Devices and Components Commonly Found in the LAN-to-WAN Domain
The LAN-to-WAN Domain represents a point of transition between more secure LANs and far less secure WANs. In this section, you’ll learn about the devices and components you’ll commonly find in the LAN-to-WAN Domain. Once you’ve learned about the devices and components, you’ll learn about controls to ensure compliance in the LAN-to-WAN Domain.
Routers
A router is a network device that connects two or more separate networks. In the context of the LAN-to-WAN Domain, a router makes the actual connection between the LAN and the WAN. A router can be a standalone network device or it can be software that runs on a computer. In either case, the hardware must contain at least two network interfaces—one for each network. A router works by inspecting the address portion of the packet and forwarding the packet to the correct network.
The process of examining each packet is time consuming and can slow your network down. Newer network devices and software often contain support for Multiprotocol Label Switching (MPLS). MPLS networks add a simple label to each network packet. The routing devices in the network forward packets based on the address in the label as opposed to data in the header portion of the packet. MPLS can dramatically increase the speed and usefulness of your network in two important ways:
MPLS takes less time to process each packet because the router only has to look at the packet’s label.
MPLS devices create virtual links between nodes that can transport higher-level encrypted packets.
Firewalls
A firewall is a network security measure designed to filter out undesirable network traffic. Like a router, a firewall can be a network device or software running on a computer. Firewalls provide an important security capability. You can define rules for each firewall that tell the firewall how to filter network traffic. You can restrict which packets you allow to flow through the LAN-to-WAN Domain. Firewalls give you the ability to aggressively control what types of information can travel between your LANs and WANs.
The simplest type of firewall is a packet-filtering firewall. The firewall examines each packet and decides on an action to take after comparing the packet’s attributes with the firewall rules. Rules commonly instruct firewalls to deny or forward packets based on the target application, Internet Protocol (IP) address, and port. You can create rules based on other criteria as well. However, protocol, IP address, and port filtering give you the ability to restrict most unwanted traffic from passing through the firewall.
Proxy Servers
A proxy server is a type of firewall that makes requests for remote services on behalf of local clients. The proxy server receives a request from a client and evaluates the request based on its defined rules. If it determines that the request is authorized, the proxy server forwards the packets to the remote server, using its own IP address as the source address. In this way, a proxy server hides the true source’s identity. The remote server only sees the IP address of the proxy server. Figure 11-3 shows how a proxy server forwards requests to remote resources.
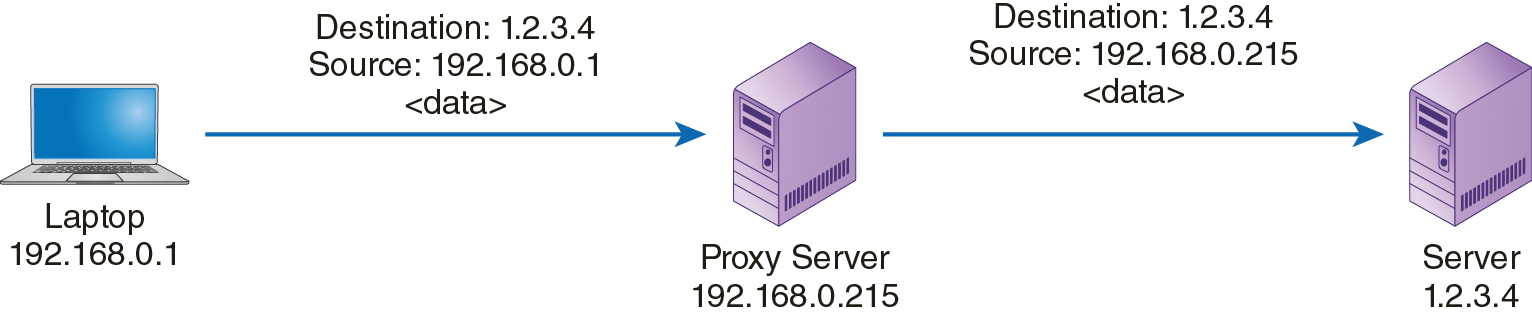
FIGURE 11-3 Network Request Using a Proxy Server
The proxy server keeps a record of sent messages in an internal table. Unless an error occurs, the remote server should send a response to the initial request. When the proxy server receives the response, it looks up the true address of the client that sent the original request and forwards the response to the client.
Proxy servers have several uses. Because they process all network traffic between clients and remote servers, they work well as content filters. Proxy servers can filter unwanted or inappropriate content using many different types of rules. Web content filters examine web-based traffic and can block web content that does not adhere to your organization’s Internet or web acceptable use policy (AUP).
DMZ
A major concern of business is how well protected the servers in the DMZ are. In other words, how well are you protecting my website? Businesses are particularly concerned about website availability and integrity. The websites for many companies represent their public image and major sales channel.
Security policies set strict rules on how DMZ traffic should be limited and monitored. Security policies outline how the DMZ server should be configured and how often security patches should be applied. Security policies also outline how often external penetration testing is conducted. Penetration testing probes and tests the network for weaknesses and vulnerability from the outside looking in. Penetration testing is required by many standards and is considered best practice.
The LAN-to-WAN Domain marks an important transition for data. Data flowing from a WAN to your LAN moves from an unsecure domain to a secure domain. It is generally a poor idea to allow any users to access resources inside your secure LANs. It is important to positively identify users to properly control access to your organization’s resources. On the other hand, many organizations do want to provide internal information to anonymous users. For example, most online retailers want anonymous users from the Internet to visit their sites and browse through their products. How do you allow anonymous users to access your data without compromising it?
The answer lies in creating an area of your IT infrastructure that allows access for anonymous users but aggressively controls information exchanges with internal resources. This special zone is connected to both the Internet and your internal secure network. A DMZ is a separate network or portion of a network that is connected to a WAN and at least one LAN, with at least one firewall between the DMZ and the LAN. Figure 11-4 shows a simple DMZ with one firewall.
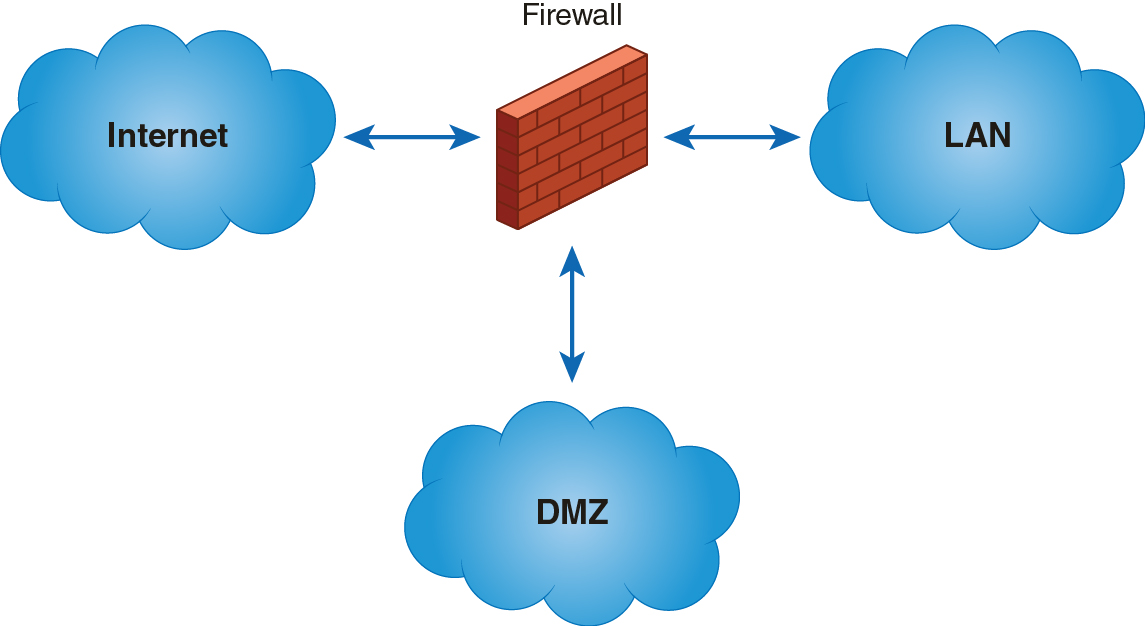
FIGURE 11-4 Simple Dmz with One Firewall
A very common use of DMZs is for web servers. Users from the Internet can access your web server and see pages generated from the web server. The web server can make limited connections to your application and database servers in your LAN. The firewall blocks connections from Internet users to your LAN but allows the web server to connect. One danger is that an attacker could compromise your web server and use it to either connect to your LAN resources or perhaps use the web server to launch attacks on other computers. To help protect your DMZ servers from launching attacks, you can add a second firewall between the DMZ and the WAN. This firewall would filter outbound traffic and would stop attacks originating from within your DMZ. Figure 11-5 shows a DMZ with two firewalls.
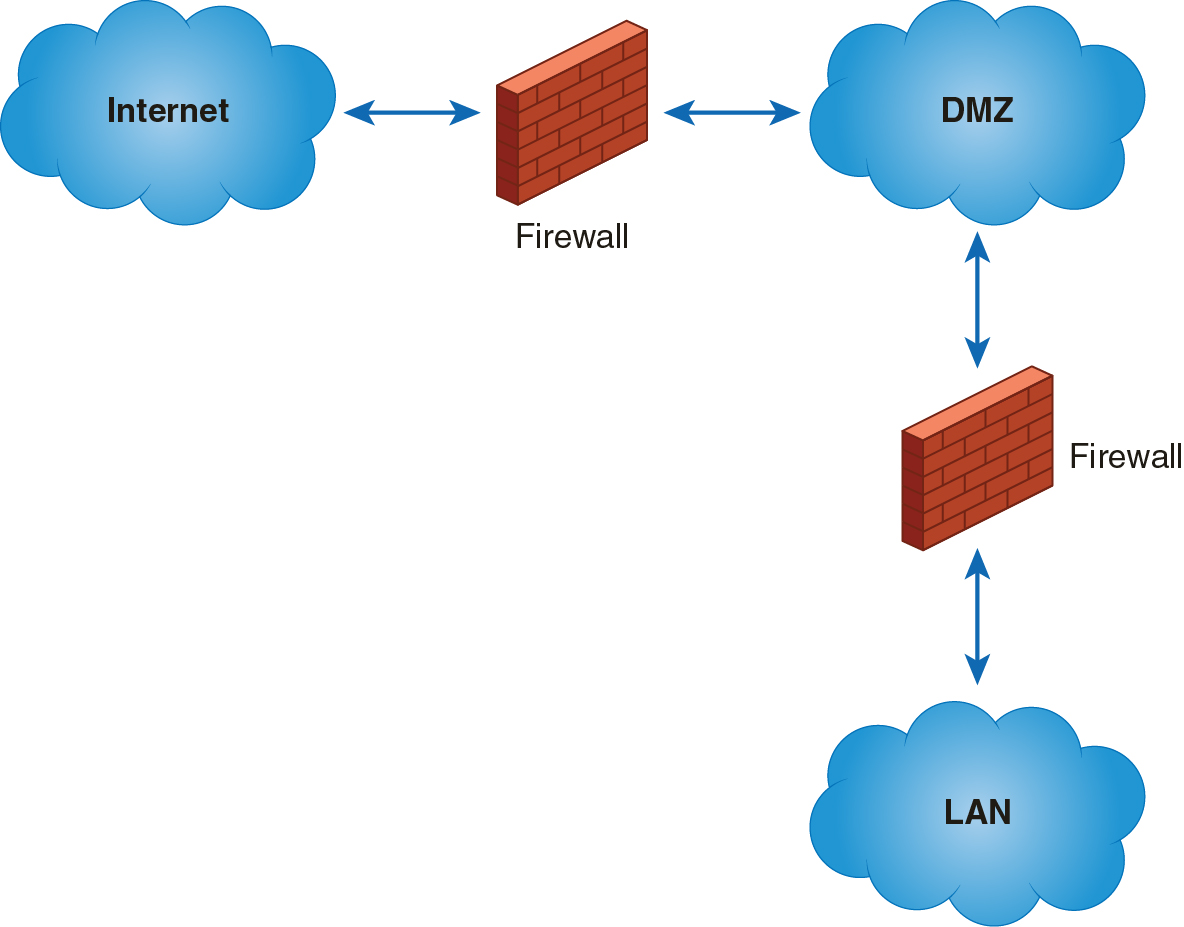
FIGURE 11-5 Dmz with Two Firewalls
Virtual Private Network Concentrator
The Remote Access Domain refers to the technology that controls how end users connect to an organization’s LAN remotely. An example would be employees who need to connect to the office network from their homes. This capability has been critical during the COVID-19 pandemic that started in 2020. Remote access has allowed organizations to keep running while protecting their workforce.
A virtual private network (VPN) concentrator is a network device that establishes secure communications between two end points, such as an employee's home network and the company network. Routers can also be used to create a VPN connection. The difference is that VPN concentrators can serve up to thousands of users at the same time beyond the capacity of many routers. It can create VPN tunnels for each employee, securing their connections to the companies’ network no matter where they are in the world.
The key benefit of a VPN connection is that all data within the connection (referred to as a VPN tunnel) are encrypted. This protects both the data within the tunnel and the connection. The organization must establish well-defined policies to ensure controls are consistently deployed. Following are typical policy examples related to VPN connections:
It is the responsibility of employees with VPN privileges to ensure that unauthorized users are not allowed access to the corporate network.
Multifactor authentication must be used to initiate a VPN session.
When actively connected to the corporate network, VPNs will force all traffic to and from the workstation over the VPN tunnel; all other traffic will be dropped.
Dual (split) tunneling is NOT permitted; only one network connection is allowed.
All computers connected to corporate internal networks via VPN or any other technology must use the most up-to-date corporate-approved anti-virus software.
VPN users will be automatically disconnected from the corporate network after 30 minutes of inactivity.
The VPN concentrator is limited to an absolute connection time of 12 hours.
Only corporate-approved VPN workstation client software may be used.
For discussion purposes, focus less on each of these individual examples and more on types of policies the auditor should expect. Policies should be clear and concise and at a sufficient level of detail that the corresponding control can be tested for operational effectiveness. Additionally, with the expansion of VPNs due to the COVID-19 pandemic, many homes are now extensions of the corporate office. Policies need to cover both physical and technical requirements. For example, the physical requirements for working from home may require users to lock up company documents at home and ban family members from accessing company assets.
Network Address Translation (NAT)
Network address translation (NAT) enables a local area network (LAN) to map internal IP addresses to external IP addresses. Typically, these translation tables are maintained and performed within network routers.
NAT services have three main benefits:
To hide internal IP addresses from the outside
To allow for more internal IP addresses
To merge multiple internal networks to form a single Internet connection.
Internet Service Provider Connections and Backup Connections
The purpose of the LAN-to-WAN Domain in most organizations is to provide a method to connect your LANs to the Internet. Connecting to the Internet is easier than ever before. All you have to do is establish an account with an Internet service provider (ISP). The ISP provides at least one method to connect your device to its network. After you have connected to its network, the ISP routes traffic from your environment to the Internet.
Your network relies on the connection to your ISP to establish Internet connections. If the connection to your ISP goes down for any reason, you’ll lose your connection to the Internet. A single ISP connection means a single point of failure. With a single point of failure, many components depend on a single component. If the single component fails, all other dependent components essentially fail as well. Figure 11-6 shows a single ISP connection that represents a single point of failure.
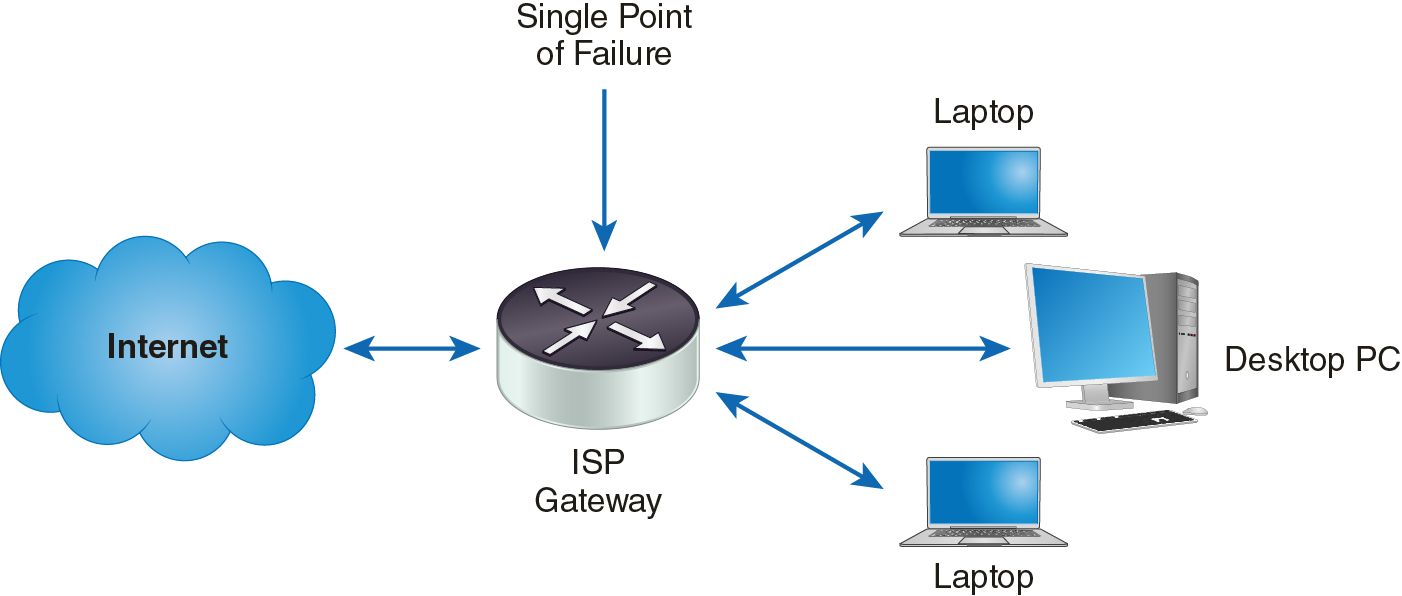
FIGURE 11-6 ISP Connection Single Point of Failure
Make sure you develop an alternative Internet connection plan to avoid a single point of failure. You’ll learn how to accomplish this in the “Dual-Homed ISP Connections” section later in the chapter.
Cloud Services
The use of cloud services is mainstream in the United States with 90% of the companies surveyed by O’Reilly in 2021. The migration to the cloud includes core applications. The survey indicates that 48% of the companies plan on moving more than 50% of their applications to the cloud, while 20% have already moved all their applications to the cloud.
What does it mean to move to the cloud? In the survey, it was clear the migration referred to corporate applications. Hosting applications in the cloud is only one potential service available to a company migration to the cloud. Additionally, the three main cloud services models include:
IaaS cloud services provider manages all the networking, data storage, and servers typically found in a traditional data center. The data center facilities are owned by the cloud service provider. The company manages the running of the servers and system and application software.
PaaS cloud service providers manage everything under IaaS plus run servers and system software. The company manages the application software.
SaaS cloud service providers manage everything under IaaS and PaaS plus run the application software. The company becomes a user of the application software with varying application privileges.
These definitions can vary depending on the cloud service provider. For example, some cloud providers offer Network as a Service (NaaS). NaaS is a subset of IaaS in which only network services are provided. Table 11-1 illustrates a high-level comparison between the three cloud services models.
TABLE 11-1 High-level comparison among IaaS, PaaS, and SaaS.
Intrusion Detection Systems/Intrusion Prevention Systems
Firewalls are extremely effective at filtering out known unwanted traffic. However, attackers are getting more and more sophisticated all the time. A firewall is only as good as its rules. Because most firewall rules are based on static attributes, they aren’t effective at protecting a network from all types of attacks.
For example, suppose an attacker compromises one of your trusted servers and installs a distributed denial of service (DDoS) agent. On command, the agent starts sending large volumes of messages to different hosts. Your firewall sees all the messages but forwards them because they originated from a trusted server. The result is a successful DDoS attack.
A type of network measure that can help in this situation is an intrusion detection system (IDS). An IDS is either a network hardware device or software that monitors real-time network activity. It compares the observed behavior with performance thresholds and trends to identify any unusual activity. If it does identify unusual activity, it sends a notification to someone who can explore the situation and react appropriately. Some systems provide the ability to automatically take action. An intrusion prevention system (IPS) extends the IDS capability by doing something to stop the attack. In the preceding example, the IPS could modify firewall rules to deny any traffic originating from the compromised server. This simple action would stop the attack.
Data Loss/Leak Security Appliances
As the volume of information flowing around networks increases, so does the concern that sensitive data will leak out of the protected environment into the public domain. Compliance requirements often place restrictions on data and how you must handle it. For example, the Payment Card Industry Data Security Standard (PCI DSS) requires your organization to protect credit card numbers both at rest and in transit. You can ensure your applications and databases protect credit card numbers, but what about other forms of data transfer? How do you protect credit card numbers in email messages?
Data leak security appliances (also called data loss security appliances) are network devices or software running on computers that scan network traffic for data-matching rules. The rules differ for each organization but would likely include patterns for matching credit card numbers, Social Security numbers, and other sensitive information for organizations enforcing PCI DSS compliance. Other requirements for protecting sensitive data would result in additional rules. The data leak security appliance helps detect and prohibit data that would otherwise leak to the public due to oversight or error. It is one more layer in a multilayered approach to security.
Web Content Filtering Devices
As you learned earlier, a web content filter is a specific type of proxy server. In addition to forwarding web requests to a remote web server, the filter scans all traffic and applies content rules. These content rules conform to the organization’s Internet AUP. Web content filters are common in many organizations that provide Internet access. The goal is to provide Internet access that is necessary or desired for appropriate users while denying inappropriate Internet use.
A web content filter evaluates content based on several different criteria, including the following:
Blacklist—This provides a list of uniform resource locators (URLs) or Domain Name System (DNS) entries from which all transfers are blocked.
URL filter—This involves scanning and evaluating URLs for inappropriate content using a dictionary of inappropriate search items.
Content keyword filtering—This involves evaluating text in content for inappropriate content using a dictionary of inappropriate search terms.
Content analysis—This involves evaluating text and nontext content for inappropriate content.
Data classification is a useful way to rank the sensitivity of data to the organization. When data are properly labeled with classification, they can be filtered as they leave the organization. Data classification be an important tool to stop sensitive information from leaving the organization. For example, there is often a requirement in companies to block emails that are sent to external users if the email contains an attachment with confidential data or customer account information. But how do you know what type of data is contained in an email? Classifying data is one approach with allows the software to examine the contents of an email and block certain data types from leaving the internal network.
While data classification can be a powerful tool, it can be challenging to enforce. Classifying data can be time-consuming if not fully integrated into the day-to-day activities of the company. Executive support is key to policy enforcement. At some point in the enforcement process, you need to change behaviors. This takes some form of disciplinary action. Even pulling someone to the side and coaching workers run the risk of negatively impacting morale. It is important that you lay the foundation for such discussions in advance. You accomplish this through the executive of the department explaining the importance of data classification and how it helps the company to protect its customers and comply with the law. This executive can send a clear message that there is zero-tolerance for ignoring such policies. The executive can also be clear that when violations of policies are brought to their attention they will be taken seriously. This type of message establishes a tone at the top.
Traffic-Monitoring Devices
Traffic-monitoring devices monitor network traffic and compare performance against a baseline. Traffic monitors can help detect network issues by identifying performance problems and alerting administrators to the problem. Network problems can be caused by the following:
Denial of service (DoS) or DDoS attacks
Device or communications failure
Bandwidth saturation
In any case, it is important to know when a problem develops. Traffic-monitoring devices can often alert administrators to emerging problems that can be addressed before they become critical.

