4
Malware Infections

One of the most well-known types of computer attacks is the transmission of malware. Sometimes mistakenly referred to as a virus, malware, or malicious software, is any piece of software designed to bypass a system’s intended operation. This activity is typically not authorized by or even visible to the user. Malware has been around for as long as modern computers have. It comes in many forms, and despite the best efforts of antivirus software, it’s still common today.
In this chapter, we’ll discuss what malware is, some of its more popular variants, and how best to defend against it, while clearing up any misconceptions you might have picked up from watching fictional hackers on television.
What Is Malware?
Malware is software designed to cause damage to computer systems. So, even though a game might consume all of your computer’s memory, it’s not considered malware. The best way to define malware damage is damage caused by an unauthorized action considered abnormal for the system. For example, a normal operation might involve a user logging into the system using a username and password set up by an internal administrator. If an application allows a black hat to access the system without using a username and password, it has performed an unauthorized action.
This might seem like splitting hairs, but it’s important to understand the difference between malware and a bug or other corrupt software. If a piece of software, like the game mentioned earlier, has an unintentional bug that causes a computer to crash or does other harm, it’s not malware, it’s just an inferior program. Likewise, a browser add-on with a privacy statement that declares, “We’re going to steal your browser history and sell it” isn’t malware, even if the reader doesn’t bother to read the statement. On the other hand, if a program appears to be running normally while also performing hidden actions, such as logging keystrokes without informing users, it’s probably malware.
For the most part, malware is fairly easy to identify because it executes obviously malicious actions, such as stealing your password or allowing another unauthorized system to access your computer. But some programs perform legitimate, authorized functions while also doing undesirable activities, such as displaying ads or recording user data. Just because a program looks, acts, and sounds like a safe program doesn’t mean it isn’t running malicious code in the background.
Types of Malware
To classify different types of malware, malware analysts generally use two attributes: how the malware infects a system and what sort of attack the malware performs. These attributes help put malware into broad classes that we can use to better defend against it. In this section, we’ll examine some of the more common classes.
Although the malware we’ll discuss in this chapter fits neatly into the classes described in the following subsections, that’s not always the case in the real world. Black hats often group malware classes together to form a single malware package. For example, you might have a virus that also installs spyware and a rootkit. For this reason, it’s important to scan every part of your computer when you’re trying to get rid of a malware infection. For instance, just because you clean up the virus files doesn’t mean you’ve eliminated the entire infection.
Viruses
Perhaps the most recognized type of malware is the virus, which we define not by what it does but by how it behaves. A user must interact with a virus before it can begin executing its malicious code. We call this interaction the trigger. The trigger could be clicking a file, running a program, or opening an attachment. Once the action is taken, the virus can run its instructions and release its payload.
A virus’s payload is the code that performs whatever malicious action the virus was programmed to execute. For example, many viruses created in the 1990s, such as Chernobyl, were designed to destroy infected systems, often by rewriting or deleting critical files (Figure 4-1). Chernobyl was created by Chen Ing-hau, a Taiwanese university student who wanted to prove that antivirus software of the time was ineffective. Once activated, the code rewrote the first kilobyte of the system’s hard drives with zeros. This destroyed many critical files necessary for the system to function, including the partition table, which helps find where information is physically stored on a hard drive.

Figure 4-1: A Windows blue screen (error screen) after a successful infection by the Chernobyl virus (original image covered by the Free Art License 1.3)
As cybercrime has become more common, attackers have begun using viruses to implant other types of malware, such as trojans or ransomware (discussed on page 59), that they can then use to further exploit the system.
Although all viruses share these common characteristics, a virus’s specific target might vary. For example, file infector viruses infect files, whereas boot sector viruses infect the boot files used to start the computer when you turn it on. Macro viruses focus on, you guessed it, macros on the system. A macro is code that translates instructions sent to the computer into a longer set of instructions. For example, when you press CTRL-C, a macro translates that keypress into the Copy command. Macros are often used in Microsoft Office applications to provide additional functionality, especially in spreadsheet applications like Excel. Some viruses, known as stealth viruses, include an added layer of coding to try and hide from antivirus software.
Worms
Worms are malware designed with one goal in mind: to reach as many systems as possible. Unlike a virus, a worm can infect systems without any direct user contact, which means it can spread through a network more easily than a virus can. Once the worm infects a new system, it looks for additional uninfected computers to which it can spread.
Worms are usually able to spread without user contact because they exploit a vulnerability that allows for remote code execution, or the execution of any code, even by unauthorized users, on the system from a remote location. This allows adversaries to install programs, create users, or even change network settings. Typically, the vulnerabilities that allow remote code execution involve tricking the system into believing a user or process has permission to run code. A classic example of this is the ILOVEYOU worm (Figure 4-2). Created in 2000, this worm took advantage of a vulnerability on Windows systems at the time that caused the file type .vsb (which indicates a Visual Basic script) to be hidden. This meant when the file was sent via email, the attachment looked like a normal text document. But when users opened it, it ran a script that infected the system by overwriting certain file types. It then used the target’s email account to send copies of the file to every contact in the address book associated with Microsoft Outlook. The most common means of spreading a worm to a new system is through email. This provides the worm with a method of reaching other users and a list of email addresses with which to do so. Within 10 days, 50 million ILOVEYOU infections were reported.

Figure 4-2: An example of the email sent by the ILOVEYOU worm
Historically, hackers have used worms as bragging rights. The more systems your worm was able to infect, the more credibility you got in the hacking community. Some worms, like Melissa, spread without a payload. Melissa was a macro created in 1999 by David Smith. It infected email systems using an attachment masquerading as a Word document. Clicking the file ran macro code that opened pornographic sites and sent copies of itself to everyone in the person’s address book. Just because a worm doesn’t have a payload doesn’t mean it isn’t harmful. Melissa took many email servers offline when the worm flooded them with emails until they crashed. Other worms, such as Code Red and SQL Slammer, also caused major outages of network services because of the amount of traffic they generated. Code Red appeared in July 2001 and within days infected nearly 400,000 systems across the internet. SQL Slammer was even quicker: when it appeared in 2003, it infected some 75,000 hosts within 10 minutes. When worms do carry payloads, they usually include malware like ransomware or remote access backdoors (which we’ll discuss shortly).
Trojans
Like the classic Greek story this type of malware is named after, a trojan is malware that pretends to be legitimate software while secretly running malicious tasks in the background. The trojan imitates many different software elements, including games, Word documents or PDFs, and even add-ons or macros. Once the trojan is installed, it usually begins running unwanted code, but it might not activate its full payload until a determined parameter is met or a command is sent. For example, many trojans send an HTTP request to a server controlled by a black hat waiting to receive commands from an infected computer. The fact that trojans mimic legitimate programs makes them very difficult to detect, which allows them to remain in place for long periods of time.
One of the most common types of trojan is called the Remote Access Trojan (RAT). Its main purpose is to place a silent, undetected program on your system that allows an adversary to control your computer remotely. This program connects to a command and control (C&C) server, which allows an attacker to send commands to your computer without detection using normal traffic filtering procedures.
Essentially, the RAT uses normal traffic, such as requests for a website on the internet, to ask for additional commands from the C&C server. The attacker can then respond with additional commands, or in the case of the RAT, use the program to gain backdoor access to the system. (Backdoor access simply means access through unknown, unauthorized means.) This allows the black hat to use the system either to move to other targets or to attack other systems.
Ransomware
Ransomware is malware that uses encryption to lock a computer until a ransom is paid. Once the ransomware deploys, it encrypts specific targets, such as files in use, entire hard drives, or even entire databases, making them impossible to use. Because the files are encrypted, the computer can’t read them, making them inaccessible until the black hat provides the key that decodes the content. The attacker holds on to the key until a ransom is paid, usually using a form of untraceable money like cryptocurrency.
Adversaries use this type of malware often because it has several strengths. First, it’s easy to deploy and scale. A single infection can spread across an entire network or encrypt key critical systems, effectively shutting down an organization. Second, it’s nearly impossible to bypass once deployed. Encryption is very hard to break, and many modern encryption protocols would take literally billions of years to crack. The only effective method to avoid paying the ransom is to maintain backups. But many organizations pay even when they have backups because of the time it takes to restore the files. Third, it’s cheap and effective. It costs nothing for an adversary to attempt infection, but a single success nets them thousands—or even hundreds of thousands—of dollars. More organizations opt to pay as the urgency of their services rises and cyber insurance that covers such attacks becomes more prevalent.
Spyware and Adware
Spyware and adware are probably some of the most annoying malware types that affect systems. Spyware steals data from your system, whereas adware injects ads into your system while you use it. Both kinds of malware typically infect web browsers or other programs that use the internet. They particularly like to hide inside add-ons or macros that users install in a browser. This allows them to track your browsing history, links clicked, and accounts accessed, all while serving up ads in annoying pop-ups that appear to randomly flash onscreen. Although these kinds of malware usually have less severe consequences than other types, they can cause your system to slow down and sometimes steal valuable personal data, including passwords. They can also lead to further infection from other malware kits because the loaded ads point to other types of malware, like trojans.
Rootkits and Bootkits
Rootkits and bootkits provide an attacker with unprecedented access to a system. A rootkit is malware that attempts to access a computer’s internal system files, which are files that run the operating system. For example, a rootkit might replace the files that control logins. By doing this, a black hat can create a secret login that gives them full administrative privileges to the system while hiding the actual account from other users, so it remains undetected. Typically, these files are off limits to unauthorized users. To access these files, the rootkit takes advantage of a vulnerability that lets it run as an administrator. From there, it can make all sorts of modifications to system files, including adding users, changing file permissions, or changing a system’s network settings.
A bootkit accesses and modifies a system’s boot record, which is a file that starts an operating system when you turn on your computer. The boot record initializes many different configurations and usually loads additional software, like hardware drivers, which an operating system uses to interact with the computer’s hardware, such as its keyboard and mouse. By modifying the boot record, the malware can change how the system functions, giving full access to a black hat or loading other malicious software, like bots, into the system (more on bots in Chapter 6). The other advantage to a bootkit is that many of the security functions that come with a system don’t launch until after the system boots. This means that the malware can run without being detected by an antivirus engine or other security tool. Internet of Things (IoT) devices, which are small devices with network connections, such as thermostats or security cameras, are especially susceptible to bootkits, because they often run all their functions almost entirely off the boot record (we’ll discuss IoT devices in Chapter 6).
Bootkits and rootkits are extremely difficult to detect on a system. Rootkits modify the programs that are designed to detect them. For example, they can modify your antivirus program so it skips the location at which the rootkit is installed when running a scan. Bootkits evade detection because traditional antivirus software only works once the operating system is loaded, which occurs after the boot record runs. This makes it very difficult to find anything wrong with the system until it’s too late.
The typical way to detect both types of infections is through traditional symptoms, such as a slow-running system, missing or corrupted files, or weird running processes. You might also be able to detect a rootkit by using antivirus software installed on a USB flash drive or other media. Some systems also have the ability to do a secure boot. This modifies the boot process to detect errors or anomalies associated with bootkits to stop them before they can be run. Windows systems perform a secure boot by checking whether the boot record came from Microsoft. If the system discovers a modified boot record, the check will cause the system to stop booting. But even then, finding the malware is only part of the battle. Removing it is tricky, and often, it’s better to completely wipe the system and reinstall it rather than risking letting the infection linger in some inaccessible corner.
Polymorphic Malware
The strongest and most dangerous form of malware is polymorphic malware. This malicious software has advanced capabilities that allow it to change its code based on certain factors, such as the kind of system it’s currently infecting or the applications running on the system. This lets it adapt to the environment instead of just running a set payload, making it extremely difficult to detect by traditional means, because it might not be harmful until a specific situation is triggered. Once the trigger is set off, the malware activates, changes its code to run destructive operations, and begins to carry out its designed task.
Fortunately for us, polymorphic malware is extremely rare and crafted for very specific targets. Because of the time and resources required to create this type of malware, only state actors normally use it. One famous example of polymorphic malware is the Stuxnet virus. This malware was designed by the United States and its allies to infect Iranian nuclear centrifuges and stop them from functioning properly. The Stuxnet creators specifically crafted it to hide until it entered the centrifuge system, at which point it rewrote its code and infected the device. Stuxnet was able to remain undetected for many months, successfully sabotaging the program.
As technology advances, writing advanced pieces of code like polymorphic malware becomes easier. You might find polymorphic features integrated into traditional malware to provide it with added functionality. For example, by using machine learning theory and algorithms, it’s possible to train malicious software to evade antivirus detection, even if an antivirus program detected that same destructive software previously. According to recent research from Hyrum Anderson, an attacker could run the malware through a set of antivirus engines using a machine learning program, which would tweak the software’s code slightly based on the result of the scans. It would repeat this cycle hundreds of thousands of times, tweaking the malware code until none of the engines returned a positive detection. The result will be a piece of harmful software that essentially runs the same as it did before but attracts no attention from antivirus engines. The adversary doesn’t have to do anything to achieve this; the machine learning program does all the work for them.
How Black Hats Deploy Malware
Black hats deploy malware for a variety of reasons. To understand how and why an attacker releases malware on a system, let’s walk through some typical attacks. Although all malware is different, most of it is installed in your system in consistent ways.
The first step to any malware deployment is to create the destructive software. Generally, adversaries do this in two ways: by taking advantage of an existing vulnerability or starting from scratch. Many black hats use malware that is already designed to exploit a vulnerability for their own attacks. This means they add specific payloads to an existing piece of malware based on their needs. A great example of this is the EternalBlue exploit, developed by the National Security Agency (NSA) and later used by attackers in several malware samples. The exploit allowed for remote code execution on a target Windows machine by taking advantage of the way the Server Message Block protocol, which manages network shares, handles certain types of information sent to it. In each case, the attackers added their own code to execute.
Writing new code from scratch is more difficult than using a framework, but it tends to be more effective. The reason is that the target system’s protections won’t have encountered the malware that was created before it’s deployed. Because antivirus software relies heavily on code from actual malware samples, a brand-new piece of malware has a much higher chance of avoiding detection (as we’ll discuss later in this chapter).
After creating the destructive code, the attacker moves to the next step: initial infection. They can install the damaging software on a system through a variety of means, but the most effective is social engineering, a process described in Chapter 3. Using phishing techniques, it’s often easy to get users to download the malware and execute it. For instance, attackers like to hide unsafe code inside nondescript files types, such as Word documents or Excel spreadsheets. Both kinds of files allow you to create macros, where black hats can store malicious code that activates when users open the document, causing the initial infection. Using links to execute scripts that download harmful code to the computer is also common. Because a lot of malware needs human interaction to work, the more benign-looking the file or link, the better. This is especially true for trojans, which must remain on the system long term to be effective.
The initial infection will release the full payload, but that doesn’t mean the malware has necessarily finished working. At this stage, some malware focuses on a specific action; for example, ransomware encrypts files or other storage media. Other malware focuses on creating an APT, which is sophisticated malware that remains hidden on a network for a long period of time, gathering data and other information before executing a large attack. A RAT is an example of a possible APT; it allows an adversary to return to a system repeatedly through the backdoor to gather more information about its environment. APTs are extremely dangerous and difficult to deal with, because by design they avoid many traditional modes of detection. Even worse, some malicious software performs flashy attacks, such as encrypting all your Word documents, to hide the secret code that installed a rootkit onto the system. This is why digital forensics is critical in a malware attack (see “How to Defend Against Malware” next).
Once the infection is in place and the payload is deployed, the contagion can be spread. This might involve sending the malware in an email using the host system’s contact list; moving through the network using transport protocols, such as File Transfer Protocol (FTP) or Hypertext Transfer Protocol (HTTP); or hiding in a file until a new user clicks it. While worms are particularly adept at spreading, ransomware and viruses can spread quickly and easily as well, although they might require user input to do so.
How to Defend Against Malware
The best way to defend against malware is to use anti-malware software, commonly referred to as antivirus programs (although they now guard against nearly all forms of malware, not just viruses). Antivirus programs are available from many commercial vendors. Microsoft systems also have a built-in antivirus program called Microsoft Defender (formerly Windows Defender). But merely downloading an antivirus program doesn’t necessarily provide complete protection. To ensure that your system is safe, you need to get the proper software to diminish the risks your computer might encounter.
Antivirus software comes in two basic detection forms: signature and heuristic. The former uses a code signature to recognize malware. A code signature is a unique part of a destructive program’s code that helps identify it. For example, let’s say you receive a file in your email. A signature antivirus program scans the file and notices that the file includes the code sparklekitten.exe as part of a macro. It then compares that code to a database of known malware signatures and determines that sparklekitten.exe is flagged as malicious. The antivirus software will then alert you and possibly quarantine the file, depending on its settings.
Signature antivirus software is extremely fast because all it does is compare a piece of code to a signature database to verify whether it is malware. Figure 4-3 shows an example of such a program running on a Linux system. It also doesn’t require many system resources, so it can run on most systems—even those with low memory capacities or a slow central processing unit (CPU), which is where the computer processes the instructions sent to it. However, for the software to detect the malware, its database must contain the malware’s signature. This means that newly created malicious software can avoid antivirus detection, at least until enough infections have been reported to the software manufacturers for them to add an accurate signature to the database. It also means that black hats can tweak the signature of a piece of malware to avoid detection (or use machine learning to change the malware, as discussed earlier in this chapter). Due to these pros and cons, it’s best to deploy signature antivirus software on endpoint systems, such as desktops, mobile phones, laptops, and other systems that work on data, to avoid slowing down actual work being done on the system.
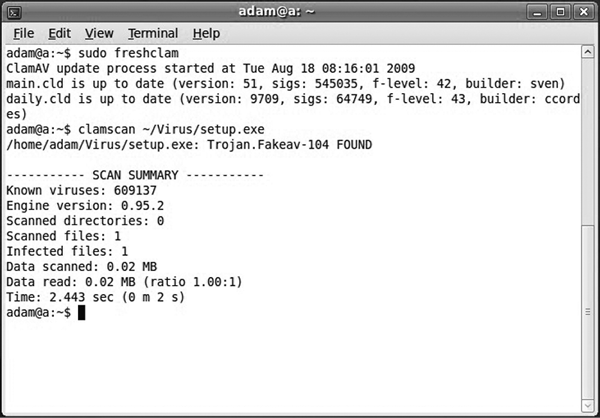
Figure 4-3: A screenshot of antivirus software running on a Linux-based system (this image was modified from the original created by SourceFire and is licensed under the GNU General Public License)
Heuristic antivirus detection adapts its detection based on the flow of traffic on a network, looking for abnormalities that are outside the normal traffic flow. What is normal will vary based on how the network is used, so the heuristic antivirus program has to spend time learning this baseline. Then it can notice anomalies. For example, if a RAT is installed on your computer, its first step is to send a message across the network to its C&C server. A heuristic antivirus program could detect this behavior and recognize that this isn’t normal traffic (maybe because it occurs at an odd hour or comes from a system that doesn’t usually send this type of traffic). However, as stated earlier, it’s still possible for the RAT to imitate what the heuristic system considers normal.
Heuristic antivirus detection is very effective because it can detect malware that is brand new, as well as malware that is trying to hide, such as rootkits or bootkits. But it requires more setup and maintenance than signature-based detection. To find traffic that isn’t normal, the heuristic engine first needs to know what normal looks like for your system. This means it must determine an accurate baseline before it can work effectively, and that baseline must routinely update as the behavior of the system’s users changes. Typically, you’ll find heuristic systems in a few key high-traffic areas, such as on the firewalls that scan traffic coming into a network from the outside.
Antivirus software of either type scans most kinds of data coming into or leaving your system, depending on the settings or the specific product you’re using. This includes documents like PDFs or pictures, applications like Excel or games, and even web traffic. The robust scanning toolkits in modern systems make it difficult for malware to find its way onto your screen by traditional means. However, good detection relies on your having a properly maintained antivirus program. You need to routinely update your software and perform automatic, periodic scanning. You should also make sure that your software is set up to scan all types of data, especially attachments in emails or downloaded files from the internet.
Despite the numerous technological advancements in antivirus software, it’s still possible for attackers to circumvent those scans by understanding and avoiding the way they detect malware files. For example, you might receive a normal, clean Word document that the antivirus software won’t react to; the document wouldn’t show up as known malware in any signature database or appear to be unusual traffic. But when you open it, you might trigger a link that reaches out to the internet and downloads ransomware. Before your antivirus software has a chance to react, the ransomware might execute and lock you out of all your files.
You can also use file integrity tools to ensure that a file hasn’t been modified to hide a trojan or other malware. A file integrity tool uses a file hash, which we’ll discuss in Chapter 9, to check whether a file was modified. Most companies provide a hash of their applications or files on their websites. You can compare this hash to the hash of the file or application you downloaded to make sure a black hat hasn’t added malware to it. If the hashes match, the file or application hasn’t been modified.
To truly keep your computer safe from malware, you must practice your social engineering defenses. Weird links, unprompted attachments sent in email, and other such suspicious requests all indicate that an adversary might be trying to get you to download malware.
Exercise: Analyzing Malware and Managing Antivirus Settings
Anticipating the sources of malware and avoiding them are critical steps to keeping your system secure. After all, if the malware never gets onto your computer, you don’t have to worry about it infecting your system. In this exercise, you’ll use some free online tools to scan a PDF and find out whether it’s infected with malware. You’ll also learn more about the antivirus settings built into your computer, so you’ll know what to do if you do accidentally download malware onto your system. By the time you finish the exercise, you’ll know how to identify and defend against all sorts of malware threats.
Analyzing Malware in Attachments
Let’s say you’ve received a strange PDF that looks like it came from a friend. This friend has sent you emails before with attachments like this, but you weren’t expecting anything from them and aren’t sure whether or not it’s malicious. One solution is to ask your friend if they sent the file; another is to just delete it and move on with your life. However, say your friend isn’t available, and you really want to know whether or not the file is safe. Well then, you’ll need to do some malware analysis.
To complete this exercise, you can use a PDF created for this book, called maliciouspdf.pdf, which is available at https://nostarch.com/cybersecurityreallyworks/. Alternatively, you can analyze any file you’d like; just make sure to label it DO NOT OPEN so you don’t forget it’s potentially malware.
First, you’ll need to verify the type of file that was sent. Office documents, executables, media files, and PDFs aren’t usually harmful unless you open them. But some, such as .js, .sh, or .script files, could execute upon downloading; others, like .dll files, might be activated by other processes once downloaded. The best option is to download a file using a virtual machine. A virtual machine is an environment that’s isolated from the rest of the physical computer, so if it does become infected, it very likely won’t infect the entire system. For malware to break out of the virtual machine, it would need to be very sophisticated software.
Because not everyone has access to a virtual machine, another solution is to download the suspected harmful file to a cloud platform. For example, if you use OneDrive for Windows, you can save the file directly to your online OneDrive folder instead of to your computer. Often, this will trigger an antivirus scan on the file, which might indicate it’s infected without you having to do further analysis. If you don’t have an online folder, the next best option is to use a flash drive or external hard drive. Although it’s still possible that malware saved to external storage will infect your main system, it reduces some of the risk. Just be sure no critical files are on the drive before you save the suspicious file.
When you download the file, make sure you do not open it. Click the Save As option and move it to a folder called something like Do Not Open or Malware to remind you and others not to accidentally open it. Also, make sure your system doesn’t autorun any files by default. Many systems present you with an Open With option when you download a file. Do not select this option.
Once you’ve safely saved the file, you can begin running it through the analysis tools. The first website you’ll use is VirusTotal (https://www.virustotal.com/), which you used in Chapter 3 to analyze a suspicious URL link. This time, you’ll use the File Analysis feature. When you load the page, you’ll see an option to upload a file for analysis. Click Choose File, navigate to your saved file, and select it for upload. Figure 4-4 shows an example using the maliciouspdf.pdf file.
Figure 4-4: The malicious PDF ready for upload
Once the file is uploaded, click Confirm Upload to begin the analysis. VirusTotal runs the file through multiple antivirus software packages and returns the results, informing you whether or not the file is malicious. Keep in mind that VirusTotal will specify the number of engines that found malware in the file. If even one engine reports the file as being unsafe, you can assume it’s malware regardless of whether the others indicate it’s clean. Figure 4-5 provides an example of the output for maliciouspdf.pdf.

Figure 4-5: The results from VirusTotal
As you can see, 37 different malware scanning services reported that the file contained malware. This file was created using a well-known exploit whose signature would have been loaded into many antivirus programs, making it easy to detect. But this might not always be the case. A file might contain new malware that doesn’t yet have a standard signature, causing VirusTotal to report the file as clean when it’s actually infected. To deal with this possibility, you’ll need to use another familiar tool, Joe Sandbox.
As you learned in Chapter 3, Joe Sandbox (https://www.joesandbox.com/) allows you to analyze a link or file using a cloud platform that functions like an actual system. In this exercise, you’ll use it to open the file in a safe environment where you can thoroughly analyze it. To start, upload the file, as shown in Figure 4-6.
Figure 4-6: Uploading the file on Joe Sandbox
Once the file is uploaded, the sandbox will take a few minutes to finish the analysis. Joe Sandbox opens the file and then runs it through several different antivirus scans. Figure 4-7 shows that these antivirus scanners identified maliciouspdf.pdf as malicious.

Figure 4-7: Joe Sandbox results for maliciouspdf.pdf
Joe Sandbox also provides additional analysis aimed at understanding what type of malware might be embedded in the file and how the malware would have affected your system if downloaded and opened. This can be especially helpful if you think you might have accidentally opened the file and need to figure out what sort of malicious activity it performed. Figure 4-8 shows some useful parts of the report on maliciouspdf.pdf.
This analysis gives you a detection level, in this case, malicious, and also provides two ways of classifying the file: Signatures and a Classification map. Recall that many antivirus programs use signature files to detect malware. The Signatures section displays the signatures that match the file being analyzed. The Classification section then provides an estimate of what type of malware the file contains based on the scans and signatures detected.

Figure 4-8: Overview of the analysis for maliciouspdf.pdf
Next, Figure 4-9 displays a breakdown of what processes were created when the file was executed in the sandbox.
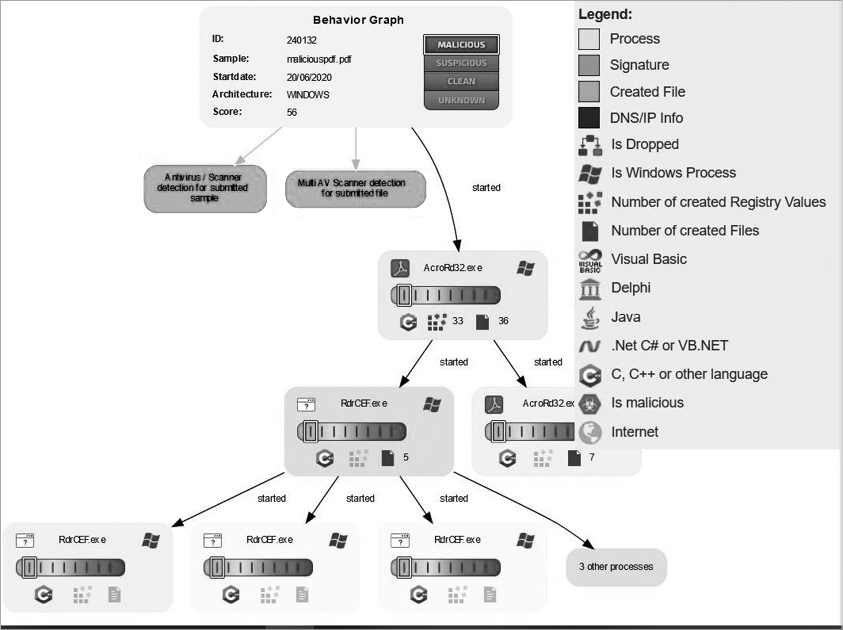
Figure 4-9: Processes created by maliciouspdf.pdf when it’s opened
The report also lists any child processes created by parent processes. In this example, the Adobe Reader process started when the PDF was opened and then spawned two child processes. One of these processes spawned even more child processes. This part of the report can be useful to identify any processes that aren’t normally found in this type of file execution, such as the child processes here, which aren’t associated with Adobe.
Reviewing Antivirus Settings
Now that you’ve analyzed the suspicious document and know it’s malware, you need to review the antivirus settings on your system to make sure your computer is protected against infection.
Built-in antivirus software doesn’t come with macOS, but you can use several third-party options to keep your system safe. All Windows 10 systems come with Microsoft Defender installed, which is integrated into the operating system’s security settings and provides a wide range of malware protection, including against ransomware. Although other commercial products, such as Sophos, Check Point, Avast, and Symantec, offer additional features, we’ll focus on Microsoft Defender because it’s free and built into Windows 10 by default.
macOS
Most modern antivirus software comes with an Apple-compatible version. If you’re looking for a free program, Avast and Sophos provide effective products. But when you use the free versions, the features are limited. Both products offer paid versions that provide more robust features.
Although not as many existing types of malware are programmed to attack Apple computers as Windows systems, it’s still essential to scan your computer regularly. It’s also critical to set automatic updates so you’ll have the latest signatures as soon as they’re available. Be wary of where you get applications, even from the official Apple store. Malware, especially ransomware and trojans, is often disguised as applications, and some of these have been known to slip past Apple’s verification process and been placed in the official store.
Windows 10
To access the Microsoft Defender settings, locate the security dashboard by entering security into the search bar located in the taskbar at the bottom-left corner of the screen. Click Windows Security and then click Virus & Threat Protection to open the Microsoft Defender settings for antivirus protection, as shown in Figure 4-10.
You can perform a few different actions using these options. First, you can run a manual scan using the Quick Scan Option. This will scan the most likely places a virus or other malware might be located, and it does so in no time at all. As you can see, the last scan done on this system took one minute and 26 seconds to scan 42,363 files. Quick scans are beneficial if you think your computer has been infected with a well-known, ordinary piece of malware. But not all malware hides in the obvious files. To make sure your system is truly clean, it’s best to scan more than those files that a quick scan inspects. To do this, click Scan Options below the Quick Scan button.

Figure 4-10: Virus & threat protection settings
Microsoft Defender offers several options for scanning other than a quick scan. The full scan option inspects your entire operating system. This is a more intense scan than a quick scan, so it can slow down your computer and takes a long time to complete. But it provides a comprehensive report of your system by checking every nook and cranny. You can also do a custom scan of specifically chosen files. It’s best to use this option when you know exactly what type of malware you’re dealing with and know where it likes to hide. For example, you could use the analysis report from Joe Sandbox to determine which files or folders a malicious file interacted with, and then scan them to see whether the malware infected your system as well. The Windows Defender Offline scan is essentially a boot sector scanning option. It restarts your computer and scans it before the system has a chance to fully boot to ensure that rootkits or bootkits are unable to hide or modify processes once the system is started. Figure 4-11 shows these scanning options.
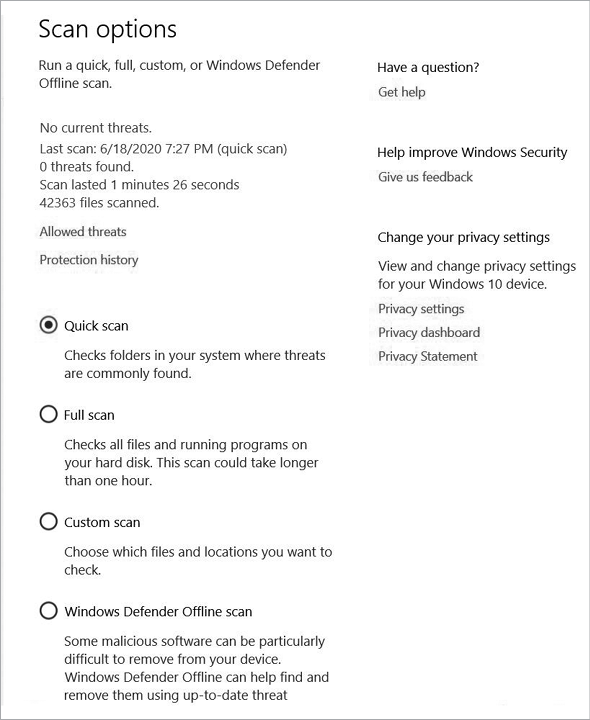
Figure 4-11: Microsoft Defender scan options
When you return to the Virus & Threat Protection dialog, find the Protection History option. This shows you a list of all the threats that Microsoft Defender has detected and what it did to neutralize them (Figure 4-12). If you’re ever concerned that a virus wasn’t mitigated properly or that the antivirus software might have removed legitimate files accidentally (which is rare but happens from time to time), you can use this dialog to view the recent activity. Figure 4-12 shows an example of two threats that were discovered and quarantined on the system (in case you were wondering what happens when you add malicious PDFs to your system as part of this exercise).
The additional options below Virus & Threat Protection Settings determine how Microsoft Defender runs, including whether it offers real-time protection, which stops malware from installing, or whether it submits samples of malicious code to an antivirus database to be used for signatures. Microsoft Defender does provide some cloud-powered heuristic resources as well, but overall, it’s a signature-based system. By default, it will automatically update its list of signatures, but you should make sure these are up-to-date nonetheless. You can manually check for updates by clicking Check for Updates in the Virus & Threat Protection dialog.

Figure 4-12: Microsoft Defender protection history
The final setting you’ll want to check is ransomware protection, as shown in Figure 4-13. To guard against ransomware, Microsoft Defender controls access to folders and provides backups using certain cloud platforms. In these settings, you can see which files are protected and modify some of the protection settings. Keep in mind that Microsoft Defender isn’t foolproof. If you maintain regular backups on an external hard drive or cloud system separate from your main storage, you’ll further help protect your system should it be locked by ransomware.
You’ve now learned how to analyze a file for potentially embedded malware and have prepared your Windows system to reduce the threat of infection. Both skills are imperative for defending your system from any malware threat. Combining these skills with those you learned in Chapter 3 will make it even more difficult for a black hat to compromise your system. Prevention is one of the best ways to defeat malware. Keep in mind that if malware never makes it onto your system, you don’t have to worry about what it does.
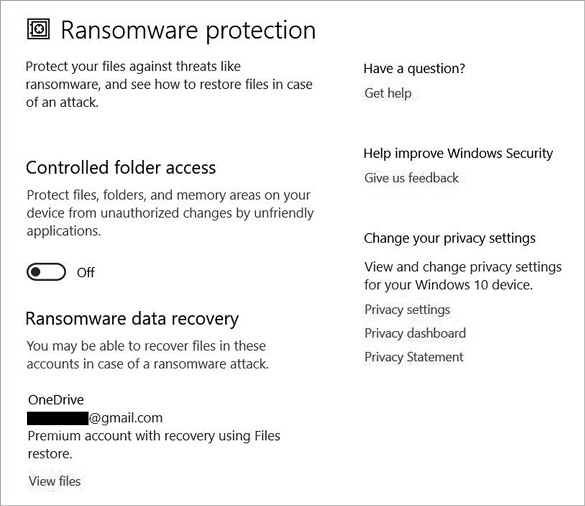
Figure 4-13: Microsoft Defender ransomware protection settings
Conclusion
This chapter focused on the various types of malware and their distinct characteristics. Viruses and worms, the most traditional malware types, typically carry payloads that perform malicious actions when activated. In addition, worms are designed to spread the malware to new systems. Ransomware encrypts files and holds them for ransom, allowing black hats to extort money from their victims. Trojans hide in plain sight, allowing backdoor access or even installing rootkits or bootkits, which infect a system’s heavier security areas to cause modifications to its operation. Spyware and adware are sometimes more annoying than they are malicious, stealing traffic and serving up ads, such as pop-ups that appear out of nowhere. But the worst type is polymorphic malware. This advanced software can change its code on the fly, allowing for advanced persistent infections that are incredibly hard to detect.
In this chapter, we also explored how to defend against malware. The key is to combine social engineering defense skills with advanced anti-malware software. By being mindful of where and what you click and what you download, you can prevent an infection. If a system does get infected, antivirus software helps detect the malicious code by using either signature or heuristic characteristics. Signature detection is fast and requires few resources but isn’t as advanced as heuristic detection, which compares traffic to a baseline to determine whether it’s normal or unusual. By combining these tactics, you can keep your system free of infection and running the way it should.
