THE INTERNET IS NECESSARY PART of today's world. The Internet and its services have become so integrated into business practices that many companies would cease to exist should the Internet fail. Individual users rely on the Internet as a personal and educational tool. The Internet is part of everyday personal and business life.
Despite the reliance on the Internet, it remains an insecure public network. While millions use the Internet each day for legitimate purposes, thousands of others use it every day for cybercrime, bullying, cyberstalking, data theft and more. Use of the Internet as a means of crime is growing, and those using the Internet must take steps to mitigate the risks.
This chapter explores the risks and threats of the Internet and the policies and procedures that can mitigate those risks.
The Internet is an insecure and unregulated environment. Those who connect to the Internet without taking steps to secure their connection and who lack a fundamental understanding of common Internet risks expose themselves to danger. This danger can take the form of viruses, data theft, identity theft, cyberbullying, phishing, and many other forms of attack.
Many users find security in believing that their computer holds no interesting information and therefore is not a target. This is untrue. Unguarded systems can be turned into zombie computers and, under the control of remote users, can be used to stage attacks against other systems or as a repository for offensive content. There is no way to avoid it; today's Internet users must understand the risks of connecting to the Internet and take appropriate steps to mitigate those risks. It all starts with understanding the risks and threats.
As a public network, the Internet is full of risks. Some of these risks are easily mitigated with virus checking and software updates, but others are difficult to predict and manage. Some security risks and threats are aimed at data and privacy, others at availability. Threats to data target application vulnerabilities, unsecured protocols, fraudulent e-mails, and poor Internet practices. Availability threats are due to bandwidth overuse, denial of service attacks, and hardware malfunctions. These threats aimed at both data and availability are just a sample of what network users are up against.
There are several categories of risks on the Internet; some are mitigated using software, others with secure protocols or common sense and policies:
The term hacker is commonly associated with cyber criminals who attack and exploit weaknesses in systems. This is not completely accurate. Historically, hackers are programmers who spend hours tampering with programs and applications, trying to figure out how they work. They do not mean or intend any harm to users or systems. Hackers often make programs better. Crackers, on the other hand, try to gain access to computer systems or applications for illegal purposes. Today, "hackers" is the accepted term for those who attempt to harm computers, users, or software. The term "crackers" has largely fallen out of favor.
Hackers can harm or gain unauthorized access to a computer system or network in several ways. These methods include:
Targeting and exploiting known vulnerabilities in software applications
Installing and using malware
Exploiting poorly managed networks where security protocols are not used or incorrectly applied
Abusing people's trust through social engineering or identity theft
Malicious software, or malware, is a serious problem. It is often assumed that malware means only viruses. There are many other forms of malware that are not viruses but are equally undesirable.
Different types of malicious software include:
Viruses—A program or piece of code that is surreptitiously loaded onto your computer without your knowledge and performs undesirable actions on the system.
Macro viruses—A macro virus is designed to infect, corrupt, and damage file formats that employ macros, such as Microsoft Office documents.
Worms—Programs designed to propagate automatically and silently, without modifying software or alerting the user. Once inside a system, they can carry out their intended harm, such as damaging data, embedding malware, or relaying sensitive information.
Trojan horses—Programs designed to trick the user into installing them. Trojan horses appear as helpful or harmless programs but when installed carry and deliver a malicious payload.
Spyware—Covertly gathers system information through the user's Internet connection without his or her knowledge, usually for advertising purposes. Spyware applications are typically bundled as a hidden component of freeware or shareware programs that can be downloaded from the Internet. By definition, a Trojan horse program installs a "backdoor" or opportunity for unauthorized access. The backdoor is typically for communication from a hacker but could also be used to install additional malware.
In order to be effective, malware requires a method to get from one computer to another. The Internet provides a great mechanism for malware to spread. Some of the common malware delivery types include:
Peer-to-peer (P2P) sharing networks—P2P sharing networks have become very popular and are widely used to download everything from music to games and applications. The problem is, many of the applications and downloads carry malware.
Network shares—A network share is a file, folder, or resource that is made available to the network. Malware can use network shares to propagate itself from system to system over the network. Poorly implemented security on network shares allows malware to replicate to a large number of computers connected to the network.
E-mail—One of the most widely exploited technologies is e-mail. With the click of a button, malware can be sent to hundreds of thousands of users. Most malware attacks through e-mail require the recipient to activate the attack either by opening an e-mail or downloading something from the e-mail, assuming it is from a trusted source.
Web browsing—Not all Web site administrators are equally prepared to protect against the above threats. If a Web site or a component of a Web site is compromised, malware may spread to all subsequent visitors of the site.
These are some examples of how malware can be transported from system to system. Those who write and export malware are always thinking of new ways to transport their software, such as through instant messaging (IM) and social networking. Keeping track of new and existing transport mechanisms is a key part of securing the network.
To protect your network from hackers, it is important to ensure that your software is up to date and all patches and service packs have been installed. This helps prevent hackers from taking advantage of vulnerabilities in the software. To help prevent malware from harming a system, ensure that trusted antivirus software is installed and up to date.
Viruses are a constant threat on the Internet. The damage from viruses varies greatly, from damaging applications on a single system to disabling an entire network. Regardless of the impact, viruses can be very destructive, causing irreplaceable loss of information and hours of productivity.
Viruses have been with us almost as long as computers have existed. Like any other part of the IT industry, viruses have evolved and today are sophisticated, difficult to detect and very dangerous. To be considered a virus, the malware must possess the following characteristics:
A virus must be able to replicate itself.
All viruses require a host program as a carrier.
Viruses must be activated or executed in order to run.
To help minimize the impact and spread of viruses, use trusted antivirus software and a firewall configured for filtering. Since new viruses are generated every day, software of this nature is not fool-proof, but it will reduce the risk of contaminating your computer.
Worm malware is different from viruses and has the potential to spread faster than any other form of malware. Worms are similar to viruses as they are able to replicate. However, worms do not require a host or user intervention to propagate. Worms spread at an alarming rate because they exploit security holes in applications or operating systems and automatically replicate and spread, looking for new hosts with the same vulnerability.
Properly configured firewalls and up-to-date antivirus programs are essential to protect from worms. In addition, care should be taken when opening unknown applications and e-mail.
Trojan horse malware is all about hiding. Trojan horse malware comes hidden in programs, for example, in a shareware game. The game looks harmless, but when downloaded and executed, the Trojan operates in the background, altering or damaging the system.
A Trojan horse is different from a virus in that a Trojan horse does not replicate itself and does not require a host program to run. The main purpose of a Trojan horse is to install additional unauthorized access points to the infected system, called "backdoors." The Trojan horse may send a small message to a controller to alert it to successful installation of the backdoor.
Trojan horses are most easily spread by being embedded in files on P2P sharing networks. Trojan horses also spread through the sharing of such programs using e-mail communications or removable media. In the past, many of the executable jokes sent through e-mail, such as cartoons and amusing games, were the front end of a Trojan horse.
Table 5-1 compares various forms of malware.
Table 5-1. Types of malware.
REPLICATE | HOST REQUIRED | USER INTERVENTION REQUIRED | |
|---|---|---|---|
Virus | Able to self-replicate | Needs a host program to propagate | Needs to be activated or executed by a user |
Trojan Horse | Does not replicate itself | Does not need a host program | User must execute program in which the Trojan horse is hidden |
Self-replicate without user intervention | Self-contained and does not need a host | Replicates and activates without requiring user intervention |
Many online attacks seek to obtain personal information that can be used for identity theft, stealing data, harassment, and much more. Protecting against personal attacks and attempts at data theft are often more about personal browsing best practices than technical solutions. Personal attacks are battled best with skepticism and caveat emptor ("let the buyer beware").
E-commerce is prevalent on the Internet and so are those who use e-commerce to defraud. Many sales and auction sites are legitimate businesses. Unfortunately, it is not always easy to tell the good from the bad. E-commerce fraud is a growing problem with losses measured in the hundreds of millions of dollars. Online fraud causes not only monetary loss but also an atmosphere of fear about online purchasing.
Combating fraud requires education and knowing what to look out for. Well-designed e-commerce sites incorporate trust elements to help build buyers' confidence. E-commerce trust elements include:
Client privacy agreement—Before giving personal information to a Web site, review its policy for client privacy. The client privacy agreement outlines what can and cannot be done with your personal data. It is a contract between you and the site. The agreement often outlines how your personal data will be stored and for how long. It may also describe how and whether it will be shared. This is an important consideration.
Trust icons and logos—These are used to associate a Web site with a known and trusted site. Examples of trust icons and logos are an icon for Secure Sockets Layer (SSL), which shows secure protocols are being used, an icon for the Better Business Bureau, icons or logos associated with trusted anti-malware companies. There are terms of use for displaying a logo and icon, but if a site qualifies, it can build trust. Of course, a fraudulent site also may display such logos to build trust. A wise buyer will exercise skepticism.
Customer comments and testimonials—Customer comments and testimonials are a great way to build visitor trust.
Contact Us form—An e-commerce site should display a way to contact the company for assistance. An e-mail should be provided at a minimum. A telephone number and address also provide assurance.
About Us page—The About Us page of a Web site showcases the company. If purchasing online, it is a good idea to read about the company and its policies.
Return policy—All e-commerce sites should display a return policy. Reputable companies offer a return policy or guarantee that fosters confidence.
If you are concerned about online fraud, pay close attention to the elements listed above. Legitimate e-commerce sites take the time to build customer trust and make the site look and feel legitimate. If you suspect a site, move on.
E-mail, IM, and social networking are designed to make it easy to stay in touch with colleagues and friends. Unfortunately, they also make it easy to harass or stalk someone online. Cyberstalking refers to repeated electronic communication with someone who does not desire the communication. It causes distress. Cyberstalking is a form of harassment. With more people using social networking sites, incidents of cyberstalking are increasing.
Cyberstalking and online harassment come in many forms. These include repeated offensive e-mails, tracking on social networking sites, IM spamming, tracking others on virtual sites, impersonating trusted friends or colleagues, constantly signing someone up for newsletters, creating online groups and forums that reflect negatively on someone, creating hate sites about someone, and creating fake sex ads. Harassment also can be done via mobile phones and handheld devices, so it can be a significant issue.
Preventing cyberstalking and harassment is not easy. Some harassment and cyberstalking tips include:
Do not give out personal information except to a known contact.
Use filtering features in e-mail and firewalls to block contacts from the harasser.
Contact the police if it becomes a serious problem.
Stop all communication with the harasser.
Block the cyberstalker from social networking sites and only add trusted friends.
One of the fastest growing crimes is that of identify theft. Identity theft goes beyond fraud by assuming someone's entire identity. This is done by obtaining personal information, such as Social Security number, driver's license, passport, and credit card numbers. There are many ways a criminal can get personal information: dumpster diving, e-mail phishing, discarded hard disks, and spyware, to name a few.
Protecting against identity theft online involves exerting extreme care over whose personal information is given to whom and why. If buying online, be sure to verify the site's terms-of-use policy that identifies how personal data will be used and stored. Look for companies that encrypt data while in storage and offer safe disposal procedures.
E-mail is an essential tool for business and has become the primary business communication medium. E-mail provides a fast, cheap, reliable universal method of global communication. While e-mail has opened worldwide communication, it has also brought a range of security concerns because it provides a gateway directly into the network through the network's users.
Preventing e-mail attacks and disruption require both technical and non-technical methods. Non-technical methods include not opening unsolicited e-mail, not opening unwanted attachments, not sending personal information that could be used against you, not giving your e-mail address to everyone who asks, not replying to spam, and not forwarding chain letters.
For technical solutions, use up-to-date virus scanners that check incoming and outgoing e-mails. Many companies also use e-mail filtering software, which performs the following:
E-mail tracking—Administrators track the e-mail habits of network users, including whether attachments are sent and how often and to whom e-mails are sent.
Keyword filtering—It is possible to provide network wide e-mail vetting. E-mail vetting software searches through e-mails using a list of keywords. Once the software finds a matching keyword, the software sends an alert to the administrator.
Legal disclaimer—Besides searching for and quarantining e-mails with offensive words and phrases, e-mail-filtering programs allow an organization to add disclaimers to outbound e-mails. The intent of the disclaimer is to reduce liability. While a company is ultimately responsible for the actions of its employees, the disclaimer shows that the employees are bound by e-mail policy.
E-mail blocking—E-mail filtering software can block both internal and external e-mails based on e-mail policy. A message may be blocked due to undesired content, including e-cards, gambling, and chain letters. Also, a message may be blocked due to unauthorized attachments, such as video and sound types, visual basic attachments, and executable files. With keyword-matching, the software can actively block e-mail from being sent to an intended recipient. For example, a company may wish to prevent its new sales strategy from being shared outside the company. E-mail filtering would not guarantee it, but it could block e-mails that contain the sales strategy as well as send an alert that someone attempted to send it.
Message priority—Non-essential e-mails with large attachments can quickly tie up network resources. In response, e-mail filtering software can flag such messages and either block them altogether or mark them to be sent in non-peak network hours. This saves significant bandwidth.
Message archiving—Increasingly, government regulations dictate that e-mail messages be retained as a record of an organization's e-mail communications. E-mail software programs allow archiving to easily retain copies of e-mails in a centralized and secure location.
Reviewing the risks and threats of the Internet can seem overwhelming, but there are some common strategies that help mitigate online risks. These include:
Keep applications and operating systems updated.
Use trusted antivirus/antispyware applications.
Ensure the applications are up to date.
Protect portable devices such as cell phones, personal digital assistants (PDAs), and portable PCs.
Password protect and encrypt data on the laptop.
Should it be stolen, it can't be read.
Secure the wireless access point.
Use perimeter protection, such as firewalls, intrusion detection systems, and intrusion prevention systems.
Encrypt data to ensure integrity and confidentiality.
Historically and even today, software developers create many applications and protocols without security issues in mind. Equally, network and system hardware are vulnerable by default. If not carefully managed, both hardware and software are easily exploited. In addition, regular users also present risk. Administrators and users should be aware of:
End-user vulnerabilities—End users can be vulnerable if they are not educated in company policies and best use practices. Many companies offer employees security training to help mitigate breaches. With a little education and a better understanding of the risks, end users are less likely to open a network to potential threat.
Security vulnerabilities—Many organizations do not use network perimeter security measures. If they do, some organizations don't ensure that security measures are properly configured. Network firewalls, for example, are useful only if properly configured.
Note
You'll learn about port vulnerabilities in more detail in the "Port 80: Open or Closed?" section later in this chapter.
Port vulnerabilities—Your computer and operating system has 65,535 ports. These ports operate like windows or doors that allow access to the system. By default, most ports are left open, "listening" and ready to receive communication. These open ports may be exploited and should be shut. A firewall closes all the doors you don't need, thus minimizing the chances of a hacker entering.
Software vulnerabilities—Many software packages, from applications to operating systems software, can be exploited due to vulnerabilities in the software. All software must be monitored and upgraded when vulnerabilities are discovered and a patch is available.
Malware vulnerabilities—Malware is an ever-present threat. Today, systems require anti-malware applications. Malware applications require maintenance and constant updates to address new threats.
Tip
As a best practice, consider visiting the vendors' Web sites of your applications periodically. If you use Microsoft products, for example, check periodically for news on new patches and security threats. In addition, it is best to leave automatic updates on to keep your system as current as possible.
In many cases, vulnerabilities are a result of inadequate policies and procedures. It is no secret that the Internet is dangerous, yet many home users and network administrators do not adequately prepare for the risks. Attacks are growing in both frequency and complexity. Systems left unsecured will at some point be attacked. At the time of this writing, an unsecured system put on the Internet takes between 15 to 30 seconds before becoming infected or compromised.
Thousands of people wake up each day and go online for no other purpose than to commit cybercrimes. It can range from an ex-partner trying to stalk someone online to cyberterrorists aiming to down the power grid or disrupt the Internet's economic structure. Many people do not consider that when they are checking Facebook, there is a cyberwar going on. Internet perpetrators may include:
Sexual predators
Cyberterrorists
Cyberstalkers
Identity thieves
Data thieves
Malware developers and distributors
E-mail spammers
There are specific measures designed to mitigate the actions of each of these perpetrators. The types of attacks these predators may use are included in the following sections.
The following list is a sample of attacks that perpetrators may use:
Password attacks—One of the most common types of attacks involves passwords. Usernames are easy enough to obtain or guess. If an attacker can get the user's password as well, the intruder can gain the level of system access associated with that user. This is why protecting administrator passwords is so important. A password with administrator privileges provides an intruder with total unrestricted access to the system or network.
Cyberstalking—Cyberstalking and the electronic tracking of people has become a huge problem online. Many people do not even know that someone is tracking them through social networking or other means.
Social engineering—It can be used both by outsiders and by people within an organization. Social engineering is a hacker term for tricking people into revealing their passwords or other privileged information. This includes trying to get users to send passwords or other information over e-mail, shoulder surfing, or other tricks Social engineering takes advantage of people's natural tendency to be helpful.
Eavesdropping—As it sounds, eavesdropping involves an intruder trying to obtain sensitive information, such as passwords, data, and procedures for performing functions, by intercepting, listening and analyzing network communications. An intruder can eavesdrop by wiretapping, using radio, or using auxiliary ports on terminals. It is also possible to eavesdrop using software that monitors packets sent over the network. In most cases, it is difficult to detect eavesdropping but fairly easy to stop. Using secure communication such as encryption assures important and sensitive data is not sent over the network in clear text.
Backdoor attacks—A backdoor attack refers to the ability to gain access to a computer or program that bypasses standard security mechanisms. Many malware applications can create backdoor access to a system. This is the method of a Trojan horse program.
Man-in-the-middle attack—In a man-in-the-middle attack, the intruder places himself between the sending and receiving devices and captures communication as it passes by. The interception of the data is invisible to those sending and receiving data. The intruder is able to capture the network data and manipulate it, change it, examine it, and then send it on.
Spoofing—In spoofing, the attacker fakes the real source of a transmission, file, or e-mail. This strategy enables the attacker to misrepresent the origin of a file in order to trick users into accepting a file download from an untrusted source, believing it came from a trusted source.
Dictionary attack—Most of the passwords used today are chosen because they are easy to remember. This leaves them open to a dictionary attack. In this type of attack, a program scans through the entries in a dictionary data file, attempting to guess a password. This attack type is ineffective where password policies require inclusion of numbers and symbols in passwords.
Brute-force attack—A brute-force attack attempts to crack a cryptographic key or password with little to knowledge or advantage. It involves programs designed to guess at every possible combination until the password or key is cracked. Of course, the more complex a password is, the harder it is to crack and the less likely a brute-force attack will be successful.
DoS attacks focus on key areas including network bandwidth, memory, CPU time, and hard-drive space. They are designed to overwhelm a resource until it becomes unavailable. The threat is against availability—with a resource overloaded, it becomes unusable. Types of DoS attacks include:
Ping flood—A ping request packet is sent to a broadcast network address where there are many hosts. The source address is shown in the packet to be the Internet Protocol (IP) address of the computer to be attacked. If the router to the network passes the ping broadcast, all computers on the network will respond with a ping reply to the system. The attacked system will be flooded with ping responses which will cause it to be unable to operate on the network for some time and may cause it to lock up.
Fraggle—A Fraggle attack sends spoofed User Datagram Protocol packets to a network's broadcast address. These packets are directed to specific ports such as port 7 or port 19. Once connected, the packets flood the system.
Smurf—A Smurf attack is similar to Fraggle except that an attacker sends a ping request to a broadcast network address with the sending address spoofed, prompting many ping replies to the victim. This will overload the victim's ability to process the replies.
Distributed denial of service (DDoS)—DDoS attacks involve a coordinated attack from hundreds or thousands of computers across the Internet. An attacker first breaks in, installs DDoS software and gains control. The attacker can then control all of these computers and launch coordinated attacks on victim sites. These attacks exhaust bandwidth, router processing capacity, or network stack resources, breaking network connectivity to the victims.
There are many other types of DoS attacks and they all seek to exploit a weakness and overwhelm a resource.
Once the decision is made to create a Web site and the site is designed, a Web hosting solution is needed. Web hosting refers to the placement of a Web site on a Web server, making it available to the Web. Web hosting companies provide storage, connectivity, security, access protocols, and other services necessary to serve files for a Web site.
There are many Web hosting companies available both for free and for cost. Additionally, it is possible to outsource the placement of hosting services or provide that service internally within the network. Web hosting is essentially the placement of your Web site on the Internet through a server.
Thousands of companies offer Web hosting services. The cost varies by a company's needs. For example, hosting companies offer both dedicated and shared hosting services. Dedicated means a dedicated server is used to provide hosting services; shared has multiple companies using the same Web server. Naturally, a dedicated Web server is much more costly than a shared server.
All Web hosting providers offer packages that provide hosting services including:
Disk storage space
Available bandwidth
Technical support
Post Office Protocol version 3 (POP3) e-mail accounts
E-mail forwarding
E-mail auto-responders
E-mail aliases
File Transfer Protocol (FTP) access
Password protection
When creating an e-commerce site, choosing the right Web hosting company and package features is critical. Among the many factors to consider:
Disk space and bandwidth—If you have a large site that generates significant monthly traffic, you need a hosting plan that matches your space and bandwidth needs. Hosting companies charge extra if your bandwidth and space requirements are exceeded.
Flexibility—Some hosting companies are rigid in their packages while others are flexible and adjust to changing business needs.
Technology—Larger hosting companies have the financial resources to purchase the latest software and hardware to provide cutting-edge services. Choosing a hosting company that has the technology and expertise is worthwhile.
Pricing—Prices of Web hosting companies vary greatly, but more expensive companies are not necessarily better. It is important to take the time to research different pricing options.
Guaranteed uptime—In choosing a Web hosting company, it's critical to consider policies around uptime and backups. Guaranteed backup refers to the mechanism a company has in place for continuation of service in the event of hardware or software failure. Many Web hosting companies list their approach to uptime and the steps they take to ensure that Web sites are available.
Backups—Consider what the hosting company offers in terms of backups, frequency, and storage of backups. Does it offer offsite backup storage? It's critical to know where and how backups are used and stored.
Security—Your Web site is operational 24/7, so you must know what steps and procedures are in place to ensure its security against internal and external attacks. This includes protocol usage and logical and physical security measures.
Dynamic service—A Web hosting company should adapt as new technologies are introduced.
Support—Most companies want a hosting company that offers quality customer support. This includes frequently asked questions (FAQ), e-mail, phone, and forum support.
You can avoid the inconvenience of changing hosting companies if you take the time to research and choose the right one initially. Additional hassles may arise if the hosting company allows you less flexibility and control than you'd have with an internally hosted Web site. A well thought-out service level agreement (SLA) can help ensure that any problems are handled as if the infrastructure were controlled internally.
Internal Web hosting refers to maintaining your own Web server and not outsourcing to an external company. There are some advantages to this approach. First, it allows you complete flexibility in terms of Web site modifications. It allows administrators to manage their own security, backups, and uptime. It takes away reliance on an external company and shifts it in-house.
If a company Web site is mission critical, that is, downtime has a serious impact on business functioning, internal hosting has a few snags. Ensuring increasingly high levels of uptime is difficult to achieve, requiring redundant hardware and expertise to manage that hardware. Many companies start out hosting their own site to save costs but, once the company grows, shift to external hosting.
If you choose internal hosting, there are many elements you need to host your site:
Web server with redundant drives and hardware to ensure uptime
High-speed Internet connection to handle bandwidth requirements
Adequate disk storage to hold the site
Physical and logical security measures including locked doors and protocols
Available IT personal who can manage the programming, maintenance, and security of the site
Strong backup procedures including considerations for offsite backup storage
Many smaller companies do not have the technology infrastructure and personnel to adequately manage their own Web server. However, for some, the benefits of internal hosting outweigh the costs and hassles of external hosting.
If you have a Web site, you are likely familiar with the need for a domain name such as www.google.com or www.mybusiness.com. When you sign up for a domain, whether it's a .org, .com, .edu, or any of the other domain suffixes available, you use an authorized domain registrar.
The governing body for all domain names is called the Internet Corporation of Assigned Names and Numbers (ICANN). Its Web address is http://www.icann.org. ICANN holds a record of every domain name, who owns it, and how and where it's being used. This is often referred to as Whois data because you can search for a domain owner and contact information from ICANN. For example, type whois <domain>.com in a search engine, and then click the Whois link that appears in order to view the information on the domain and owner.
Note
Most hosting companies provide a link to the Whois database on their Web sites. You can also visit http://www.icann.org to access links to the Whois Search Web page.
A Whois search can return a lot of information. It may reveal the domain owner's home address, work address, phone, e-mail address, and more. You can also find information on how long an individual or company has owned the domain.
WHOIS is not without problems. When it was first available, people used it as a way to find e-mail addresses for spamming purposes and to find new startups even before their Web sites were live. For these and other reasons, registrars started to offer private settings.
Private Whois settings provide more protection of personal data. Often, just the information from the hosting company is provided. However, authorities such as police can request your registrant information, private or not.
Tip
Check your Whois information to make sure the information is accurate and up to date. This is the official record of ownership and contact information for domain transfers and other domain management needs, as well as protecting your property from fraud or theft.
The choice of using private settings or public Whois information depends on whether you want personal contact information released. In some cases, it's good to allow people to see your information to be able to contact you. However, you should use private settings if you don't want personal information to be exposed.
Domain Name System (DNS) servers perform a relatively basic, but very vital, role for the Web and its users. The function of a DNS server is to provide name resolution from domain names to IP addresses. This means it maps the domain name, such as google.com, to its IP address. The DNS server follows a systematic process. The DNS server consults its own databases for the requested information. If need be, a DNS server will also contact other DNS servers as needed to get the necessary information. This process may involve a large number of queries.
As you may know, each endpoint network device, such as a server or workstation, requires a unique IP address. A device's IP address is similar to a physical mailing address for snail mail in that it helps data get routed to the proper recipient. Because people cannot be expected to remember hundreds of IP addresses, we rely on a hierarchical system of domain names. In terms of hierarchy, domains read right to left, with the first being a special top-level domain (TLD). Examples are .com, .net, .aero or .edu. These represent a group or type of domains. For example .aero is for registered airline companies or pilots, while .edu is strictly for educational institutions. The next domain after the TLD provides an easy-to-remember host name, such as google.com, to access the hosts. When you type google.com into a Web browser, your configured DNS server takes the request and searches through a system of servers to find the correct Transmission Control Protocol/Internet Protocol (TCP/IP) address that relates to google.com. After the DNS server discovers the correct IP address, the DNS server returns the address to the client. The client can then communicate to the IP address, i.e., your browser can then browse to the Web server.
To assist subsequent requests for the same address, the DNS server adds the address to its cache. This includes requests from workstations as well as requests from other DNS servers searching to resolve the same domain name. For a workstation to send requests to the DNS server, the IP address of the DNS server must be known to the workstations.
This can be provided manually, or Dynamic Host Configuration Protocol (DHCP) service also can include the DNS server address when providing an IP address.
Before DNS was used, resolution of host names was performed through static text files. These text files are called HOSTS files and are still the first source for attempting domain name resolution by default for many operating systems today. However, HOSTS files normally hold very little information and the client must rely on DNS.
To ensure that DNS servers are not overwhelmed with requests, the domain name space is divided into a hierarchy of subdomains, each of which has a number of servers providing name resolution services. Other domains are then listed as subdomains of the sub-domains, and so on. To avoid overwhelming the domain servers, a DNS administrator can designate a DNS server as a DNS authority for a subdomain. This authority server handles all resolution requests for that subdomain.
Note
Most common operating systems provide the ability to act as a DNS server. Some implementations are more sophisticated than others, but the basic principle of host name-to-IP-address resolution remains the same.
The amount of computing power required by a DNS server is proportional to the number of DNS requests that it will handle. Within an organization, records might be configured for only a relatively small number of hosts, and there might be only a small number of client requests. In such an environment, it would be unlikely to have a server dedicated to DNS functions. In contrast, a DNS server for an Internet service provider would need to be powerful enough to accommodate perhaps millions of requests per hour.
Although servers running DNS are likely to have fault-tolerant measures implemented, DNS itself has mechanisms that can deal with server downtime. In addition, most DNS clients can be configured with multiple DNS servers' addresses should the first-choice server be unavailable for any reason.
The Domain Name System (DNS) is the standard name resolution strategy used on networks today. DNS is non-proprietary, meaning that it works on all operating system platforms from Linux, to UNIX and Windows operating systems. The function of DNS is to resolve host names such as http://google.com, to an IP address. In this case, google.com resolves to 74.125.39.103, one of many different IP addresses for Google, depending on your location. Host names make it easier for people to remember Web addresses rather than their IP address.
DNS operates in the DNS namespace. The DNS namespace is an organized, hierarchal division of DNS names. At the top level of the DNS hierarchy is an unnamed DNS node known as the root. For the entire Internet there are 13 root servers. All other nodes in the DNS hierarchy are known as labels. Together they form the DNS tree.
Perhaps the best example of a DNS tree can be seen using the Internet. At the top level are domains such as .com, .org, or .edu as well as domains for countries such as .ca (Canada), or .de (Germany). These are in fact called TLDs or top level domains. Table 5-2 shows some of the more common top-level domain names and their intended purpose.
Below these top-level domains are the subdomains associated with organizations, for example, Microsoft.com. In many of the TLDs in Table 5-2, any individual may register a subdomain. However, some TLDs restrict who may register a subdomain. For example, the TLD ".aero" is available only to organizations and people in the aviation industry. Figure 5-1 shows a sample of the DNS organization of the Internet.
The DNS naming structure can be confusing. Consider the following DNS name for a server:
bigbox.support.acme.com
When reviewing a DNS naming system, whether for an internal DNS or Internet DNS, the left-most part identifies the machine name, in this case bigbox. Moving to the right, support is a child domain of acme.com.
Continuing to the right you have acme.com that is a child domain of the top-level domain .com. In this case, whoever wanted to create the domain acme.com had to contact an established domain registrar. For the .com domain, there are several commercial registrars available for individuals and organizations to create subdomains.
Most internal networks and the Internet use DNS naming. This means that you will need to plan and design the DNS namespace that will be used. You should consider your organization's functions or internal divisions, such as shoes.xyz.com and support.xyz.com. Perhaps it's important to identify by geographical location, such as prague.xyz.com or peoria.xyz.com.
The first step is to choose the top-level domain name that will be used to host the organization's name on the Internet. Although .com is the most popular, a nonprofit organization may opt to use .org, and a university may use .edu. Next, choose the second-level domain name that identifies the actual organization, google.com, for example. This is often referred to as the parent domain name and is the domain name used on the Internet.
To develop a namespace, many organizations map out the namespace according to how it will best suit the organization.
DNS is a fundamental service for networks and therefore has to be secured. There are many different strategies to secure DNS servers, many of which involve verifying that the DNS server is correctly installed. Before looking at ways to protect the DNS service, let's take a quick look at the types of attacks that are used against DNS systems:
DoS—DoS attacks attempt to overflow the DNS server with recursive queries or queries it must forward to another DNS server. The intended result is to tax the resources of the original DNS server, leaving it unable to handle legitimate name resolution requests.
Footprinting—In this type of attack, the attacker attempts to obtain DNS zone data which may provide the domain names, computer names and even IP addresses of network systems. This is an early form of reconnaissance before a targeted attack.
Address spoofing—Essentially, IP spoofing involves convincing a sending computer that the attacker is the intended recipient when it isn't. Network devices use the IP address to determine the sender and receiver for a data transmission. In spoofing, the hacker assumes the identity of a legitimate IP node.
Redirection—In a redirection attack, the attacker attempts to redirect DNS queries to servers operated by the attacker.
This chapter has mentioned "domain" in several different contexts. You learned about domain names for Web sites, the Domain Name System, DNS servers, and DNS attacks. This section focuses on one of seven domains in a typical information technology (IT) infrastructure that plays an important role in mitigating risk when connecting to the Internet—the LAN-to-WAN Domain.
To provide some background, there are seven domains in a typical IT infrastructure, as follows:
User—This domain refers to any users of an organization's IT system. It includes employees, consultants, contractors, or any other third party. These users are called "end users."
Workstation—This area refers to the computing devices used by end users. This includes devices such as desktop or laptop computers.
LAN—This domain refers to the organization's local area network (LAN) technologies. A LAN is two or more computers connected together within a small area.
WAN—A wide area network (WAN) is a network that spans a large geographical area. The most common example of a WAN is the Internet. Organization's with remote locations use a WAN to connect those locations.
LAN-to-WAN—This domain refers to the organization's infrastructure that connects the organization's LAN to a WAN.
Remote Access—This domain refers to the processes and procedures that end users use to remotely access the organization's IT infrastructure and data.
System/Application—This domain refers to the equipment and data an organization uses to support its IT infrastructure. It includes hardware, operating system software, database software, client-server applications.
Figure 5-2 shows the seven domains of a typical IT infrastructure. Because the LAN-to-WAN Domain figures prominently in regards to Web-related security issues, the next section focuses on this domain.
The administration of local area networks and wide area networks is a complex task. Not only must administrators concern themselves with the day-to-day user end operations, they must also be vigilant about the constant threat of attack. Many network administrators are highly paid to ensure that network communications, hardware, and the entire network is secure. Any security breaches are the responsibility of the administrator. This can be a stressful position.
This section explores some of the methods commonly used to protect networks.
Perimeter defense strategies refer to security measures on the edge of the network that protect the internal network from external attack. No one perimeter security mechanism is enough to protect the network. Instead security is achieved from a combination of properly executed security strategies. It's a cliché but true that security is only as strong as the weakest link. So the administrator must consider all possible threats and practice sound risk management.
Perimeter security strategies employ both hardware and software controls:
Antivirus/spyware/spam/phishing software
Intrusion detection systems
Intrusion prevention systems
DoS/DDoS defense
Firewalls
Application control and bandwidth management
Demilitarized zones
Port management
The following section explores some of the more common perimeter security strategies and how they are used in a network environment.
When configuring network security and using secure protocols such as IPSec or restricting unused network services, it is important to understand ports and their purposes. Each protocol within the TCP/IP suite has a port association. During communication, the target port is checked to see which protocol or service it is destined for. The request is then forwarded to that protocol or service. As an example, HTTP uses port 80, so when a Web browser requests a Web page, the request is sent through port 80 on the target system. If port 80 is shut, the HTTP service will be unavailable.
A system has 65,535 ports available, numbered from 1 through 65535. These are broken down into three distinct designations: well-known ports (1–1023), registered ports (1024–49151), and dynamic ports (49152–65535). The dynamic ports are also sometimes called the ephemeral or private ports.
Table 5-3 presents some of the most familiar services and their respective port. The table also specifies whether the service relies on the TCP or UDP method of sending.
Table 5-3. Protocols, port assignments, and services.
PROTOCOL | PORT ASSIGNMENT | TCP/UDP PORT |
|---|---|---|
File Transfer Protocol (FTP) | 21 | TCP |
Secure Shell (SSH) | 22 | TCP |
Telnet | 23 | TCP |
Simple Mail Transfer Protocol (SMTP) | 25 | TCP |
Domain Name System (DNS) | 53 | UDP |
Trivial File Transfer Protocol (TFTP) | 69 | UDP |
Hypertext Transfer Protocol (HTTP) | 80 | TCP/UDP |
Post Office Protocol version 3 (POP3) | 110 | TCP |
Network News Transfer Protocol (NNTP) | 119 | TCP |
Internet Message Access Protocol version 4 (IMAP4) | 143 | TCP |
Simple Network Management Protocol (SNMP) | 161 | UDP |
Hypertext Transfer Protocol Secure (HTTPS) | 443 | TCP |
Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are two protocols in the Transport layer of the Internet Protocol Suite. Of the 65,535 ports available, a service may use either TCP or UDP for communication. The primary difference between TCP and UDP is in guarantee of delivery. UDP sends information and assumes it was delivered, while TCP checks to ensure delivery.
When securing a network, it is recommend to shut down unused ports to help prevent unwanted access. Be warned, however, that once the port is shut, the associated service is not available.
As previously mentioned, the Internet can be a dangerous place unless proper security measures are taken. Security is an essential consideration for today's networks. When it comes to perimeter network security, the name of the game is firewalls. However, many organizations and home owners see the firewall as the only needed perimeter security measure. While it is important, it is not the only measure needed.
The ability to protect data and to stop intruders from accessing internal networks is becoming increasingly important to organizations and individuals alike. This protection, from a network connectivity perspective, comes in the form of a firewall. Firewalls are not a new technology, and as more organizations connect their networks to the Internet, firewalls have become commonplace.
Basically, a firewall controls, prevents, and monitors incoming and outgoing network access. It is the job of the firewall to prevent unauthorized network access, both from outside and inside network users. Depending on the type of firewall, data packets sent to and from the network pass through the firewall, and all this data can be checked for whether it is allowed for transfer. Figure 5-3 shows how a firewall system typically fits into a network.
In essence, the simplest type of firewall is a router in that it makes forwarding or blocking decisions based upon given criteria. The difference between a firewall and a router is that a firewall can make the decisions based on a wider variety of criteria than a router can. Firewalls that perform essentially as a router decide by simple routing information whether to allow or deny network traffic. These "packet filtering" firewalls are fast and cheap. The next type of firewall is called a circuit gateway firewall, and it will better hide the network behind it. These firewalls can make decisions based on both TCP and IP information. Those cost a bit more but are still not as intelligent as an application-layer gateway firewall. These firewalls, also called proxies, can allow or deny traffic based on application commands. The most complex and costly firewall of all is the stateful multi-layer packet inspection firewall. These firewalls combine the qualities of the previous three. Although the most common use of a firewall is to protect the boundary of an organization's network, some companies use firewalls internally as well to protect network areas containing sensitive data, such as research or accounting information.
Today's advanced firewall systems provide many security services on incoming communications:
Content filtering—Many firewalls can be configured to check the content leaving and entering the site and flag it if it appears to be a threat. Content blocking involves allowing or denying transmissions based on content.
Virus scanning services—A firewall server can use anti-malware software to check all incoming and outgoing transmissions for malware. This provides centralized, network-wide malware scanning and vetting services.
Network address translation (NAT)—To protect the identity of machines on the internal network, and to allow more flexibility in internal TCP/IP addressing structures, many firewalls (and proxy servers, which are covered in the next section) translate the originating address of data into a different address, which is then used on the Internet. Network address translation is a popular function because it works around the limited availability of TCP/IP addresses.
Signature identification—All applications have unique signature identifiers. In the antivirus world, a signature is an algorithm that uniquely identifies a specific virus, worm or Trojan horse. Firewalls can be configured to detect certain signatures that are associated with malware or other undesirable applications and block them from entering the network.
Address filtering—Firewalls can be configured to filter by Web address. This is an excellent way to exclude known malware and undesirable sites.
Many of these functions are not considered initially. However, because the firewall sits at the perimeter of the network, it is an ideal place to combine security services that closely monitor network traffic and access.
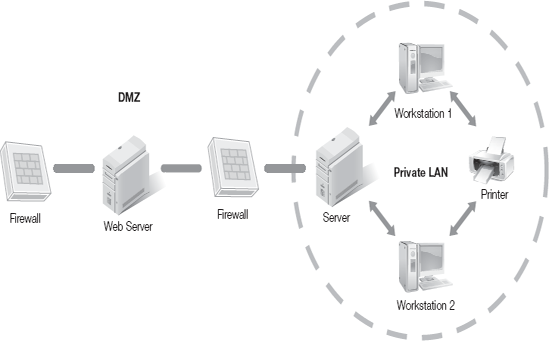
Also at the perimeter of the network is something known as the demilitarized zone (DMZ). Some network servers need to be accessible to both internal and external users. It is possible to put such servers into the internal network but that gives a level of access that may not be wanted. Therefore, these servers are put in the DMZ. The DMZ is part of a network on which you place servers that must be accessible by sources both outside and inside your network. However, the DMZ is not connected directly to either network, and it must always be accessed through the firewall. This means that external users do not gain access to the internal network at all.
A DMZ creates additional security for the internal network by placing publicly accessed servers outside the local network. You can create an additional step that makes it more difficult for an intruder to gain access to the internal network.
There are different ways to deploy a DMZ depending on the organization's security needs. Two common DMZ strategies include the N-tier and the three-homed firewall configurations. With the three-homed configuration, the firewall filters traffic between the two network segments. An N-tier configuration uses two firewalls with the DMZ sandwiched in between. In this configuration, an attacker would need to pass through two firewalls to access the internal network. Figure 5-4 shows an example of three-homed firewall and Figure 5-5 shows the N-tier firewall design.
Proxy servers and firewalls go hand in hand in networks. The proxy server sits between the client computer and the Internet, monitoring Web page client requests. If a client wants to access the google.com Web site, the request is first sent to the proxy server rather than directly to the Internet. The proxy server identifies whether the requested page is in its cache and if so returns the page to the client.
Retrieving pages from the proxy cache is faster than going on the Internet to retrieve the page and also reduces usage bandwidth by limiting client requests that actually have to go online. If the requested page in not in the proxy cache, the client request is forwarded to the appropriate Web site and the information is returned to the client. The transaction between the proxy server and the client is largely transparent to the user with no apparent lag time.
One issue that has plagued proxy services is stale content. When a Web page is retrieved from the cache, it may not be the most recent site update. This may not matter for some sites, but for others with more dynamic content, the cache would be stale. To combat this, the proxy server is configured to periodically revisit commonly accessed sites and retrieve the most current data for the cache. This is an automatic process, but the frequency with which proxy servers update their cache can be configured by administrators. Figure 5-6 shows an example of a proxy server.
Two other perimeter security defense mechanisms are the intrusion detection system (IDS) and the intrusion prevention system (IPS). The IDS device actively monitors the data packets that travel the network and compares traffic against its parameters of known threats. The IDS will pinpoint any traffic that falls outside the secure parameters. All potentially dangerous traffic is flagged and logged. It is up to the administrator to review the log file and take appropriate actions to manage the potential threat.
The IDS is a passive security measure in that it only monitors the network and doesn't take steps to mitigate the risk. In addition, many IDS systems are prone to a "better safe than sorry" security approach. When the IDS device encounters network traffic which may be suspicious, it logs that traffic along with all suspicious traffic. Thus, IDS devices generate numerous false reports in an attempt to perform a thorough job. This causes the administrator to weed through many false security reports, which can be time consuming. To reduce the administrator's time reviewing logs, the IDS device must be tuned. By spending the time necessary to tune the IDS, the organization will save much more time in the long run.
The IPS systems device goes one step beyond the IDS in that it flags potentially harmful traffic and also attempts to prevent that traffic from harming the network. IPS systems can automatically block suspicious traffic. In this way, IPS systems are known as a reactive security measure.
IDS and IPS systems are not a replacement for a firewall system as they provide different services. They are used in conjunction to help create a comprehensive security plan.
Note
Many perimeter security defense mechanisms such as the firewall, IDS, and IPS can be host-based or network-based. Host-based security systems are installed on the local system and provide security services for a single host. Network-based systems monitor an entire network.
A primary focus of network security is to guard the perimeter of the network to keep out external threats. Anti-malware software, firewalls, IDS, IPS, and e-mail filtering software were designed to address the external threat. These mitigating strategies neglected the threat from inside the network.
Security measures have evolved in recent years and now protection within the network and data protection are as important as managing external threats. Internal threats come from many sources: disgruntled employees, stolen laptops, captured network data, stolen backups and hardware, to name a few. These threats have pushed security strategies focusing on data leakage protection.
"Data leak prevention," also known as data loss prevention, focuses on efforts to control what information leaves the network and in what form. It focuses on the confidentiality and integrity of information. Data leakage can happen in a variety of ways including:
Stolen hardware—Laptops stolen with company information can be a disaster. All company laptops need to have data encryption and passwords in case they fall into the wrong hands.
Misplaced backups—Backups, if stolen, can be restored and the data stolen. Most companies use both physical and logical methods to secure data backups.
E-mail—E-mail is one of the biggest sources of data leaks both by intentional and unintentional methods.
Non-secure transmissions—It is a good practice to encrypt sensitive data on the internal network and if it is sent externally. Use secure protocols such as IPSec to help ensure data is safe in transmission.
Undeleted files—Files are often recoverable even when they appear deleted. Software used for undeleting files is commonplace and easy to use. Policies should be developed to manage the disposal of computer equipment to prevent possible data loss.
Portable devices—Flash drives, thumb drives, and CDs/DVDs offer more ways for data to be purposefully leaked. Prevention has become very challenging. Some practices for organizations include disabling universal serial bus (USB) ports and including read-only CD/DVD drives in users' workstations.
The prevention of data loss requires a multifaceted approach of non-technical solutions, such as end-user education, and a variety of security strategies, including protocols, physical security, and encryption strategies.
Regardless of threats on the Internet, people will go online. The trick is to do so safely and to reduce the risks to yourself and the network. The following is a list of best practices when connecting to the Internet:
Keep all applications current—Look for updates to software including productivity software, virus and operating systems.
Use trusted anti-malware software—Antivirus software includes mitigation strategies for known malware. Keep this software installed and current.
Use perimeter security—Home users and corporate networks need to incorporate strong perimeter security strategies. This includes the firewall, IDS, and IPS. In addition to installing them, take the time to use them properly. For home users, IDS and IPS functionality is sometimes included in full-featured antivirus software.
Secure backups—Backups on removable media such as tape sets and USB needs to be secure in the event of theft.
Use secure passwords—Choosing hard-to-guess passwords goes a long way to securing many online transactions.
Report cybercrime—If you suspect that you or someone you know is a victim of cybercrime such as stalking or bullying, report it to the police.
Personal information—If using social networking sites, use caution when divulging personal information.
Use data encryption—The ability to encrypt data is built into operating systems. It is a best practice to encrypt data to prevent it from being read if stolen.
Best practices for Internet connectivity follow a series of commonsense strategies and technical solutions. Never assume you are anonymous or secure on the Internet. It is a best practice to assume someone is trying to access your system and act accordingly.
There are many risks associated with online connectivity. Despite these risks, businesses and personal users will continue to use the Internet. Therefore, they must employ strategies to mitigate the risks. These strategies require a combination of non-technical and technical methods.
Adware
Client privacy agreement
Cracker
Cyberstalking
DNS namespace
Domain Name System (DNS)
E-mail filtering
Hacker
Identify theft
Intrusion detection system (IDS)
Intrusion prevention system (IPS)
Macro virus
Malware hoax
Spyware
Trojan horse
Worms
Worms are able to self-replicate.
True
False
You have created a Web site and need to increase visitor trust. Which of the following methods are used to build trust? (Select two.)
Logos
Testimonials
Color choice
Font size
IDS and IPS systems are a replacement for a firewall system.
True
False
Which of the following attack types is based on faking the real source of a transmission, file, or e-mail?
Backdoor
DDoS
Spoofing
Front door
To increase network security, you have decided to block port 21. Which of the following services is associated with port 21?
FTP
HTTPS
DNS
SFTP
A(n) _____ is a passive network monitoring and security system.
Servers within the DMZ sit outside of the local network.
True
False
Port _____ is used by the HTTP protocol.
A _____ sits between the Internet and the client systems responding to client requests for Web pages.
Which of the following best describes the function of the DNS server?
Uses Media Access Control addresses to locate network systems
Provides host name-to-IP resolution
Provides IP name resolution
Encrypts host names
A DoS attack is designed to overwhelm a particular resource making it unavailable.
True
False