Chapter 11
Every Step Matters
The reporter tucked her earpiece back into her ear. The noise of tens of thousands of people echoing around the exhibit hall was almost deafening, but she could hear her producer clearly in her earpiece. Behind her were the flashing lights of a technology booth with the MarchFit logo clearly displayed over her shoulder. She adjusted her dark hair back into place and held her microphone out in front of her. The cameraman counted down from three, and she began her opening, “Hi, this is Monica Stuart reporting to you live from the massive Consumer Electronics Show, the biggest technology event in the world. And stealing all the headlines of the show this year? MarchFit. I'm here with Olivia Reynolds, founder of MarchFit. Olivia, I don't think anyone was expecting what you had in store for us.”
The camera turned so that both Monica and Olivia were now in the shot. Olivia was already holding her own microphone. “I'm thrilled to be here,” Olivia said. “The last six months have been some of the hardest times in my life. But seeing how excited people are for our new gaming treadmill makes me feel like it was all worth it.”
“The world wants to know: Are you a gamer?” Monica asked.
Olivia laughed. “I have to admit that I've been playing Elden Ring entirely on our new treadmill at the office for a few months. Running around killing monsters for an hour is my new favorite workout.”
“Take us through a tour of how the treadmill works,” Monica said, as the camera turned again to show the MarchFit booth. There were sixteen treadmills arranged in a square, each occupied by a gamer wearing a VR headset. A line extended halfway across the exhibit hall with people waiting their turn to play. Each treadmill had a pole extending from the side of the base to about seven feet in the air. The players wore harnesses that were hung from the pole to keep them from falling over. The players were running, jumping, or dodging from side to side as they swung their arms. The treadmill closest to the camera had changed shape slightly so that the player appeared to be running up a hill.
“The treadmills allow for full 360-degree motion and integrate fully with the player's motion in the game,” Olivia explained. “As you can see, they can simulate going over different types of terrain thanks to the internal arms inside the treadmill.” There was a video playing behind Olivia that showed a cross section of the treadmill to show how each of the arms inside the treadmill could move independently from one another. “We already integrate with all the different VR platforms, but for those who prefer a more traditional experience, we also integrate with PCs thanks to our quad curved gaming monitors,” she said, pointing to a treadmill surrounded by monitors where a pro European player was playing FIFA.
“Well, I'll let you go since it looks like you've got a lot of people that want your attention,” Monica said, gesturing to executives from Activision, Microsoft, Nintendo, EA, and Sony who had gathered around them waiting for their turn to talk to Olivia. Olivia's assistant led her back to one of the meeting areas on the second story of the booth and the executives all followed, hoping to get their turn. Monica gestured to the cameraman, and they began to break down their gear to move on to their next interview.
Hours later, Olivia walked out of the meeting to look over the balcony of their booth. Dylan was there drinking a coffee. “Hey, it's good to see you again. I still feel bad that you were forced out as CEO. I wish there was something I could have done.”
“Are you kidding?” Olivia said. “It was the best thing that could have happened. I'm an engineer and an inventor first. It was the right time to hand off the role to someone who could focus on running the company. Now I get to spend my time doing what I love, which is building new things.”
“That's really cool,” Dylan admitted, remembering all the tools in her office. “I had no idea what I was in for, but I'm glad I stuck it out.”
“I didn't know what I was getting into when I started the company! I felt like I had to be both Jobs and Wozniak. But now that I've gone through it, I think I'm more like Woz.”
“Really? I always thought of you more as a Hedy Lamarr type.” Dylan said.
“The important thing was to make sure the product launch happened,” Olivia said. “Hey, are you busy right now?”
“I was just about to walk around and check out some of the new products on the floor,” Dylan said.
“Oh, sorry. You won't have time for that. The folks from the gaming companies wanted to talk to you about Zero Trust. They want to know how we turned our security around so quickly. I think they were more excited to talk to you than they were about talking to me,” she said, opening the door to the meeting room for him.
Several days later, Dylan sat down at his desk. It felt like the first time he'd actually been in his own office since he started at MarchFit. He had a window overlooking the lobby of the building and could see the wire mesh shoes running down the center of the corridor. He started his next Zoom meeting early so he wouldn't forget, then began unpacking the cardboard box he had brought from home but hadn't yet had time to unpack. He pulled out a painting his daughter had painted for him when she was a child and placed it on his desk. Dylan continued unpacking until Aaron joined the call. “Dylan, nice to hear from you,” he said as his video came online.
“You still owe me one last phone call,” Dylan said. “I thought it would be nice to do a video chat since things have settled down and our Zero Trust project has wrapped up.”
“Wrapped up?” Aaron asked.
“We finished up the project just in time for the new product launch just like we had planned,” Dylan said.
“Oh, man, that's good to hear. But you're definitely not done.” Aaron laughed.
“Did I miss a step?” Dylan asked. “We went through all our protect surfaces and used the design methodology to tailor our controls. I mean I get that it's a continuous process, but…”
“It seems like I may have forgotten to mention the Zero Trust Maturity Model,” Aaron said apologetically.
“I thought we were going to do Zero Trust in six months?” Dylan asked. “How long will the rest of the process take?”
“We didn't just pick the six-month time frame because MarchFit had a product launch coming up,” Aaron explained. “We picked the six-month time frame because of the natural business cycle. I recommend to all of our clients that we focus our efforts into six- to nine-month initiatives. We do that for a few reasons, but the biggest one is because of the corporate budget cycle. When we get budget allocated for our projects we have to be able to show value based on that budget allocation. If we started with a three-or five-year campaign, we'd lose funding halfway through the project and the initiative would get abandoned because we couldn't show any return on the business’s investment.”
“That makes sense,” Dylan admitted.
“Because Zero Trust is a strategic initiative,” Aaron explained, “it's important to benchmark your Zero Trust journey and measure your maturity over time. We designed the maturity model based on the standard Capability Maturity Model, which has five stages: initial, repeatable, defined, managed, and optimized. For each protect surface, the Zero Trust Maturity Model measures the maturity of each stage of the design methodology.”
“So we need to baseline our level of maturity for each of our protect surfaces, and the next step would be to select goals for improving each of those areas?” Dylan guessed.
“That's right. But keep in mind you'll always need to be strategic with what areas you want to focus on improving. The priority will always align with MarchFit's priorities and the specific risks you're facing,” Aaron said.
“Does that mean it's OK to not be as mature in some less-critical areas?” Dylan asked, pulling out a snow globe from the box and placing it on his desk. Inside was a picture of Dylan and his daughter from a summer vacation.
“You'll have to go through that rightsizing exercise to make sure you've got the resources you need to deliver the right level of security. You don't need to have the same level of maturity for each step in the design methodology or for every protect surface. But starting with the baseline can help you show how and where you're investing in security and how that aligns with the business.”
“That seems like it would become really complicated to explain,” Dylan admitted.
“I like using the transaction flow matrix chart that John Kindervag developed to help show how protect surface policies are developed to talk internally. Here, let me share my screen.”
“The transaction flow matrix can help you understand how each of the different protect surfaces can potentially impact one another. As you think about the maturity of your protect surfaces, you'll need to think about how the blast radius from a compromise in one might impact the other protect surfaces.”
“You're saying that we can't think about any protect surface in a vacuum?” Dylan said.
“Exactly,” Aaron confirmed. “But you only have so many IT resources. So if you had ten team members and eight of them are tied up working on firewall rules because of all the complexity of your rules, then you might be sacrificing control over identities or visibility into logs, for example.”
“What do you think we should work on next?” Dylan asked.
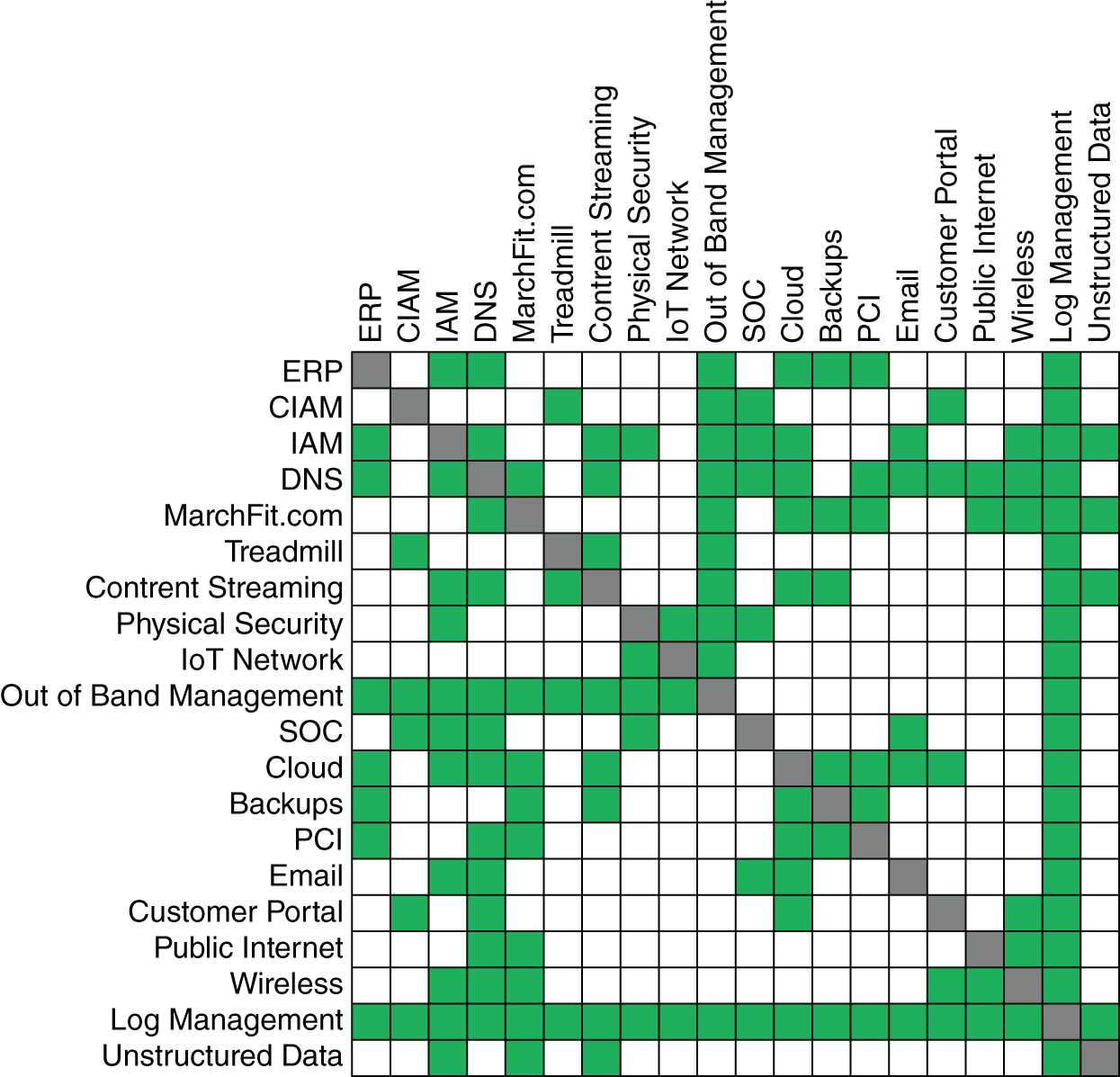
Transaction Flow Map One—All the protect surfaces are defined, and the transaction flow matrix can show which protect surfaces are allowed to communicate with one another.
“I've got a few ideas. If I were you I'd be looking into continuous flow mapping using BAS—breach and attack simulation—or emulation tools. I'd also be looking carefully at deception technologies.”
“I've never heard of breach and attack simulation,” Dylan admitted.
“Not many organizations have complete testing infrastructures where they can detonate malware and test whether all their controls are adequate,” Aaron explained. “BAS or emulation software helps do this kind of testing in more of a real-time way than doing an extended security assessment or penetration test. I think it's most beneficial for more mature organizations. Breach and attack simulation can simulate how a real attacker might attempt to attack an organization using predefined attack paths. With emulation, the tools help customize how attacks are launched, using threat intelligence to contextualize how the business actually works.”
“What makes you say we should look at deception?” Dylan asked.
“With Zero Trust, we've focused on removing all the trusts we can in order to make our networks more secure. But with deception, we can selectively add trusts back into the network using lures, beacons, breadcrumbs, and decoys. The idea is that Zero Trust can conceal real data while revealing fake trusted sources to distract, delay, or detect threat actors. I know we've talked about the MITRE ATT&CK framework in the past, but they also have something called the Engage framework. Let me show you,” Aaron said, pulling up the MITRE Engage framework.
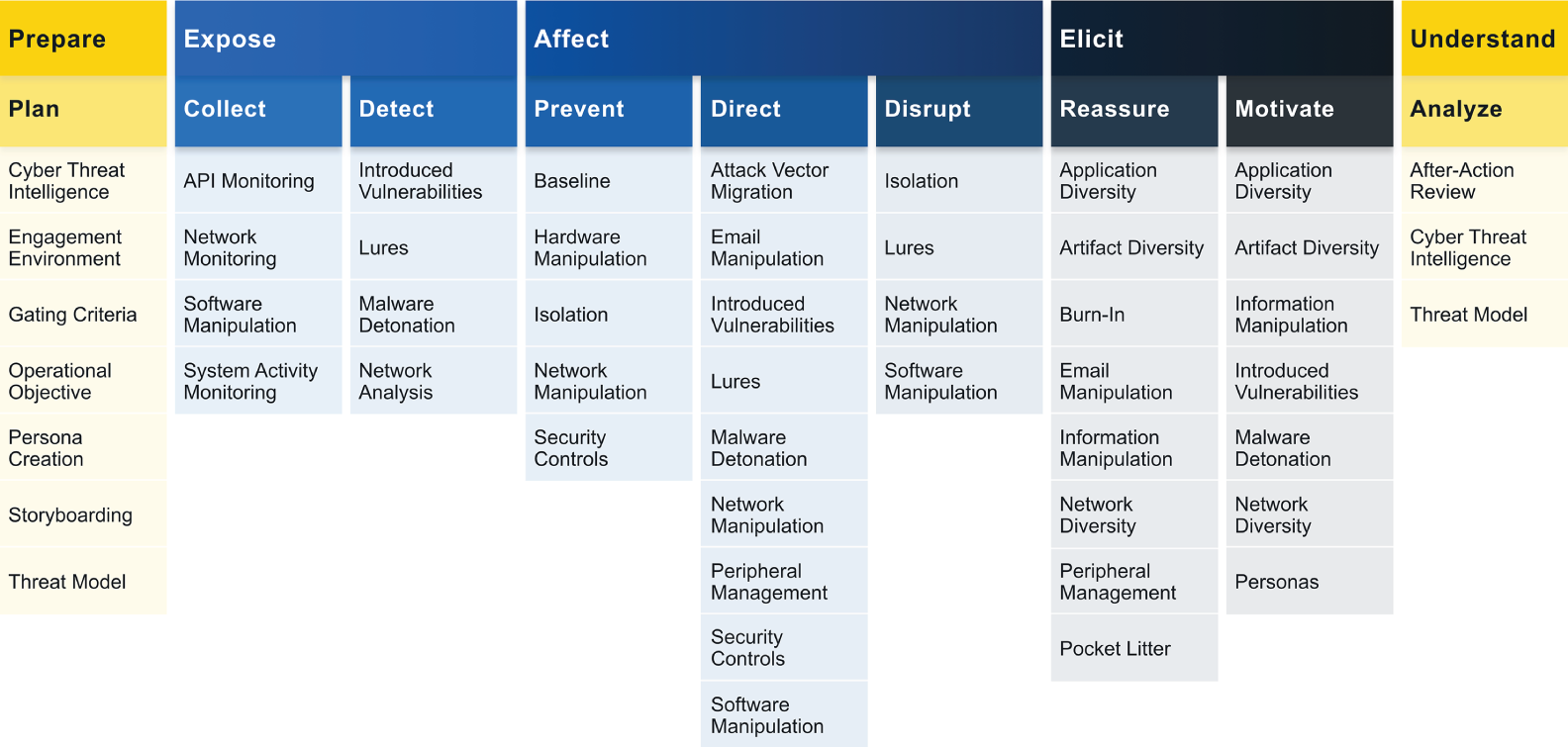
MITRE Engage Matrix—The Engage Matrix depicts five stages of creating an active defense to disrupt cyberattacks using deception technologies.
“The MITRE ATT&CK Framework provides an analysis of all the TTPs of attacker behavior so that defenders can better understand and defend against those TTPs,” Aaron explained. “The Engage Matrix is a framework for defenders to help them to provide an active defense against attackers. The idea isn't to just passively defend, it is to proactively engage attackers to bring the fight to them.”
“Does that mean we're going to hack back?” Dylan asked.
“No, as far as I know hacking back is still illegal,” Aaron said. “But using tools like deception can get inside the heads of our adversaries.”
“How does that work?” Dylan asked.
“The first principle of Zero Trust is to remove all trust relationships from digital systems,” Aaron said. “With the Engage Matrix, we build profiles of threat actors that target us, and carefully expose specific resources that act like breadcrumbs that lead the attacker toward lures or honeypots. The next phase is to expose what the attackers are after with those breadcrumbs. Then we disrupt the attacker, what they have visibility into, and what actions they may take next. We induce them to show us what their toolkits look like and we use that to help us better understand their capabilities. That feeds into the threat intel pipeline and helps us improve the controls we have on our protect surfaces.”
“I've always heard that honeypots can attract unwanted attention,” Dylan said.
“I'm not recommending that you set up a honeypot that's exposed to the Internet,” Aaron said. “That will be too noisy to provide any real value. But it's been shown that when threat actors know that you're using deception technologies in your network, the bad guys spend less time inside your network.”
“It's like when a burglar hears a siren in the distance and worries that it's the police coming for them,” Dylan said.
“That's right. The NSA actually had some pen testers attempt to get into different networks, but when they told them they were using deception technologies, the red teams started to doubt their own tools and questioned whether the targets they were finding that had weaknesses were actually decoys. This effect persisted even when the NSA wasn't actually using deception.”
“Like when people put a home alarm monitoring company sign on their house but don't actually have an alarm,” Dylan said.
“Exactly. In a way, we're taking advantage of the trust relationship that the attackers have with their own tools or their own telemetry. Deception brings the fight to the mind of the adversary. We're getting inside their heads to disrupt attacks,” Aaron explained.
“Well, I guess we still have a lot of work to do,” Dylan said.
“Good luck, Dylan. Let's definitely grab lunch and catch up the next time I'm in town!” Aaron said.
Dylan had just finished the call when Noor knocked on the door to his office and stepped in. “I don't think I've ever seen you in your office before,” she said.
“I've figured that if I'm in my office, I'm not doing my job,” he said with a laugh. “It's been going from one meeting to another and making sure everyone on the team has everything they need.” He pushed his chair away from his desk so he wouldn't be distracted by his computer.
“Do you mind if I sit?” Dylan nodded and she sat down. She saw the picture of the girl on Dylan's desk. “I didn't know you had a daughter.”
“Oh, yeah. She's in college now. She wants to be a veterinarian one day, but we'll see if that changes by the time she's done,” he said, smiling warmly.
“I've got some good news,” Noor said, smiling. “As you know, I've been serving both as MarchFit's CIO and as our CISO. I talked to Vic and Donna, and we all agree that it's time that we hired our first dedicated CISO.”
“That's fantastic news,” Dylan said.
“Well, given your experience, we were hoping that you might be interested in the role,” Noor said.
“Me?” Dylan said.
“Take some time to think about it,” Noor said. “No rush this time. I would like you to get some security certifications in the first year on the job. We would be willing to send you to an executive CISO leadership institute to help you continue to develop your skills as well. But you don't have to say yes now.”
Dylan was standing at the projection screen inside ZTC. He was outlining the next phase of Project Zero Trust after reviewing the maturity model. Harmony, Rose, Isabelle, and Nigel were sitting at their seats watching his presentation when there was a knock at the door. Harmony turned out the lights, then flipped a switch that turned on some colored disco lights. Brent came into the briefing center pushing a cart with a giant trophy on it.
“Guys, you didn't have to do this,” Dylan said.
“We all got trophies too,” Harmony said, passing out small trophies to all the team members.
“We're gonna have to change the codes to the briefing center,” Dylan said, seeing that the trophies had been 3D printed.
“Don't you dare,” Brent said. “I get ninety percent of my coffee intake from that espresso machine.”
“How much coffee do you drink?” Rose asked.
“Not coffee. Espresso,” Brent said. “And for your information,” he said to Dylan, “that's not a trophy. It's a cake.” And Brent produced a giant kitchen knife and proceeded to cut into the trophy.
“It's just like that show on Netflix, Is It Cake!” Isabelle squealed. “The base even looks like wood with that grain.” The trophy had a plaque at the bottom that read: “Zero Trust Champion 2022: Dylan Thomas.”
They stopped the meeting to eat the cake. It was delicious.
“I'm gonna need to build a pretty good security team,” Dylan said as the others finished their cake. “You guys know anyone who wants to work for a brand-new CISO?” he asked.
“I think you've already got a pretty good team,” Rose said. Although everyone's mouths were full, murmurs of agreement came from around the room.
“Aw, guys. I didn't want to assume that you'd want to move over to the new team,” Dylan said.
“And leave all this cake for someone else?” Harmony said. “Forget it.”
“Well, it's not just going to be us. We'll have to do some recruiting as well,” Dylan said.
Several months later Dylan was standing in front of a group of new members of his security team on the steps to the executive briefing center. He put his hand on the metal shoe that was halfway up the stairs. The group followed him up the stairs and stood underneath the giant shoe.
Dylan spoke up and said, “Turn around and take a look at MarchFit's motto just above the entrance to the building.” The group turned around and Dylan continued speaking. “The first thing that I want you all to know is that we're not measured on whether we are hacked or not,” he said. “We're measured on how we respond to those challenges. We're measured on whether we rise to the challenge. Every step matters.”
Key Takeaways
One of the biggest obstacles to improving security for organizations today is that there are so many technology silos. Some teams only support antivirus products or firewalls. Other teams do database encryption or application security. Some teams support identity. Other teams do cloud security. Some teams report to a CIO, whereas others report to a CTO or CISO. These silos prevent collaboration and communication. I believe that a Zero Trust strategy can help break down these silos and help unify teams around a singular focus: preventing or containing data breaches. This is why Project Zero Trust brought together a team of diverse individuals from throughout MarchFit—to break down these barriers and help the organization evolve.
When I started my own Zero Trust journey, I didn't take into account whether I'd be able to scale our implementation of microsegmentation and other controls along with the size of the team that I had at the time. We were extremely granular in our controls in order to contain the blast radius of any incident. But because we didn't start with the concept of protect surfaces, we applied the same level of focus and control everywhere. As a result, our controls became too complex to manage. I believe that John Kindervag's Zero Trust Design Principles and Methodology can drastically reduce the complexity in your approach to Zero Trust.
The only way to be successful at implementing Zero Trust is to build a team. Success starts with support at the highest levels of your organization. Zero Trust will require changes, and those changes will require you to collaborate with different business leaders throughout your organization to both understand how the business functions and coordinate security with how the business uses technology.
But you also need a team in IT. Most of the changes that are required to support Zero Trust won't necessarily be done by security teams. Dylan's team was made up of people from all over IT who supported security. Much of the work that will be required will be done by infrastructure teams that support networks or servers. We included examples of how application owners and software developers are also a part of the process to limit trust in how their systems work. Zero Trust projects that bring together diverse teams help break down silos and allow for streamlined collaboration. MarchFit created an Identity Governance group and an Enterprise Architecture Group and had mature project management to ensure that the Zero Trust initiatives were completed in a reasonable time period and that these changes would be sustained as the business continued to grow and change.
Zero Trust requires you to have the basics in place. One of the first places you should start is with an inventory. In order to protect something, you need to know where it is, how it works, and what it needs to talk to. In Zero Trust, there is no concept of unknown traffic. If it is unknown, it is blocked by default. The next step in Zero Trust requires you to prioritize your efforts. Having done a business impact assessment is helpful because this document will measure the impact to the business for each service in the organization. To know what applications are the crown jewels, you can look to this document. In addition, every organization needs to have a technology risk register to have a current list of the biggest threats to the business from a technology perspective. A risk register should include much more than vulnerabilities; it can document lack of capabilities in specific areas and identify single points of failure or weaknesses in the various controls that the organization has in place.
Having the basics helps speed along the process, but if those basics aren't already in place, launching a Zero Trust project can help your organization build out your inventory, risk register, CMDB, and business continuity plans along the way.
An organization can't have cybersecurity without good physical security. We chose physical security as one of the learning protect surfaces because it is so often overlooked when it comes to security. Often, organizations outsource security guard duties to third parties. The physical security technologies like card readers and cameras are also often outsourced. Without internal oversight, these organizations will focus on keeping these systems operational without regard for the security of those systems. Although an organization can bring in partners to help with physical security, organizations can't outsource the responsibility and accountability for security.
In the beginning, we started by understanding the business. The Project Zero Trust team worked on several practice and learning protect surfaces so that they were prepared to fully implement Zero Trust when they got to the crown jewels of the organization: the ERP system. Because the ERP system is so critical to the business, the team was also exposed to several different departments to better understand how the business operates. ERP systems today are often a blind spot to security teams; they don't receive ERP logs, perform vulnerability scans, or review code changes prior to being deployed in production. These challenges are critical for any protect surface, but ERP systems may require specialized tools to accomplish this task.
Identity is the cornerstone of Zero Trust. Identity is both a protect surface and a critical control. The identity system needs to be protected better than almost any other protect surface because of its criticality to an organization. Consumer Identity and Access Management is your outward-facing identity surface and should be separated from your employee and privileged account management platforms. But Zero Trust also consumes identity—many of the controls that Zero Trust employs rely on identity to be effective. This is so true that the NIST standard for Zero Trust (NIST SP 800-207) focuses on identity to drive Zero Trust deployments.
Many organizations that develop their own software have adopted a DevOps philosophy to help them focus on the business. DevOps helps organizations deliver better software more quickly, and this development pipeline can include security testing that can ensure that trust relationships, like embedded passwords, emails, or IP addresses, are removed from code before being released into production.
The SOC plays a huge role in Zero Trust because of their unique view of an organization. The SOC correlates strongly with the monitor and maintain phase of the Zero Trust design methodology, and whether the SOC is run inside an organization or is run by an MSSP, the SOC should provide continuous feedback on the state of an organization. Rather than simply viewing alerts and escalating them back to an organization, a Zero Trust SOC can help improve controls inside an organization to reduce false positives and help identify opportunities for improvement. Maintaining an internal 24x7 SOC is probably outside the capabilities of most organizations. Working with an MSSP service that can help tailor their monitoring to meet your business needs is crucial. But you also need an MSSP that can align with your own protect surfaces, incorporate data from penetration testing findings, and integrate with your specialized internal tools.
Many organizations have chosen to leverage cloud services to help improve their scalability. The cloud, however, isn't just one protect surface; it's many different ones. One of the best ways to ensure that Zero Trust processes are followed in the cloud is to have strong IT governance controls in place, like a Project Management Office to enforce that consistent controls are in place to protect cloud-based services. To protect something, you have to be able to see it. Unlike for on-premises services, there is limited visibility into cloud services, so additional tools like WAFs, CASBs, or API monitoring are needed. In addition, because cloud services necessarily involve third parties, organizations need to have strong contract and third-party vendor management processes in place to manage the risk of a third party having a breach.
People play a critical role in the success of Zero Trust. Most security practitioners will tell you that security is made up of people, processes, and technology. But people are the ones who write and follow processes. People are the ones who create, configure, and use the technology. People are the most important part of the organization, and they make all the difference when it comes to security. In order for the changes that Zero Trust will require to be sustainable, an organization's culture must be supportive. Security should be integrated into everything that the organization does, from training to weekly departmental meetings. And performing regular tabletop exercises will help bring the organization together to intentionally develop this culture.
Every organization in the world should be doing cybersecurity tabletop exercises just like businesses are required to perform annual fire drills. They are critical to help employees know what to do when something bad happens. The amount of effort it takes to develop a tabletop exercise can vary greatly depending on how complex a scenario will be taken on. A simple tabletop can be based on freely available templates from CISA. MarchFit's MSEL that was used for their tabletop exercise is included in Appendix C. Any tabletop exercise—and especially a live-fire exercise—takes preparation to ensure that the exercise provides real value for the organization. The PZT team spent weeks prior to the event preparing the scenario and developing all the supporting materials to make sure the event went off smoothly.
Some people say security starts from the top down, while others say that it comes from the bottom up. And they're both right. The leaders of MarchFit supported Project Zero Trust and paved the way for its success. The 2021 Verizon Data Breach report indicates that rogue insiders are responsible for 22 percent of all data breaches (www.verizon.com/business/resources/reports/dbir). MarchFit could have been one of those organizations, but the culture of the organization is what allowed Rose to come forward to help catch the hacker without fear of retribution from her boss.
Zero Trust primarily focuses on prevention, and one of the key elements to accomplish this is containment. Containment limits lateral movement inside an organization to other more critical systems through techniques like microsegmentation and least privilege access. Containment can also be accomplished by quickly identifying when resources are impacted by an intrusion, limiting the amount of time a threat actor has on the network to accomplish their objectives.
Because Zero Trust is a strategic initiative, it's important to benchmark your Zero Trust journey and measure how your maturity changes over time after making adjustments to your protect surfaces. The maturity model is based on the standard Capability Maturity Model, which has five stages: (1) Initial, (2) Repeatable, (3) Defined, (4) Managed, and (5) Optimized. For each protect surface, the Zero Trust Maturity Model measures the maturity of each of the five stages of the design methodology. For any given protect surface, each stage of the design methodology could have different levels of maturity, and there should be a strategic plan for improving your Zero Trust maturity based on your risk register and the criticality of the protect surface. In addition, you should take into account the overall view of how all of the protect surfaces interact, because an incident in one could impact others that are a part of the transaction flow.
In the beginning of the story, the Project Zero Trust team was given six months to implement Zero Trust in MarchFit. Six months may seem like a short amount of time, but based on feedback I've received from other cybersecurity leaders who've gone through Zero Trust transformations, six to nine months is actually a good time frame. You shouldn't expect to complete your Zero Trust journey in just a few months. But you do need to be able to demonstrate value in a reasonable period of time to justify the business value to your executive stakeholders. Breaking down your Zero Trust journey into bite-sized pieces can help ensure the long-term success of the initiative. You can use the first phase of a Zero Trust project to build the business case to move on to the next phase. This is where the Zero Trust Maturity Model can come into play. Your first steps might be from level one to level two, and the following year you can move from stage two to stage three.
“Every Step Matters.”
I chose this for MarchFit's creed because it resonates so much with what we do in cybersecurity—and, in particular, Zero Trust. There is a reason for everything we do, and everything we do makes a difference. Every Step Matters.
