CHAPTER 7
AWS Reference Architecture
As mentioned in Chapter 5, the NIST Cybersecurity Framework (CSF) was originally published in February 2014 in response to Presidential Executive Order 13636, “Improving Critical Infrastructure Cybersecurity,” which called for the development of a voluntary framework to help organizations improve the cybersecurity, risk management, and resilience of their systems.
NIST conferred with a broad range of partners from government, industry, and academia for over a year to build a consensus-based set of sound guidelines and practices. While intended for adoption by the critical infrastructure sector, the foundational set of cybersecurity disciplines comprising the CSF have been supported by government and industry as a recommended baseline for use by any organization, regardless of its sector or size. Industry is increasingly referencing the CSF as a de facto cybersecurity standard.
AWS Security Framework Overview
The Amazon NIST Cybersecurity Framework report articulates that the NIST CSF offers a simple construct consisting of three elements—core, tiers, and profiles. See Figure 7.1.
- The core represents a set of cybersecurity practices and outcomes, and technical, operational, and managerial security controls (referred to as informative references) that support the five risk management functions–Identify, Protect, Detect, Respond, and Recover.
- The tiers characterize an organization's aptitude and maturity for managing the CSF functions and controls.
- Profiles are intended to convey the organization's “as is” and “to be” cybersecurity postures.
These three elements enable organizations to prioritize and address cybersecurity risks consistent with their business and mission needs. It is important to note that implementation of the core, tiers, and profiles are the responsibility of the organization adopting the CSF (e.g., government agency, financial institution, commercial startup, etc.).
This chapter focuses on AWS solutions and capabilities supporting the core that can enable you to achieve the security outcomes (i.e., subcategories) in the CSF. It also describes how AWS services that have been accredited under FedRAMP Moderate and ISO 9001/27001/27017/27018 align to the CSF. The core references security controls from widely adopted, internationally recognized standards such as ISO/IEC 27001, NIST 800-53, and Control Objectives for Information and Related Technology (COBIT).
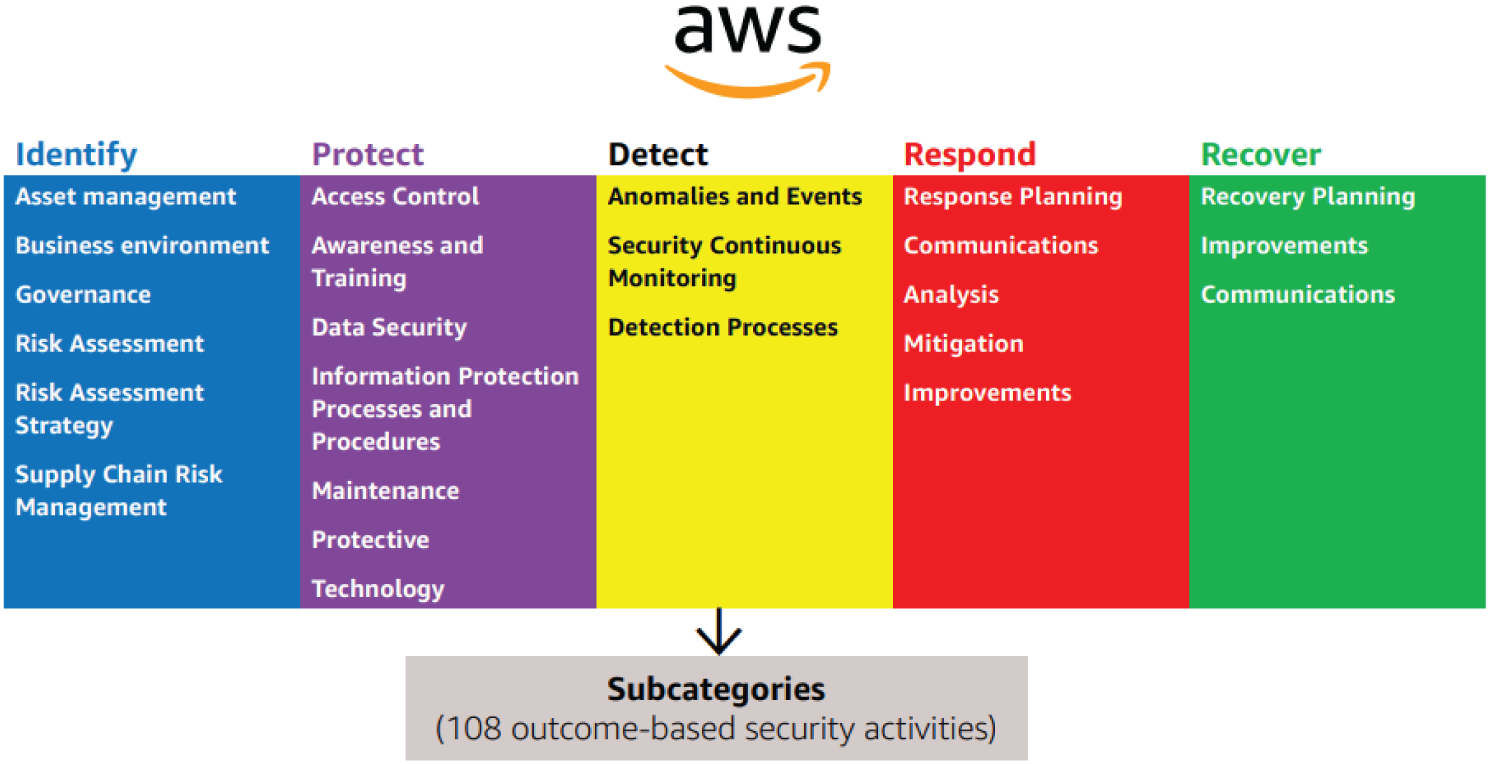
Figure 7.1: Amazon NIST Cybersecurity Framework (CSF)
The Identify Function Overview
This section addresses the six categories that comprise the “Identify” function: Asset Management, Business Environment, Governance, Risk Assessment, Risk Management Strategy, and Supply Chain Risk Management. They “develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities.”
- Asset Management: The data, personnel, devices, systems, and facilities that enable the organization to achieve business purposes are identified and managed consistent with their relative importance to business objectives and the organization's risk strategy.
- Business Environment: The organization's mission, objectives, stakeholders, and activities are understood and prioritized; this information is used to inform cybersecurity roles, responsibilities, and risk management decisions.
- Governance: The policies, procedures, and processes to manage and monitor the organization's regulatory, legal, risk, environmental, and operational requirements are understood and inform the management of cybersecurity risk.
- Risk Assessment: The organization understands the cybersecurity risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals.
- Risk Management Strategy: The organization's priorities, constraints, risk tolerances, and assumptions are established and used to support operational risk decisions.
- Supply Chain Risk Management: The organization's priorities, constraints, risk tolerances, and assumptions are established and used to support risk decisions associated with managing supply chain risk. The organization has established and implemented the processes to identify, assess, and manage supply chain risks.
The Protect Function Overview
This section addresses the six categories that comprise the “Protect” function: Access Control, Awareness and Training, Data Security, Information Protection Processes and Procedures, Maintenance, and Protective Technology. The section also highlights AWS solutions that you can leverage to align to this Protect function.
- Identity Management, Authentication, and Access Control: Access to physical and logical assets and associated facilities is limited to authorized users, processes, and devices and is managed consistent with the assessed risk of unauthorized access to authorized activities and transactions.
- Awareness and Training: The organization's personnel and partners are provided cybersecurity awareness education and are trained to perform their cybersecurity-related duties and responsibilities consistent with related policies, procedures, and agreements.
- Data Security: Information and records (data) are managed consistent with the organization's risk strategy to protect the confidentiality, integrity, and availability of information.
- Information Protection Processes and Procedures: Security policies (that address purpose, scope, roles, responsibilities, management commitment, and coordination among organizational entities), processes, and procedures are maintained and used to manage protection of information systems and assets.
- Maintenance: Maintenance and repairs of industrial control and information system components is performed consistent with policies and procedures.
- Protective Technology: Technical security solutions are managed to ensure the security and resilience of systems and assets, consistent with related policies, procedures, and agreements.
The Detect Function Overview
This section addresses the three categories that comprise the “Detect” function: Anomalies and Events, Security Continuous Monitoring, and Detection Processes. We summarize the key AWS solutions that you can leverage to align to this function.
- Anomalies and Events: Anomalous activity is detected in a timely manner and the potential impact of events is understood.
- Security Continuous Monitoring: The information system and assets are monitored at discrete intervals to identify cybersecurity events and verify the effectiveness of protective measures.
- Detection Processes: Detection processes and procedures are maintained and tested to ensure timely and adequate awareness of anomalous events.
The Respond Function Overview
This section addresses the five categories that comprise the “Respond” function: Response Planning, Communications, Analysis, Mitigations, and Improvements. We also summarize the key AWS solutions that you can leverage to align to this function.
- Response Planning: Response processes and procedures are executed and maintained to ensure timely response to detected cybersecurity events.
- Communications: Response activities are coordinated with internal and external stakeholders, as appropriate, to include external support from law enforcement agencies.
- Analysis: Analysis is conducted to ensure adequate response and support recovery activities.
- Mitigation: Activities are performed to prevent expansion of an event, mitigate its effects, and eradicate the incident.
- Improvements: Organizational response activities are improved by incorporating lessons learned from current and previous detection/response activities.
The Recover Function Overview
This section addresses the three categories that comprise the “Recover” function: Recovery Planning, Improvements, and Communications. We also summarize the key AWS solutions that you can leverage to align to this function.
- Recovery Planning: Recovery processes and procedures are executed and maintained to ensure timely restoration of systems or assets affected by cybersecurity events.
- Improvements: Recovery planning and processes are improved by incorporating lessons learned into future activities.
- Communications: Restoration activities are coordinated with internal and external parties, such as coordinating centers, Internet service providers, owners of attacking systems, victims, other CSIRTs, and vendors.
AWS solutions validated by third-party assessors are available today for public and commercial sector alignment with the NIST CSF. Each of these services maintains a current accreditation under FedRAMP Moderate and/or ISO 27001. When deploying AWS solutions, organizations can have the assurance that AWS services uphold risk management best practices defined in the CSF and can leverage these solutions for their own alignment to the CSF.
Let's investigate these capabilities in detail. The next section refers to an AWS capability reference architecture that can be aligned to the MITRE ATT&CK Framework.
AWS Reference Architecture
Figure 7.2 illustrates an AWS Reference Architecture that was introduced at the AWS re-Invent conference and is slowly gaining traction in the industry. We discuss each of these capabilities in detail in the following sections.
The Identify Function
This section discusses the Identify capability addressed by the AWS service shown in Figure 7.3. We discuss each of the key services in detail in the subsequent sections.
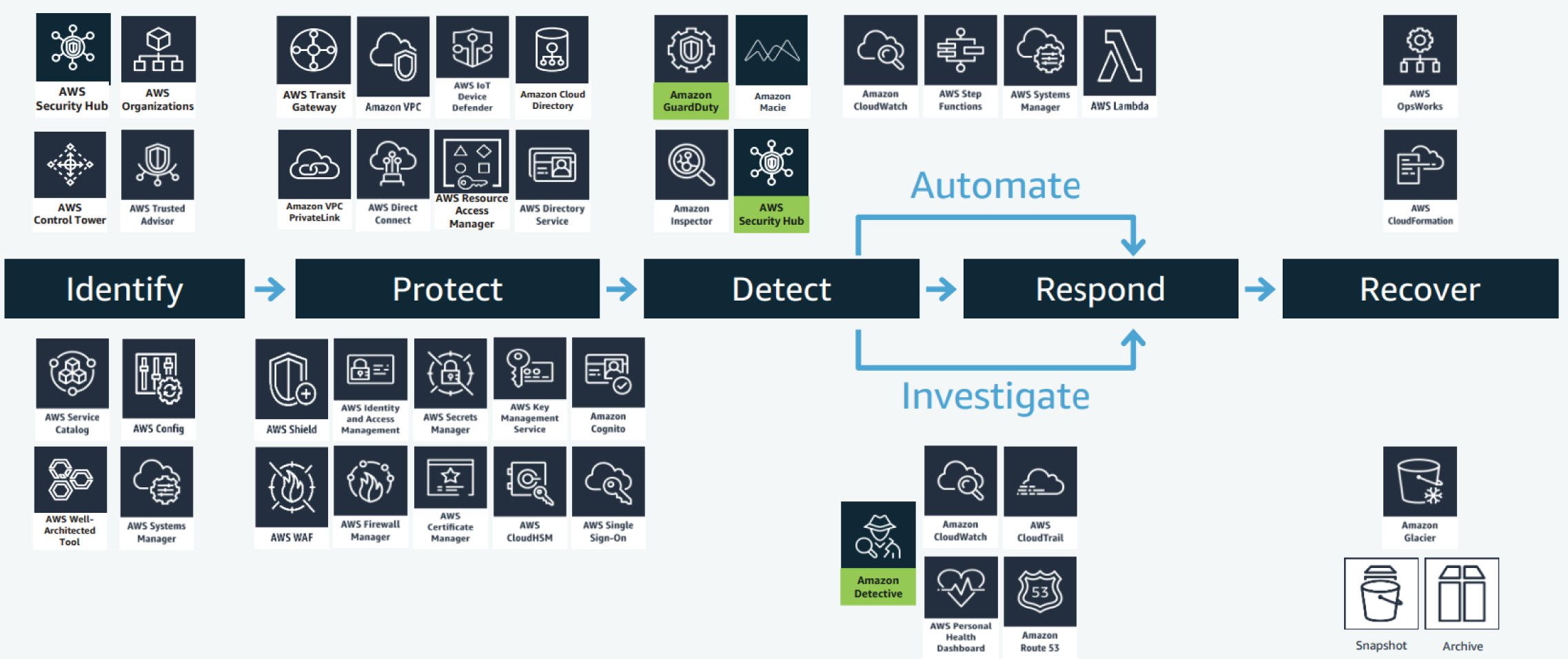
Figure 7.2: AWS Reference Architecture aligned to the MITRE ATT&CK Framework
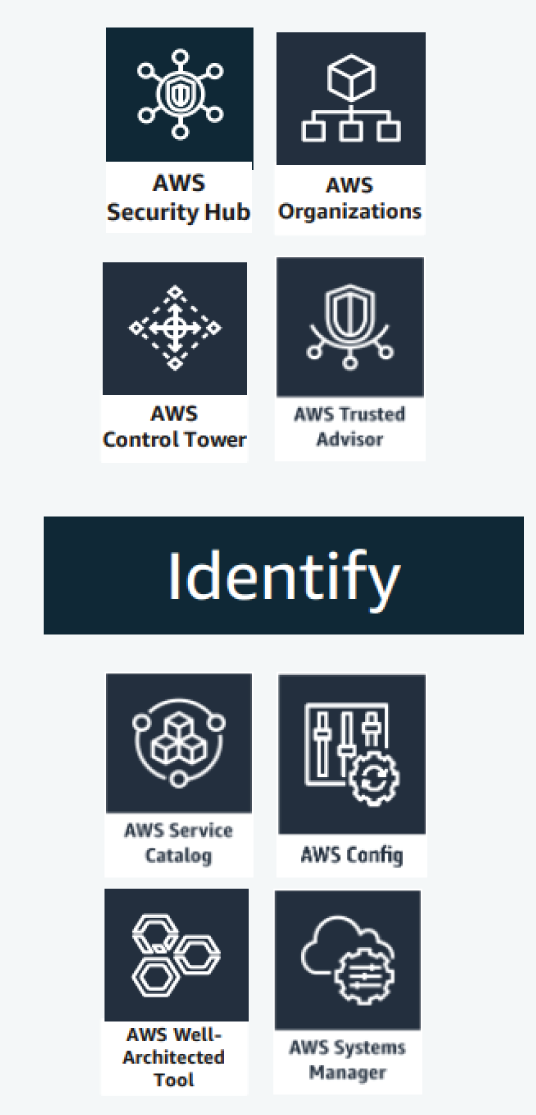
Figure 7.3: Identify components of AWS Reference Architecture
Security Hub
AWS Security Hub gives a comprehensive view of security alerts and security posture across all AWS accounts. There is a range of powerful security tools at your disposal, from firewalls and endpoint protection to vulnerability and compliance scanners. But often this leaves hunting teams switching back-and-forth between these tools to deal with hundreds, and sometimes thousands, of security alerts every day. With Security Hub, you now have a single place that aggregates, organizes, and prioritizes your security alerts, or findings, from multiple AWS services, such as Amazon GuardDuty, Amazon Inspector, Amazon Macie, AWS Identity and Access Management (IAM) Access Analyzer, AWS Systems Manager, and AWS Firewall Manager, as well as from AWS Partner Network (APN) solutions. AWS Security Hub continuously monitors your environment using automated security checks based on the AWS best practices and industry standards that your organization follows. You can also take action on these security findings by investigating them in Amazon Detective or by using Amazon CloudWatch Event rules to send the findings to ticketing, chat, Security Information and Event Management (SIEM), Security Orchestration Automation and Response (SOAR), and incident management tools or to custom remediation playbooks. Figure 7.4 articulates its components and architecture.
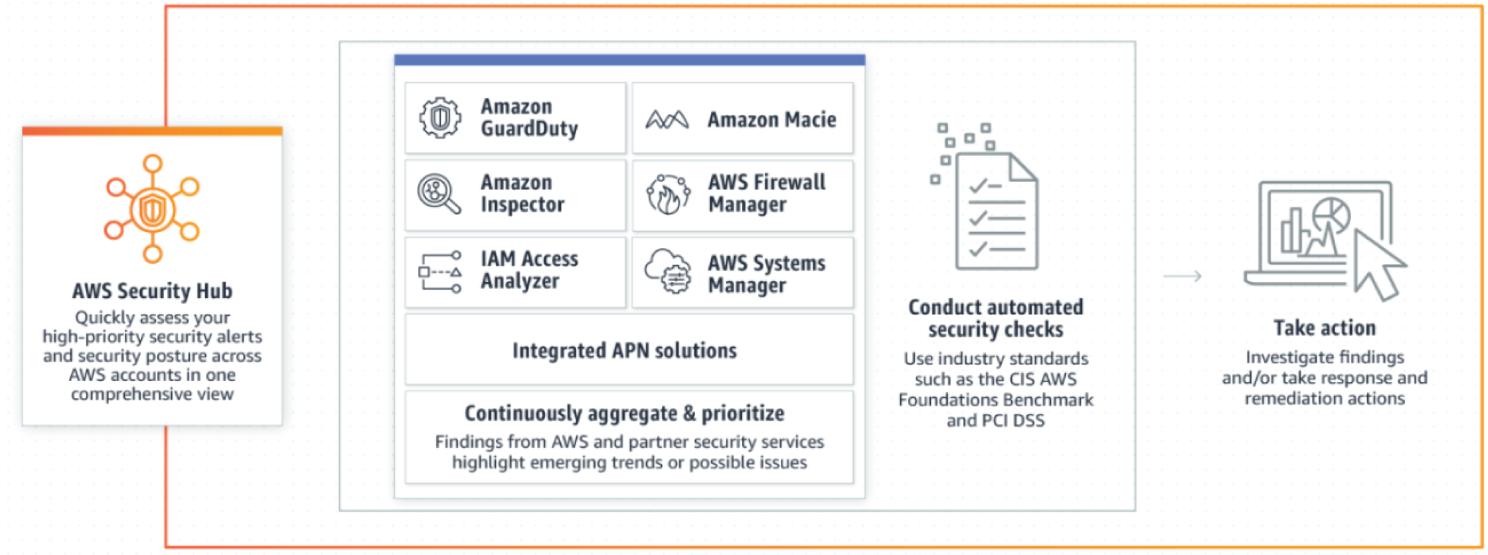
Figure 7.4: Security Hub architecture
AWS Config
AWS Config is a service that enables organizations to assess, audit, and evaluate the configurations of their AWS resources (see Figure 7.5). Config continuously monitors and records their AWS resource configurations and allows them to automate the evaluation of recorded configurations against desired configurations. With Config, your company can review changes in configurations and relationships between AWS resources, dive into detailed resource configuration histories, and determine your overall compliance against the configurations specified in your internal guidelines. This enables you to simplify compliance auditing, security analysis, change management, and operational troubleshooting. The key benefits are as follows:
- Continuous monitoring: With AWS Config, you are able to continuously monitor and record configuration changes of your AWS resources. Config also enables you to inventory your AWS resources, the configurations of your AWS resources, as well as software configurations within EC2 instances at any point in time. Once change from a previous state is detected, an Amazon Simple Notification Service (SNS) notification can be delivered for you to review and take action.
- Change management: With AWS Config, you can track the relationships among resources and review resource dependencies prior to making changes. Once a change occurs, you are able to quickly review the history of the resource's configuration and determine what the resource's configuration looked like at any point in the past. Config provides you with information to assess how a change to a resource configuration would affect your other resources, which minimizes the impact of change-related incidents.
- Enterprise-wide compliance monitoring: With multi-account, multi-region data aggregation in AWS Config, you can view compliance status across your enterprise and identify non-compliant accounts. You can dive deeper to view status for a specific region or a specific account across regions. You can view this data from the Config console in a central account, removing the need to retrieve this information individually from each account and each region.
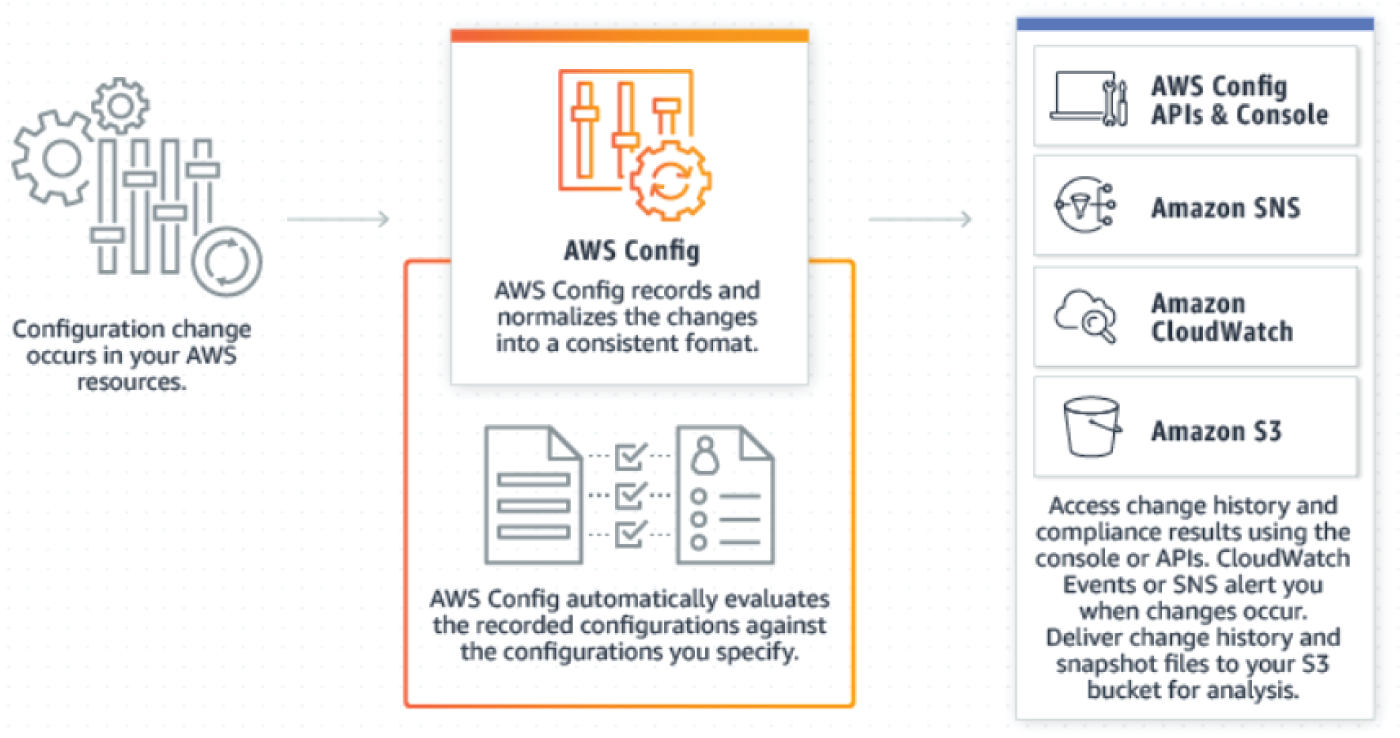
Figure 7.5: AWS Config components
AWS Organizations
AWS Organizations helps centrally manage and govern environment as you grow and scale your AWS resources (see Figure 7.6). Using AWS Organizations, you can programmatically create new AWS accounts and allocate resources, group accounts to organize your workflows, apply policies to accounts or groups for governance, and simplify billing by using a single payment method for all of your accounts.
In addition, AWS Organizations is integrated with other AWS services so you can define central configurations, security mechanisms, audit requirements, and resource sharing across accounts in your organization. AWS Organizations is available to all AWS customers at no additional charge. The key benefits are:
- Centrally secure and audit your environment across accounts: Manage auditing at scale using AWS CloudTrail to create an immutable log of all events from accounts. You can enforce and monitor backup requirements with AWS Backup, or centrally define your recommended configuration criteria across resources, AWS Regions, and accounts with AWS Config. You can also use AWS Control Tower to establish cross-account security audits, or manage and view policies applied across accounts. In addition, you can protect your resources by centrally managing security services, such as detecting threats with Amazon GuardDuty, or reviewing unintended access with AWS IAM Access Analyzer.
- Efficiently provision resources across accounts: You can reduce resource duplication by sharing critical resources within your organization using AWS Resource Access Manager (RAM). Organizations also helps you meet your software license agreements with AWS License Manager, and maintain a catalog of IT services and custom products with AWS Service Catalog.
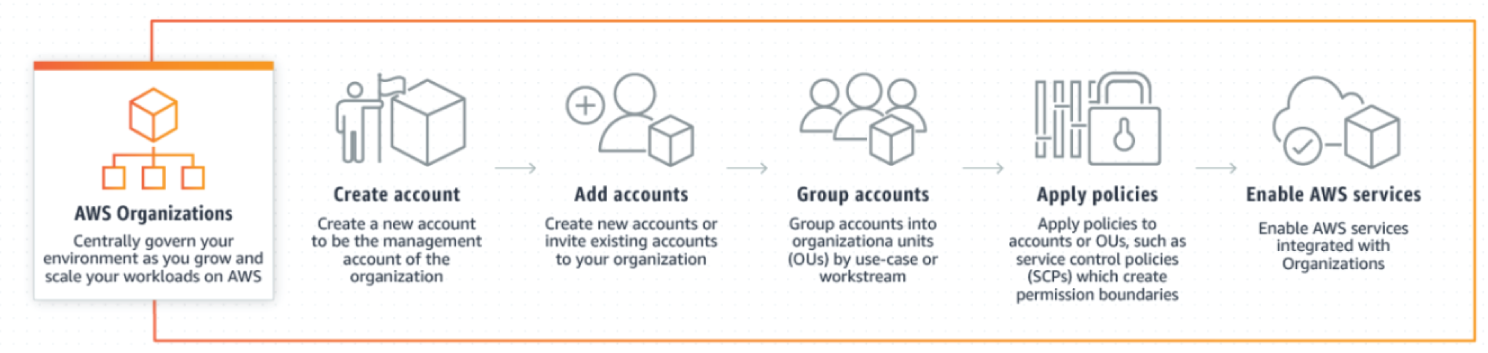
Figure 7.6: AWS Organizations components
AWS Control Tower
If you have multiple AWS accounts and teams, cloud setup and governance can be complex and time-consuming. AWS Control Tower provides the easiest way to set up and govern a secure, multi-account AWS environment, called a landing zone (see Figure 7.7). AWS Control Tower creates a landing zone using AWS Organizations, bringing ongoing account management and governance as well as implementation best practices based on AWS's experience. With AWS Control Tower, builders can provision new AWS accounts in a few clicks, while you have peace of mind knowing that your accounts conform to company-wide policies. AWS customers can implement AWS Control Tower, extend governance into new or existing accounts, and gain visibility into their compliance status quickly. If you are building a new AWS environment, starting out on your journey to AWS, or starting a new cloud initiative, Control Tower will help you get started quickly with built-in governance and best practices. The key features are as follows:
- Automate ongoing policy management: Control Tower provides mandatory and strongly recommended high-level rules, called guardrails, that help enforce your policies using service control policies (SCPs), or detect policy violations using AWS Config rules. These rules remain in effect as you create new accounts or make changes to your existing accounts, and Control Tower provides a summary report of how each account conforms to your enabled policies.
- View policy-level summaries of your AWS environment: Control Tower provides you with an integrated dashboard so you can see a top-level summary of policies applied to your AWS environment. You can view details on the accounts provisioned, the guardrails enabled across your accounts, and account-level status for compliance with your guardrails.
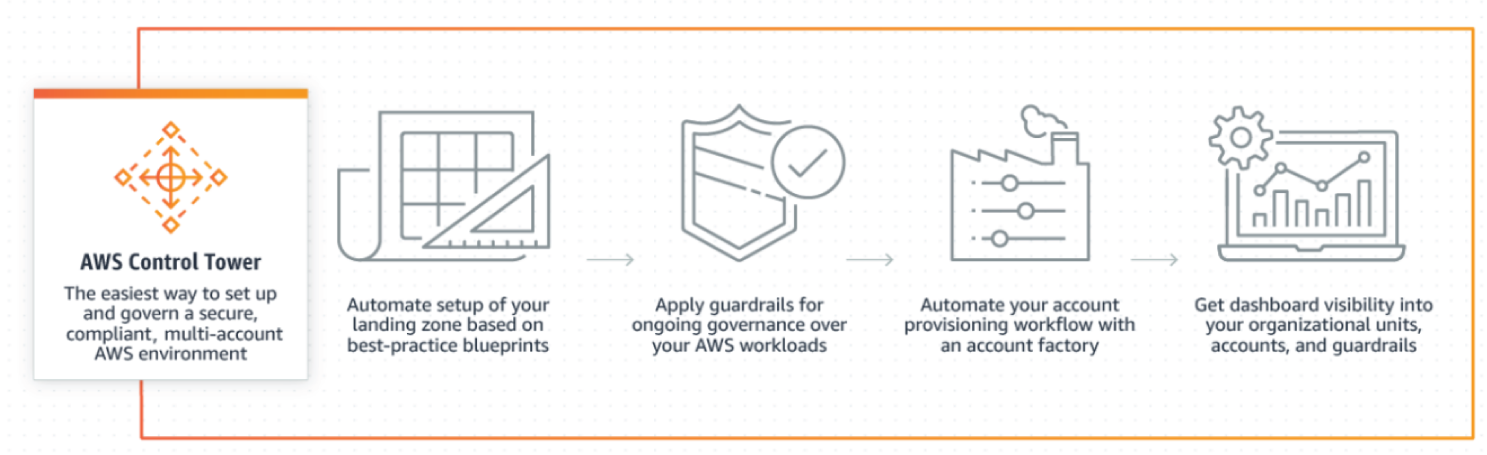
Figure 7.7: AWS Control Tower components
AWS Trusted Advisor
AWS Trusted Advisor is an online tool that provides real-time guidance to help provision your resources following AWS best practices (see Figure 7.8). Trusted Advisor checks help optimize AWS infrastructure, improve security and performance, reduce your overall costs, and monitor service limits. Whether establishing new workflows, developing applications, or as part of ongoing improvement, take advantage of the recommendations provided by Trusted Advisor on a regular basis to help keep your solutions provisioned optimally.
AWS Basic Support and AWS Developer Support customers get access to six security checks (S3 Bucket Permissions, Security Groups - Specific Ports Unrestricted, IAM Use, MFA on Root Account, EBS Public Snapshots, RDS Public Snapshots) and 50 service limit checks. AWS Business Support and AWS Enterprise Support customers get access to all 115 Trusted Advisor checks (14 cost optimization, 17 security, 24 fault tolerance, 10 performance, and 50 service limits) and recommendations. The key features are as follows:
- Cost optimization: AWS Trusted Advisor can save you money on AWS by eliminating unused and idle resources or by making commitments to reserved capacity.
- Security: AWS Trusted Advisor can improve the security of your application by closing gaps, enabling various AWS security features, and examining your permissions.
- Fault tolerance: AWS Trusted Advisor can increase the availability and redundancy of your AWS application by taking advantage of auto scaling, health checks, multi AZ, and backup capabilities.
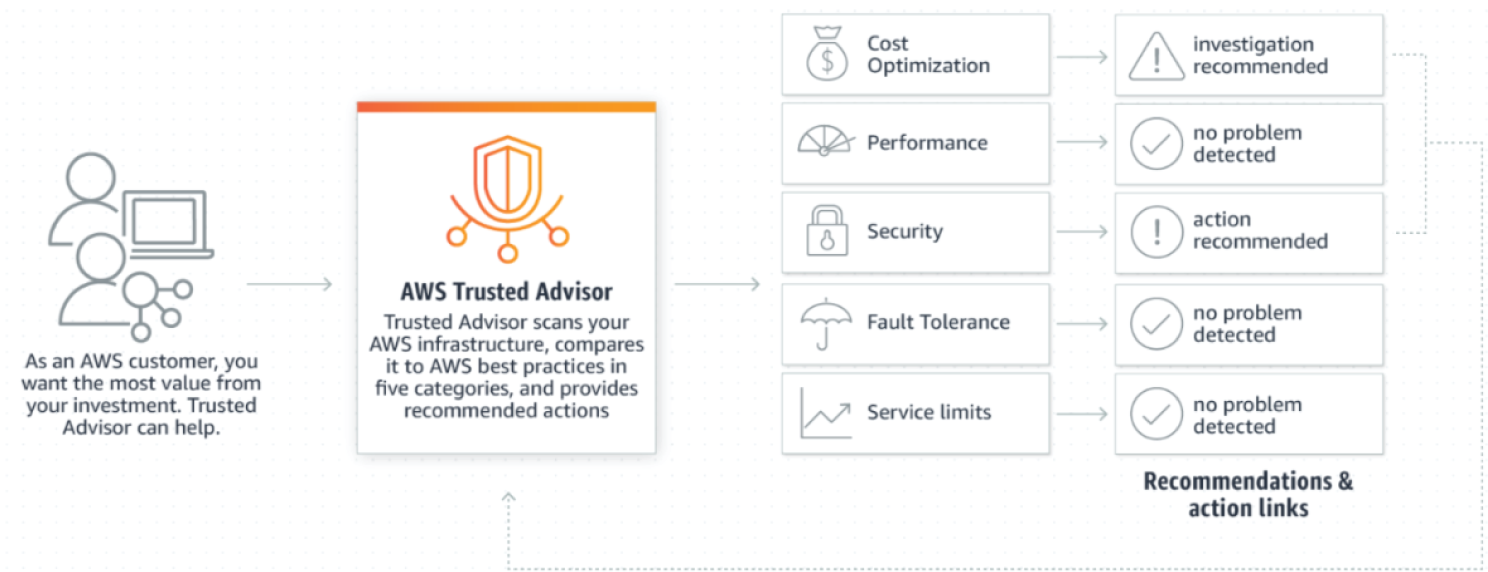
Figure 7.8: AWS Trusted Advisor components
AWS Well-Architected Tool
The AWS Well-Architected Tool helps to review the state of workloads and compares them to the latest AWS architectural best practices (see Figure 7.9). The tool is based on the AWS Well-Architected Framework, developed to help cloud architects build secure, high-performing, resilient, and efficient application infrastructure. This framework provides a consistent approach for customers and partners to evaluate architectures, has been used in tens of thousands of workload reviews conducted by the AWS solutions architecture team, and provides guidance to help implement designs that scale with application needs over time.
To use this free tool, available in the AWS Management Console, just define your workload and answer a set of questions regarding operational excellence, security, reliability, performance efficiency, and cost optimization. The AWS Well-Architected Tool then provides a plan for how to architect for the cloud using established best practices. The key features are as follows:
- Review your workloads consistently: The AWS Well-Architected Tool offers your organization a single tool and consistent process to help you review and measure your cloud architectures. When you are responsible for multiple workloads across your organization, the tool enables you to monitor their overall status and helps you to understand potential risks. Use the results that the tool provides to identify next steps for improvement, drive architectural decisions, and bring architecture considerations into your corporate governance process.
- Identify and implement improvements: Use the AWS Well-Architected Tool to support continuous improvement throughout the workload lifecycle. The tool makes it easy to save point-in-time milestones and track changes to your workload. Whenever you want, initiate a new review process to help ensure your architecture continues to improve over time.
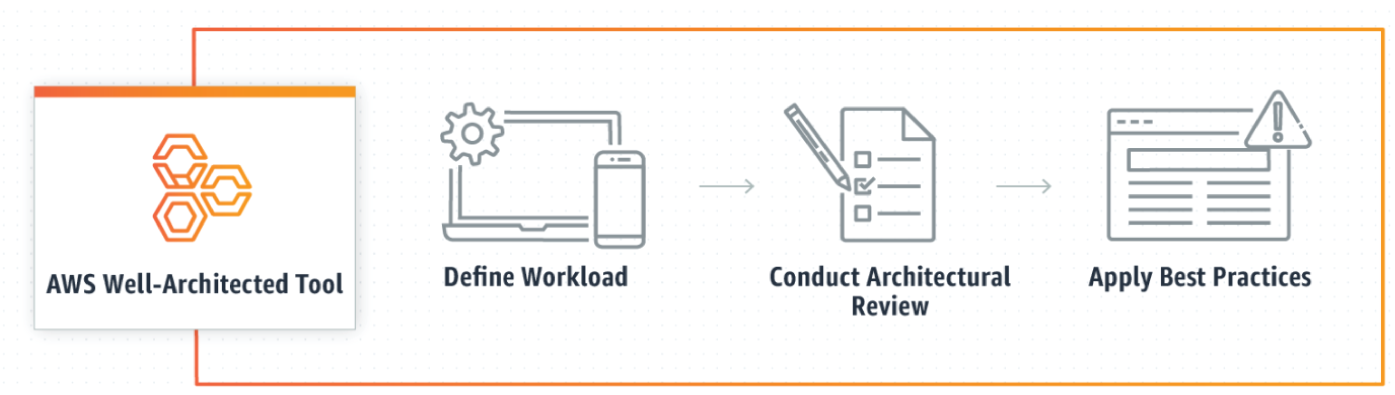
Figure 7.9: AWS Well-Architected Tool components
AWS Service Catalog
AWS Service Catalog allows organizations to create and manage catalogs of IT services that are approved for use on AWS. These IT services can include everything from virtual machine images, servers, software, and databases to complete multi-tier application architectures. AWS Service Catalog allows you to centrally manage deployed IT services and your applications, resources, and metadata. This helps you achieve consistent governance and meet your compliance requirements, while enabling users to quickly deploy only the approved IT services they need. With AWS Service Catalog AppRegistry, organizations can understand the application context of their AWS resources. You can define and manage your applications and their metadata, to keep track of cost, performance, security, compliance, and operational status at the application level. The key features are as follows:
- Manage all of your application information on AWS: AWS Service Catalog AppRegistry provides a single repository for collecting and managing your application resources on AWS. You define your application metadata, which may include information from your internal systems, other AWS services, and software vendors. Builders can include a reference to their application within the infrastructure code, and business stakeholders have up-to-date information on application contents and metadata, such as organizational ownership, data sensitivity, and cost center.
- Ensure compliance with corporate standards: AWS Service Catalog provides a single location where organizations can centrally manage catalogs of IT services. With AWS Service Catalog you can control which IT services and versions are available, what is configured in each of the available services, and who gets permission access by individual, group, department, or cost center.
- Connect with ITSM/ITOM software: The AWS Service Management Connector helps IT Service Management (ITSM) administrators improve governance over provisioned AWS and third-party products. ITSM tools, such as ServiceNow and Jira Service Desk, connect with the AWS Management and Governance services AWS Service Catalog, AWS Config, and AWS Systems Manager. ITSM users can connect to AWS Service Catalog to request, provision, and manage AWS and third-party services and resources.
AWS Systems Manager
AWS Systems Manager gives visibility and control of your infrastructure on AWS. Systems Manager provides a unified user interface so you can view operational data from multiple AWS services and allows you to automate operational tasks across your AWS resources. With Systems Manager, you can group resources, like Amazon EC2 instances, Amazon EKS clusters, Amazon S3 buckets, or Amazon RDS instances, by application, view operational data for monitoring and troubleshooting, implement pre-approved change work flows, and audit operational changes for your groups of resources. Systems Manager simplifies resource and application management, shortens the time to detect and resolve operational problems, and makes it easy to operate and manage your infrastructure securely at scale (see Figure 7.10). The key features are as follows:
- Shorten the time to detect problems: AWS Systems Manager helps you quickly view operational data for groups of resources, so you can quickly identify any issues that might impact applications that use those resources. You can group your resources by applications, application layers, production versus development environments, or anything else you choose. Systems Manager presents the operational data for your resource groups in a single, easy-to-read dashboard so you don't have to navigate to other AWS consoles. For example, if you have an application that uses Amazon EC2, Amazon EKS, Amazon S3, and Amazon RDS, you can use Systems Manager to create a resource group for the application and easily see the software installed on your Amazon EC2 instances, any changes in your Amazon S3 objects, or database instances that have stopped.
- Improve visibility and control: Using AWS Systems Manager, you can discover applications, view operations data (e.g., deployment status, Amazon CloudWatch alarms, resource configurations, and operational issues), and perform remedial actions in the context of an application. You can request operational changes using predefined approval workflows and audit each change after it has been completed. You can then view detailed system configurations, operating system patch levels, software installations, application configurations, and other details about your environment through the Systems Manager Explorer and Inventory dashboards. Systems Manager is integrated with AWS Config so you can easily view changes across your resources as they occur over time.
- Manage hybrid environments: With AWS Systems Manager, you can manage servers running on AWS and in your on-premises datacenter through a single interface. Systems Manager securely communicates with a lightweight agent installed on your servers to run management tasks. This helps you manage resources for Windows, Linux, and Mac operating systems running on Amazon EC2 or on-premises. Systems Manager offers you a consistent administrator experience across your fleet of servers, making it easier to configure and audit logs, manipulate registry keys, navigate file systems, update user access permissions, and monitor critical metrics.
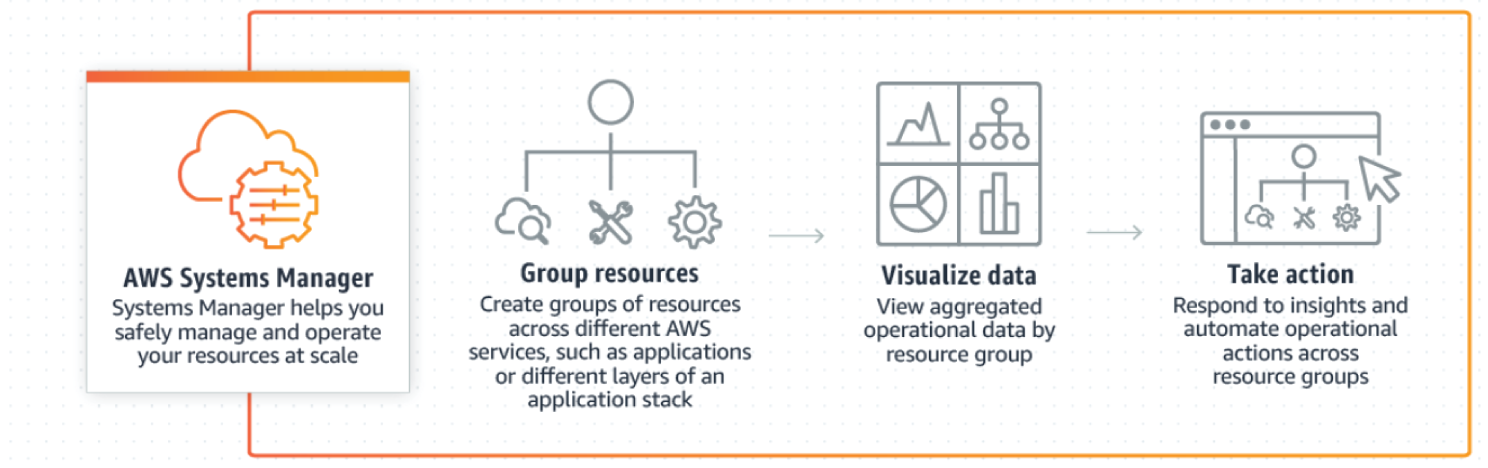
Figure 7.10: AWS Systems Manager components
Let's now discuss the Protect capability of the AWS Reference Architecture (see Figure 7.11). AWS presents a number of key services to augment an organization's Protect capability posture. We dive into all these key services in the subsequent sections.
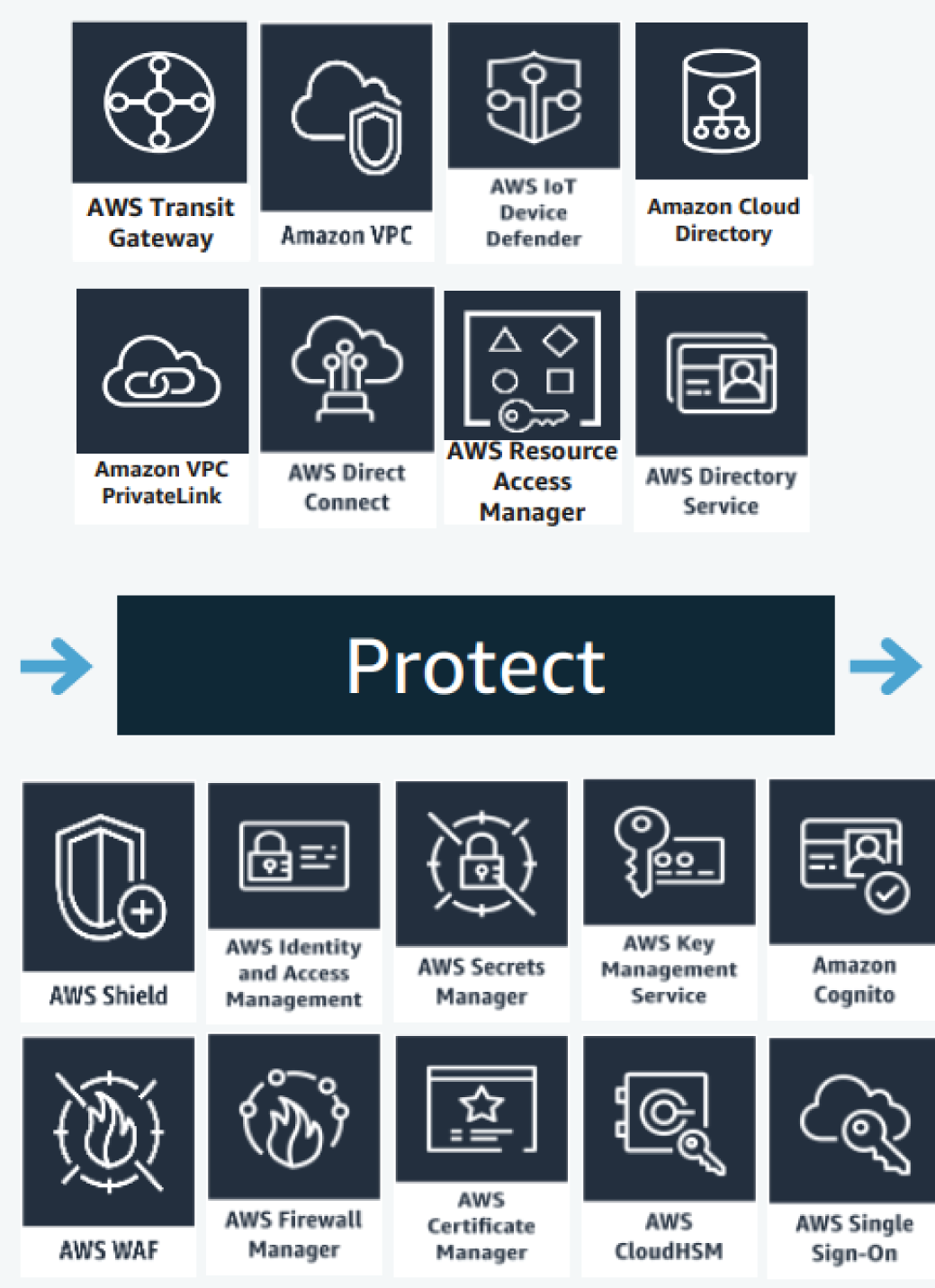
Figure 7.11: Protect components of AWS Reference Architecture
AWS Identity and Access Management (IAM)
AWS Identity and Access Management (IAM) enables organizations to manage access to AWS services and resources securely. Using IAM, you can create and manage AWS users and groups, and use permissions to allow and deny their access to AWS resources. IAM is a feature of your AWS account offered at no additional charge. You will be charged only for use of other AWS services by your users. The key features are as follows:
- Fine-grained access control to AWS resources: IAM enables your users to control access to AWS service APIs and to specific resources. IAM also enables you to add specific conditions such as time of day to control how a user can use AWS, their originating IP address, whether they are using SSL, or whether they have authenticated with a multi-factor authentication device.
- Multi-factor authentication for highly privileged users: Protect your AWS environment by using AWS MFA, a security feature available at no extra cost that augments user name and password credentials. MFA requires users to prove physical possession of a hardware MFA token or MFA-enabled mobile device by providing a valid MFA code.
- Analyze access: IAM helps you analyze access across your AWS environment. Your security teams and administrators can quickly validate that your policies only provide the intended public and cross-account access to your resources. You can also easily identify and refine your policies to allow access to only the services being used. This helps you to better adhere to the principle of least privilege.
AWS IAM allows you to:
- Manage IAM users and their access: Create users in IAM, assign them individual security credentials (in other words, access keys, passwords, and multi-factor authentication devices), or request temporary security credentials to provide users access to AWS services and resources. You can manage permissions in order to control which operations a user can perform.
- Manage IAM roles and their permissions: Create roles in IAM and manage permissions to control which operations can be performed by the entity, or AWS service, that assumes the role. You can also define which entity is allowed to assume the role. In addition, you can use service-linked roles to delegate permissions to AWS services that create and manage AWS resources on your behalf.
- Manage federated users and their permissions: Enable identity federation to allow existing identities (users, groups, and roles) in your enterprise to access the AWS Management Console, call AWS APIs, and access resources, without the need to create an IAM user for each identity. Use any identity management solution that supports SAML 2.0, or use one of our federation samples (AWS Console SSO or API federation).
AWS Single Sign-On (SSO)
AWS Single Sign-On (SSO) makes it easy to centrally manage access to multiple AWS accounts and business applications and provide users with single sign-on access to all their assigned accounts and applications from one place. With AWS SSO, you can easily manage access and user permissions to all of your accounts in AWS Organizations centrally. AWS SSO configures and maintains all the necessary permissions for your accounts automatically, without requiring any additional setup in the individual accounts. You can assign user permissions based on common job functions and customize these permissions to meet your specific security requirements. AWS SSO also includes built-in integrations to many business applications, such as Salesforce, Box, and Microsoft 365. See Figure 7.12.
With AWS SSO, you can create and manage user identities in AWS SSO's identity store, or easily connect to your existing identity source, including Microsoft Active Directory, Okta Universal Directory, and Azure Active Directory (Azure AD). AWS SSO allows you to select user attributes, such as cost center, title, or locale, from your identity source, and then use them for attribute-based access control in AWS. The key features are as follows:
- Access accounts and applications from one place: AWS SSO provides a user portal so users can find and access the roles they can assume in their assigned AWS accounts and business applications in one place. AWS SSO offers pre-configured SAML integrations to many business applications, including Salesforce, Box, and Microsoft 365. AWS monitors these integrations for changes and updates the integration on your behalf automatically. The AWS SSO application configuration wizard helps you extend SSO access to any application that supports Security Assertion Markup Language (SAML) 2.0.
- Create users in AWS SSO or connect to your existing identities: AWS SSO gives you the option to create your user identities and groups in AWS SSO. And, if you already use Microsoft Active Directory Domain Services, Okta Universal Directory, Azure AD, or another supported identity provider, your users can access AWS with their existing corporate credentials, and your administrators can continue to manage users and groups in your existing identity source. With AWS SSO, you can enable standards-based strong authentication capabilities for all your users across all identity sources.
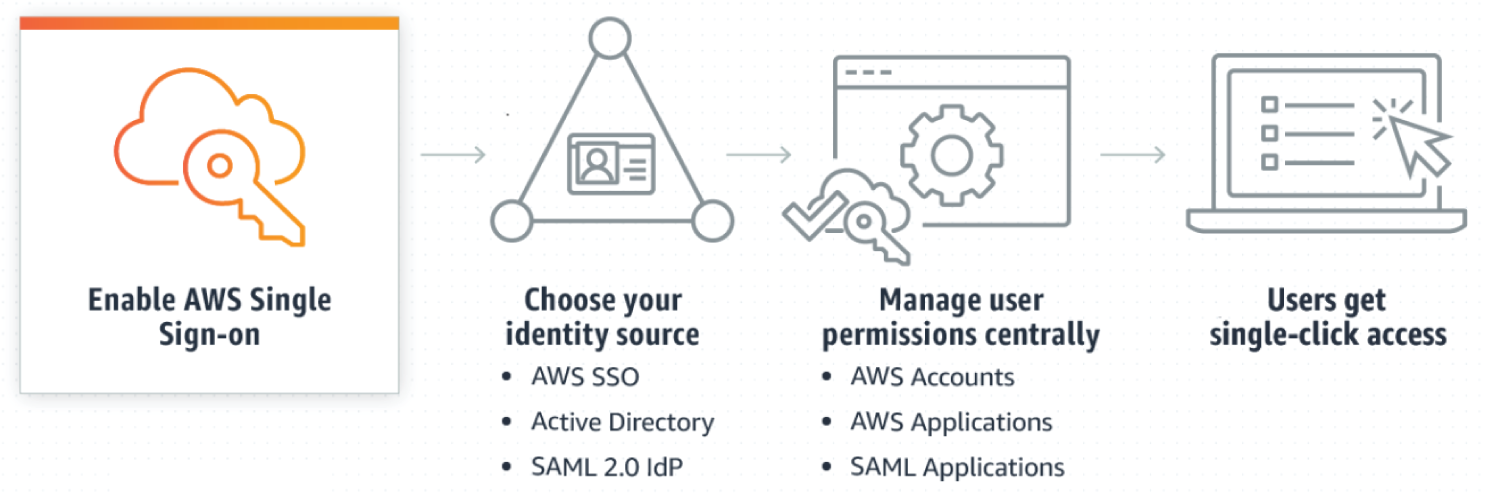
Figure 7.12: AWS Single Sign-On components
AWS Shield
AWS Shield is a managed Distributed Denial of Service (DDoS) protection service that safeguards applications running on AWS. AWS Shield provides always-on detection and automatic inline mitigations that minimize application downtime and latency, so there is no need to engage AWS Support to benefit from DDoS protection. There are two tiers of AWS Shield: Standard and Advanced.
All AWS customers benefit from the automatic protections of AWS Shield Standard, at no additional charge. AWS Shield Standard defends against most common, frequently occurring network and transport layer DDoS attacks that target your website or applications. When you use AWS Shield Standard with Amazon CloudFront and Amazon Route 53, you receive comprehensive availability protection against all known infrastructure (Layers 3 and 4) attacks.
For higher levels of protection against attacks targeting your applications running on Amazon Elastic Compute Cloud (EC2), Elastic Load Balancing (ELB), Amazon CloudFront, AWS Global Accelerator, and Amazon Route 53 resources, you can subscribe to AWS Shield Advanced. In addition to the network and transport layer protections that come with Standard, AWS Shield Advanced provides additional detection and mitigation against large and sophisticated DDoS attacks, near real-time visibility into attacks, and integration with AWS WAF, a web application firewall. AWS Shield Advanced also gives you 24x7 access to the AWS DDoS Response Team (DRT) and protection against DDoS-related spikes in your Amazon Elastic Compute Cloud (EC2), Elastic Load Balancing (ELB), Amazon CloudFront, AWS Global Accelerator, and Amazon Route 53 charges.
AWS Shield Advanced is available globally on all Amazon CloudFront, AWS Global Accelerator, and Amazon Route 53 edge locations. You can protect your web applications hosted anywhere in the world by deploying Amazon CloudFront in front of your application. Your origin servers can be Amazon S3, Amazon Elastic Compute Cloud (EC2), Elastic Load Balancing (ELB), or a custom server outside of AWS.
With AWS Shield Advanced, you have the flexibility to choose the resources to protect for infrastructure (Layers 3 and 4) protection. You can write customized rules with AWS WAF to mitigate sophisticated application layer attacks. These customizable rules can be deployed instantly, allowing you to quickly mitigate attacks. You can set up rules proactively to automatically block bad traffic, or respond to incidents as they occur. You also have 24x7 access to the AWS DDoS Response Team (DRT), who can write rules on your behalf to mitigate application layer DDoS attacks.
AWS Web Application Firewall (WAF)
AWS WAF is a web application firewall that helps protect web applications or APIs against common web exploits and web bots (i.e., web robots) that may affect availability, compromise security, or consume excessive resources. AWS WAF gives you control over how traffic reaches your applications by enabling you to create security rules that control web bot traffic and block common attack patterns, such as SQL injection or cross-site scripting. You can also customize rules that filter out specific traffic patterns. You can get started quickly using Managed Rules for AWS WAF, a pre-configured set of rules managed by AWS or AWS Marketplace Sellers to address issues like the OWASP Top 10 security risks and automated bots that consume excess resources, skew metrics, or can cause downtime. These rules are regularly updated as new issues emerge. AWS WAF includes a full-featured API that you can use to automate the creation, deployment, and maintenance of security rules.
You can deploy AWS WAF on Amazon CloudFront as part of your CDN solution, the Application Load Balancer that fronts your web servers or origin servers running on EC2, Amazon API Gateway for your REST APIs, or AWS AppSync for your GraphQL APIs. With AWS WAF, you pay only for what you use and the pricing is based on how many rules you deploy and how many web requests your application receives.
With Managed Rules for AWS WAF, you can quickly get started and protect your web application or APIs against common threats. You can select from many rule types, such as ones that address issues like the Open Web Application Security Project (OWASP) Top 10 security risks, threats specific to Content Management Systems (CMS), or emerging Common Vulnerabilities and Exposures (CVE). Managed rules are automatically updated as new issues emerge, so that you can spend more time building applications.
With AWS WAF Bot Control, you get visibility and control over common and pervasive bot traffic to your applications. Within the AWS WAF console, you can monitor common bots, such as status monitors and search engines, and get detailed, real-time visibility into the category, identity, and other details of web bot traffic. You can also block, or rate-limit, traffic from pervasive bots, such as scrapers, scanners, and crawlers. Using AWS Firewall Manager, you can deploy the Bot Control managed rule group across multiple accounts in your AWS Organization. See Figure 7.13.
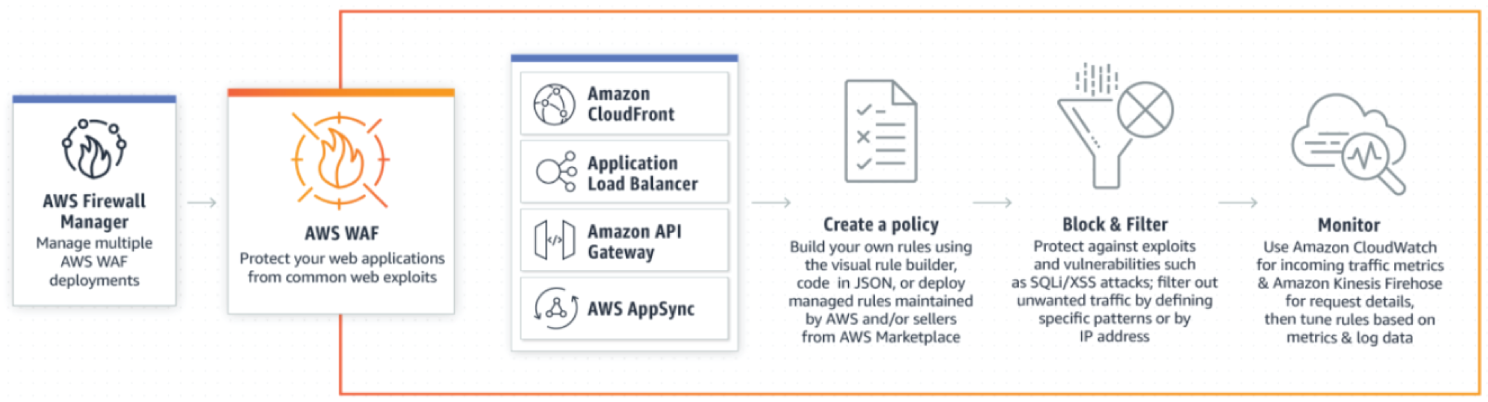
Figure 7.13: AWS Web Application Firewall components
AWS Firewall Manager
AWS Firewall Manager is a security management service that allows organizations to centrally configure and manage firewall rules across all accounts and applications in AWS Organizations. As new applications are created, Firewall Manager makes it easy to bring new applications and resources into compliance by enforcing a common set of security rules. Now you have a single service to build firewall rules, create security policies, and enforce them in a consistent, hierarchical manner across your entire infrastructure, from a central administrator account.
Using AWS Firewall Manager, you can easily roll out AWS WAF rules for your Application Load Balancers, API Gateways, and Amazon CloudFront distributions. You can create AWS Shield Advanced protections for your Application Load Balancers, ELB Classic Load Balancers, Elastic IP Addresses, and CloudFront distributions. You can also configure new Amazon Virtual Private Cloud (VPC) security groups and audit any existing VPC security groups for your Amazon EC2, Application Load Balancer (ALB), and ENI resource types. You can deploy AWS Network Firewalls across accounts and VPCs in your organization. Finally, with AWS Firewall Manager, you can also associate your VPCs with Amazon Route 53 Resolvers DNS Firewall rules. The key features are as follows:
- Simplify management of firewall rules across your accounts: AWS Firewall Manager is integrated with AWS Organizations so you can enable AWS WAF rules, AWS Shield Advanced protections, security groups, AWS Network Firewall rules, and Amazon Route 53 Resolver DNS Firewall rules for your Amazon VPC across multiple AWS accounts and resources from a single place. You can group rules, build policies, and centrally apply those policies across your entire infrastructure. For example, you can delegate the creation of application-specific rules within an account while retaining the ability to enforce global security policies across accounts.
- Centrally deploy protections for your VPCs: With Firewall Manager, your security administrator can deploy a baseline set of VPC security group rules for EC2 instances, Application Load Balancers (ALBs), and Elastic Network Interfaces (ENIs) in your Amazon VPCs. At the same time, you can also audit any existing security groups in your VPCs for over-permissive rules and remediate them from a single place. You can leverage Firewall Manager to deploy rules for AWS Network Firewalls across your VPCs in your organization, to control traffic leaving and entering your network. At the same time, with Firewall Manager, you can also associate your VPCs with Route 53 Resolver DNS Firewall rules to block DNS queries made for known malicious domains and to allow queries for trusted domains.
- Ensure compliance of existing and new applications: AWS Firewall Manager automatically enforces mandatory security policies that you define across existing and newly created resources. The service discovers new resources as they are created across accounts. For example, if you are required to meet U.S. Department of Treasury's Office of Foreign Assets Control (OFAC) regulations, you can use Firewall Manager to deploy an AWS WAF rule to block traffic from embargoed countries across your Application Load Balancer, API Gateway, and Amazon CloudFront accounts. As new resources are created, they will automatically be brought under the policy scope.
AWS Cloud HSM
AWS CloudHSM is a cloud-based hardware security module (HSM) that enables you to easily generate and use your own encryption keys on the AWS Cloud. With CloudHSM, you can manage your own encryption keys using FIPS 140-2 Level 3 validated HSMs. CloudHSM offers you the flexibility to integrate with your applications using industry-standard APIs, such as PKCS#11, Java Cryptography Extensions (JCE), and Microsoft CryptoNG (CNG) libraries. See Figure 7.14.
CloudHSM is standards-compliant and enables you to export all of your keys to most other commercially available HSMs, subject to your configurations. It is a fully managed service that automates time-consuming administrative tasks for you, such as hardware provisioning, software patching, high-availability, and backups. CloudHSM also enables you to scale quickly by adding and removing HSM capacity on-demand, with no up-front costs.
AWS CloudHSM enables you to generate and use your encryption keys on a FIPS 140-2 Level 3 validated hardware. CloudHSM protects your keys with exclusive, single-tenant access to tamper-resistant HSM instances in your own Amazon Virtual Private Cloud (VPC).
You can configure AWS Key Management Service (KMS) to use your AWS CloudHSM cluster as a custom key store rather than the default KMS key store. With a KMS custom key store you benefit from the integration between KMS and AWS services that encrypt data while retaining control of the HSMs that protect your KMS master keys. KMS custom key store gives you the best of both worlds, combining single-tenant HSMs under your control with the ease of use and integration of AWS KMS.

Figure 7.14: AWS Cloud HSM components
AWS CloudHSM runs in your own Amazon Virtual Private Cloud (VPC), enabling you to easily use your HSMs with applications running on your Amazon EC2 instances. With CloudHSM, you can use standard VPC security controls to manage access to your HSMs. Your applications connect to your HSMs using mutually authenticated SSL channels established by your HSM client software. Since your HSMs are located in Amazon datacenters near your EC2 instances, you can reduce the network latency between your applications and HSMs versus an on-premises HSM. The following components are illustrated in Figure 7.14.
- A: AWS manages the hardware security module (HSM) appliance, but does not have access to your keys
- B: You control and manage your own keys
- C: Application performance improves (due to close proximity with AWS workloads)
- D: Secure key storage in tamper-resistant hardware available in multiple Availability Zones (AZs)
- E: Your HSMs are in your Virtual Private Cloud (VPC) and isolated from other AWS networks
Separation of duties and role-based access control is inherent in the design of the AWS CloudHSM. AWS monitors the health and network availability of your HSMs but is not involved in the creation and management of the key material stored within your HSMs. You control the HSMs and the generation and use of your encryption keys.
AWS Secrets Manager
AWS Secrets Manager helps to protect secrets needed to access your applications, services, and IT resources. The service enables you to easily rotate, manage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle. Users and applications retrieve secrets with a call to Secrets Manager APIs, eliminating the need to hardcode sensitive information in plain text. Secrets Manager offers secret rotation with built-in integration for Amazon RDS, Amazon Redshift, and Amazon DocumentDB. Also, the service is extensible to other types of secrets, including API keys and OAuth tokens. In addition, Secrets Manager enables you to control access to secrets using fine-grained permissions and audit secret rotation centrally for resources in the AWS Cloud, third-party services, and on-premises.
AWS Secrets Manager helps you meet your security and compliance requirements by enabling you to rotate secrets safely without the need for code deployments. For example, Secrets Manager offers built-in integration for Amazon RDS, Amazon Redshift, and Amazon DocumentDB and rotates these database credentials on your behalf automatically. You can customize Lambda functions to extend Secrets Manager rotation to other secret types, such as API keys and OAuth tokens. Retrieving the secret from Secrets Manager ensures that developers and applications are using the latest version of your secrets.
AWS Secrets Manager enables you to easily replicate secrets in multiple AWS regions to support your multi-region applications and disaster recovery scenarios. The multi-Region secrets feature abstracts the complexity of replicating and managing secrets across multiple regions, enabling you to simply access and read secrets where you need them.
AWS Key Management Service (KMS)
AWS Key Management Service (KMS) makes it easy to create and manage cryptographic keys and control their use across a wide range of AWS services and applications. AWS KMS is a secure and resilient service that uses hardware security modules that have been validated under FIPS 140-2, or are in the process of being validated, to protect your keys. AWS KMS is integrated with AWS CloudTrail to provide you with logs of all key usage to help meet your regulatory and compliance needs. The key features are as follows:
- Encrypt data in your applications: AWS KMS is integrated with the AWS Encryption SDK to enable you to use KMS-protected data encryption keys to encrypt locally within your applications. Using simple APIs, you can also build encryption and key management into your own applications wherever they run.
- Digitally sign data: AWS KMS enables you to perform digital signing operations using asymmetric key pairs to ensure the integrity of your data. Recipients of digitally signed data can verify the signatures whether they have an AWS account or not.
- Centralized key management: AWS KMS presents a single control point to manage keys and define policies consistently across integrated AWS services and your own applications. You can easily create, import, rotate, delete, and manage permissions on keys from the AWS Management Console or by using the AWS SDK or CLI.
- Manage encryption for AWS services: AWS KMS is integrated with AWS services to simplify using your keys to encrypt data across your AWS workloads. You choose the level of access control that you need, including the ability to share encrypted resources between accounts and services. KMS logs all use keys to AWS CloudTrail to give you an independent view of who accessed your encrypted data, including AWS services using them on your behalf.
AWS Certificate Manager
AWS Certificate Manager is a service that lets organizations easily provision, manage, and deploy public and private Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates for use with AWS services and your internal connected resources. SSL/TLS certificates are used to secure network communications and establish the identity of websites over the Internet as well as resources on private networks. AWS Certificate Manager removes the time-consuming manual process of purchasing, uploading, and renewing SSL/TLS certificates.
With AWS Certificate Manager, you can quickly request a certificate, deploy it on ACM-integrated AWS resources, such as Elastic Load Balancers, Amazon CloudFront distributions, and APIs on API Gateway, and let AWS Certificate Manager handle certificate renewals. It also enables you to create private certificates for your internal resources and manage the certificate lifecycle centrally. Public and private certificates provisioned through AWS Certificate Manager for use with ACM-integrated services are free. You pay only for the AWS resources you create to run your application. With AWS Certificate Manager Private Certificate Authority, you pay monthly for the operation of the private CA and for the private certificates you issue.
AWS Certificate Manager manages the renewal process for the certificates managed in ACM and used with ACM-integrated services, such as Elastic Load Balancing and API Gateway. ACM can automate renewal and deployment of these certificates. With ACM Private CA APIs, ACM enables you to automate creation and renewal of private certificates for on-premises resources, EC2 instances, and IoT devices.
AWS IoT Device Defender
AWS IoT Device Defender is a fully managed service that helps you secure your fleet of IoT devices. AWS IoT Device Defender continuously audits your IoT configurations to make sure that they aren't deviating from security best practices. A configuration is a set of technical controls you set to help keep information secure when devices are communicating with each other and the cloud. AWS IoT Device Defender makes it easy to maintain and enforce IoT configurations, such as ensuring device identity, authenticating and authorizing devices, and encrypting device data. AWS IoT Device Defender continuously audits the IoT configurations on your devices against a set of predefined security best practices. AWS IoT Device Defender sends an alert if there are any gaps in your IoT configuration that might create a security risk, such as identity certificates being shared across multiple devices or a device with a revoked identity certificate trying to connect to AWS IoT Core.
AWS IoT Device Defender also lets you continuously monitor security metrics from devices and AWS IoT Core for deviations from the expected behaviors for each device. You can define the appropriate behavior for your devices or use machine learning to model the regular device behavior based on historical data. If something doesn't look right according to defined behaviors or ML models, AWS IoT Device Defender pushes an alarm so you can take action to mitigate the issue. For example, traffic spikes in outbound traffic might indicate that a device is participating in a DDoS attack. AWS IoT Greengrass automatically integrates with AWS IoT Device Defender to provide security metrics from the devices for evaluation.
AWS IoT Device Defender can send alarms to the AWS IoT Console, Amazon CloudWatch, and Amazon SNS. If you determine that you need to take an action based on an alarm, you can use AWS IoT Device Defender built-in mitigation actions such as adding them to a group (for example, quarantine) or AWS IoT Device Management to take additional mitigation steps such as pushing security fixes.
Amazon Virtual Private Cloud
Amazon Virtual Private Cloud (Amazon VPC) is a service enabling the launch of AWS resources in a logically isolated virtual network that you define. You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways. You can use both IPv4 and IPv6 for most resources in your virtual private cloud, helping to ensure secure and easy access to resources and applications.
As one of AWS's foundational services, Amazon VPC makes it easy to customize your VPC's network configuration. You can create a public-facing subnet for your web servers that have access to the Internet. It also lets you place your backend systems, such as databases or application servers, in a private-facing subnet with no Internet access. Amazon VPC lets you use multiple layers of security, including security groups and network access control lists, to help control access to Amazon EC2 instances in each subnet. The key features are as follows:
- Secure and monitored network connections: Amazon VPC provides advanced security features that allow you to perform inbound and outbound filtering at the instance and subnet level. Additionally, you can store data in Amazon S3 and restrict access so that it's only accessible from instances inside your VPC. Amazon VPC also has monitoring features that let you perform functions like out-of-band monitoring and inline traffic inspection, which help you screen and secure traffic.
- Customizable virtual network: Amazon VPC helps you control your virtual networking environment by letting you choose your own IP Address range, create your own subnets, and configure route tables to any available gateways. You can customize the network configuration by creating a public-facing subnet for your web servers that has access to the Internet. Place your backend systems, such as databases or application servers, in a private-facing subnet. With Amazon VPC, you can ensure that your virtual private cloud is configured to fit your specific business needs.
- Host multi-tier web applications: Host multi-tier web applications and strictly enforce access and security restrictions between your web servers, application servers, and databases. Launch web servers in a publicly accessible subnet while running your application servers and databases in private subnets. This will ensure that application servers and databases cannot be directly accessed from the Internet. You control access between the servers and subnets using inbound and outbound packet filtering provided by network access control lists and security groups. To create a VPC that supports this use case, you can select “VPC with Public and Private Subnets” in the Amazon VPC console wizard.
- Back up and recover your data after a disaster: By using Amazon VPC for disaster recovery, you receive all the benefits of a disaster recovery site at a fraction of the cost. You can periodically back up critical data from your datacenter to a small number of Amazon EC2 instances with Amazon Elastic Block Store (EBS) volumes, or import your virtual machine images to Amazon EC2. To ensure business continuity, Amazon VPC allows you to quickly launch replacement compute capacity in AWS. When the disaster is over, you can send your mission-critical data back to your datacenter and terminate the Amazon EC2 instances that you no longer need.
AWS PrivateLink
AWS PrivateLink provides private connectivity between VPCs, AWS services, and your on-premises networks, without exposing your traffic to the public Internet. AWS PrivateLink makes it easy to connect services across different accounts and VPCs to significantly simplify your network architecture.
Interface VPC endpoints, powered by AWS PrivateLink, connect you to services hosted by AWS Partners and supported solutions available in AWS Marketplace. By powering Gateway Load Balancer endpoints, AWS PrivateLink brings the same level of security and performance to your virtual network appliances or custom traffic inspection logic. The key features are as follows:
- Simplify network management: You can connect services across different accounts and Amazon VPCs, with no need for firewall rules, path definitions, or route tables. There is no need to configure an Internet gateway, VPC peering connection, or manage VPC Classless Inter-Domain Routing (CIDRs). Because AWS PrivateLink simplifies your network architecture, it is easier for you to manage your global network.
- Accelerate your cloud migration: More easily migrate traditional on-premises applications to SaaS offerings hosted in the cloud with AWS PrivateLink. Since your data does not get exposed to the Internet where it can be compromised, you can migrate and use more cloud services with the confidence that your traffic remains secure. You no longer have to choose between using a service and exposing your critical data to the Internet. You can find the latest controls in place to help customers stay complaint on our AWS Compliance Programs page. See Figure 7.15.
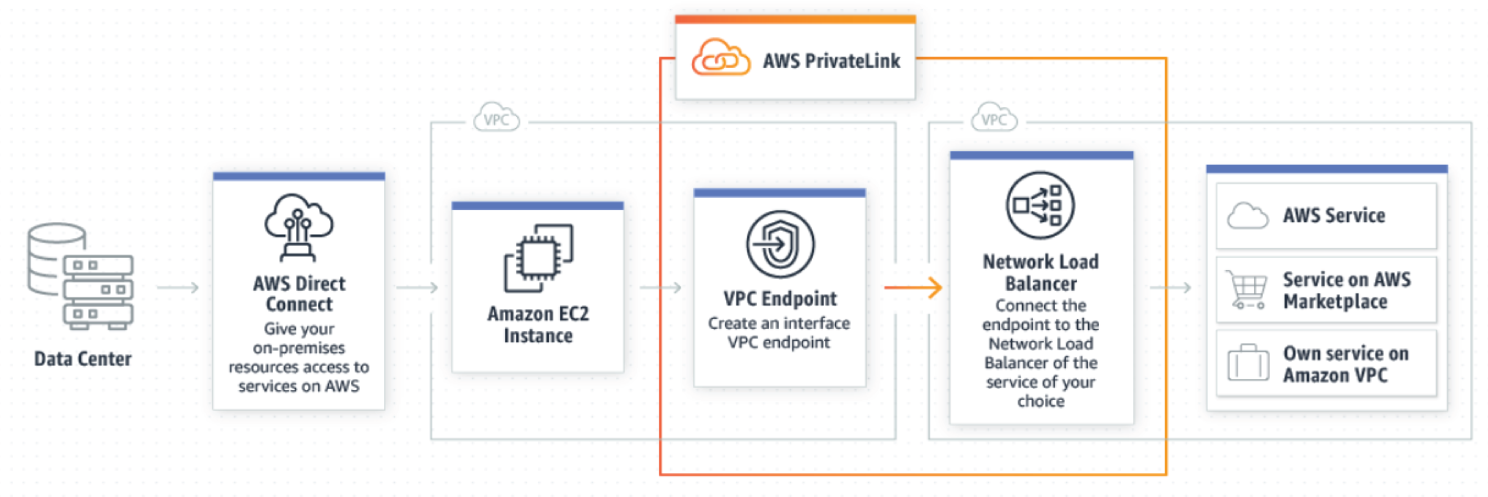
Figure 7.15: AWS PrivateLink components
AWS Direct Connect
AWS Direct Connect is a cloud service solution that makes it easy to establish a dedicated network connection from your premises to AWS. Using AWS Direct Connect, you establish a private connection between AWS and your datacenter, office, or colocation environment. This can increase bandwidth throughput and provide a more consistent network experience than Internet-based connections.
AWS Direct Connect is compatible with all AWS services accessible over the Internet, and is available in speeds starting at 50 Mbps and scaling up to 100 Gbps. The key features are illustrated in Figure 7.16.
- Protect data in transit: Ensure communication between your datacenter, branch office, or colocation facility is protected by taking advantage of Direct Connect encryption options. 10 Gbps and 100 Gbps connections offer native IEEE 802.1AE (MACsec) point-to-point encryption at select locations. AWS Site-to-Site VPN connections using IPsec (IP security) are also available and can be used with any AWS Direct Connect connection.
- Consistent network performance: AWS Direct Connect links to all your AWS resources, transferring data directly from your datacenter, office, or colocation environment into and from AWS. With AWS Direct Connect, you choose the data that utilizes the private connection and how that data is routed, which can provide a more consistent network experience than Internet-based connections.
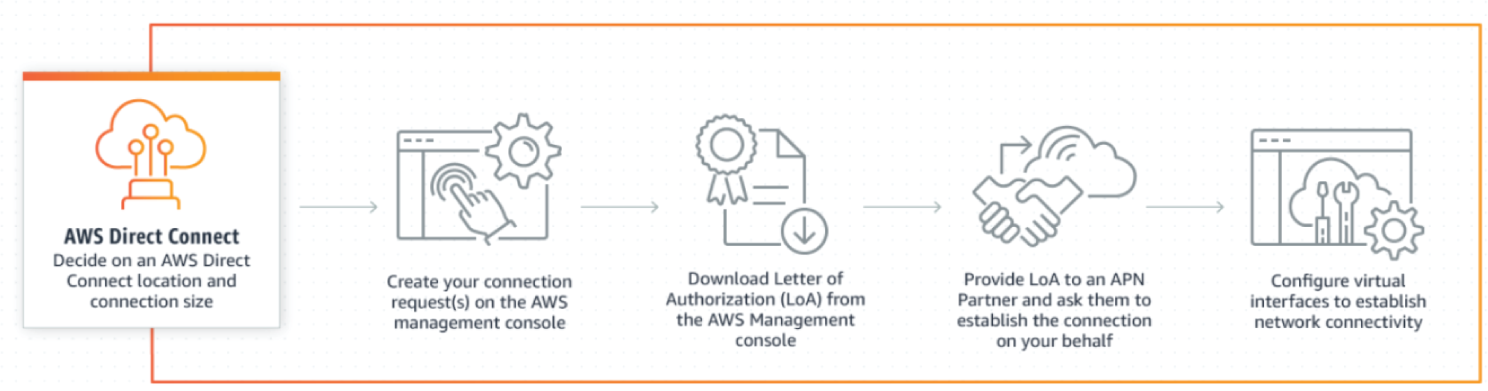
Figure 7.16: AWS Direct Connect components
AWS Transit Gateway
AWS Transit Gateway connects VPCs and on-premises networks through a central hub. This simplifies your network and puts an end to complex peering relationships. It acts as a cloud router, as each new connection is only made once. See Figure 7.17.
As you expand globally, inter-Region peering connects AWS Transit Gateways together using the AWS global network. Your data is automatically encrypted, and never travels over the public Internet. And, because of its central position, AWS Transit Gateway Network Manager has a unique view over your entire network, even connecting to Software-Defined Wide Area Network (SD-WAN) devices. The key features are as follows:
- Better visibility and control: With AWS Transit Gateway Network Manager, you can easily monitor your Amazon VPCs and edge connections from a central console. Integrated with popular SD-WAN devices, AWS Transit Gateway Network Manager helps you quickly identify issues and react to events on your global network.
- Flexible multicast: AWS Transit Gateway multicast support distributes the same content to multiple specific destinations. This eliminates the need for expensive on-premises multicast networks and reduces the bandwidth needed for high-throughput applications such as video conferencing, media, or teleconferencing.
AWS Resource Access Manager
AWS Resource Access Manager (RAM) is a service that enables easy and secure sharing of AWS resources with any AWS account or within the AWS Organization. You can share AWS Transit Gateways, Subnets, AWS License Manager configurations, and Amazon Route 53 Resolver rules resources with RAM. See Figure 7.18.
Many organizations use multiple accounts to create administrative or billing isolation, and to limit the impact of errors. RAM eliminates the need to create duplicate resources in multiple accounts, reducing the operational overhead of managing those resources in every single account you own. You can create resources centrally in a multi-account environment, and use RAM to share those resources across accounts in three simple steps: create a Resource Share, specify resources, and specify accounts. RAM is available to you at no additional charge. The key features are as follows:
- Reduce operational overhead: Procure AWS resources centrally, and use RAM to share resources such as subnets or License Manager configurations with other accounts. This eliminates the need to provision duplicate resources in every account in a multi-account environment, reducing the operational overhead of managing those resources in every account.
- Improve security and visibility: RAM leverages existing policies and permissions set in AWS Identity and Access Management (IAM) to govern the consumption of shared resources. RAM also provides comprehensive visibility into shared resources to set alarms and visualize logs through integration with Amazon CloudWatch and AWS CloudTrail.
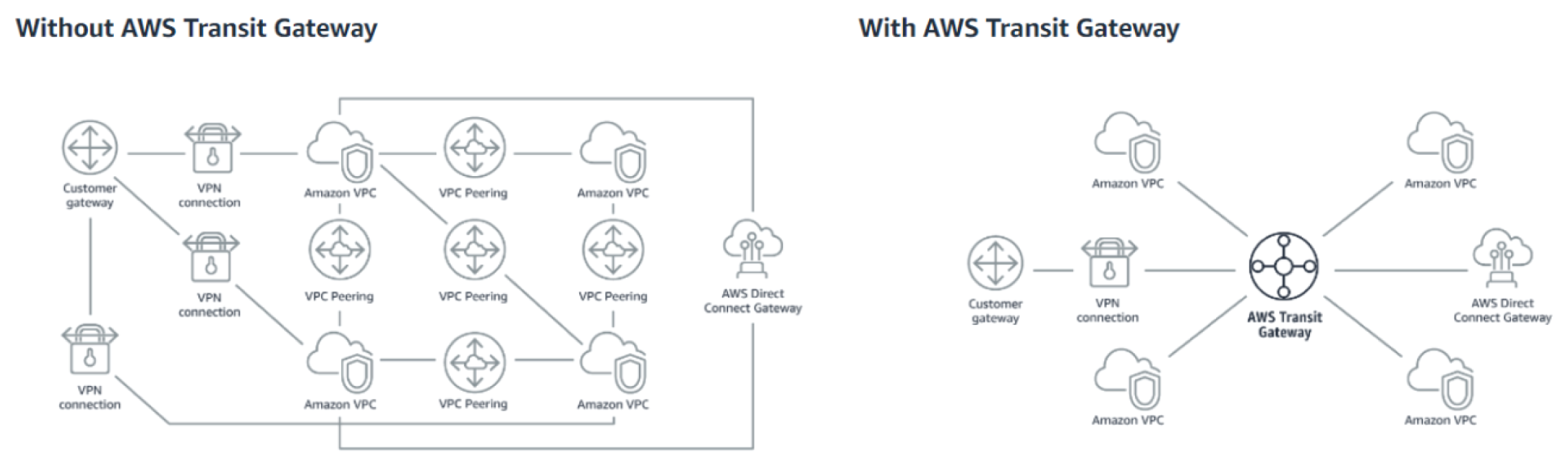
Figure 7.17: AWS Transit Gateway components
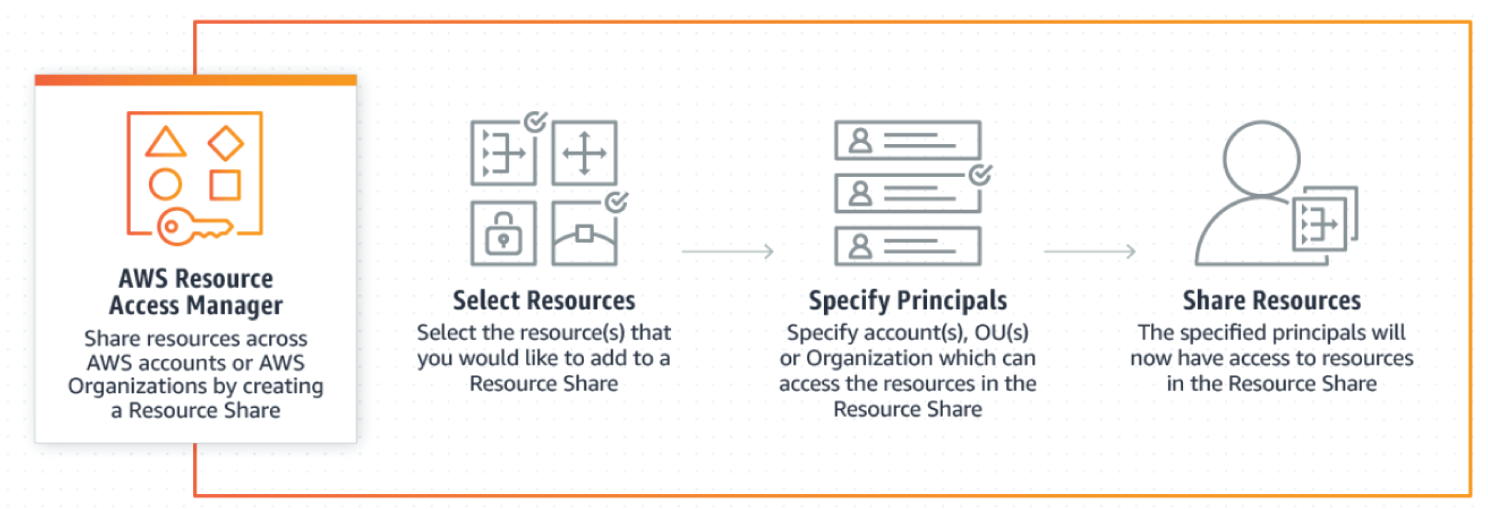
Figure 7.18: AWS Resource Access Manager components
The Detect and Respond Functions
Figure 7.19 shows the specific Detect and Respond capabilities available in the AWS Reference Architecture. Note that Amazon has aggregated the Detect and Respond capabilities under one heading due to the close alignment of their services.
Figure 7.19: Detect components of the AWS Reference Architecture
GuardDuty
Amazon GuardDuty is a threat detection service that continuously monitors for malicious activity and unauthorized behavior to protect AWS accounts, workloads, and data stored in Amazon S3. With the cloud, the collection and aggregation of account and network activities is simplified, but it can be time-consuming for security teams to continuously analyze event log data for potential threats. With GuardDuty, you now have an intelligent and cost-effective option for continuous threat detection in AWS. The service uses machine learning, anomaly detection, and integrated threat intelligence to identify and prioritize potential threats. See Figure 7.20.
GuardDuty analyzes tens of billions of events across multiple AWS data sources, such as AWS CloudTrail event logs, Amazon VPC Flow Logs, and DNS logs. With a few clicks in the AWS Management Console, GuardDuty can be enabled with no software or hardware to deploy or maintain. By integrating with Amazon CloudWatch Events, GuardDuty alerts are actionable, easy to aggregate across multiple accounts, and straightforward to push into existing event management and workflow systems. The key features are as follows:
- Comprehensive threat identification: Amazon GuardDuty identifies threats by continuously monitoring the network activity, data access patterns, and account behavior within the AWS environment. GuardDuty comes integrated with up-to-date threat intelligence feeds from AWS, CrowdStrike, and Proofpoint. Threat intelligence coupled with machine learning and behavior models help you detect activity such as crypto-currency mining, credential compromise behavior, unauthorized and unusual data access, communication with known command-and-control servers, or API calls from known malicious IPs.
- Strengthens security through automation: In addition to detecting threats, Amazon GuardDuty also makes it easy to automate how you respond to threats, reducing your remediation and recovery time. GuardDuty can perform automated remediation actions by leveraging Amazon CloudWatch events and AWS Lambda. GuardDuty security findings are informative and actionable for security operations. The findings include the affected resource's details and attacker information, such as IP address and geolocation.
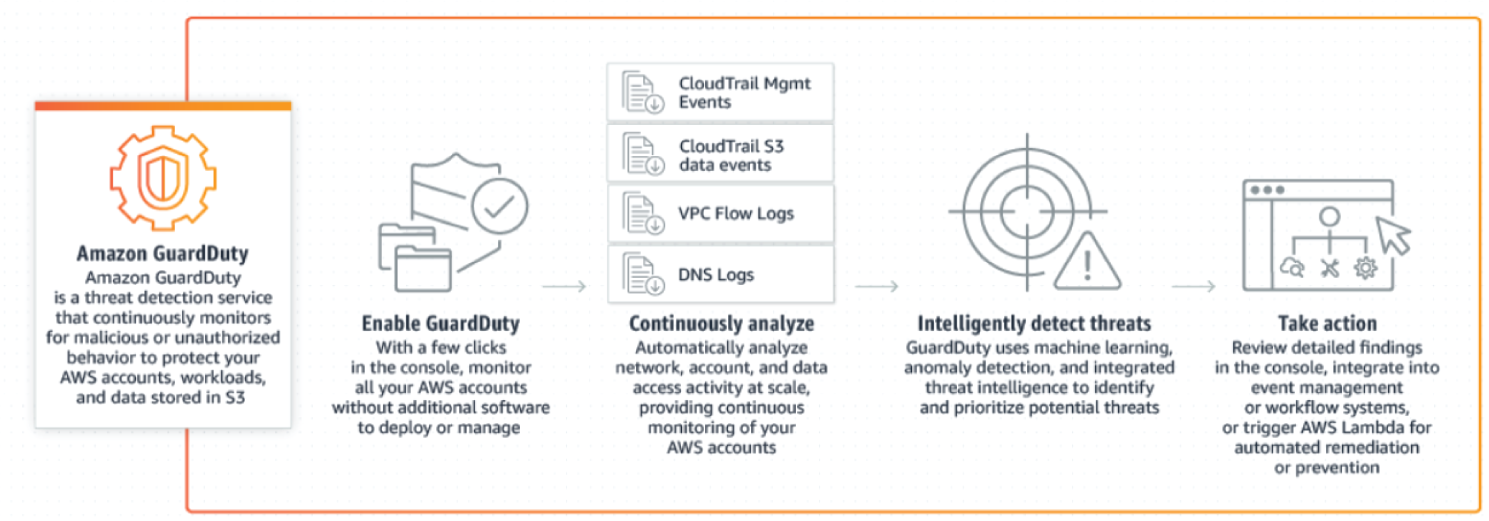
Figure 7.20: AWS GuardDuty components and architecture
Amazon GuardDuty gives you access to built-in detection techniques that are developed and optimized for the cloud. The detection algorithms are maintained and continuously improved on by AWS Security. The primary detection categories include:
- Reconnaissance: Activity suggesting reconnaissance by an attacker, such as unusual API activity, intra-VPC port scanning, unusual patterns of failed login requests, or unblocked port probing from a known bad IP.
- Instance compromise: Activity indicating an instance compromise, such as cryptocurrency mining, backdoor command and control (C&C) activity, malware using domain generation algorithms (DGA), outbound denial of service activity, unusually high volume of network traffic, unusual network protocols, outbound instance communication with a known malicious IP, temporary Amazon EC2 credentials used by an external IP address, and data exfiltration using DNS.
- Account compromise: Common patterns indicative of account compromise include API calls from an unusual geolocation or anonymizing proxy, attempts to disable AWS CloudTrail logging, changes that weaken the account password policy, unusual instance or infrastructure launches, infrastructure deployments in an unusual region, and API calls from known malicious IP addresses.
- Bucket compromise: Activity indicating a bucket compromise, such as suspicious data access patterns indicating credential misuse, unusual S3 API activity from a remote host, unauthorized S3 access from known malicious IP addresses, and API calls to retrieve data in S3 buckets from users that had no prior history of accessing the bucket or invoked from an unusual location. Amazon GuardDuty continuously monitors and analyzes AWS CloudTrail S3 data events (e.g., GetObject, ListObjects, and DeleteObject) to detect suspicious activity across all of your Amazon S3 buckets.
Amazon Detective
Amazon Detective makes it easy to analyze, investigate, and quickly identify the root cause of potential security issues or suspicious activities. Amazon Detective automatically collects log data from your AWS resources and uses machine learning, statistical analysis, and graph theory to build a linked set of data that enables you to easily conduct faster and more efficient security investigations.
AWS security services like Amazon GuardDuty, Amazon Macie, and AWS Security Hub as well as partner security products can be used to identify potential security issues, or findings. These services are really helpful in alerting you when something is wrong and pointing out where to go to fix it. But sometimes there might be a security finding where you need to dig a lot deeper and analyze more information to isolate the root cause and take action. Determining the root cause of security findings can be a complex process that often involves collecting and combining logs from many separate data sources, using extract, transform, and load (ETL) tools or custom scripting to organize the data, and then security analysts having to analyze the data and conduct lengthy investigations.
Amazon Detective simplifies this process by enabling your security teams to easily investigate and quickly get to the root cause of a finding. Amazon Detective can analyze trillions of events from multiple data sources such as Virtual Private Cloud (VPC) Flow Logs, AWS CloudTrail, and Amazon GuardDuty, and automatically creates a unified, interactive view of your resources, users, and the interactions between them over time. With this unified view, you can visualize all the details and context in one place to identify the underlying reasons for the findings, drill down into relevant historical activities, and quickly determine the root cause.
Amazon Detective produces visualizations with the information you need to investigate and respond to security findings. It helps you answer questions like “is this normal for this role to have so many failed API calls?” or “is this spike in traffic from this instance expected?” without having to organize any data or develop, configure, or tune your own queries and algorithms. Amazon Detective maintains up to a year of aggregated data that shows changes in the type and volume of activity over a selected time window, and links those changes to security findings. See Figure 7.21.
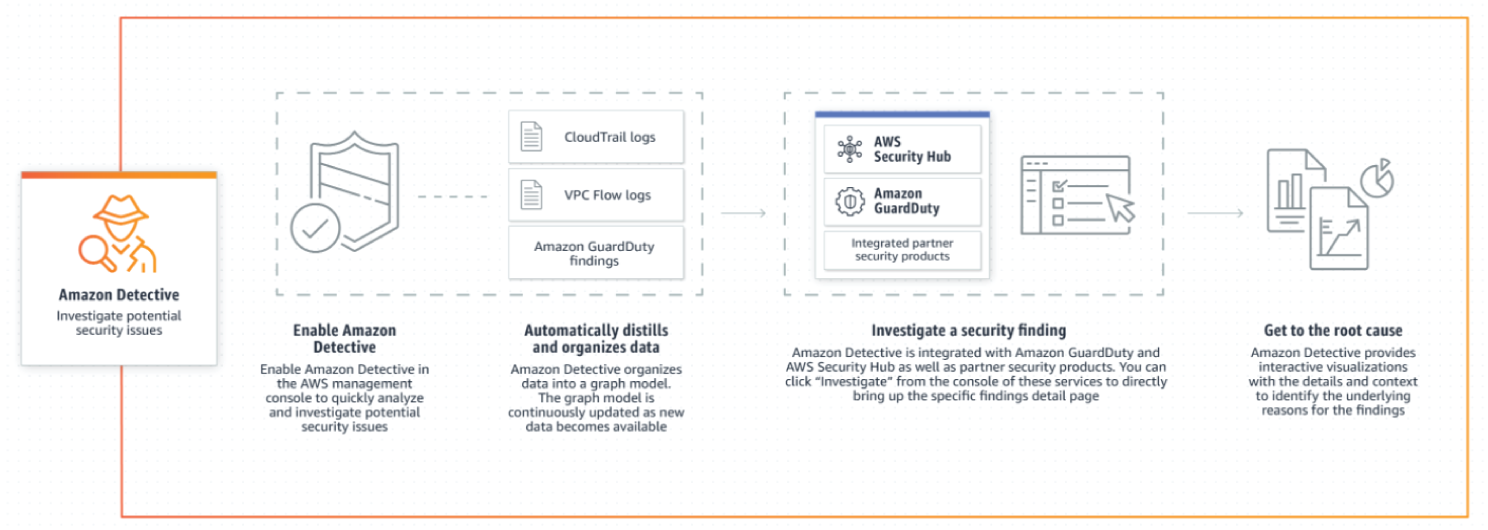
Figure 7.21: AWS Amazon Detective components
Amazon Macie
Amazon Macie is a fully managed data security and data privacy service that uses machine learning and pattern matching to discover and protect your sensitive data in AWS.
As organizations manage growing volumes of data, identifying and protecting their sensitive data at scale can become increasingly complex, expensive, and time-consuming. Amazon Macie automates the discovery of sensitive data at scale and lowers the cost of protecting your data. Macie automatically provides an inventory of Amazon S3 buckets including a list of unencrypted buckets, publicly accessible buckets, and buckets shared with AWS accounts outside those you have defined in AWS Organizations. Then, Macie applies machine learning and pattern matching techniques to the buckets you select to identify and alert you to sensitive data, such as personally identifiable information (PII). See Figure 7.22.
Macie's alerts, or findings, can be searched and filtered in the AWS Management Console and sent to Amazon EventBridge, formerly called Amazon CloudWatch Events, for easy integration with existing workflow or event management systems, or to be used in combination with AWS services, such as AWS Step Functions to take automated remediation actions. This can help you meet regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) and General Data Privacy Regulation (GDPR). You can get started with Amazon Macie by leveraging the 30-day free trial for bucket evaluation.
Amazon Macie uses machine learning and pattern matching to cost efficiently discover sensitive data at scale. Macie automatically detects a large and growing list of sensitive data types, including personal identifiable information (PII) such as names, addresses, and credit card numbers. The service also allows you to define your own custom sensitive data types so you can discover and protect the sensitive data that may be unique to your business or use case.
Amazon Macie gives you constant visibility of the data security and data privacy of your data stored in Amazon S3. Macie automatically and continually evaluates all of your S3 buckets and alerts you to any unencrypted buckets, publicly accessible buckets, or buckets shared with AWS accounts outside those you have defined in the AWS Organizations. Macie provides native multi-account support so you can view your data security posture across your entire S3 environment from a single Macie administrator account.
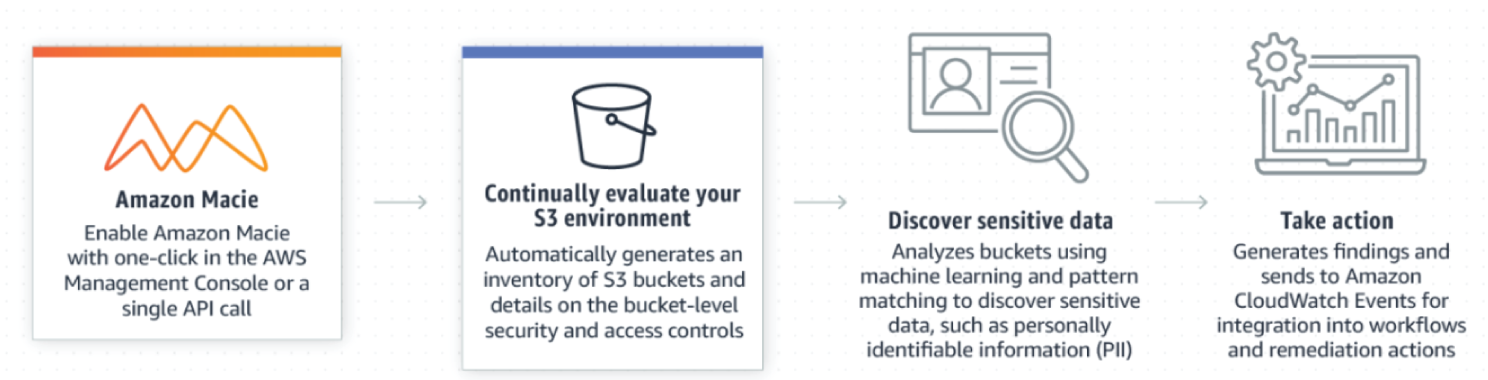
Figure 7.22: Amazon Macie components
Amazon Inspector
Amazon Inspector is an automated security assessment service that helps improve the security and compliance of applications deployed on AWS. Amazon Inspector automatically assesses applications for exposure, vulnerabilities, and deviations from best practices. After performing an assessment, Amazon Inspector produces a detailed list of security findings prioritized by level of severity. These findings can be reviewed directly or as part of detailed assessment reports that are available via the Amazon Inspector console or API.
Amazon Inspector security assessments help you check for unintended network accessibility of your Amazon EC2 instances and for vulnerabilities on those EC2 instances. Amazon Inspector assessments are offered to you as predefined rules packages mapped to common security best practices and vulnerability definitions. Examples of built-in rules include checking for access to your EC2 instances from the Internet, remote root login being enabled, or vulnerable software versions installed. These rules are regularly updated by AWS security researchers. The key features are as follows:
- Amazon Inspector helps you to identify security vulnerabilities as well as deviations from security best practices in applications, both before they are deployed, and while they are running in a production environment. This helps improve the overall security posture of your applications deployed on AWS.
- Amazon Inspector is an API-driven service that analyzes network configurations in your AWS account and uses an optional agent for visibility into your Amazon EC2 instances. This makes it easy for you to build Inspector assessments right into your existing DevOps process, decentralizing and automating vulnerability assessments, and empowering your development and operations teams to make security assessments an integral part of the deployment process.
- Amazon Inspector allows you to define standards and best practices for your applications and validate adherence to these standards. This simplifies enforcement of your organization's security standards and best practices, and helps to proactively manage security issues before they impact your production application.
Amazon CloudTrail
AWS CloudTrail is a service that enables governance, compliance, operational auditing, and risk auditing of your AWS account. With CloudTrail, you can log, continuously monitor, and retain account activity related to actions across your AWS infrastructure. CloudTrail provides event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command-line tools, and other AWS services. This event history simplifies security analysis, resource change tracking, and troubleshooting. See Figure 7.23.
In addition, you can use CloudTrail to detect unusual activity in your AWS accounts. These capabilities help simplify operational analysis and troubleshooting. The key features are as follows:
- Visibility into user and resource activity: AWS CloudTrail increases visibility into your user and resource activity by recording AWS Management Console actions and API calls. You can identify which users and accounts called AWS, the source IP address from which the calls were made, and when the calls occurred.
- Security analysis and troubleshooting: With AWS CloudTrail, you can discover and troubleshoot security and operational issues by capturing a comprehensive history of changes that occurred in your AWS account within a specified period of time.
- Security automation: AWS CloudTrail allows you to track and automatically respond to account activity threatening the security of your AWS resources. With Amazon CloudWatch Events integration, you can define workflows that execute when events that can result in security vulnerabilities are detected. For example, you can create a workflow to add a specific policy to an Amazon S3 bucket when CloudTrail logs an API call that makes that bucket public.
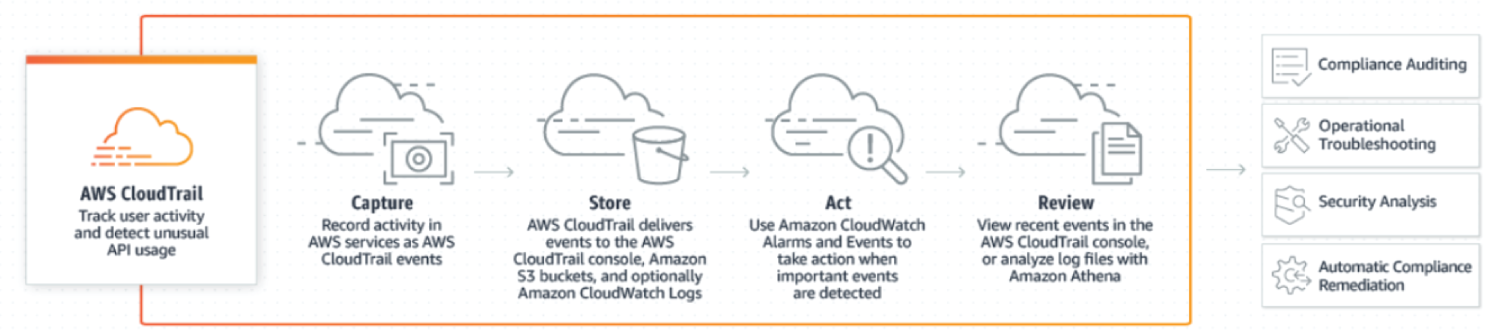
Figure 7.23: AWS CloudTrail components
Amazon CloudWatch
Amazon CloudWatch is a monitoring and observability service built for DevOps engineers, developers, site reliability engineers (SREs), and IT managers. CloudWatch provides you with data and actionable insights to monitor your applications, respond to system-wide performance changes, optimize resource utilization, and get a unified view of operational health. CloudWatch collects monitoring and operational data in the form of logs, metrics, and events, providing you with a unified view of AWS resources, applications, and services that run on AWS and on-premises servers. You can use CloudWatch to detect anomalous behavior in your environments, set alarms, visualize logs and metrics side by side, take automated actions, troubleshoot issues, and discover insights to keep your applications running smoothly. See Figure 7.24.
The key features are as follows:
- Observability on a single platform across applications and infrastructure: Modern applications such as those running on microservices architectures generate large volumes of data in the form of metrics, logs, and events. Amazon CloudWatch enables you to collect, access, and correlate this data on a single platform from across all your AWS resources, applications, and services that run on AWS and on-premises servers, helping you break down data silos so you can easily gain system-wide visibility and quickly resolve issues.
- Improve operational performance and resource optimization: Amazon CloudWatch enables you to set alarms and automate actions based on either predefined thresholds, or on machine learning algorithms that identify anomalous behavior in your metrics. For example, it can start Amazon EC2 Auto Scaling automatically, or stop an instance to reduce billing overages. You can also use CloudWatch Events for serverless to trigger workflows with services like AWS Lambda, Amazon SNS, and AWS CloudFormation.
- Get operational visibility and insight: To optimize performance and resource utilization, you need a unified operational view, real-time granular data, and historical reference. CloudWatch provides automatic dashboards, data with 1-second granularity, and up to 15 months of metrics storage and retention. You can also perform metric math on your data to derive operational and utilization insights; for example, you can aggregate usage across an entire fleet of EC2 instances.
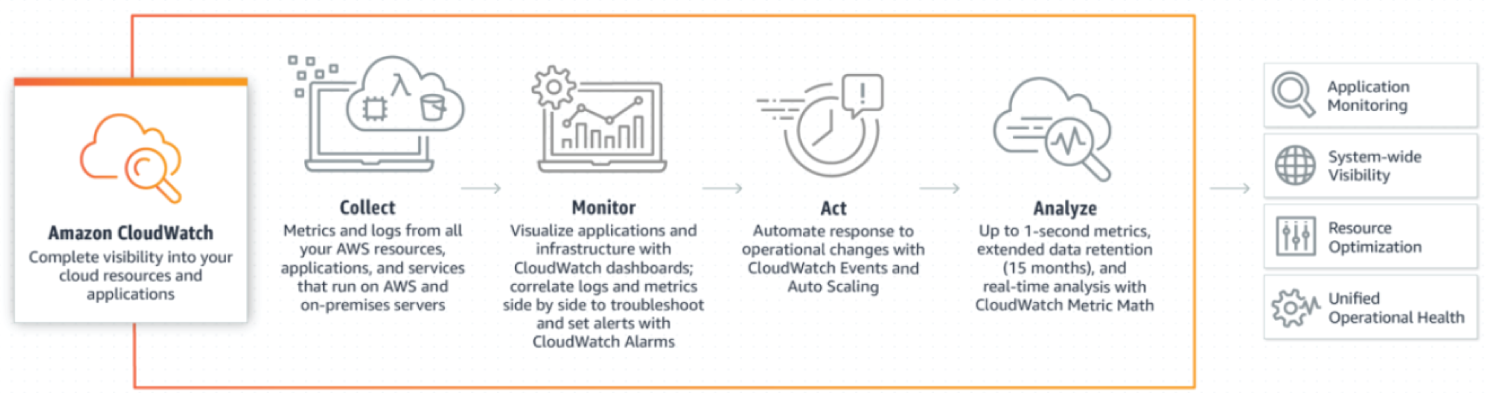
Figure 7.24: Amazon CloudWatch components and architecture
Amazon Lambda
AWS Lambda is a serverless compute service that lets you run code without provisioning or managing servers, creating workload-aware cluster scaling logic, maintaining event integrations, or managing runtimes. With Lambda, you can run code for virtually any type of application or backend service—all with zero administration. Just upload your code as a ZIP file or container image, and Lambda automatically and precisely allocates compute execution power and runs your code based on the incoming request or event, for any scale of traffic. You can set up your code to automatically trigger from 140 AWS services or call it directly from any web or mobile app. You can write Lambda functions in your favorite language (Node.js, Python, Go, Java, and more) and use both serverless and container tools, such as AWS SAM or Docker CLI, to build, test, and deploy your functions. See Figure 7.25.
The key features are as follows:
- No servers to manage: AWS Lambda automatically runs your code without requiring you to provision or manage infrastructure. Just write the code and upload it to Lambda either as a ZIP file or container image.
- Continuous scaling: AWS Lambda automatically scales your application by running code in response to each event. Your code runs in parallel and processes each trigger individually, scaling precisely with the size of the workload, from a few requests per day, to hundreds of thousands per second.
- Consistent performance at any scale: With AWS Lambda, you can optimize your code execution time by choosing the right memory size for your function. You can also keep your functions initialized and hyper-ready to respond within double-digit milliseconds by enabling provisioned concurrency.

Figure 7.25: AWS Lambda components
AWS Step Functions
AWS Step Functions is a serverless function orchestrator that makes it easy to sequence AWS Lambda functions and multiple AWS services into business-critical applications. Through its visual interface, you can create and run a series of check-pointed and event-driven workflows that maintain the application state. The output of one step acts as an input to the next. Each step in your application executes in order, as defined by your business logic. See Figure 7.26.
Orchestrating a series of individual serverless applications, managing retries, and debugging failures can be challenging. As your distributed applications become more complex, the complexity of managing them also grows. With its built-in operational controls, Step Functions manages sequencing, error handling, retry logic, and state, removing a significant operational burden from your team. The key features are as follows:
- Build and update apps quickly: Lets you build visual workflows that enable fast translation of business requirements into technical requirements. You can build applications in a matter of minutes, and when needs change, you can swap or reorganize components without customizing any code.
- Improve resiliency: Manages state, checkpoints, and restarts for you to make sure that your application executes in order and as expected. Built-in try/catch, retry, and rollback capabilities deal with errors and exceptions automatically.
- Write less code: Manages the logic of your application for you, and implements basic primitives such as branching, parallel execution, and timeouts. This removes extra code that may be repeated in your microservices and functions.
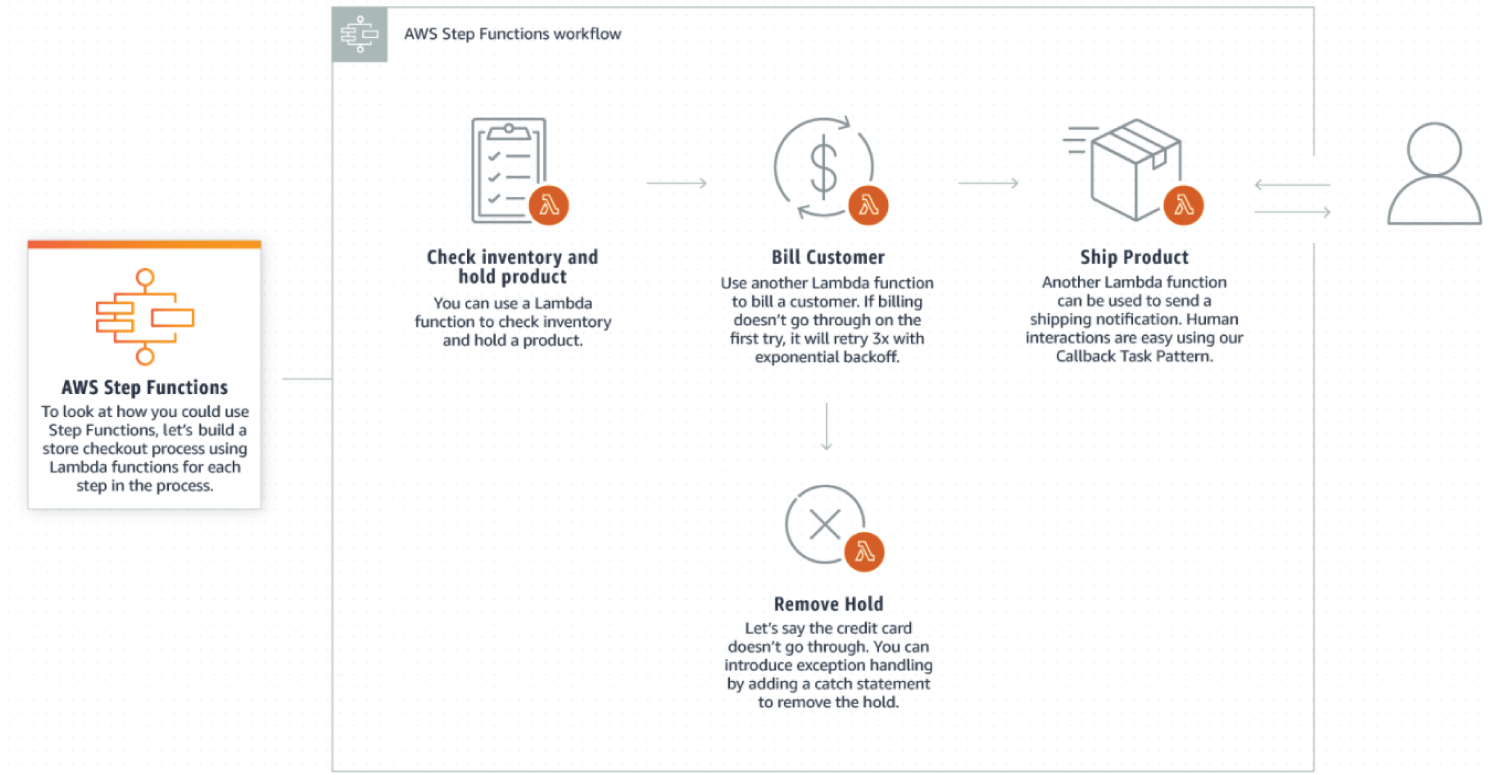
Figure 7.26: AWS Step Functions components and architecture
Amazon Route 53
Amazon Route 53 is a highly available and scalable cloud Domain Name System (DNS) web service. It is designed to give developers and businesses an extremely reliable and cost-effective way to route end users to Internet applications by translating names like www.example.com into the numeric IP addresses like 192.0.2.1 that computers use to connect to each other. Amazon Route 53 is fully compliant with IPv6 as well.
Amazon Route 53 effectively connects user requests to infrastructure running in AWS—such as Amazon EC2 instances, Elastic Load Balancing load balancers, or Amazon S3 buckets—and can also be used to route users to infrastructure outside of AWS. You can use Amazon Route 53 to configure DNS health checks to route traffic to healthy endpoints or to independently monitor the health of your application and its endpoints. Amazon Route 53 Traffic Flow makes it easy for you to manage traffic globally through a variety of routing types, including Latency Based Routing, Geo DNS, Geoproximity, and Weighted Round Robin—all of which can be combined with DNS Failover in order to enable a variety of low-latency, fault-tolerant architectures. Using Amazon Route 53 Traffic Flow's simple visual editor, you can easily manage how your end users are routed to your application's endpoints—whether in a single AWS region or distributed around the globe. Amazon Route 53 also offers Domain Name Registration—you can purchase and manage domain names such as example.com and Amazon Route 53 will automatically configure DNS settings for your domains. The key features are as follows:
- Highly available and reliable: Amazon Route 53 is built using AWS's highly available and reliable infrastructure. The distributed nature of our DNS servers helps ensure a consistent ability to route your end users to your application. Features such as Amazon Route 53 Traffic Flow help you improve reliability with easy configuration of failover to re-route your users to an alternate location if your primary application endpoint becomes unavailable. Amazon Route 53 is designed to provide the level of dependability required by important applications. Amazon Route 53 is backed by the Amazon Route 53 Service Level Agreement.
- Flexible: Amazon Route 53 Traffic Flow routes traffic based on multiple criteria, such as endpoint health, geographic location, and latency. You can configure multiple traffic policies and decide which policies are active at any given time. You can create and edit traffic policies using the simple visual editor in the Route 53 console, AWS SDKs, or the Route 53 API. Traffic Flow's versioning feature maintains a history of changes to your traffic policies, so you can easily roll back to a previous version using the console or API.
- Simplifies the hybrid cloud: Amazon Route 53 Resolver provides recursive DNS for your Amazon VPC and on-premises networks over AWS Direct Connect or AWS Managed VPN.
AWS Personal Health Dashboard
AWS Personal Health Dashboard provides alerts and remediation guidance when AWS is experiencing events that may impact you. While the Service Health Dashboard displays the general status of AWS services, Personal Health Dashboard gives you a personalized view into the performance and availability of the AWS services underlying your AWS resources.
The dashboard displays relevant and timely information to help you manage events in progress, and provides proactive notification to help you plan for scheduled activities. With Personal Health Dashboard, alerts are triggered by changes in the health of AWS resources, giving you event visibility and guidance to help quickly diagnose and resolve issues. The key features are as follows:
- Personalized view of service health: Gives you a personalized view of the status of the AWS services that power your applications, enabling you to quickly see when AWS is experiencing issues that may impact you. For example, in the event of a lost Amazon Elastic Block Store (EBS) volume associated with one of your Amazon EC2 instances, you would gain quick visibility into the status of the specific service you are using, helping save precious time troubleshooting to determine root cause.
- Proactive notifications: Provides forward-looking notifications, and you can set up alerts across multiple channels, including email and mobile notifications, so you receive timely and relevant information to help plan for scheduled changes that may affect you. In the event of AWS hardware maintenance activities that may impact one of your Amazon EC2 instances, for example, you would receive an alert with information to help you plan for, and proactively address any issues associated with the upcoming change.
- Aggregates health events across AWS Organizations: If you use AWS Organizations, AWS Health allows you to aggregate notifications from all accounts in your organization. This provides centralized and real-time access to all AWS Health events posted to individual accounts in your organization, including operational issues, scheduled maintenance, and account notifications.
The Recover Functions
This section discusses the Recover capability of the AWS Reference Architecture, as illustrated in Figure 7.27.
Figure 7.27: Recover components of the AWS Reference Architecture
Amazon Glacier
Amazon S3 Glacier and S3 Glacier Deep Archive are secure, durable, and extremely low-cost Amazon S3 cloud storage classes for data archiving and long-term backup. They are designed to deliver 99.999999999% durability, and provide comprehensive security and compliance capabilities that can help meet even the most stringent regulatory requirements. To keep costs low yet suitable for varying retrieval needs, Amazon S3 Glacier provides three options for access to archives, from a few minutes to several hours, and S3 Glacier Deep Archive provides two access options ranging from 12 to 48 hours.
The Amazon S3 Glacier storage class provides three retrieval options to fit your use case. Expedited retrievals typically return data in 1–5 minutes, and are great for Active Archive use cases. Standard retrievals typically complete within 3–5 hours, and work well for less time-sensitive needs like backup data, media editing, or long-term analytics. Bulk retrievals are the lowest-cost retrieval option, returning large amounts of data within 5–12 hours. The Amazon S3 Glacier Deep Archive storage class provides two retrieval options ranging from 12–48 hours.
In addition to integration with most AWS services, Amazon S3 object storage services include tens of thousands of consulting, systems integrator, and independent software vendor partners, with more joining every month. AWS Partner Network partners have adapted their services and software to work with Amazon S3 storage classes for solutions like Backup & Recovery, Archiving, and Disaster Recovery. No other cloud provider has more partners with solutions that are pre-integrated to work with their service.
AWS CloudFormation
AWS CloudFormation gives you an easy way to model a collection of related AWS and third-party resources, provision them quickly and consistently, and manage them throughout their lifecycles, by treating infrastructure as code. A CloudFormation template describes your desired resources and their dependencies so you can launch and configure them together as a stack. You can use a template to create, update, and delete an entire stack as a single unit, as often as you need to, instead of managing resources individually. You can manage and provision stacks across multiple AWS accounts and AWS Regions (see Figure 7.28). The key features are as follows:
- Automate best practices: With CloudFormation, you can apply DevOps and GitOps best practices using widely adopted processes such as starting with a Git repository and deploying through a CI/CD pipeline. You can also simplify auditing changes and trigger automated deployments with pipeline integrations such as GitHub Actions and AWS CodePipeline.
- Scale your infrastructure worldwide: Manage resource scaling by sharing CloudFormation templates to be used across your organization, to meet safety, compliance, and configuration standards across all AWS accounts and regions. Templates and parameters enable easy scaling so you can share best practices and company policies. Additionally, CloudFormation StackSets enables you to create, update, or delete stacks across multiple AWS accounts and Regions, with a single operation.
- Manage third-party and private resources: Model, provision, and manage third-party application resources (such as monitoring, team productivity, incident management, CI/CD, and version control applications) alongside your AWS resources. Use the open source CloudFormation CLI to build your own CloudFormation resource providers—native AWS types published as open source.
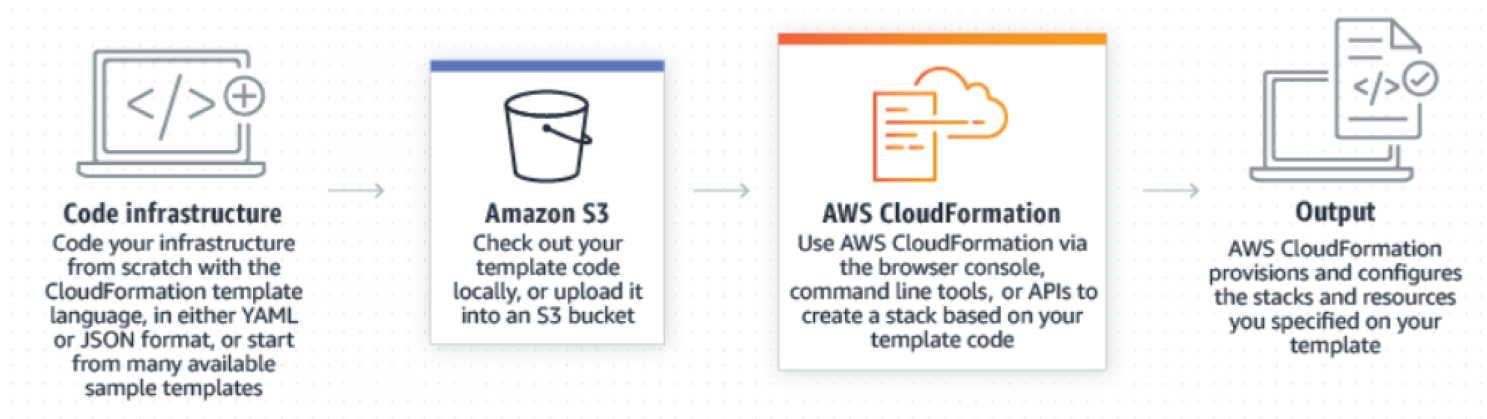
Figure 7.28: AWS CloudFormation components
CloudEndure Disaster Recovery
IT disasters such as datacenter failures, server corruptions, or cyber-attacks can not only disrupt businesses, but also cause data loss, impact your revenue, and damage your reputation. CloudEndure Disaster Recovery minimizes downtime and data loss by providing fast, reliable recovery of physical, virtual, and cloud-based servers into AWS Cloud, including public regions, AWS GovCloud (US), and AWS Outposts.
You can use CloudEndure Disaster Recovery to protect your most critical databases, including Oracle, MySQL, and SQL Server, as well as enterprise applications such as SAP.
CloudEndure Disaster Recovery continuously replicates your machines (including operating system, system state configuration, databases, applications, and files) into a low-cost staging area in your target AWS account and preferred Region. In the case of a disaster, you can instruct CloudEndure Disaster Recovery to automatically launch thousands of your machines in their fully provisioned state in minutes.
By replicating your machines into a low-cost staging area while still being able to launch fully provisioned machines within minutes, CloudEndure Disaster Recovery can significantly reduce the cost of your disaster recovery infrastructure. The key features are as follows:
- Reduce downtime and protect against data loss: Unlike snapshot-based solutions that update target locations at distinct, infrequent intervals, CloudEndure Disaster Recovery provides asynchronous, continuous replication. This enables Recovery Point Objectives (RPOs) of seconds. Automated machine conversion and orchestration enable Recovery Time Objectives (RTOs) of minutes. You can meet these stringent recovery objectives even for your largest write-intensive workloads.
- Protect enterprise applications and databases with a single tool: CloudEndure Disaster Recovery allows you to achieve business continuity for your most critical databases, including Oracle, MySQL, and SQL Server, as well as enterprise applications such as SAP. This means that you don't need to purchase multiple application-specific replication tools because CloudEndure Disaster Recovery replicates all applications and databases that run on supported operating systems.
- Protect your data from ransomware attacks: In the event of a ransomware attack, use CloudEndure Disaster Recovery to launch an unencrypted, uncorrupted version of your servers on your target AWS Region. CloudEndure Disaster Recovery provides point-in-time recovery, which enables failback to a recovery point from before the attack. This minimizes data loss and enables the quick return to normal operations.
AWS OpsWorks
AWS OpsWorks is a configuration management service that provides managed instances of Chef and Puppet. Chef and Puppet are automation platforms that allow you to use code to automate the configurations of your servers. OpsWorks lets you use Chef and Puppet to automate how servers are configured, deployed, and managed across your Amazon EC2 instances or on-premises compute environments. OpsWorks has three offerings—AWS OpsWorks for Chef Automate, AWS OpsWorks for Puppet Enterprise, and AWS OpsWorks Stacks. The key features are as follows:
- AWS OpsWorks for Chef Automate: AWS OpsWorks for Chef Automate is a fully managed configuration management service that hosts Chef Automate, a suite of automation tools from Chef for configuration management, compliance and security, and continuous deployment. OpsWorks also maintains your Chef server by automatically patching, updating, and backing up your server. OpsWorks eliminates the need to operate your own configuration management systems or worry about maintaining its infrastructure. OpsWorks gives you access to all of the Chef Automate features, such as configuration and compliance management, which you manage through the Chef console or command-line tools like Knife. It also works seamlessly with your existing Chef cookbooks.
- AWS OpsWorks for Puppet Enterprise: AWS OpsWorks for Puppet Enterprise is a fully managed configuration management service that hosts Puppet Enterprise, a set of automation tools from Puppet for infrastructure and application management. OpsWorks also maintains your Puppet master server by automatically patching, updating, and backing up your server. OpsWorks eliminates the need to operate your own configuration management systems or worry about maintaining its infrastructure. OpsWorks gives you access to all of the Puppet Enterprise features, which you manage through the Puppet console. It also works seamlessly with your existing Puppet code.
Summary
- AWS aligns its threat-hunting capabilities to simulate the majority of the MITRE ATT&CK Framework TTPs.
- The Identify function is addressed by services such as security hub, AWS config, AWS organization, AWS Control Tower, AWS Trusted Advisor, AWS Well-Architected Tool, AWS Services Catalog, and AWS Systems Manager.
- The Protect function is addressed by key services such as AWS Identity & Access Management, AWS Single Sign-On, AWS Shield, AWS Web Application Firewall, AWS Cloud HSM, AWS Secrets Manager, AWS Certificate Manager, AWS IoT Device Defender, and AWS Virtual Private Cloud.
- The Detect and Respond functions are addressed by GuardDuty, Amazon Detective, Amazon Macie, Amazon Inspector, Amazon CloudTrail, Amazon CloudWatch, Amazon Lambda, and AWS Route 53.
- Amazon GuardDuty and Inspector are key detection services that leverage machine learning and artificial intelligence. They are very beneficial to organizations' threat-hunting capability.
- Amazon Macie provides a key data classification capability that prevents many threats to organizations. It can be configured to have automatic detection or manual detection capability.
- The Recovery function is addressed by Amazon Glacier, AWS CloudFormation, CloudEndure Disaster Recovery, and AWS OpsWorks.
