CHAPTER 8
Emergent Trends and Non-Wi-Fi Wireless
This chapter wraps up our content with a focus on some of the more fluid and transient aspects of wireless security.
Up until this point, the guidance and information in the book should persist for several years, with a few slight adjustments and evolutions here and there. Moving forward through this chapter, however, the content is less evergreen by design.
Instead of omitting emerging technologies that prove significant in wireless security, those topics that are more volatile are aggregated here, and presented with the caveat in large, flashing letters that everything you read moving forward is subject to change throughout the life of this book. Consider it a launching point for further investigation to update your knowledge.
This chapter's content is distilled down to two broad topic areas:
- Emergent Trends Impacting Wireless
- Enterprise IoT Technologies and Non-802.11 Wireless
This chapter concludes with final thoughts and key takeaways from throughout the book.
Emergent Trends Impacting Wireless
With so many connected devices, the explosive growth of IoT, and a cadre of digital transformation initiatives across all industries, just about every trend these days impacts wireless, and therefore security.
We're going to tackle a handful of the most pressing issues and the topics that address the most-asked questions by networking, wireless, and security professionals, including:
- Cloud-Managed Edge Architectures
- Remote Workforce
- Bring Your Own Device
- Zero Trust Strategies
- Internet of Things (IoT)
Cloud-Managed Edge Architectures
Over the last few years, the networking industry has begun its journey toward a converged edge architecture, and that journey is taking most of us to the cloud. Firewalls and gateways, SD-WAN appliances, and switches are being managed alongside Wi-Fi devices—and mostly in the cloud.
The trend is apparent when you look at Aruba Network's Central cloud, Juniper's Mist AI, ExtremeCloud IQ, and Fortinet's FortiLAN Cloud. These enterprise solutions followed suit after products like Meraki paved the way, proving the benefits of the cloud and ease of management in the SMB market.
The converged and converging edge and the move to cloud management brings a few considerations for security architecture and network operations in general, including:
- Modified privileged access management
- Use of APIs in favor of traditional network management
- Requirement of new skills
- Tighter vendor vetting, privacy, and security certifications
First, as soon as our entire network stack is accessible from the Internet, we have to rethink secure management access. For a refresher, visit Chapter 6, “Hardening the Wireless Infrastructure,” and find the topic of “Addressing Privileged Access.” The first thing I have clients do with cloud-managed platforms is enable 2FA. When the entire Internet becomes your management network, the architecture must change accordingly.
The next seemingly innocent shift is toward API-managed edge networks. With companies like Juniper moving away from SNMP and even CLI in favor of API-based management of APs and switches, tides are turning, and traditional networking tools and processes will likewise shift.
These two trends alone are early warning signs that network architects and administrators will need to retool themselves along with the network.
Lastly, managing devices in and from the cloud does present new security risks. Even if the vendor isn't collecting client traffic, the platform has metadata, user and endpoint location info, personal information including email addresses and usernames, RADIUS shared secrets, entire IP schemas—and all of that is in the cloud. For most organizations, that's okay if the vendor has properly secured their own environment. When you engage with a cloud provider in any way, the organization is effectively extending its trust boundary to include the provider.
Governmental requirements in many countries have driven vendors toward certain security practices and certifications, and the rest of enterprises should follow suit by better vetting vendors and demanding proof of ISO 27001-certified datacenters and SOC-2 compliance at a minimum.
Remote Workforce
The sudden work-from-anywhere model hit the world without warning in 2020, leaving companies still trying to adjust and address security gaps throughout 2021 and beyond.
In the U.S., several reports show we went from less than 5 percent of employees working from home three days a week or more to over 50 percent in 2021. Gartner reports similar spikes using slightly different criteria in its research. Figure 8.1 shows trending predictions of remote work by country from 2019 through 2025.
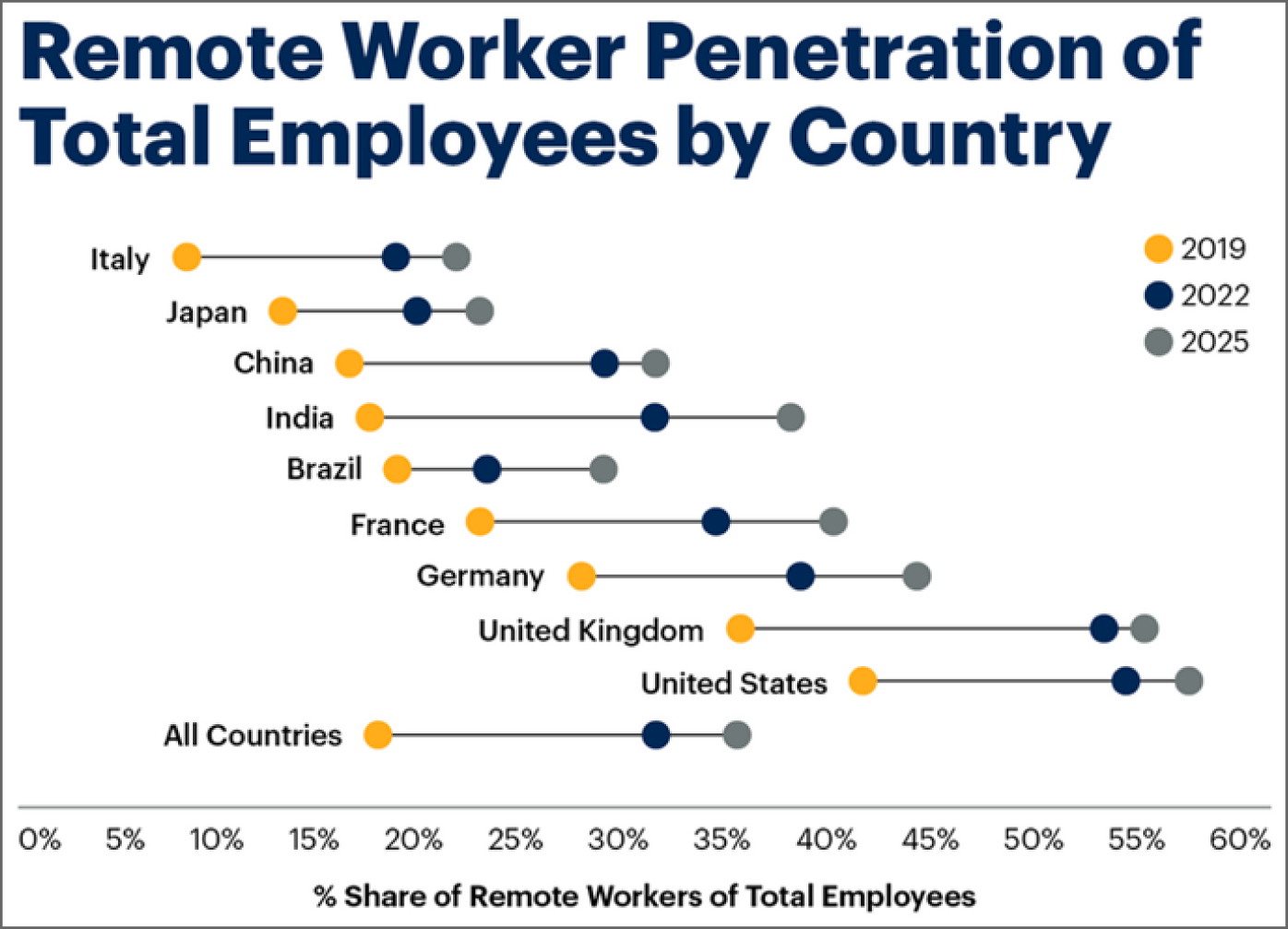
Figure 8.1: Gartner's predictive analysis shows a continued increase in remote workers across the world.
From a wireless and security architecture perspective, the impacts on our work have included:
- Addition of remote APs for home users
- Support for remote and home workers' devices
- Increase in use of personal devices
- Additional projects while offices are mostly unpopulated
- Talent shortage and staffing issues
- Architecture changes to support migrating applications and services to the cloud
- Changes in processes to accommodate zero touch and remote provisioning of infrastructure and endpoints
- Requirements for network admins' remote management access to systems
Challenges Supporting Work from Home and Remote Users
Supporting enterprise products in residential settings is challenging—the IT team has no control over the home user's Internet speed or quality; no visibility into the connectivity and physical location of devices; and APs in the home require power injectors and other accessories, along with cables.
In fact, Microsoft's report “The New Future of Work” (https://www.microsoft.com/en-us/research/project/the-new-future-of-work/) cites poor Internet performance as the top issue identified by IT professionals when asked about the biggest challenges for employees working from home. And enterprise remote APs or VPNs are only as good as the Internet connection at the remote site.
To add complexity, the use of personal devices for business applications has increased, forcing enterprise IT and help desk teams to support a much larger breadth of devices than before.
Technologically, the first obvious change for many has been the use of remote APs to support subsets of remote workers. Preferred over traditional VPNs by some users, remote APs extend the organization's Wi-Fi (and often, wired) networks to the user's home. Remote APs are described more in Chapter 1, “Introduction to Concepts and Relationships.”
Balancing Additional Work and the Tech Talent Shortage
On the other end of the spectrum, work within the organization's traditional campus environments has increased for many professionals as teams take advantage of unoccupied and sparsely populated offices. Backlogged projects are being tackled while structured cabling and IT teams have easy access to workspaces and common areas, with little worry of disrupting employees.
The other side effect of vacant office buildings has been that many enterprises are downsizing, leaving, or remodeling offices to accommodate the new future of work. All of these lead to more workload on the IT and security teams, and there's little to no relief for many while the additional workload coincides with staffing shortages.
“The Great Resignation,” as it's been dubbed, hit critical mass mid-2021, and it hit hardest in the IT sector. While 40 percent of remaining employees surveyed were considering quitting their job, that percentage was a whopping 72 percent for tech employees in a report from TalentLMS (Sources: https://www.microsoft.com/en-us/worklab/work-trend-index and https://www.talentlms.com/tech-employees-great-resignation-statistics).
IT and infosec roles were already posting record shortages before the pandemic stay-at-home orders were issued in 2020. The climate of added workloads, lack of social interactions with coworkers, and filling in for missing headcount is taking its toll—on personal well-being as well as enterprise security posture. When you're burning the candle at both ends, some tasks will have to fall off the list; things will get missed, and vulnerabilities will be introduced.
Process Changes to Address Remote Work
The to-do lists continue growing, as enterprises are forced to restructure applications to support a remote workforce—often moving servers and services to the cloud, some of which impacts the connectivity and security monitoring of networks.
Contributing to the resignation crisis among all employees, frustration with technology—laptops and remote network connections that don't work—are cited as a top reason people are leaving their jobs. The added friction of increased security requirements such as MFA aren't helping either. Confusion about what to do when technology doesn't work is also a leading problem.
Network services traditionally hosted on-prem are moving to hybrid and cloud models to help reduce user friction and ensure services are available without time-consuming access methods that further irritate users. These moves impact authentication and IAM processes, requiring integrations with APIs and a move toward SAML-based logins.
Along with changes in services and applications, the processes for provisioning infrastructure are changing—often moving toward automated and zero touch provisioning technologies, which may require additional upfront work and reconfiguration of existing network devices. The remote model necessitates modifications in how teams support end users and provision their devices as well.
And it's not just the end users that are remote. The IT teams, network architects, and help desk may also be remote, in whole or part and full time or part time. That means yet more changes to processes and architecture to ensure secure remote privileged access, account validation without in-person processes, and finding better ways to collaborate remotely.
Recommendations for Navigating a Remote Workforce
When it comes to supporting and securing remote workers, there are a lot of factors that are simply out of our control.
The most meaningful, and perhaps the most unexpected piece of advice I can offer fellow technologists and security professionals is to take care of yourself—physically, emotionally, mentally—whatever that means, and find ways to stay grounded, remain mindful, and build your own personal resilience.
The demands put on IT and infosec teams was overwhelming before the pandemic, and the speed of change in technology is dizzying without having new major projects thrown at us. Things may have to fall through the cracks, and some ends may be left loose. That, along with a few other tips and tricks for navigating the changing workforce include:
- Maintaining personal mindfulness and resilience to manage additional stress of changes
- Creating documentation, even if ad hoc, to track changes and notes
- Identifying repeatable processes and streamlining operations
- Offloading information-gathering tasks to vendors and resellers
- Creating processes to offload subsets of your work to more junior staff
- Leveraging zero touch deployments when possible
- Working on communicating clearly and often to avoid misunderstandings, friction, and rework
- Relying on peer groups within your industry or interest area to crowdsource resolutions to challenging issues
Bring Your Own Device
We're going to cover technical elements here, but if you take nothing else away from the topic of bring your own device (BYOD), what I hope sticks with you is the complexity of BYOD from the business and legal perspectives, and that BYOD policies are not something that should be left for IT teams to write or enforce single-handedly.
Also, there's only one hard and fast rule for BYOD: Access to any secured or sensitive resources should only be allowed from a device the organization has some level of visibility into or control over. You'll hear this repeated throughout this part of the book in various ways.
Retaining visibility and/or control can be accomplished in a few ways. The following subtopics will break down the models and best practices, but for context the goal can be reached in several ways, including:
- Personal device with corporate-managed mobile device management (MDM) agent to enforce device security and posture
- Personal device with NAC agent or agentless scanning to verify security posture
- Corporate-managed, personally enabled device under full enterprise management
Stats on BYOD and Policies
Even though around 60 percent of organizations have a BYOD program, more than half of them don't have or enforce a formal BYOD policy. And, regardless of the organization's official BYOD policy, two out of three employees use their devices at work—even if it's forbidden.
Without a policy for BYOD, organizations and employees are both left to be victims of circumstance.
Aside from the legal considerations, mobile devices continue to be the source of many breaches worldwide. At one point, 68 percent of healthcare data breaches were due to the loss or theft of mobile devices or files, as reported by Bitglass, and that number has continued to grow.
Policies and accompanying security controls can enforce meaningful protection of enterprise data on mobile and personal devices, offering mechanisms to encrypt data, enforce strong passwords and lockout timers, along with emergency remote wipe or GPS tracking to locate lost or stolen devices.
Worldwide, 97 percent of companies were affected by mobile threats, including reports that almost half of organizations (46 percent) reported at least one employee having downloaded malicious applications on a smartphone. It's probably no surprise then that nearly every organization surveyed reported at least one smartphone malware attack. (Source: Checkpoint Mobile Security Report 2021, https://pages.checkpoint.com/mobile-security-report-2021.html.)
Other Models for Ownership, Management, and Use
BYOD isn't the only way personal devices are used in the organization. There's yet another alphabet soup describing varying ownership, management, and use relationships, including the following:
- Bring Your Own Device The traditional BYOD model describes a device that's wholly owned by the employee, and on which the enterprise may (or may not) request to install MDM or an agent to containerize corporate data for security purposes.
Challenges with traditional BYOD are that the organization's IT teams may find they need to support a breadth of device types, operating systems, and generations. App incompatibility, restrictions on MDM permissions, and the general overhead of help desk teams can be troublesome with BYOD.
- Choose Your Own Device Choose your own device (CYOD) models were meant to address employees' desires to not be forced into a single type of device, while allowing the enterprise to focus on supporting a subset of devices with known compatibility.
In CYOD, the organization offers the employee their choice of a selection of supported devices. The ownership model can be corporate-owned or personally owned, but regardless, the organization will only allow and support use of the approved devices for business purposes.
- Company-Owned, Personally Enabled Company-owned, personally enabled (COPE) devices tighten security one notch beyond CYOD. In COPE models, the organization owns and manages the device, but allows certain personal applications and uses such as voice calls, texts, and allowlisted applications.
COPE is emerging as a great option for security-conscious organizations that want to allow some workforce flexibility and, most notably, not force employees to carry two devices. COPE models should take advantage of built-in secure containerization or add-on software to separate personal and business data as much as possible.
Like CYOD, the COPE program may include a short list of devices for the employee to choose from, but unlike CYOD, the organization maintains ownership and control of the device, and pays for it.
- Company-Owned, Business Use Only Company-owned, business use only (COBO) is just as it sounds—the device is locked completely, disallowing personal applications. COBO policies could be for any employee in a high-security environment such as financial, healthcare, or certain government agencies. It's also appropriate for shared device environments where one device is used by different employees at different times, such as for shift workers in a warehouse or field technicians.
Table 8.1 captures the various ownership-management models and the relative risk level associated with each.
Further defining BYOD in the organization can be completed now that you're familiar with the options for ownership and management of devices.
Table 8.1: Management and ownership models for devices
| MODEL | DEVICE OWNERSHIP | DEVICE MANAGEMENT | USE | RISK LEVEL |
|---|---|---|---|---|
| BYOD (Unmanaged) | Employee | Employee | Personal + business | High |
| BYOD (Managed) | Employee | Employee, with company MDM | Personal + business | Medium-high |
| CYOD | Employee or Company | Company | Personal + business | Medium |
| COPE | Company | Company, allowing personal use | Business + personal | Medium-Low |
| COBO | Company | Company | Business only | Low |
Further Defining BYOD in Your Organization
Chapter 5, “Planning and Design for Secure Wireless,” outlined two basic starting points for defining BYOD in the organization:
- Allow personal devices on the network but with Internet-only access
- Allow personal devices on the network with some level of access to internal or protected resources
Our goal at that time was to gather enough information for a general planning table. Now diving deeper into BYOD, the objective is to further refine the definitions to begin drafting appropriate controls for securing BYOD (or one of the other management models). Considerations are summarized in Table 8.2 and include:
- Form Factor Smartphone, tablet, laptop, etc.
- Ownership and Management Model Unmanaged BYOD, managed BYOD, CYOD, COPE, or COBO.
- Corporate Visibility and Control Based on the management model and the device type(s), what visibility or control does the organization have over the device to ensure security?
- Access Requirements Internet-hosted SaaS applications, on-prem, or IaaS/PaaS resources, and the nature of the networks, endpoints, and data being accessed.
- Access Source Where is the user accessing resources from—within the traditional perimeter in-office, or from home/remote? And if remote, what countries or regions?
Privacy and data protections vary in different parts of the world, as to approved encryption technologies. In addition, some industry segments will have additional restrictions for business conducted (and data transferred) to and from foreign countries.
Table 8.2: Table of BYOD access planning
| FORM FACTOR | OWNERSHIP/MANAGEMENT | ACCESS REQUIREMENTS | ACCESS SOURCE |
|---|---|---|---|
|
|
|
|
The following sections will offer guidance through the decision-making processes, but the one combination to always avoid is any unmanaged device accessing anything other than Internet-based resources. And, in organizations beginning a zero-trust strategy, even that access should be metered and controlled in some way.
Legal Considerations for BYOD
The most critical input into any BYOD policy will be those of legal considerations. Organizations have a responsibility as stewards of their data, and they have a responsibility to ensure employee privacy is maintained—it's all a delicate balancing act. Legal obligations and options related to BYOD policies vary by region, and even by state within the U.S.
In a tragic 1977 plane crash, two members of the rock band Lynyrd Skynyrd were killed. The survivors and families made a blood oath that no one should ever again perform as “Lynyrd Skynyrd,” and that oath was legally memorialized in a 1988 Consent Order.
What can Lynyrd Skynyrd possibly have to do with BYOD? Well, almost thirty years later, one of the few survivors, drummer Artimus Pyle, began consulting with a production company (Cleopatra Films) for a biopic about the band's 1977 plane crash. Other members from the original blood oath took legal action against Cleopatra Films, and won, blocking production of the movie. One large body of evidence was related to text messages exchanged between Pyle and the main writer (a contractor of Cleopatra Films)—the text messages (evidence in the case) were lost when the writer changed phones.
Shortening the story; the court found Cleopatra Films was guilty of “spoilation of evidence” by not having control over their contractor's text message as critical evidence in the case. The writer wasn't an employee of the film company, nor was he using a company-provided device. But there was also no policy in place outlining expectations of the use of personal devices, or ownership of data (including texts) on that device. The court awarded an adverse inference against Cleopatra Films, saying it was “common sense” the contactor's texts were in Cleopatra's control. There is a happy ending though; in 2018, the judgment was overturned and in 2020 Street Survivors: The True Story of the Lynyrd Skynyrd Plane Crash was finally released.
It's a fun story that brilliantly demonstrates the twisty legal issues organizations must navigate through BYOD policies.
And it's just one example in a long list of BYOD gone bad. In another case, audio manufacturer Klipsch won a case when it moved for e-discovery sanctions against a defendant accused of selling counterfeit product. The appeals court faulted the other company for “failing to have a software usage policy in place requiring its employees to segregate personal and business accounts or to otherwise ensure that professional communications sent through personal accounts could be preserved.” The findings (and lack of policy and enforcement) cost the defendant $5M USD.
These are just a few of the many legal considerations that go into planning a BYOD policy:
- E-discovery requirements, defining what's in scope on personal devices, processes, and employee obligations during litigation holds
- Data ownership and management, including what obligations the organization has to protect its data, and what legal entitlements it has to wipe or back up data from personal devices
- Data privacy, including what the company is legally allowed to do to, or view from a personal device such as texts, calls, photos, GPS tracking, or browsing history
- Employee lifecycle, including what happens to the corporate data when an employee separates from the company
- Illegal activity, including what the organization is allowed or obligated to do in the discovery of illegal activity
Legal considerations don't stop at data protection. In 2021, Coca-Cola was slapped with a $21M USD judgment after one of its truck drivers hit a woman, reportedly distracted while chatting on the phone. Even though the company's policy prescribed the use of a hands-free device while driving, the plaintiff's lawyers convinced the jury that the policy was “vague and ambiguous.”
Just to recap, we don't expect (or want) technologists or architects to be legal professionals. The point of this content is merely to demonstrate how bizarre and complex the laws can be, and the risk posed to an organization by ineffective or insufficient policies or controls.
Even if you stayed at a Holiday Inn Express last night, let the lawyers figure this part out.
Technical Considerations for Securing BYOD
Chapter 5 lightly touched on BYOD in the section “Planning Processes and Templates.” In that content, the first exercise was to define what BYOD means in the organization. Picking up where that left off, the steps that follow are to work with executive leadership to define a BYOD policy and specify parameters around who can access what, from what device, when, and how. The technical planning for this was covered also in Chapter 5's “Sample Access Rights Planning Templates.”
With any luck, BYOD policies will stipulate that the organization only allows access to secure resources from devices that are under some form of management by the organization. In that case, depending on the ownership and management model, solutions like MDM products may be in order.
MDM solutions don't stop at personal smartphones—they're the cure for all that ails us when we need control over otherwise unmanaged devices. For our purposes, I'm going to place anything that's remotely MDM into the “MDM” category as described with the following features. MDM products offer one or more of these technical controls:
- Enforcing passwords and password complexity
- Enforcing screen lock timeouts and incorrect login lockouts
- Containerizing corporate data away from personal data and applications
- Supporting e-discovery processes including holds
- Implementing a remote wipe sequence for corporate (and at times, personal) data and applications (if lost or stolen)
- Allowing remote lock of the device (if lost or stolen)
- Locating the device (if lost or stolen)
- Installing device certificates (including ones for Wi-Fi authentication)
- Installing server certificates (including RADIUS server certificates for 802.1X-secured Wi-Fi)
- Pushing enterprise applications to the device
- Pushing passphrases for WPA2- or WPA3-Personal networks
- Joining the endpoint to the enterprise domain
- Running security posture checks and enforcing posture
MDM-type products aren't just for phones; depending on the product and vendor, they may be used on any of the following:
- Virtual desktops
- Standard OS desktops and laptops
- Tablets
- Smartphones
One of the most challenging technical hurdles is that most MDM tools will work on (for example) iOS, Android, and Windows (along with virtual desktops) but the controls available per device OS will vary from one another and will vary over time. And the options and behavior vary depending on the MDM product used and the device's native containerization—for example, an Android device with Samsung Knox has security options beyond a standard Android device. Like so many of our other tools, MDM solutions may be integrated into our existing infrastructure (such as subsets of Microsoft Intune) or installed as a third-party solution.
Choosing an MDM tool is another choice very personal to each organization—the types of devices, operating systems, and the granularity of control varies by product, as does the integration with other tools.
Recommendations for Securing BYOD
At this point, I hope you're appropriately apprehensive of creating BYOD policies. It is also my hope you're able to motivate the organization to create or update BYOD policies if needed, but in the absence of that, there are a few best practices around BYOD that are generally safe for most environments.
Also, since the recommendations are dependent on the BYOD model (Internet-only access versus internal access), that's how they're organized All of these factors should be evaluated when considering an MDM platform.
Recommendations for BYOD Internet-only Access
In Chapter 5 it was noted that planning for Internet-only BYOD is fairly straightforward. The one request that makes it more complicated than standard guest portals is that many organizations want their employees to be able to use the Internet-only connection without the friction and frustration of a daily captive portal experience.
This is a completely legitimate desire—however, to meet this objective, decision-makers will often instruct wireless architects to allow personal devices on the secured network—either by allowing users to join 802.1X-secured networks with their domain usernames and passwords, or by having personal devices on an internal passphrase-secured network (WPA2- or WPA3-Personal). Neither of these are advised because they introduce several security risks.
Instead, for personal devices requiring Internet-only access, with the goal of not repeating a daily captive portal, one of these methods should be used. These are presented in order of most to least secure, but all are valid options.
- Registration-based BYOD Captive Portal This would allow employees to register their personal devices under their domain account using a portal page; the account can be authorized for a period of time or indefinitely.
With some products, the users can manage their list of approved personal devices, and a maximum number of devices per user can be specified. These features are most often available with a NAC product, but some Wi-Fi products are adding built-in support for this as well.
Notably, this option links the otherwise unknown personal device to a known user, but it does so safely, without exposing the user credential on the unmanaged device.
- Basic BYOD Captive Portal with an Extended Cache Timer A basic portal would look just like a guest portal, but the timer would be set for a much longer duration; for example, instead of a 1-day guest account, the employee can join with their device and not have to revisit the portal for 3–6 months, or even a year. The portal can be a subfunction of an existing guest portal and of course should offer Internet-only access.
- Passphrase-Secured BYOD Network Passphrase-secured networks for BYOD access is perfectly acceptable, as long as the access is Internet-only, but it's preferred to separate personal devices from any other corporate endpoints such as IoT devices.
This can be accomplished with separate SSIDs, or through dynamic VLANs (or roles, policies, etc.). If at all possible, use WPA3-Personal for this purpose—remember that WPA3-Personal networks are far superior in security to legacy WPA2-Personal networks.
Recommendations for BYOD with Internal Access
Circling back to the opening paragraph—the one hard-and-fast rule for secure BYOD is that access to any secured or sensitive resources should only be allowed from a device the organization has some level of visibility into or control over.
From a technical perspective, I'd encourage you to advocate for this model and/or to start with this access until better direction is offered by the organization.
Organizations should not allow personal devices on secure production Wi-Fi networks unless all of the following criteria are met:
- There's a business case outlining the requirements and there is no other way to meet the business objective
- There's a policy in place (approved by executive leadership) stating that personal devices are allowed, along with the conditions and access; and in the absence of a policy, request approval for personal devices in writing (email is fine) from your manager or other leader in the organization
- Each user participating in BYOD has read, acknowledged, and signed the BYOD end user policy
- The organization has some visibility into the security posture of the personal device such as through an MDM tool or NAC agent
- There is a mechanism to securely onboard the personal device to the network, such as through an MDM and certificates, or through a NAC product
- There's no onboarding mechanism that puts the user's domain credentials at risk; specifically, the users should not join an 802.1X-secured network from a personal device using domain credentials
In addition to the preceding requirements, there are a few additional recommended items that would offer additional security:
- Use granular access policies to allow access only to the required resources
- Preferably, do not co-mingle unmanaged personal devices with managed devices on the same SSID or VLAN
- Have a way to determine which devices on the network are personally owned, and also to identify the user/owner of the device
- If possible, use an MDM or agent for security posture scanning to ensure the personal devices are not infected, and meet minimum security requirements such as passwords and patching
The reasons for the recommendations here are covered throughout the book, and especially in Chapter 3, “Understanding Authentication and Authorization,” and Chapter 6.
Zero Trust Strategies
Zero trust is one of today's (and tomorrow's) super-hyped topics and while I'm certainly not here to toss buzzwords around, zero trust is a timely and relevant topic for network and security architects. I don't plan to go deeply into the topic, but I work a lot in this space and feel there's value in clearing up a few misconceptions and points of confusion related to network security and zero trust.
The Current State of Zero Trust
Think of zero trust as a mindset, and not a product set. It's just like saying “layered defense.” While the models and frameworks floating around seem to indicate zero trust is an all-or-nothing, super-granular architecture, the reality is that applying one-to-one access rules for every endpoint and user, to and from every service, server, and resource is impossible with current tools. It's neither practical nor desirable at this stage.
With today's zero trust strategies, the goal is to incrementally remove inherent trust and apply specific, context-based access rights. Moving away from traditional remote access VPN solutions is a perfect example of removing inherent trust—many VPN implementations today are an “all or nothing” access model; a remote user is either allowed on the network, or not. Believe it or not, relatively few VPN deployments apply granular access policies; instead, it's just as though the user were inside the office with the normal layer 2/3 access that accompanies it.
Instead, a zero trust strategy would direct us toward evaluating both the endpoint device and the user—perhaps performing a security posture scan and ensuring the user is requesting access from an approved region—and then the user is granted only the access needed, such as the ability to connect to a subset of servers or services in the organization.
Similarly, zero trust strategies will begin to inform stricter control for management access of systems, adding contextual information and enforcing greater security such as two-factor authentication (2FA). Zero trust isn't some imaginary mystical creature—it's really just the next evolution of network access control (NAC); one that incorporates cloud-routed technologies and Internet-based resources instead of (or in addition to) traditional on-prem models.
Moving toward a zero trust architecture is incremental and organizations will start identifying use cases and subsets of data or resources that are flagged as more sensitive than others, and that's where zero trust begins.
Zero Trust Language
Further proving the point that zero trust is just the next evolution of NAC, the terminology from the formal zero trust frameworks (such as NIST's) uses the same language from NAC and authentication models, such as:
- Policy Decision Point The Policy Decision Point (PDP) is the brain of a zero trust ecosystem: it's the policy engine making decisions about access rights. Conceptually, the PDP takes inputs from various other systems (most likely via APIs) and then connects to policy enforcement points (PEPs), which will enforce the decision made. In reality, while a centralized PDP is idealistic, there is no one master product available to perform PDP functions for the breadth of use cases for zero trust.
- Policy Enforcement Point Policy Enforcement Points (PEPs) enforce the access policies as directed and orchestrated by the PDP. PEPs can be any piece of software or hardware that can apply an access policy or control traffic flows; including (but not limited to) zero-trust enabled switches, routers, and firewalls. Software agents and endpoint software with built-in host firewalls can also be PEPs. From our earlier example, a VPN appliance would also be a PEP.
- Subject The subject in zero trust lingo is just the device or user requesting access to a resource (aka target).
- Target The target is then the resource being accessed. A target can be a specific server or device, or it could be as granular as a single database, service, or microservice running on a server or serverless infrastructure. Approaching it from a broader perspective, a target could be a set of resources, like an entire network segment—something referred to as an enclave model.
- Action Action describes the action allowed or access to be granted. This could be allowing communication over a specific port or protocol, or it could be an action policy that allows all traffic to and from a network.
- Condition If the action is only permissible with certain conditions, those are specified by the PDP. This may include dynamic conditions within the environment, subject, or target that determine access.
For example, a condition could be that the subject is making the access request from within a list of allowed geographies. The condition might also stipulate that the subject device has been scanned for security posture and passed. Or certain variables may be factored and require the user to elevate their privilege using 2FA to gain access to a secured resource.
Figure 8.2 shows a simplified diagram of a zero trust ecosystem with the labels for PDP, PEP, subject, and target. In the figure, a central policy engine is making decisions about access to the on-prem resources (in an enclave model) and to cloud-hosted resources, which may be granular per-service policies or also a group of resources. Although depicted with a user/device as subject, in zero trust models the subject could be a server or microservice.
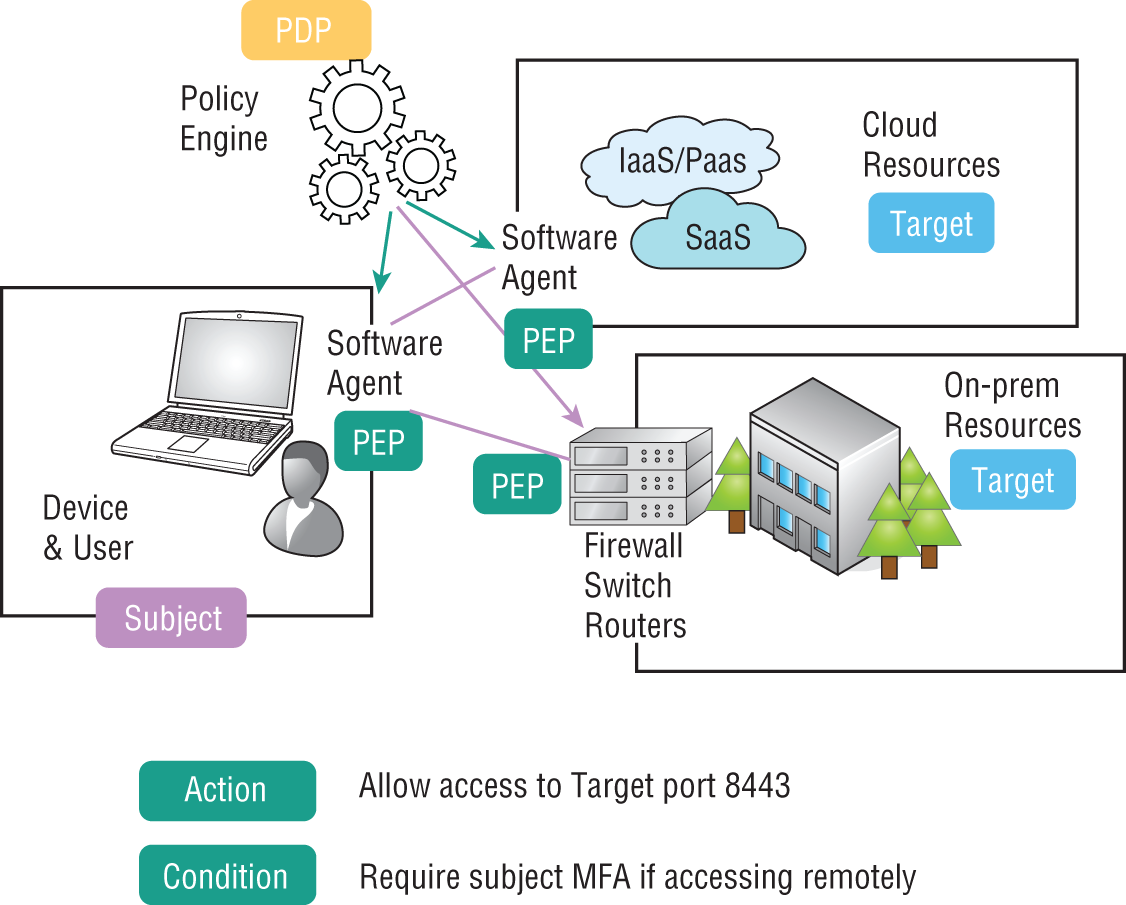
Figure 8.2: Zero trust terminology is just an upcycle of NAC
Types of Zero Trust Products
Common features of products that support a zero trust strategy may focus on one or more of the following attributes:
- Provide encryption of data in transit
- Manage the data path of connections
- Perform or enable security inspection of traffic
- Provide secure and granular remote access
- Provide secure and granular privileged access
- Enable concept of least privilege
- Ensure strong identity and authentication
- Use scalable integration methods such as APIs and SAML
I group the product sets into two main categories—cloud-routed and direct-routed. Currently, most direct-routed solutions are designed for on-prem use cases but that will evolve over time. The details of these are covered next.
At time of writing, these products are rarely converged, meaning there are virtually no products that are designed to (efficiently) enforce access control over the Internet and on-prem.
Segueing to the next topic, Figure 8.3 offers a simplified view of cloud-routed versus direct-routed models common in today's zero trust products. With cloud-routed solutions, not only is the policy engine typically in the cloud, but the cloud is also in the data path, and essentially “stitches” together access between two resources. Conversely, direct-routed models enforce connections directly between the user and the PEP, which may be a switch, firewall, or any of the aforementioned devices.
This model is simplified in that it's possible to use cloud-routed products even for localized on-prem campus deployments, and it's also possible to use direct-routed products for resources that are remote or cloud hosted.
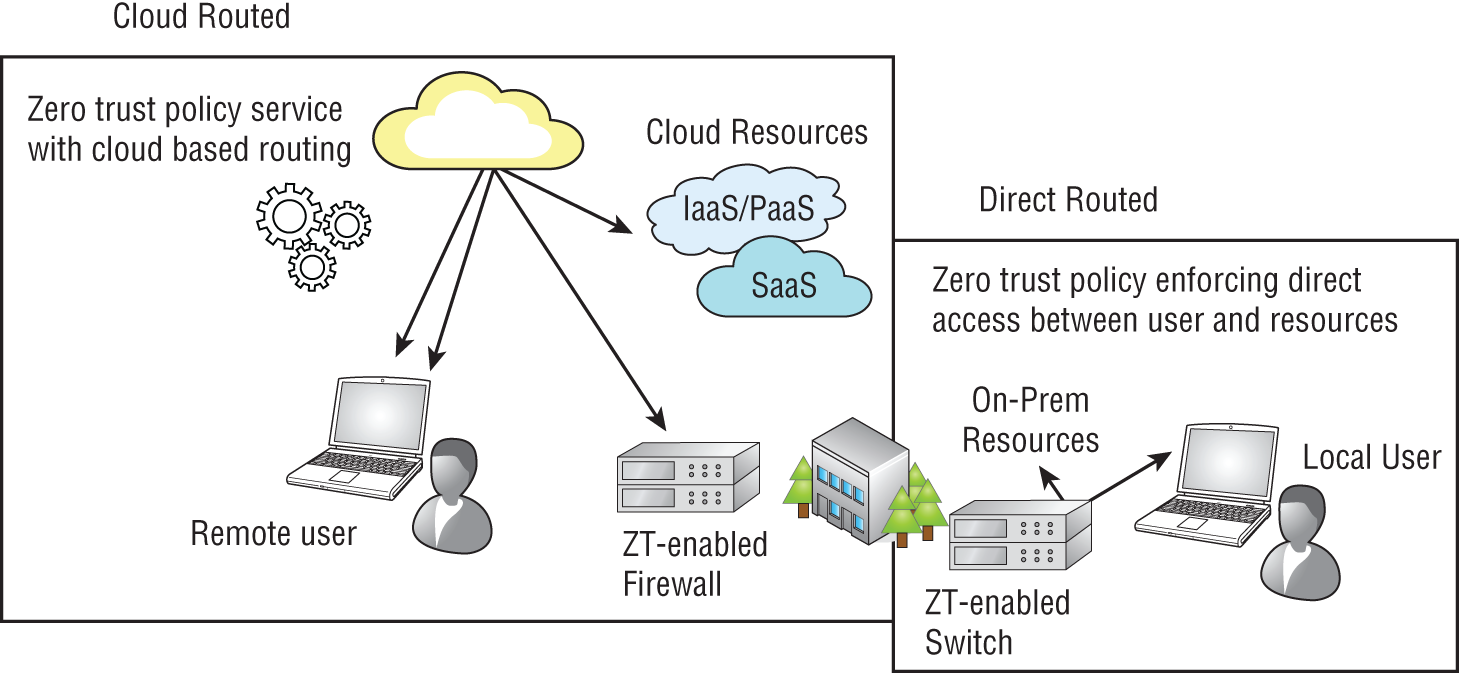
Figure 8.3: Simplified view of cloud-routed versus direct-routed zero trust product features
Cloud-Routed and Cloud Native Products
Cloud-routed and cloud native products are primarily focused on securing access to and from users that are not co-located with the resource because the data path involves the Internet. For example, if a user is working from home and accessing a resource on-prem or in the cloud, a cloud-routed product is well suited for the model.
Conversely, if the user is co-located on-prem with the resources, routing traffic out to and back from the Internet is not ideal. Depending on the network, data, and implementation, this hairpin routing out and back in from the Internet may be acceptable, but it's not how these products were envisioned.
These classifications of products, their features, and vendors change almost daily. These are all highly volatile markets, but for context, today's most common cloud-routed products include the following solutions:
- Zero Trust Network Access (ZTNA)
- Secure Access Service Edge (SASE)
- Cloud Access Security Broker (CASB)
- Secure Web Gateway (SWG)
- Software-defined WAN (SD-WAN)
- Workload and microsegmentation
- Software-Defined Perimeter (SDP)
ZTNA is an actual product and is not to be confused with zero trust as a strategy or architecture. Someone out there just wanted to further complicate and confuse us all with that name. SASE offerings are most often a ZTNA solution with additional services. The lines between the products listed here are blurry, at best.
Direct-Routed and On-Prem Products
The types of products designed to support zero trust strategies within a campus environment include:
- Network-based microsegmentation (next-gen NAC, SDN, VXLAN)
- Agent-based microsegmentation
- Network access control (NAC)
- Software-defined WAN (SD-WAN)
- On-prem components of Secure Access Service Edge (SASE)
- Zero trust enabled firewalls and gateways
- Purpose-built appliances
There are some crossover products and features between cloud-routed and on-prem products. There's also some re-use of language such as “microsegmentation,” however that word means two different things. Originally a datacenter concept for controlling authorization between servers, services, and microservices—the term microsegmentation was then borrowed by the network security vendors to describe more granular access controls from their products.
The result is that a microsegmentation product for datacenter and cloud applications is not the same as a microsegmentation product for network security on-prem. They're completely different technologies, operate with different enforcement mechanisms (covered next), and therefore have no overlap nor any relationship to one another.
Segmentation Enforcement Models
Diving into the enforcement mechanisms for zero trust products could be its own book, so I'll try to distill this down to a few salient points.
Software-based PEPs
Software-based PEPs use agents on the requestor (subject) and/or the resource being accessed (target), and will most often use one or more of the following enforcement mechanisms to enforce an access policy:
- DNS
- Local host firewall
- Local routing control
- External routing control
The level of enforcement granularity may include one or more of the following, and the access policy may be unidirectional or bidirectional, meaning it may be initiated from the requestor (aka the subject), the resource (aka the target), or either. Some cloud-routed solutions offer limited granularity and may only be built to establish connections unidirectionally.
- Application signatures
- URL/URI
- TCP (any port)
- TCP (specific list of ports)
- UDP (any port)
- Microservices
Although software-based PEPs are viable on campus infrastructures with on-prem resources, they're more often used for access enforcement to and from Internet-based resources.
For this reason, most current products that are controlling access with campus environments are using on-prem products and the appliance-based PEPs described next.
Appliance-based PEPs
Appliance-based PEPs may be physical hardware or virtual appliances and include many of our traditional networking technologies such as firewalls, switches, routers, SD-WAN gateway, Wi-Fi controller or AP, or a purpose-built vendor device.
Just as with other access control technologies, the enforcement mechanisms in appliances most often include:
- Firewall policies or zones
- VLANs
- SDN or SD-WAN policies
- ACLs (static or dynamic)
- Routes (static or dynamic)
- VXLAN
The granularity of appliance-based PEP enforcement varies slightly from software PEPs, and includes the following:
- Application signatures
- Any TCP or UDP port or protocol
- TCP (specific list of ports)
- IP addresses or networks
Most of the appliance enforcement mechanisms will look familiar—they were covered as filtering and segmentation methods in Chapter 2, “Understanding Technical Elements.”
Zero Trust Strategy's Impact on Wireless
The purpose of this content is to demonstrate that zero trust is not a mythical beast—it's built on principles (and even products) familiar to network and security architects. There's a lot of confusion in the market due to poor communication from vendors as to how their products work—specifically what enforcement mechanisms they're using, what level of granularity can be applied, and in which directions.
For now, the cloud-routed products are most appropriate for applying granular controls to and from users and resources that are not co-located. By inference then, for most readers of this book, you're interested in the on-prem infrastructure solutions for zero trust and the appliance-based PEPs. There will likely come a time in the future that the two may converge, but the overlap is so minimal currently it's negligible.
As it relates to this book's contents, zero trust initiatives may impact wireless architecture and security in one or more of the following ways:
- Prescribe stricter control of management access to systems including Wi-Fi controllers, and especially remote access
- Enforce more granular access rights for users with remote APs
- Define requirements for further segmentation of classes of endpoints such as separating IoT devices from other managed endpoints
- Define additional requirements for MFA/2FA for certain users or access and new SAML integrations for authentication
- Define additional requirements for device certificates along with user-based access
- Require new models for IoT connectivity and access control
- Involve new integration models including a broader use of APIs
Internet of Things
Managing the Internet of Things (IoT) is certainly a pain point for network architects everywhere, and it's a force to be reckoned with. The following section, “Enterprise IoT Technologies and Non-802.11 Wireless,” takes a deeper look at the models and wireless technologies prevalent in enterprise IoT, including (and especially) non-802.11-based wireless.
First, I want to present a high-level view of IoT models to serve as context because the term “IoT” tends to get thrown around, describing anything from a network printer to a structural strain gauge sensor the size of your pinky finger.
IoT models are based on connectivity, topology, and whether the protocol is natively locally routed, translated to IP, or routed to IP. These different models are grouped in the following way:
- LAN-based IoT
- Protocol-translated IoT
- Protocol-routed IoT
Figure 8.4 shows the three models side-by-side. LAN-based IoT models use standard IPv4 and/or IPv6 at the edge for LAN connectivity. Protocol-translated IoT has no IP protocol at the edge (instead uses Bluetooth, BLE, Zigbee, etc.) and requires a protocol gateway to translate the non-IP data to IP-based data to be then routed through networks to the Internet. Protocol-routed IoT seems similar to protocol-translated at first glance, with the important differentiator being the use of an adapted IPv6 protocol at the edge devices, which is then converted and routed.
LAN-based IoT
LAN-based IoT devices can be considered non-traditional endpoints that are connected to standard networks, wired, or Wi-Fi (802.11 WLAN). While it's common to throw non-traditional endpoints into the IoT bucket, strictly speaking (in the IoT communities) these don't quite qualify for an IoT designation.
However, since it's so commonly addressed along with IoT in networking, I'm including it as a model. It's certainly valid in that non-traditional endpoints take a bit more time and attention to identify and secure on any network.
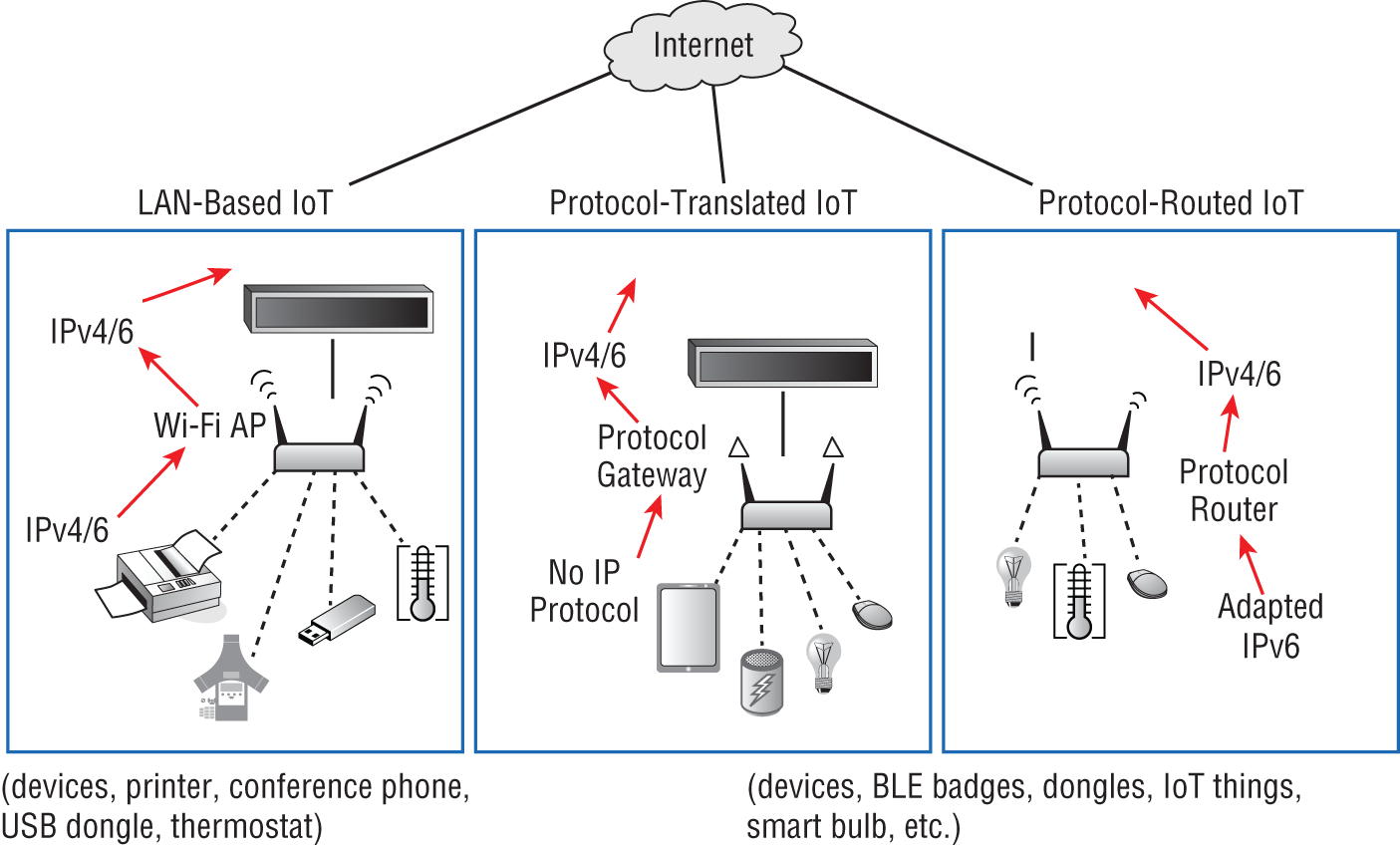
Figure 8.4: LAN-based IoT vs. protocol-translated IoT vs. protocol-routed IoT
Non-traditional endpoints on the LAN may include:
- Non-user-based devices such as printers
- VoIP and VoWiFi (voice over IP and over Wi-Fi) phones
- Screen casting devices
- Wi-Fi-connected facilities environmental control systems such as temperature sensors, lighting, and HVAC controls
- Wi-Fi-connected facilities security systems including door entry security and IP-based cameras
- Wi-Fi localized temperature sensors such as those used in pharmaceutical and food safety refrigeration
- Wi-Fi-connected vending machines, trash, and recycling
These endpoints have locally routed IP addresses (IPv4 or IPv6) and connectivity and data paths the same as other traditional LAN- or WLAN-connected devices such as laptops.
The list here is provided only as an example; many IoT device manufacturers offer multiple connection models. For example, many kinds of sensors could be Wi-Fi connected but may also support deployment on RF in the sub 1 GHz range, and/or via direct cellular connection.
Also, remember that just because an endpoint is network connected doesn't mean it's Internet connected. Many devices described as LAN-based IoT are just local network-connected endpoints, not IoT.
Protocol-Translated IoT
Protocol-translated IoT devices aren't IP-addressed at the edge. Instead, there's a non-IP-based protocol in use along with a protocol gateway or protocol translator.
For context, common protocol-translated IoT technologies include Bluetooth and BLE and Zigbee. This IoT model isn't just for localized and personal LANs, though—it's also common in private WAN technologies (such as Sigfox and LoRaWAN) as well as some industrial automation technologies like WirelessHART. These other non-802.11-based IoT technologies are covered next in “Enterprise IoT Technologies and Non-802.11 Wireless.”
In these models, the edge endpoints (which may or may not be in a mesh topology) communicate to a protocol gateway, which converts the data to IP for forwarding and routing to the LAN or Internet.
Protocol-Routed IoT
What's not included in protocol translated IoT are protocol-routed technologies such as Thread and others based on 6loWPAN.
These use IP addressing at the edge similar to LAN-based IoT but are not based on common Wi-Fi connectivity and may use an IP adaptation layer. This is explained more in depth in this chapter's next section.
Other protocol-routed IoT technologies include cellular IoT and private cellular.
For some technologies, an adaptation layer is used to compress (for example) IPv6 to a format that can be transferred over wireless technologies with tiny frame sizes such as 802.15.4 (the layer 1/2 RF standard that Zigbee and Thread use). This is exactly what 6loWPAN offers.
Enterprise IoT Technologies and Non-802.11 Wireless
A book on enterprise wireless wouldn't be complete without all the latest non-802.11 technologies. Those presented here are in varying states of flux and evolution, and so I've chosen to organize this in a non-traditional way and hit the highlights.
Security considerations covered here, instead of being protocol-specific (which change regularly) focus on less mutable characteristics such as the physical layer, topologies, connectivity models, and coverage areas. As these technologies grow over time, the guidance here should persist even through significant flux.
First is a high-level introduction of the various technologies to get familiar with the context, followed by characteristics that factor into connectivity and security architectures:
- IoT Considerations
- Technologies and Protocols by Use Case
- Features and Characteristics Impact on Security
- Other Considerations for Secure IoT Architecture
IoT Considerations
Among the countless connectivity and security considerations, IoT devices collectively are heavily influenced by a few IoT-specific characteristics, including the following features.
- Battery Life Most edge IoT devices are not connected to AC power, nor do they have extensive battery or recharging capabilities. While there's been progress in the move toward energy-harvesting capabilities in IoT devices, batteries will remain a part of IoT life at least for the foreseeable future. If you're not familiar with the term, energy harvesting is a process to capture energy from renewable sources (such as movement, light, UV, RF, etc.) and convert it to usable electrical energy.
For the rest of the world's IoT devices, power is a precious commodity, and connectivity protocols for IoT are modified to preserve battery life. This means less frequent transmissions, shorter transmissions, antennas that use less power. and at times an inability to communicate with the IoT device between scheduled transmissions.
- Form Factor The form factor of the device will dictate in large part the capabilities tied to onboard resources such as memory and processing power, in addition to battery. Although not a hard rule, and certainly not a linear relationship, generally the smaller an IoT device gets, the fewer capabilities it can accommodate. This translates into trade-offs for security and performance as vendor implementations streamline resources by reducing unique encryption keys in storage, bypassing provisioning security, or simply removing processing power required to perform computationally complex encryption.
- Location Where the device is, physically, and how accessible it is—to you and to potential adversaries—is an important IoT consideration. When physical security can't be ensured, additional logical protections are needed. And, for unreachable devices deployed in remote areas, access for the purposes of software and security updates may not be viable.
- Bandwidth The bandwidth a wirelessly connected IoT device can make use of will vary depending on the technology and deployment. In most cases, endpoints that are physically farther from the wireless base station and those that are extremely power-restricted will use radios that support very small transmission bandwidths. This reduction allows for a greater range in connectivity (by eliminating other interference with broader bands) and aids in preserving battery life. See Figure 8.5 for a high-level comparison of battery and range for several IoT technologies.
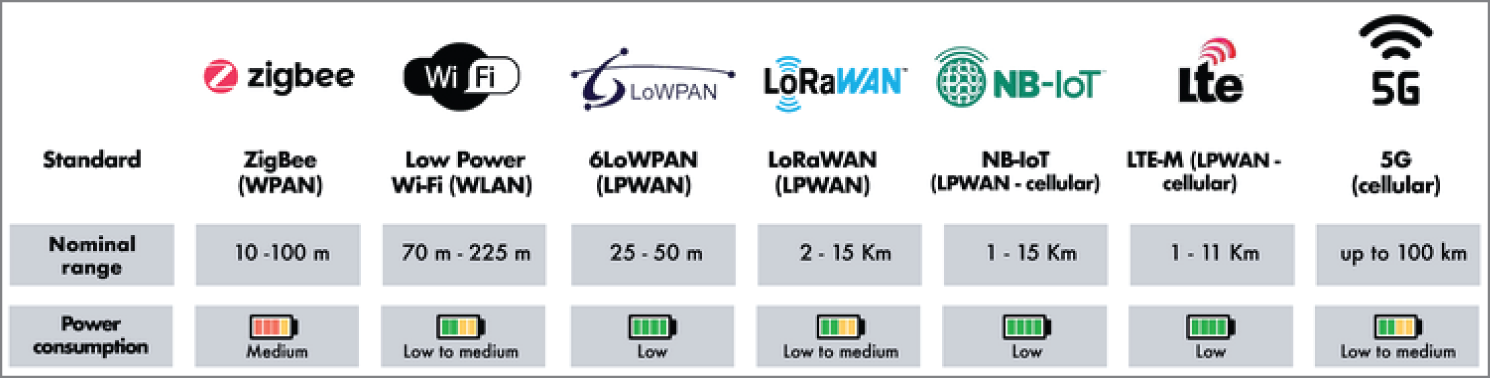
Figure 8.5: Comparison of power consumption and range for common IoT technologies
Technologies and Protocols by Use Case
There are a multitude IoT protocols, many of which are used primarily for home automation and hobbyist projects. The technologies here are of a scope limited to those appropriate for use in an enterprise environment. Other technologies and protocols not specified here follow similar models to the smart building and home automation suite.
We're going to take a brief tour of the following classes of IoT technologies:
- LAN-based IoT
- Bluetooth and BLE
- Smart Building and Home Automation
- Public Cellular for IoT
- Private Cellular and Cellular LANs
- Private WANs
- Industrial Automation
You can see the mapping of IoT technologies to edge IP protocol, connectivity model, coverage, physical layer, and whether it's mesh or not in Figure 8.6. Lighter connectivity lines indicate partial or limited applicability.
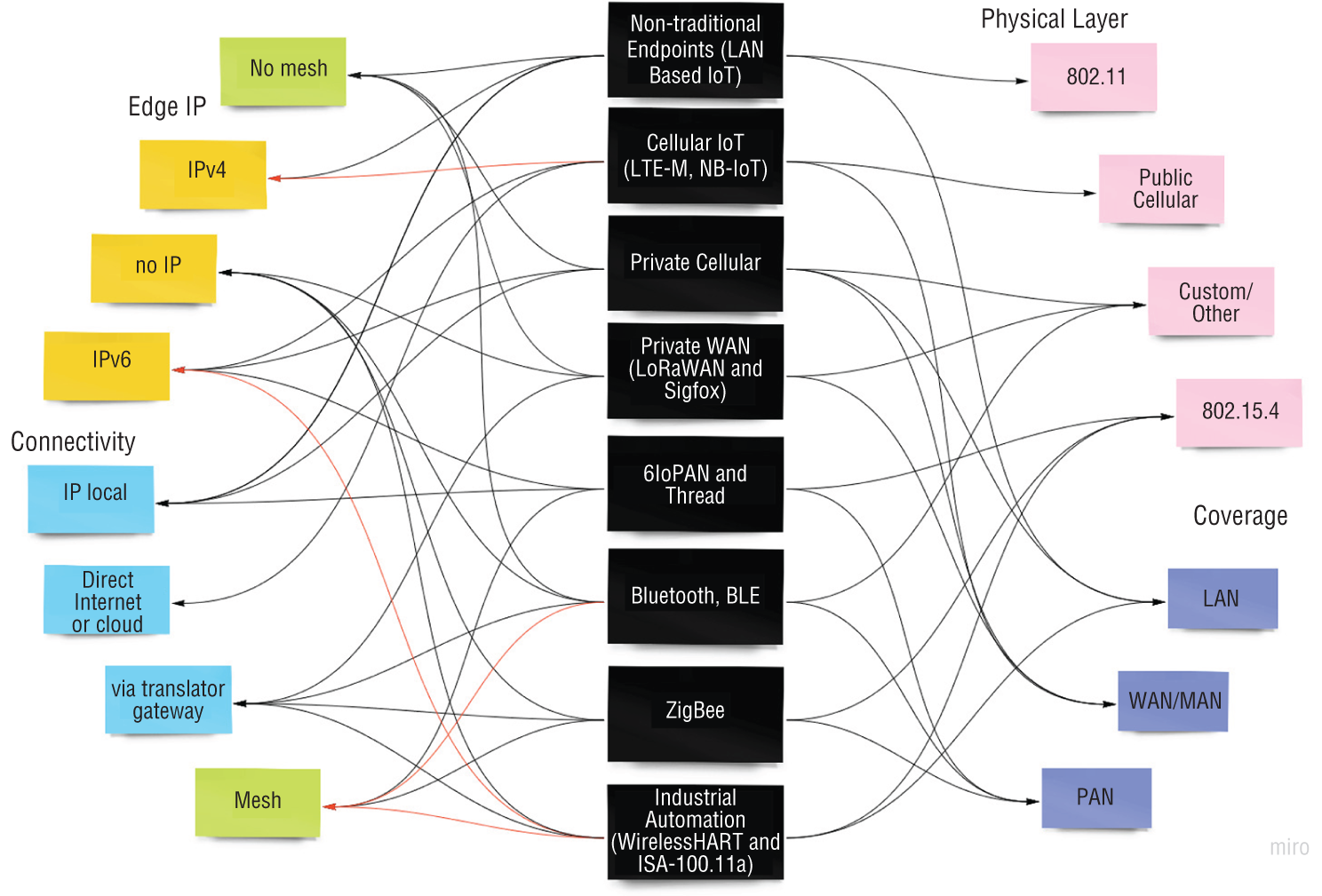
Figure 8.6: Visual map of IoT technologies, their topologies, coverage areas, physical layer, and edge IP model
LAN-based IoT
LAN-based IoT are the pseudo-IoT devices that don't quite earn the “IoT” title but are nevertheless connected devices we're forced to deal with and secure.
A large portion of this book has been dedicated to 802.11-based Wi-Fi security, and I'm not going to repeat all of those concepts here. There are, however, some unique considerations when dealing with the non-traditional endpoints on Wi-Fi networks, and those considerations are addressed here.
Securing LAN-based IoT includes the following challenges and considerations.
Device Identification
Most often, we have three ways to identify an endpoint on the LAN: it was manually provisioned, and the MAC address and other identifiers were documented; it has a logged-on user that identifies the device; or it has a device certificate that identifies the device.
In the absence of one of those three more deterministic methods, processes for identifying a device is more of a guess. Profiling methods (common in NAC, UEBA, and Wi-Fi products) gain some context by looking at the NIC OUI to determine the manufacturer and by watching aspects of traffic passing through such as DHCP requests. Other profiling methods may layer additional criteria such as mapping open ports or parsing an HTTP header. In total there are about twenty common active profiling mechanisms.
Newer profiling methods incorporate data from watching mirrored traffic on the network to get even more context about the endpoint and what it's doing on the network. Each of these methods offers an increasing level of confidence about the identity of the device, but none guarantee 100 percent accuracy.
When it comes to device identify with non-traditional endpoints, this is by far the most time-consuming task in any project (including and especially NAC projects).
Device Authentication
Device authentication becomes another challenge with many LAN-based IoT devices. Even though connected with familiar Wi-Fi technology, the endpoint may not support authentication (remembering that passphrases aren't considered true authentication).
Most of the more standard network devices including printers and VoIP phones do support 802.1X, and therefore can be authenticated with either a device certificate or device domain credentials. Other endpoints support no authentication but could use MAC Authentication Bypass (MAB, which again isn't really authentication in the infosec sense.)
Software Updates and Patching
Maintaining basic security hygiene with software updates and security patches is also challenging with many IoT devices (LAN-based and otherwise). It seems in many environments even printers and other readily accessible devices don't receive regular patches.
IoT endpoints without standard interfaces are even more cumbersome to update, often requiring additional management platforms.
Creation and Maintenance of Segmentation Policies
In a perfect world, each grouping of IoT devices would have granular access policies restricting traffic to and from only the requisite resources. In practice, many organizations have a single IoT-designated passphrase-secured network and throw everything there together, with little to no additional segmentation.
Wi-Fi, NAC, and authentication server products all support varying approaches to label and further segment IoT devices. Some offer integrations with external devices such as firewalls (which model traffic and apply labels to the endpoints); others rely on authentication policies with basic dynamic VLAN assignments.
Limited Options for Secure Wi-Fi Connections
Even when properly segmented, many IoT devices don't have robust support for secure Wi-Fi connectivity, making them vulnerable to over-the-air attacks. For example, Figure 8.7 shows a table from current product documentation for a vendor's industrial environmental monitoring systems. The wireless products referenced include sensors for temperature, pressure, humidity, sound, and cryogenic systems, among others, and are marketed to customers in healthcare, pharmaceutical, and food safety.
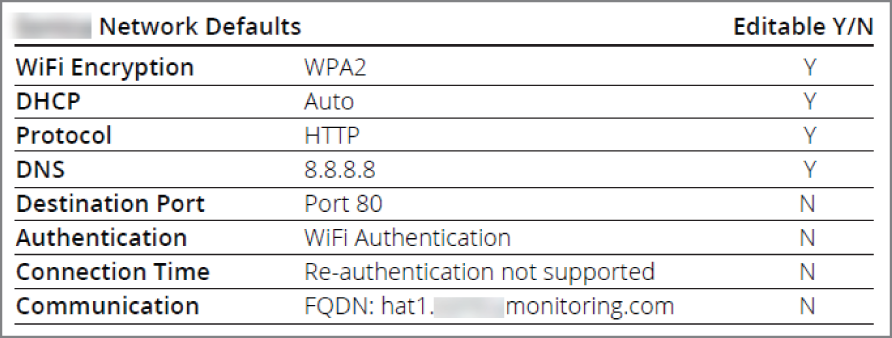
Figure 8.7: Excerpt table from a network connectivity datasheet for a Wi-Fi-enabled sensor product
In the network requirements, the table shows only WPA2-Personal is supported, and communication is by default HTTP over port 80. The port is not editable by the customer. This vendor also claims their system can “effectively reduce the potential for any type of network attack to zero” which is, of course, misleading.
Bluetooth and BLE
I'm a big fan of IEEE and standards, so I'm going to lead off with this. The Bluetooth specifications are no longer based on IEEE standards. Originally, they were part of IEEE 802.15.1 Working Group, but later spun off to the Bluetooth Special Interest Group (SIG, at www.bluetooth.com).
In addition, the bulk of Bluetooth devices have been created for personal and residential use—not commercial applications. The use cases have been changing in recent years with the growth of IoT in the enterprise, but there's a lot of legacy technology and the goal of most Bluetooth products is to simplify connectivity, reduce user friction, and reduce support calls.
As you'll see throughout the overview of Bluetooth and BLE, the default mode of operation is the least secure. To make these products appropriate for commercial use requires the product manufacturers to select secure implementations, incorporate those modules into the product, and to regulate allowing backward compatibility that may lead to less secure operating modes.
Bluetooth and BLE in the Enterprise
Classic Bluetooth and Bluetooth Low Energy (BLE) have been fixtures within most enterprise environments for some time. Classic Bluetooth has been well-suited for wireless accessories that require constant data transmission, such as wireless headsets and speakers.
But all that constant connection puts a drain on batteries, and battery life is of particular concern when it comes to IoT devices. The low energy (LE) specification of Bluetooth came along to help alleviate issues related to battery life and offer an alternate model with less power consumption (as well as some additional features).
Whereas Classic Bluetooth is still primarily used for connecting wireless peripherals, BLE expands on that connectivity and supports additional use cases including indoor location services. Just a few of the BLE applications include:
- Connectivity for power-sensitive IoT devices such as medical monitoring devices and industrial sensors
- Connectivity of personal wearables
- Mobile applications with BLE location points of interest
- Mobile applications with BLE door entry systems in hospitality
Bluetooth up through version 5.3 also supports a mechanism to switch to Wi-Fi-based connections. A museum with BLE-enabled points of interest and a mobile app may make use of this; the museum visitors can move throughout the museum and receive exhibit-specific information based on their location. The app might then push a document or video down to the app and could use Wi-Fi for that transfer to make use of higher bandwidths than what's available through Bluetooth (a feature referred to as alternative MAC/PHY, or AMP).
Bluetooth vs. BLE
Devices may support both classic Bluetooth and BLE operations simultaneously. Due to the differing battery requirements and use cases, whereas Bluetooth is always connection-based, BLE can be connection-less, meaning devices can interact with one another through listening to beacons instead of formally connecting through pairing.
From a layer 1 perspective, both Bluetooth and BLE use the industrial, scientific, and medical (ISM) portion of the 2.4 GHz spectrum (also used by 802.11 Wi-Fi), but Bluetooth and BLE both use different spectrum hopping methods and channel selection algorithms to avoid interference with other devices in the same airspace, including Wi-Fi.
Network Connectivity and Addressing
Considering network topology and connectivity, Bluetooth does not use IP addressing. Instead, it relies on 48-bit addresses (like a MAC address), the first half of which specify the organizationally unique identifier (OUI), just as in Wi-Fi devices.
Bluetooth creates small piconets (up to 8 devices due to 3-bit addressing) and multiple piconets can then connect to form what's called a scatternet. On the other hand, BLE uses 24-bit device addressing and could (theoretically) support piconets with millions of devices—although in practice they're much smaller—but this speaks to the expanded use cases of mesh IoT devices such as many sensors.
Provisioning and BLE Secure Connections
Bluetooth and BLE both use similar provisioning processes, which include:
- Numeric comparison, where one device displays a short code that can be matched to the other.
- Passkey entry, which is available for devices capable of input. The central device can generate a PIN that can be entered on a joining device, or the PIN is set during manufacturing and manually entered on both devices.
- Just Works™, which is a very lightweight pairing that uses a null value during the key exchange, effectively offering only connectivity and no security during the pairing process.
- Out of band (OOB) pairing, which allows Bluetooth devices to use a different wireless protocol to exchange keys and sensitive data not appropriate for Bluetooth (such as medical or payment card data). OOB could be used to connect capable devices over Wi-Fi or NFC, for example.
By far, the least secure mechanism is Just Works, yet it's the default mode of operation in Bluetooth devices. Other modes can be susceptible to eavesdropping and man-in-the-middle attacks, depending on the version and implementation. For more on why Just Works doesn't work, read the IEEE whitepaper on BLE Just Works security vulnerabilities, “Bluetooth Low Energy Makes ‘Just Works' Not Work,” at https://ieeexplore.ieee.org/document/9108931.
BLE got a major bump in provisioning security with the BLE Secure Connections, introduced in version 4.2. With that, the devices use Elliptic Curve Diffie-Hellman (ECDH) key exchange, similar to many Wi-Fi operations. This addressed the problem of possible eavesdropping and man-in-the-middle attacks during the pairing process. The idea in legacy implementations was that the connection was only vulnerable during the pairing process, but the reality was that it introduced too great a risk for many of today's commercial and medical BLE applications.
An important note is that BLE 4.2 devices are compatible with older 4.0 and 4.1 versions, however the BLE Secure Connections operation is not—meaning if a more capable BLE 4.2 device is paired with a legacy device, it will not benefit from the increased security.
Speaking of encryption, the following modes are supported and in all cases AES-CCM mode is used after the devices are paired (through the secure ECDH or other mechanisms):
- Encryption disabled for all data
- Encryption enabled for unicast only
- Encryption enabled for all data
Bluetooth Exploits in the Wild
An Internet search will yield countless results for Bluetooth vulnerabilities. Here are a few that made recent headlines.
- BrakTooth and SweynTooth Throughout 2020 and 2021, researchers released numerous new findings exploiting even the more secure BLE 4.2 modules. In fact, the BrakTooth suite of attacks in late 2021 resulted in disclosure of 16 new security vulnerabilities on top of exploiting 15 already known.
The result? Everything from nagging denial-of-service attacks to full code execution on the Bluetooth-connected endpoints. Many of the devices tested included boards used in commercial products and industrial automation and monitoring, in addition to LED light controls and gaming systems.
Other devices impacted by the vulnerabilities include smartphones, tablets, and laptops, as Intel, Qualcomm, and others used affected chips. The attacks were executed with equipment totaling less than $20 USD.
The same researchers also released SweynTooth in 2020, discovering 17 new vulnerabilities. In those attacks, researchers were able to trigger crashes, buffer overflows, device locks, and even completely bypass security on BLE devices. These attacks, like BrakTooth, were tested on several chips including those used in smart locks, Fitbits, TSA-compliant luggage locks, smart plugs, and other smart home products. They were also found to be successful against other wearables and medical devices including a blood glucose meter and a Bluetooth-enabled pacemaker shown in Figure 8.8.
The group's research including BrakTooth and SweynTooth can be found at
https://asset-group.github.io/.
Figure 8.8: The Bluetooth-enabled Azure Medtronic pacemaker was just one of the many products vulnerable to the latest waves of Bluetooth and BLE attacks.
- Bluetooth Impersonation Attack Tested on more than 28 unique chips, the Bluetooth Impersonation Attack (BIAS) was successful on every device, including chips from Apple, Qualcomm, Intel, and Samsung. The vulnerability allows an attacker to impersonate any device that has been paired in the presence of the attacker.
- Hacked e-Scooter In one incident researchers were able to abuse a misconfiguration in Xiaomi brand electric scooters' Bluetooth authentication, and control scooters from 100 meters away—sending unauthenticated commands to lock (stop) scooters, brake, accelerate, and even deploy malware.
You can read a recap of the research and accompanying video “Xiaomi Electric Scooters Vulnerable to Life-Threatening Remote Hacks” at
https://thehackernews.com/2019/02/xiaomi-electric-scooter-hack.html.
Bluetooth and BLE attacks could go on for pages. My only reason for including these few examples is to demonstrate three points. First, even the newer versions of the BLE products are susceptible to attacks, and those attacks are non-trivial and can be life threatening in certain products. Second, the vulnerabilities are being disclosed almost daily. This proves the point that any specific guidance for Bluetooth and BLE specifically will be out of date quickly. Last, but not least, these attacks have been successful on popular wearables and smartphones (including Apple and Android), which further calls into question the use of peer-enabled protocols in a secure enterprise environment (a soapbox topic in Chapter 6).
I'm not suggesting organizations impose a moratorium on consumer devices, but they should be carefully considered, and the enterprise environment should be secured from these devices as best they can.
Smart Building and Home Automation
Aside from the ever-pervasive Bluetooth and BLE products, smart building and home automation products have evolved to use technologies based on the 802.15.4 physical layer such as 6loWPAN, Thread, and Zigbee—all of which differ from Bluetooth not only in the physical connectivity standard but also in coverage models.
Zigbee
Zigbee is the outlier here, being a non-IP-based protocol. Although a step up from Bluetooth, Zigbee has not gained the traction in large-scale deployments due to limitations of its mesh architecture and lack of IP stack. Because Zigbee (along with Bluetooth) doesn't use edge IP addressing, a translator is required to convert Zigbee protocol into IP protocol for forwarding or routing to and from IP-based networks.
Despite a few alliance agreements here and there, Zigbee has been fizzling out in recent years, replaced by newer, faster, and more scalable stacks like those based on 6loWPAN. Zigbee has been rebranded as part of the Connectivity Standards Alliance (www.csa-iot.org), along with Matter and other technologies.
Thread and 6loWPAN
Thread is one such communication stack based on 6loWPAN and therefore IPv6. All of these (Thread, 6loWPAN, and Zigbee) work on top of the 802.15.4 physical layer, which specifies tiny packet sizes of 127 bytes. The challenge is, IPv6 frames are about ten times that size at 1280 bytes. I'm about to switch from bytes to bits; one byte is eight bits. Also contributing to the length crisis, IPv6 addresses are long at 128-bits (for context, an IPv4 address is 32-bits).
6loWPAN is simply an adaptation layer that allows sending IPv6 over 802.15.4; it does this by compressing the IPv6 address and headers and handling fragmentation. Figure 8.9 offers a visual of the difference in ratios of IPv4 to IPv6 addressing and of the frame sizes of 802.15.4 versus IPv6. Effectively, 6loWPAN's task is to shrink IPv6 to about one-tenth its original size, in order to transfer it over 802.15.4.
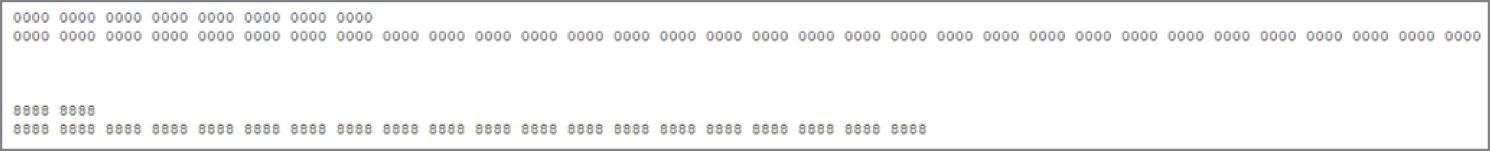
Figure 8.9: Visualizing the ratio of IPv4 to IPv6 addresses (top) and 802.15.4 packet size versus IPv6 standard packet size (bottom)
Figure 8.10 shows the Thread communication stack and the placement of 6loWPAN as the adaptation between layers 2 and 3 of the traditional OSI stack. Layers 1 and 2 of Thread (and 6loWPAN) use 802.15.4. Unlike Zigbee, Thread stops short of the application layer, allowing for extensible uses
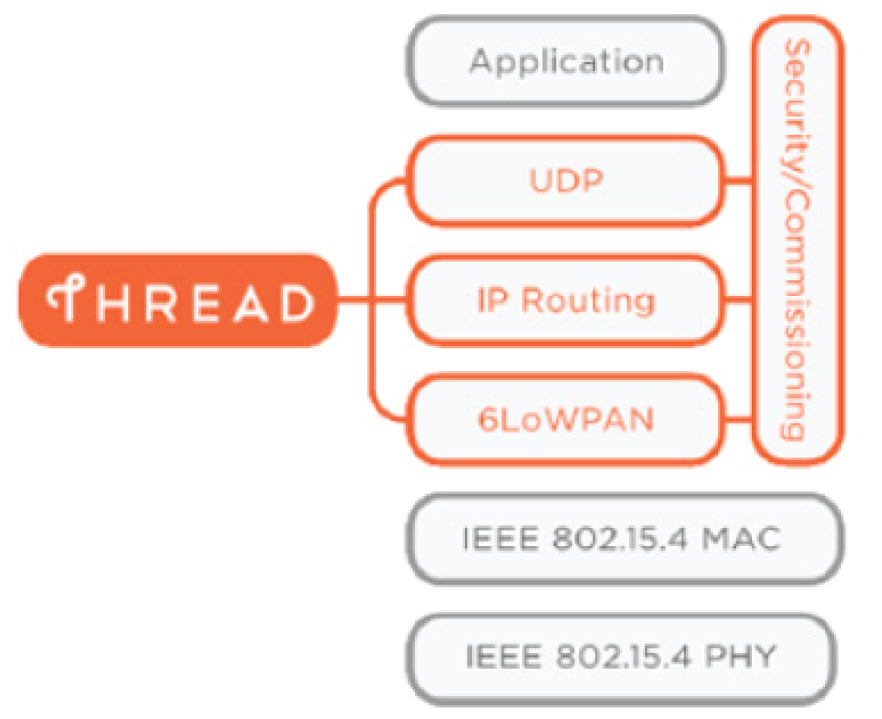
Figure 8.10: The Thread communication stack
The result of this stack and the IPv6 compression is that Thread (like many of its IoT cousins) requires a Thread-capable router to convert the local (compressed IPv6) addresses to something routable with full addressing.
I mention this because the language on the Thread Group site and documentation can be a little misleading and confusing, as it repeatedly notes there's “no need for a proprietary hub, gateway, or translator.” That's true but it (and any 6loWPAN communication) does require a border router to convert the addressing and shortened headers.
The best way I've heard it described is like network address translation (NAT). If you contrast the private IP address space with publicly routable IP address spaces, the private address (such as 192.168.1.12) wouldn't be able to communicate directly with 4.2.2.2. Instead, it would go through a router or firewall that would convert the source and destination addresses so the publicly routed data can find its way back to the private IP address.
There is a major difference between 6loWPAN and non-IP technologies like Bluetooth and Zigbee. The border router is just that—it's routing the packets to and from the local (compressed) IPv6 addressed endpoints. Bluetooth and Zigbee aren't speaking IP at all, and their traffic must fully be translated to IP to interact with IP networks.
Public Cellular for IoT
As with everything else IoT-related, cellular connections needed a rework to be IoT-friendly. Standard cellular communication protocols are designed for high-bandwidth and low-latency data applications like video and voice, but IoT devices require much smaller bandwidth, and many want shorter communication time to preserve battery life.
Cellular IoT protocols address needs of:
- Low power utilization
- Low cost
- Reduced transmission frequency
- Extended connectivity ranges
- Low bandwidth
Public cellular (as opposed to private cellular, covered next) operates in licensed RF spectrums by mobile network operators (MNOs, or carriers). All current cellular technology is packet-switched, and IP-based for voice, data, and messaging.
Table 8.3 summarizes the recent generations of cellular technologies. Technically 4G-LTE is the marketing term for an enhanced version of 3G, and not full 4G. 4G-LTE, while much better than 3G, never met the specifications for 4G by the ITU Radiocommunication Sector (ITU-R), but it allowed older phone technologies to take advantage of faster speeds. The use of 4G LTE has become mainstream now since consumers tend to associate it with something better than just “4G.” The standards are a little fuzzy in cellular all around. Today's 5G deployments are non-standalone (NSA) deployments that rely on a 4G network core, meaning just like 4G, our 5G isn't really 5G quite yet.
Table 8.3: Cellular generations and technologies
| GENERATION | TECHNOLOGIES |
|---|---|
| 3G (~2000) | UMTS, CDMA2000 |
| 4G (~2010) | LTE- Long Term Evolution |
| 5G (~2020) | NR - New Radio |
Cellular standards are managed by the 3GPP group (www.3gpp.org), which has a similar relationship to cellular standards as the IEEE does to 802.11. We hear about entire generations of cellular such as 3G, 4G (and 4G LTE), and 5G (NR), but in between these major families are smaller revisions and updates. In these releases, starting in 2008, 3GPP has introduced options to support IoT needs with direct cellular connectivity.
For context, the 5G in the wild now is release 15, which is considered phase 1. Phase 2 is attached to release 16, where the 5G benefits are to be fully realized based on the specifications. Release 17 will expand on 5G with industry-specific features; it was due for release late 2021 but 3GPP put the work on hold hoping to resume in-person meetings, and the new dates were mid-2022.
The technologies described here are all based on 4G/LTE, with the exception of Category NB1, which is 5G-ready as well. Within the realm of IoT-friendly cellular are those shown in Table 8.4.
Table 8.4: Excerpt of 3GPP releases and IoT-friendly classes
| RELEASE | CATEGORY | MAXIMUM DOWN/UP | BANDWIDTH | FEATURES AND USE CASES |
|---|---|---|---|---|
| 8 | 1 | 10 / 5 Mbps | 1.4 - 20 MHz | Higher bandwidth, lower latency: use cases digital signage, audio/video |
| 12 | 0 | 1 / 1 Mbps | 1.4 - 20 MHz | First major IoT enhancement with power saving and reduced throughput |
| 13 | NB1 (NB-IoT) | 0.68 / 1 Mbps | 180 KHz | Support endpoints that don't roam; half duplex; very low bandwidth; low energy; use cases smart metering |
| 13 | M1 (eMTC) | 1 / 1 Mbps | 1.4 MHz | Supports endpoints that roam/move; enhanced power save modes; use cases outpatient monitoring, asset tracking |
Cat-1 supports higher bandwidths and lower latency (great for IoT with voice or video) than the other IoT protocols but is based on standard LTE protocols and therefore doesn't offer the power and range benefits introduced later.
Among other issues, the challenges with cellular technologies for IoT is that they're designed for a certain level of interaction with the endpoints, which is not conducive to IoT devices that need long sleep times to preserve battery.
The remaining categories from the table (Cat-0, NB-1, and M1) all include significant changes to accommodate IoT, especially in the realm of power saving, with NB-1 supporting deployments with 10-year battery life.
Each of the standards come with pros and cons, and therefore are appropriate for different use cases.
As the world transitions to 5G technology, network function virtualization (NFV) and software-defined networking (SDN) allow for much more flexibility for use case support. Combined, these support technologies such as network slicing, which allows 5G radios to service multiple devices with unique needs, simultaneously. If one device is a tiny IoT sensor that communicates infrequently and in short, small bursts and another device is using high bandwidth to support virtual reality (VR), 5G will be able to manage those needs independently with proper power, range, and bandwidth that's device-specific.
That brings a marked change to how IoT has been handled in 3G and 4G, and it opens up Pandora's box of IoT use cases. Figure 8.11 shows conceptual 5G network slices serving both a low-bandwidth IoT device and a high-bandwidth streaming media device. The cellular radio can adjust to meet the disparate power, bandwidth, and range demands of both at the same time.
Figure 8.11: 5G network slices can divvy up airtime and bandwidth to meet varying needs.
Private Cellular and Cellular LANs
We're switching gears here from IoT technologies supported by public cellular network carriers to the use of private cellular technology including the use of cellular within the enterprise LAN.
Private cellular solutions are designed for private use—meaning an enterprise organization has local infrastructure for its own connectivity. It's not shared with public users, and not meant for Random Randi Person walking through the building with their Vodaphone or Verizon device. Technically, there's one exception to this: an organization with a private cellular infrastructure could choose to deploy a neutral host network, but that's purely optional and outside the scope of this book.
Use cases for private cellular and cellular LANs include:
- Healthcare monitoring, collaboration, and paging
- Manufacturing autonomous guided vehicles
- Educational institutions' long-range backhauls for in-home student connectivity
- Retail point of sale and digital displays
- Push-to-talk applications in any vertical
- Smart building connectivity
- Security and facilities indoor, outdoor, and backhaul connectivity
Private cellular LAN is the new kid on the wireless block, but it's growing quickly. Private cellular networks take cellular connectivity features and bring them into the organization for use as a local network, hence the term cellular LAN.
In some regions, a full private cellular deployment doesn't have to involve a mobile network operator (MNO), or carrier, at all. Instead, the organization may own and manage its own cellular LAN infrastructure, and the data isn't required to be passed over a carrier network. Effectively, it can be used just like an 802.11 WLAN but using cellular technology.
I'll spend a bit more time on the topic of cellular LANs than other technologies since it's very likely network and wireless architects across many industries will be involved in planning and/or deploying private cellular in the coming years. Figure 8.12 offers a simplified view of a cellular LAN. Not pictured is the cellular packet core (a bit like a souped-up Wi-Fi controller), which may be located on-prem, or in a public or private cloud.
Figure 8.12: Cellular LANs are deployed much like Wi-Fi.
This overview of private cellular technology covers the following:
- Current State of Private Cellular by Country
- Deployment Models and Architectures
- Service Delivery Options
- Licensing and Spectrum Utilization
- Comparison of Cellular to Wi-Fi
- Considerations for Private Cellular
Current State of Private Cellular by Country
If you haven't heard of private cellular networks yet, it's probably because spectrum for this use case is just now being opened up around the globe.
The following is the current state as of early 2022, with the expectation that by the time you're reading this, the status for some countries will have changed.
In the U.S., the designated RF for private cellular is the Citizens Broadband Radio Service (CBRS) spectrum—in the 3.5 GHz band nestled neatly between 2.4 GHz and 5 GHz without interfering. On that spectrum, we can use both 4G and 5G technology.
Outside of the U.S.—Japan, Norway, Germany, the Netherlands, Poland, and Sweden—have all identified spectrum for private cellular use. Following a slightly different model, Australia, China, France, the Czech Republic, along with Hungary, Portugal, South Africa, and Spain offer leased spectrum for private cellular use. As of writing, spectrum allocations in Canada, Mexico, Brazil, and Turkey are to be determined.
Throughout Europe, many EU member countries have specified or are considering use of frequency bands n77 and n78 for 5G private networks. These operate in the 3.4-3.8GHz and 3.8-4.2GHz spectrums for n78 and n77, respectively. The UK has settled on n77 as well as band 40 and is exploring additional spectrum.
Deployment Models and Architectures
Cellular technologies have their own vernacular and architecture that doesn't correlate directly to Wi-Fi, aside from the concepts of radios in a cellular Radio Access Network providing connectivity conceptually as a Wi-Fi AP would. Behind the radios are a packet core in cellular, which offers a breadth of authentication and coordination functions. The packet core could be likened to a Wi-Fi controller but that's a grossly overly simplified correlation.
The two areas I want to cover are the deployment architectures and models that describe how private cellular is used, and how it may be integrated into the existing enterprise LAN:
- Deployment Architectures
- Deployment Models
- Deployment Architectures Deployment architectures describe how, when, and where private cellular networks are used within an enterprise.
- Private Cellular LAN for Endpoint Connectivity Private cellular can be deployed as a cellular LAN, offering endpoint connectivity both indoor and outdoor. This most closely mimics an 802.11 WLAN, with the notable exception that the RF technology used is not based on 802.11 standards.
Endpoints connecting directly to a cellular LAN require either a physical SIM card, a software-based eSIM, or an adapter/dongle.
The upcoming section “Comparison of Cellular to Wi-Fi” will offer more details about how cellular LAN compares to Wi-Fi.
- Private Cellular Backhaul and Fixed Wireless Private cellular can be deployed in fixed wireless and backhaul architectures as well. In these deployments the goal is to offer point-to-point or point-to-multipoint connectivity acting as a wireless bridge, versus servicing endpoints directly.
One deployment option is to use private cellular over a distance to connect to remote gateways that can convert cellular to Wi-Fi. The use case of this architecture would be a municipality or school that may want to extend Internet access to employees or students in rural areas without reliable broadband access. Municipalities and various commercial organizations also use remote gateways to service endpoints in hard-to-reach locations where wired cabling is not possible or is cost prohibitive. Endpoints in this use case include video cameras, IoT sensors, and remote payment kiosks such as parking meters.
- Deployment Models Deployment models describe the level of integration into the enterprise LAN, and the option to extend services between the cellular and traditional LANs.
Private cellular LAN integration is vendor-dependent, as some offer only overlay solutions that are fully managed, others offer enterprise-managed LAN-integrated solutions, as well as everything in between.
The architecture and management model will also influence cost. For fully managed services there's obviously an ongoing subscription fee. With consumption-based models (like Amazon Web Services), customers pay based on the level of capacity and throughput.
Regardless of the pricing models, current solutions can be loosely categorized into parallel, overlay or integrated LAN solutions.
- Parallel to LAN Many MNO-managed solutions are installed as a dedicated second network, parallel to the existing LAN. In this model, the cellular LAN infrastructure is deployed with a dedicated network infrastructure, cabling, and connectivity.
In this deployment model, there is no direct connection or integration between the private cellular network and the existing enterprise LAN. Traffic between the two networks would have to be routed externally. In this model, the cellular packet core is hosted and managed by the provider and is not located within the enterprise environment.
Within the realm of parallel solutions, the features and requirements may vary greatly. Some offerings are designed only for vendor-specific traffic (such as one offering from Motorola currently that prioritizes its voice and push-to-talk traffic only).
Considerations and variations in requirements for solutions deployed in parallel to the LAN include:
- Offerings may require dedicated cabling for cellular APs
- Some offerings require a full parallel infrastructure including switching, routing, and a separate broadband connection
- Offerings may be limited to specifying QoS for certain devices and applications
- Offerings with a remote packet core and no local handoff will introduce undesired hairpin routing and potential latency
- The provider will own and manage the packet core, meaning the enterprise does not have full control over the data or data paths for privacy
- Overlay to LAN Private cellular deployments that rely in part on the existing enterprise infrastructure may be deployed as an overlay to the LAN. From an architecture perspective, the overlay model falls between the parallel and integrated deployment models.
Depending on the solution, the packet core may be located within the enterprise environment, or it may be offsite and managed by the provider. Most overlay solutions will provide the RAN but rely on the enterprise's existing switching, routing, and Internet connections.
Considerations for overlay solutions include many of those covered previously in “Parallel to LAN,” and some items from the upcoming section on “Integrated to LAN” also apply.
- Integrated to LAN Solutions that can be fully integrated to the enterprise LAN bring several benefits, and I'm partial to these solutions personally, whether delivered as fully managed solution or not.
In broad terms, with a cellular LAN solution, it may be integrated to the LAN in a few ways. And, more specifically, a fully featured solution will offer use of all integration options on a per-use case basis—similar in concept to how we're able to tunnel or bridge Wi-Fi traffic, except we're talking about the handoff between the cellular packet core and the LAN.
Currently available options to integrate the cellular LAN to the enterprise LAN include core handoffs that can:
- Bridge cellular traffic to the LAN
- Route cellular traffic to the LAN
- NAT cellular traffic to the LAN
One or more of these handoff techniques can be used based on the needs. Aside from the data paths, other integrations to the LAN and network services may include the following:
- DNS
- DHCP
- Specifying authorization from enterprise RADIUS/AAA
- Mapping endpoints to enterprise VLANs
- Applying ACLs to cellular LAN traffic to and from the enterprise LAN
For solutions that are integrated, the level of integration will vary by vendor. Some may offer basic local handoffs, while others offer deeper integrations with network and domain services including RADIUS.
Figure 8.13 shows how cellular LANs can be integrated into the enterprise LAN including support for routing to/from the LAN, bridging to VLANs, and NAT.
- Parallel to LAN Many MNO-managed solutions are installed as a dedicated second network, parallel to the existing LAN. In this model, the cellular LAN infrastructure is deployed with a dedicated network infrastructure, cabling, and connectivity.
- Deployment Models Deployment models describe the level of integration into the enterprise LAN, and the option to extend services between the cellular and traditional LANs.
- Private Cellular Backhaul and Fixed Wireless Private cellular can be deployed in fixed wireless and backhaul architectures as well. In these deployments the goal is to offer point-to-point or point-to-multipoint connectivity acting as a wireless bridge, versus servicing endpoints directly.
- Private Cellular LAN for Endpoint Connectivity Private cellular can be deployed as a cellular LAN, offering endpoint connectivity both indoor and outdoor. This most closely mimics an 802.11 WLAN, with the notable exception that the RF technology used is not based on 802.11 standards.
Figure 8.13: Cellular LANs can be integrated into the enterprise LAN several ways.
- The deployment model (overlay or integrated) will dictate how tightly the services of the enterprise LAN and cellular LAN can be integrated. Obviously, in a pure overlay model with all traffic routed out to the Internet (and back into the enterprise if needed), the options for integrating services such as VLANs and RADIUS are limited.
Service Delivery Options
As with all topics in this chapter, the status of private cellular is in flux almost daily and varies by region. The statements about service delivery models are generalizations based on what's in the market today:
- Managed Service by a Mobile Network Operator
- Managed Service by a Third Party
- Enterprise-managed
- Managed Service by a Mobile Network Operator Private cellular solutions may be offered by MNOs, and in some regions that may be the only option. A main consideration for MNO-provided private cellular is the privacy of the enterprise data. Just as with public cellular data, if an MNO is in control of, or has visibility into the enterprise data or metadata, there is opportunity for them to share or monetize that. It's also possible the contract may include clauses affording the MNO additional liberties. Reviewing the contract and privacy statements is always advised with any managed service, whether from an MNO or any third party. Most MNO-provided solutions follow the parallel to LAN deployment model.
- Managed Service by a Third Party Private cellular solutions can also be provided as a fully managed service by non-MNOs and other third parties. In these instances, the infrastructure is managed by a third party, but the third party is not an MNO. This can assuage some of the data privacy and performance concerns of MNO-provided offerings, but as always, check the contracts carefully.
Managed deployments may be fixed-fee models or based on consumption. Check the billing structure carefully, as some services include billing for data that stays within the enterprise.
Fully managed deployments are vendor-specific, and some may impact the options for integration into the enterprise LAN, offering only an overlay option. At least today, backhaul and fixed wireless solutions are most often provided as managed services.
Managed solutions range in level of touch and control. Some providers may not allow enterprise IT teams to manage or co-manage the cellular LAN or endpoints at all, while others offer more flexibility.
- Enterprise-managed In many regions, a private cellular solution can be deployed and/or managed by the enterprise IT team. This is especially easy with cellular LAN deployments where the solution can be managed very similarly to Wi-Fi.
For enterprises that wish to manage their own infrastructure, the requirements vary by region. Some require license and certification for specific use cases. For example, deploying CBRS in the U.S. requires involvement from a CBRS Certified Professional Installer (CPI). The level of touch depends on whether the solution is deployed indoor or outdoor.
Licensing and Spectrum Utilization
Private cellular technologies can run in licensed spectrum, unlicensed spectrum, and shared spectrum with different models:
- Leased licensed spectrum
- Shared/coordinated spectrum
- Other dedicated spectrum
- Unlicensed spectrum (supported but not widely used)
As a comparison, public cellular (like your mobile phone) operates in licensed RF spectrums. Depending on the geographic region, private cellular may operate in licensed, unlicensed, or lightly licensed (shared) spectrum.
- Leased Licensed Spectrum Today's cellular connectivity uses allocated spectrum that's licensed to various carriers. RF spectrum is managed per region or country. MNOs can lease portions of their licensed spectrum to an enterprise or entity for private cellular.
- Shared/Coordinated Spectrum Private cellular in many regions including the U.S. uses a “shared” or lightly licensed spectrum that relies on coordination services, which are always subscription-based. In the U.S. the dedicated spectrum is CBRS, or LTE band 48. As you'll see in “Comparison of Cellular to Wi-Fi” this sits around the 3.5 GHz spectrum.
Specifically for CBRS, there are three tiers of access prioritization: incumbents, priority, and general. Incumbents are afforded the highest priority and include fixed satellite services, radar, and defense. Priority access licenses (PALs) are available for a portion of the dedicated spectrum. PALs are bid on regionally and those entities are given higher priority than general access (for that spectrum). General access is the level most used for localized cellular LANs and is everything else that isn't formally registered as incumbent or priority.
Since it's coordinated spectrum, to enforce the three access tiers CBRS includes a central coordination system called Spectrum Access System (SAS).
- Other Dedicated Spectrum In some regions, private cellular uses dedicated spectrum that's not necessarily shared or coordinated but is also not a slice of an existing MNO spectrum. This varies by country and is in flux. For example, in the UK, spectrum may be applied for and granted for a small fee. The model is similar to coordinated spectrum but is static in nature through the manual application and allocation process.
- Unlicensed Spectrum (Supported but Not Widely Used) It is also possible to deploy private cellular in unlicensed spectrums (as Wi-Fi does). This is supported by technology such as MulteFire but is not widely used. Using cellular technology on unlicensed spectrum forces it to behave more like Wi-Fi, which negates many of the RF benefits of cellular.
Comparison of Cellular to Wi-Fi
In many cases, cellular technology can offer specific advantages over other wireless. If you reflect for a minute on the different experiences you've had with mobile phones versus Wi-Fi, you'll begin to understand some of the advantages cellular connectivity might bring.
From an RF perspective, private cellular can offer more resilience and coverage than Wi-Fi. It can also operate at higher density, longer distances, and in harsher (RF) noise environments, making it ideal for certain applications. Plus, cellular has guaranteed QoS and SLA due to scheduling versus Wi-Fi's contention-based operation. This feature alone has a significant impact on the reliability of the connection and support for latency-sensitive applications.
Table 8.5 touches on a few technology comparisons of private cellular to 802.11 Wi-Fi technology. As always, there are many other factors to consider when deciding what wireless connectivity is best for a given use case. This information is selected to demonstrate the drivers behind moving some enterprise applications from Wi-Fi to private cellular or cellular LAN connectivity.
The details following Table 8.5 focus on comparisons of:
- Distance/Coverage
- RF Resiliency, Spectral Efficiency, and Interference
- Device Identity and Authentication
- Transmission Scheduling, QoS, and Roaming
- Access Hardware
- Supporting Clients
- Traffic/Data Path
Table 8.5: Private cellular vs. Wi-Fi
| FEATURE | PRIVATE CELLULAR | TRADITIONAL WI-FI |
|---|---|---|
| Coverage distance | Long, Kms (~25k sq ft / 2k sq m indoors; 1M sq ft outdoor) | Short, meters (~2k sq ft /180 sq m indoors and varies outdoor) |
| Resiliency on RF | High resiliency | Medium-low resiliency, depends on network design |
| Device identity and authentication | Inherent and mutual / SIM-based | Configured with services, profiling, authentication server, user login, passphrases, or certificates |
| Device density | High | Low |
| RF spectrum | Varies by region (dedicated 3.5 GHz CBRS band in U S ; shared/coordinated); some countries use public cellular licensed RF | 2.4 GHz, 5 GHz, 6 GHz |
| RF interference impact | Low/limited, depends on spectrum | Medium-high; all Wi-Fi devices and others on spectrum above, including microwaves, Bluetooth |
| Transmission scheduling | Coordinated and guaranteed | Contention-based using CSMA/CA |
| Security | Native and integrated | Overlay, varies |
| QoS | Integrated and configurable | Configurable, varies by Wi-Fi vendor and deployment |
| Roaming & latency | Seamless, very low latency | Varies greatly by deployment and endpoint capability |
| Access hardware | NodeB cellular AP | 802.11 Wi-Fi AP |
| Supporting clients | Most phones, tablets, many laptops, growing number of handhelds and IoT devices, all tested for conformance and interoperability | All 802.11 endpoints (ideally Wi-Fi Alliance certified but remains optional) |
| Traffic/data path | Depends on deployment and region but can be LAN -> WAN and/or ISP | LAN -> WAN and/or ISP |
There's a lot to unravel here, so let's look at a few of these comparisons and offer additional context. For readability, some topics in Table 8.5 will be consolidated and detailed together, and others are omitted from further explanation. The highlights are as follows:
- Distance/Coverage Layers 1 and 2 of cellular are substantially different than Wi-Fi. The different modulation and encoding techniques mean cellular signals are viable well beyond the threshold of Wi-Fi.
We describe how well a wireless signal can be heard over the ambient noise floor in terms of decibels (dB), as a relative signal strength. The absolute power is defined in units of dBm (decibels relative to a milliwatt), which is a logarithmic (not linear) scale. Without boring you to death with RF math, in Wi-Fi we usually design for something in the neighborhood of –65 to –75 dBm, which gives us a net positive of around 15 dB signal above the noise floor.
Cellular technologies use small subcarriers, which means the endpoint can still receive and decode data with much weaker signals. By comparison, 4G/LTE coverage may be designed in the –95 to –110 dBm range. Both Wi-Fi 6 and LTE are using orthogonal frequency-division multiple access (OFDMA) modulation but applied differently. In addition, cellular clients can transmit at a higher power than Wi-Fi, meaning they can communicate farther distances from the radio.
The result is that a single 4G/LTE eNodeB (cellular AP) can cover three to four times the area as Wi-Fi indoors, and ten times the area outdoors. That's significant.
As an example, Figure 8.14 shows a vendor's budgetary network planner for a 500,000 sq ft convention center. This tool offers a rough estimate and doesn't take the place of a proper design, but the output estimates just 22 cellular APs, versus what would easily require over 125 Wi-Fi APs (and that's being very generous to Wi-Fi).
- RF Resiliency, Spectral Efficiency, and Interference Proper Wi-Fi design can get complicated quickly. The 2.4 and 5 GHz RF spectrums used by Wi-Fi are crowded, and the transmission is contention-based (something covered in “Transmission Scheduling, QoS, and Roaming” shortly). In addition, in Wi-Fi, it's the endpoints that make decisions about roaming and connectivity. There are numerous roaming protocols, and not all endpoints support all protocols, further adding complexity.
The combination of the spectrum interference, contention mechanisms (endpoints having to fight for airtime), and the often unpredictable behavior of endpoints render the resilience of Wi-Fi over the air quite volatile.
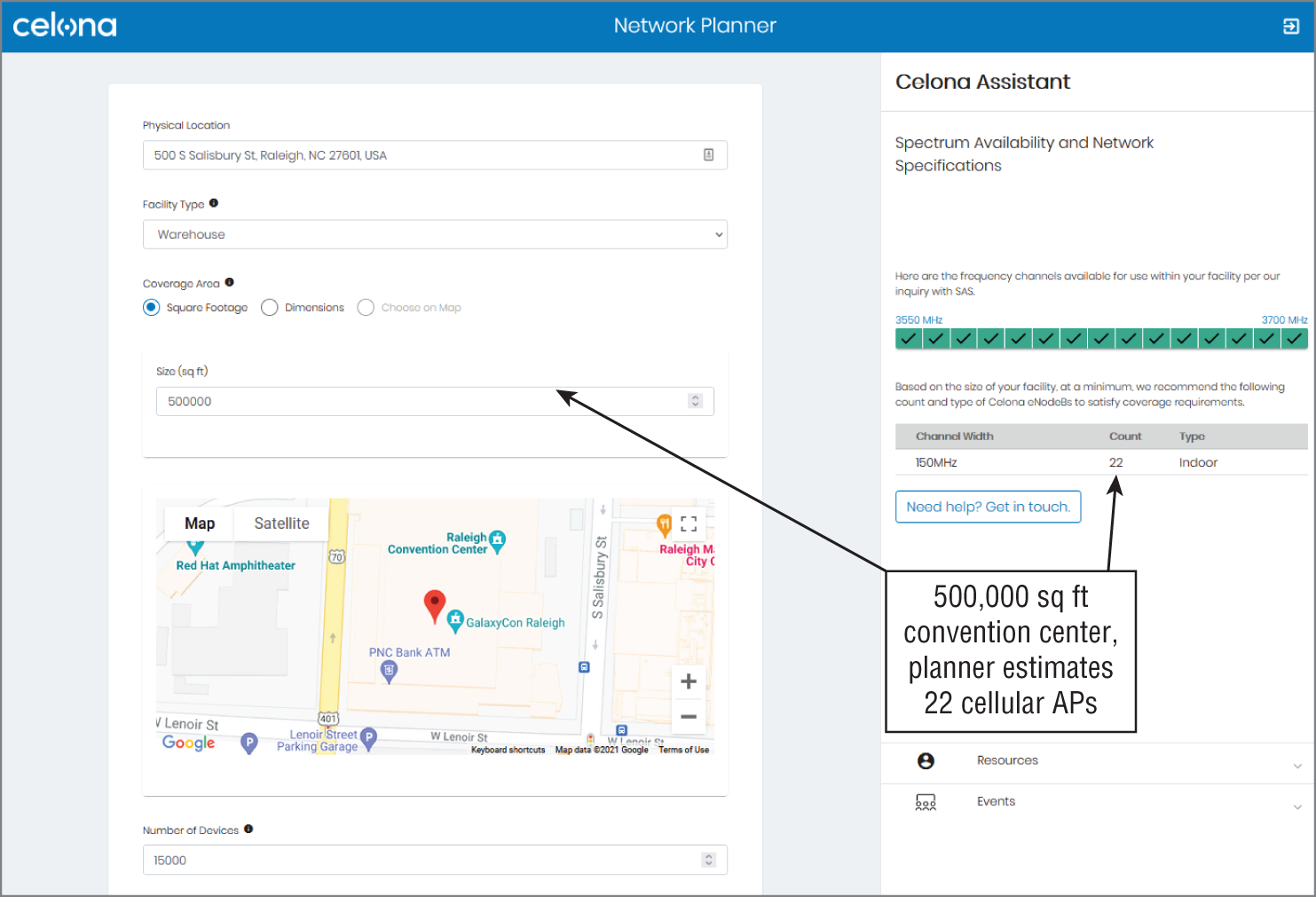
Figure 8.14: As an example of the coverage capabilities, this vendor’s rough estimate for a 500,000 sq ft facility is just 22 cellular APs.
Conversely, private cellular technologies work in a less cluttered (at least for now) and a more strictly managed spectrum, include guaranteed scheduling of transmissions, enforce system-coordinated roaming, and (as described in the prior section) can operate effectively with much weaker signal strength. The system coordination extends to spectral efficiency as well; in cellular, the coordination by the cellular APs allows for spectrum re-use and very granular scheduling. This brings the added benefit of allowing for much denser endpoint populations in the same airspace and even on the same radio.
- Device Identity and Authentication As someone who's worked with network access control (NAC) technologies for many years, device identity and authentication is always a pain point. Earlier in this chapter, challenges with endpoint identity and authentication were captured in “LAN-Based IoT.”
In Wi-Fi, if an endpoint doesn't have a user attached, we don't always know what it is—an especially daunting task with the insurgence of IoT in the enterprise. Simply identifying a device becomes a complex dance of profiling mechanisms and parsing network traffic from DHCP requests and/or mirrored ports. The level of assurance varies, and at best the IoT endpoints have an assertion of identity (most often based on MAC address), and rarely, if ever, true authentication. IoT endpoints that support device certificates are the rare exception.
Cellular technologies, public and private, use unique identifiers coded into the hardware and linked to a physical SIM or software-based eSIM. The identity is immutable, and private cellular endpoints are known and provisioned, meaning the enterprise knows exactly what something is without guessing. In addition, the unique device IDs along with cryptographic keys are used for mutual authentication between the cellular endpoint and the network.
- Transmission Scheduling, QoS, and Roaming As hinted earlier, in Wi-Fi, the endpoints are in control of their wireless experience. They make decisions about which APs to connect to, when and how to roam between APs, and they're active participants in the contention-based processes for securing airtime to transmit.
Cellular technologies operate the other way around; the infrastructure is in control of when and how the endpoint connects, when it transmits, as well as when, how, and to where it roams.
That coordination is made possible by the mandatory RF feedback loop in cellular technology using channel quality indicator (CQI). These metrics let the cellular infrastructure know the RF conditions as experienced by the endpoint. That data allows the infrastructure to direct the endpoint to use the best client modulation through adaptive modulation and coding (AMC). The process can be compared conceptually to 802.11k and 802.11v in Wi-Fi with the understanding that client support of Wi-Fi protocols is optional and the experience inconsistent.
- Because of that one fundamental differentiator, cellular is able to guarantee time slots and create an environment of predictable performance. It's a good fit for applications that are latency-sensitive or require strict service level agreements (SLAs) and QoS. In fact, not only does cellular have an absolute command of the scheduling, but 5G technologies introduce network slicing and support QoS over the air to a great degree.
As you've probably learned through your journey with this book, Wi-Fi can get pretty dang complicated. Even on its best days, Wi-Fi networks will have collisions, congestion, and large variations in performance due to 802.11 contention mechanisms. Clients do what they want and often operate off-standard. Toss in the occasional monkey wrench of poor RF design, hidden node, and misbehaving clients, and it's a mess.
When it comes to roaming, the variability with Wi-Fi endpoints is just as troublesome. There are numerous standards and variations in endpoint support for Wi-Fi. Certifying devices (infrastructure and endpoints) with the Wi-Fi Alliance is purely optional, and even for vendors that pursue it, they may opt for the lowest requirements and not test and certify critical features such as Fast BSS Transition for secure roaming and WPA-Enterprise operation to support 802.1X.
In Chapter 4, in “Understanding Wi-Fi Design Impacts on Security,” we took a deep look at the roaming technologies in Wi-Fi and the supplemental protocols required to facilitate fast and secure roaming between APs on encrypted networks. That same section discussed at length the challenges with supporting both security and speed and the resulting common use of less secure networks to support low-latency applications.
Cellular has been designed to support voice and has inherent mechanisms for ensuring both QoS and seamless, low-latency roaming.
- Figure 8.15 demonstrates the roaming decisions in Wi-Fi (by the endpoint) versus roaming in cellular where the packet core makes the decision about endpoint roaming.
Figure 8.15: Comparison of roaming decisions on Wi-Fi (left) versus cellular and cellular LANs (right)
- Access Hardware Where Wi-Fi has APs, cellular access radios are referred to as NodeBs, specifically eNodeBs in 4G, and gNodeB in 5G (for Evolved NodeB and Next Generation NodeB, respectively).
You'll also see references in cellular terminology to a packet core or mobile core. In private cellular LANs, this is a virtual or physical appliance that acts much like a Wi-Fi controller. It handles many functions like managing the cellular APs, authentication, routing, and applying QoS policies and access control policies.
Figure 8.16 offers a view of both an indoor and outdoor cellular AP. Very similar to Wi-Fi APs, most cellular nodes (or cellular APs) run on PoE and standard cabling. Unlike Wi-Fi the reach of private cellular is much greater, especially outdoors.

Figure 8.16: Cellular nodes (or cellular APs) look and operate very much like Wi-Fi APs. Pictured here are two models from Celona, one outdoor and one indoor, along with SIM cards.
- Supporting Clients One area Wi-Fi has a huge leg up on cellular is with the breadth of endpoints that support Wi-Fi, but that's been changing since 2020. It's obvious that mobile phones and many tablets have cellular support, but what's less obvious is that many of today's laptops support it as well.
Endpoint adoption of the CBRS (band 48) in the U.S. has jumped significantly, and other regions of the world are following suit. To date, just some of the devices that support CBRS include Apple iPads; Dell, HP, and Lenovo laptops; Microsoft Surface devices; Panasonic rugged laptops; Zebra and other handheld scanners, and chipsets from Qualcomm.
For devices that don't natively support SIM, eSIM, or have private cellular radios, there are adapters that can be used with most IP devices to convert them to cellular endpoints.
- Traffic/Data Path With cellular LANs, the data path can be identical to an enterprise Wi-Fi data path. And, depending on the vendor, it can be far more flexible than that of traditional controller-based APs. Cellular's use of NFV and microservices means the core duties could be distributed and virtualized on-prem or in a public or private cloud.
Security and Privacy in Private Cellular
Cellular brings several advantages in terms of security. Its inherent device identity offers the foundation required for data confidentiality and integrity. Looking back to the IAC (integrity, availability, and confidentiality) triad of infosec, cellular can help in all three aspects, and can do it natively, without requiring external products or services.
In the prior topics I've shared several bullets and explanations of the possible security benefits of cellular technologies. There are a few additional points and overarching themes to call out for private cellular LANs specifically.
- Identity, Authentication, and Encryption Cellular has inherent strong device identification and authentication using SIM/eSIMs, eliminating the need to “guess” what mystery endpoints are for specifying access control. This is also used for strong encryption over the air and extended through to the packet core and beyond.
Cellular LAN products can come pre-hardened, and most can offer added integrity through authentication of the system components to one another, natively—meaning the endpoints authenticate to the cellular APs (or NodeBs), which in turn authenticate to the core, which authenticates to a central management platform, if applicable.
Most private cellular deployments support the same AES-128 bit encryption comparable to WPA3-secured networks, with AES-256 on the near horizon—encryption comparable to the WPA3-Enterprise 192-bit, CNSA suite. In the Wi-Fi ecosystem, to get the same level of integrity and confidentiality requires the addition of NAC-type products, and/or a PKI infrastructure with device certificates.
- Segmentation Also, cellular (especially 5G) has intrinsic segmentation over the air and private cellular systems can extend this end-to-end throughout the LAN infrastructure. Some products can slice and encrypt over the air at the granularity of a single flow.
Segmentation can be extended to or through the enterprise LAN, depending on the product and implementation. With integrated solutions, the cellular slice or segment can be carried through to the wired side and handed off to the LAN just like any other wired or Wi-Fi traffic, and segmentation can be preserved, changed, or modified at that point, based on policy.
- Data Privacy Integrated cellular LANs have the potential to keep enterprise data in control of the organization and eliminates privacy concerns related to passing data through carriers/MNOs or other managed service providers.
The privacy statements are vendor- and deployment-dependent. Solutions offered by MNOs and/or as a fully managed service by a third party may have visibility into certain aspects of the data or metadata.
As with all hosted services, read and vet the provider's privacy statement that details how your organization's data privacy will be maintained, and whether the provider may be giving or selling data to third parties.
- Centralized Security and Risk Management Cellular LANs that can be integrated to the enterprise LAN aid in centralizing visibility and control, allowing organizations to maintain security compliance and incorporate IoT connectivity into existing risk management models and zero trust strategies.
Private WANs
There are many types of IoT WAN technologies, and most fall into the low power WAN (LP-WAN) category. Cellular IoT technologies also fall in this bucket, but the private WAN technologies differ in their use of proprietary, non-standard, or unlicensed connectivity over long distances.
Private WAN technologies, like other LP-WANs, offer connectivity over coverage areas ranging from municipal- to nation-wide. I'm omitting the spectrums for these since they vary per region.
These and other LP-WANs are used to connect IoT devices including over longer distances, and specific use cases include:
- Agricultural, for monitoring weather conditions, silo and tank levels, soil data, and temperature
- Smart buildings, including smoke alarms, security alarms, monitoring for rodent infestation, and garbage collection
- Smart cities, for monitoring water facilities, management of street lighting, structural integrity sensors, parking management, and connected digital signage
- Logistics, for tracking vehicles, warehouse security, and food safety monitoring
- Utilities, including consumption meters, remote facility monitoring, supply monitoring, and surveillance
Two private WAN technologies are Sigfox and LoRaWAN. I'm only providing a brief overview of these technologies because they (and the next topic of industrial automation) are a bit more of a niche than the other technologies here.
- Sigfox Sigfox wholly owns the connectivity technology from the cloud services to the endpoint software, offering the solution much like a carrier model. The endpoint hardware, though, is open market.
Sigfox enjoys a much larger client base in Europe than the U.S. and other parts of the world (see Figure 8.17). Among other challenges, in the U.S., the designated 900 MHz frequency is a bit crowded, and the FCC limits the time-on-air. Also, only one Sigfox network can be deployed in any area, which is limiting. Originally designed for unidirectional sensor communication, it has limited bidirectional support.
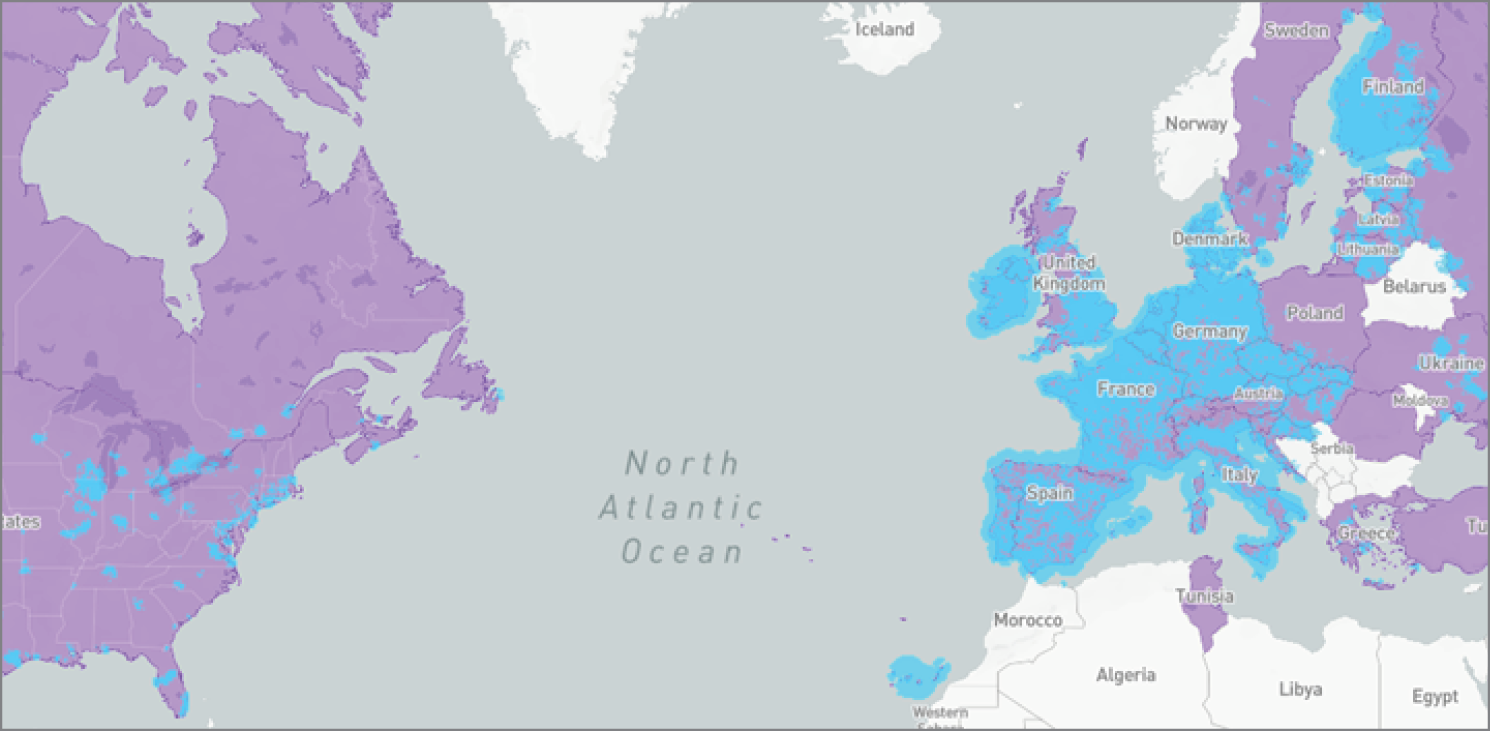
Figure 8.17: Sigfox adoption is focused in about a dozen European countries and a few smaller Asian countries, shown in the medium grey tones such as France and Germany.
- Although Sigfox touts a presence in 75 countries, implementations outside Europe, Japan, South Korea, and Thailand are spotty, at best. In early 2022, Sigfox announced its intentions to file bankruptcy and seek a buyer, which will likely influence the future of this technology.
More information on Sigfox can be found at
www.sigfox.com.
- LoRaWAN LoRaWAN has similar use cases to Sigfox, but a business model that's opposite. The LoRa specifications are available for all to use through the LoRa Alliance, but there is only one hardware vendor for the LoRa radios—Semtech. For coverage context, the entire country of Belgium (12k sq mi/30k sq km) is blanketed with just seven LoRaWAN gateways. The LoRa Alliance can be found at
https://lora-alliance.org.
Recapping, Sigfox is a service offering and a platform that's wholly owned, and the radio hardware is open source. Sigfox manages the network as a service (just like a carrier) and charges based on an OpEx model. LoRaWAN, on the other hand, offers a fully open ecosystem but only one hardware vendor, and unlike Sigfox, enterprises can build and operate their own LoRa network.
There are many other technical differentiators such as the modulation, bandwidth, encryption, and uni- versus bi-directional communication models.
LoRaWAN specifies encryption using AES-128 and offers some enhancements such as separation of authentication and encryption keys. On the other hand, Sigfox doesn't encrypt messages anywhere in its stack—something left to the customer to address.
Industrial Automation
Ready for more acronyms? Industrial automation technologies covered here fall into the low-rate wireless personal area networks (LR-WPAN) category—not to be confused with the LP-WANs just covered. And these are also based on the 802.15.4 layers 1 and 2, along with 6loWPAN, Thread, and Zigbee covered earlier in the chapter.
While all of these collectively fall into the industrial-IoT (IIoT) heading, the two mentioned here—WirelessHART and ISA100.11a—are particularly well-suited for industrial automation, the convergence of operational technology (OT) with wireless IT.
Industrial automation technologies are used for many industry 4.0 applications in a few primary categories, including:
- Safety
- Monitoring
- Control
- WirelessHART and ISA100.11a WirelessHART and ISA100.11a are the two main industrial automation connectivity protocols. Both used for similar applications, the decision of which protocol to use comes down to vendor selection.
WirelessHART is the protocol of choice for vendors such as Emerson, Siemens, and ABB, among others. ISA100.11a is mostly supported by Honeywell and Yakogawa.
Because of that, it's unlikely the wireless or network architect will be in the position to specify the protocol, but here are a few key differentiators to consider when securing these networks.
- Network Topology and Security Both based on the 802.15.4 standard, ISA100.11a was primarily designed as a star topology, while WirelessHART uses mesh extensively. From a network management perspective, ISA100.11a supports administrative configuration of how devices and routers are allowed to communicate.
ISA100.11a doesn't define the full application stack and can therefore be extended to support Fieldbus, Profibus, HART, and other legacy protocols.
Another key differentiator is the use of IP protocols, with WirelessHART not using IP at edge devices, and ISA100.11a (like Thread) built on 6loWPAN and therefore IPv6 at the edge. And, although based on 802.15.4, both WirelessHART and ISA100.11a modified the layer 2 operations, meaning they're not strictly implementing the 802.15.4 standard.
Provisioning options are similar between WirelessHART and ISA100.11a, and both support a suite of security keys including join keys, network keys, and session keys. WirelessHART requires all keys, but ISA100.11a specifies join and session keys as optional.
The systems will ship with default keys to get started, but best practices entail creating new keys and exchanging them out-of-band to prevent eavesdropping and exposure of the keying information.
See Figure 8.18 and Figure 8.19 for WirelessHART and ISA100.11a architectures, respectively.
Features and Characteristics Impact on Security
All of the IoT technologies mentioned so far have varying (but often overlapping) features and characteristics, such as the RF spectrum in use, the topology, whether they're IP-based or not, etc.
While the protocols, security features, and implementations of those technologies may evolve over time, their more static characteristics offer some long-standing guidance on considerations for securing these networks.
Following is a brief overview of the considerations for IoT and non-802.11 wireless as it relates to:
- Physical Layer and RF Spectrums
- Coverage
- Edge IP Protocols
- Topology and Connectivity
Figure 8.18: Diagram of WirelessHART architecture
Physical Layer and RF Spectrums
The rainbow of wireless connectivity standards ranges from sub-1 GHz up through 50 GHz and beyond. Most of the technologies covered here operate in the 800–900 MHz (~400 MHz in some parts of Asia) to 2.4 GHz (802.11, 802.15.4, and Bluetooth), 3.5 GHz (CBRS and other private cellular), 5 and 6 GHz (802.11), and other cellular spectrums with 5G.
And of course, these spectrums range from licensed to unlicensed (such as 802.11 and 802.15), and everything in between with the shared spectrum (lightly licensed) CBRS space in the U.S.
The same principles covered in Chapter 7 in the section “Security Monitoring and Tools for Wireless” apply here. For security monitoring over the air, the tools must have visibility into that spectrum. Whether a narrow or wide band sensor is used, it needs to cover the spectrum(s) in scope, and of course, multiple sensors can be used as appropriate for varying location and radio needs.
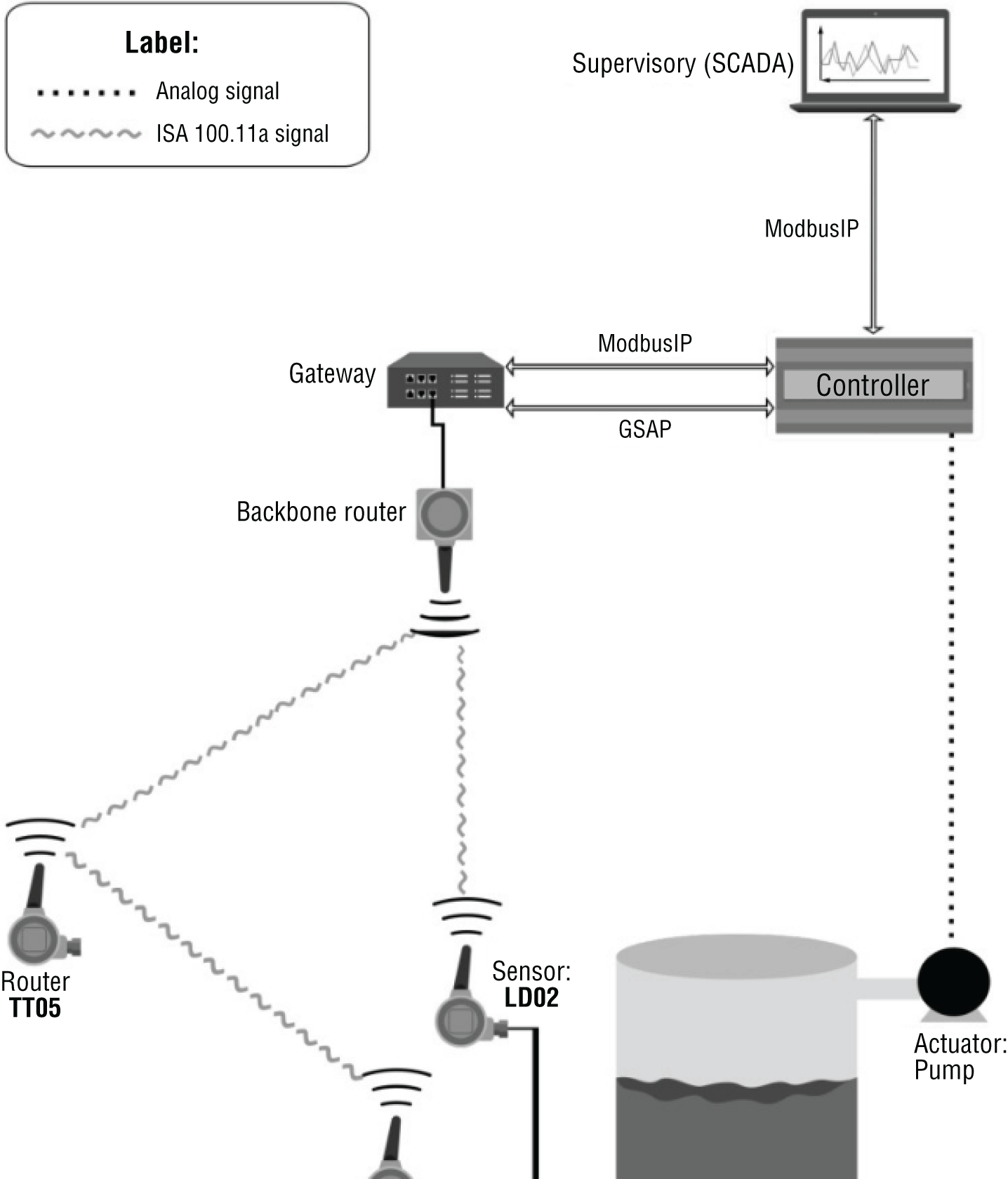
Figure 8.19: ISA100.11a sample architecture
Coverage
Connectivity models here range from very localized personal area networks (PANs) to local area networks (LANs), and metropolitan and wide area networks (MANs and WANs). Coverage models for IoT devices include:
- Personal area networks (PANs), including Bluetooth, 802.15.4-based technologies, and localized industrial automation
- Local area networks (LANs), including 802.11, in-building private cellular, and broader coverage industrial automation
- Metropolitan and wide area networks (MANs/WANs), including cellular IoT, outdoor and fixed private cellular, and private WANs
PANs and LANs are easily monitored and managed due to their localized nature, while MANs and WANs present a bit more of a challenge.
Security considerations for coverage models include the impact on:
- Over-the-air monitoring ability
- Accessibility
- Physical security of endpoint
As always, over-the-air monitoring means security sensors must be in proximity to the assets to be monitored (in addition to requiring appropriate radios). For PANs and LANs in the enterprise environment, it's easy because if you have Wi-Fi APs, you have a tool for at least some basic monitoring. For those longer-range MAN and WAN deployments, depending on the nature and criticality of the network, security monitoring may be desirable; in those cases, the tools in Chapter 7's topic of “Spectrum Analyzers and Special-Purpose Monitoring” offer a few options.
For provisioning, updates, and general manageability of the endpoints, the accessibility of those devices is also a factor. Again, PANs and LANs are going to be easier than, for example, a sensor that's buried a meter under soil 10Km away, or a pressure sensor embedded in a bridge. Consider the accessibility in planning ongoing maintenance, and if endpoints aren't accessible after deployment, plan for contingencies up front.
Aside from your ability to access an endpoint for maintenance, consider accessibility of the device by an adversary. If someone were to get his or her hands on one or more endpoints, consider what risk that poses, and plan for mitigations prior to deployment.
Edge IP Protocols
Across the half dozen or so groups of technologies presented, some use IPv4 addressing at the edge, others IPv6, and still others use none at all:
- IPv4 addressing, used in 802.11 and older cellular
- IPv6 addressing, used in all 6loWPAN, Thread, cellular, some 802.11, and ISA-100.11a
- No IP addressing, used in Bluetooth, BLE, Zigbee, Sigfox, and WirelessHART
Whether endpoints are IP-capable or not usually speaks to their other capabilities in terms of memory and processing—features that impact their ability to perform computations for encryption and decryption, and to store multiple keys. The result is that, while a specification may define options for multiple levels of keys, the implementation may reduce or eliminate keys, or downgrade to a lesser protocol during provisioning/pairing or encrypting. Thus, the IP stack (or lack of) will often influence security decisions related to:
- Endpoint capabilities
- Requirement for translator gateways
- Protocol vulnerability and mitigation
- Enterprise visibility and security controls
Technologies that don't have IP addressing at the endpoints will require a translator gateway device to convert data to IP-routable packets for connection beyond the local network. By virtue of them being the Internet of Things, IoT devices will at some point require IP connectivity. Translator gateways can introduce both a point of failure and a point of vulnerability.
The protocol(s) in use will, of course, impact the specific vulnerabilities and threats for the devices as well. While many translate, IPv4 attacks vary from IPv6, and non-IP-based attacks use different tools and tactics. Conversely, for security monitoring tools, visibility into IoT devices is usually easier with IP-based communications.
Topology and Connectivity
The network topology is another security consideration. Networks described here are sometimes IP local connected, directly connected to the Internet, connected via a translator gateway, and/or mesh—with the note that mesh is not mutually inclusive or exclusive of the other three. And some technologies support more than one topology.
- IP local connectivity, used in 802.11, private cellular LANs, 6loWPAN, Thread, and ISA-100.11a
- Direct routing to Internet, available in cellular IoT
- Connectivity via a translator gateway, required with Bluetooth/BLE, Zigbee, LoRaWAN, Sigfox, and WirelessHART
- Mesh topology, used to varying degrees by BLE, 6loWPAN, Thread, Zigbee, and WirelessHART
The data path of any communication will, by necessity, impact the security architecture. As with prior bullets, security monitoring and policies are well equipped to monitor and control local IP-based traffic. It's a trickier task for endpoints that directly connect to the Internet, and for technologies that communicate on non-IP protocols and require translation. The provisioning processes and security of the devices is also influenced by the connectivity method.
Non-IP networks that require a translator gateway, as mentioned earlier, present both a point of failure and point of vulnerability. Additional monitoring may be required for these infrastructures.
In addition, mesh topologies introduce additional considerations for both system resiliency and availability and security. Mesh uses the endpoint devices as routing hops, and the exact functions vary by protocol and implementation. Where, how, and when data is pushed through the mesh is a factor in securing mesh—how the data is encrypted, by what keys, and when is a critical piece of information. The time-to-live or hop maximums also factor into the equation for availability and throughput. How trust and peering in a mesh is established is another consideration.
Topology impacts security considerations primarily related to:
- Data path
- Vulnerability of translator gateways
- Mesh protocols
Other Considerations for Secure IoT Architecture
The four preceding topics have captured most of the factors impacting decisions around securing IoT devices, and specifically non-802.11 devices.
Those are summarized here in brief:
- Over-the-air monitoring capabilities
- Accessibility of IoT devices and gateways by admins and adversaries
- Endpoint capabilities including memory, processing, battery
- Networks requiring translator gateways
- Vulnerabilities specific to protocols
- Monitoring and mitigations specific to protocols
- Data path based on topology
- Use of mesh routing
In addition, there are just a few additional observations of current IoT security operations not included in the preceding bullets:
- Integrity of device provisioning and updates is something to be examined closely. The examples of the constant volume of Bluetooth and BLE vulnerabilities related to pairing and joining are only to serve as an example for all IoT-connected devices.
- Not all IoT protocols specify or require encryption. One example was Sigfox, where the burden is on the customer to ensure security.
- Even protocols that specify encryption and integrity don't enforce it; it's an option. Those technologies can often be forced into a downgrade attack even if a more secure mode is in use. For example, several BLE attacks even with the newer security modules were able to force pairing to Just Works, with no authentication.
- Going one step further, even if the implementation does include encryption, the key exchanges, management, and hierarchy of keys may be flawed or insecure. For example, several define options for network (group) keys along with pairwise (unicast) keys. However, depending on the vendor and implementation, the system may use only group keys and shared keys, creating security vulnerabilities.
- The security capabilities, requirements, and implementations are dependent on intertwined relationship of numerous factors including ones mentioned here and beyond.
- In general, consumer-grade equipment is configured for the easiest plug-and-play operation. Many commercial products follow suit, but some take security seriously and offer hardened protocols and tested products appropriate for enterprise use.
- The security of your IoT devices should be aligned with the criticality of the system, the sensitivity of the data, and the connectivity to other assets and networks. Don't spend $1M defending a $20 asset. And don't render a $1M asset insecure with a $20 IoT device.
Final Thoughts from the Book
Well, we made it! Here we are at the very end of the last chapter of the book.
There's been a lot of content delivered in these eight chapters, and I truly hope you've found at least a few nuggets of useful information. Realizing this book has delivered an entire tour of information security concepts, roles, risk and compliance, technical controls, planning guidance, and a journey through IoT and other emergent trends, I'm taking this opportunity to recap the most significant points I hope you'll take away:
- Wireless (including and especially Wi-Fi) is a complex topic.
- RF designs greatly impact Wi-Fi security.
- There are several right ways to design secure wireless.
- Wireless security is described in levels, not absolutes.
- A wireless infrastructure is only as secure as its weakest link.
- WPA3 security is transformative but only as good as your migration plan.
And as for the recommendations for designing and maintaining secure wireless networks, here are takeaways by chapter.
- Chapter 1, “Introduction to Concepts and Relationships”
- There may be many people and roles involved in architecting secure wireless; meet them and communicate often.
- You can justify many wireless design needs in the name of IAC (integrity, availability, and confidentiality).
- Strictly speaking in infosec and compliance terms, MAC authentication and passphrase-secured networks are considered identity, not authentication.
- Chapter 2, “Understanding Technical Elements”
- Data paths, segmentation, Wi-Fi architecture, and network configurations are all intertwined.
- WPA2-Personal is “the new WEP”: remove it from your network as quickly as possible.
- Contrary to prior guidance, secure networks will require separating SSIDs to a greater degree, instead of collapsing them.
- Using “Transition Mode” networks that support WPA2 and WPA3 together is not advised unless absolutely necessary.
- Chapter 3, “Understanding Authentication and Authorization”
- Dynamic VLANs (or other authorization) can be easily configured as a standard RADIUS attribute using any product.
- EAP methods go beyond just PEAP and TLS.
- MAC Authentication Bypass is a good option, but most implementations are done insecurely; don't comingle MAB (or any MAC auth) with full 802.1X endpoints.
- Chapter 4, “Understanding Domain and Wi-Fi Design Impacts”
- RF design and coverage impacts the function of key exchanges for secure roaming, and therefore security.
- Chapter 5, “Planning and Design for Secure Wireless”
- There are dozens of interrelated inputs and outputs involved in designing secure wireless.
- There are three main topic areas technical and non-technical executive leaders should know including budgeting, selecting products, and expectations for security.
- Chapter 6, “Hardening the Wireless Infrastructure”
- Hardening guidance is tiered, and strict hardening isn't recommended for all environments.
- Protected Management Frames (PMF) will add security but also impact current monitoring tools.
- Consumer technologies can have a place on enterprise networks, but it won't be a secure network.
- Ease-of-use zero configuration protocols like mDNS and Bonjour introduce extensive vulnerabilities to enterprise networks and are a primary entry point for pen testers and attackers.
- Chapter 7, “Monitoring and Maintenance of Wireless Networks”
- Pen testers and security assessors are your friends; they're going to find problems, be glad it's a friend not a foe breaking in.
- All wireless networks should include some amount of WIPS monitoring and rogue APs should be addressed and removed.
- As non-802.11 wireless is introduced to the enterprise, security will necessitate additional monitoring tools.
- Events that present immediate security risk should be alerted and acted on; other events should be logged and/or reported for future analysis.
- Chapter 8, “Emergent Trends and Non-Wi-Fi Wireless”
- BYOD policies are legal documents and shouldn't be created by IT teams without legal and human resources' input.
- The only hard rule of securing BYOD is to not allow unmanaged devices access to secured resources.
- Zero trust strategies are real, and they're attainable.
- There are numerous non-Wi-Fi IoT technologies appropriate for enterprise use.
As always you can find me online at www.securityuncorked.com and www.viszensecurity.com.
Until the next book—so long, and thanks for all the fish.
