What is now commonly referred to as digital forensics is a profession that was once made up of unstructured processes, custom home-grown toolsets, and knowledge based on the collective work of hobbyists. Over the past 50 years, the profession of digital forensics has evolved significantly alongside technological advancements to become a mature discipline where a common body of knowledge (CBK)—made up of proven scientific principles, methodologies, and techniques—has brought about a globally adopted level of standardization and formal structure.
While it is relatively well known that there are legal aspects involved with digital forensics, most people are surprised to learn that the profession involves a great deal of scientific principles, methodologies, and techniques. Not only does digital forensics require a significant amount of specialized training and skills to properly apply these scientific fundamentals, digital forensics is also somewhat of an art form where analytical experience comes into play.
The Role of Technology in Crime
In relation to crime, technology can play multiple roles that in turn produce many types of digital artifacts that can be used as digital evidence. Depending on how much digital evidence is contained within any given piece of technology, it may or may not be authorized for seizure and subsequent collection of evidence as part of an investigation. In any case, when technology plays a role in criminal activity, it is much easier to justify its seizure so evidence can be processed.
Through the years, several authors have tried to develop a standard classification scheme for the distinct roles technology can play in crime. In the 1970s, Donn Parker was one of the first individuals to recognize the potential seriousness of technology-relates crimes which led him to create the following four categories which remain relevant today:
1. Object of Crime applies when technology is affected by the crime (e.g., when a device is stolen or damaged).
2. Subject of Crime applies when technology is in the environment in which the crime was committed (e.g., system infected by malware).
3. Tool of Crime applies when technology is used to conduct or plan crime (e.g., illegally forged documents).
4. Symbol of Crime applies when technology is used to deceive or intimidate (e.g., falsified investment profits).
Distinguishing when technology plays one role or another is important on many levels. For example, knowing when technology is an object or subject is important because, from the perspective of the practitioner, this demonstrates intent of the perpetrator. Also, when technology is a tool, like a gun or other weapon, this could lead to additional charges or increased punishment. However, although technology as a symbol may seem irrelevant because no actual system is involved in the crime, when categorized under this role technology is represented as an idea, belief, or any entity that can be useful in understanding motivations for committing the crime. As an example, CEOs are a symbol of their organization and as such can become either the victim or target of crime because of what they symbolize.
In 1994, the U.S. Department of Justice (USDOJ) developed their own categorization scheme that made a clear distinction between hardware, being physical components, and information, being data and programs that are stored or transmitted. It is important to note that with a single crime there is the potential to fall into one or more of these categories; for example, when a system is used as the instrument of crime, it may also contain information as evidence. The categories proposed by the USDOJ include:
• Hardware as Contraband or Fruits of Crime (i.e., any item that is illegal to be possessed or was obtained illegally)
• Hardware as an Instrumentality (i.e., when technology played a role in committing the crime; such as a gun or weapon)
• Hardware as Evidence (i.e., scanners with unique characteristics that can be used and linked to the creation of digitized content)
• Information as Contraband or Fruits of Crime (i.e., computer programs that can encrypt content to conceal evidence)
• Information as an Instrumentality (i.e., programs used to break into other systems)
• Information as Evidence (i.e., digital artifacts revealing a user’s activities on a system)
In 2002, the USDOJ updated their categorization scheme as part of their publication titled Searching and Seizing Computers and Obtaining Electronic Evidence in Criminal Investigations. The most notable difference in the updated categorization was the realization that data and program content, not the hardware, are usually the target of the crime; but even when information is the target it may be necessary to collect the hardware.
History of Digital Crime and Forensics
Information technology has been involved in criminal activities for more than half of a century. Dating as far back as the 1960s, computer crimes were first committed as either physical damage or as sabotage to computer systems. But when technology first arrived, most people did not think that it would one day become such an integral part of our everyday lives. If history has taught us anything, it’s that as information technology advances there will always be new and evolved digital crimes.
With the growing commercialization of technology and the expansion of the Internet, computer crimes continue to take the next step in an ever-evolving threat landscape. Moving forward from the 1970s and into the new millennium, computer crimes expanded from just damage and sabotage to digital crimes such as fraud, denial of service (DoS), SPAM, advanced persistent threats (APT), and extortion.
From the 1960s to 1980s, computers were owned and operated by corporations, universities, research centers, and government agencies. Computers were used primarily as industrial systems largely supporting data processing functions and were, for the most part, not connected to the outside world. Responsibility for securing these computer systems was left to administrators who would perform routine audits to ensure the efficiency and accuracy of the data processing functions. These activities were essentially the first systematic approach to a computer security discipline.
It was during this time that the computer first became a point of interest to the information security, legal, and law enforcement communities. Several government agencies started creating small ad hoc groups of individuals who were then provided with basic training on computer systems. These “investigators” would work with administrators to gather information from the computer systems to be used as evidence in criminal matters.
In 1968, in Olympia, Washington, an IBM 1401 Data Processing System was shot twice by a pistol-toting intruder.
Following closely behind in February 1969, the largest student riot in Canada ignited when police were called in to stop a student occupation of several floors of the Hall Building at Concordia University. When the police arrived to control the protest, a fire broke out, resulting in computer data and university property being destroyed. The damages totaled $2 million, and 97 people were arrested.
Prior to the 1980s, computer crimes were largely dealt with under existing laws. However, in response to an increasing number of computer crimes, law enforcement agencies began establishing new laws to address computer crimes. The first computer crime law, the Florida Computer Crimes Act, was created in 1978 to address fraud, intrusion, and all unauthorized access to computer systems. The evolution of crime into computer systems during this time led to new terms such as computer forensics, forensics computer analysis, and forensics computing.
With the arrival of the IBM personal computer (PC), there was a sudden explosion of computer hobbyists around the world. These PCs had very few applications and were not user friendly, which enticed hobbyists to write program code and access the internals of both the hardware and operating system (OS) to better understand how they worked. Amongst the hobbyists were individuals from law enforcement, government agencies, and other organizations who collectively shared their understanding of computer systems and how technology could play a larger role as a source of evidence. Much of the time and money spent by these individuals to learn about these modern technologies was done of their own accord because their respective agencies did not necessarily support their efforts.
Investigations performed by these pioneers were rudimentary from today’s perspective. The Internet was not yet widely available for consumer use, which limited the scope of most investigations to data recovery on standalone computer systems. Cyber criminals mostly consisted of a mix of traditional criminals who used technology to support their activities (e.g., phreaking) and people who used their technical skills to illegally access other computers.
During this time, there were very few tools available, which left investigators to either build their own or use available data protection and recovery applications to perform analysis. Additionally, the only means of preserving evidence was taking logical backups of data onto magnetic tape, hoping that the original attributes were preserved, and restoring the data to another disk, where analysis was performed using command-line utilities.
Throughout the 1990s, forensics tools began to emerge from both the hobbyists (e.g., Dan J. Mare’s Maresware, Gord Hama’s RCMP Utilities) and larger software vendors (e.g., Norton’s Utilities, Mace Utilities). These applications and software suites were developed to solve specific forensics activities (e.g., imaging, file recovery) and proved to be powerful tools for the computer forensics practice.
As technology became more widely available and reports of different types of computer crimes were becoming more widely known, law enforcement agencies around the world started responding by enacting laws similar to that passed by Florida. In 1983, Canada was the first to respond by amending their criminal code to address computer crimes. Following their lead, several other nations began implementing legislation in response to computer crimes, including the 1984 U.S. Federal Computer Fraud and Abuse Act, the 1989 amendment of the Australian Crimes Act to include Offenses Relating to Computers, and the 1990 British Computer Abuse Act.
Parallel to the establishment of computer laws, interest in the forensics community was growing, as was its popularity. Agencies recognized that many forensics investigations were performed by individuals who had minimal training, operated on their own terms, used their own equipment, and did not follow any formal quality control. From this, efforts began to create a CBK of principles, methodologies, and techniques that could be applied to standardize and bring formal structure to computer forensics.
The next decade proved to be a major step forward in the maturity of digital forensics. Technology quickly became pervasive amongst consumers, where it was embedded in many facets of our daily lives, which drove significant technology innovation (e.g., mobile devices). Plus, the Internet had gained enough momentum for it to become more readily available for use in homes and businesses, introducing personal accessibility to email and web browsing.
Accompanied by these advances in technology was the opportunity for criminals to commit new cybercrimes. An example of this opportunity being made available through technology occurred following the events on September 11, 2001, when investigators realized that digital evidence of the attack was recoverable on computers located across the world. This revelation reinforced the fact that criminals were using technology in the same ubiquitous ways as the everyday consumer.
From the technology-sponsored growth of digital crime, the term computer forensics became increasing challenging to use because both crimes and evidence could now be found throughout networks, printers, and other devices. In 2001, the first annual Digital Forensics Research Workshop (DFRWS) recognized that computer forensics was considered a specialization and proposed the use of the term digital forensics to describe the discipline as a whole.
Expansion of the field into the all-encompassing digital forensics resulted in the creation of specializations for investigating different technologies. In addition to the traditional computer forensics becoming a concentration, there was the introduction of network forensics and mobile forensics. However, with the formation of these specializations came increased technical sophistication and legal scrutiny over requirements to follow standardized principles, methodologies, and techniques.
The formalization of digital forensics led to the first publication of standardized principles being issued between 1999 and 2000 from the combined work of the International Organization on Computer Evidence (IOCE), the G-8 High Tech Crime Subcommittee, and the Scientific Working Group on Digital Evidence (SWGDE). Likewise, forensics tools evolved from simple home-grown applications used by hobbyists into sophisticated commercial suites of tools. At the same time, the digital forensics community continued to mature, with professional certification programs being created not only to recognize individuals with the appropriate knowledge and experience but also to acknowledge laboratory environments that met the requirements of forensic science principles, methodologies, and techniques.
Due to the academic preparation required and formal training requirements, the maturity of digital forensics has grown exponentially to a point where it is now recognized by the information security profession as a core skill area. Colleges and universities have recognized the popularity and appeal of digital forensics, which has led to the creation of numerous academic and professional education programs around the world. Furthermore, the number of international conferences dedicated to the field of digital forensics continues to increase as the integration of digital forensics with other professions evolves.
During this time, the American Academy of Forensic Sciences (AAFS), one of the most widely recognized professional organizations for establishing the forensics disciplines, created a new section specific to digital and multimedia sciences (DMS). This development led to a major advancement in recognizing digital forensics as a scientific discipline by providing a common foundation for specialized groups of people who can share knowledge and address current forensics challenges.
Technology has now reached a point in its evolution where almost every device has some type of storage medium and can, in some fashion, be connected to the Internet. Naturally this has driven the development of systems and applications that are increasingly adaptive and accessible from virtually anywhere and, if not secured properly, by anyone. Capitalizing on technology’s modern pervasiveness, cybercriminals once again have expanded their portfolio to incorporate new and sophisticated attacks such as varying levels of phishing campaigns (e.g., spear, whaling, cloning), advanced persistent threats (APT), and even cyber espionage.
With the change in cyberattacks comes new ways that digital evidence is created, gathered, and processed. Adapting to the new wave of digital evidence sources, commercial software suites began to transform from offering functionality specific to digital forensics and now benefit other professions where digital forensics is used. Including professions like cybersecurity, electronic discovery (e-discovery), and incident response, digital forensics has become an underlying foundation driving several information security disciplines.
The digital forensics discipline has come a long way in the past 50 years. What started out as a hobby made up mostly of home-grown tools and quite often insufficient processes has arrived at a convergence of various law enforcement organizations and intelligence agencies in which everybody is following the same consistent principles, methodologies, and techniques.
Predicting what the future holds for digital forensics is not overly challenging. Rather, if history has taught us anything about how the past has shaped what digital forensics is today, the most realistic and accurate prediction that can be made is this: every person and group involved with digital forensics today will have some type of influence on what the future brings.
For the most part, digital forensics has become what it is today because of the tactical influences that have consistently driven its development and maturity, such as technology advancements, creation of commercial tools, and integration with other professions. On the other hand, while the list of strategic influences might be somewhat smaller, the alignment to forensic science and subsequent creation of principles, methodologies, and techniques to abide by brought about a standardization and formality to the structure of digital forensics. There are also influences that exist in both tactical and strategic realms that should be considered for the future of digital forensics, for example:
• The continued development of the CBK based on research, knowledge, and experiences of the digital forensics community. At the end of the day, the digital forensics investigators of the future will be better trained and educated because the CBK that was established before them will be extensive and readily available. Organizations will need to ensure that they employ digital forensics professionals who not only are accredited to conduct digital forensics investigations, but also have strong business and technical qualities.
• Historically, advancements introduced innovative ways for technology to be used as either the fruit, tool, or instrument of crime, resulting in an evolution in how digital forensics has been used to investigate these crimes. Until recently, cybercrime was traditionally committed with a focus primarily on content (e.g., data exfiltration) and done so with little context (e.g., where attacks are being perpetrated). Naturally, cybercriminals of the future will be better trained, funded, and organized to the point that the value of their collective efforts will be realized, resulting in heightened situational awareness involving their attacks.
• To counter the evolving threat landscape, commercial digital forensics tools will need to evolve to be able to:
• Easily adapt with the ever-growing volumes of data that need to be analyzed
• Further automate known, verified, and validated analytic functions to alleviate manual processing time and reduce error probability
• Understand and interpret both the content and context of human language and communications for better analytical results
• Given the fact that some investigations encompass an international scope, such as data residing under multiple jurisdictions, laws and regulations must evolve to enable a global standard for digital forensics.
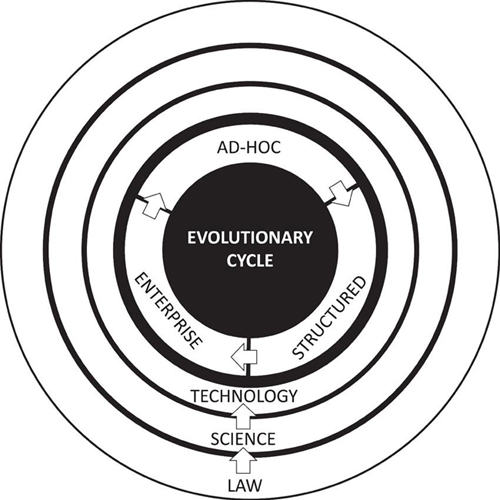
Evolutionary Cycle of Digital Forensics
Digital forensics has become the scientific discipline it is today because of the work done by all those involved since its inception back in the 1970s. Driving structure and maturity in the discipline and community is the product of influences both tactical, such as technology advancements, and strategic, such as the creation of global working groups dedicated to digital forensics.
If we’ve learned anything about how the past activities have shaped digital forensics into what it is today, the best and most educated prediction is that history will repeat itself. This doesn’t mean that the digital forensics profession will revert to the way it was in the 1970s; rather the maturity of the discipline will be subject to continuous improvement transformations that follow a cyclical methodology like the one illustrated in Figure 1.1.
Figure 1.1 Digital forensics evolutionary cycle.
The ad hoc phase is the starting point in the continuous transformation of the digital forensics discipline. Also referred to as pre-forensics or proto-forensics, this phase is characterized by the absence of structure, ambiguous goals, and an overall lack of tools, processes, and training. This phase can be related to the time from the 1970s and into the mid-1980s.
Looking back at the history of digital forensics and crime, it is evident that both technology advancements and legal precedence are the major contributors to any type of evolution relating to the digital forensics discipline. Generally, the term ad hoc refers to the methodology via which something new has been created (e.g., law) and because of this the approach is disorganized or not theory driven. This is not to say that we ignore everything that came previously and start anew, but that with new developments in technology there is a need to circle back to ensure structure is provided in terms of digital forensics capabilities.
The structured phase is the next step in the continuous transformation of digital forensics, as seen from the mid-1980s into the 1990s. This phase is characterized by the development of complex solutions that bring harmony and structure to processes and tools that were identified as challenges faced during the ad hoc phase. Elements specifically addressed during this phase include:
• Establishment of policy-based programs (i.e., laws, regulations);
• Definition and coordination of processes that align with established policies; and
• Requirements for forensically sound tools.
First, for investigative processes to be clearly defined and documented there need to be policies in place, such as laws and regulations, to establish a foundation from which to work. In turn, these policies drive the need to legitimize processes and tools to ensure they are consistently applied to warrant repeatable and reproducible outcomes. Ultimately, if the tools used cannot consistently reproduce results, their legitimacy can be called into question and the viability of evidence gathered or processed cannot be guaranteed. All things considered, for processes and tools to produce credible evidence that is forensically sound requires them to be:
• Verifiable as authentic to the original source data;
• Collected and preserved in a manner that preserves their integrity; and
• Analyzed using tools and techniques that maintain their integrity.
At the end of this phase, the formal structure brings processes and tools in line with the scientific principles, methodologies, and techniques required for achieving a state of maturity.
The enterprise phase is the last step in the maturity of a digital forensics; like the progress made at the start of the new millennium (2000s) and beyond. This phase is characterized by the recognition of processes and tools being an actual science that involves the real-time collection of evidence, the general acceptance of the development of effective tools and processes, and the application of formally structured principles, methodologies, and techniques.
Ultimately, this phase of the digital forensics evolution came about from the need to automate digital forensics processes. Not only does this automation support the ability to perform proactive evidence collection, but it also allows for methodologies and techniques to be consistently applied to maintain standards set out by the legal system to ensure the legal admissibility of evidence.
The evolution of digital forensics is cyclical when it comes to maturing existing scientific principles, methodologies, and techniques to adapt with modern technologies or standards (i.e., laws and regulations). However, at the same time the evolution of digital forensics is linear in the sense that the as scientific principles, methodologies, and techniques are being matured, the continued development and contribution to the digital forensics CBK persists.
Principles of Digital Forensics
Digital forensics is the application of science to law and subsequently must follow the scientific principles, methodologies, and techniques required for admissibility in a court of law. Even if legal prosecution is not the end goal of an investigation (e.g., corporate policy violations), there may be a requirement for legal action at some point. Therefore, it is important to handle all potential digital evidence in a manner that guarantees it will remain legally admissible.
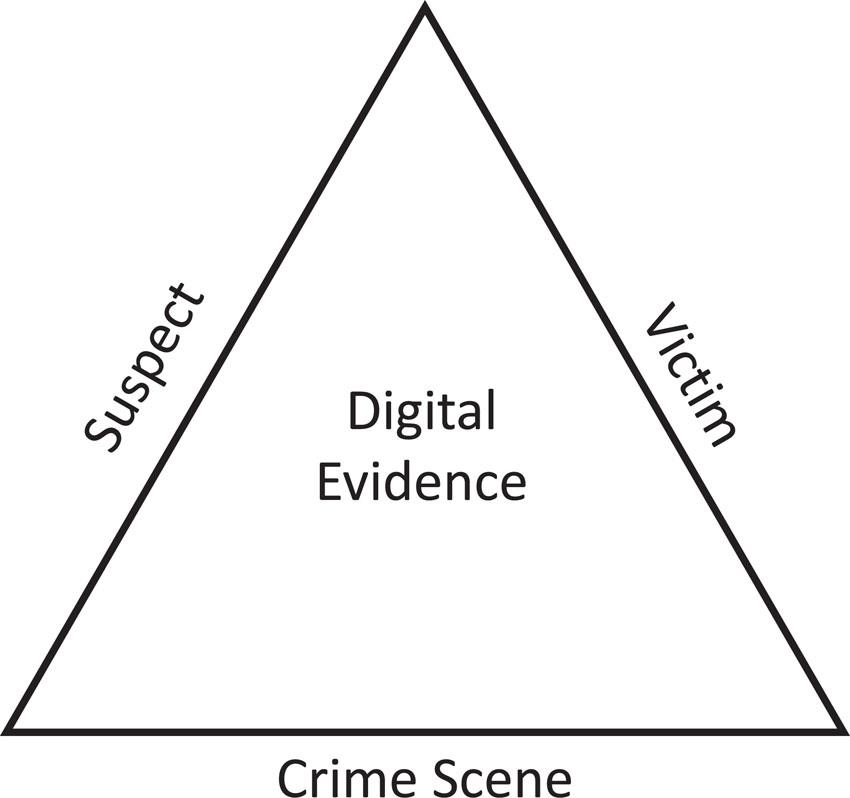
One of the main goals when conducting a forensics investigation is to establish factual conclusions that are based on credible evidence. According to Locard’s exchange principle, illustrated in Figure 1.2, anyone or anything entering a crime scene takes something with them and leaves something behind when they leave. In general, Locard’s exchange principle states that with contact between entities, there will be an exchange.
Figure 1.2 Locard’s exchange principle triad.
In the physical world, an example of this exchange can occur when a perpetrator inadvertently leaves fingerprints or traces of blood at the crime scene. Or a perpetrator might take a crucial piece of evidence away from the crime scene, such as a knife, to make the job of identifying evidence more challenging. In both examples, these exchanges produce tangible forms of evidence that demonstrate both class and individual characteristics. Evidence that possesses class characteristics, otherwise referred to as class evidence, has features that group items by type, such hair color. On its own, this type of evidence does not provide conclusive identification of a perpetrator and individualizing characteristics. What individualizes evidence, such as hair color, are those characteristics with unique qualities that differentiate one from another and help to narrow the group to a single item. Using the analogy of hair color, examples of individual characteristics include length, style (e.g. straight, wavy), and highlights.
In the digital world, evidence exists in a logical state that is much more intangible than physical evidence is. However, exchanges like those in the physical world can persist and are equally as relevant in the digital world. Email communication and web browsing are clear examples of how these exchanges occur within the digital world. If a threatening email message is sent, the individuals computer will contain artifacts of this, as will the email servers used to transmit the message. Practitioners can identify and gather a copious amount of evidence relating to this threatening email in the form of access logs, email logs, and other artifacts within computer systems.
Evidence can make or break an investigation. Equally important in both the physical and digital worlds, it is critical that evidence is handled in a way that will not raise questions when being presented in a court of law.
Forensically sound is a term used to qualify and, in some cases, justify the use of a technology or methodology. Likewise, forensic soundness occurs when electronically stored information (ESI), as digital evidence, remains complete and materially unaltered as result of using a technology or methodology. This means that during every digital investigation, proper techniques must be used, following consistent methodologies that are based on established scientific principles, to achieve forensic soundness specific to digital evidence:
• Minimally handle the original. Digital forensics processes should be minimally applied to original data sources. To achieve this, forensics images of ESI should be taken and used to perform investigative processes and techniques.
• Account for any change. In some instances, digital evidence can change from its original state. When change occurs, it should be documented to note the nature, extent, and reason for the change.
• Comply with the rules of evidence. Throughout an investigation, applicable rules of evidence (e.g., laws and regulations) should be considered. Refer to Chapter 16, “Ensuring Legal Review,” for additional information.
• Avoid exceeding one’s knowledge. Do not undertake any activity or task that is beyond your current level of knowledge and skill.
Perhaps one of the biggest reasons digital evidence does not maintain forensic soundness is human error. To guarantee digital evidence remains forensically sound, ESI must be gathered, processed, and maintained following principles, methodologies, and techniques that do not alter its state at any time, thus demonstrating that it is authentic and has integrity.
The authenticity of digital evidence is maintained to demonstrate it is the same data that was originally seized. From a technical perspective, there are times digital evidence cannot be compared to its original state, such as with random access memory (RAM) that is constantly in a state of change. For these occurrences, point in time snapshots are taken that demonstrate the state of the technology at that moment. From a legal perspective, authentication means satisfying the legal systems that the:
• Content of the record has remained unchanged;
• Information in the record does in fact originate from its original source; and
• Extraneous information about the record is accurate (e.g., time stamp).
Supporting the need to establish authenticity, the goal of maintaining the integrity of digital evidence is to demonstrate that it has not been changed since the time it was first gathered. In digital forensics, verifying integrity generally involves comparing the digital fingerprint of digital evidence when it is first gathered and subsequently throughout its entire lifecycle. Currently, the most common means of generating a digital fingerprint in digital forensics is to use a one-way cryptographic hash algorithm such as the Message Digest Algorithm family (i.e., MD5, MD6) or the Secure Hashing Algorithm family (i.e., SHA-1, SHA-2, SHA-3).
In 2004–2005, experts identified that the MD5 and SHA-1 algorithms contained flaws where two unique inputs, having distinctively different properties and characteristics, would result in the same computational hash value being outputted.
Dubbed a “hash collision,” this meant that the same computational hash value could be engineered in such a way that multiple pieces of digital evidence could return the same hash value. Naturally, this raised concerns in the digital forensics community about the potential impact on the legal admissibility of digital evidence.
In 2009, during the matter of United States v. Joseph Schmidt III, the court ruled that the chance of a hash collision is not significant and is not an issue. Specifically, a digital fingerprint of a file still produces a unique digital algorithm that uniquely identifies that file.
This ruling allows the integrity of digital evidence that was done using either the MD5 or SHA1 algorithms to be relied upon as legally admissible.
The near uniqueness of these cryptographic algorithms makes them an important technique for documenting the integrity of digital evidence. While the potential for hash collisions exists, use of the Message Digest Algorithm family or Secure Hashing Algorithm family remains an acceptable way of demonstrating the authenticity and integrity of digital evidence.
Perhaps the most important aspect of maintaining authenticity and integrity is documenting the continuity of possession for digital evidence. This chain of custody is used to demonstrate the transfer of ownership over digital evidence between entities and can be used to validate the integrity of evidence being presented in court. Without a chain of custody in place, arguments can be made that evidence has been tampered with, altered, or improperly handled, which can lead to potential evidence contamination with other consequences. It is best to keep the number of custody transfers to a minimum, as these individuals can be called upon to provide testimony on the handling of evidence during the time they controlled it.
A sample template that can be used as a chain of custody form has been provided in the Templates section of this book.
As the digital forensics discipline continues to evolve along with technology advancements, one of the most challenging activities is to ensure that the fundamental principles, methodologies, and techniques are updated. There is a constant struggle to maintain a balance between collecting digital evidence as efficiently as possible without modifying the integrity of the data in the process. Fortunately, the principles and methodologies of forensic science have been clearly defined and well established over several decades, allowing them to be applied relatively seamlessly to any form of digital evidence.
Types of Forensics Investigations
Traditionally, digital forensics is performed in response to an event and focuses on determining the root cause of the event. The purpose of performing a digital forensics investigation is to establish factual conclusions from digital evidence existing on any number of different technologies (e.g., game consoles, mobile devices, computer systems), across dissimilar network architectures (e.g., private, public, cloud), or in varying states (e.g., volatile, static).
Since the beginning of computer forensics in the 1980s, the application of forensic science has become an underlying foundation that has seen an integration of consistent principles that support repeatable methodologies and techniques within several other information security disciplines. The application of digital forensic science in other disciplines provides organizations with an acceptable level of assurance that validated and verified processes are being followed to gather, process, and safeguard digital evidence. Examples of disciplines where digital forensic science is used include:
• Computer forensics, which relates to the gathering and analysis of digital information as digital evidence on computer systems and electronic storage media
• Network forensics, which relates to the monitoring and analysis of network traffic for the purposes of information gathering, gathering of digital evidence, or intrusion detection
• Incident response, which relates to reducing business impact by managing the occurrence of computer security events
• Memory forensics, which relates to the gathering and analysis of digital information as digital evidence contained within a system’s RAM
• Electronic discovery (e-discovery), which relates to the discovery, preservation, processing, and production of electronically stored information (ESI) in support of government or litigation matters
• Cloud forensics, which relates to the gathering and analysis of digital information as digital evidence from cloud computing systems
Even if legal prosecution is not the end goal of the investigation, such as with a corporate policy violation, there may be some form of legal action, such as employee termination. It is important that principles, methodologies, and techniques of forensic science are consistently followed because the investigation may wind up in a court of law at some point. Regardless of criminal proceedings, every digital forensics investigation must ensure that:
• An exact copy of digital data is created to ensure no information is lost or overlooked;
• The authenticity of digital data is preserved using cryptographic algorithms;
• A chain of custody is established to maintain integrity through the evidence’s life cycle; and
• Actions taken by people through the different investigative phases are recorded.
The legal aspects of technology crimes have many overlapping areas of laws and regulations. While there are commonalities amongst them, the number of international laws and regulations enacted do vary when it comes to their respective statutes, standards, and precedence. Generally, these laws and regulations were created with the intention of bridging the gap between risk (i.e., criminal activity) and technology (i.e., fruit or tool). The laws and regulations were also designed to anticipate the potential for dispute and reduce the likelihood of such dispute.
Jurisdiction is the power, or right, of a legal system (i.e., court, law enforcement) to exercise its authority in deciding over a (1) person, relating to the authority for trying individuals as a defendant; (2) subject matter, relating to authority originating from the country’s laws and regulations; or (3) territory, relating to the geographic area where a court has authority to decide. In some cases, depending on the crime committed, concurrent jurisdiction can exist where two different legal systems have simultaneous authority over the same case.
In the simplest of scenarios, a legal matter can be tried in the location (i.e., country) where the crime took place. However, with the ways in which technology, such as the Internet, has an extensive global reach and crimes are committed using this delivery channel spanning several countries, it has become somewhat challenging to determine where to prosecute. In cases when there is contention over where a case should be tried, the jurisdiction of the court needs to be assessed and alternatives considered.
Although modern technology adds an additional layer of complexity to jurisdiction issues, international courts are becoming more familiar with laws and regulations relating to technology and are making more informed decisions about which legal system has jurisdiction.
This book is written from a non-technical, business perspective and is intended for use as an implementation guide to prepare any organization to enhance its digital forensics readiness by moving away from reacting to incidents/events and becoming proactive with investigations.
While the basic principles, methodologies, and techniques of digital forensics are covered, this book focuses on outlining—in detail—how an organization can enhance its knowledge, processes, and technologies to implement effective and proactive digital forensics readiness.
There are countless resources available that are designed specifically to teach different the basics or specifics contained within the digital forensics discipline. The volume of reference material on digital forensics topics is beyond the scope of this text, which intends to identify and include them as a reference in this book. Contained within the bibliography of this book are numerous publications on the topic of digital forensics that can be consulted for more information.
The rise and continued evolution of cybercrime has made a significant contribution to the formation of what digital forensic science is today. Growing from the pastime of hobbyists, the establishment of forensically sound principles, methodologies, and techniques has turned it into a respected and authoritative discipline.