Lesson 15
Manage System Resources
Goals
 Explore and understand macOS file layout
Explore and understand macOS file layout Discover common system files, their location, and their purpose
Discover common system files, their location, and their purpose Describe System Integrity Protection
Describe System Integrity Protection Manage font resources
Manage font resources
The macOS system files are streamlined and organized in a layout that is easy to manage and provides strong security. This lesson focuses on the composition and organization of the files and folders that make up macOS.
As covered in Reference 11.1, “File Systems,” macOS Monterey uses a read-only signed system volume (SSV) to protect macOS system software. The read-write APFS Data volume is usually named Macintosh HD - Data or Data and is mounted at /System/Volumes/Data in a way that preserves the appearance of a single volume. macOS uses firm links so that when you use the Finder to open /Applications, for example, the Finder displays the contents of both /Applications (from the read-only snapshot of the APFS System volume) and /System/Volumes/Data (from the read-write APFS Data volume).
Reference 15.1 macOS File Resources
If you open the root (beginning) of the file system from the Finder, the Finder displays four default visible folders: Applications, Library, System, and Users. If you use Terminal to examine the root of the file system, you’ll discover more items.
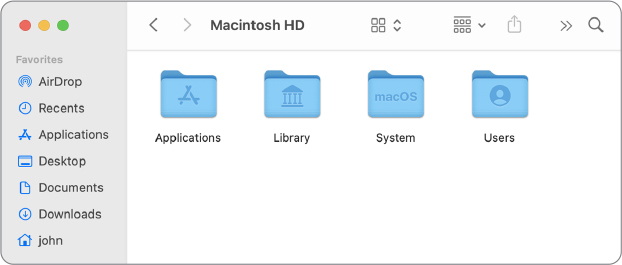
Here are descriptions of the default system root folders that the Finder displays:
 Applications—Often called the local Applications folder, this is the default location for apps available to local users. Only administrator users can make changes to the contents of this folder.
Applications—Often called the local Applications folder, this is the default location for apps available to local users. Only administrator users can make changes to the contents of this folder. Library—Often called the local Library folder, this is the default location for ancillary system and app resources available to users. Only administrator users can make changes to the contents of this folder.
Library—Often called the local Library folder, this is the default location for ancillary system and app resources available to users. Only administrator users can make changes to the contents of this folder. System—This folder contains resources required by macOS for primary functionality. With System Integrity Protection (SIP) enabled by default in macOS, no user or process can make changes to most of the content of the System folder. Details regarding SIP are covered later in this lesson.
System—This folder contains resources required by macOS for primary functionality. With System Integrity Protection (SIP) enabled by default in macOS, no user or process can make changes to most of the content of the System folder. Details regarding SIP are covered later in this lesson. Users—This is the default location for local user home folders. Lesson 8, “Manage User Home Folders,” covers this topic in greater detail.
Users—This is the default location for local user home folders. Lesson 8, “Manage User Home Folders,” covers this topic in greater detail.
Library Resources
macOS-specific system resources are stored in Library folders throughout the system volume. A system resource is a resource that is not a general-use app or a user file. The Library folder keeps user and system resources organized and separated from the items you use every day.
You should be familiar with these system resources:
 Application Support—This folder is in the user and local Library folders. Any ancillary data needed by an app might be in this folder. For example, it often contains help files or templates for an app.
Application Support—This folder is in the user and local Library folders. Any ancillary data needed by an app might be in this folder. For example, it often contains help files or templates for an app. Containers and Group Containers—These folders contain resources for sandboxed apps. There is more information about these folders later in this section.
Containers and Group Containers—These folders contain resources for sandboxed apps. There is more information about these folders later in this section. Extensions—Kernel extensions (kexts) and third-party kernel extensions (sometimes referred to as legacy system extensions, legacy kernel extensions or deprecated kernel extensions) are found only in the /Library and /System/Library folders. Kernel extensions are low-level drivers that attach themselves to the kernel, or core, of the operating system, and that provide driver support for hardware, networking, and peripherals. Kernel extensions load and unload automatically; they’re are covered in greater detail in Lesson 9.9, “Approve Third-Party Kernel Extensions.”
Extensions—Kernel extensions (kexts) and third-party kernel extensions (sometimes referred to as legacy system extensions, legacy kernel extensions or deprecated kernel extensions) are found only in the /Library and /System/Library folders. Kernel extensions are low-level drivers that attach themselves to the kernel, or core, of the operating system, and that provide driver support for hardware, networking, and peripherals. Kernel extensions load and unload automatically; they’re are covered in greater detail in Lesson 9.9, “Approve Third-Party Kernel Extensions.” Fonts—Fonts are files that describe typefaces used for both screen display and printing. Font management is covered later in this lesson.
Fonts—Fonts are files that describe typefaces used for both screen display and printing. Font management is covered later in this lesson. Frameworks—Frameworks are repositories of shared code used among different parts of the operating system or apps. Frameworks load and unload automatically. You can view your Mac computer’s currently loaded frameworks with System Information.
Frameworks—Frameworks are repositories of shared code used among different parts of the operating system or apps. Frameworks load and unload automatically. You can view your Mac computer’s currently loaded frameworks with System Information. Keychains—Keychains are used to securely store sensitive information, including passwords, certificates, keys, Safari AutoFill information, and notes. Keychain technology is covered in Lesson 9, “Manage Security and Privacy.”
Keychains—Keychains are used to securely store sensitive information, including passwords, certificates, keys, Safari AutoFill information, and notes. Keychain technology is covered in Lesson 9, “Manage Security and Privacy.” LaunchDaemons and LaunchAgents—These define processes that start with the launchd process. macOS uses many background processes that are started by launchd. LaunchAgents are used for processes that need to start up only when a user is logged in, whereas LaunchDaemons are used to start processes that always run in the background, even when no users are logged in. More about launchd can be found in Lesson 28, “Troubleshoot Startup and System Issues.”
LaunchDaemons and LaunchAgents—These define processes that start with the launchd process. macOS uses many background processes that are started by launchd. LaunchAgents are used for processes that need to start up only when a user is logged in, whereas LaunchDaemons are used to start processes that always run in the background, even when no users are logged in. More about launchd can be found in Lesson 28, “Troubleshoot Startup and System Issues.” Logs—Many system processes and apps record progress or error messages to log files. You can inspect log files using Console.
Logs—Many system processes and apps record progress or error messages to log files. You can inspect log files using Console. PreferencePanes—PreferencePanes are used by System Preferences to provide interfaces for system configuration. Using System Preferences is covered in Lesson 3, “Set Up and Configure macOS.”
PreferencePanes—PreferencePanes are used by System Preferences to provide interfaces for system configuration. Using System Preferences is covered in Lesson 3, “Set Up and Configure macOS.” Preferences—Preferences are used to store system and app configuration settings. Every time you configure a setting for any app or system function, it is saved to a preference file. Because preferences play such a critical role in system functionality, troubleshooting preference files is covered separately in Lesson 20, “Manage and Troubleshoot Apps.”
Preferences—Preferences are used to store system and app configuration settings. Every time you configure a setting for any app or system function, it is saved to a preference file. Because preferences play such a critical role in system functionality, troubleshooting preference files is covered separately in Lesson 20, “Manage and Troubleshoot Apps.”
Resource Hierarchy
Library folders are in separate domains: user, local, network, and system (network domains are legacy and outside the scope of this guide). Segregating resources into domains provides increased administrative flexibility, resource security, and system reliability. With resource domains you can choose to allocate certain resources to all users or just specific users. Standard users can add resources to their own home folder only and cannot access other users’ resources.
The system resource domains are, in order:
 User—Each user has their own Library folder in the home folder for resources. When resources are placed here, only the user has access to them. The user’s Library folder is hidden by default to prevent users from accidentally making changes that could be detrimental. Many apps and processes continue to rely on this location for resources.
User—Each user has their own Library folder in the home folder for resources. When resources are placed here, only the user has access to them. The user’s Library folder is hidden by default to prevent users from accidentally making changes that could be detrimental. Many apps and processes continue to rely on this location for resources. Local—Both /Applications and /Library are part of the local resource domain. Any resources placed in these two folders are available to all local user accounts. By default, only administrator users can make changes to local resources.
Local—Both /Applications and /Library are part of the local resource domain. Any resources placed in these two folders are available to all local user accounts. By default, only administrator users can make changes to local resources. System—The system domain encompasses the items necessary to provide core system functionality. This includes an app folder located at /System/Library/CoreServices/Applications. Many hidden items at the root of the system volume also make up the system resource domain, but the only one the Finder displays is the /System/Library folder. With SIP enabled, no user or process can modify most of the /System folder.
System—The system domain encompasses the items necessary to provide core system functionality. This includes an app folder located at /System/Library/CoreServices/Applications. Many hidden items at the root of the system volume also make up the system resource domain, but the only one the Finder displays is the /System/Library folder. With SIP enabled, no user or process can modify most of the /System folder.
With different domains containing resources, multiple copies of similar resources may be available to the Mac and user. macOS handles this by searching for resources from the most specific (those in the user domain) to the least specific (those in the system domain). The following graphic represents the order in which resource contention is resolved from a user’s home folder (1) to the System folder (3).
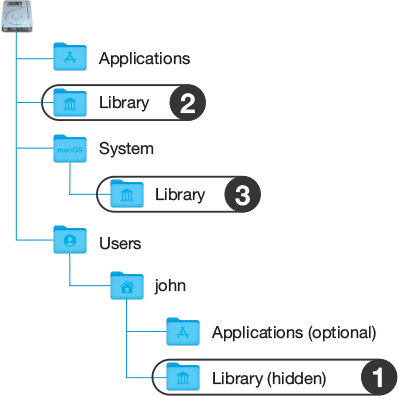
If multiple similar resources are discovered, macOS uses the resource most specific to the user. For example, if two versions of the font Times New Roman are found—one in the local Library and one in the user’s Library—macOS uses the copy of the font in the user’s Library.
App Sandbox Containers
App sandbox containers enhance running-app security. Sandboxed apps are allowed access only to the specific items they need to function. Most apps built into macOS and apps from the App Store are sandboxed apps.
Sandboxed apps can access special folders that are referred to as containers. macOS manages the content of these containers to ensure that an app isn’t allowed access to other items in the file system. A user opening a document outside of an app container is the only way a sandboxed app is allowed access outside of its container.
App containers are in ~/Library/Containers. When a sandboxed app starts up the first time, macOS creates a container folder for the app if it doesn’t exist already, named with its bundle identifier. The bundle identifier identifies an app by its creator and app title. For example, the container folder for News is ~/Library/Containers/com.apple.News. The Finder may display the container with the app’s name and custom icon.
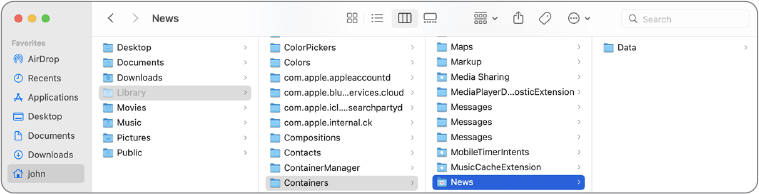
The root content of an app container is a hidden property list file (with the extension .plist) containing app information, a Data folder, and possibly an OldData folder. The Data folder is the app’s current active container. Any OldData folder you find contains previously used app items. The content of the Data folder mostly mimics the user home folder, but with one key distinction: it contains only the items that the app is allowed to access.
Items created and managed by the sandboxed app are the only original items in the container Data folder. If a user enables iCloud Drive, you might also find a CloudKit folder for maintaining items stored in iCloud.
Items that originated from other apps or a user’s file-opening action are represented as symbolic links that point to the original item outside of the container. macOS creates these symbolic links when the user opens an item in the sandboxed app. With external items represented in this way, an item can stay in its original location while also being accessible to a sandboxed app that can access only its own container.
App Group Containers
Although a user can allow sandboxed apps to access files beyond the app container, sandboxing prevents apps from doing this automatically. To facilitate sharing app resources automatically, developers of sandboxed apps can request that macOS create a shared app group container.
The ~/Library/Group Containers folder contains shared app containers. When a sandboxed app starts up the first time and requests access to share app resources, macOS creates a group container folder for the app, named with its bundle identifier.
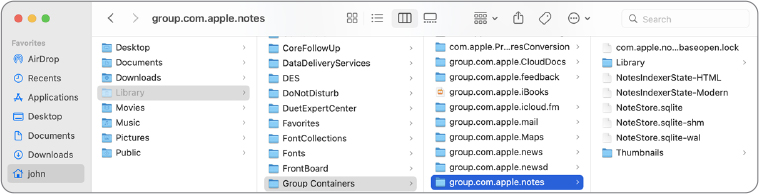
Unlike app sandbox containers that simulate an entire user home folder, app group containers hold only items to be shared between apps. Using Notes as an example, in the previous screenshot the Finder displays the NoteStore database and other files. In this instance, the Notes data is shared so that other apps can access user note entries. macOS controls access to this to ensure that only Apple-verified processes can access the user’s Notes database.
Troubleshoot System Resources
You may experience an error message calling out an issue with a specific item, but you may also experience a situation where the item appears to be missing. macOS ignores a system resource if it determines that the resource is corrupted or missing. Replace the suspect or missing item with a working copy.
When troubleshooting system resources, remember the resource domain hierarchy. Using fonts as an example, you may load a version of a font in the local Library folder as required by your workflow to operate properly. In spite of this, a user may load another version of the same font in their home folder. In this case, the user might experience workflow problems even though it appears that they are using the correct font.
Logging in with another account is a quick way to determine whether the problem is in the user’s home folder. You can also use System Information to list active system resources. System Information shows the file path of the loaded system resources, so you can spot resources that are loading from the user’s Library.
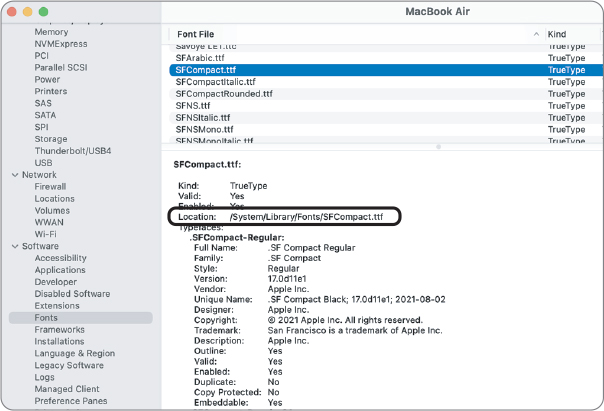
Reference 15.2 System Integrity Protection
In macOS Monterey, the SSV is a read-only APFS snapshot of the read-only APFS System volume, which provides a layer of protection. System Integrity Protection (SIP) further protects your Mac by helping to prevent potentially malicious software from modifying protected files and folders. SIP restricts the System Administrator account (the root user account) and limits the actions that the root user can perform on protected parts of the Mac operating system.
SIP includes protection for these parts of macOS that are already part of the read-only SSV mounted at /:
 /System
/System /usr
/usr /bin
/bin /sbin
/sbin
SIP also protects portions of macOS that are part of the read-write APFS Data volume mounted at /System/Volumes/Data:
 Apps that are preinstalled with macOS (including /System/Volumes/Data/Applications/Safari.app)
Apps that are preinstalled with macOS (including /System/Volumes/Data/Applications/Safari.app) /private/var/db/ConfigurationProfiles
/private/var/db/ConfigurationProfiles
Third-party apps and installers can continue to write to the following paths in the read-write volume:
 /Applications (/System/Volumes/Data/Applications)
/Applications (/System/Volumes/Data/Applications) /Library
/Library /usr/local
/usr/local
SIP allows only processes that are signed by Apple with special entitlements to modify parts of your Mac that are protected by SIP. For instance, Apple software updates and Apple installers are allowed to write to system files.
SIP also helps ensure that only a user, and not malicious software, can change a startup disk.
If you upgrade from an earlier version of macOS, the installer might move an item aside if it conflicts with SIP.
Older peripheral and printer driver software may be impacted by SIP. If you discover that a third-party product is impeded by SIP, contact the developer to provide a version compatible with macOS Monterey.
You can disable SIP by using the csrutil command (Configurable Security Restrictions) when your Mac is started from the recoveryOS; however, doing so greatly reduces the security of data on your Mac. The setting is saved to the Mac computer’s firmware, so resetting the parameter RAM of an Intel-based Mac enables SIP again. It’s also possible that a software update will reenable SIP.
If SIP is disabled, the root user has access to any file in the APFS Data volume that isn’t protected by privacy protections, including third-party apps that run as the root user. Malicious software can obtain root-level access if a user enters an administrator name and password to install the software. This would allow the software to modify or overwrite any system file or app. It’s best practice to keep SIP enabled at all times.
To prevent an unauthorized user from disabling SIP, you can secure how your Intel-based Mac starts up, including setting a computer firmware password to disallow starting from the recoveryOS, as detailed in Reference 5.3, “Secure Startup.”
For more information about SIP, refer to Apple Support article HT204899, “About System Integrity Protection on your Mac.”
Reference 15.3 Manage Font Resources
One way to experience the system resource domain hierarchy is by managing fonts. macOS has advanced font-management technology that enables the use of a nearly unlimited number of fonts of nearly any font type, including bitmap, TrueType, OpenType, and PostScript fonts.
Fonts are installed in the Font folders in the Library folders throughout macOS. A user can manually install fonts by dragging them into ~/Library/Fonts. Administrators can install fonts for all users by dragging them into /Library/Fonts. This flexible font system enables administrators to better control font use. For example, a font vendor licensing model may grant only specific access for an individual user.
And macOS includes fonts in /System/Library/Fonts. You can’t modify the contents of that folder.
Install Fonts Using Font Book
macOS includes a font-management tool, Font Book, which automatically installs fonts for you. Font Book can also be used to organize fonts into more manageable collections, enable or disable fonts to simplify font lists, and resolve duplicate fonts. Exercise 15.1, “Manage Font Resources,” has detailed instructions for managing fonts.
Note
Third-party font-management tools may interrupt Font Book and take over font management for macOS.
macOS Monterey provides fonts in three categories:
 Fonts included with macOS Monterey—fonts installed and enabled automatically
Fonts included with macOS Monterey—fonts installed and enabled automatically Fonts available for download in macOS Monterey with Font Book—fonts you can download and enable using Font Book
Fonts available for download in macOS Monterey with Font Book—fonts you can download and enable using Font Book Fonts available for document support in macOS Monterey—fonts that are available only in documents that already use the font, or in apps that request the font by name
Fonts available for document support in macOS Monterey—fonts that are available only in documents that already use the font, or in apps that request the font by name
You can use Font Book to restore fonts that were originally installed with macOS Monterey. The following illustration highlights two features of Font Book. The command File > Restore Standard Fonts will restore the original fonts that were installed with macOS Monterey, and clicking the highlighted Download button will download and install the font Spot Mono Medium.
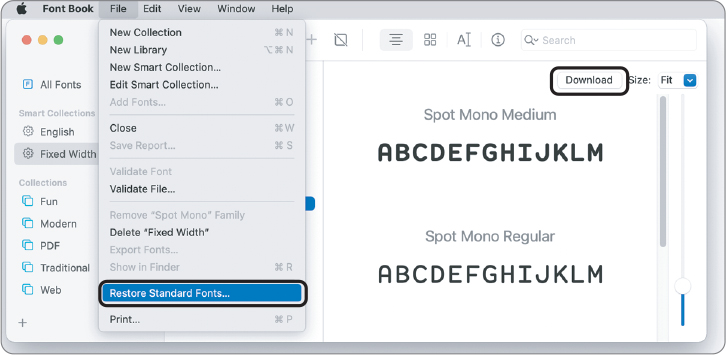
Note
If you choose Restore Standard Fonts the fonts originally installed with macOS Monterey will be restored and any additional fonts you’ve installed are uninstalled and placed in /Library/Fonts (Removed) or in ~/Library/Fonts (Removed). You can verify and reinstall them.
Exercise 15.1 Manage Font Resources
In this exercise, you validate that when a font is in /Library/Fonts, it is available to all users. You also confirm that when a font is installed in a single user’s Fonts folder, it is available only to that one user.
Add a Font
You can use Font Book to install a font that only one user of the Mac can use.
Verify that no users have Fast User Switching sessions active. If users other than John are logged in, log them out.
If necessary, log in as John Appleseed.
Open Font Book, which is in the /Applications folder.
Choose Font Book > Preferences (Command-Comma).
Ensure that Default Install Location is set to User.
Close Font Book preferences.
Switch to the Finder, then open /Users/Shared/StudentMaterials/Lesson15.
Double-click the font OpenSans-Regular.ttf.
This opens OpenSans-Regular.ttf in Font Book, which shows a preview of the font and gives you the option to install it.
Click Install Font.
If necessary, select User in the sidebar.
Open Sans is the only font that’s installed for John’s user account.
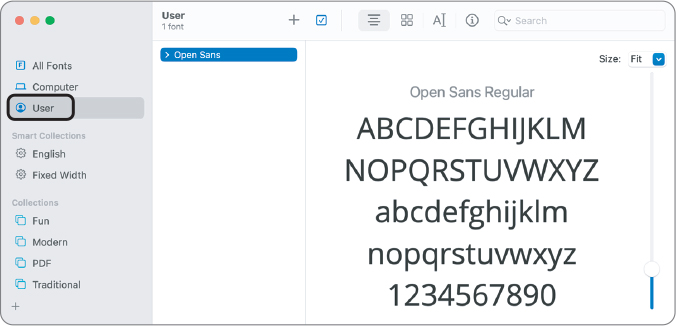
Select All Fonts from the sidebar, then scroll to find the instance of Open Sans.
Since this view shows all available fonts, including those installed for the current user and those installed for all Mac users, Open Sans appears in the list.
Control-click Open Sans, then choose Show in Finder from the shortcut menu.
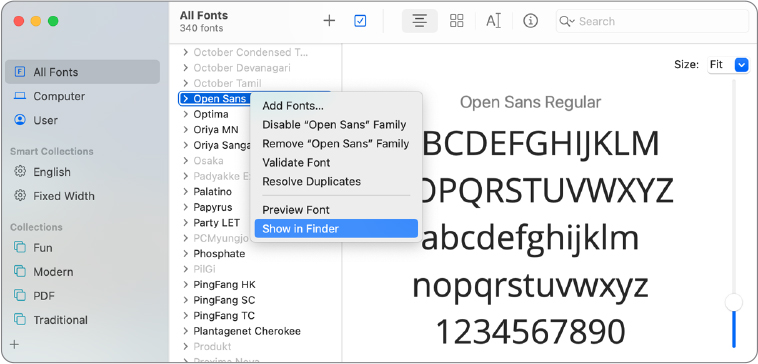
The Finder opens a window that displays the font file.
If necessary, widen the Finder window, then choose View > as Columns. You can also click the column view button in the toolbar or use the shortcut Command-3.

To verify your location, choose View > Show Path Bar.
The path bar at the bottom of the window shows that the font file is in the Fonts folder in John’s user library, previously referred to as ~/Library/Fonts, /Users/john/Library/Fonts, and Macintosh HD > Users > john > Library > Fonts. It’s the only font installed there.
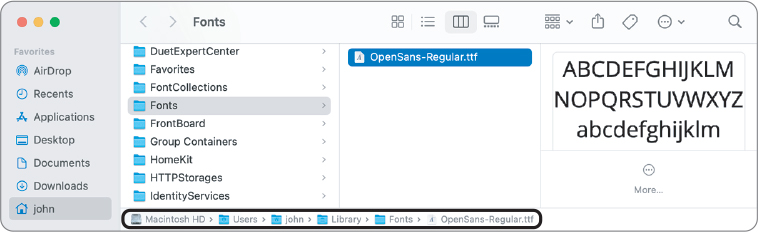
Confirm a Font Is Unavailable to Other Users
If you log in as a different user, even as an administrator, you don’t have access to the fonts in John’s Fonts folder.
Use Fast User Switching to switch to the Local Administrator account.
Open Font Book, then look for the Open Sans font.
Open Sans doesn’t appear in Font Book for the Local Administrator account. At this time, you could add Open Sans to this account, just as you added it to John’s account. You would have to copy the font file to a location that Local Administrator can access or install it to the location for all users, /Library/Fonts.
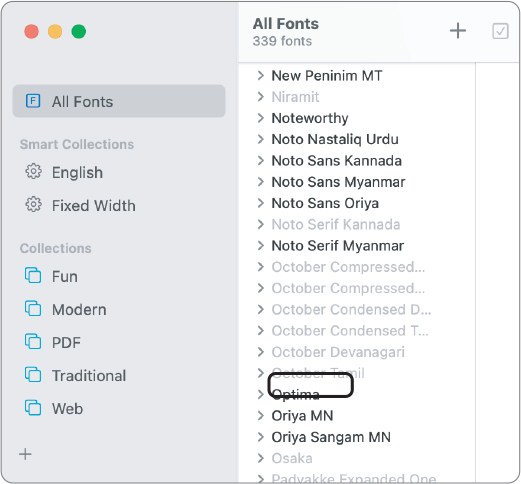
Quit Font Book.
Log out of Local Administrator.
Make a Font Available to Other Users
Move Open Sans to the Fonts folder for all users.
Log in as John Appleseed, then, if necessary, open Font Book.
Control-click Open Sans and choose Remove “Open Sans” Family.
In the dialog that appears, click Remove.
Open Sans is removed from John’s Fonts folder (/Users/john/Library/Fonts) and placed in the Trash.
Choose Font Book > Preferences (Command-Comma), then change Default Install Location to Computer.
Close Font Book preferences.
Switch to the Finder, then open /Users/Shared/StudentMaterials/Lesson15.
Double-click the font OpenSans-Regular.ttf.
Click Install Font.
Authenticate as Local Administrator.
In Font Book, control-click Open Sans, then choose Show in Finder from the shortcut menu.
The Finder opens a window that displays the font file. Notice that in the path bar, Open Sans is now installed in /Library/Fonts, which makes it available to all users.
Disable a Font
Use Font Book to watch what happens when you disable a font.
Switch back to Font Book.
Locate Open Sans in the Font column.
Select Open Sans, then click the Disable button in the toolbar.
In the confirmation dialog, click Disable.
This disables the font. Confirm that the word Off appears next to the Open Sans font in Font Book.
In the Finder, navigate to the folder /Library/Fonts.
Observe that the font Open Sans is still in the folder.
Disabling a font in Font Book does not remove it from its installed location. Even though the font is disabled for use, Font Book shows a real-time display of the fonts in the macOS search path.
Validate Fonts
Because you changed your font configuration, you use Font Book to check your new setup.
In the Font Book window, select All Fonts in the sidebar, click any font in the Font column, then press Command-A to select all fonts.
Choose File > Validate Fonts.
Font Book reads and validates the font files, then checks for corruption.
When the validation scan finishes, quit Font Book.
Log out as John Appleseed.
