Chapter 2
Zero Trust Is a Strategy
Dylan was walking quickly, trying to keep up with Aaron as he walked up the stairs to the executive briefing center. Dylan was carrying a backpack with all of the paper documentation he had received from Noor the day before. Behind them was a woman wearing jeans and a black hoodie and a tattered backpack whistling the opening riff from “Careless Whisper.” Following her was a woman wearing cat-eye glasses and a vintage 1950s dress and carrying a leather satchel. A tall man wearing a polo shirt and a short man wearing a red Arsenal football jersey loitered behind, heads bowed down looking at their cell phones.
The briefing center was at the end of the lobby that separated north MarchFit from south MarchFit. The conference center was a free-standing island of steel and glass that appeared to float above the rest of the headquarters building lobby.
The smell of freshly brewed espresso greeted them as they walked through the entrance. Isabelle was sipping from a tiny coffee mug watching them. She lifted her espresso mug in salute to the group as they swiped their badges to enter the suite.
The IT incident response teams had taken over the south side conference rooms, trying to complete the remediation of all the computers that had been ransomed but also trying to piece together how the ransomware got in at all. The north side conference rooms were all taken by lawyers and marketing teams discussing the potential responses to the lawsuits that the company was facing. That left the Project Zero Trust team the luxury conference rooms usually reserved for meeting with the company's largest clients and investors.
“Your new laptop is on the table,” Isabelle said to Dylan between sips of espresso.
“That's a good sign. Does that mean we're back in business?” Dylan asked.
“We're in good shape. They're bringing up parts of the network one by one. It sounds like we're actually ahead of schedule,” Isabelle said.
“It's like an episode of CSI exploded all over the place,” Harmony said, holding up a conference phone that could have been a small stealth drone. She set the phone down and ran to the small white box at the end of the room. “Is this a 3D printer?” she exclaimed. “Why would they need a 3D printer in a conference room?”
“It's so they can fabricate custom treadmill parts during meetings with clients,” Isabelle explained. “It's the quietest 3D printer on the market.”
“It's like being on Star Trek,” said Harmony, touching the 20-foot-wide video wall that occupied the whole of the back wall of the conference room. As she touched it, the cursor responded, bringing up a welcome video on how to use the wall. “IT'S A TOUCH SCREEN?” she exclaimed.
Dylan began to address the group. “I’d like to thank you all in advance for all the hard work that we're about to put into this, well, we're calling it Project Zero Trust. And I'd like to introduce Aaron Rapaport, who… .”
“What's your strategy for success when it comes to security?” Aaron interrupted, addressing the whole conference room. He paused for several seconds waiting for someone to answer. “You guys do have a strategy, right?”
“From what I've heard so far, it sounds like MarchFit had a defense-in-depth approach to security,” Dylan said defensively.
Aaron paused and took a deep breath. “Let's back up a bit, and start with what a strategy is. A strategy is like a plan on how to achieve a specific goal, right? So at the end, you'll know when you've reached your goal. Now, here's my question: How do you know when you've successfully achieved your goals with defense in depth?”
“Wouldn't you know when the number of successful attacks starts to go down?” Dylan answered.
“You don't control the number of attacks the bad guys send against you, and you may not always know whether they've been successful or not. How many layers do you need to keep the bad guys out? Eight? Ten? Twenty? This is why embracing defense in depth as your strategy really turns out to look a lot more like ‘expense in depth.’ There's no measure for success. And you're spending money you don't have on things you don't need to protect.”
“What about our attack surface?” Dylan asked. “I've heard security people at conferences talking about shrinking the attack surface. Shouldn't we be doing that, too?”
Aaron laughed. “The whole world is your attack surface! Any person or device anywhere on the planet could unwittingly be used to attack you. Instead, with Zero Trust, we focus only on the things that we can control. This is why we shrink it down to something very small and easily known, like the ‘protect surface.’”
“We've always had a best-of-breed strategy,” said the woman in the hoodie.
“Who are you?” asked Aaron.
“Harmony Gold,” she responded, and shook Aaron's hand. “I'm a network engineer.”
“Harmony, lots of organizations use consultants or industry analysts to decide which are the best products to buy. This isn't a strategy, either. Having the best products doesn't stop organizations from getting breached. What really matters is making all those separate elements work together in one integrated system that is custom tailored to fit your unique business.”
The sliding doors to the conference room whooshed open and the two men wearing polo shirts finally walked into the room, laughing. “The funeral is tomato!” said the taller of the two men, and then repeated the final point for emphasis, “Tomato!”
“I'm so glad you could join us today,” Aaron said sarcastically. “Your company just experienced a breach and you're the team that's going to make sure it never happens again. So what's your strategy for making that happen?”
“Isn't there some list of best practices somewhere that we can just follow?” the tall man asked, taking his seat. And after a moment he added, “I'm Brent, by the way. This is Nigel. He's English.” Nigel nodded and sat down.
“You didn't really specify which checklist you had in mind, Brent. But it doesn't matter, because compliance checklists aren't a strategy. There are some good tactics on those lists, but a lot of companies that were compliant got breached.”
Nigel was showing Brent something on his cell phone. Harmony was staring out into the lobby watching the people walking north and south.
“What's going on with you guys?” Dylan asked. “Don't you guys realize how important Project Zero Trust is?”
“Sorry, Dylan,” said the woman wearing cat-eye glasses. She was already sitting at the conference room table. Dylan hadn't realized she was there. “I thought this project was a punishment. Everyone else at the company is either working on the new product release or getting the company working again.”
Nigel spoke up. “Sorry, mate, nobody wants us on their projects. So you're stuck with us.”
“What do you guys do?” Dylan asked.
“I do identity,” Brent said. “And Nigel here is one of the most underrated developers you'll ever get stuck with.”
“I don't buy that for a minute,” Dylan countered. “Getting the company back up and running is pretty urgent, but Project Zero Trust is going to change the company. And the six of us are going to be at the heart of that change. Noor wouldn't have selected y'all if she didn't have faith that we were exactly the right people for the job.”
“Oh, and I should add that the PMO will push through any changes that the team recommends with immediate emergency change control,” Isabelle added. “And our budget comes directly from Olivia, for what it's worth. It's not a blank check or anything, but it's as close as we'll ever get.”
Aaron tapped on the video wall and a diagram of all of MarchFit's networks appeared on the wall. The treadmill network was depicted by a cloud in between two boxes, one marked data center and the other treadmills. Below that was a star-shaped network connecting various retail location icons with a building labeled Headquarters.
“The good news is that we don't need a blank check. Zero Trust is the best strategy we have for protecting MarchFit because it was purposefully created for preventing breaches. You've probably heard that an ounce of prevention is worth a pound of cure. We've studied organizations that have implemented Zero Trust, and we've shown that this focus on prevention really does create a tenfold decrease in cost and complexity. It might feel like leading a security incident response team is doing the ‘real’ security work, but I think it starts with people like you, doing the work of prevention every day.”
“There are only nine things you need to know to do Zero Trust. Nine things. That's all. Anybody can remember nine things, I hope. Right?” Aaron pulled up a slide, displaying it next to the picture of the MarchFit network infrastructure:
- Focus on business outcomes.
- Design from the inside out.
- Determine who/what needs access.
- Inspect and log all traffic.
“There are four design principles and five steps to applying it. But the first of all the design principles is to focus on the business outcomes. If you don't know why you're doing something, you can't protect it. So how do you guys make money?”
“We sell subscriptions to our fitness network. And workout clothes. People love the clothes,” the woman in the cat-eye glasses said.
“I didn't catch your name?” Aaron asked.
“It's Rose,” she said quietly.
“Exactly, Rose. MarchFit is really a media company. You have a movie-quality studio, and the best athletes all over the world are your personal trainers. It's easy to think of yourselves as a company that makes treadmills with a desk attached to them. But your margins for hardware are very small. The reason that people love the company is the content.”
“How exactly does that help us prevent a cybercriminal from getting in?” Brent asked.
“Just looking at the picture, you can tell that this network was designed from the outside in.” Aaron pointed at the network diagram. “The detail in the picture focuses on the endpoints at the edge and then goes inward. That's why it fails, because we don't know what we're protecting.”
“We just had a case of ransomware. Shouldn't we be focusing more on the endpoints at the edge?” Harmony asked.
“I heard from Noor this morning,” Isabelle said, “that it's looking like the ransomware was installed by a user who had local admin privileges. You could just as easily argue it was a permissions issue,” she said, folding her arms.
“This is why the third step we have is least privilege control access on a need-to-know basis,” Aaron added. “Ask the question, does so-and-so need to have access to that data to get their job done? That's how I tell them. Don't use the words ‘least privilege.’ Say, ‘Aaron, do you need that access to that data to do your job?’ I'll bet most times the answer is no. We give too much access to too many people for no reason.”
“I think we've all seen admin privileges given out to directors or executives as a status symbol instead of as a core part of their jobs,” Dylan said.
Aaron nodded. “Then the fourth step is, inspect and log all that traffic, because in cases where we've seen there were rogue insiders or compromised accounts, no one looked at their packets post-authentication. We have this movement that Zero Trust equals identity and it doesn't. We're going to say that in the end, it consumes identity. You need to look at the packets post-authentication and see what they're doing. Is there attack traffic in there? Are they downloading thousands of documents? Are there hundreds of SSH connections outside the company? To even have a chance at detecting those anomalies, you need to have the data in the form of network or server logs.”
“This is just a bunch of theory,” Nigel interrupted. “When are we going to actually protect something?”
Aaron changed to the next slide, which had the following words:
- Define the protect surface.
- Map the transaction flows.
- Architect a Zero Trust environment.
- Create Zero Trust policies.
- Monitor and maintain.
“I mentioned there were four design principles. But there is also a five-step methodology to applying those principles. I completely agree that it would be boring just to talk about the methodology, and it's better to just get some hands-on experience.”
“Wait, we're going to start making changes now?” Dylan asked.
“We've got emergency authorization for any change we request,” Isabelle confirmed. “If we put a request in it should be done within a few minutes.”
“Don't worry, Dylan, we're not going to start with anything critical. The first step in the methodology is to define your protect surface. But at this point, we will only start with a learning protect surface.” Aaron pulled up a slide with a line that looked like a wave. The bottom-left part of the wave was labeled “Learning” protect surfaces. As the wave went up, it was labeled “Practice” protect surfaces. The crest of the wave was labeled “Crown Jewels,” which are the most business-critical protect surfaces, with the Secondary and Tertiary protect surfaces further down the wave.
“The only way to eat an elephant is one bite at a time. Everybody thinks, ‘Oh, how are we ever going to implement Zero Trust?’ Our environment is big so we break it down into little sections. You take a big problem, and you break it down into really small problems, and that's how you solve it. You can't do everything at once. That's why the first step in Zero Trust is to find the protect surfaces. You already know what these are. You've got your Business Continuity Plans and your Business Impact Assessments that tell you what the most important applications are in your environment.”
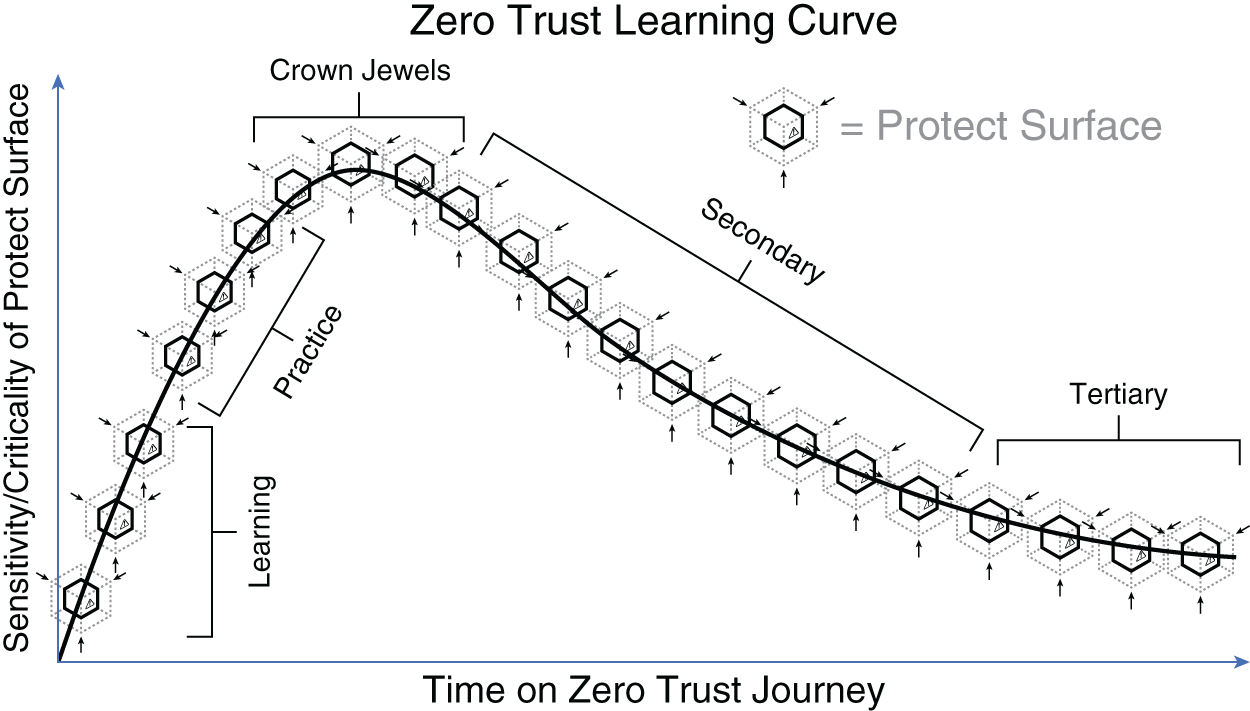
An organization's Zero Trust journey should begin with protecting several less-critical protect surfaces in order to prepare the team for success in more complex and critical protect surfaces later on.
Courtesy of ON2IT
“What about a basic application?” Brent asked. “Like DNS?”
“Your learning protect surface needs to be something that won't matter if we mess up,” Aaron said. “DNS is definitely a business-critical application that we'll save for later.”
“We have a SharePoint site for the training team. It's just an internal site for our team. It won't be a big deal if we take it down for a bit. Nobody will notice,” said Rose.
“Perfect. Harmony, can you pull up the firewall rules for Rose's SharePoint site?”
Harmony connected her laptop to the video wall and began connecting to the terminal server with access to the management network. She pulled up a browser window with the firewall management application and searched for all the policies with the SharePoint label. A list of firewall policies came up showing the source port and address as well as the destination ports and addresses. Rose's server was at the end, labeled “Training Team.”
“Every protect surface is bespoke,” Aaron continued, “so each time you select a new protect surface, you need to follow this same methodology. This is the repeatable process for deploying Zero Trust. The second step for deploying Zero Trust in each protect surface is to map the transaction flows. I learned this the hard way. Early on, I was working on deploying some technology to a protect surface. There was a Windows 98 computer, and the client said to get rid of it since they couldn't possibly be running any production services there. Of course, it took everything down because it was the polling server between the point-of-sale terminals of about five thousand restaurants. As soon as you took it out, all these restaurants closed for the day because they couldn't process credit cards.”
“What if the software documentation sucks?” Brent asked.
“This is one of the most common issues with implementing software with a Zero Trust approach,” Aaron explained. “You only want to open the ports and the addresses needed and nothing else. I've seen documentation that tells you not to run a firewall at all. Some software guides don't tell you all the ports you'll need to open up, or sometimes they will tell you the wrong port numbers. Sometimes they don't document all the dependencies needed to harden a server, or they call on a library that we didn't know we needed as a prerequisite. You just need to keep in mind that all we're trying to do is create a micro-perimeter around a protect surface. You don't have to lock down everything inside the protect surface, because you're containing the blast radius to that protect surface.”
“That makes sense,” Dylan said.
“For some of the more critical applications, I'll actually recommend running packet captures. For new services, you might run all your traffic through a proxy in a test environment to show you all of the ports that are running,” Aaron said. “But in this case, Dylan, can you run the netstat command on the server and show all the current running network connections?”
Dylan connected to the video wall and pulled up the server next to the window where Harmony was displaying the firewall rules and typed the netstat command. The server displayed a list of connected sessions currently running on the server, showing the protocol, source, and destination addresses. Harmony scrolled through the firewall policies to display the firewall rules so they were side by side with the output from the netstat command.
There were a number of firewall rules, each allowing different ports to be accessed on the SharePoint server.
“Does anyone notice what's wrong with this picture?” Aaron asked.
“The list of ports doesn't match up,” Rose said. “The firewall policy allows a bunch of different ports to be open that aren't running on the server itself.”
“This is more common than you think,” Aaron observed. “Often servers will be decommissioned and new ones built with the same IP address. But no one tells the firewall admin, which it looks like may have been the case here. Dylan, take a note to review your server workflow process to look at decommissioning devices. Does anyone else see anything?”
“I don't understand,” Harmony said. “All of the rules here are about what can talk to Rose's server, but there aren't any rules stopping Rose's server from talking out.”
“Good catch, Harmony. This is one of the most common issues with how admins have configured firewalls for a long time. The idea was called a ‘trust model,’ and the way we trained firewall admins for years was that a server with high trust could always talk down to lower levels of trust with no restrictions. But, as we saw in the SolarWinds case and in all malware cases that have command and control, if you don't have a rule that specifies that this resource can only talk to these certain things, then it can—and will—talk to anything on the Internet. There is never a time that any resource on your internal network should go outbound to an unknown server on the Internet. In Zero Trust, there's no concept of unknown traffic. If it is unknown, it should be blocked automatically by default. This is the problem. By allowing all outbound traffic, you're allowing malware to call out to their command and control networks. If you kill command and control, you're going to kill all this ransomware.”
“You mean just a couple of firewall rules could have prevented this ransomware outbreak?” Nigel asked.
“Everyone wants to know what product to buy to do Zero Trust or to eliminate ransomware. The truth is that you won't know the answer to that until you've gone through the process. Which brings us to the third step in the methodology: architecting our Zero Trust environment. What protections do you have so far?”
Dylan spoke up. “There's endpoint protection already on the server, and there's a firewall in place. What else do we need?”
“This can get complicated quickly,” Aaron said. “It sounds like there's already an out-of-band management system in place for the network devices and servers, which is essential. If this were a public SharePoint site, I might recommend adding a web application firewall, or WAF, to the architecture. But since this isn't a public SharePoint site, I'd actually prefer to just limit the server to talking internally.”
“Rose, is that okay with you?” Dylan asked.
“There's actually some stuff there that isn't public. Can we make sure only people on my team have access?” Rose asked.
“Even better,” Dylan said. “We can just create an address group for your team.”
Aaron chuckled. “A lot of organizations limit access to sensitive servers by IP address so that you can only connect to a server from some secret server admin's desktop. But this isn't Zero Trust. It turns out in practice that attackers are very good at figuring out where those holes are. I'd prefer making a rule based on your role in the organization. Brent, is that something you can help with?” Aaron asked. Brent nodded and pointed out the correct role name for the training team to Harmony.
“This looks a lot like the same architecture that we use for several other of our applications,” Harmony observed. “It's almost like it was copied and pasted from another application.”
“That's how we used to do it in the old days,” Aaron explained. “You'd look at the reference architecture and just copy that for every application you're setting up. Every Zero Trust environment is tailor-made for each protect surface. Until we know what we need to protect and how it works, we can't tell you what controls should be in there.”
“Wearing a one-size-fits-all suit means it's easier to pick your pockets?” Dylan asked.
“It's not the worst analogy I've ever heard,” Aaron responded.
“I've heard some companies hire enterprise architects to do this for them?” Nigel asked.
“Enterprise architecture is a key part of an organization's Zero Trust strategy,” Aaron confirmed. “They're the group that needs to carry the torch for Zero Trust. They're also the ones that have to do all the care and feeding.”
“Cool, so when do we hire these enterprise architects?” Brent asked.
“Oh, I thought you knew.” Aaron laughed. “You guys are the enterprise architecture group. Congratulations. There are a lot of ways to do enterprise architecture. But you don't have to hire someone with the title of architect to do it. Having a cross-organizational team helps eliminate silos and provides much-needed perspective.”
The team all looked at each other in silence. Brent was the first one to speak up. “I knew I should have asked for a raise.”
“The fourth step is to create your Zero Trust policies. I know you're not all firewall administrators, but it's not just about firewall policy. Think about the who, what, where, when, and why. This comes from a Rudyard Kipling poem written in 1902,” Aaron said, pointing to the screen:
I have six honest serving men
They taught me all I knew
I call them What and Where and When
And How and Why and Who
“So you are Kipling's six honest serving men. Excuse me, ladies. Three men and three women. All these ‘Ws’ and ‘Hs’ are layer seven replacements for an old protocol, source IP, destination IP address, rule set. Here is how I break this down,” Aaron said, pointing back to the screen:

John Kindervag's Kipling Method for developing security policies for individual protect surfaces
Courtesy of ON2IT
Aaron's phone rang and he picked it up. He excused himself while the rest of the team reviewed the diagram.
Dylan stood up and walked closer to the screen. “This is different from how I've normally configured policy on a firewall,” he observed.
“But we're not just talking about a firewall anymore,” Harmony said. “We need to secure a whole protect surface. It would make sense to think of security policy from a larger perspective.”
“That makes sense,” Dylan agreed. “We need to think about all the controls we'll use at the same time so we can make them work together.”
“I don't understand the Why column,” Isabelle said.
“I think that's referring to business drivers or regulations,” Dylan said. “The ‘why’ for a policy could be compliance or to achieve a business goal or because it reinforces our Zero Trust strategy. Classification and data ID are about helping classify the data for compliance purposes.”
“What about who?” Isabelle asked. “What about the customers?”
“The ‘who’ is actually why Zero Trust was created,” Aaron said, coming back into the room. “We personify computers and computer networks and extend the same trust that we give to an individual to the ones and zeros flowing over a wire. But today, we can build identity into our firewall rules so that while one individual or role or group can get access to a website, other groups are automatically blocked. Similarly, for the ‘what’ policies, we can write rules based on the Application ID tag of the data that is contained in the payload of the packet. If we were tagging that, we could automate that rule process.”
“And then the ‘how’ statement is, what other things do I need to do to the packet to secure it?” Harmony added. “Do we need to run it through an IPS, or a sandbox, or a URL filter?”
“Exactly,” Aaron said. “Kipling would be proud of us. In this case, let's limit the policy on the firewall to just Rose's team and allow only internal access. That's step four, and then step five is to monitor and maintain.”
“Does that mean that my team needs to monitor the site? Or does someone else do that part?” Rose asked.
“SharePoint and other services like it are a challenge to secure because it's the users themselves who are allowed to share files with other people,” Aaron explained. “For a larger SharePoint site that is hosted online, you should consider looking at a cloud access security broker, or CASB, that has some data leakage protection or DLP capabilities. That's just a fancy way of saying you can use a proxy or endpoint agent to monitor for when people upload files with credit card numbers, for example. But some of those tools will also tell you when a file or folder is shared with the public. In this case, let's just look at who has access manually.”
“There are a lot more people who have access to this site than I expected,” Rose said. “But it looks like these files are all shared with people inside MarchFit. Is that okay?” she asked.
“I'd say that's up to you,” Aaron answered. “This is also a good lesson for us. It's up to the business to decide the answers to many of the questions we'll be asking. Sometimes, we'll need to help educate them about good security practices. But sometimes, they have a business need to share information. For monitor and maintain, we take all of the telemetry—whether it's from a network detection and response tool, or from firewall or server application logs—and then learn from it. As we learn over time, we can make security stronger and stronger.”
“This is a perfect place to pause our discussion,” Dylan said. “It's actually just about time to join the daily status call with the incident response team. Feel free to stand up and grab some coffee while we get the Zoom meeting set up.”
Brent and Nigel stood up and went to the espresso machine, each of them looking at the machine from different angles trying to figure out how to make a cup of coffee. Isabelle demonstrated how the machine worked for them, then took her newly filled cup and went back to the table. Rose excused herself to the washroom just to the side of the entrance of the briefing center. Harmony hunched over her laptop, her face just inches from the screen as she furiously typed an email.
Dylan logged in to their web conferencing tool and displayed it on the video wall, stretching it out along the length of the wall to show all the participants. Kim and Donna were hunched over speaking with Noor while others filed into the main IT conference room. Kim was wearing a different red suit, but Noor was wearing another black suit and black tie. Peter, the security consultant, was sitting next to Noor, and it looked like he hadn't been to sleep yet and was wearing the same suit from the day before, with more wrinkles. April was also in the room, wearing a yellow track suit, and looked like she had just finished a workout. There were also a number of individuals from across the company logged in remotely.
Noor started speaking, and the conference room camera switched to her. “Thanks to everyone for joining. We've really made a lot of progress …” Laughter interrupted her.
“I'm so sorry,” said a voice with a heavy Eastern European accent barely containing their laughter, “please continue.”
“I'm sorry, who is speaking?” Noor asked. Dylan began scrolling through the long list of participants to see who was talking. His heart dropped when he saw the name “3nc0r3” in the list. Someone clicked the picture of the speaker, and the grainy image of a man in a black hoodie wearing a mask from the band KISS, the one with a star over one eye, took over the whole screen.
“Shut down the conference line,” Dylan said urgently, “it's the cybercriminal. He's Zoom-bombing us.”
“I wouldn't hang up on me, if I were you. It's very rude,” 3nc0r3 said, still laughing. “I've been listening to your conference calls. I know you have decided not to pay my ransom. But this is big-time mistake.”
“Don't take it personally,” Noor suggested. “It's just business.”
“I like America. You do good business. Lots freedom of speeches. You talk so much, but wonder if you want the world to know what you say?”
“What are you talking about?” Noor asked.
“Oh, no,” Dylan muttered.
“We have many megabytes of data,” 3nc0r3 confirmed. “I know you've been discussing not paying the piper. I will release them to the world if you do not pay the ransom.”
Kim leaned over to whisper to Noor, “If that's all he has, then …”
“Oh, so sorry,” 3nc0r3 corrected. “I meant terabytes. Always get those confused. 753 terabytes. I'll post a sample online now just to show seriousness. Nothing personal, it's just business.” He smiled and then dropped from the video conference.
April pulled up her phone and said, “He's already posted the link to download the sample file.”
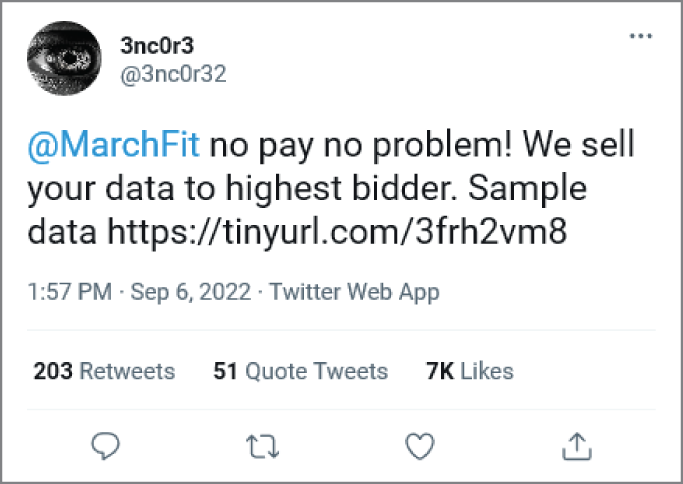
Tweet from the cybercriminal 3nc0r3 sharing a link to sample data online to prove that he had actually stolen MarchFit information
Peter seemed to wake up at that point. “Nobody download that file. I'll grab it and put it through our sandbox to make sure it doesn't have more ransomware.”
Key Takeaways
To be successful at anything, and especially in cybersecurity, you need a strategy to achieve your goals. In cybersecurity, the goal is to avoid being breached. Zero Trust is that strategy for success. But what makes a successful strategy? A strategy is a plan to achieve your goals. But you also need to know when you're making progress toward your goals, which is why the best strategies are measurable. There are a number of concepts in cybersecurity that sound like strategies but actually aren't:
- Defense in depth—Often, defense in depth is compared to an onion; it has multiple layers. But how many layers do you need before you're secure? In this way, defense in depth fails as a strategy because it's not measurable.
- Compliance—Many businesses are required to be in compliance with many different compliance frameworks. Although being compliant may be measurable, the goal isn't to be secure. Compliance is often a minimum starting place that regulators can agree on, but the unique needs of each business require a more tailored approach.
- Best of breed—Best of breed versus platform is more of a philosophical debate about the effectiveness of tools. The goal of this approach isn't to prevent a breach; it's to find the best vendors.
The Four Zero Trust Design Principles
The first and most important principle of your Zero Trust strategy is to ensure that you understand how the business makes money and what the organization hopes to achieve. Zero Trust should align with business outcomes, not prevent the business from operating effectively. There are a huge number of tools or products available to help you along in your Zero Trust journey, but it's important to always keep these four principles in mind to stay focused on the big picture:
- Focus on business outcomes.
- Design from the inside out.
- Determine who/what needs access.
- Inspect and log all traffic.
The Five-Step Zero Trust Design Methodology
To make your Zero Trust journey achievable, you need a repeatable process to follow. The first step is to break down your environment into smaller pieces that you need to protect. Many organizations focus on reducing the scope of their attack surface. An attack surface is all the possible points of attack a threat actor could leverage to access a system and steal or exfiltrate data. In practice, the attack surface for a global organization with users working remotely could encompass the whole world. Rather than focusing on your “attack surface,” which is huge and hard for you to control, the Zero Trust design methodology focuses on what you can control: protect surfaces. Each protect surface helps you limit the blast radius of any attack to just that portion of your environment by doing the following five steps:
- Define the protect surface.
- Map the transaction flows.
- Architect a Zero Trust environment.
- Create Zero Trust policies.
- Monitor and maintain.
The Zero Trust Implementation Curve
When beginning your Zero Trust journey, you'll need to start by going through the five-step methodology on non-business-critical systems. You want to create an environment for learning where making a mistake won't impact your organization. If you already have a Business Continuity Plan (BCP) or a Business Impact Assessment (BIA), these documents should have already categorized the applications that are most important to your business. Once you are ready to begin working on critical protect surfaces, you should focus on the most important systems first to protect your crown jewels as quickly as possible:
- Learning protect surfaces
- Practice protect surfaces
- The “crown jewels” (aka business-critical protect surfaces)
- Secondary protect surfaces
- Tertiary protect surfaces
