CHAPTER 8
Threat Hunting in Other Cloud Providers
The objective of this chapter is to explore the current threat-hunting capabilities in other leading cloud service providers (CSPs) such as Google, IBM, Oracle, and Alibaba.
There are three main service models of cloud computing—Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). There are clear differences between the three and what they can offer a business in terms of storage and resource pooling, but they can also interact with each other to form one comprehensive model of cloud computing.
Cloud platform providers of IaaS, PaaS, and SaaS have built or adopted threat-hunting capabilities to protect their customer's data residing on their platform. We went deeper into Microsoft Azure and AWS threat-hunting capabilities in previous chapters. Let's take a look at threat-hunting capabilities of some of the other leading cloud computing platform providers who offer all three main cloud service models—IaaS, PaaS, and SaaS—to enterprises and small to medium businesses. Note that key SaaS cloud capabilities such as Salesforce are not addressed, since the focus is on “pure cloud platform” providers who provide all IaaS, PaaS, and SaaS.
The Google Cloud Platform
The Google Cloud Platform is a suite of cloud computing services that runs on the same infrastructure that Google uses internally for its end-user products, such as Google Search, Gmail, file storage, and YouTube. Alongside a set of management tools, it provides a series of modular cloud services, including computing, data storage, data analytics, and machine learning.
Google's threat-hunting capability centers on the Chronicle platform (Figure 8.1). Chronicle is a cloud service, built as a specialized layer on top of core Google infrastructure, designed for enterprises to privately retain, analyze, and search the massive amounts of security and network telemetry they generate. Chronicle normalizes, indexes, correlates, and analyzes the data to provide instant analysis and context on risky activity. Chronicle is a global security telemetry platform for detection, investigation, and threat hunting within your enterprise network.
The key services that Chronicle provides include the following:
- Threat Investigation: VirusTotal Enterprise owns an extensive malware intelligence database that can link and visualize malware relationships across external files, domains, and internal assets. Chronicle takes advantage of the largest malware database in the world to provide enterprises with its threat investigation services. Chronicle's threat investigation services capabilities also include continuous automation and speed to ensure that threats are discovered in near real-time.
- Threat Hunting and Detection: Reducing false positives and eliminating the use of triaging in detecting threats speeds up the threat-hunting and detection processes for security analysts. Chronicle helps achieve this through retroactive correlation of enterprise security telemetry with backing from threat intelligence sources such as Avast and AVG. This process reduces the duration of security analysis by ensuring real threats are detected and providing a comprehensive analysis of discovered threats.
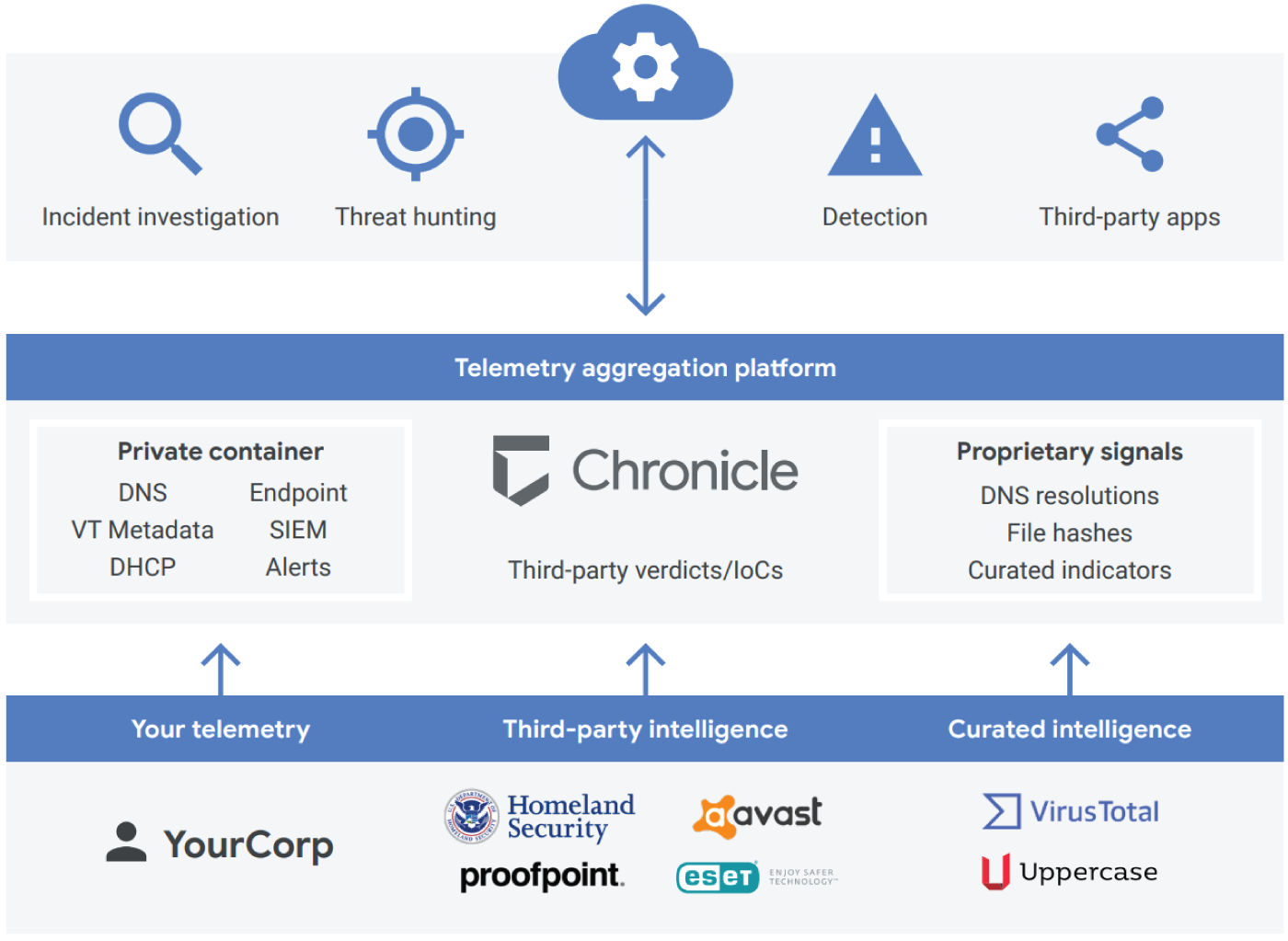
Figure 8.1: Chronicle overview
- Security Analytics: The Chronicle platform is capable of ingesting large datasets, indexing, correlating, and providing enterprise-grade security analyses in seconds. The high speed at which Chronicle executes security analytics means that teams can upload their security telemetry onto the platform and start analyzing it within seconds.
- Security Operations on GCP with Security Command Center: Security Command Center offers a single platform to aggregate and manage security findings on GCP. It was designed by Google to provide visibility into how resources are configured as well as the ability to reliably detect threats in real time. Security misconfigurations are often in and of themselves vulnerabilities. Therefore, monitoring for misconfigurations is one of its core capabilities in addition to monitoring for common web application vulnerabilities. Security Command Center offers near-real-time visibility into GCP resources and policies, as well as the detection of threats and compliance violations based on industry standards and benchmarks. You should consider using this service if you want to obtain a centralized view of your security and data attack surface.
Google Cloud Platform Security Architecture alignment to NIST
Google's NIST Cybersecurity Framework and Google Cloud whitepaper at https://services.google.com/fh/files/misc/gcp_nist_cybersecurity_framework.pdf mentions that NIST CSF complements, but does not replace, an organization's risk management process and cybersecurity program. It continues to elaborate that cloud computing allows organizations to leverage a shared security model (discussed in Chapters 4 and 6). Data security is still the responsibility of the organization's reference architecture.
The following section outlines categories and subcategories of the NIST Cybersecurity Framework. Corresponding to each NIST CSF category and subcategory are recommendations on how to meet and implement these requirements in Google Cloud. Organizations can leverage some or all of the suggested components to define, enforce, and manage cloud security and compliance.
The Identify Function
The data, personnel, devices, systems, and facilities that enable the organization to achieve business purposes are identified and managed consistent with their relative importance to organizational objectives and the organization's risk strategy.
- Cloud Identity: Google's Identity as a Service (IDaaS). Manage users, groups, devices, and applications across your organization.
https://cloud.google.com/identity/ - Google Admin Console: Manage and add users, devices, data regions, and security settings.
https://gsuite.google.com/products/admin/ - Cloud Resource Manager: Get an org-wide snapshot of your GCP resources and policies.
https://cloud.google.com/resource-manager/docs/cloud-asset-inventory/overview - Forseti Security: Cloud Asset API to collect and store information about your GCP resources. (
https://forsetisecurity.org/docs/latest/configure/inventory/index.html - Cloud Security Command Center (CSCC): Enhance your security posture with centralized asset discovery and inventory, sensitive data identification, app vulnerability detection, access control monitoring, anomaly detection, and input from third-party security tools with real-time notifications.
https://cloud.google.com/security-command-center/ - Cloud Private Catalog: Build out and manage a cloud catalog to manage your cloud resources and make them easily discoverable.
https://cloud.google.com/private-catalog/ - Cloud Data Catalog: Fully managed metadata discovery and management platform. Helps organizations quickly discover, manage, secure, and understand their data assets.
https://cloud.google.com/data-catalog/ - Identity Platform: Add Google-grade identity and access management to your apps. Identity Platform is a customer identity and access management (CIAM) platform that helps organizations add identity and access management functionality to their applications.
https://cloud.google.com/identity-cp/ - Cloud Identity & Access Management: Maintain fine-grained control over who has access to what cloud resources. Define access roles and permissions while enforcing separation of duties and least privilege.
https://cloud.google.com/iam/ - Google Cloud Adoption Framework: Determine your organization's cloud readiness and strategically map out your journey to the cloud.
https://cloud.google.com/adoption-framework/ - Professional Services: Advisory capability to engage business leaders and users on innovating daily business processes with Google.
https://services.google.com/fh/files/misc/transformation_advisory.pdf - Google's Security & Trust Center: Understand and leverage Google's ISO, SOC, PCI, HIPAA, FedRAMP, FIPS GDPR, and other compliance standards, regulations, and certifications.
https://cloud.google.com/sec - Cloud Security Scanner: Automatically scan App Engine applications for common vulnerabilities such as XXS, flash injection, mixed HTTP(S) content, outdated and insecure libraries.
https://cloud.google.com/security-scanner/ - Container Registry Vulnerability Scanner: Scan container images stored in Container Registry for common vulnerabilities.
https://cloud.google.com/container-registry/docs/container-analysis - Cloud Armor: Protect your infrastructure and web applications from Distributed Denial of Service (DDoS) attacks.
https://cloud.google.com/armor/ - Phishing Protection: Quickly report unsafe URLs to Google Safe Browsing and view status in Cloud Security Command Center.
https://cloud.google.com/phishing-protection/
The Protect Function
Access to physical and logical assets and associated facilities is limited to authorized users, processes, and devices, and is managed consistent with the assessed risk of unauthorized access to authorized activities and transactions.
- Cloud Identity & Access Management: Maintain fine-grained control over who has access to what cloud resources. Define access roles and permissions while enforcing separation of duties and least privilege.
https://cloud.google.com/iam/ - Cloud Identity Google's Identity as a Service (IDaaS): Manage users, groups, devices, and applications across your organization. Also implements MFA and SSO.
https://cloud.google.com/identity/ - Google Admin Console: Manage and add users, devices, data regions and security settings.
https://gsuite.google.com/products/admin/ - VPC Service Controls: Define a security perimeter around specific GCP resources to help mitigate data exfiltration risks.
https://cloud.google.com/vpc-service-controls/ - Cloud Identity Aware Proxy: Build an enterprise security model to control access to your applications and VMs. Verify user identities and access request context to determine if users should be allowed access to resources.
https://cloud.google.com/iap/ - Forseti Security: Systematically monitor your GCP resources, create and enforce rule-based security policies. Codify your security stance to maintain compliance and governance.
https://forsetisecurity.org/about/ - Context Aware Access: Manage access to apps and infrastructure based on a user's identity and context.
https://cloud.google.com/context-aware-access/ - Identity Platform: Add Google-grade identity and access management to your apps. Identity Platform is a customer identity and access management (CIAM) platform that helps organizations add identity and access management functionality to their applications.
https://cloud.google.com/identity-cp/ - Cloud VPC: Manage network functionality and segmentation of cloud resources. Leverage Cloud Router, Cloud VPN, Firewalls, Routes, VPC Flow Logs, Shared VPC, and VPC peering for more granular network security.
https://cloud.google.com/vpc/ - Cloud Resource Manager: Manage and separate GCP resource hierarchy across your organization, folders, and projects.
https://cloud.google.com/resource-manager/ - Google Cloud Training: Leverage on-demand Coursera courses, hands-on qwiklabs, and Google or Partner-led classroom instruction to train your organization.
https://cloud.google.com/training/ - Google Cloud Adoption Framework: Determine your organization's cloud readiness and strategically map out your journey to the cloud.
https://cloud.google.com/adoption-framework/ - Professional Services: Advisory capability to engage business leaders and users on innovating daily business processes with Google.
https://services.google.com/fh/files/misc/transformation_advisory.pdf - Google Encryption at Rest: All data in Google is encrypted at rest by default using envelope encryption.
https://cloud.google.com/security/encryption-at-rest/ - Cloud Key Management Service: Manage, generate, use, rotate, and destroy AES256, RSA 2048, RSA 3072, RSA 4096, EC P256, and EC P384 cryptographic keys on Google Cloud.
https://cloud.google.com/kms/ - Customer Supplied Encryption Keys (CSEKs): In addition to Google's default encryption, supply your own AES256 encryption keys to encrypt GCP data.
https://cloud.google.com/storage/docs/encryption/customer-supplied-keys - Cloud HSM: Protect your encryption keys in the cloud using a fully hosted, FIPS 140-2 Level 3 compliant hardware security model.
https://cloud.google.com/hsm/ - Google Encryption in Transit: Data encrypted in transit automatically at layer 7 and layer 3/4 in Google Cloud via TLS.
https://cloud.google.com/security/encryption-in-transit/ - GCP Quotas: Set, enforce, and request quotas on resource usage to regulate how much of a particular GCP resource a project can use.
https://cloud.google.com/docs/quota - Autoscaling: Use GCE managed instance groups or managed compute services like Google App Engine to automatically scale capacity based on need or Cloud Monitoring metrics.
https://cloud.google.com/compute/docs/autoscaler/ - Cloud Data Loss Prevention: Configure DLP to automatically discover, classify, and redact sensitive data in Google Cloud & G Suite.
https://cloud.google.com/dlp/ - Phishing Protection: Quickly report unsafe URLs to Google Safe Browsing and view status in Cloud Security Command Center.
https://cloud.google.com/phishing-protection/ - Access Approval API: Allows you to explicitly approve access to your data or configurations on GCP before it happens.
https://cloud.google.com/access-approval/docs/overview - VPC Service: Controls define a security perimeter around specific GCP resources to help mitigate data exfiltration risks.
https://cloud.google.com/vpc-service-controls/ - Titan Security Key: Prevent account hacks, phishing attacks, and enforce MFA/2SV using Titan Security Keys.
https://cloud.google.com/titan-security-key/ - Shielded VMs: Leverage hardened virtual machines on GCP that defend against rootkits, botkits, protect against remote attacks, privilege escalation, and malicious insiders.
https://cloud.google.com/shielded-vm/ - reCAPTCHA: Protect your website from fraudulent activity, spam, and abuse.
https://cloud.google.com/recaptcha-enterprise/ - Binary Authorization: Deploy-time security controls to ensure that only trusted container images are deployed on Kubernetes. Requires images to be signed by trusted authorities during development and enforces signature validation during deployment.
https://cloud.google.com/binary-authorization/
The Detect Function
Anomalous activity is detected and the potential impact of events is understood.
- Cloud VPC: Manage network functionality and segmentation of cloud resources. Leverage Cloud Router, Cloud VPN, Firewalls, Routes, VPC Flow Logs, Shared VPC, and VPC peering for more granular network security.
https://cloud.google.com/vpc/ - Traffic Director: Enterprise-ready traffic management for open service mesh. Delivers configuration and traffic control intelligence to sidecar service proxies.
https://cloud.google.com/traffic-director/ - VPC Service Controls: Define a security perimeter around specific GCP resources to help mitigate data exfiltration risks.
https://cloud.google.com/vpc-service-controls/ - Cloud Armor: Protect your infrastructure and web applications from Distributed Denial of Service (DDoS) attacks.
https://cloud.google.com/armor/ - G Suite Phishing & Malware Protection: Advanced phishing and malware protection. Place emails in quarantine, protect against anomalous attachments, protect Google Groups from inbound email spoofing.
https://support.google.com/a/answer/7577854 - Network Telemetry: Enable firewall logging, VPC flow logs, performance monitoring and metrics, and log exports to keep your networks and services secure.
https://cloud.google.com/network-telemetry/ - Incident Response Management: Leverage IRM with Monitoring to identify, manage, investigate, and resolve incidents.
https://cloud.google.com/incident-response/docs/ - Cloud Operations Suite: Store, search, analyze, monitor, and alert on log data and events in Google Cloud. Includes error reporting, production application profiling, application tracing, alerting, debugging, and third-party integrations.
https://cloud.google.com/stackdriver/ - Cloud Security Scanner: Automatically scan App Engine, Compute Engine, and Kubernetes Engine applications for common vulnerabilities such as XXS, flash injection, mixed HTTP(S) content, outdated and insecure libraries.
https://cloud.google.com/security-scanner/ - Container Registry: Scan container images stored in Container Registry for common vulnerabilities.
https://cloud.google.com/container-registry/docs/container-analysis - Cloud Security Command Center (CSCC): Enhance your security posture with centralized asset discovery and inventory, sensitive data identification, app vulnerability detection, access control monitoring, anomaly detection, and input from third-party security tools with real-time notifications.
https://cloud.google.com/security-command-center/ - G Suite Security Center: Actionable security insights for G Suite. Protect your organization with security analytics and best practice recommendations from Google. Get insights into external file sharing, visibility into spam and malware targeting users within your organization.
https://gsuite.google.com/products/admin/security-center/ - Android Enterprise: Provides multiple layers of security to prevent intrusions including built-in Titan Security Keys, Google Play Protect, Management APIs, hardened OS platform, and dedicated hardware.
https://www.android.com/enterprise/security/https://blog.google/technology/safety-security/your-android-phone-is-a-security-key/ - Google's Security & Trust Center: Understand and leverage Google's ISO, SOC, PCI, HIPAA, FedRAMP, FIPS GDPR, and other compliance standards, regulations, and certifications.
https://cloud.google.com/sec - Event Threat Detection: Uncover security threats in Google Cloud Platform environments.
https://cloud.google.com/event-threat-detection/ - Cloud Pub/Sub: Stream analytics, events, notifications, and messages.
https://cloud.google.com/pubsub/ - Cloud Functions: Event-driven serverless compute platform.
https://cloud.google.com/functions/ - Policy Intelligence: Smart access control for your GCP resources. Helps enterprises understand and manage their policies to reduce risk.
https://cloud.google.com/policy-intelligence/
The Respond Function
Response processes and procedures are executed and maintained, to ensure response to detected cybersecurity incidents.
- Incident Response Management: Leverage IRM with Monitoring to identify, manage, investigate, and resolve incidents.
https://cloud.google.com/incident-response/docs/ - G Suite Security Center: Actionable security insights for G Suite. Protect your organization with security analytics and best practice recommendations from Google. Get insights into external file sharing, visibility into spam and malware targeting users within your organization.
https://gsuite.google.com/products/admin/security-center/ - Cloud Security Command Center (CSCC): Enhance your security posture with centralized asset discovery and inventory, sensitive data identification, app vulnerability detection, access control monitoring, anomaly detection, and input from third-party security tools with real-time notifications.
https://cloud.google.com/security-command-center/ - Cloud Identity & Access Management: Maintain fine-grained control over who has access to what cloud resources. Define access roles & permissions while enforcing separation of duties and least privilege.
https://cloud.google.com/iam/ - Cloud Identity Google's Identity as a Service (IDaaS): Manage users, groups, devices, and applications across your organization.
https://cloud.google.com/identity/ - Google Admin Console: Manage and add users, devices, data regions and security settings.
https://gsuite.google.com/products/admin/ - Identity Platform: Add Google-grade identity and access management to your apps. Identity Platform is a customer identity and access management (CIAM) platform that helps organizations add identity and access management functionality to their applications.
https://cloud.google.com/identity-cp/ - Cloud Operations Suite: Store, search, analyze, monitor, and alert on log data and events in Google Cloud. Includes error reporting, production application profiling, application tracing, alerting, debugging, and third-party integrations.
https://cloud.google.com/stackdriver/ - Log Exports: Export logs to GCS for storage and archival, to BigQuery for analysis, or to external systems for broader integration and analysis.
https://cloud.google.com/logging/docs/export/ - BigQuery: Serverless, highly scalable, and cost-effective cloud data warehouse with an in-memory BI Engine and machine learning built in. Analyze all your batch and streaming data.
https://cloud.google.com/bigquery/ - Event Threat: Event Threat Detection to uncover security threats in Google Cloud Platform environments.
https://cloud.google.com/event-threat-detection/ - Forseti Security: Systematically monitor your GCP resources, create and enforce rule-based security policies. Codify your security stance to maintain compliance and governance.
https://forsetisecurity.org/about/ - Cloud Security Scanner: Automatically scan App Engine, Compute Engine, and Kubernetes Engine applications for common vulnerabilities such as XXS, flash injection, mixed HTTP(S) content, outdated, and insecure libraries.
https://cloud.google.com/security-scanner/ - Cloud Armor: Protect your infrastructure and web applications from Distributed Denial of Service (DDoS) attacks.
https://cloud.google.com/armor/ - Container Registry Vulnerability Scanner: Scan container images stored in Container Registry for common vulnerabilities.
https://cloud.google.com/container-registry/docs/container-analysis - Phishing Protection: Quickly report unsafe URLs to Google Safe Browsing and view status in Cloud Security Command Center.
https://cloud.google.com/phishing-protection/
The Recover Function
Recovery processes and procedures are executed and maintained to ensure restoration of systems or assets affected by cybersecurity incidents.
- Google Cloud Disaster Recovery: Build a disaster recovery architecture and plan for data and applications in Google Cloud.
https://cloud.google.com/solutions/dr-scenarios-planning-guide - Global, Regional: Build in high availability by leveraging global, zonal, and regional Google Cloud resources.
https://cloud.google.com/compute/docs/regions-zones/global-regional-zonal-resources - Google Cloud Load Balancing: Implement global network autoscaling, HTTP(S), TCP, SSL, and Internal Load Balancing.
https://cloud.google.com/load-balancing/ - Cloud CDN: Deliver content across Google's global, low-latency network using cloud content delivery network.
https://cloud.google.com/cdn/ - Autoscaling: Use GCE managed instance groups or managed compute services like Google App Engine to automatically scale capacity based on need or Cloud Monitoring metrics.
https://cloud.google.com/compute/docs/autoscaler/ - Google Deployment Manager: Create and manage cloud resources with simple templates. Specify all the resources needed for your application in a declarative format, use templates to parameterize and reuse configurations.
https://cloud.google.com/deployment-manager/ - Incident Response Management: Leverage IRM with Monitoring to identify, manage, investigate, and resolve incidents.
https://cloud.google.com/incident-response/docs/ - Contact Center AI: Combine the best of Google AI with your customer contact center software to improve customer experience and operational efficiency.
https://cloud.google.com/solutions/contact-center/ - Google Cloud Status Dashboard: View the current status of GCP services and uptime.
https://status.cloud.google.com/
With capabilities in place to track and maintain security measures and controls, the CSF and Google Cloud make it possible for organizations to gain meaningful insights into how security configurations affect organizational objectives and business outcomes. Under a shared responsibility model (discussed in Chapters 4 and 6), companies can offload security components to be enforced by Google on trusted, validated, and accredited cloud services infrastructure. Secure by design, Google Cloud implements built-in, layered security measures across a global network to protect user information, identities, applications, and devices. Leveraging the robust set of security products and services made available to customers, organizations can protect critical assets while meeting compliance requirements for any industry on Google Cloud.
The IBM Cloud
IBM Cloud is a set of cloud computing services for business offered by International Business Machines (IBM). The IBM Cloud includes IaaS, SaaS, and PaaS offered through public, private, and hybrid cloud delivery models.
IBM Cloud Pak for Security is an open security platform that connects to customers' existing data sources to generate deeper insights and enables customers to act faster with automation. Whether the data resides on IBM or third-party tools, on-premises, or multiple cloud environments, the platform helps customers to find and respond to threats and risks—all while leaving the data where it is. Therefore, the customers can uncover hidden threats, make informed risk-based decisions, and respond to incidents faster.
IBM Cloud Pak for Security provides a platform to quickly integrate with customers' existing security tools and generate deeper insights into threats across hybrid, multi-cloud environments. The Cloud Pak for Security platform uses an infrastructure-independent common operating environment that can be installed and run anywhere (Figure 8.2).
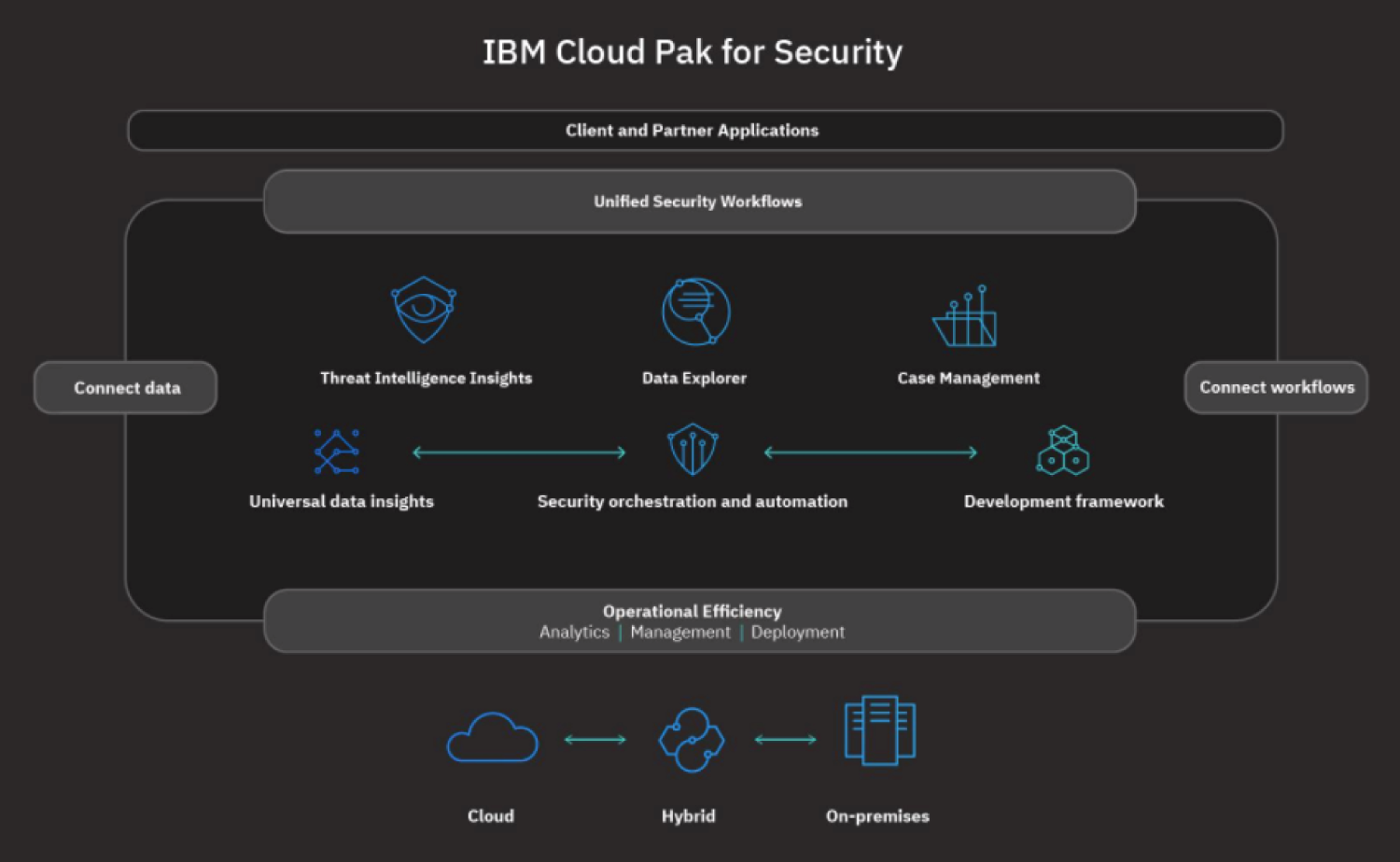
Figure 8.2: IBM Cloud Security
IBM Security Data Explorer for IBM Cloud Pak for Security enables federated investigations across IBM and third-party data sources. It connects insights from multiple security solutions, endpoint detection and response tools, and data stored in data lakes. It also gains insights from multi-cloud environments monitored by SIEM tools like Splunk and IBM QRadar.
IBM's QRadar Security Intelligence Platform is offered as an on-premises solution and delivers intelligent security analytics, enabling visibility, detection, and investigation for a wide range of known and unknown threats. Event analytics ingest, parse, normalize, correlate, and analyze log and event data to detect indicators of threats. Event analytics also identify anomalous activities, automatically connect related threat activity, and alert security teams to potential threats. Flow analytics collect, extract, and normalize valuable network flow data and packet metadata to augment log-based security insights. Flow analytics also identify network- and application-level threat activity, such as phishing, lateral movement, and data exfiltration.
IBM Security i2 helps cyberanalysts conduct cyber threat hunting by turning disparate datasets into comprehensive and actionable intelligence in near real-time. This cost-effective solution reduces training, maintenance, and deployment costs.
IBM Cloud Security Advisor is a security dashboard that provides centralized security management. The dashboard unifies vulnerability and network data as well as application and system findings from IBM services, partners, and user-defined sources.
By centralizing visibility and enabling drill down to resolution, Security Advisor empowers the security admin to cohesively manage security on IBM Cloud workloads.
With IBM Cloud Security and Compliance Center, you can embed security checks into your everyday workflows to help monitor for security and compliance. By monitoring for risks, you can identify security vulnerabilities and quickly work to mitigate the impact and fix the issue.
Oracle Cloud Infrastructure Security
Oracle, a platform provider of enterprise cloud computing, is empowering businesses of all sizes on their journey of digital transformation. Oracle Cloud provides leading-edge capabilities in SaaS, PaaS, IaaS, and DaaS (Data as a Service).
Oracle's security practices encompass how the company develops and manages enterprise systems, and cloud and on-premises products and services. Oracle's security-first approach with the following focus protects customers' valuable data in the cloud and on-premises:
- Reduce Risk: Strengthen security posture and reduce risk with security-first design principles that center on providing built-in security controls. These include isolated network virtualization in Oracle Cloud Infrastructure and strict separation of duties in Oracle Database.
- Automate Security: Automate security to reduce complexity, prevent human error, and lower cost with automated patching for Autonomous Database and threat mitigation for Oracle Cloud Infrastructure provided by the Cloud Access Security Broker (CASB) cloud service and Identity Cloud Service.
- Continuous Protection: Keep the customer business protected using always-on encryption and continuous monitoring of user behavior with Autonomous Database and Oracle Cloud Infrastructure, further mitigating risk with the CASB Cloud Service and Identity Cloud Service.
Oracle's public cloud delivers high customer isolation and automated protections with data residency, sovereignty, and cloud security at the core of its innovation and operations.
Oracle SaaS Cloud Security Threat Intelligence
The Oracle SaaS Cloud Security (SCS) organization has significantly advanced and matured its threat intelligence program to align with the rapid adoption and growth of cloud-based SaaS applications. At a high-level, the SCS organization has three sustaining threat intelligence goals:
- Accurately and consistently identify and assess threats against Oracle SaaS.
- Adjust the prioritization of security DevSecOps engineering activities and projects based on findings from the threat intelligence program.
- Collaborate and share feeds, analysis, and insights with other security lines of business inside Oracle.
Threat intelligence has a continuous lifecycle, just like DevSecOps, that adapts and improves over time, based on results (Figure 8.3).
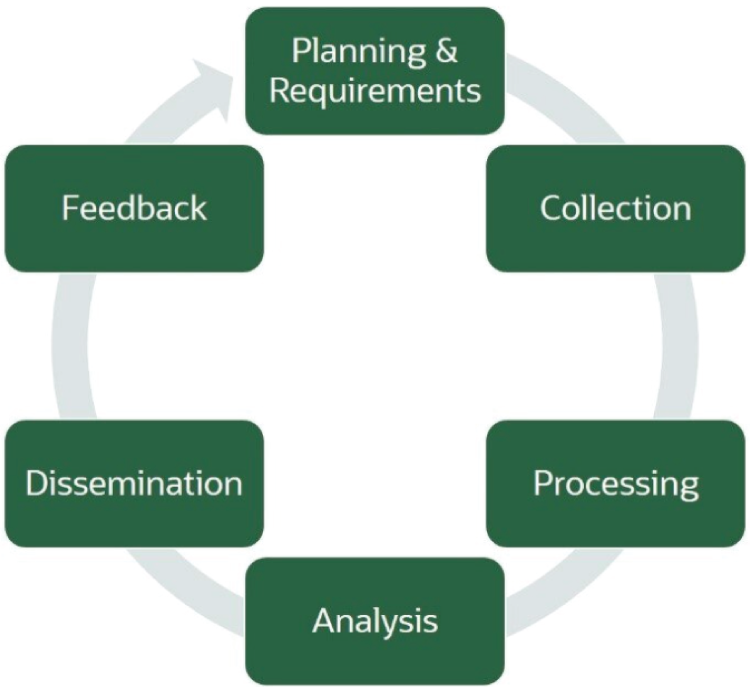
Figure 8.3: Oracle threat intelligence lifecycle
During the Analysis phase of the threat intelligence lifecycle, you can analyze the information and how a particular threat might potentially impact the customer environment. This analysis can include threat-hunting activities, which are the proactive search for signs of active or historical malicious activity in the infrastructure or applications. SCS uses both structured and unstructured threat-hunting approaches. Structured threat hunting determines what you want to look for and then detect if it is in place. Unstructured threat hunting is dependent on reviewing raw threat intelligence and signals to identify anomalies that may not have been detected in the past.
Oracle Cloud Guard is a unified security solution that provides a global and centralized approach to the protection of all the customers' assets. It works to analyze data, detect threats and misconfigurations automatically, then hunt down and kill those security threats without requiring human oversight. Oracle Cloud Guard continuously collects data from every part of the infrastructure and application stack, including audit logs, Oracle Data Safe, Oracle OS Management Service, as well as third-party products. Oracle Cloud Guard proactively detects and stops anomalous activity it identifies, shutting down a malicious instance automatically, and proactively revoking user permissions when it detects anomalous user behavior.
The Alibaba Cloud
The Alibaba Cloud is a multinational cloud computing company, a subsidiary of the Alibaba Group. Alibaba Cloud provides cloud computing services to online businesses and Alibaba's own e-commerce ecosystem.
Alibaba's Cloud Security Center is a unified security management system that identifies, analyzes, and alerts security threats in real time, helps organizations to achieve threat detection, response, traceability, automated security operations, protect assets and on-premises servers on the cloud, and meet regulatory compliance requirements through security capabilities such as anti-ransom, anti-virus, tamper-proof, mirror security scanning, and compliance checks.
Cloud Security Center helps you collect and present more than 10 types of logs and asset fingerprints on the cloud and expand security visibility with security posture analysis combined with network entity threat intelligence. Security Center integrates more than 250 threat detection models that are based on big data, six virus scan engines, seven webshell engines, and two threat detection engines for cloud services.
Security Center automatically collects various log data from your services on the cloud and implements control over found security threats. The threat detection and investigation and response capabilities include:
- Automated Alert Detection and Association: Automatically associates alerts and identifies intrusions caused by low-risk anomalies to improve operational efficiency.
- Custom Alerts: The real-time analysis and aggregation of third-party data on the cloud. It also supports custom alert rules.
- Security Overview: Security screen to show network security from multiple dimensions with various metrics.
- Automated Attack Traceability: Automatically traces the sources and causes of attacks. This helps you understand the ins and outs of intrusion threats and make quick responses.
- Log Analysis and Audit: Provides the capability to analyze logs for threat anomalies and confirm to regulatory compliance for each geolocation.
The cloud threat detection feature provided by Security Center is also integrated with major antivirus engines. The feature detects threats based on large amounts of threat intelligence data provided by Alibaba Cloud. The feature also provides an exception detection module designed by Alibaba Cloud that detects threats based on machine learning and deep learning. These capabilities of the cloud threat detection feature enable both full-scale and dynamic antivirus protection for your assets.
The next chapter explores the future of threat hunting and the challenges we face as defenders against technology advances.
Summary
- Other cloud service providers, such as Google, IBM, Oracle, and Alibaba, facilitate threat-hunting capabilities through their capability stack aligned to the MITRE ATT&CK Framework.
- Google Cloud Platform offers extensive threat prevention capability similar to Azure and AWS. GCP offers threat protection across all five pillars of the NIST Framework (i.e., Identify, Protect, Detect, Respond, and Recover).
- Oracle and Alibaba Cloud platforms offer capability across major threat vectors. These platform security offerings are still evolving compared to Azure, AWS, and GCP.
References
- NIST Cybersecurity Framework & Google Cloud (
https://services.google.com/fh/files/misc/gcp_nist_cybersecurity_framework.pdf) - IBM Cloud Pak for Security (
https://www.ibm.com/support/knowledgecenter/en/SSTDPP_1.4.0/platform/docs/scp-core/overview.html) - Cyber Threat Hunting | IBM (
https://www.ibm.com/security/cyber-threat-hunting) - How Threat Intelligence Complements Security Controls in Oracle SaaS Cloud | Oracle Cloud Security Blog (
https://blogs.oracle.com/cloudsecurity/how-threat-intelligence-complements-security-controls-in-oracle-saas-cloud) - Security Center: Comprehensive and Intelligent Security Management System - Alibaba Cloud (
https://www.alibabacloud.com/product/security-center?spm=a3c0i.11071746.3212395230.6.5cce5db9eI8pkT) - Cloud Security: Secures Your Business, Operations, Network & Applications - Alibaba Cloud (
https://www.alibabacloud.com/product/security?spm=a2c5t.10695662.1996646101.searchclickresult.22706cb6vU9hLw#J_3212395230) - Cloud threat detection - Threat Detection| Alibaba Cloud Documentation Center (
https://www.alibabacloud.com/help/doc-detail/89379.htm)
