Chapter 10
Securing Your Small Business
IN THIS CHAPTER
![]() Remaining cybersecure as a small business
Remaining cybersecure as a small business
![]() Dealing with employees
Dealing with employees
![]() Dealing with remote workforces
Dealing with remote workforces
![]() Understanding important regulations and standards
Understanding important regulations and standards
Nearly everything I discuss in this book applies to both individuals and businesses. Small business owners and workers should be aware of some points that may not necessarily be important for individuals. This chapter discusses some such cybersecurity issues.
One important note: Small businesses tend to frequently lack proper cybersecurity, and as a result, I could probably write an entire series of books about improving the cybersecurity of small businesses. As such, this chapter isn’t a comprehensive list of everything that every small business needs to know. Rather, it provides some cybersecurity “food for thought” for those running small businesses.
Making Sure Someone Is In Charge
Individuals at home are responsible for the security of their computers, but what happens when you have a network and multiple users? Somebody within the business needs to ultimately “own” responsibility for information security. That person may be you, the business owner, or someone else. But whoever is in charge must clearly understand that they are responsible.
In many small businesses, the person in charge of information security will outsource some of the day-to-day activities that are involved with performing the cybersecurity function. Even so, that person is ultimately responsible for ensuring that necessary activities, such as installing security patches, happen — and happen on time. If a breach occurs, “I thought so-and-so was taking care of that security function” is not a valid excuse that will carry a lot of weight — although, sadly, we hear people trying to use it on a regular basis.
Watching Out for Employees
Employees, and the many cybersecurity risks that they create, can become major headaches for small businesses. Human errors are the No. 1 catalyst for data breaches. Even if you’re reading this book and seeking to improve your cybersecurity knowledge and posture, your employees and coworkers may not have the same level of commitment as you do when it comes to protecting your data and systems.
As such, one of the most important things small business owners can do is to educate their employees. Education consists of essentially three necessary components:
- Awareness of threats: You must ensure that every employee working for the business understands that they, and the business as a whole, are targets. People who believe that criminals want to breach their computers, phones, and databases, or want to otherwise steal their data, act differently than people who have not internalized such realities. While formal, regular training is ideal, even a single, short conversation conducted when workers start, and refreshed with periodic reminders, can deliver significant value in this regard.
Basic information-security training: All employees should understand certain basics of information security. They should, for example, know to avoid cyber-risky behavior, such as opening attachments and clicking on links found in unexpected email messages, downloading music or videos from questionable sources, inappropriately using public Wi-Fi, or buying products from unknown stores with too-good-to-be-true prices and no publicly known physical address.
Numerous related training materials (often free) are available online. That said, never rely on training in itself to serve as the sole line of defense against any substantial human risk. Remember, we know with certainty that many people still do stupid things even after receiving clear training to the contrary. Furthermore, training does nothing to address rogue employees who intentionally sabotage information security.
- Practice: Information security training should not be theoretical. Employees should be given the opportunity to practice what they have learned — for example, by identifying and deleting/reporting a test phishing email.
Incentivize employees
Just as you should hold employees accountable for their actions if things go amiss, you should also reward employees for performing their jobs in a cyber-secure fashion and acting with proper cyberhygiene. Positive reinforcement can go a long way and is almost always better received than negative reinforcement.
Furthermore, many organizations have successfully implemented reporting systems that allow employees to anonymously notify the relevant powers within the business of suspicious insider activities that may indicate a threat, as well as potential bugs in systems, that could lead to vulnerabilities. Such programs are common among larger businesses, but can also be of benefit to small companies and other organizations.
Avoid giving out the keys to the castle
There are countless stories of employees making mistakes that open the organizational “door” to hackers. Likewise, there have been numerus cases of disgruntled employees stealing data and/or sabotaging systems. The damage from such incidents can be catastrophic to a small business. Protect yourself and your business from these types of risks by setting up your information infrastructure to contain the damage if something does go amiss.
Limiting access can make a world of difference in terms of the scope of a data leak if an employee goes rogue. Many businesses have learned this lesson the hard way. Don’t become one of them.
Give everyone separate credentials
Every employee accessing each and every system in use by the organization should have their own login credentials to that system. Do not share credentials!
Implementing such a scheme improves the ability to audit people’s activities (which may be necessary if a data breach or other cybersecurity event happens) and also encourages people to better protect their passwords because they know that if the account is misused, management will address the matter with them personally rather than with a team. The knowledge that employees are going to be held accountable for their behavior for maintaining or compromising security can work wonders in a proactive sense.
Likewise, every person should have their own multifactor authentication capabilities — whether that be a physical token, a code generated on their smartphone, and so on.
Restrict administrators
System administrators typically have superuser privileges — meaning that they may be able to access, read, delete, and modify other people’s data. It is essential, therefore, that if you — the business owner — are not the only superuser, that you implement controls to monitor what an administrator does. For example, you can log administrator actions on a separate machine that the administrator does not have access to.
Allowing access from only a specific machine in a specific location — which is sometimes not possible due to business needs — is another approach, as it allows a camera to be aimed toward that machine to record everything that the administrator does.
Limit access to corporate accounts
Your business itself may have several of its own accounts. For example, it may have social media accounts — a Facebook page, Instagram account, and a Twitter account — customer support, email accounts, phone accounts, and other utility accounts.
Basic control and audibility are simple to achieve when it comes to Facebook Pages, for example, as you can own the Facebook Page for the business, while providing other people the ability to write to the page. In some other environments, however, granular controls aren’t available and you will need to decide between providing multiple people logins to a social media account or having them submit content to a single person (perhaps, even you) who makes the relevant posts.
The challenge of providing every authorized user of corporate social media accounts with their own account to achieve both control and audibility is exacerbated by the fact that all sensitive accounts should be protected with multifactor authentication. (See Chapter 7 for more on multifactor authentication.)
Some systems offer multifactor authentication capabilities that account for the fact that multiple independent users may need to be given auditable access to a single account. In some cases, however, systems that offer multifactor authentication capabilities do not blend well with multi-person environments. They may, for example, allow for only one cellphone number to which one-time passwords are sent via SMS. In such scenarios, you will need to decide whether to
- Use the multifactor authentication, but with a work-around. For example, by using a VOIP number to receive the texts and configuring the VOIP number to forward the messages on to multiple parties via email (as is offered at no cost, for example, by Google Voice).
- Use the multifactor authentication with no work-around. Configure the authorized users’ devices not to need multifactor authentication for the activities that they perform.
- Use a form of multifactor authentication that does not need a work-around. For example, one that allows multiple users to independently authenticate using different credentials and multifactor logins, and subsequently receive permission to act on the same account.
- Use a form of multifactor authentication that does not need a work-around, but does not multifactor separately for different users. For example, allowing users to use separate initial authentication credentials, but use shared multifactor credentials such as by giving them a one-time code generator configured with the same seed (that is, configured to produce exactly the same one-time codes at exactly the same times).
- Not use the multifactor authentication, but instead rely solely on strong passwords. This solution is not recommended.
- Find another work-around by modifying your processes, procedures, or technologies used to access such systems.
- Utilize third-party products that overlay systems. This is often the best option when available.
While larger enterprises almost always follow some variant of the last approach — both for management and security reasons — many small businesses tend to take the easy way out and simply not use strong, multifactor authentication in such cases. The cost of implementing proper security — both in terms of dollars and time — is usually quite low, so exploring third-party products should definitely be done before deciding to take another approach.
Implement employee policies
Businesses of all sizes that have employees need an employee handbook that includes specific rules regarding employee usage of business technology systems and data. It is beyond the scope of this book to cover all elements of employee handbooks, but the following are examples of rules that businesses can implement to govern the use of company technology resources:
- Company’s employees are expected to use technology responsibly, appropriately, and productively, as necessary to perform their professional responsibilities.
- The use of company devices, as well as company Internet access and email, as provided to employees by the company, are for job-related activities. Minimal personal use is acceptable provided that the employees using it as such does not violate any other rules described in this document and does not interfere with their work.
- Employees are responsible for any computer hardware and software provided by the company, including for the safeguarding of such items from theft, loss, or damage.
- Employees are responsible for their accounts provided by the company, including the safeguarding of access to the accounts.
- Employees are strictly prohibited from sharing any company-provided items used for authentication (passwords, hardware authentication devices, PINs, and so on) and are responsible for safeguarding such items.
- Employees are strictly prohibited from connecting any networking devices, such as routers, access points, range extenders, and so on, to company networks unless explicitly authorized to do so by the company’s CEO. Likewise, employees are strictly prohibited from connecting any personal computers or electronic devices — including any Internet of Things (IoT) devices — to company networks other than to the Guest network, under the conditions stated explicitly in the Bring Your Own Device (BYOD) policy.
- Employees are responsible to make sure that security software is running on all company-provided devices. Company will provide such software, but it is beyond company’s ability to check that such systems are always functioning as expected. Employees may not deactivate or otherwise cripple such security systems, and must promptly notify company’s IT department if they suspect that any portion of the security systems may be compromised, nonfunctioning, or malfunctioning.
- Employees are responsible to make sure that security software is kept up to date. All company-issued devices come equipped with Auto-Update enabled; employees must not disable this feature.
- Likewise, employees are responsible for keeping their devices up to date with the latest operating system, driver, and application patches when vendors issue such patches. All company-issued devices come equipped with Auto-Update enabled; employees must not disable this feature.
- Performing any illegal activity — whether or not the act involved is a felony, a misdemeanor, or a violation of civil law — is strictly prohibited. This rule applies to federal law, state law, and local law in any area and at any time in which the employee is subject to such laws.
- Copyrighted materials belonging to any party other than the company or employee may not be stored or transmitted by the employee on company equipment without explicit written permission of the copyright holder. Material that the company has licensed may be transmitted as permitted by the relevant licenses.
- Sending mass unsolicited emails (spamming) is prohibited.
- The use of company resources to perform any task that is inconsistent with company’s mission — even if such task is not technically illegal — is prohibited. This includes, but is not limited to, the accessing or transmitting sexually explicit material, vulgarities, hate speech, defamatory materials, discriminatory materials, images or description of violence, threats, cyberbullying, hacking-related material, stolen material, and so on.
- The previous rule shall not apply to employees whose job entails working with such material, only to the extent that is reasonably needed for them to perform the duties of their jobs. For example, personnel responsible for configuring the company’s email filter may, without violating the preceding rule, email one another about adding to the filter configuration various terms related to hate speech and vulgarities.
- No company devices equipped with Wi-Fi or cellular communication capabilities may be turned on in China or Russia without explicit written permission from the company’s CEO. Loaner devices will be made available for employees making trips to those regions. Any personal device turned on in those regions may not be connected to the Guest network (or any other company network).
- All use of public Wi-Fi with corporate devices must comply with the company’s Public Wi-Fi policies. Ideally, companies should ban such use except in rare, specific types of cases.
- Employees must backup their computers by using the company’s backup system as discussed in the company’s backup policy.
- Employees may not copy or otherwise back up data from company devices to their personal computers, storage devices, or cloud-based repositories such as DropBox, Google Drive, Box, or any other such services.
- Any and all passwords for any and all systems used as part of an employees’ job must be unique and not reused on any other systems. All such passwords must consist of three or more words, at least one of which is not found in the English dictionary, joined together with numbers or special characters or meet all the following conditions:
- Contain eight characters or more with at least one uppercase character
- Contain at least one lowercase character
- Contain at least one number
- Not contain any words that can be found in an English dictionary
- Names of relatives, friends, or colleagues may not be used as part of any password
- Data may be taken out of the office for business purposes only and must be encrypted prior to removal. This rule applies whether the data is on hard drive, SSD, CD/DVD, USB drive, or on any other media or is transmitted over the Internet. It may not be taken out of the office by copying to employee cloud-storage accounts (such as Google Drive or Dropbox). Any and all data taken out of the business’s infrastructure or infrastructure contracted for use by the business must be returned to the business (or at the company’s sole discretion, destroyed) immediately after its remote use is complete or upon employee’s termination of employment, whichever is sooner.
- In the event of a breach or other cybersecurity event or of any natural or man-made disaster, no employees other than the company’s officially designated spokesperson may speak to the media on behalf of the company.
- No devices from any manufacturer that the FBI, the FCC, or other United States federal agencies have warned that they believe are potentially unsafe and/or that foreign governments are using to spy on Americans may be connected to any company network (including the guest network) or brought into the physical offices of the company. Nor should company data ever be stored or processed on such devices.
Enforce social media policies
Devising, implementing, and enforcing social media policies is important because inappropriate social media posts made by your employees (or yourself) can inflict all sorts of damage. They can leak sensitive information, violate compliance rules, and assist criminals to social engineer and attack your organization, expose your business to boycotts and/or lawsuits, and so on.
Monitor employees
Regardless of whether or not they plan to actually monitor employees’ usage of technology, companies should inform users that they have a right to do so. If an employee were to go rogue and steal data, for example, you do not want to have the admissibility of evidence challenged on the grounds that you had no right to monitor the employee. Furthermore, telling employees that they may be monitored reduces the likelihood of employees doing things that they are not supposed to do because they know that they may be monitored while doing such things. Of course, monitoring should be done only on employer-issued devices and networks. (This is discussed in more detail in the section on remote work that follows.)
Here is an example of text that you can provide to employees as part of an employee handbook or the like when they begin work:
- Company, at its sole discretion, and without any further notice to employee, reserves the right to monitor, examine, review, record, collect, store, copy, transmit to others, and control any and all email and other electronic communications, files, and any and all other content, network activity including Internet use, transmitted by or through its technology systems or stored in its technology systems or systems, whether onsite or offsite. Such systems shall include systems that it owns and operates and systems that it leases, licenses, or to which it otherwise has any usage rights.
- Furthermore, whether sent to an internal party, external party, or both, any and all email, text and/or other instant messages, voicemail, and/or any and all other electronic communications are considered to be Company’s business records, and may be subject to discovery in the event of litigation and/or to disclosure based on warrants served upon company or requests from regulators and other parties.
Dealing with a Remote Workforce
While the concept of working remotely is not new, the number of people who actually work from home has skyrocketed since early 2020 when the novel coronavirus began to spread like wildfire throughout the world. The resulting COVID-19 pandemic has become, by far, the leading motivator for change vis-à-vis remote working. It quickly transformed the world from one in which nearly all people worked at locations chosen and administered by their employers, to one in which a significant percentage of the population worked solely from home. Even as people return to workplaces after the pandemic, many are still telecommuting from home some of the time.
While working remotely during a global pandemic may help people remain safe from invisible microscopic attackers, and may even offer various productivity and financial benefits to employers, the fact that remote workers must access important data and systems from geographically scattered environments not managed by their employers creates all sorts of cybersecurity concerns. Entire books could be written on such a topic — and probably will be. But for those who wish to learn what cybersecurity safeguards they can take while working from home, the following overview of some important ideas may prove useful.
Use work devices and separate work networks
If employees connect to employer networks, access employer systems, or work with employer data with their own personal devices, employers run serious risks of malware infections, data being stored in insecure locations, data being pilfered by nefarious parties, and all sorts of other cybersecurity nightmares. As such, if possible, all remote work should be done on computers and other types of computing devices that are owned by, managed by, and issued to employees by the employer.
Ideally, access to employer systems should also be conducted using Internet connections and networking equipment paid for and managed by the employer. And no personal devices should be connected. Employers might want to have the ability to remotely access such devices to monitor and/or wipe such devices in case they are lost or stolen. In many cases, however, such arrangements are either impractical or impossible, and as such, various other types of precautions should be taken.
If employees will be using their own Internet connections, for example, it is ideal that employers provide a network router to employees so that employees can connect that router to their home network routers, and thereby isolate the employer’s equipment and data from the main network segment at home and all of its traffic.
Set up virtual private networks
A virtual private network (VPN) provides remote workers with several significant benefits. It can prevent unauthorized parties from sharing any Internet connection back to the employer’s network, and can prevent other parties connected to the same local network, as well as the Internet service provider for that connection, from seeing the contents of the VPN user’s transmissions.
As such, a VPN from the separate network router to a special corporate remote-worker network (for those familiar with the term, this network would likely be a form of demilitarized zone [DMZ] — not fully trusted by the company, but yet not open to the public) may also ideal, especially if the user needs to use multiple corporate devices from the remote location, or in situations in which multiple employees may be working at that location. When network-to-network VPNs are not possible — or when only one user is using only one device — a connection directly from the user’s remote corporate device may be appropriate.
In some cases, either type of VPN connection may actually be dangerous from a cybersecurity perspective, such as if an employer does not have the expertise or the capability to properly implement and supervise such a VPN. Even when no VPN is used, however, isolating work devices from any personal devices through the use of a separate network at the remote location (as described earlier) is ideal.
Of course, you can also subscribe to consumer-type VPN services, but these services are less ideal because these services do not connect the remote worker to the employer’s infrastructure via a “secure tunnel” (think of a secured-by-encryption communication pathway over the insecure Internet); rather, they connect the employee to the VPN provider’s systems over a secure tunnel and then communicate from the VPN provider’s infrastructure to others on the Internet using potentially insecure transmissions.
Create standardized communication protocols
As discussed in Chapter 6, ideally, an organization should create standardized policies, procedures, and technologies for any video calls or chatting, and security should weigh heavily as a factor when such decisions are made. Relevant policies should include configuration requirements, such as requiring that all video calls require a password in order for someone to gain access, that virtual “waiting rooms” be utilized to prevent anyone from attending a meeting until admitted by the host, and that only users properly authenticated and signed into the communication platform be admitted into any non-public meetings.
Use a known network
When working from home, make sure that any network to which you connect wirelessly is using encryption and a strong Wi-Fi key (WPA2 or better). The reason for such advice is not only to ensure that communications cannot be monitored between your devices and the Wi-Fi access point or router, but also to ensure that you are connecting to the correct access point or router in the first place.
Hackers can set up “evil twin networks” with the same name as your network, for example, and if you receive a better signal from the evil twin access point, your device may connect to it rather than the intended, legitimate access point. Utilizing Wi-Fi security reduces the likelihood of such a problematic connection occurring, as the hacker is unlikely to have established the same encryption key. (And if somehow an attacker has your key, you have bigger problems than just this connection.)
Determine how backups are handled
Make sure you have a plan in place — and properly implemented — for how remote workers’ systems and data will be backed up. Backups should be performed, managed, and administered by the employer. Do not rely on employees to back up employer data. If for some reason, despite all of the information provided earlier in this chapter, you find yourself in a situation in which employees are using personal devices for working remotely, be absolutely sure as their employer not to back up any personal contents of such devices.
Be careful where you work remotely
Keep in mind that working from home is likely to be less secure than working at a normal professional work location, not only for technical reasons, but also due to the people often present in the respective areas. Simply put, besides technical issues, as discussed elsewhere in this book, working remotely creates major concerns about “shoulder surfing.” Ideally, therefore, remote employees should be working strictly from home and other locations with strongly controlled human access, and not from coffee shops, airports, libraries, public parks, sidewalks, and/or restaurants.
Also, it should be noted that with workers situated in the safety of their homes, unauthorized outsiders are far more unlikely to see what appears on the display of the employee’s computer or hear sensitive information conveyed by the employee during voice-based phone calls, many organizations are rightfully still uncomfortable with their employees’ children or significant others knowing all sorts of information that remote workers may handle and expose during work-at-home sessions.
In addition, privacy screens for laptops can reduce the likelihood of anyone being able to read what appears on the display. Such screens allow displayed contents to be seen clearly when someone looks directly at them, but not when someone looks from the side.
Be extra vigilant regarding social engineering
Would-be cyberattackers know that remote workers make good targets not only because of the technical cybersecurity limitations present at the vast majority of home-office sites, but because of human weaknesses as well.
Unlike their in-office counterparts, for example, people working remotely cannot simply walk down the hall and ask someone about a particular request allegedly made by that person and received in a chat message or email. Remote workers are also more likely than in-office workers to deviate from normal business hours for their work schedules. And, such workers rarely benefit as much as do their in-office counterparts, from robust technology suites implemented to protect people from phishing and other social engineering attacks.
For those reasons as well as others, remote workers are believed by many to be more likely to be successfully social engineered by criminals than are otherwise similar people working in professional offices. Remote workers are more likely to open problematic emails, click on dangerous links, and/or otherwise inadvertently take action based on the request of a criminal. Think for a moment how likely you would be — if you were working remotely — to open a spear-phishing email made to look like it was sent by your boss with the subject, “Important Updates to Corporate Remote Working Policy.”
As such, remote workers must be especially vigilant against social engineering attacks. To learn more about such attacks and how to defend against them, see Chapter 9.
Considering Cybersecurity Insurance
While cybersecurity insurance may be overkill for most small businesses, if you believe that your business could suffer a catastrophic loss or even fail altogether if it were to be breached, you may want to consider buying insurance. If you do pursue this route, keep in mind that nearly all cybersecurity insurance policies have carve outs, or exclusions — so make sure that you understand exactly what is covered and what is not and for what amount of damage you are actually covered. If your business fails because you were breached, a policy that pays only to have an expert spend two hours restoring your data is not going to be worth much.
In fact, to the contrary, insurers normally require that a business meet a certain standard of cybersecurity to purchase and maintain coverage. In some cases, the insurer may even refuse to pay a claim if it finds that the insured party was breached at least in part due to negligence on the insured’s part or due to the failure of the breached party to adhere to certain standards or practices mandated by the relevant insurance policy.
Complying with Regulations and Compliance
Businesses may be bound by various laws, contractual obligations, and industry standards when it comes to cybersecurity. Your local Small Business Administration office may be able to provide you with guidance as to what regulations potentially impact you. Remember, though, that there is no substitute for hiring a properly trained lawyer experienced with this area of law to provide professional advice optimized for your particular situation.
The following sections provide examples of several such regulations, standards, and so on that often impact small businesses.
Protecting employee data
You’re responsible for protecting sensitive information about your employees. If you don’t properly protect this information, you could end up in hot water with government regulators, with your employees, or in the eyes of the public.
For physical files, you should, in general, protect records with at least double-locking — storing the paper files in a locked cabinet within a locked room (and not using the same key for both). For electronic files, the files should be stored encrypted within a password-protected folder, drive, or virtual drive. Such standards, however, may not be adequate in every particular situation, which is why you should check with an attorney.
Remember, employee personnel records, W2 forms, Social Security numbers, I9 employment eligibility forms, home addresses and phone numbers, medical information including COVID-19 test results and/or vaccination records and any other health-related information that you may maintain, vacation records, family leave records, and so on are all potentially considered private.
PCI DSS
Payment Card Industry Data Security Standard (PCI DSS) is an information security standard for organizations that handle major credit cards and their associated information. The standard has been updated and expanded multiple times; the most current version is Version 3.2.1, published in May 2018.
While all companies of all sizes that are subject to the PCI DSS standard must be compliant with it, PCI does take into effect the different levels of resources available to different sized businesses. PCI Compliance has effectively four different levels. To what level an organization must comply is normally based primarily on how many credit card transactions it processes per year. Other factors, such as how risky the payments are that the company receives, also weigh in. The different levels are
- PCI Level 4: Standards for businesses that process fewer than 20,000 credit card transactions per year
- PCI Level 3: Standards for businesses that process between 20,000 and 1,000,000 credit card transactions per year
- PCI Level 2: Standards for businesses that process between 1,000,000 and 6,000,000 credit card transactions per year
- PCI Level 1: Standards for businesses that process more than 6,000,000 credit card transactions per year
Exploring PCI in detail is beyond the scope of this book. Entire books have been written on the topic, and various organizations offer classes dedicated to the topic. If you operate a small business and process credit card payments or store credit card data for any other reason, be sure to engage someone knowledgeable in PCI to help guide you. In many cases, your credit card processors will be able to recommend a proper consultant or guide you themselves.
Breach disclosure laws
In recent years, various jurisdictions have enacted so-called breach disclosure laws, which require businesses to disclose to the public if they suspect that a breach may have endangered certain types of stored information. Breach disclosure laws vary quite a bit from jurisdiction to jurisdiction, but in some cases, they may apply even to the smallest of businesses.
The laws that apply to your business may include not only those of the jurisdiction within which you’re physically located but the jurisdictions of the people you’re handling information for.
GDPR
The General Data Protection Regulation (GDPR) is a European privacy regulation that went into effect in 2018 and applies to all businesses handling the consumer data of residents of the European Union, no matter the size, industry, or country of origin of the business and no matter whether the EU resident is physically located within the EU. It provides for stiff fines for businesses that do not properly protect private information belonging to EU residents. This regulation means that a small business in New York that sells an item to an EU resident located in New York may be subject to GDPR for information about the purchaser and, can, in theory, face stiff penalties if it fails to properly protect that person’s data. For example, in July 2019, the United Kingdom’s Information Commissioner’s Office (ICO) announced that it intended to fine British Airways about $230 million and Marriott about $123 million for GDPR-related violations stemming from data breaches.
GDPR is complex. If you think that your business may be subject to GDPR, speak with an attorney who handles such matters.
HIPAA
Federal law throughout the United States of America requires parties that house healthcare-related information to protect it in order to maintain the privacy of the individuals whose medical information appears in the data. The Health Insurance Portability and Accountability Act (HIPAA), which went into effect in 1996, provides for stiff penalties for improperly defending such information. Be sure to learn whether HIPAA applies to your business and, if so, ensure that you are properly protecting the data to which it applies according to industry standards or better. Many other jurisdictions around the world have regulations similar in concept to HIPAA.
Biometric data
If you utilize any forms of biometric authentication or for any other reason store biometric data, you may be subject to various privacy and security laws governing that data. Multiple states have already enacted laws in this regard, and others are likely to follow.
Anti-money laundering laws
Anti-money laundering laws seek to make it difficult for criminals to convert illegally obtained money into money that appears to have been legally obtained. While many anti-money laundering laws are applicable primarily to financial institutions, anyone utilizing cryptocurrency for performing transactions with unknown parties should be sure that their actions do not violate these laws.
International sanctions
Paying ransomware ransoms can sometimes in itself be a crime, especially in situations in which the criminals receiving the payments are under sanctions (meaning it is a federal crime to conduct any financial transactions with them). While, to date, people who have paid ransoms have not been prosecuted by the U.S. government for violating such laws, there are indications that tolerance for such violations may be waning.
Handling Internet Access
Small businesses face significant challenges related to Internet access and information systems that individuals rarely must think about, and must take various actions to prevent the emergence of various dangers. The following sections cover a few examples.
Segregate Internet access for personal devices
If you provide Internet access for visitors to your place of business, and/or for your employees to use with their personal smartphones and tablets while at work, implement this Internet access on a separate network from the network(s) used to run your business. Most modern routers offer such a capability, which is usually found somewhere in the configuration with a name like Guest network. (Likewise, as mentioned earlier in this chapter, remote home-based workers should be keeping their work and personal networks separate.)
Create bring your own device (BYOD) policies
If you allow employees to perform business activities on their own personal laptops or mobile devices, you need to create policies regarding such activity and implement technology to protect your data in such an environment.
In general, small businesses should not allow bring your own device (BYOD) — even if doing so is tempting. In the vast majority of cases when small businesses do allow employees to use their own devices for work-related activities, data remains improperly protected, and problems develop if an employee leaves the organization (especially if the employee leaves under less than optimal circumstances).
If you do allow BYOD, be sure to set proper policies and procedures — both for usage and for decommissioning any company technology on such devices, as well as for removing any company data when an employee leaves. Develop a full mobile device security plan that includes remote wipe capabilities, enforces protection of passwords and other sensitive data, processes work-related data in an isolated area of the device that other apps can’t access (a process known as sandboxing), installs, runs, and updates mobile-optimized security software, prohibits staff from using public Wi-Fi for sensitive work-related tasks, prohibits certain activities from the devices while corporate data is on them, and so on.
Properly handle inbound access
One of the biggest differences between individuals and businesses using the Internet is often the need of the business to provide inbound access for untrusted parties. Unknown parties must be able to initiate communications that result in communications with internal servers within your business.
For example, if a business offers products for sale online, it must allow untrusted parties to access its website to make purchases (see Figure 10-1). Those parties connect to the website, which must connect to payment systems and internal order tracking systems, even though they are untrusted. (Individuals typically do not have to allow any such inbound access to their computers.)
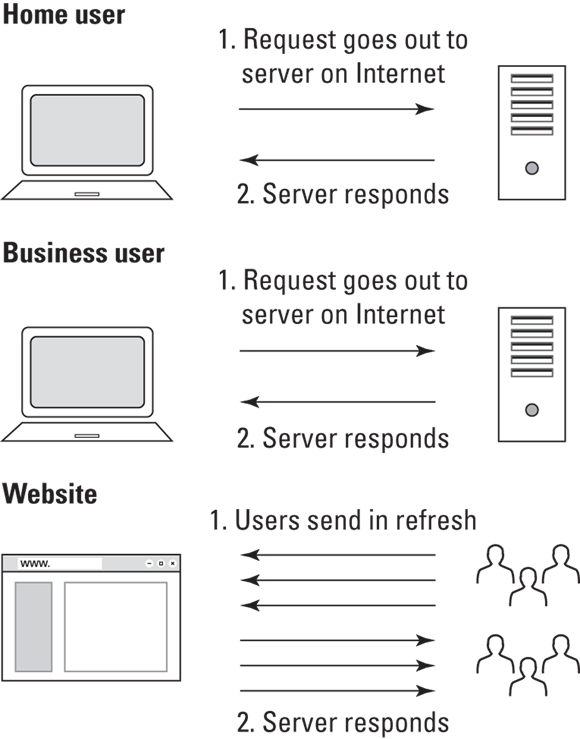
FIGURE 10-1: Inbound access is one major difference between businesses and individuals.
While small businesses can theoretically properly secure web servers, email servers, and so on, the reality is that few, if any, small businesses have the resources to adequately do so, unless they’re in the cybersecurity business to begin with. As such, it is wise for small businesses to consider using third-party software and infrastructure, set up by an expert, and managed by experts, to host any systems used for inbound access. To do so, a business may assume any one or more of several approaches:
- Utilize a major retailer’s website. If you’re selling items online, and sell only through the websites of major retailers, such as Amazon, Rakuten, and/or eBay, those sites serve as a major buffer between your business’s systems and the outside world. The security armies at those companies defend their customer-facing systems from attacks. In many cases, such systems don’t require small businesses to receive inbound communications, and when they do, the communications emanate from those retailers’ systems, not from the public. Of course, many factors go into deciding whether to sell via a major retailer — online markets do take hefty commissions, for example. When you weigh the factors in making such a decision, keep the security advantages in mind.
- Utilize a third-party hosted retail platform. In such a case, the third party manages most of the infrastructure and security for you, but you customize and manage the actual online store. Such a model does not offer quite the same level of isolation from outside users as does the preceding model, but it does offer much greater buffering against attacks than if you operate your own platform by yourself. Shopify is an example of a popular third-party platform.
- Operate your own platform, hosted by a third party that is also responsible for security. This approach offers better protection than managing the security yourself, but it does not isolate your code from outsiders trying to find vulnerabilities and attack. It also places responsibility for the upkeep and security of the platform on you.
- Operate your own system hosted either internally or externally and use a managed services provider to manage your security. In such a case, you’re fully responsible for the security of the platform and infrastructure, but you’re outsourcing much of the actual work required to satisfy that responsibility to a third party.
Other models and many variants of the models I list exist as well.
While the models may step from easier to secure to harder to secure, they also step from less customizable to more customizable. In addition, while the earlier models may cost less for smaller businesses, the expense of the earlier models typically grows much faster than do the later ones as a business grows.
Protect against denial-of-service attacks
If you operate any Internet-facing sites as part of your business, make sure that you have security technology implemented to protect against denial-of-service (DoS) attacks. If you’re selling via retailers, they likely have it already. If you’re using a third-party cloud platform, the provider may supply it as well. If you’re running the site on your own, you should obtain protection to ensure that someone can’t easily take your site — and your business — offline. Various companies specialize in providing such protection.
Use https
If your business operates a website, be sure to install a valid TLS/SSL certificate so that users can communicate with it over a secure connection and know that the site actually belongs to your business.
Use a VPN
As is discussed earlier in this chapter regarding home-based workers, if you intend to provide employees remote access to corporate systems, consider using a virtual private network (VPN) and multifactor authentication. In the case of remote access, the VPN should create an encrypted tunnel between your remote users and your business, not between users and a VPN provider. The tunnel both protects against people snooping on the communications between remote users and the business and also allows remote users to function as if they were in the company’s offices, and utilize various business resources available only to insiders. Multifactor authentication is discussed in detail in Chapter 7. Of course, if you use third-party, cloud-based systems, the relevant providers should already have security capabilities deployed that you can leverage — do so.
Run penetration tests
Individuals rarely run tests to see whether hackers can penetrate into their systems, and neither do most small businesses. Doing so, however, can be valuable — especially if you are deploying a new system of some sort or upgrading network infrastructure. See Chapter 17 for more on penetration testing.
Be careful with IoT devices
Many businesses today utilize connected cameras, alarms, and so on. Be sure that someone is responsible for overseeing the security of these devices, which should be run on separate networks (or virtual segments) than any computers used to operate the business. Control access to these devices and do not allow employees to connect any unauthorized IoT devices to the business’s networks. Ideally, purchase IoT devices only if they are made by a respectable manufacturer. Don’t, for example, seek to get the least expensive connected cameras available online regardless of who made them and where they were made. For more on IoT devices, see Chapter 18.
Use multiple network segments
Depending on the size and nature of your business, isolating various computers onto different network segments may be wise. A software development company, for example, should not have developers coding on the same network that the operations folks use to manage payroll and accounts payable. (As is discussed earlier in this chapter, the same holds true for remote home-based workers. Their personal and work networks should be separated.)
Be careful with payment cards
If you accept credit and/or debit cards — and are not selling via a major retailer’s website — make sure to speak with your processor about various anti-fraud technology options that may be available to you. And make sure you comply with PCI DSS as discussed earlier in this chapter.
Managing Power Issues
Use an uninterruptable power supply (UPS) on all systems that you can’t afford to have go down even momentarily. Do not overload UPSs — make sure they can handle the total load needed for all of the devices plugged into them. Also, make sure the power supplies can keep the systems up and running for longer than any expected outage. If you’re selling various goods and services via online retail, for example, you may lose current sales and future sales, as well as suffer reputational harm, if your ability to sell goes offline even for a short period of time.

 Confusion as to who within an organization is responsible for cybersecurity often leads to major cybersecurity headaches.
Confusion as to who within an organization is responsible for cybersecurity often leads to major cybersecurity headaches. How can you do this? Give workers access to all the computer systems and data that they need in order to do their jobs with maximum performance, but do not give them access to anything else of a sensitive nature. Programmers shouldn’t be able to access a business’s payroll system, for example, and a comptroller doesn’t need access to the version control system housing the source code of a company’s proprietary software.
How can you do this? Give workers access to all the computer systems and data that they need in order to do their jobs with maximum performance, but do not give them access to anything else of a sensitive nature. Programmers shouldn’t be able to access a business’s payroll system, for example, and a comptroller doesn’t need access to the version control system housing the source code of a company’s proprietary software. Of course, never, ever, attempt to monitor an employees’ actions on their personal devices.
Of course, never, ever, attempt to monitor an employees’ actions on their personal devices.