Chapter 1
Implement modern device services
This chapter covers cloud-based services within Microsoft 365 that are designed to deploy, secure, and manage devices in the enterprise. Throughout this book, you will work with various Microsoft technologies that are included in the Enterprise Mobility + Security (EMS) licensing suite. A majority of services are administered through the Microsoft Endpoint Manager admin center, but there are other portals such as the Azure Portal and the Microsoft Store for Business portal. Along the way there will be several walkthroughs and examples that illustrate how to manage these tools. For these demonstrations we do recommend that you follow along in your own lab. Here are a few links to help get you started:
Enterprise Mobility + Security 90-day trial (includes Azure Active Directory Premium P2) https://www.microsoft.com/cloud-platform/enterprise-mobility-security-trial
Office 365 Business Premium 30-day trial https://products.office.com/business/office-365-business-premium
Skills in this chapter:
Skill 1.1: Plan device management
Device management is one of the core services provided by Microsoft Intune that is managed through the Microsoft Endpoint Manager admin center. Device management requires that the Microsoft Endpoint Manager be configured, and that the appropriate licenses are available in the tenant. You will assign these licenses to users, which in turn can use the devices that are enrolled in the tenant. After the devices are enrolled, you can manage and monitor the devices from the Microsoft Endpoint Manager admin center.
Plan device monitoring
This skill section reviews device, or endpoint, monitoring options available through Microsoft 365 Defender. These offerings enable organizations to monitor the health and compliance of the devices and apps in their environment. The two primary tools for monitoring endpoints are provided through the Microsoft 365 security center and the Microsoft Endpoint Manager admin center.
The Microsoft 365 security center is a one-stop shop that brings Defender for Endpoint, Defender for Office 365, Microsoft 365 Defender, and other tools together into one interface. From the security center, you can perform many monitoring actions:
View your Microsoft Secure Score The Secure Score gives you recommended improvement actions based on the current configuration of your environment.
View device compliance Determine the number, type, and names of devices that are compliant, noncompliant, in a grace period, or not evaluated.
View devices at risk Display the number of devices and their risk level based on the current configuration.
View devices with active malware Track the security events and enforce configuration, compliance, and remediation through Intune device management.
To enable Microsoft 365 Defender, you must have either the global administrator or security administrator Azure Active Directory role. When you enable Microsoft 365 Defender, there are tenant settings that must be configured, including:
Data storage location The primary location of business for the organization where data residency will apply.
Data retention The default retention period is six months, but can be changed.
Preview features Preview features are enabled by default.
The Microsoft Endpoint Manager admin center provides an all-in-one admin center for device enrollment, device and configuration compliance, endpoint security, and other reporting capabilities. The built-in reports are categorized into four focus areas.
Operational Targeted and action-oriented data
Organizations High-level summary reviews for an organization
Historical Displays patterns and trends over a period of time
Specialist Enables you to use the underlying data to create your own custom reports
Figure 1-1 shows the default home page of the Microsoft Endpoint Manager admin center with healthy and active device status reports.
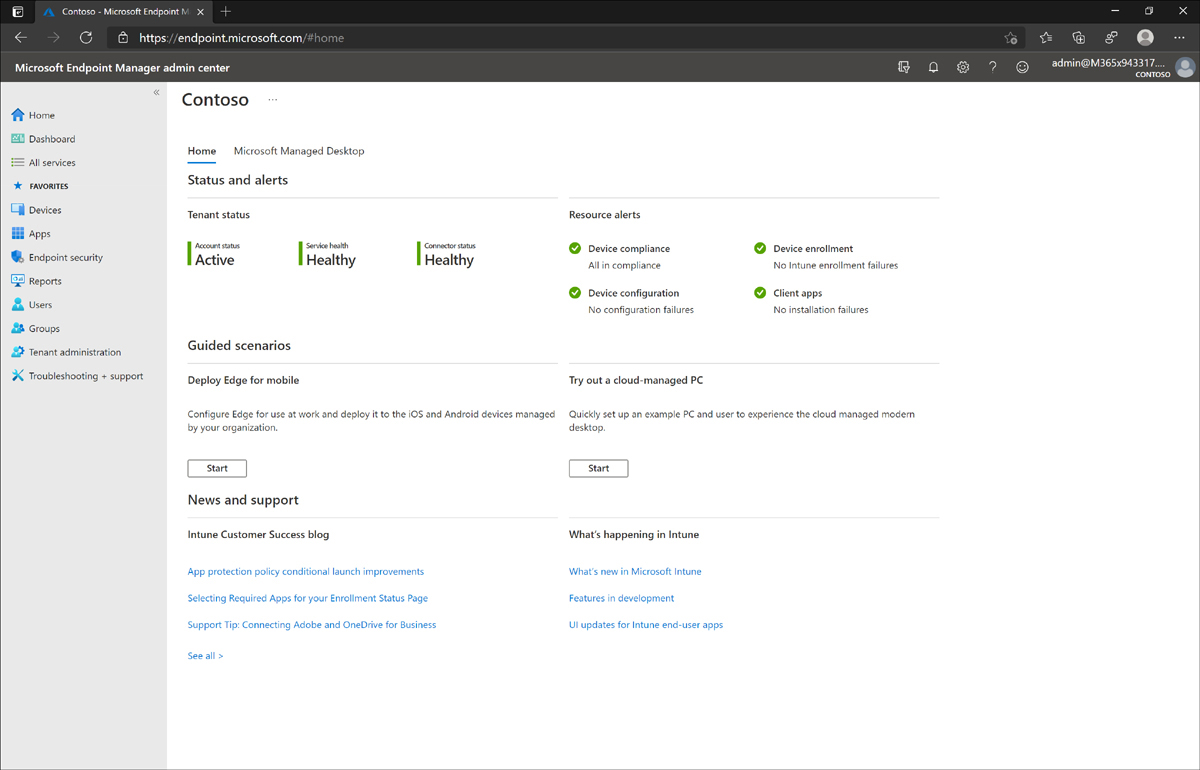
Figure 1-1 Microsoft Endpoint Manager admin center
Note
To review the logs used as part of reporting, you must have either the global administrator or Intune service administrator role, or have the Intune administrator role with read permissions.
Plan Microsoft Endpoint Manager implementation
Microsoft offers a combination of endpoint solutions that are managed through the Microsoft Endpoint Manager admin center. These offerings have changed over the years, with heavy investments in cloud services and integration with Azure. The introduction of Windows 10 has also influenced the way you manage devices with a set of native mobile device management (MDM) protocols within the operating system, eliminating the need to install another agent on your endpoints. Which solution to choose depends on your organization’s deployment goals and objectives. The two primary device-management solutions provided by Microsoft are:
Microsoft Intune This solution works best for customers who require modern management capabilities for Windows 10 devices, but also need to limit their on-premises server infrastructure. Microsoft Intune is a cloud-based management solution that does not require additional server infrastructure. Platform support for Intune includes management capabilities for Windows 10 and macOS. You also have access to features like Autopilot, which can help reduce traditional operating system deployment requirements.
Co-management between Microsoft Intune and ConfigMgr This solution bridges Microsoft Intune and ConfigMgr, enabling customers to co-manage devices based on their requirements. ConfigMgr is an on-premises management solution that includes additional platform support, such as Windows Server. It also includes a unique set of technologies, such as task sequences and image deployment. Environments with co-management can take workloads for their Windows 10 devices and mobile devices and move them to the cloud, while still supporting traditional infrastructure.
Set up Intune
There are several steps required to set up Intune before you can manage devices. These steps are as follows:
Understand supported configurations These include the supported device operating system, network requirements, and commercial versus sovereign cloud.
Create a subscription Add Intune to your tenant, taking into consideration whether you have a Microsoft Online Services account, an Enterprise Agreement, or a volume licensing agreement.
Configure a custom domain name Configure a custom or vanity domain name to use with your tenant. It is recommended to do this before adding user accounts to simplify account management.
Add users and groups Add individual users and groups to Intune. Alternatively, connect to Active Directory with Intune for synchronization.
Assign licenses Associate purchased Intune or Enterprise Mobility + Security licenses with user accounts.
Set the MDM authority This applies only to tenants with a service release earlier than 1911. Tenants running 1911 or later are automatically configured to Intune.
Assign apps Apps can be assigned to groups for automatic or optional installation.
Configure devices Configure the profiles that manages device settings and features.
Customize the portals Add your company branding to the various portals.
Enable device enrollment Enable certain devices to be enrolled for management by Intune.
Configure app policies Configure specific app protection policies for apps protected by Intune.
Need More Review? Setting Up Microsoft Intune
For a more detailed step by step for setting up Intune, visit https://docs.microsoft.com/en-us/mem/intune/fundamentals/setup-steps.
Assign licenses
You can assign Intune licenses to users from both the Microsoft Endpoint Manager admin center and the Azure portal within Azure Active Directory. To assign a license from the admin center, follow these steps:
Log in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com.
Click Users.
Click All Users, then click the user for whom you want to change license assignments.
Click Licenses, and then click Assignments.
Select the Microsoft Intune check box and click Save. (The location of the check box varies depending on the type of license you purchased.)
Figure 1-2 shows the Microsoft Intune license enabled as part of the Enterprise Mobility + Security E5 license suite. Each licensed user can access and use the services defined in their profiles for up to 15 managed devices.

Figure 1-2 Assign licenses to users.
Plan for configuration profiles
In this section, you’ll review the available settings for configuration profiles. Configuration profiles define the settings that you wish to implement on the devices that are managed. For example, you can customize the browser settings on Windows clients or prevent access to Bluetooth on mobile devices. Configuration profiles are built to define these settings per platform. The supported platforms from the Microsoft Endpoint Manager admin center are:
Android device administrator
Android Enterprise
iOS/iPad OS
macOS
Windows 10 and later
After you select the platform to define a profile for, you must select a profile type. The types of profiles vary depending on the platform you selected. For macOS and Windows device types, the options are either Settings Catalog or Templates. The Settings Catalog is a list of all available settings for the selected operating system. For Windows, that equates thousands of settings.
Templates are commonly used tools that need configuration. For example, there are templates for endpoint protection, VPN and Wi-Fi configuration, certificates, device features, and more.
Need More Review? Setting Up Microsoft Intune
For more information on applying the settings of a configuration profile, visit https://docs.microsoft.com/en-us/mem/intune/configuration/device-profiles.
You create a configuration profile from the Microsoft Endpoint Manger admin center. To create a configuration profile, perform the following steps:
Log in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com/.
Click Devices.
Click Configuration Profiles.
Click Create Profile.
In the Platform drop-down menu, select an operating system—in this example, Windows 10 and Later.
In the Profile type drop-down menu, select a profile—in this example, Templates.
In the list of available templates, click Wi-Fi.
Click Create.
On the Basics tab, type a name for the profile, such as Required-Wi-Fi.
Click Next.
In the Wi-Fi Type drop-down menu, select Basic.
Complete the configuration settings for the Wi-Fi network the device will connect to.
Figure 1-3 illustrates automatically connecting to a Wi-Fi network named ContosoWifi that has WPA2 security and a pre-shared key of Secure123!.

Figure 1-3 Wi-Fi configuration profile settings
Click Next.
On the Assignments tab, click Add All Devices. Alternatively, select the groups of devices that the profile should apply to.
Click Next.
On the Applicability Rules tab, leave the defaults blank. Alternatively, add rule filters to specify when this configuration profile should be applied.
Click Next, and then click Create.
The configuration rule is created and added to the devices you selected.
After you create the profile, you can see its status on a per-device and per-user level. Note, however, that it might take a few minutes for the profile to deploy and be applied on the devices, depending on the number of devices and their connection type. Figure 1-4 shows the status of the newly created profile being applied to a Windows 10 device.
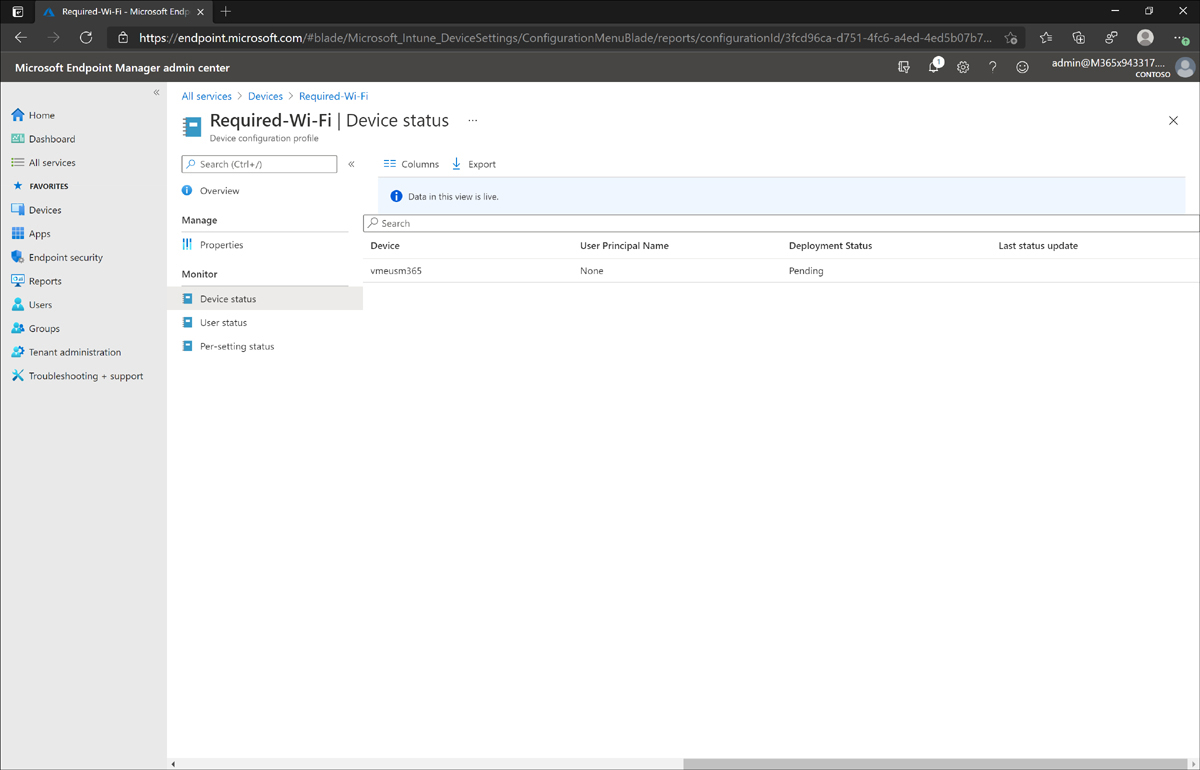
Figure 1-4 Pending profile deployment
Skill 1.2: Manage device compliance
Device compliance is the practice of ensuring that the devices accessing your environment meet a distinct set of requirements, often defined by the IT and cybersecurity teams in your organization. For the purposes of this exam, device compliance is also referred to as a feature in Microsoft Intune. This feature is provided to aid administrators in defining their compliance requirements and using them to delegate access to data and services. As an administrator, it is your job to understand the use cases for device compliance and how to implement them.
The compliance policies that you define make up the connective tissue for several other actions in the platform. For example, the compliance status of a device can be leveraged as a determining factor for granting access to Exchange Online. This is accomplished using conditional access policies, another key feature covered in this chapter. Conditional access policies are a different type of policy, managed within Azure Active Directory (Azure AD), for allowing and denying access to data and services.
Plan for device compliance
This skill section covers planning considerations for device compliance. This includes topics such as prerequisites before implementation, compliance workflows, and possible use cases for your organization. Later in this chapter, you will work with conditional access policies. One of the dependencies for conditional access is the compliance status of the end-user device. The MS-101 exam presents scenarios dealing with Intune enrollment, device compliance, and conditional access. As you prepare, take time to work with these technologies in the Azure portal and see what the dependencies are.
Understand the prerequisites for device compliance
Before you get started creating device-compliance policies, there are some technical prerequisites to plan for. Throughout this book you will see some trending prerequisites for each of the cloud technologies, particularly around the required subscriptions. Keep an eye out for these for the exam and take some extra time to understand which features are included with the various subscription models.
These are the prerequisites for device compliance:
Subscriptions Device-compliance technology relies on Azure AD and Microsoft Intune. The device must be enrolled in Intune to receive a compliance policy, and the compliance flag is written to Azure AD for other features, such as conditional access. At a minimum you need a standalone Intune subscription and an Azure AD Premium P1 subscription. The higher-tiered subscriptions, such as Azure AD Premium P2, do not include additional capabilities focused on device compliance.
Platform support Device-compliance policies support a wide range of platforms. (For clarification, the term platform refers to the operating system, not the physical hardware.) Platform support is an important prerequisite if you are planning to manage devices that are not supported. At the time of this writing, the following platforms are supported:
Android
Android Enterprise
iOS
macOS
Windows 8.1
Windows 10
Enrollment Devices cannot report compliance until they are enrolled in Microsoft Intune.
Need More Review? Choosing a Subscription
For more information about the different editions of Azure AD and their corresponding subscription tier, visit https://azure.microsoft.com/en-us/pricing/details/active-directory/. For more information about subscriptions pertaining to Microsoft Intune, visit https://www.microsoft.com/en-us/cloud-platform/microsoft-intune-pricing.
Understand the process flow for device compliance
Device compliance and conditional access are both policy-based technologies. You configure the policy to address your needs, and then assign that policy to the desired resources in Microsoft Intune. Devices will evaluate the policy and report back whether they meet the requirements or not. The compliance state is then written to the device object in Azure AD as a custom attribute. The state of that attribute will determine whether the device is approved to access data and services. This is where conditional access enters the picture, which is covered in more detail later in this chapter.
Figure 1-5 illustrates the device-compliance flow. In this example, we are using the default configuration for device compliance. As an administrator, you have a few options to change this flow to meet your needs.
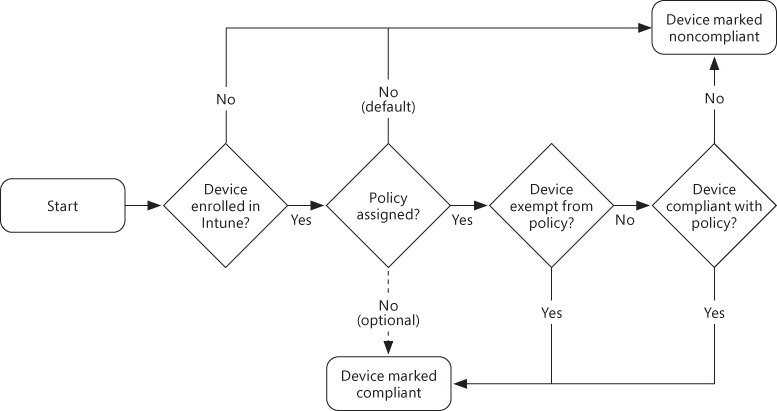
Figure 1-5 Device-compliance process flow
These next few items address controls that are available to administrators to alter the device-compliance flow.
Intune enrollment Devices that are not enrolled in Intune cannot receive device-compliance policies. This also applies to devices that are Azure AD joined. This was covered earlier in the prerequisites section. In this context, it can also be used to prevent compliance policies from applying to unmanaged devices.
Policy assignment In the compliance policy settings for Microsoft Intune, you have the option to mark devices as compliant if they do not have a policy assigned. By default, all devices without an assigned policy are marked as noncompliant. But you do have the option to change this behavior, making all devices compliant by default. This is represented by the dashed line between the policy assigned and the device marked compliant in the illustration, also marked as optional.
Device exemption Device exemption is another control you can configure. This is accomplished in the policy settings by defining which device platforms the compliance policy is scoped for. If your compliance policy includes all platforms except iOS, then iOS devices will be exempt from running that policy.
Determine use cases for device compliance
In this section, you are going to look at some potential use cases for device compliance. First, understand that compliance policies contain a series of rules that you define. These rules determine whether a device is compliant. Compliance policies can help to remediate certain conditions, but in most cases the device will be quarantined, and remediation will be left up to the user. For example, suppose you have a device-compliance policy that has a security rule that requires a password before unlocking a device. If a device is noncompliant with this policy, the user will be prompted to set a password on their noncompliant device.
Users with devices that are marked as noncompliant will receive notifications about the conflicting rules. As an administrator, you can also create a conditional access policy to block these devices until they are remediated. See Table 1-1 for a series of compliance policies and corresponding sample use cases.
Table 1-1 Device compliance use cases
Platform |
Setting(s) |
Sample Use Case |
|---|---|---|
Windows 10 |
Minimum OS version Valid operating system builds |
Windows 10 devices that are not running the latest cumulative update are marked as noncompliant. Windows 10 devices running a supported release are still valid while upgrades are rolling out. |
macOS |
Require system integrity protection |
macOS devices that do not have system integrity protection enabled are marked as noncompliant. |
Android |
Rooted devices Encryption of data storage on device |
Android devices that are rooted are marked as noncompliant. Android devices that do not have data storage encryption enabled are marked as noncompliant. |
iOS |
Jailbroken devices Minimum OS version Restricted apps |
iOS devices that are jailbroken are marked as noncompliant. iOS devices that are not running the latest major release of iOS are marked as noncompliant. iOS devices that have the Dropbox app installed are marked as noncompliant. |
Design conditional access policies
In this skill section, you will review the design aspects of conditional access policies. As you prepare for these skills, plan to spend time working in the Azure portal and following along to review the interface and controls for conditional access.
This section began by covering what device compliance means from a cloud-management perspective. Now you will see how device compliance is used to establish access requirements for data and services in your organization.
Design for the protection of data and services using conditional access policies
There are a variety of policy settings available for conditional access, and a mixture of configurations that you can implement. Let’s first look at the Conditional Access Policies blade in the Azure portal. This will help set the stage for conditional access policies and introduce you to some key terms. Figure 1-6 shows the New Conditional Access Policy blade. Let’s drill down and take a closer look at each of the available options.
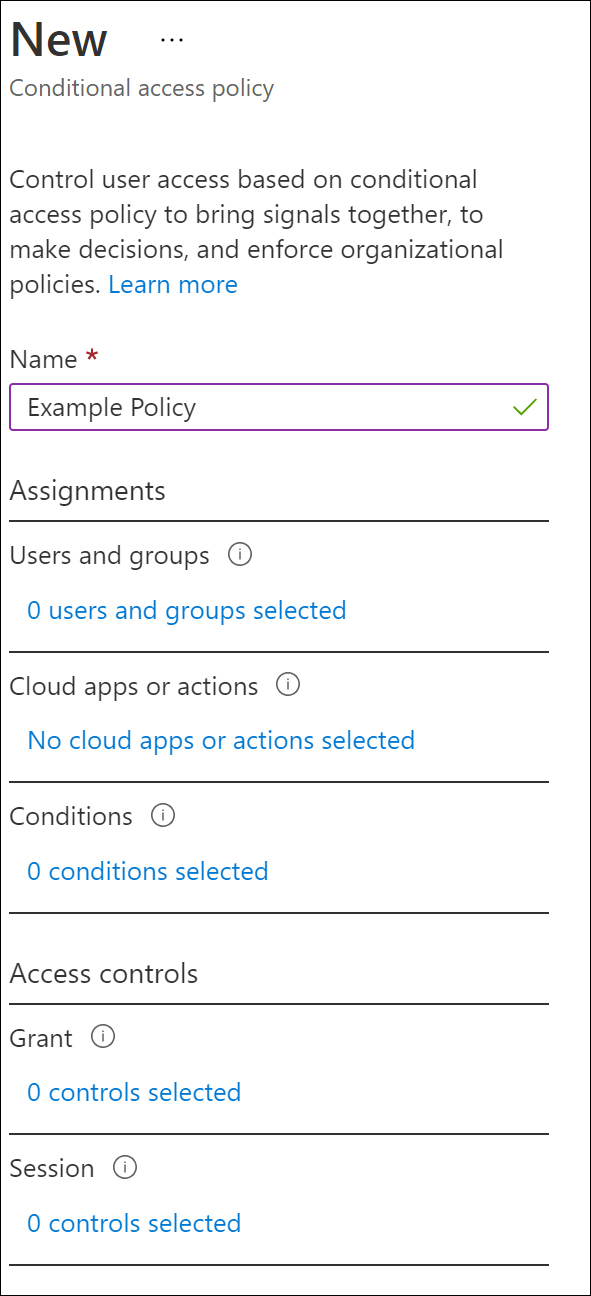
Figure 1-6 Conditional access policy creation
Assignments These define the scope, criteria, and conditions of the policy you are deploying. The New Conditional Access Policy blade contains three assignment categories:
Users and Groups These define who will receive the policy. You can either include or exclude users and groups. Although the New Conditional Access Policy blade does not prevent you from proceeding, all conditional access policies require a user and group assignment before they can be applied. For includes, you can select all users or specific users and groups. For example, if you have a group that contains only your marketing team, you can select that as an option. For excludes, you can select all guest users (defined by the userType attribute), specific directory roles (such as application developer), or specific users or groups.
Cloud Apps or Actions These define the services that users will access for productivity. You have the choice to include or exclude services on a predefined list of supported cloud apps. For includes, you can select all cloud apps or specific apps, such as Microsoft Teams. For excludes, you can select specific apps.
Conditions These define when a policy is applied. See Table 1-2 for a breakdown of each condition, the available options, and some sample use cases.
Table 1-2 Conditional access options
Condition |
Description |
Options |
Sample Use Case |
|---|---|---|---|
Sign-in risk |
Azure AD determines a user’s sign-in risk based on a configurable policy under Azure AD Identity Protection. |
High, medium, low, or no risk |
Enforce MFA policy for users who are flagged with a medium sign-in risk. |
Device platforms |
Azure AD retrieves the operating system of the joined device, but the information is not verified. This should be combined with a Microsoft Intune enrollment and device-compliance policy. |
Android, iOS, Windows Phone, Windows, macOS |
Enforce an app restriction policy on iOS and Android devices only. |
Locations |
Locations are used to define trusted network locations. Trusted network locations are configured in Azure AD under Named Locations. |
Trusted locations |
Block access to Exchange Online from the San Francisco office with an IP subnet of 10.20.11.0/22 |
Client apps (preview) |
Set conditional restrictions based on specific client apps. |
Browsers, mobile apps, and desktop clients |
Restrict access to mobile apps unless the device is marked as compliant. |
Device state (preview) |
Exclude corporate or trusted devices from conditional access restrictions. |
Hybrid Azure AD joined devices, devices marked as compliant |
Enforce restrictions to Office 365 Exchange Online for noncompliant devices. |
Access Controls These define additional requirements for granting or denying access, along with session controls for limiting the experience within cloud apps. The following options are available from the Access Controls section:
Grant This enables you to block access based on the conditions that you defined under the Assignments section. Alternatively, you can choose to grant access and enforce additional requirements. For example, you can require MFA or only grant access to devices that are marked as compliant through device-compliance policies.
Session This enables you to limit the experience within certain cloud apps. At the time of this writing, Exchange Online and SharePoint Online are the only cloud apps that support app enforced restrictions. Enabling this feature adds real-time monitoring and control capabilities to these apps.
Now that you have spent some time exploring the interface, let’s look at how a conditional access policy is constructed. The policy is made up of two parts: the condition and the access control. You can also look at these in the following context: when this happens (condition), then do this (access control). For the exam you should be familiar with this formula and how it corresponds to conditional access restrictions. See Table 1-3 for a few examples on how conditional access policies are assembled.
Table 1-3 Conditions and access controls
When This Happens (Condition) |
Then Do This (Access Control) |
|---|---|
Windows and macOS device owners are accessing SharePoint Online from an untrusted network. Additional security requirements are needed. |
Grant access to SharePoint Online for Windows and macOS devices. Require multi-factor authentication and a compliant device when accessed from an untrusted network. |
The sales team is accessing Exchange Online from their iOS and Android devices. These devices must be compliant before access is granted. |
Grant access to Exchange Online for the sales group. Require all sales team device owners to be enrolled in Intune and marked as compliant. |
All users are accessing Microsoft Teams from trusted and untrusted networks. Users that are on an untrusted network need additional security requirements. |
Grant access to Microsoft Teams for all users. Require multi-factor authentication when accessed from an untrusted network. |
BYOD devices are accessing Exchange Online from their browser. Access needs to be restricted to approved apps. |
Grant access to Exchange Online for all users. Restrict access to trusted client apps only. |
The following list covers prerequisites that you must be familiar with. Some of these are firm requirements and others are strategic questions to help prepare you for designing policies.
Subscriptions The basic capabilities of conditional access are available with an Azure AD premium subscription. There are additional capabilities, however, that will not be available until you upgrade your subscription. These include the following:
Azure AD Premium P1 The P1 subscription provides you with the basic capabilities of conditional access policies.
Azure AD Premium P2 The P2 subscription enables Identity Protection, which is required if you want to leverage sign-in risk. Sign-in risk is a capability that determines whether a user sign-in is malicious and measures the risk level. This can be leveraged as part of your policy conditions.
Microsoft Intune Intune can be purchased standalone or through an Enterprise Mobility + Security E3 or E5 subscription. Policy definitions that require a compliant device depend on the device being enrolled in Intune.
Need More Review? Subscription Details
For more information about Azure AD subscriptions, visit https://azure.microsoft.com/pricing/details/active-directory/. For more information about Microsoft Intune subscriptions, visit https://www.microsoft.com/cloud-platform/microsoft-intune-pricing.
Permissions Before you can start creating and managing conditional access policies, you will need the appropriate permissions assigned to your account. Conditional access administrator is a predefined role that that enables the necessary privileges.
Requirements to be delivered What requirements do you have for device compliance and conditional access? This is something you should start defining from the beginning. Determine whether your goal is something straightforward (such as enforcing multi-factor authentication for users) or something more advanced (such as restricting access to SharePoint Online from Windows devices when they are connected to an untrusted network).
Device management What kind of device-management solution are you using today? The full capabilities of conditional access have dependencies on Microsoft Intune, but if you are using ConfigMgr, you can enable co-management and start leveraging conditional access policies sooner.
Device platforms What types of devices and operating systems do you need to support? Conditional access policies support a variety of operating systems. At the time of this writing, the only current outliers are devices running Linux. Consider the devices in your environment and what types of restrictions you need to enforce.
Email requirements What are your access requirements around email? Email is often used as one of the first services for enforcing conditional access restrictions. If your goal is to enable access restrictions for Exchange Online, then selecting the cloud app from the default list of assignments is straightforward, and is something you will look at later in this chapter. If your goal is to enable access restrictions for an on-premises Exchange server, you must plan for additional prerequisites, such as installing and configuring the on-premises Exchange connector.
Design device-based and app-based conditional access policies
First, understand that a conditional access policy can contain any mixture of options, including device-based and app-based restrictions. The distinction between device-based and app-based restrictions is relative to the controls that you select and how you structure your policies. That said, device-based and app-based policies can have different requirements and can operate independently of each other if you choose.
Let’s look at a few examples:
Device-based This first policy focuses on device-based controls. Here, the policy requires multi-factor authentication on untrusted networks for iOS devices. The policy is assigned to all users. In this example we have not defined any app-based restrictions, keeping the focus on the platform and network.
App-based This second policy focuses on app-based controls. Here, the policy requires approved client apps when accessing Exchange Online. This policy is assigned to all users. In this example we have not defined any device-based restrictions, keeping the focus on application controls.
Mixed This third policy includes a mixture of controls. Here, the policy requires all platforms to be enrolled in Intune and marked compliant before they can access Exchange Online from approved client apps. In this example we are specifying device-based restrictions and app-based restrictions to accomplish the desired result.
At this stage you should have a good understanding of the differences between device-based and app-based policies. Next, let’s examine the individual controls related to each policy type. The following items are focused on device-based policy requirements:
Azure AD joined This requirement is available as both a condition and an access control item. When you are defining a condition, you have the option to exclude devices that are Azure AD joined. This is available through the Device State blade. You could use this in a scenario where you are locking down access, but want to ignore Azure AD–joined devices. Alternatively, when you are defining the controls for granting access, you have the option to require Azure AD–joined devices. This is available through the Grant blade for access control and can be used as one of many required controls before enabling access to cloud apps.
Device compliance This requirement is available as both a condition and an access control item, similar to the Azure AD–joined requirement mentioned in the previous bullet. Devices must be enrolled in Microsoft Intune and be marked as compliant for this requirement to work. When you are defining a condition, you have the option to exclude devices that are marked as compliant. This is available through the Device State blade. This could be used in a scenario where you are locking down access but want to ignore enrolled devices that are compliant. Alternatively, when you are defining the controls for granting access, you have the option to require enrolled and compliant devices. This is available through the Grant blade for access control and can be used as one of many required controls before enabling access to cloud apps.
Device enrollment This requirement is not directly defined through a conditional access policy but is a prerequisite for identifying device compliance.
Device platforms This requirement is available as a condition item. When you are defining a condition, you have the option to include or exclude the following operating systems: Android, iOS, Windows Phone, Windows, and macOS. This is available through the Device Platforms blade. It could be used in a scenario where you are restricting access to a cloud app and want to exclude certain platforms.
Next, let’s examine app-based requirements. We introduced session controls earlier in this skill section, which enable you to limit the experience within cloud apps. Two of the requirements we are going to cover are enabled using session controls. The following items are focused on app-based policy requirements.
Use app-enforced restrictions This requirement is available as an access control item. When you are defining access controls, you have the option to enable app-enforced restrictions. This is defined on the Session blade. It could be used in a scenario where you need to provide limited access to Office 365 Exchange Online or SharePoint Online for noncompliant devices.
Use conditional access app control This requirement is available as an access control item. When you are defining access controls, you have the option to enable conditional access app control. This is defined on the Session blade. It could be used in a scenario where you need to monitor and control application access in real time. Access and session policies can then be configured through the Cloud App Security portal, enabling granular control over user access.
Available policies These include access, activity, app discovery, app permission, cloud discovery anomaly detection, files, and session policies. Some of these are designed for monitoring and alerting, while others have automated actions that can be enabled.
Require approved client app This requirement is available as an access control item. When you are defining access controls, you have the option to enable the requirement for approved client apps. This is defined on the Grant blade. It can be used in a scenario where you need to ensure services are accessed only from approved client applications.
Note Approved Client Apps
Enabling the requirement for approved client apps will prevent users from accessing services from native or third-party apps that Microsoft has not approved. For a list of approved client apps, visit https://docs.microsoft.com/azure/active-directory/conditional-access/technical-reference#approved-client-app-requirement.
Plan for attack surface reduction
Reducing the attack surface is a method of reducing the number of vulnerabilities and threats the organization might be exposed to by using these devices. This section covers how to reduce the attack surface by using Intune to increase endpoint security. After you enroll Windows 10 (or later) devices in Intune, you can use endpoint security policies and Windows Defender’s antivirus software to configure device security settings and mitigate attacks.
Note
To use security policies in Intune to reduce the attack surface, you must be using Windows 10 or later as the device operating system, and the Windows Defender antivirus software must be the primary antivirus software on the device.
Endpoint security profiles
To reduce the attack surface of a device, you can use endpoint security profiles in Intune. When creating a new profile, the supported operating system is Windows 10 or later. The available profile settings are as follows:
App and Browser Isolation Isolating processes and applications on the device can prevent known and zero-day attacks. You can manage these settings with Windows Defender Application Guard with Defender for Endpoint by identifying the apps, websites, or networks that should be trusted.
Device Control This setting enables you to configure security settings for removable media on the device.
Attack Surface Reduction Rules This setting configures the available options in the Defender for Endpoint software on the device. This can include configuring rules and actions to take for downloaded executable files or suspicious scripts.
Exploit Protection This helps protect against malware that has been identified to use known exploits for the selected platform or device to prevent the malware from spreading.
Web Protection (Microsoft Edge Legacy) This setting enables you to protect against harmful websites that are phishing, using known exploits, distributing malware, and more.
Application Control These settings enable you to block unsigned scripts or installation files and restrict applications that can access the system kernel.
Configure endpoint security profiles
To create a policy that uses one of these available profile settings, follow these steps.
Log in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com.
Click Endpoint Security.
Under Manage, click Attack Surface Reduction.
Click Create Policy.
Select the platform and desired profile type. For this example, select Device Control.
Click Create.
On the Basics tab, type a name for the policy — for example, DeviceControlPolicy — and click Next.
On the Configuration Settings tab, configure the desired policy. For example, set Block Removable Storage and Block Bluetooth Connections to Yes. (See Figure 1-7.) Then click Next. Figure 1-7 shows these settings being configured.
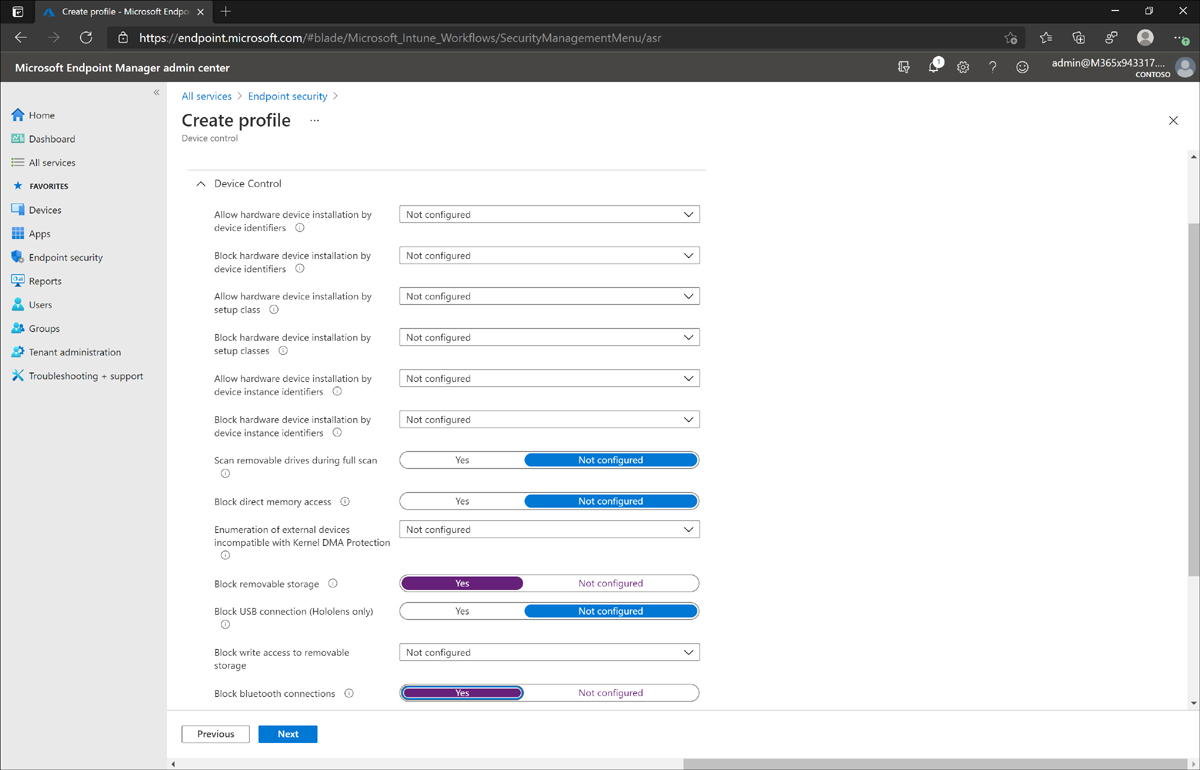
Figure 1-7 Endpoint security policy
On the Scope Tags tab, select any desired scope tags. For this example, leave the default (blank) settings as is and click Next.
Scope tags enable you to filter the policy to specific tags.
On the Assignments tab, configure the included or excluded groups that the policy should apply to. For this example, click Add All Devices and then click Next.
On the Review + Create tab, click Create.
Similar to the configuration profile you created in skill section 1.1, the endpoint security policy you create here will apply to the users or devices that you assigned it to in step 10.
After you create the policy, you can view its assignment status and properties by selecting it. Figure 1-8 displays the configured policy in the Microsoft Endpoint Manager admin center.

Figure 1-8 Configured and assigned endpoint security policy
Configure security baselines
This section introduces security baselines and how to configure them for Windows 10 devices that are managed by Intune. Security baselines provide a default configuration of settings or policies that are applied to a group of users or devices. For example, you can automatically assign a set of security policies for a publicly accessible kiosk machine. A different set of policies, or a baseline, can be configured for mobile devices carried by sales staff. The settings you configure for these devices might span multiple individual policies and are combined to create a baseline.
There are three types of security baseline instances that can be created and managed with Intune:
MDM security baseline This baseline enables you to configure any of the thousands of various settings that are available in Windows 10.
Microsoft Defender for Endpoint baseline This baseline is used specifically with Defender for Endpoint and configures the various settings included with Defender.
Microsoft Edge baseline This baseline configures settings that relate specifically to the Microsoft Edge web browser.
Baselines can and will change over time with the introduction of new features for the platform you are targeting or as best practices evolve. When one of these things happen, a new version is introduced to the baseline. You can also choose to change the version of a baseline on your own without the need to create a new profile.
Creating multiple versions or having multiple instances of a baseline can cause conflicts in settings. As your organization grows, or you simply have more baselines to manage, be aware of the conflicts that can arise by having different baselines for different devices.
You configure security baselines in the Microsoft Endpoint Manager admin center. Follow these steps:
Log in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com.
Click Endpoint Security, and then click Security Baselines.
Click the desired baseline instance to create a policy for — for example, Microsoft Edge Baseline.
Click Create Profile.
On the Basics tab, type a name for the policy — for example, BrowserBaseline — and then click Next.
On the Configuration Settings tab, configure the desired settings for the Microsoft Edge browser. For example, set the Enable Saving Passwords to the Password Manager setting to Enabled. Then click Next.
On the Scope Tags tab, set any filters based on scope tags to apply the profile to. Then click Next.
On the Assignments tab, select the devices or users to apply the baseline to. For example, click Add All Devices. Then click Next.
Click Create. Figure 1-9 shows the configured baseline policy with the Microsoft Edge settings defined.
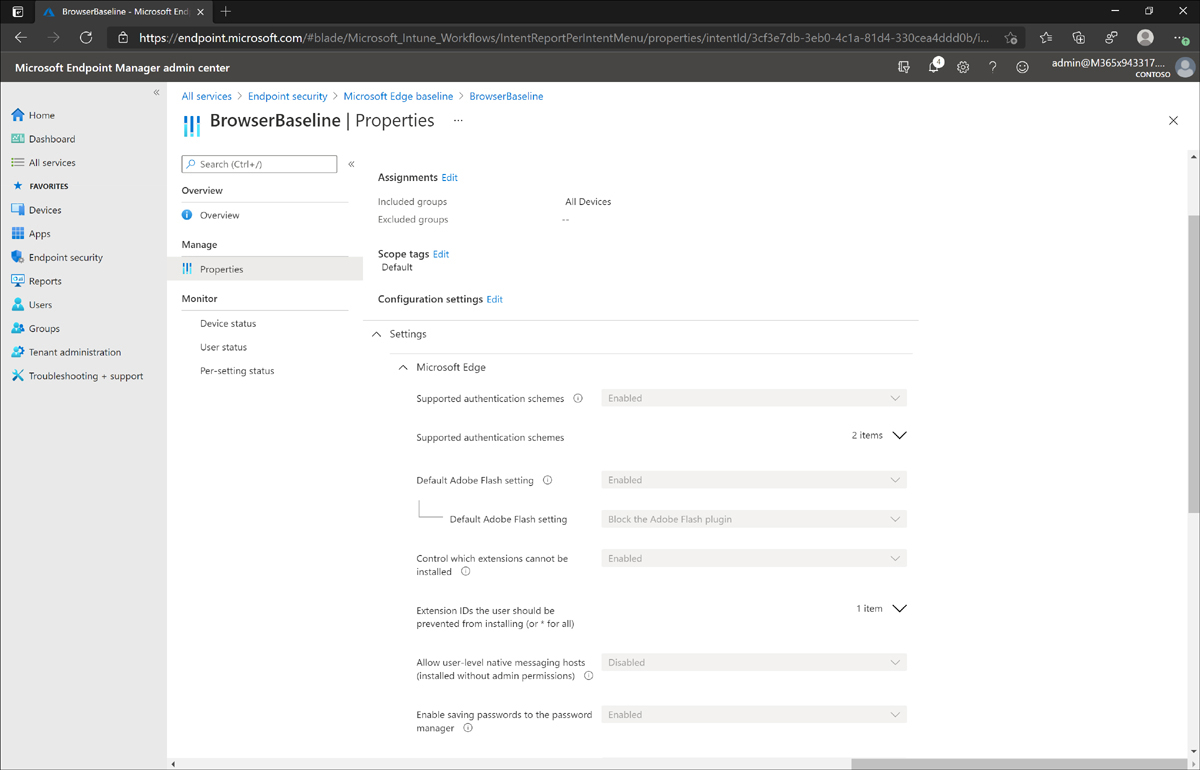
Figure 1-9 Security baseline for Microsoft Edge
Configure device-compliance policy
This section covers the creation process for device-compliance policies in Microsoft Intune. The examples cover common use cases for device compliance. Like the other policies and profiles you have explored so far, there are various options and configurations for administrators to work with. These include the ability to connect with third-party vendor solutions to enhance the native capabilities.
Note
As you navigate through the portal, remember that conditional access policies can leverage compliance status for restricting access to data and services.
Navigate and configure device-compliance settings
When you access the Device Compliance blade for the first time, the first thing you might notice is the number of options available compared to the conditional access interface. The core functions are split into three groups: manage, monitor, and setup.
Log in to the Microsoft Endpoint Manager admin center at https://endpoint.azure.com/.
Click Devices, and then click Compliance Policies.
Click Create Policy.
Select the desired platform for the policy to apply to, and then click Create.
On the Basics tab, provide a name for the policy, such as CompliancePolicy, and then click Next.
On the Compliance Settings tab, select the settings required for the device to be considered compliant, and then click Next. For example, choose Require for the Require BitLocker setting. Figure 1-10 shows the compliance settings to configure for Windows 10 device health.

Figure 1-10 Device-compliance policies
On the Actions for Noncompliance tab, select the action(s) to take if the device does not meet the settings defined on the previous tab, and then click Next.
For example, you can choose to send an email notification to the end user and other recipients or retire the device after a set period of time.
On the Assignments tab, add the users or groups that you want the policy to apply to. For example, click Add All Users. Then click Next.
Review your settings and then click Create.
Device compliance includes several built-in reports for administrators to review and export as needed. This includes an overview dashboard, providing a high-level look at overall compliance and areas of interest. Later in this section you will look at monitoring in more detail.
When you first begin working with device compliance, there are some configurations that you should review. In the Compliance Policies blade, click Compliance Policy Settings. There are three controls on this blade that you should explore before you begin creating policies.
Mark Devices with No Compliance Policy Assigned As [Compliant | Not Compliant] The default configuration for this setting is Not Compliant. In many cases, this will be the desired setting, because you will want to have some understanding of the device state before granting it access to services. For example, consider a scenario in which you assign a conditional access policy that requires devices to be compliant to access Exchange Online.
Enhanced Jailbreak Detection [Enabled | Disabled] The default configuration for this setting is Disabled. Enabling this feature requires iOS devices to evaluate and report their jailbreak status more frequently in conjunction with leveraging location services. Note that enabling this setting will affect the device’s battery life.
Compliance Status Validity Period (Days) [1–120] The default configuration for this setting is 30 days. This value determines the frequency with which devices must report back their device-compliance status to Intune. If a device does not report compliance within the required timeframe, it will be marked as noncompliant.
Each compliance policy you create is associated with a specific device platform, unlike conditional access policies, which enable you to select multiple platforms. Each platform has its own set of options. Some will be similar across platforms, but others will not. For example, macOS has a rule requiring system integrity protection, which is exclusive to this platform. Based on this, you should design your policies on a per-platform basis.
Skill 1.3: Plan for apps
Most organizations assume responsibility for a range of devices and apps. These must be maintained and supported to ensure that employees are productive, are successful, and have a healthy work-life balance.
There are common factors that organizations must consider when planning for devices:
The physical hardware and generation of that hardware
The operating system and version
Peripherals such as display adapters or printers
For apps, planning considerations may include:
Line-of-business (LOB) applications
Preferred publishers
Licensing
Version control
As you plan for devices and apps, you must also consider how these planning considerations will be distributed, configured, and supported.
For the MS-101 exam, planning for devices and apps is focused on testing your knowledge of the Microsoft 365 ecosystem and how these technologies solve different problems. This chapter focuses on device management and security. This includes a deep dive into device co-management and a look at device profiles and security with Microsoft Intune. App deployment, management of apps, and app security will also be covered.
Create and configure Microsoft Store for Business
The method in which applications are delivered to users and devices has evolved over the years. For traditional Win32 applications, some organizations may still have help desk staff who manage and install these apps manually. Others may be leveraging features like ConfigMgr’s application model, which offers a custom-tailored self-service method for employees to install traditional Win32 applications.
Another self-service app experience is available through the Microsoft Store. This service was introduced in Windows 8 as a standalone application that was installed with the operating system. At that time, it was referred to as the Windows Store. As with many other app store platforms, consumers can navigate the store and install apps that Microsoft had approved for publication. The apps in the Microsoft Store are not packaged in the traditional Win32 format. Instead, they are packaged using the Universal Windows Platform (UWP).
Enterprise and education customers have access to the Microsoft Store for Business (MSfB) or Microsoft Store for Education (MSfE), respectively. For this exam, we will focus on the MSfB, but the two stores provide parallel offerings. Administrators also have the option to configure a private store, enabling them to purchase apps in bulk, assign licenses, and deliver apps using self-service or direct assignment. This design has evolved with Windows 10 and is the focus here.
Plan for Microsoft Store for Business prerequisites
The MSfB is designed for organizations that want to take a modern approach to managing their application portfolio. Managing and delivering apps using this solution provides IT administrators with several capabilities. Table 1-4 contains a list of core features included with the MSfB.
Table 1-4 Microsoft Store for Business features
Feature |
Description |
|---|---|
Scaling flexibility |
The MSfB is a cloud-based technology, providing a robust and reliable infrastructure for hosting and distributing apps across different geolocations and org sizes. Customers that already have Azure AD, Office 365, and Windows 10 deployed can enable an end-to-end app-management solution using the MSfB. Customers that have an on-premises management solution can enable integration with the MSfB and begin modernizing their apps. |
Purchasing and licensing |
Administrators can procure apps and licensing in volume. Licenses can be assigned and reclaimed. |
Private store |
Administrators can enable a private store for their organization. This store can be customized with managed apps and collections, providing users with a tailored experience. The private store can be accessed from the Microsoft Store app on Windows 10 devices or from a web browser. |
App distribution |
Apps acquired through the MSfB can be distributed to users in multiple ways. For example, apps can be: Assigned to users or groups and made available through the private store for download and installation Distributed using ConfigMgr or third-party management solutions, or during image deployment Distributed offline without connecting to the MSfB using the Deployment Image Servicing and Management (DISM) command-line tool or provisioning packages |
Line-of-business apps |
Administrators can add LOB apps to the private store for management and distribution. |
App updates |
Apps that are purchased and managed online can receive automatic updates through the MSfB. |
As you begin planning for MSfB, there are a few prerequisites that you should be familiar with. First, you must understand the difference between the two available licensing models: online-licensed apps and offline-licensed apps. Which licensing model you choose can dictate which prerequisites you need to address.
Online-licensed apps Apps purchased using the online licensing model require users to connect to the Microsoft Store service to acquire the app and corresponding license. Licenses are maintained using the user’s Azure AD identity. This is the default license model, and it will be the primary option if your users have Azure AD accounts and if access to the Microsoft Store is enabled.
Offline-licensed apps Apps purchased using the offline licensing model do not require connectivity to the Microsoft Store. Instead, administrators can download their purchased apps and licenses for deployment within their internal network. Not all apps support offline licensing. It is up to the independent software vendor (ISV) to opt in for this option in the development center by selecting the Disconnected (Offline) Licensing setting during submission. Offline-licensed apps can be deployed at imaging time using a provisioning package or distributed to systems using a management solution such as ConfigMgr.
Next, let’s cover the baseline prerequisites for setting up MSfB. These are items you must plan for before you begin your implementation. Take note of the items that mention online and offline licensing requirements. These will differ slightly depending on which licensing model you choose.
Microsoft Store for Business account A global administrator must visit https://businessstore.microsoft.com and sign in to activate the private store.
Azure AD accounts for admins Administrators tasked with acquiring apps, distributing apps, and manage licensing need an Azure AD account. These requirements are the same for both online and offline licensing.
Azure AD accounts for users An Azure AD account is required for users who access the MSfB to download and install online-licensed apps. Users do not require an Azure AD account for offline-licensed apps.
Platform support Users accessing the MSfB must do so from a supported PC or mobile device. This includes Windows 10, version 1511, or later.
Browser support Administrators managing the MSfB must do so from a supported browser. MSfB is compatible with Internet Explorer 10 or later and current versions of Microsoft Edge, Chrome, or Firefox.
Set up the private store
The private store is designed to help organizations deliver a unified experience to their employees when browsing and installing apps. This feature enables administrators to customize their own private Microsoft Store and manage app purchasing and distribution. From a user-experience perspective, this includes the ability to adjust app visibility in the store based on user or group membership, along with grouping and sorting apps to your liking. Figure 1-11 shows an example of the Contoso Electronics private store. In this section, we will walk through the process of setting up a private store for MSfB.
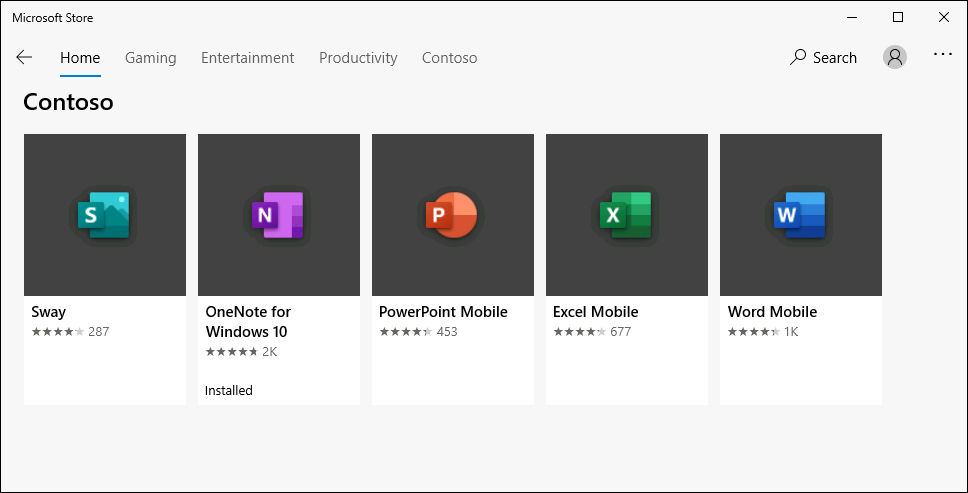
Figure 1-11 Contoso private store
For the following example, suppose you are an admin for Contoso Electronics. You have been tasked with creating a private store for your organization. Follow these steps to set up the private store:
Navigate to the Microsoft Store For Business at https://businessstore.microsoft.com.
Sign in using an Azure AD global administrator account.
Signing in without a global administrator account will only give you access to browse the standard Microsoft Store For Business.
In the menu bar at the top of the page, click the Private Store option. (See Figure 1-12.)
Figure 1-12 Microsoft Store for Business portal
If this option is not visible, maximize your browser window. Alternatively, locate the collapse menu button in the upper-left corner, click it, and select Private Store from the navigation menu.
A Microsoft Store for Business consent form opens.
The first time you try to manage the private store, you will be prompted to activate it. Click the Activate Private Store link (see Figure 1-13) to continue with the initial setup.
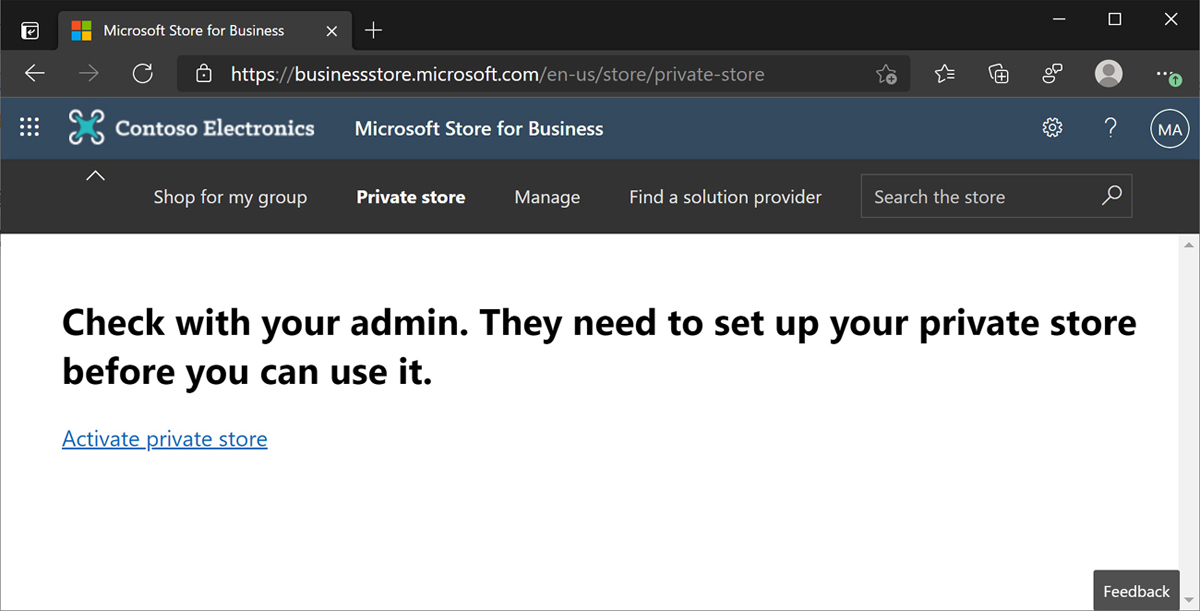
Figure 1-13 Microsoft Store for Business activation screen
Note First Time Sign-in
The first time you log in to the MSfB as a global administrator, most actions will trigger this first-time consent form. This time, you clicked the Private Store button to review the consent form; if you had clicked Find A Solution Provider, it would have triggered the same form.
The private store has now been created and is associated with your Azure AD tenant. Once this happens and the store becomes available, you can access the Manage menu, which contains several administrative options, which you will review in more detail in the next section.
At the time of this writing, if you click the Private Store option after accepting the consent form, you will see text that states: Check with your admin. They need to set up your private store before you can use it. This can be a bit confusing because the store has already been created. It turns out that before you can access the private store and see apps, you must accept a service agreement. You can do this by adding an app to your inventory.
Continuing with the Contoso Electronics scenario, register a free copy of the OneNote app to trigger and accept the pending service agreement.
In the menu bar at the top of the page, type OneNote in the search box and press Enter.
If the search box is not visible, maximize your browser window. Alternatively, locate the collapse menu button in the upper-left corner, click it, and enter your search term in the navigation menu.
In the search results, locate and click the free Microsoft OneNote app.
On the OneNote shop page, click Get the App.
Review the Microsoft Store for Business and Education Services Agreement, select the check box to accept the agreement, and click Accept. (See Figure 1-14.) This agreement is required to start using the private store.
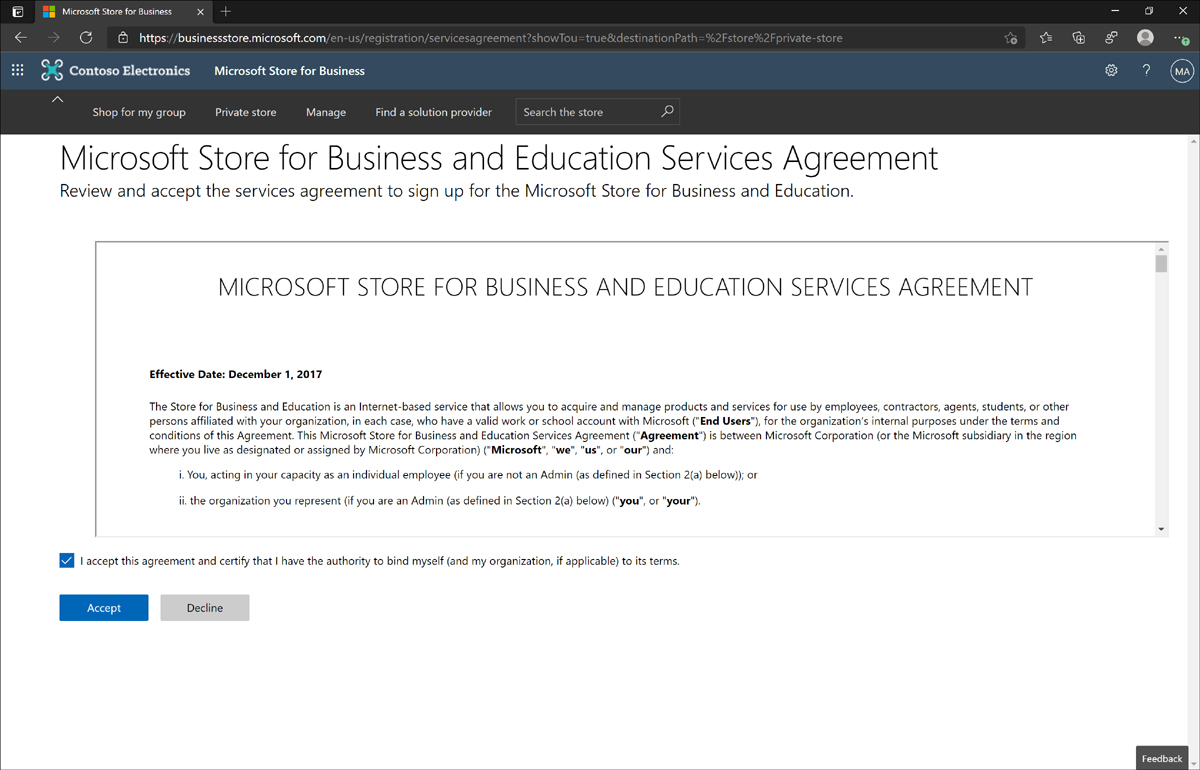
Figure 1-14 Microsoft Store for Business and Education Services Agreement
On the Thanks for Your Order page, click Close. This confirms that the app has been purchased and added to your app inventory.
Note Get New Apps
It may take as long as 24 hours for new apps you add to your inventory to become visible in the private store. In the preceding example, the OneNote app was visible in the private store within 5 minutes. This is worth noting if you are troubleshooting why a recently added app has not appeared in the private store yet.
At the conclusion of this scenario, the Private Store option on the menu bar will be replaced with the name of your organization (taken from your Azure tenant). When you click your organization name, you should see the OneNote app listed in your app inventory. At this stage, you can open the Microsoft Store on a compatible Windows 10 device, sign in with your Azure AD credentials, and access your organization’s private store.
Real World Only Show the Private Store
The private store can provide organizations with an end-to-end app-management solution. In some environments, once the private store is deployed, you might need to hide the default Microsoft Store. You can achieve this using group policy with the following setting: Only Display The Private Store within the Microsoft Store. For more information on configuring this policy setting, visit https://docs.microsoft.com/microsoft-store/manage-access-to-private-store#show-private-store-only-using-group-policy.
Configure Microsoft Store for Business
The management portal for MSfB contains several pages for app administration, licensing, and account management. Among these pages are a few controls to customize the private store. This section will introduce you to the portal and walk through each of the available menu options.
Figure 1-15 shows the MSfB management portal. To access this portal, you click the Manage button along the top of the screen. In this figure you see a navigation menu in the left pane, and the Overview page open on the right. The navigation menu contains the administrative controls for managing your organization’s MSfB experience. Let’s take a closer look at the available options in the navigation menu.
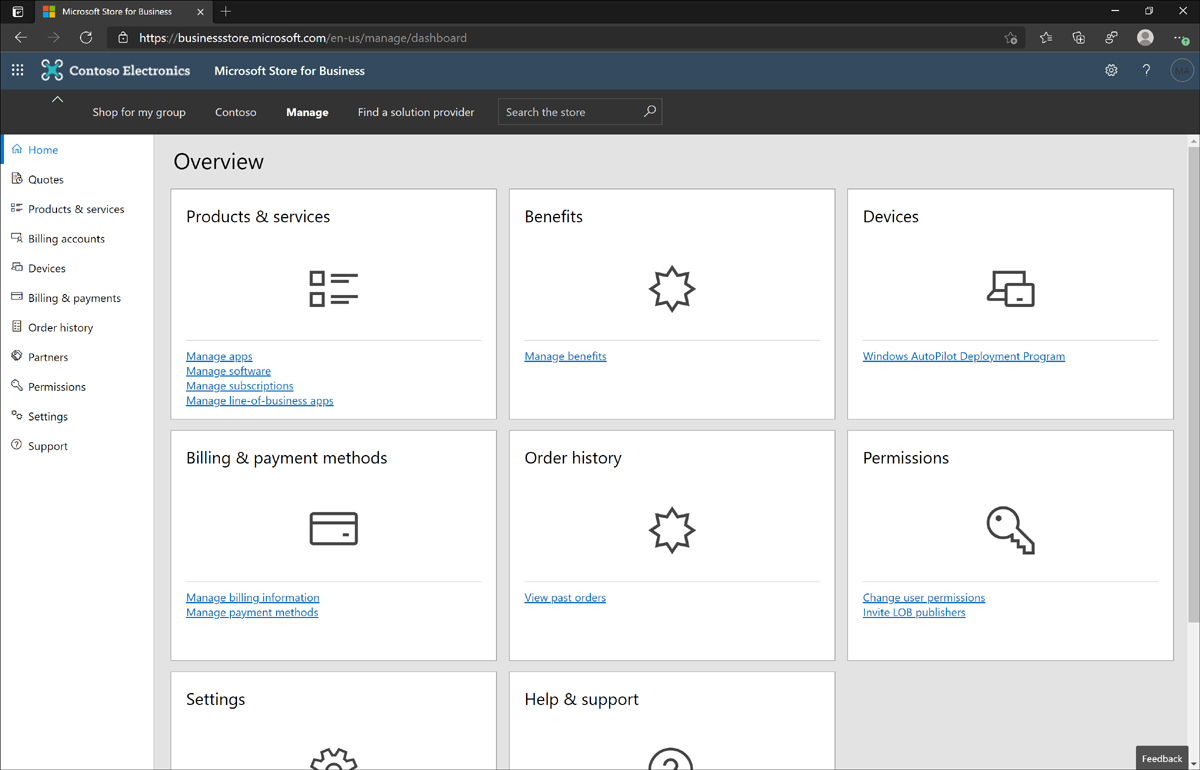
Figure 1-15 Microsoft Store for Business management portal
Home This directs you to a page that provides an overview dashboard with summary information for various items such as license availability and recent purchases. The overview also includes drill-down objects to other management options such as settings and permissions.
Quotes Use this page to view and interact with quotes that have been assigned to your organization for apps and other solutions. This page will be blank unless you have a partner that has sent you a quote.
Products & Services Use this page to view your app inventory, benefits information, and new LOB apps. App inventory will include all registered apps for your organization along with drill-down details and customization options for each app. Benefits information is tied to your Microsoft agreement. LOB apps are any newly registered LOB apps assigned to your organization.
Benefits Use this page to view account profile information, status information for your Microsoft agreements, connected tenants that you established with the Microsoft Products and Services Agreement (MSPA), and review requests that require admin approval.
Devices Use this page to manage your Windows AutoPilot deployments. AutoPilot is a technology that enables administrators to reduce traditional imaging needs by configuring automated system setup and configuration with Azure AD, Intune, Office 365, and MSfB.
Billing & Payments Use this page to view invoices assigned to your organization and manage your account payment methods.
Order History Use this page to view your order history and order details for software and subscriptions purchased by your organization.
Partners Use this page to view the list of partners assigned to your organization. Partners are available to help organizations purchase and manage products and services. You can search for partner details by navigating to the Find a Solution Provider menu option.
Permissions Use this page to view and manage the role-based access controls for your organization. This includes roles for admin, purchaser, basic purchaser, and device guard signer. Once your private store is active, it is important to review the default options and define the roles according to your business needs.
Settings Use this page to view and manage the core settings for your organization’s store experience. This includes shopping controls based on role-based access, distribution settings, and connectivity to your preferred MDM solution, device guard policies, and notification controls for invoices.
Support Use this page to access support information about MSfB and opening support requests.
Now that you have a better understanding of the management portal, let’s look at some customization controls for the private store. There are two primary locations that contain settings pertaining to the private store. The first is the private store itself, which is listed in the menu bar as the name of your organization. In this example, the private store is called Contoso Electronics. Click this link to access the store interface, shown in Figure 1-16.

Figure 1-16 Microsoft Store for Business private store
This page enables administrators to customize the store interface for their employees. The changes you make here will be visible to employees when they access your organization’s private store. Available options include the ability to create new collections by clicking the +Add Collection button. You can also remove collections and assign apps to collections by clicking the more options icon (•••) next to the collection name.
In this example, the default collection, Contoso Electronics, which contains all available apps by default, is hidden. To replace this collection, we created two new collections: Contoso (shown in Figure 1-16) and File Sharing (not shown). These new collections contain a custom list of apps based on our preference.
To access the second location for customizing the private store, open the Manage page, click the Products & Services tile, and then click the Apps & Software tab. On this page, you will see a list of apps from your inventory, as shown in Figure 1-17.
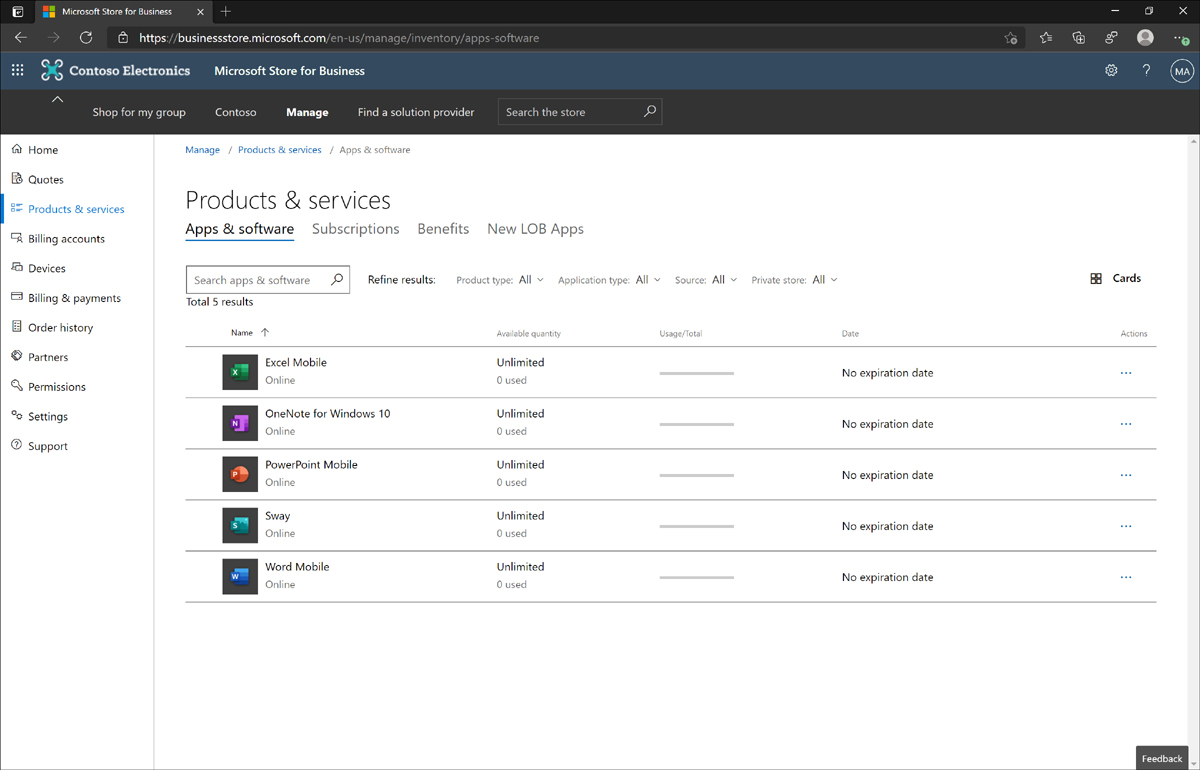
Figure 1-17 Private store availability
Plan app deployment
In this section, you will work with app deployment in the cloud. App deployment with Microsoft 365 is centralized around cloud-based management. Traditional solutions for on-premises app deployment are still available, but working with apps in the cloud is the focus for this exam.
The two major technologies that we will be focusing on are MSfB and Microsoft Intune. These technologies can operate independently, but are designed to be integrated for end-to-end coverage. For example, MSfB standalone can offer a suitable solution for Windows 10 devices, but if you need to distribute apps to iOS and Android, then integrating Intune makes sense.
Plan for app deployment prerequisites
There are a few different ways to deploy apps in the Microsoft cloud. The prerequisites for these methods depend on the requirements of the organization. For example, if your organization uses Office 365 but does not have an Intune subscription, you can still use the MSfB to help manage apps on Windows 10 devices. If your organization does have an Intune subscription, you can set up an MSfB account and integrate it with Intune to streamline the management and distribution of your apps across multiple platforms.
Based on the examples described previously, many prerequisites for app deployment are conditional. That said, you should be familiar with each of the available options and in what situations they apply:
Microsoft Store for Business Standalone If you choose to leverage the benefits of MSfB, your organization must have an active MSfB account.
Microsoft Store for Business + Intune If you plan to connect your MSfB account with Intune, you must activate Microsoft Intune. You can do this from the Intune portal; choose Manage, select Settings, select Distribute, and then choose Management Tools.
Microsoft Intune If you choose to leverage Intune for app management and distribution, your organization must have an active Intune subscription. This includes setting the MDM authority to Intune in the Azure portal.
Device Enrollment If you plan to require app installation on devices, those devices must be enrolled with Intune.
Supported Platforms MSfB supports Windows 10 devices. If you need to support other platforms, such as Android or iOS, you must consider an Intune subscription.
Supported App Types MSfB supports the conversion of multiple Windows app file formats into APPX bundles for distribution. This conversion process requires an install sequence and capture of the app. Intune has a conversion process that converts the installer to a compatible INTUNEWIN bundle. The Intune solution is in preview at the time of this writing. Both scenarios should be planned for if you have a requirement to deploy Win32 apps.
Plan for app deployment types
This section covers planning considerations for app deployment types. This refers to the various app deployment types that Microsoft Intune supports. In the management portal, administrators have access to a variety of app types that they can deploy to users and devices.
One of the first things to consider when planning your app-management model is file formats. An app’s file format can vary by publisher and platform. Variations by publisher exist only for Windows apps, where you have traditional file formats such as EXE and MSI, and newer formats such as APPX and MSIX. This segmentation adds a lot of effort for IT admins that support a variety of apps. Variations by platform includes Android, iOS, and Windows. Modern and mobile apps are all platform-specific and must be considered.
Next, you should know which app-deployment types are available in Intune, and what options they provide. For this, you will open the management portal and look at the client apps.
Log in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com/.
Click Apps.
On the Apps blade, click All Apps.
On the All Aps blade, click Add.
On the Add App blade, review the list of available app types. See Table 1-5 for a breakdown of each app type and its capabilities.
Table 1-5 Client app types
Platform |
App Type |
Notes |
|---|---|---|
Android, iOS, Windows, Managed Google Play |
Store app |
All store apps require an app store URL that directs the app to the appropriate provider. With MSfB integration, Microsoft Store apps are automatically synchronized with Intune every 24 hours. |
Windows 10, macOS |
M365 apps, Microsoft Edge v77 and later |
Microsoft 365 apps can be bundled as a suite or created as standalone apps. Additional configuration options are available for architecture type, update channel, removal of previous MSI versions, automatic agreement acceptance, and shared computer activation. |
macOS |
Microsoft Defender for Endpoint |
Manage app deployment for macOS when using the Microsoft Defender for Endpoint on an Apple macOS device. |
Web link |
Other |
Web links enable you to create an app that launches a browser to a specific URL, such as your help desk portal. |
Built-in app |
Other |
Built-in apps enable you to quickly distribute curated managed apps, such as Office 365 and Adobe Reader for iOS and Android. |
Line-of-business (LOB) app |
Other |
Line-of-business (LOB) apps enable you to upload in-house apps. Accepted file formats include MSI, MSIX, MSIXBUNDLE, APPX, and APPXBUNDLE. |
Windows app (Win32) (preview) |
Other |
Win32 app enables you to upload a repackaged application using the INTUNEWIN file format. At the time of this writing, this feature is in preview. |
Android Enterprise system app |
Other |
Android Enterprise system apps allow you to enable or disable certain system applications for Android devices that are managed by an enterprise. |
Create and deploy apps with Intune
This section walks through the app-creation process in Intune and covers how to deploy those apps to enrolled devices. Intune’s app-deployment capabilities continue to evolve, with recent additions including Win32 app support. These are some notable milestones for the product because Win32 app support breaks the barrier from traditional on-premises app management requirements with new cloud capabilities.
Manage Store Apps with Intune
Before you start working with apps in Intune, remember that you can synchronize Microsoft Store apps. Enabling this capability will simplify the management of Microsoft Store apps and provide you the ability to deploy them using Intune.
Navigate to the Microsoft Store for Business at https://www.microsoft.com/business-store.
Sign in using an Azure AD account with admin access.
On the menu bar at the top of the page, click Manage.
Click Settings in the navigation menu on the left.
On the Settings page, select the Distribute tab.
On the Distribute tab, under Management Tools, click Activate in the Action column for the Microsoft Intune and Microsoft Intune Enrollment settings, as shown in Figure 1-18.
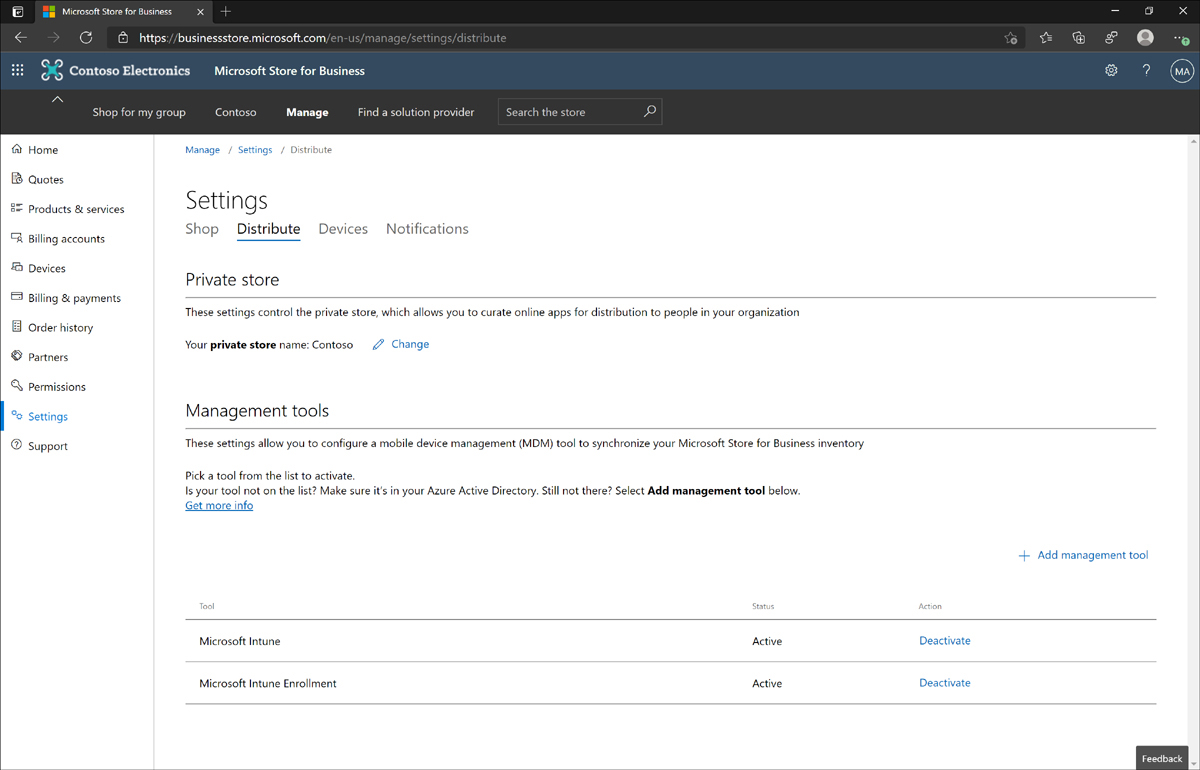
Figure 1-18 Microsoft Store for Business management tools
Create apps in Intune
We covered app deployment types earlier in this skill. This is one of the first options that you configure when creating apps in Intune. From there, you can begin adding apps to your Intune library. In this section, you will add an Office 365 app to your Intune app library. This will introduce you to the app-creation process and help you get comfortable with the portal.
Log in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com/.
Click Apps, and then click All Apps.
On the All Apps blade, click Add in the menu.
On the Add Microsoft 365 Apps blade, select Windows 10 under the Office 365 Suite app type, and then click Next.
In the App Suite Information tab, fill in the following values and then click Next:
Suite Name Type a name for the app. This name should be unique to prevent conflicts in the company portal. This is a required field.
Suite Description Type a description for the app. This is a required field.
Publisher This field is prepopulated for Office 365 apps. For apps where the field is not populated, enter a publisher for the app.
Category This field is optional. There are nine categories to choose from, and you can select as many as you want. Assigning a category enables users to filter apps more easily. Office 365 apps default to the Productivity category.
Display This as a Featured App in the Company Portal This toggle specifies whether the app will appear on the main page of the company portal. Set the toggle to Yes.
Note
The company portal is used by employees to access and install apps. It can be accessed from the Microsoft Store app or by visiting https://portal.manage.microsoft.com/.
Information URL This field is optional. You can enter a web address that contains information about the app. For this example, leave this field blank.
Privacy URL This field is optional. You can enter a web address that contains privacy information about the app. Leave this field blank.
Developer This field is optional. It is prepopulated for Office 365 apps.
Owner This field is optional. It is prepopulated for Office 365 apps.
Notes This field is optional. Leave this field blank.
Logo This field is optional. It is prepopulated for Office 365 apps.
On the Configure App Suite tab, open the Select Office Apps drop-down list in the Configure App Suite section. You will see a list of all the available products in the Microsoft 365 suite.
Select the check box next to each of the following products (see Figure 1-19):
Excel
OneDrive
OneNote
Outlook
PowerPoint
Teams
Word
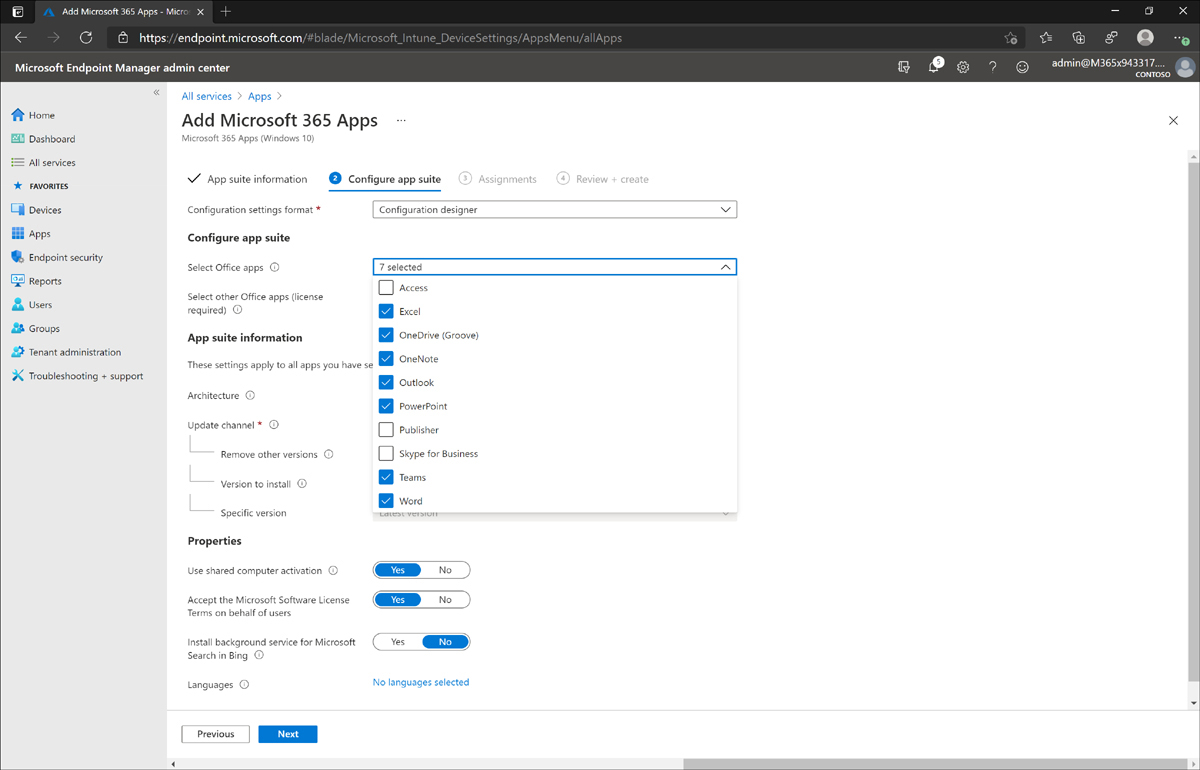
Figure 1-19 Office 365 app suite configuration
The Configure App Suite tab also includes information pertaining to app metadata, such as the app’s name and description. Because this is an Office 365 app, some fields are prepopulated, such as the publisher and app icon.
In the App Suite Information section of the Configure App Suite tab, fill in the following values and leave other values at their default setting. (See Figure 1-20.) Then click Next.
Architecture 64-bit
Update Channel Monthly (Targeted)
Remove Other Versions Yes
Version to Install Latest
Specific Version Latest Version
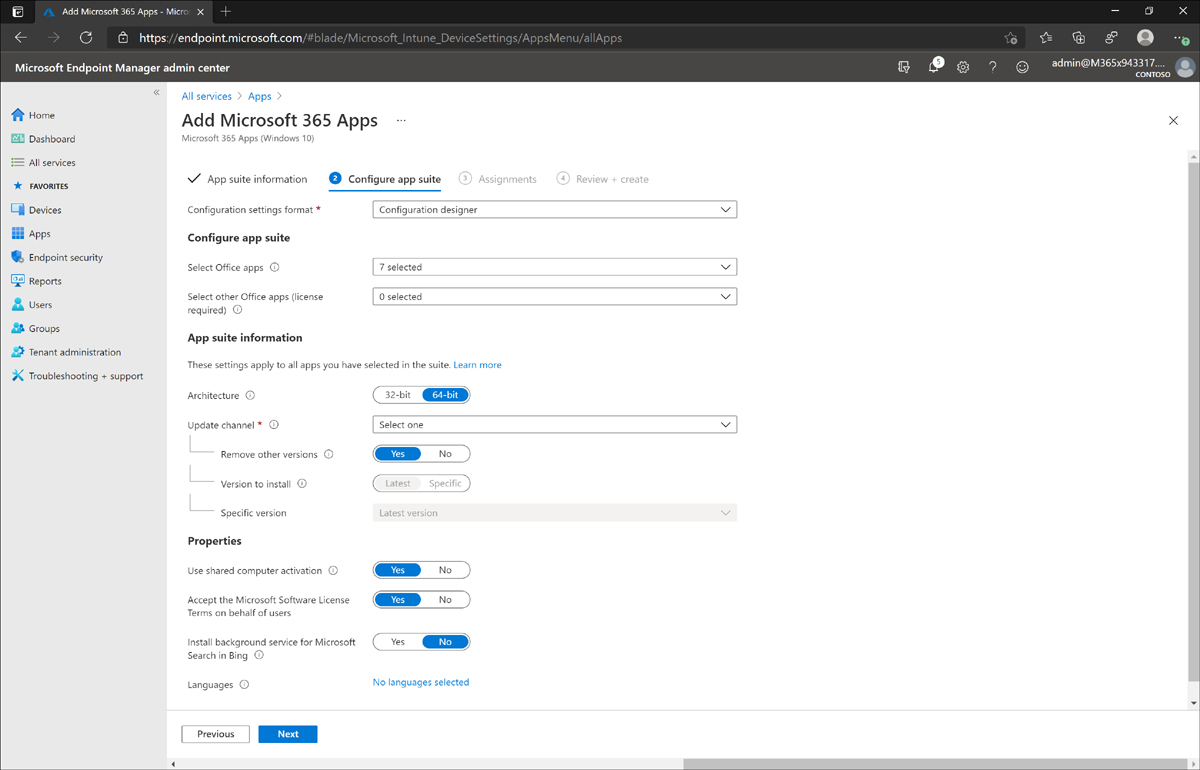
Figure 1-20 Office 365 app suite information
In the Properties section of the Configure App Suite tab, fill in the following values, leave the other values at their default setting, and click Next. (Refer to Figure 1-20.)
Use Shared Computer Activation Yes
Accept the Microsoft Software License Terms on Behalf of Users Yes
Languages No changes
On the Assignments tab, choose whether to make the device available to specific users, devices, or groups, and then click Next.
On the Review + Create tab, click Create.
With these steps complete, you should have the new Office 365 Suite app listed on the Client Apps – Apps blade alongside the MSfB apps you saw earlier in this skill section.
Assign apps in Intune
You can assign apps that are present in your Intune app library to groups of users and devices for install or uninstall. When you create a new app assignment, you are given three assignment types to choose from:
Available for enrolled devices Makes the app available to devices that are enrolled in Intune.
Required Forces the app to install on the targeted group of users or devices.
Uninstall Forces the app to be uninstalled from the targeted group of users or devices.
In the following example, you will assign the Office 365 Suite app to various Contoso Electronics groups and configure the app to be required for all devices.
Log in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com/.
Click Apps and then click All Apps.
Locate the Microsoft 365 apps for Windows 10 app and select it.
On the app page, click Properties.
On the Properties page, next to Assignments, click Edit.
On the Assignments blade, select the groups to add the assignment to, and then click Review + Save.
Plan for mobile application management
This section covers planning considerations for application management on mobile devices. Application management refers to the protection of company data within an application. For example, suppose a user opens an email containing confidential information from their corporate account using Microsoft Outlook for Android. You can use application management to prevent the user from copying data from the email and pasting it into another application. For the exam, you must be comfortable with creating and assigning these policies.
Plan for app protection prerequisites
The capability to manage the data within an application has evolved over the years. Microsoft’s solution for this is called app protection policies. This is a feature available with Microsoft Intune.
In the past, application management required the management of the device running the app. With app protection policies, the policy is assigned to the user. This alleviates the need for devices to be enrolled in an MDM. Instead, the user signs in to the app with their Azure AD account and the necessary policies get applied.
The following list covers the basic prerequisites for deploying app protection policies in an organization:
Azure AD subscription A basic Azure AD subscription is required to establish Azure AD accounts.
Intune subscription App protection policies are a capability of Microsoft Intune. You need an Intune subscription to create and manage these policies. In addition, users to whom these policies are assigned require an Intune license.
Office 365 subscription App protection policies assigned to Office 365 mobile apps require users to have an Office 365 license assigned to their Azure AD account.
Azure AD account Users must have an Azure AD account.
Supported platforms App protection policies are supported for iOS, Android, and Windows 10.
Security groups App protection policies are assigned to Azure AD security groups that contain user objects. You must create the desired groups in Azure AD or synchronize your existing on-premises groups using Azure AD Connect.
Supported apps App protection policies are not available for all apps. The app must support the Intune SDK features that enable app management.
Configure app protection policies
In this section you will create an app protection policy and assign it to a group of users. A common scenario that you may be presented with is app management for Office 365. These are often the core productivity apps for users, and company data is an important aspect to consider.
In the following example, you are going to create an app protection policy for the Contoso Electronics sales team. These users travel often and use a mixture of corporate and personal mobile devices to access company resources. The app protection policy will control data for each of the core Office 365 mobile apps.
Log in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com/.
Click Apps.
Under Policy, click App Protection Policies.
On the App Protection Policies blade, click Create Policy, and then click Android.
On the Basics tab, fill in the following information:
Name APP for Android
Description APP for Office 365 apps on Android
Platform Android
Target To All App Types Yes
On the Apps tab, select the following apps and click Next:
Excel
OneNote
Outlook
PowerPoint
Word
On the Data Protection tab (see Figure 1-21), select the following options and click Next.
Backup Org Data to Android Backup Services Block
Send Org Data to Other Apps Policy Managed Apps
Receive Data from Other Apps Policy Managed Apps
Save Copies of Org Data Block
Allow User to Save Copies to Selected Services OneDrive For Business
Restrict Cut, Copy, And Paste Between Other Apps Policy Managed Apps
Screen Capture and Google Assistant Disable
Encrypt Org Data Require
Encrypt Org Data on Enrolled Devices Require
Sync App with Native Contacts App Disable
Printing Org Data Disable
Share Web Content with Policy Managed Browsers Require
Figure 1-21 App protection policy Data Protection tab
On the Access Requirements tab (see Figure 1-22), select the following options and click OK.
PIN for Access Require
PIN Type Numeric
Simple PIN Block
Select Minimum PIN Length 6
Fingerprint Instead Of PIN For Access (Android 6.0+) Allow
Override Fingerprint with PIN After Timeout Require
Timeout (Minutes of Inactivity) 30
App PIN When Device PIN Is Set Require
Work or School Account Credentials for Access Require
Recheck the Access Requirements After (Minutes of Inactivity) 30
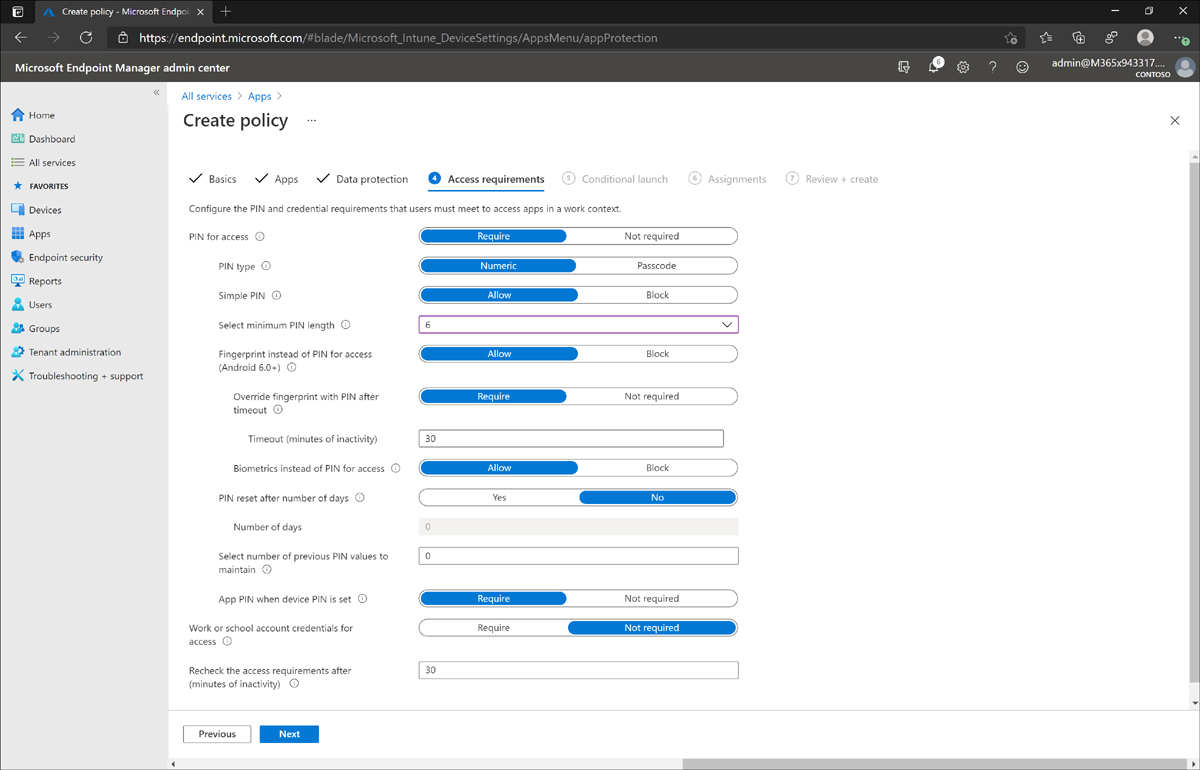
Figure 1-22 App protection policy Access Requirements tab
On the Conditional Launch tab (see Figure 1-23), review the default options and click OK.

Figure 1-23 App protection policy Conditional Launch tab
Conditional launch enforces periodic checks to ensure that app protection policies are up to date and compliant. There are seven available settings:
Max PIN Attempts If a user enters their PIN incorrectly more than the defined number of times, the user can be forced to reset their PIN or the app data can be wiped.
Offline Grace Period If the managed app does not check in for a defined period, access to the app can be blocked or the app data can be wiped.
Jailbroken/Rooted Devices If the device has been jailbroken or rooted, access to the app can be blocked or the app data can be wiped.
Min OS Version If the device OS does not meet the minimum version, the user can be warned, access to the app can be blocked, or the app data can be wiped.
Min App Version If the app does not meet the minimum version, the user can be warned, access to the app can be blocked, or the app data can be wiped.
Min Patch Version If the device OS does not meet the minimum patch version, the user can be warned, access to the app can be blocked, or the app data can be wiped.
Device Manufacturer(s) If the device is not made by the specified manufacturer, access to the app can be blocked or the app data can be wiped.
On the Add a Policy blade, click Create.
On the Client Apps – App Protection Policies blade, select the APP for Android policy.
On the Intune App Protection blade, under Manage, click Assignments.
On the Intune App Protection – Assignments blade, on the Include tab, click Select Groups to Include.
Select the Contoso Electronics Sales group and click Select.
After completing these steps, you should have a new app protection policy created and deployed. You can review the check-in information for users that access this app by navigating to the APP For Android setting and selecting Overview. This tab provides insight into how many users are accessing the associated apps and the check-in count for each app in the policy.
Skill 1.4: Plan Windows 10 deployment
In 2015, Microsoft released Windows 10, an operating system that would completely shift the industry and the way in which enterprises managed and supported Windows. In the past, you could expect a new version of Windows every three to five years, and the support lifecycle for those versions would overlap by a good margin. Organizations had very little pressure to quickly adopt the next major release. They could wait 12 months for major issues to be addressed, and then spend an additional 12 to 18 months testing and deploying the next release of Windows.
Windows 10 has evolved greatly since its introduction. The current version of the popular client operating system is delivered to customers as a service, meaning that instead of waiting three to five years for new features or intermittent service packs, Microsoft deploys a major feature update every six months. These feature updates introduce new capabilities, security enhancements, bug fixes, and much more. In addition, the support lifecycle for Windows 10 releases is shorter than previous versions of Windows. This encourages organizations to stay current with Windows 10.
This skill section covers Windows 10 in depth. This includes planning considerations around Windows as a service (WaaS), a term you should become very familiar with. It walks through the various deployment methods for Windows 10 and looks at the pros and cons for each. It also covers upgrade readiness, a service that helps customers prepare for Windows 10 and maintain compatibility. Finally, it looks at the various security features introduced with Windows 10, which represent one of the major benefits of adopting and staying current with Windows 10.
Plan for Windows as a service (WaaS)
IT organizations that have delivered and supported earlier versions of Windows will experience some significant changes when they adopt Windows 10. Although upgrading to Windows 10 (moving from Windows 7 to Windows 10, for example) shares a lot of similarities with previous upgrades, once your fleet of devices is running Windows 10, you must establish guiding principles for supporting upcoming feature updates, such as hardware, driver, and application compatibility.
This section introduces the core components and services of WaaS. This includes a closer look at servicing channels, which determine your feature update deployment cycle. It also covers Windows Insider for Business. This is a program based on Windows Insider that provides organizations with a centralized approach for testing and providing feedback.
Identify the core components for WaaS
The term as a service (aaS) reflects a transformation in the way digital services are provided to customers. Some common examples of this model include software as a service (SaaS) and infrastructure as a service (IaaS). Both examples are built on cloud-based technologies. Customers now have the option to purchase Microsoft Office as a subscription (SaaS), providing frequent updates and new capabilities every month. Landing servers in your local data center may not be realistic when you can move those servers to the cloud (IaaS) and reduce on-premises support and maintenance.
With Windows 10, Microsoft introduced Windows as a service (WaaS). The idea behind WaaS is that customers no longer buy a new version of Windows every three to five years. Instead, you purchase Windows 10 and receive frequent updates and features.
Moving Windows to a semi-annual release schedule enabled Microsoft to make some foundational changes in how the operating system would be serviced moving forward. As part of that transformation, the company introduced new components in Windows 10 to support the WaaS model. Each of the following is a key component of WaaS and relates to how you will manage Windows 10.
Feature updates These updates deliver new functionality to the operating system. Feature updates are a core design change in Windows 10 and are a foundation of WaaS. Microsoft delivers these updates twice a year, once in the fall and one in the spring. From a deployment perspective, these updates are designed to be installed in place, over the existing version of Windows 10. Users can expect to retain all their data and applications during the upgrade process. Microsoft has also introduced several tools to help administrators deliver these updates. We will be reviewing each of these tools in this skill section.
Quality updates These updates deliver security and reliability fixes to the operating system. Quality updates redefine the way administrators manage patching for Windows devices. Before Windows 10, Microsoft released a variety of individual updates on “patch Tuesday.” In managed environments, administrators could then choose which updates to install. For example, some organizations might only install critical security updates each month or completely miss an important update from a previous month. This resulted in fragmented patch levels and reliability issues. Quality updates help address these problems. They are cumulative, meaning the patch content from the previous month is automatically rolled into the next month’s update. They are also condensed, reducing the number of individual updates you need to deploy and manage. For example, instead of six individual security updates for August, you have a single quality update.
Servicing channels Servicing channels are the management controls used to determine which release of Windows 10 is deployed and when. Feature updates can be delivered using management solutions such as ConfigMgr, but they can also be delivered through Windows Update. Administrators must consider how they want to manage these updates and how frequently they want them installed.
Deployment rings Deployment rings are used to roll out Windows 10 feature updates in stages. A ring contains a collection of devices that you determine are ready for the upgrade. You might have a ring for pilot devices and a ring for production. These rings can also directly relate to different management solutions and deployment scenarios such as ConfigMgr with Windows 10 Servicing or Intune with Windows 10 Update Rings.
Windows Insider The Windows Insider program was originally delivered in parallel with the first release of Windows 10. Customers were given the opportunity to join this program and test pre-release features. Participants had access to a feedback mechanism where they could share ideas and bugs. For enterprise customers, Windows Insider for Business was introduced to make enrollment easier.
Plan for servicing channels
We touched briefly on servicing channels in the last section. This section covers servicing channels in detail.
First, it is worth noting that the terminology for servicing channels has changed since their introduction. This was done to help align the update terminology between Windows 10 and Office 365. Earlier naming standards used branch identifiers — for example, Current Branch (CB), Current Branch for Business, and Long-Term Servicing Branch (LTSB). LTSB is still associated with some early editions of Windows Enterprise, but all other components are now referred to as servicing channels.
Servicing channels are broken down into three different types, each delivering a different service. As an administrator, it is your responsibility to identify and deploy the appropriate servicing channel based on the needs of your organization.
Insider program With Windows 10, Microsoft has encouraged customers to start their testing early. Windows Insider delivers a servicing channel that enables customers to enroll their devices and begin testing new features and capabilities before they are released to the general public. This enables business customers to start compatibility testing earlier. Members of the Insider program also have a direct feedback link through the Feedback Hub application. The Insider program supports three deployment rings:
Fast ring Members of this ring are the first to receive new features and changes. These enhancements are validated on a small population of devices before they become available to the fast ring. Customers should expect possible issues and blockers when enrolled in this ring.
Slow ring Members of this ring receive Insider builds after members of the fast ring. These builds include updates and fixes for issues identified by fast ring members. There is still a risk that these builds could experience issues, but in general, they are more stable.
Release preview ring Members of this ring receive a release preview Insider build in advance of general availability. This enables organizations to start piloting the next release of Windows 10 with minimal risk while still having the ability to provide feedback.
Semi-annual channel After a new feature update is released to the general public, it enters the semi-annual channel. At this point, administrators can begin managing how these updates are delivered to their production devices. There are two deployment rings for this servicing channel.
Semi-annual channel (targeted) Newly released updates will enter this deployment ring first. Customers who choose this ring will receive the latest feature update, with the option to defer up to 365 days.
Semi-annual channel After a period of time, usually about four months, feature updates are moved to the semi-annual channel deployment ring. This provides organizations with another option for postponing their rollout in addition to the 365-day deferral rules.
Long-term servicing channel Customers with specialized systems running Windows 10, such as medical equipment or heavy machinery, can leverage the long-term servicing channel to prevent the deployment of feature updates and receive extended support. Unlike with the semi-annual channel, administrators must install the LTSB edition of Windows 10 Enterprise. There is no configuration option to quickly switch between the long-term servicing channel and semi-annual channel. Administrators must re-image devices if they need to make this change. Also, the long-term servicing channel is not designed for systems that are used for productivity or content creation. Devices running Office should not be using the long-term servicing channel.
Each servicing channel also has a different release cadence and support lifecycle. See Table 1-6 for these details.
Table 1-6 Servicing channel support
Servicing Channel |
New Releases |
End of Support |
|---|---|---|
Insider program – fast ring |
Weekly |
It varies from release to release, but all Insider builds will eventually expire if you do not stay current. |
Insider program - slow ring |
Monthly |
It varies from release to release, but all Insider builds will eventually expire if you do not stay current. |
Semi-annual channel |
Every six months |
Fall releases have 30 months of support. Spring releases have 18 months of support. |
Long-term servicing channel |
Every two to three years |
Up to 10 years of support. |
Plan for Windows Insider for Business
Windows Insider delivers pre-release builds of Windows 10 to customers that enroll in the Insider program. Once enrolled, your device will start receiving Insider builds. As a participant, you get to try new features and capabilities before they are released. The Insider build also includes a dedicated channel for reporting issues or general feedback to the Windows development team. Through this program Microsoft can collect real-world data from a vast range of users and devices. This data helps address issues and improve Windows before an update is released to the general public.
After joining the Insider program, you enroll your existing Windows 10 device by navigating to the Windows Insider Program Settings page, shown in Figure 1-24. From there, click Get Started and enter your account credentials.

Figure 1-24 Windows Insider Program Settings page
Windows Insider for Business is the same Insider program that we just reviewed, but with some extra controls to help organizations manage their enrolled users and devices. These controls include:
Domain registration Customers that are synced with Azure Active Directory (Azure AD) can register their tenant with the Windows Insider program. This enables employees to sign in with their Azure AD credentials.
Track feedback The feedback submitted through the Feedback Hub is tagged with the corresponding user’s Azure AD account. This feedback can then be tracked for internal analysis and data collection.
You can register your domain with the Windows Insider program by following these steps:
Navigate to the Windows Insider registration page at https://insider.windows.com/en-us/register.
Sign in with your Azure AD account and confirm you have access to complete the registration.
Confirmation is shown at the top of the page under Register Your Domain with the Windows Insider Program.
Your account must meet the following requirements. If these requirements are met, you will see a message prompting you to register your domain, as shown in Figure 1-25.

Figure 1-25 Windows Insider for Business sign-in confirmation
Assigned the global administrator role in Azure AD
Existing participant of the Windows Insider program
On the Manage Insider Preview Builds page, click the Register link.
On the Register page, review the program agreement, select the check box to accept the terms, and click Register.
Review the registration results to confirm your organization was successfully registered. (See Figure 1-26.)
Figure 1-26 Windows Insider for Business registration
Plan the appropriate Windows 10 Enterprise deployment method
With Windows 10, deployment methods involve both the initial deployment of the operating system and the deployment of future feature updates. Feature updates in Windows 10 are responsible for upgrading the operating system from one major release to the next. Both scenarios play an important role when you are supporting WaaS. You can use many of the techniques covered in this section to manage new deployments of Windows 10 and support future feature updates.
Windows 10 allows for many of the traditional deployment scenarios that you may already be familiar with. For example, deploying the latest version of Windows during an organization’s next major hardware refresh was a common scenario for earlier versions of the operating system. There are new methods available with Windows 10, however — for example, the in-place upgrade, which can help simplify your migration if new hardware is not readily available.
In this section, you will look at a variety of deployment methods available for Windows 10, along with the pros and cons for each method. This includes capabilities available with modern servicing, such as Windows Update for Business. You will also work with task sequences in ConfigMgr as part of the in-place upgrade. Finally, this section covers the traditional methods that are still supported with Windows 10.
Plan for deploying Windows 10 Enterprise
There are two main scenarios associated with Windows 10 deployment. The first scenario involves moving to Windows 10 from an earlier version of the operating system — for example, if your client devices have Windows 8.1 installed, and you are planning a migration to Windows 10. The second scenario involves keeping Windows 10 current with the latest feature updates — for example, your client devices have Windows 10, version 1803 installed, and you are planning to upgrade to Windows 10, version 1809. There are deployment methods for each of these scenarios.
In some cases, a deployment method can be used for both deployments and upgrades, such as the in-place upgrade. Other methods are more specific, such as Windows Update for Business. The first thing you must understand is what options are available and in what scenarios they apply.
Traditional methods This category includes several of the deployment methods used with earlier versions of the Windows operating system. Microsoft has continued to support these methods, and has released compatibility updates for tools such as the Microsoft Deployment Toolkit (MDT) and the Windows Assessment and Deployment Kit (Windows ADK), both of which support traditional imaging and upgrades. Specific deployment methods in this category include the following:
Bare metal This deployment method is for scenarios where new hardware is procured or existing hardware is repurposed. In both situations, a Windows image is installed and configured according to the organization’s IT standards. Bare metal deployments occur at most organizations and are commonly leveraged in situations where you must roll out a new version of the operating system or another major application, such as Microsoft Office. It can help consolidate efforts.
Refresh This deployment method is for scenarios where an existing device needs to be wiped and reloaded. In this situation, the existing user state is backed up, the disk is wiped, the latest image is installed, and the user state is restored. Refresh deployments are often seen when a device becomes inoperable and needs to be wiped. This type of deployment can also be used in upgrade scenarios, such as moving from Windows 7 to Windows 10.
Replace This deployment method is similar to the refresh method but includes new hardware as part of the process. For example, suppose a user is running a three-year-old laptop with Windows 8.1 installed. You could back up the user state on this laptop and replace it by restoring the backup to a new laptop running Windows 10.
In-place upgrade This deployment method is for scenarios where an earlier version of Windows (including an earlier version of Windows 10) is installed on a device and you upgrade the device to Windows 10 or to a newer release of Windows 10. This method pertains to upgrading to Windows 10 and staying current. For example, suppose you have a device running Windows 7 and you deploy an in-place upgrade for Windows 10, version 1809. Alternatively, suppose you have a device running Windows 10, version 1803 and you deploy an in-place upgrade for Windows 10, version 1809. Either way, you could use this deployment method. This method retains the applications, settings, and user data on the system. The old version of Windows is moved to a Windows.old folder for a configurable amount of time, which can then be referenced in the event you need to roll back the operating system.
Modern servicing This deployment method is for scenarios where you need to keep current with new releases of Windows 10. Similar to the in-place upgrade, modern servicing can address situations where you are moving from one version of Windows 10 to the next. However, modern servicing technologies are specific to Windows 10, and cannot be used with earlier versions of the operating system. Windows Update for Business (WUfB), Windows Server Update Services (WSUS), and System Center Configuration Manager (ConfigMgr) are all tools that support modern servicing.
Now that you have covered the basic deployment methods for Windows 10, let’s take a look at the different deployment formats. Windows 10 is available in two formats:
Electronic Software Delivery (ESD) Available through Windows Update or the Windows 10 Media Creation Tool
Windows Imaging Format (WIM) Available through traditional installation media (ISO)
There are a number of solutions available for each deployment format, with pros and cons for each. See Table 1-7 for a breakdown of these formats.
Table 1-7 Modern servicing techniques
Deployment Format |
Delivery Solution |
Pros |
Cons |
|---|---|---|---|
Electronic Software Delivery (ESD) |
Windows Update for Business (WUfB) Windows Server Update Services (WSUS) System Center Configuration Manager (ConfigMgr) |
Smallest package size Fastest installation |
Limited control to handle pre and post upgrade tasks |
Windows Imaging Format (WIM) |
System Center Configuration Manager (ConfigMgr) Microsoft Deployment Toolkit (MDT) Third-party management solutions |
Full control over the upgrade experience end-to-end |
Highest administrative effort Largest package size |
The delivery solutions noted in Table 1-7 are described as follows:
Windows Update for Business (WUfB) WUfB is a series of new policies available to Windows 10 clients. These policies enable administrators to manage the servicing channel and deferral settings for Windows 10 feature updates and quality updates. This service delivers updates to clients through the public Windows Update network using the ESD deployment format. WUfB policies can be configured using a group policy object (GPO) or Intune MDM policy.
Windows Server Update Services (WSUS) WSUS is an on-premises solution for organizations that need to fully manage the updates that they deploy to their clients. Administrators can synchronize with the Microsoft Update catalog and deploy approved updates for all supported versions of the Windows operating system. This includes feature updates and quality updates for Windows 10.
System Center Configuration Manager (ConfigMgr) ConfigMgr is an on-premises device-management solution for organizations that need to fully manage the updates that they deploy to their clients. With ConfigMgr, administrators are given the option to use task sequences or software updates (WSUS). With task sequences, you have additional control over the in-place upgrade scenario.
Microsoft Deployment Toolkit (MDT) MDT is a free deployment tool that enables administrators to support Windows 10 images and in-place upgrades. Similar to ConfigMgr, MDT uses task sequences for image creation and upgrades.
As you prepare to deploy Windows 10 using the in-place upgrade method, there are a number of items to consider. Although there are several benefits to supporting this method, each of the following issues can affect the success of your implementation.
Compatibility You must review all hardware, drivers, and applications for Windows 10 compatibility. Older hardware, including peripherals, may not support the latest release of Windows 10 or have supported drivers, in which case they would need to be replaced or updated. Applications that are incompatible can cause the upgrade to fail and must be assessed as well. Later in this skill section, you will review Upgrade Readiness, a service provided by Microsoft to help identify compatibility issues.
Legacy BIOS to UEFI Windows 10 supports legacy BIOS and UEFI, both of which use different partition maps on the system drive. That said, there are security features, such as Secure Boot, that require UEFI. In this case, you can complete an in-place upgrade on a device running legacy BIOS and then use the MBR2GPT tool to convert the partition map from master boot record (MBR) to GUID partition table (GPT).
Need More Review? Running MBR2GPT
For more information about the MBR2GPT tool, including prerequisites and instructions, visit https://docs.microsoft.com/windows/deployment/mbr-to-gpt.
Disk encryption The Windows 10 in-place upgrade supports BitLocker natively. If the system drive is encrypted with BitLocker, the upgrade will work without any additional administrative effort. If the drive is encrypted with a third-party solution, you must contact the vendor for instructions on how to address the encryption software during the upgrade.
Language packs The Windows 10 in-place upgrade will retain the system default user interface (UI) language. Any additional language packs that have been installed previously must be re-installed following the upgrade.
32-bit to 64-bit The Windows 10 in-place upgrade does not support upgrading devices from 32-bit versions of Windows to 64-bit versions. If this is a scenario you need to plan for, consider using the refresh or replace deployment method instead.
Windows to Go Windows to Go is a feature that enables customers to boot a Windows installation from a supported USB storage device. The Windows 10 in-place upgrade is not supported on Windows to Go devices running older versions of the operating system. Once a device is running Windows 10, however, future feature updates can be installed using this method.
Existing images If you have an existing operating system image for Windows 7 or Windows 8.1, installing that image, upgrading it to Windows 10, and recapturing it is not supported. A new operating system must be re-created for Windows 10 deployments. Alternatively, you can start using offline servicing to avoid traditional reference image designs.
Need More Review? Windows 10 Offline Servicing
For more information about offline servicing for Windows 10, visit https://docs.microsoft.com/windows-hardware/manufacture/desktop/understanding-servicing-strategies.
Dual-boot The Windows 10 in-place upgrade supports devices running a single version of Windows. Devices configured in a dual-boot or multi-boot configuration are not supported.
Design an in-place upgrade for Windows 10
In this section, you take a closer look at the in-place upgrade deployment method. This is a common starting point for organizations that are planning their migration to Windows 10. In the following example, you will work with a task sequence in ConfigMgr, version 1810. In this version of ConfigMgr, a task sequence template is provided to support in-place upgrade scenarios.
To begin, you must download a copy of the Windows 10 installation media. You can retrieve this by downloading the latest Windows 10 ISO from the Microsoft volume license service center (VLSC). To access the VLSC, visit https://www.microsoft.com/Licensing/servicecenter/default.aspx. After you have downloaded Windows 10, you must extract the files from that ISO in preparation for creating the operating system upgrade package required by ConfigMgr. See Figure 1-27 for an example of the extracted files needed.
Figure 1-27 Windows 10 installation media
ConfigMgr requires the Windows 10 installation media in order to complete the in-place upgrade. The installation media is referenced in the task sequence as an operating system upgrade package. When this step runs, ConfigMgr executes setup.exe with a series of command-line options that instruct the setup operation on how to complete the upgrade. Setup.exe can be executed independently of ConfigMgr; it is worth reviewing the variety of supported options.
Need More Review? Windows Setup Command-Line Options
For more information about the supported Windows setup command-line options, including examples on how to use these options, visit https://docs.microsoft.com/windows-hardware/manufacture/desktop/windows-setup-command-line-options.
Figure 1-28 shows an example of the in-place upgrade task sequence template provided with ConfigMgr, version 1810. Each group in this task sequence template is provided to assist you with creating a working upgrade deployment. You can add, remove, or modify any of these steps to meet your requirements. Each group contains a basic description to provide additional guidance.

Figure 1-28 In-place upgrade task sequence
The groups are as follows:
Prepare for Upgrade This group is designed for steps that will run in the current operating system. These steps should be focused on pre-upgrade operations, such as checking for 20 GB of free disk space (a requirement for setup) or ensuring that the computer is connected to a wired connection (if you do not support upgrades over wireless).
Upgrade the Operating System This group is designed for steps that trigger the in-place upgrade. The Upgrade Operating System and Restart Computer steps are included as part of the template. The Upgrade Operating System step includes a number of options. (See Figure 1-29.) In this figure, the Perform Windows Setup Compatibility Scan Without Starting Upgrade check box is selected. This setting runs setup using the
/Comaptoption. The Windows setup will scan the device for possible incompatibilities. If any are found, a return code is generated with a series of logs that require further analysis.
Figure 1-29 The Upgrade Operating System task sequence
Post-Processing This group is designed for steps that need to run after the upgrade has completed successfully. This group will run if the task sequence variable
_SMSTSSetupRollbackequalsfalse. Possible steps might include installing applications, resuming disk encryption, and running custom configuration changes for your organization.Rollback This group is designed for steps that need to run after an upgrade has failed and triggered a rollback. This group will run if the task sequence variable
_SMSTSSetupRollbackequalstrue. Possible steps might include sending an email notification to the device owner that the upgrade was unsuccessful and automatically creating an incident in your service desk system.Run Actions on Failure Similar to the rollback group, this group is designed for steps that need to run after an upgrade has failed. This group will run if the task sequence variable
_SMSTSOSUpgradeActionReturnCodedoes not equal0. Possible steps might include running a log collector or diagnostic tool such as SetupDiag.
Note Setupdiag
SetupDiag is a diagnostic tool designed to analyze Windows setup failures and provide summarized results on what caused the failure. For more information about SetupDiag, visit https://docs.microsoft.com/windows/deployment/upgrade/setupdiag.
After you have configured this task sequence to meet your needs, you can use the deployment ring strategy discussed earlier in this chapter. In ConfigMgr, this can be done using a series of device collections (groups of devices) followed by a phase deployment (a multi-phase deployment based on success criteria). For the exam, you will want to be familiar with the in-place upgrade task sequence and what its capabilities are compared to other deployment methods.
Design a servicing plan for Windows 10
This section looks at the modern servicing deployment method. This method delivers new feature updates to existing devices that already have Windows 10 installed. With modern servicing, feature updates are installed in much the same way as they are with the more traditional Windows Update. In the following examples, you will review three techniques for enabling modern servicing.
Use Modern servicing with Microsoft Intune
The first solution you will look at involves the Windows 10 update rings in Microsoft Intune. This solution requires target devices to be enrolled in Intune. Once enrolled, devices that have this policy assigned will be configured to use Windows Update for Business. Follow these steps to create an update ring policy in Microsoft Intune.
Log in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com/.
Click Devices.
Click Windows 10 Update Rings.
On the Windows 10 Update Rings page, click Create Profile.
Figure 1-30 shows the Update Ring Settings tab, which shows the update ring settings available through this policy.
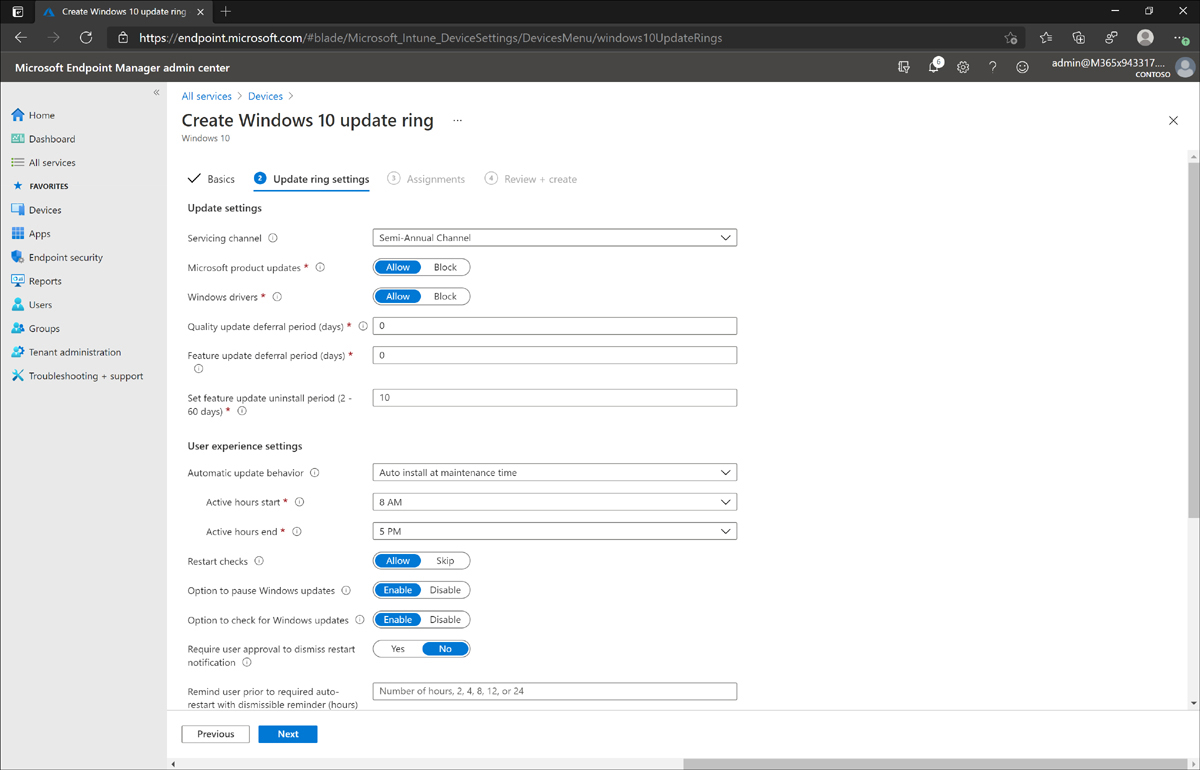
Figure 1-30 Windows 10 update rings
The update ring settings are split into two sections: Update Settings and User Experience Settings. In the Update Settings section are two controls that are used to manage the deployment of feature updates. These include the following:
Servicing Channel This drop-down list includes each of the servicing channels you reviewed in Skill 4.1. Use this option to set up deployment rings for Windows Insider for Business or to configure deployments of public releases when they reach the semi-annual channel.
Feature Update Deferral Period (Days) This feature enables you to defer an update for as long as 365 days. It is designed to give you an additional grace period to accommodate your deployment workflow.
After configuring and assigning this policy, you have the option to pause the assignment for as many as 35 days in case you need to halt all upgrades to troubleshoot an issue. You can set this option in the Software Updates – Windows 10 Update Rings blade, which you access by selecting the policy and clicking Pause on its Overview page. When you are ready to resume the assignment, you can do so from the same blade; otherwise, the assignment will automatically resume after 35 days.
Use Modern servicing with Group Policy
The next solution you will review involves configuring WUfB using the group policy. These group policy settings are identical to the ones in Intune, so this will be a brief example. The major difference with group policy is how the various settings are split into individual policies. For instance, the settings for user experience are broken down between multiple policies. In the following example, you will configure a new GPO for WUfB using the latest ADMX templates provided with Windows 10, version 1809.
Open the Group Policy Management Editor.
Create a new GPO and name it WUfB.
Right-click the new GPO and click Edit.
Under Computer Configuration, expand Policies.
Expand Administrative Templates.
Expand Windows Components.
Expand Windows Update.
Expand Windows Update for Business.
Locate and edit the Select When Preview Builds and Feature Updates Are Received policy.
Select the Enabled option and configure the following options (see Figure 1-31). Then click OK.
Select the Windows Readiness Level for the Updates You Want to Receive Semi-Annual Channel
After a Preview Build or Feature Update Is Released, Defer Receiving It for This Many Days 0
Pause Preview Builds or Feature Updates Starting Leave this value blank

Figure 1-31 GPO for feature updates
Modern servicing with ConfigMgr
The last solution you will review is the Window 10 servicing feature in ConfigMgr. This deployment method is ideal for organizations that have chosen the ESD update format but still want to manage update deployments through ConfigMgr.
Windows 10 servicing uses ConfigMgr’s Software Update feature. This feature employs WSUS to synchronize updates from the Microsoft Update catalog. Those updates can then be managed and deployed by ConfigMgr. The Windows 10 Servicing feature leverages these capabilities.
The creation wizard will walk you through creating a servicing plan, setting up deployment rings, and creating the deployment. In this example, you will create a servicing plan in ConfigMgr, version 1810.
Click Start, search for Configuration Manager Console, and select it.
In the Configuration Manager Console, click the Software Library workspace.
In the Overview page, expand Windows 10 Servicing, and select Servicing Plans.
In the ribbon, click Create Servicing Plan.
Figure 1-32 shows an example of a Windows 10 servicing plan created in ConfigMgr. The summary page outlines the configuration options for each of the various controls available on each page in the creation wizard. The pages are as follows:
General Assign a name and description for the servicing plan.
Servicing Plan Select the device collection that will receive the deployment generated by this servicing plan.
Deployment Ring Select a servicing channel and delay deployment up to 120 days. Note that your only options for servicing channels are Semi-Annual Channel (Targeted) and Semi-Annual Channel. You do not have options for Windows Insider builds.
Upgrades Define the criteria for the updates you are deploying with this servicing plan. For example, if you are creating a servicing plan for just 64-bit devices, you can configure the architecture attribute to only retrieve 64-bit updates.
Deployment Schedule Define when the update will become available and when it will be enforced.
User Experience Configure what notifications are displayed to the user and how reboot behavior will be handled. If you are using maintenance windows in ConfigMgr, you can configure whether they are acknowledged for this deployment.
Package Assign a deployment package or configure the servicing plan to use the Microsoft cloud, reducing the need to download and replicate content internally.

Figure 1-32 Windows 10 servicing plan summary
Analyze upgrade readiness for Windows 10
Earlier in this chapter, you explored some of the requirements that you must consider before deploying Windows 10. Most customers preparing to deploy a new operating system are going to perform extensive testing and validation of their hardware, drivers, and applications before they start large-scale deployments. This process can be time-consuming — even more so when that operating system is undergoing major changes every six months.
Upgrade readiness is a service provided by Microsoft to help customers identify compatibility concerns in support of WaaS. Customers that choose to enroll in this service can get metrics and visual indicators on which components need the most attention and which devices are ready to upgrade. This is made possible using Windows telemetry and the Microsoft cloud.
Plan for upgrade readiness
To prepare for upgrade readiness, you must be familiar with the requirements for Windows Analytics. To begin, let’s cover the fundamentals of upgrade readiness and items that you should be familiar with:
Telemetry The upgrade readiness service requires that you set the Windows telemetry level to basic (minimum) for any devices that you enroll in the service.
Operating system support Upgrade readiness supports devices running Windows 7 SP1, Windows 8.1, or Windows 10. For Windows 7 SP1, you must install KB2952664. For Windows 8.1, you must install KB2976978.
Target operating system Upgrade readiness can provide you with compatibility information for one operating system version at a time. For example, in Figure 1-33, you can see the Target Version to be Evaluated drop-down menu. This option is configured as part of the solution settings in Azure. The operating system version you select will be used for data analysis. When a new Windows 10 feature update is released, you must update this field to the new build number. A change to the target version can take up to 24 hours to apply.

Figure 1-33 Upgrade readiness solution settings
Data availability After a device is configured to upload telemetry and associate it with a commercial ID, it can take up to 72 hours for that data to become visible in upgrade readiness. After that, you can expect to see updates every 24 hours. For example, if a device has an incompatible application and you update that application, the change will be reflected within 24 hours.
Cost The upgrade readiness service is offered free of cost. This free offering provides seven days of historical data and up to 500 MB of storage. If your organization decides it needs to retain 90 days of historical data, you must procure Azure storage to accommodate this requirement.
Navigate upgrade readiness
After you have set up your devices to upload telemetry to Microsoft with your organization’s commercial ID, the results will be shown in the Log Analytics service in the Azure portal. From there, you can begin navigating through the different blades and assessing your organization’s upgrade readiness.
The following steps will introduce you to the upgrade readiness solution in the Azure portal. For this demonstration, we have already created a Log Analytics workspace for Contoso Electronics, named -Analytics. The devices in this organization are also configured for upgrade readiness. You will look at the Contoso Electronics environment to determine whether the organization is ready to adopt Windows 10. To access the upgrade readiness solution, follow these steps.
Log in to the Microsoft Azure portal at https://portal.azure.com/.
Click All Services.
Search for Log Analytics and select it.
On the Log Analytics blade, select the workspace containing your upgrade readiness solution — in this example, -Analytics.
On the -Analytics blade, under General, select Solutions.
On the -Analytics – Solutions blade, select the solution starting with CompatibilityAssessment — in this example, CompatibilityAssessment(-Analytics).
On the CompatibilityAssessment(-Analytics) blade, click the Upgrade Readiness tile.
The Upgrade Readiness Workflow page opens. It consists of multiple blades with data related to Windows 10 compatibility.
The next blade you are presented with relative to upgrade readiness is STEP 1: Identify Important Apps. (See Figure 1-34.) This blade is designed to highlight applications in your environment that may need attention before deploying Windows 10. The first number on this blade, labeled Total Applications, indicates the total number of applications identified in your organization. The second number, labeled Applications in Need of Review, indicates the number of applications for which Microsoft does not have compatibility information and which it recommends that you review. You can click either of these values to drill down into the various data categories.

Figure 1-34 Upgrade Readiness - Identify Important Apps
Applications are automatically grouped based on importance. For example, applications that are installed on less than 2% of devices are grouped together. You also have the option to assign or modify the importance level with a selection of built-in options. You accomplish this by clicking the Assign Importance link at the bottom of the blade. Defining the importance level will assist in organizing your application portfolio and defining which applications are upgrade ready. Importance levels include the following:
Not reviewed This is the default importance level for applications that are installed on more than 2% of devices. To clearly understand which apps are important, you can modify this default value to something with additional meaning.
Mission critical This is an optional importance level, signifying a mission-critical dependency on the application.
Business critical This is an optional importance level, signifying a business-critical dependency on the application.
Important This is an optional importance level, signifying the application is important to the organization.
Best effort This is an optional importance level, signifying the application is not important and compatibility will be approached as a best effort.
Ignore This is an optional importance level, signifying the application is not important and can be safely ignored from future compatibility reports. Selecting this option will mark the application as upgrade ready, removing it as a blocker.
Review in progress This is an optional importance level, signifying the application is currently under review and the importance level has not yet been identified.
The next blade you are presented with is STEP 2: Resolve Issues. This step in the workflow includes a series of blades for addressing issues that are considered to be upgrade blockers. See the following list for more information about each of the blades in step 2.
Review Applications with Known Issues This blade highlights applications with known issues. Applications that Microsoft has a fix for will be marked accordingly, reducing the number of applications that you must review. As you review these apps, you have the option to adjust the upgrade readiness value, approving or blocking applications from the upgrade. These values include:
Not Reviewed This is the default value for applications that are installed on more than 2% of devices and all drivers.
Review in Progress Assigning this value to an application or driver will prevent it from being approved until it can be marked as ready to upgrade. This should be used for any applications or drivers that you still need to validate.
Ready to Upgrade Assigning this value to an application or driver will mark it as upgrade ready.
Won’t Upgrade Assigning this value to an application or driver will mark all corresponding devices as not upgrade ready.
Review Known Driver Issues This blade highlights drivers with known issues. Drivers that Microsoft has information on will be marked accordingly. For example, if newer versions of various drivers are available through Windows Update, those drivers will be grouped together. Similar to the previous application blades, you can define the same upgrade readiness values to approve or deny drivers.
Review Low-Risk Apps and Drivers This blade highlights applications and drivers that need review but are determined to be low risk based on various conditions. For example, if Microsoft has identified an application as highly adopted (installed on more than 100,000 devices), that application will be marked as low risk.
Prioritize App and Driver Testing This blade highlights applications and drivers that are currently blocking the upgrade for your target operating system on more than 80% of devices. Reviewing and prioritizing these items can yield a high return for upgrade readiness.
The next blade you are presented with is STEP 3: Deploy (see Figure 1-35). This step in the workflow consolidates all information that has been collected and categorizes devices based on upgrade readiness. There are three upgrade options on this blade:
Figure 1-35 Upgrade Readiness - Deploy
Review in Progress Devices in this category have at least one application or driver installed that has been marked as review in progress. These markings are applied in step 1 and step 2 of the workflow.
Won’t Upgrade Devices in this category have at least one application or driver installed that has been marked as won’t upgrade. Alternatively, these devices do not meet a system requirement to complete the upgrade, such as free disk space.
Ready to Upgrade Devices in this category have all applications and drivers marked as ready to upgrade. When you are ready to deploy the upgrade to these devices, export the list of computers and target them with your preferred management solution.
The next blade you are presented with is STEP 4: Monitor. This step in the workflow includes a series of blades for monitoring the progress of your upgrade deployments. See the following list for more information about each of the blades in step 4.
Update Progress (Last 30 Days) This blade highlights the deployment status for all your devices. There are five deployment categories that group devices.
Not Started Devices that have not started the upgrade. This includes devices that are upgrade ready and those that are not.
Upgrade completed Devices that have successfully completed the upgrade to your target operating system.
Failed Devices that attempted to upgrade to your target operating system but were unsuccessful.
In Progress Devices that have started the upgrade to your target operating system and have not yet reported back their results.
Progress stalled Devices that have started the upgrade and stalled.
Driver issues Drivers that are reporting issues following a successful upgrade. This information includes the problem code reported in device manager for the affected device(s).
User feedback User feedback submitted through the Feedback Hub app. Users that have submitted feedback using their Azure AD account will be consolidated and displayed here for review.
Need More Review? Upgrade Readiness
For more information about enabling upgrade readiness to support Windows 10, visit https://docs.microsoft.com/windows/deployment/upgrade/use-upgrade-readiness-to-manage-windows-upgrades.
Evaluate and deploy additional Windows 10 Enterprise security features
Windows 10 is a cloud-connected operating system, engineered to protect against modern-day security threats. Windows 10 introduces a new collection of security features and enhancements that earlier versions of the operating system do not offer. Some Windows 10 security features can be connected to Microsoft 365 for centralized management and reporting.
This section explores the core security features available with Windows 10, including those that integrate with Microsoft 365, as well as what options you have available to evaluate these features in your environment. For the exam, you must be familiar with these features and their capabilities.
Note
Moving to a semi-annual release cycle has enabled Microsoft to address major security vulnerabilities in a much shorter timeframe. This also means that these features are frequently evolving over time with new releases of Windows 10.
The security capabilities in Windows 10 are grouped into three categories:
Identity and access management Security features in this category focus on enhancing security identities. This includes capabilities such as two-factor authentication and biometric credentials.
Information protection Security features in this category focus on protecting the data in your organization. This includes capabilities such as drive encryption, data leakage protection, and information protection.
Threat protection Security features in this category focus on protecting against vulnerabilities and threats. This includes capabilities such as antivirus, antimalware, and behavioral monitoring.
Table 1-8 includes a breakdown of each core Windows 10 security component, its protection category, the required Windows edition, and a description of its capabilities. In this table, you will see references to S Mode. Alongside the variety of security features built into Windows 10, S Mode adjusts the behavior of the operating system. When activated, new security requirements are enforced, such as only allowing apps from the Microsoft Store and limiting browser usage to Microsoft Edge.
Need More Review? Windows 10 s in Mode
For more information about Windows 10 in S mode, visit https://support.microsoft.com/help/4020089/windows-10-in-s-mode-faq.
Table 1-8 Windows 10 security components
Technology |
Protection Category |
Windows Edition |
Description |
|---|---|---|---|
Windows Hello for Business |
Identity and access management |
S mode, Enterprise |
Password replacement, enabling strong two-factor authentication for PCs and mobile devices. Leverages biometric credentials and supports Active Directory and Azure AD accounts. |
Windows Defender Credential Guard |
Identity and access management |
S mode Enterprise, Enterprise |
Virtualization-based security that protects secrets stored on the device, including NTLM password hashes, Kerberos credentials, and credential manager domain credentials. |
BitLocker |
Information protection |
S mode, Pro, Enterprise |
Drive encryption solution that is strongest when combined with a hardware-based Trusted Platform Module (TPM). Supports the escrowing of recovery keys in Azure AD. |
Windows Information Protection |
Information protection |
S mode, Pro, Enterprise |
Data leakage prevention (DLP) solution that can apply additional protection to company files, preventing data leakage. |
Windows Defender Application Guard |
Threat protection |
S mode Enterprise, Enterprise |
Enhanced security for Microsoft Edge that isolates untrusted sites to a Hyper-V enabled container, protecting the host operating system from potential threats. |
Windows Defender Application Control |
Threat protection |
Enterprise |
Policy-based protection that prevents access to non-approved applications. |
Windows Defender Exploit Guard |
Threat protection |
S mode, Pro, Enterprise |
Collection of host intrusion prevention tools focused at reducing fileless attacks. Features include exploit protection, attack surface reduction rules, network protection, and controlled folder access. |
Windows Defender Antivirus |
Threat protection |
S mode, Pro, Enterprise |
Antivirus and antimalware definition-based solution that is integrated with Windows 10. |
Microsoft Defender for Endpoint |
Threat protection |
Enterprise |
Cloud-connected integration with the built-in security features in Windows 10. Provides behavioral-based analysis using machine learning and cloud-based analytics. Includes monitoring and alerts based on threat intelligence data generated by Microsoft and collected by other partners. |
From an evaluation perspective, the majority of these features are built into the operating system. As long as you have a compatible edition of Windows 10, you can enable these features for testing without any additional licensing. To keep current with the list of available features, including requirements and deployment documentation, visit https://docs.microsoft.com/windows/security/.
Skill 1.5: Enroll devices
Enrolling devices is the first step to enabling them to receive the compliance and configuration polices that you have created, and to gain access to the Microsoft Store for Business to access apps. Device enrollment also sets the baseline that you configured in skill section 1.2.
Plan for device join to Azure Active Directory (Azure AD) and plan for device enrollment
When you enroll a device, you join that device to an Azure Active Directory tenant associated with Microsoft Intune. Before you can join or enroll a device, you must meet certain prerequisites that relate to the Azure AD tenant:
The MDM authority must be set to Intune
The devices you plan to manage must be supported. Supported device types include:
Android
iOS/iPadOS
macOS
Windows
For iOS, iPadOS, and macOS, you must have an Apple ID and an MDM push certificate.
Users and groups must have been configured with enrollment policies
If the device you plan to enroll was previously part of a different MDM policy or tenant, the device might need to be factory reset before Intune policies can be applied. The device platforms that require a reset include the following:
Android Enterprise corporate-owned work profile
Android Enterprise fully managed
Android Enterprise dedicated devices
iOS/iPad OS
macOS
If you plan to enroll devices in bulk before distributing or assigning them to users, you should create a device enrollment manager (DEM) account in Microsoft Intune. The DEM account is a standard Azure Active Directory user that has been added to the list of DEM accounts in Intune. Follow these steps to add an existing user as a DEM account in Intune:
Sign in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com.
Click Devices, and then click Enroll Devices.
Click Device Enrollment Managers, and then click Add.
Specify the user principal name of an existing AD account that you want to serve as a DEM account and click Add. Figure 1-36 shows a DEM account in Intune.
Figure 1-36 Device enrollment managers
Note
User accounts that are DEMs can enroll up to 1,000 devices in Intune, compared to the default limit of 15 for a normal user account.
Enable device enrollment
You can manage device enrollment with Intune by creating deployment profiles, setting enrollment restrictions, and setting enrollment limits. You create deployment profiles for various platforms to control how devices are connected, depending on the device type.
Create deployment profiles
Deployment profiles customize the provisioning experience and preconfigured settings to simplify enrollment for end-users. To configure a deployment profile, follow these steps.
Sign in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com.
Click Devices, and then click Enroll Devices.
Click Windows Enrollment, and then click Deployment Profiles.
Click Create Profile, and then click Windows PC.
On the Basics tab, enter a name for the profile — for example, AutopilotProfile1.
On the Out-of-Box Experience (OOBE) tab, enter the following settings (see Figure 1-37), and then click Next.
Deployment Mode User-Driven
Join to Azure AD As Azure AD Joined
Microsoft Software License Terms Hide
Privacy Settings Hide
Hide Change Account Options Hide
User Account Type Administrator
Allow White Globe OOBE Yes
Language (Region) Operating System Default
Automatically Configure Keyboard Yes
Apply Device Name Template Yes
Name %SERIAL%
Figure 1-37 Out-of-box experience (OOBE) settings
On the Assignments tab, select the groups to add or exclude from being applied — for example, All Devices. Then click Next.
On the Review + Create tab, click Create.
Set device enrollment restrictions
This section covers the controls given to administrators to limit the number and type of devices a user can enroll. Limiting the number of devices assigned to a user can help with license constraints and organization. In addition, restricting devices that are running an older operating system is a requirement for many organizations due to security and compliance concerns. Finally, blocking personally owned devices may be a scenario you need to consider if your organization is not ready to support a bring your own device (BYOD) model. Table 1-9 explains the various enrollment restriction options.
Table 1-9 Device enrollment restrictions
Restrictions |
Restriction Type |
Description |
|---|---|---|
Maximum number of enrolled devices |
Limit restriction |
Restrict the number of devices a user can enroll, ranging from 1 to 15. |
Allow or block based on device platforms |
Type restriction |
Restrict device enrollment by device platform, including Android, Android work profile, iOS, macOS, and Windows (MDM). |
Allow or block based on platform operating system |
Type restriction |
Restrict device enrollment by operating system, providing a minimum and maximum version number. |
Allow or block personally owned devices |
Type restriction |
Restrict device enrollment to corporate-owned devices, requiring additional steps to define a device as corporate-owned. |
Note Personally Owned Devices
The ability to allow and block personally owned devices depends on other factors in your MDM configuration. For Windows (MDM), if the device was previously enrolled through a bulk provisioning package, like ConfigMgr Co-Management or Windows Autopilot, it will be allowed to enroll.
Device Limit Restriction
In this section, you implement a restriction to limit the number of devices a user can enroll with:
Sign in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com.
Click Devices, and then click Enroll Devices.
Click Enrollment Restrictions.
On the Enrollment Restrictions blade, review the items under Device Type Restrictions and Device Limit Restrictions. (See Figure 1-38.)

Figure 1-38 Device enrollment restrictions
Note that there is a default enrollment restriction for each restriction. Both can be modified, but not deleted.
Click Create Restriction, and then click Device Limit Restriction.
On the Basics tab, provide a name for the restriction — for example, Custom Device Limit.
On the Device Limit tab, open the Device Limit drop-down list and choose 5.
On the Scope Tags tab, specify a scope if required for the deployment, and click Next.
On the Assignments tab, specify the groups that the enrollment restriction should apply to, and click Next.
On the Review + Create tab, click Create.
A new custom device restriction is created and is available on the Device Enrollment – Enrollment Restrictions blade.
Here you worked with limit restrictions. Assigning a limit prevents users from enrolling more than the defined value. The default restriction allows users to enroll up to five devices. Attempting to enroll more than five will result in a notification.
Device Type Restrictions
The second enrollment restriction you will work with limits enrollment by the type of device:
Sign in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com.
Click Devices, and then click Enroll Devices.
Click Enrollment Restrictions
Click Create Restriction, and then click Device Type Restriction.
On the Basics tab, provide a name for the restriction — for example, Custom Type Restriction.
On the Platform Settings tab, select the desired combination of settings to allow or restrict devices by platform, version, whether they are personally owned, or device manufacturer. Figure 1-39 shows a configuration that blocks Android devices. Then click Next.

Figure 1-39 Device type restrictions
On the Scope Tags tab, specify a scope if required for the deployment, and click Next.
On the Assignments tab, specify the groups that the enrollment restriction should apply to, and click Next.
On the Review + Create tab, click Create.
With these steps complete, you should have a custom device type restriction available on the Enrollment Restrictions blade. In this example, you worked with platform restrictions. Platform restrictions provide a granular set of controls for approving specific device types and operating system versions. With an enrollment plan that supports BYOD, controlling the minimum and maximum operating system version can prevent known vulnerabilities or pre-release versions from entering your environment. Figure 1-40 shows the configured device type and limit restrictions.

Figure 1-40 Custom restrictions
Assign enrollment restrictions
Let’s examine the process for assigning enrollment restrictions. First, you must understand the priority system. The priority value, shown on the Device Enrollment – Enrollment Restrictions blade, is for users who are members of multiple groups, but may have different enrollment restrictions assigned. You can change the priority value in the portal by dragging a device restriction up or down the list.
Real World Device Restriction Priorities
Suppose Ethan is a member of two Azure AD groups: IT and All Employees. The IT group has device-enrollment restrictions that allow members to enroll all device types. This device restriction has a priority of 1. The All Employees group has device-enrollment restrictions that only allow members to enroll Windows (MDM) devices. This device restriction has a priority of 2. In this situation, Ethan would receive the IT device restrictions due to the higher priority.
Enrollment restrictions are assigned to Azure AD groups. The following steps assume you already have an Azure AD group created with the users you need to target.
Sign in to the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com.
Click Devices, and then click Enroll Devices.
Click Enrollment Restrictions
Click the ellipses (...) next to the custom device limit restriction that was previously created.
On the Custom Device Limit blade, click Assign.
The device restriction should become available in the portal and can be assigned to an Azure AD group of your choosing.
Thought experiment
In this thought experiment, demonstrate your skills and knowledge of the topics covered in this chapter. You can find the answer to this thought experiment in the next section.
Contoso Electronics is a global organization, spanning 200 locations and supporting 25,000 mobile devices. Some offices have slow WAN links, but all locations have fast internet connections.
The organization is using ConfigMgr for device management and deployment. All employees are registered in Azure AD and have an Office 365 license assigned. Last year they started introducing Windows 10 through a traditional bare metal deployment. The organization has 2,500 devices that run Windows 10, version 1803. The remaining devices run Windows 8.1.
Your manager has tasked you with creating a deployment plan for fully adopting Windows 10 over the next six months and keeping current with new releases. As the technical lead for enterprise device management, you have started testing the in-place upgrade using ConfigMgr, going from Windows 8.1 to Windows 10. Some devices upgraded successfully, but others failed. As part of your deployment design, you must address the following questions, while minimizing on-premises infrastructure:
The in-place upgrade from Windows 8.1 to Windows 10 has surfaced some compatibility issues. What solution should you implement to track compatibility for your fleet and what steps do you need to take to implement this solution?
Windows 10 Enterprise 64-bit is the target operating system for your fleet. Recently, you found that 5% of your Windows 8.1 devices are 32-bit. What solution will you use to upgrade these devices?
What servicing channels should you adopt to keep current with the latest releases of Windows 10 and what steps do you need to take to implement them?
The 2,500 devices running Windows 10 must be upgraded to version 1809. What solution should you implement to upgrade these devices?
Your CIO is asking you to begin migrating MDM workloads to Intune. What MDM solution addresses this requirement?
Thought experiment answers
This section contains the solution to the thought experiment. Each answer explains why the answer choice is correct.
To address compatibility issues with Windows 10, you should implement upgrade readiness. To accomplish this, you must create a Log Analytics workspace in Azure. After creating the workspace, you should create and deploy a GPO with Windows telemetry enabled and set to basic, along with your commercial ID. The Windows 8.1 computers will also need KB2976978 installed before they can upload data.
The Windows 8.1 computers must be upgraded using a refresh or replace deployment method. The user state can be captured with ConfigMgr and restored after the device has been re-imaged using a Windows 10 64-bit installation.
To support the latest release of Windows 10, you should adopt a semi-annual channel (targeted) and plan for the Windows Insider channel to prepare for new versions of the operating system. You should use a GPO to configure the servicing channel.
You should use Windows Update for Business to manage the upgrade from Windows 10, version 1803 to Windows 10, version 1809.
The best solution is to use Microsoft Intune with co-management enabled in ConfigMgr. This solution will deliver a cloud-based MDM with support for iOS, Android, and Windows 10. This will also enable the organization to transition workloads for Windows 10 from ConfigMgr to Microsoft Intune. The existing devices enrolled in MDM for Office 365 can also be assigned EMS licenses and can be converted to Intune.
Chapter summary
There are two MDM solutions that you can deploy with Microsoft 365: standalone Intune and MDM with Microsoft 365.
Cloud-based MDM solutions can reduce on-premises server infrastructure, but network bandwidth needs to be sized appropriately.
Policy conflicts should be reviewed and addressed as part of your planning phase for implementing Intune.
Setting an MDM authority is a requirement for managing devices with Intune, but is configured by default to Microsoft Intune for new tenants.
The MDM authority can be changed when moving between MDM solutions.
There are predefined device enrollment restrictions with Microsoft Intune.
You should be familiar with the enrollment restrictions interface in Microsoft Intune, including where to create restrictions.
You should be familiar with the priority system used by enrollment restrictions and how to assign them to devices.
You should be familiar with the subscription requirements for Microsoft Intune and Azure AD, along with the supported platforms for compliance policies.
You should be familiar with the fundamentals of a compliance policy, how they are assigned to devices, and how a device is marked for compliance.
You should have some understanding on what rules a device-compliance policy can check for and use cases that align with those rules.
You should be familiar with the conditional access conditions and how they correspond to the policies you create.
You should be familiar with the conditional access controls available in the Azure portal, how these controls relate to each other, and how to design policies using these controls.
You should be familiar with device-based and app-based policies, including how they are defined and what role they play in policy design.
You should be familiar with navigating the New Conditional Access Policy blade, including items like named locations and terms of use.
You should be familiar with how to create, assign, and enforce conditional access policies for users and groups.
You should be familiar with navigating the Device Compliance blade, with a focus on the available compliance configurations settings and relative use cases for changing the default values.
You should be familiar with how to create, assign, and evaluate device-compliance policies. Keep in mind that compliance policies are created on a per-platform basis and are used by conditional access policies when referencing compliance status.
You must be familiar with the terminology used to describe WaaS. This includes terms such as feature updates, quality updates, and deployment rings.
You must be familiar with servicing channels and how they operate. This includes the available channels and configuration options.
You must be familiar with WUfB and its importance in supporting the WaaS model.
You must be familiar with the different deployment methods and what their capabilities are. This includes traditional deployments, in-place upgrades, and modern servicing.
You must be familiar with the Windows 10 in-place upgrade. This includes planning considerations, requirements, and solutions for deployment.
You must be familiar with modern servicing. This includes understanding the differences between servicing and in-place upgrades, the limitations, and the various solutions that can enable modern servicing.
You must be familiar with what upgrade readiness can provide and how it is implemented.
You must be familiar with the upgrade readiness workflow. This includes the different blades and the information they provide.
You must be familiar with each of the security features included with Windows 10. This includes an understanding of their capabilities and possible use cases.
You should be familiar with MSfB, including how to navigate the management portal, add apps, and connect it with Intune for centralized management.
You should be familiar with app deployment prerequisites. This includes conditional requirements depending on the needs of an organization.
You should be familiar with creating and assigning apps in Intune. This includes navigating the client app blades in the Intune console.
You should have a basic understanding of device health and upgrade readiness, including their requirements and capabilities.
You should be familiar with the capabilities of device profiles and the use cases they address. This includes platform support and profile types.
You should be familiar with using the portal to create and assign device profiles.
You should be familiar with the requirements for app protection policies, with an emphasis on the required subscriptions and supported platforms.
You should be familiar with navigating through the app protection policy blades, along with the extensive number of controls available for managing and securing app data.
You should be familiar with the prerequisites and setup process required to activate the MSfB for an organization.
You should be familiar with navigating the MSfB management portal, including searching for new apps in the Microsoft Store and adding them to an organization’s app inventory.
App collections and app visibility in the private store are managed through the MSfB portal, from the Private Store page.

