room.
![]() Deluge: Allows large amounts of water to be released into the room, which obviously makes this not a good choice where computing equipment will be located.
Deluge: Allows large amounts of water to be released into the room, which obviously makes this not a good choice where computing equipment will be located.
At one time, fire suppression systems used Halon gas, which works well by suppressing combustion through a chemical reaction. However, these systems are no longer used because they have been found to damage the ozone layer.
EPA-approved replacements for Halon include:
![]() Water
Water
![]() Argon
Argon
![]() NAF-S-III
NAF-S-III
Another fire suppression system that can be used in computer rooms that will not damage computers and is safe for humans is FM-200.
Power Supply
The power supply is the lifeblood of the enterprise and all of its equipment. In this section, we look at common power issues and some of the prevention mechanisms and mitigation techniques that will allow the company to continue to operate when power problems arise.
Types of Outages
When discussing power issues, you should be familiar with the following terms:
![]() Surge: A prolonged high voltage
Surge: A prolonged high voltage
![]() Brownout: A prolonged drop in power that is below normal voltage
Brownout: A prolonged drop in power that is below normal voltage
![]() Fault: A momentary power outage
Fault: A momentary power outage
![]() Blackout: A prolonged power outage
Blackout: A prolonged power outage
![]() Sags: A momentary reduction in the level of power
Sags: A momentary reduction in the level of power
However, possible power problems go beyond partial or total loss of power. Power lines can introduce noise and interfere with communications in the network. In any case where large electric motors or source of certain types of light, such as florescent lighting, are present, shielded cabling should be used to help prevent radio frequency interference (RFI) and electromagnetic interference (EMI).
Preventive Measures
Procedures to prevent static electricity from damaging components should be observed. Some precautions to take are:
![]() Use anti-static sprays.
Use anti-static sprays.
![]() Maintain proper humidity levels.
Maintain proper humidity levels.
![]() Use anti-static mats and wrist bands.
Use anti-static mats and wrist bands.
To protect against dirty power (sags and surges) and both partial and total power outages, the following devices can be deployed:
![]() Power conditioners: Go between the wall outlet and the device and smooth out the fluctuations of power delivered to the device, protecting against sags and surges.
Power conditioners: Go between the wall outlet and the device and smooth out the fluctuations of power delivered to the device, protecting against sags and surges.
![]() Uninterruptible power supplies (UPSs): Go between the wall outlet and the device and use a battery to provide power if the source from the wall is lost.
Uninterruptible power supplies (UPSs): Go between the wall outlet and the device and use a battery to provide power if the source from the wall is lost.
HVAC
Heating and air conditioning systems are not just in place for the comfort of the employees. The massive amounts of computing equipment deployed by most enterprises are even more dependent on these systems than humans. Without the proper environmental conditions, computing equipment won’t complain; it will just stop working. Computing equipment and infrastructure devices like routers and switches do not like the following conditions:
![]() Heat: Excessive heat causes reboots and crashes
Heat: Excessive heat causes reboots and crashes
![]() Humidity: Causes corrosion problems with connections
Humidity: Causes corrosion problems with connections
![]() Low humidity: Dry conditions encourage static electricity, which can damage equipment
Low humidity: Dry conditions encourage static electricity, which can damage equipment
With respect to temperature, some important facts to know are:
![]() At 100 degrees, damage starts occurring to magnetic media.
At 100 degrees, damage starts occurring to magnetic media.
![]() At 175 degrees, damage starts occurring to computers and peripherals.
At 175 degrees, damage starts occurring to computers and peripherals.
![]() At 350 degrees, damage starts occurring to paper products.
At 350 degrees, damage starts occurring to paper products.
In summary, the conditions need to be perfect for these devices. It is for this reason that AC units should be dedicated to the information processing facilities and on a separate power source than the other HVAC systems.
Water Leakage and Flooding
As much as computing systems dislike heat, they dislike water even more. It also can cause extensive damage to flooring, walls, and the facility foundation. Water detectors should be placed under raised floors and over dropped ceilings so that leaks in the ceiling and water under the floors are detected before they cause a problem.
Speaking of raised floors, in areas such as wiring closets, data centers, and server rooms, all floors should be raised to provide additional margin for error in the case of rising water.
Environmental Alarms
An error that causes a system to be vulnerable because of the environment in which it is installed is called an environmental error. Considering the various challenges presented by the environmental demands placed on the facility by the computing equipment and the costs of failing to address these needs, it behooves the enterprise to have some system that alerts when environmental conditions are less than desirable. An alert system such as a hygrometer, which monitors humidity, should be in place in areas where sensitive equipment resides. The system should also monitor temperature as well. These types of controls are considered physical controls.
Equipment Security
The physical security of the equipment has been stressed throughout this book. This section discusses corporate procedures concerning equipment and media and the use of safes and vaults for protecting other valuable physical assets.
Corporate Procedures
Physical security of equipment and media should be designed into the security policies and procedures of the company. These procedures should address the following issues.
Tamper Protection
It should not be possible for unauthorized persons to access and change the configuration of any devices. This means additional measures, such as the ones in the remainder of this section, should be followed to prevent this. Tampering includes defacing, damaging, or changing the configuration of a device. Integrity verification programs should be used by applications to look for evidence of data tampering, errors, and omissions.
Encryption
Encrypting sensitive data stored on devices can help to prevent the exposure of data in the event of a theft or in the event of inappropriate access of the device. Cryptography and encryption concepts are covered extensively earlier in this chapter.
Inventory
Recognizing when items are stolen is impossible if no item count or inventory system exists. All equipment should be inventoried, and all relevant information about each device should be maintained and kept up to date. Maintain this information both electronically and in hard copy.
Physical Protection of Security Devices
Security devices, such as firewalls, NAT devices, and intrusion detection and prevention systems, should receive the most attention because they relate to physical and logical security.
Beyond this, devices that can be easily stolen, such as laptops, tablets, and smartphones, should be locked away. If that is not practical, then lock these types of devices to a stationary object. A good example of this is the cable locks used with laptops.
Tracking Devices
When the technology is available, tracking of small devices can be used to help mitigate loss of both devices and their data, as previously covered. Most smartphones now include tracking software that allows you to locate the device after it has been stolen or lost by using either cell tower tracking or GPS. Deploy this technology when available.
Another useful feature available on these same types of devices is a remote wipe feature. This allows sending a signal to a stolen device instructing it to wipe out the data contained on the device. Finally, these devices typically also come with the ability to remotely lock the device when misplaced.
Portable Media Procedures
As previously covered, strict control of the use of portable media devices can help prevent sensitive information from leaving the network. This includes CDs, DVDs, flash drives, thumb drives, and external hard drives. Although written rules should be in effect about the use of these devices, using security policies to prevent the copying of data to these media types is also possible. Allowing the copying of data to these drive types as long as the data is encrypted is also possible. If these functions are provided by the network operating system, you should deploy them.
Safes, Vaults, and Locking
With respect to protecting physical assets such as laptops, smartphones, tablets, and so on, nothing beats physically locking the devices away. In cases where it is possible to do so, lockable cabinets are a good solution for storing these devices. In addition to selecting the proper lock (locks are discussed earlier in this chapter), all equipment should be inventoried, and a system devised for maintaining these counts as the devices come and go.
Some items require even more protection than a locked cabinet. Keep important legal documents and any other items of extreme value in a safe or a vault for the added protection these items require. Fire-proof safes and vaults can provide protection for contents even during a fire.
Exam Preparation Tasks
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 3-9 lists a reference of these key topics and the page numbers on which each is found.
Complete the Tables and Lists from Memory
Print a copy of the CD Appendix A, “Memory Tables,” or at least the sections for this chapter, and complete the tables and lists from memory. The CD Appendix B, “Memory Tables Answer Key,” includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
Brewer-Nash (Chinese Wall) model
certificate revocation list (CRL)
Cipher Block Chaining MAC (CBC-MAC)
closed-circuit television (CCTV)
Crime Prevention Through Environmental Design (CPTED)
Digital Encryption Standard (DES)
Digital Signature Standard (DSS)
Extensible Markup Language (XML)
Field-Programmable Gate Array (FPGA)
Information Technology Security Evaluation Criteria (ITSEC)
infrastructure as a service (IaaS)
International Data Encryption Algorithm (IDEA)
mercury vapor
mono-alphabetic substation cipher
natural territorials reinforcement
Online Certificate Status Protocol (OCSP)
Open Web Application Security Project (OWASP)
polyalphabetic substation cipher
proximity authentication device
Security Assertion Markup Language (SAML)
time-of-check/time-of-use attack
Trusted Computer System Evaluation Criteria (TCSEC)
uninterruptible power supply (UPS)
Answer Review Questions
1. Which of the following is provided if data cannot be read?
a. integrity
b. confidentiality
c. availability
2. In a distributed environment, which of the following is software that ties the client and server software together?
a. embedded systems
b. mobile code
c. virtual computing
d. middleware
3. Which of the following comprises the components (hardware, firmware, and/or software) that are trusted to enforce the security policy of the system?
a. security perimeter
b. reference monitor
c. Trusted Computer Base (TCB)
4. Which process converts plaintext into ciphertext?
a. hashing
b. decryption
c. encryption
d. digital signature
5. Which type of cipher is the Caesar cipher?
a. polyalphabetic substitution
b. mono-alphabetic substitution
c. polyalphabetic transposition
d. mono-alphabetic transposition
6. What is the most secure encryption scheme?
a. concealment cipher
b. symmetric algorithm
c. one-time pad
d. asymmetric algorithm
7. Which 3DES implementation encrypts each block of data three times, each time with a different key?
a. 3DES-EDE3
b. 3DES-EEE3
c. 3DES-EDE2
d. 3DES-EEE2
8. Which of the following is NOT a hash function?
a. ECC
b. MD6
c. SHA-2
d. RIPEMD-160
9. Which of the following is an example of preventing an internal threat?
a. a door lock system on a server room
b. an electric fence surrounding a facility
c. armed guards outside a facility
d. parking lot cameras
10. Which of the following is NOT one of the three main strategies that guide CPTED?
a. Natural Access Control
b. Natural Surveillance Reinforcement
c. Natural Territorials Reinforcement
d. Natural Surveillance
11. What occurs when different encryption keys generate the same ciphertext from the same plaintext message?
a. key clustering
b. cryptanalysis
c. keyspace
d. confusion
12. Which encryption system uses a private or secret key that must remain secret between the two parties?
a. running key cipher
b. concealment cipher
c. asymmetric algorithm
d. symmetric algorithm
13. Which of the following is an asymmetric algorithm?
a. IDEA
b. Twofish
c. RC6
d. RSA
14. Which PKI component contains a list of all the certificates that have been revoked?
a. CA
b. RA
c. CRL
d. OCSP
15. Which attack executed against a cryptographic algorithm uses all possible keys until a key is discovered that successfully decrypts the ciphertext?
a. frequency analysis
b. reverse engineering
c. ciphertext-only attack
d. brute force
16. In ISO/IEC 15288:2015, which process category includes acquisition and supply?
a. Technical management processes
b. Technical processes
c. Agreement processes
d. Organizational project-enabling processes
17. Which of the following is NOT a principle in the risk-based category of NIST 800-27 Rev A?
a. Assume that external systems are insecure.
b. Eliminate risk.
c. Protect information while being processed, in transit, and in storage.
d. Protect against all likely classes of attacks.
18. Which statement is true of dedicated security mode?
a. It employs a single classification level.
b. All users have the same security clearance, but they do not all possess a need-to-know clearance for all the information in the system.
c. All users must possess the highest security clearance, but they must also have valid need-to-know clearance, a signed NDA, and formal approval for all information to which they have access.
d. Systems allow two or more classification levels of information to be processed at the same time.
19. What is the first step in ISO/IEC 27001:2013?
a. Identify the requirements.
b. Perform risk assessment and risk treatment.
c. Maintain and monitor the ISMS.
d. Obtain management support.
20. Which two processor states are supported by most processors?
a. supervisor state and problem state
b. supervisor state and kernel state
c. problem state and user state
d. supervisor state and elevated state
21. When supporting a BYOD initiative, from which group do you probably have most to fear?
a. hacktivists
b. careless users
c. software vendors
d. mobile device vendors
22. Which term applies to embedded devices that bring with them security concerns because engineers that design these devices do not always worry about security?
a. BYOD
b. NDA
c. IoT
d. ITSEC
23. Which option best describes the primary concern of NIST SP 800-57?
b. symmetric encryption
c. message integrity
d. key management
24. Which of the following key types requires only integrity security protection?
a. public signature verification key
b. private signature key
c. symmetric authentication key
d. private authentication key
25. What is the final phase of the cryptographic key management life cycle, according to NIST SP 800-57?
a. operational phase
b. destroyed phase
c. pre-operational phase
d. post-operational phase
Answers and Explanations
1. b. Confidentiality is provided if the data cannot be read. This can be provided either through access controls and encryption for data as it exists on a hard drive or through encryption as the data is in transit.
2. d. In a distributed environment, middleware is software that ties the client and server software together. It is neither a part of the operating system nor a part of the server software. It is the code that lies between the operating system and applications on each side of a distributed computing system in a network.
3. c. The TCB comprises the components (hardware, firmware, and/or software) that are trusted to enforce the security policy of the system and that if compromised jeopardize the security properties of the entire system.
4. c. Encryption converts plaintext into ciphertext. Hashing reduces a message to a hash value. Decryption converts ciphertext into plaintext. A digital signature is an object that provides sender authentication and message integrity by including a digital signature with the original message.
5. b. The Caesar cipher is a mono-alphabetic substitution cipher. The Vigenere substitution is a polyalphabetic substitution.
6. c. A one-time pad is the most secure encryption scheme because it is used only once.
7. b. The 3DES-EEE3 implementation encrypts each block of data three times, each time with a different key. The 3DES-EDE3 implementation encrypts each block of data with the first key, decrypts each block with the second key, and encrypts each block with the third key. The 3DES-EDE2 implementation encrypts each block of data with the first key, decrypts each block with the second key, and then encrypts each block with the first key. The 3DES-EEE2 implementation encrypts each block of data with the first key, encrypts each block with the second key, and then encrypts each block with the third key.
8. a. ECC is NOT a hash function. It is an asymmetric algorithm. All the other options are hash functions.
9. a. An electric fence surrounding a facility is designed to prevent access to the building by those who should not have any access (an external threat), whereas a door lock system on the server room that requires a swipe of the employee card is designed to prevent access by those who are already in the building (an internal threat).
10. b. The three strategies are natural access control, natural territorials reinforcement, and natural surveillance.
11. a. Key clustering occurs when different encryption keys generate the same ciphertext from the same plaintext message. Cryptanalysis is the science of decrypting ciphertext without prior knowledge of the key or cryptosystem used. A keyspace is all the possible key values when using a particular algorithm or other security measure. Confusion is the process of changing a key value during each round of encryption.
12. d. A symmetric algorithm uses a private or secret key that must remain secret between the two parties. A running key cipher uses a physical component, usually a book, to provide the polyalphabetic characters. A concealment cipher occurs when plaintext is interspersed somewhere within other written material. An asymmetric algorithm uses both a public key and a private or secret key.
13. d. RSA is an asymmetric algorithm. All the other algorithms are symmetric algorithms.
14. c. A CRL contains a list of all the certificates that have been revoked. A CA is the entity that creates and signs digital certificates, maintains the certificates, and revokes them when necessary. An RA verifies the requestor’s identity, registers the requestor, and passes the request to the CA. OCSP is an Internet protocol that obtains the revocation status of an X.509 digital certificate.
15. d. A brute-force attack executed against a cryptographic algorithm uses all possible keys until a key is discovered that successfully decrypts the ciphertext. A frequency analysis attack relies on the fact that substitution and transposition ciphers will result in repeated patterns in ciphertext. A reverse engineering attack occurs when an attacker purchases a particular cryptographic product to attempt to reverse engineer the product to discover confidential information about the cryptographic algorithm used. A ciphertext-only attack uses several encrypted messages (ciphertext) to figure out the key used in the encryption process.
16. c. ISO/IEC 15288:2015 establishes four categories of processes:
![]() Agreement processes, including acquisition and supply
Agreement processes, including acquisition and supply
![]() Organizational project-enabling processes, including infrastructure management, quality management, and knowledge management
Organizational project-enabling processes, including infrastructure management, quality management, and knowledge management
![]() Technical management processes, including project planning, risk management, configuration management, and quality assurance
Technical management processes, including project planning, risk management, configuration management, and quality assurance
![]() Technical processes, including system requirements definition, system analysis, implementation, integration, operation, maintenance, and disposal
Technical processes, including system requirements definition, system analysis, implementation, integration, operation, maintenance, and disposal
17. b. NIST 800-27 Rev A does NOT require that risk be eliminated. These are the risk-based principles in NIST 800-27 Rev A:
![]() Reduce risk to an acceptable level.
Reduce risk to an acceptable level.
![]() Assume that external systems are insecure.
Assume that external systems are insecure.
![]() Identify potential trade-offs between reducing risk and increased costs and decrease in other aspects of operational effectiveness.
Identify potential trade-offs between reducing risk and increased costs and decrease in other aspects of operational effectiveness.
![]() Implement tailored system security measures to meet organizational security goals.
Implement tailored system security measures to meet organizational security goals.
![]() Protect information while being processed, in transit, and in storage.
Protect information while being processed, in transit, and in storage.
![]() Consider custom products to achieve adequate security.
Consider custom products to achieve adequate security.
![]() Protect against all likely classes of attacks.
Protect against all likely classes of attacks.
18. a. Dedicated security mode employs a single classification level.
19. d. The first step in ISO/IEC 27001:2013 is to obtain management support.
20. a. Two processor states are supported by most processors: supervisor state (or kernel mode) and problem state (or user mode).
21. b. As a security professional, when supporting a BYOD initiative, you should take into consideration that you probably have more to fear from the carelessness of the users than you do from hackers.
22. c. Internet of Things (IoT) is the term used for embedded devices and their security concerns because engineers that design these devices do not always worry about security.
23. d. Key management is the primary concern of NIST SP 800-57.
24. a. Public signature verification keys require only integrity security protection.
25. b. The destroyed phase is the final phase of the cryptographic key management life cycle, according to NIST SP 800-57.