Compliance Law Requirements and Business Drivers
Organizations rely on distributed architecture. Many organizations deploy their enterprise applications as distributed applications. Today many core applications are being migrated to the cloud. Although the actual applications and resources belong in other domains, clients need the ability to access resources and run distributed programs. Providing the ability to connect to geographically diverse resources is the main purpose of the WAN Domain. Although making your resources and data available to more users is a good thing, you must pay close attention to security. Keeping your data secure as they leave your network takes advance planning. Always consider how secure your data are in each of the domains of your IT infrastructure. Figure 12-1 shows the WAN Domain in the context of the seven domains in the IT infrastructure.
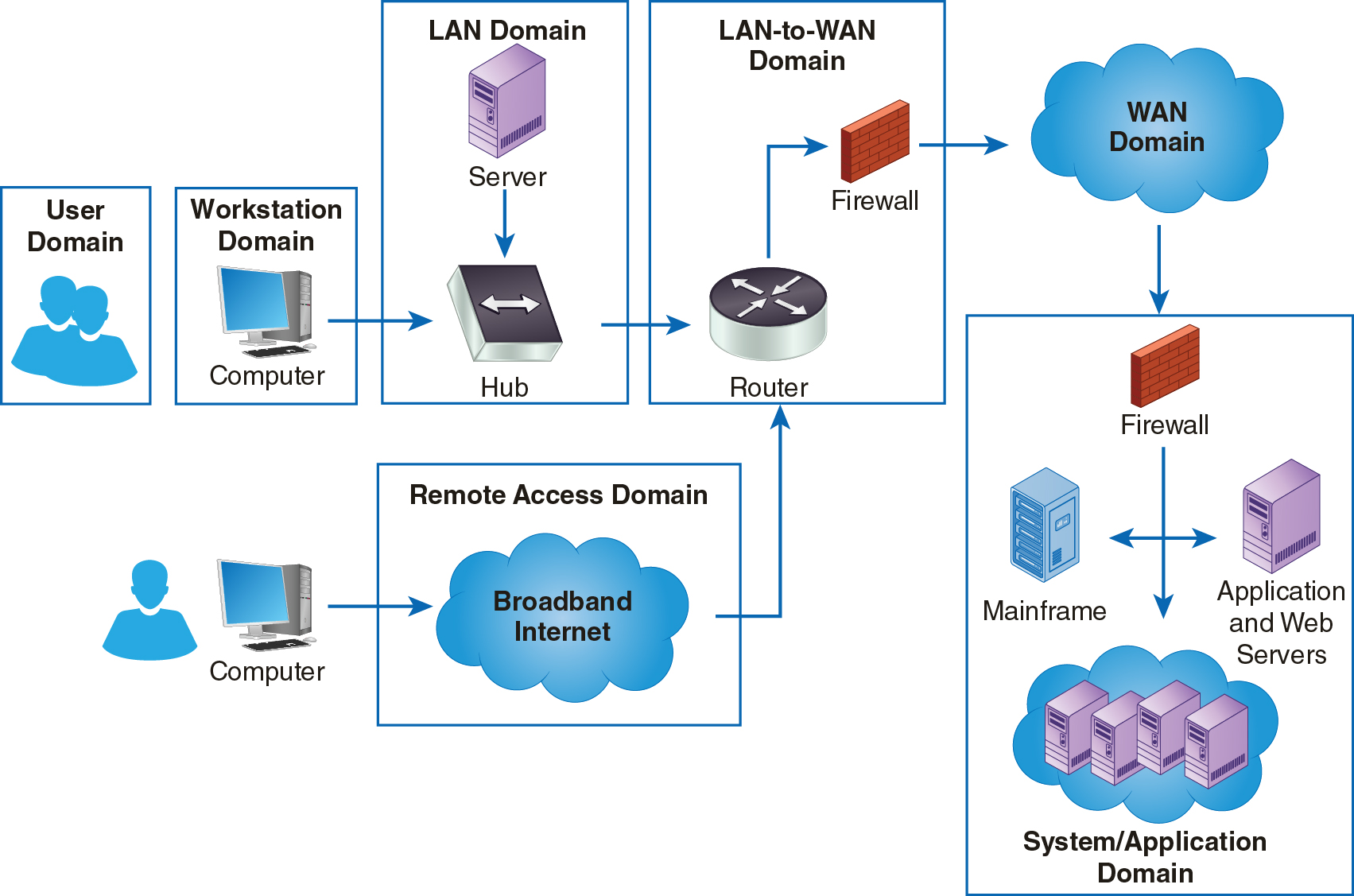
FIGURE 12-1 The WAN Domain within the seven domains of a typical IT infrastructure.
Your responsibility to keep your data secure does not stop when data leave the controlled area of your networks. The WAN Domain represents an area that might be out of your control. Your responsibility to secure data means to protect it in such a way that it is secure even when traveling across an untrusted network. Ensuring data are safe even in the WAN Domain makes it possible for your organization to deploy distributed applications that can provide unprecedented functionality to remote users. Implementing the controls necessary to support your security policy in the WAN Domain makes your organization more secure and allows you to provide a higher level of visibility to your data.
Protecting Data Privacy
WANs allows you to connect to your headquarters to several branch offices using a WAN. You connect each of your LANs to the WAN and all your nodes can communicate. The only problem is that you now depend on another organization to communicate. Each time you send a message from your headquarters to a branch office, that message travels across someone else’s network. You no longer have control over who sees your network traffic or who can alter it. Figure 12-2 shows how data traveling from one of your nodes to another across a WAN are out of your control.
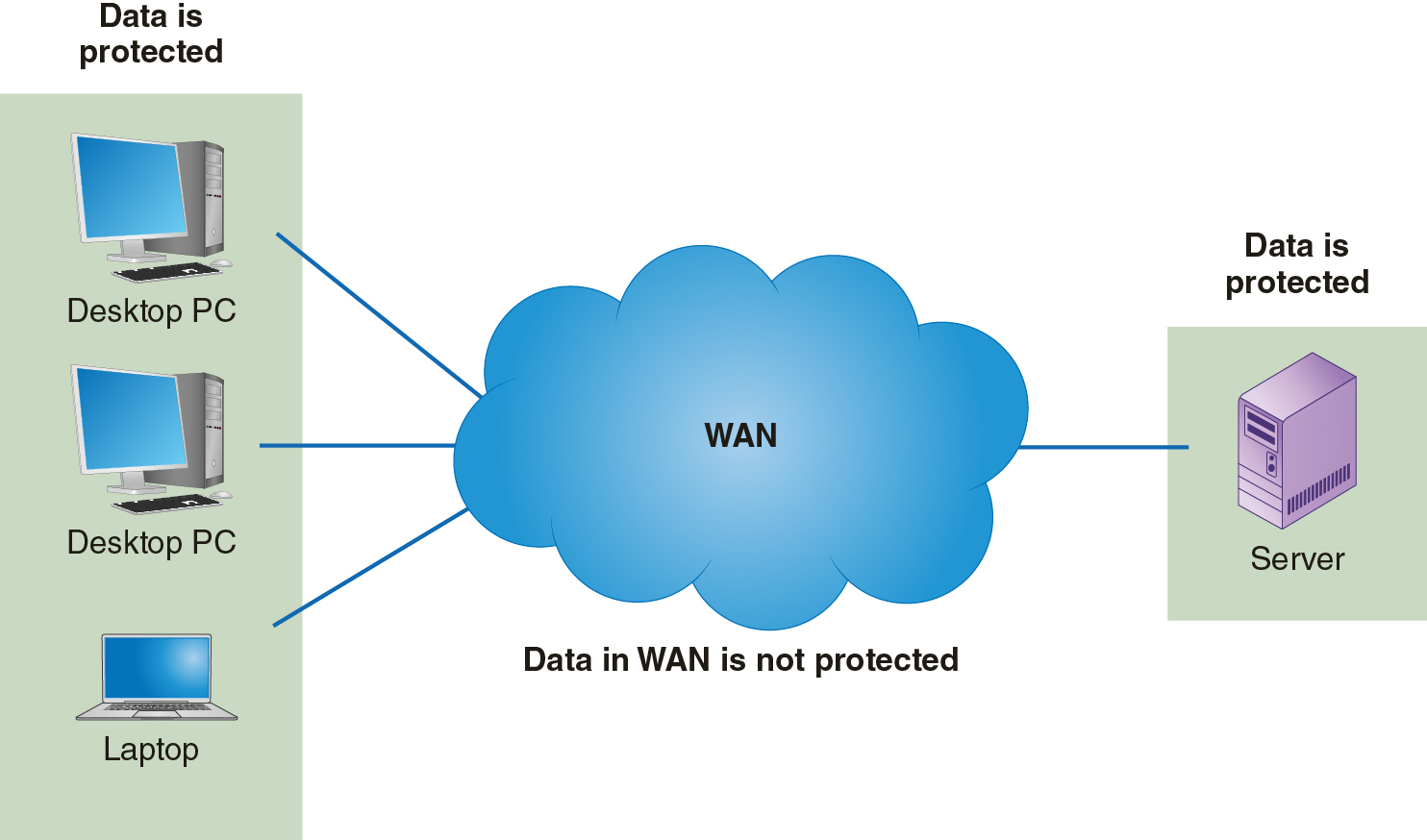
FIGURE 12-2 Lack of control for data traveling across a WAN.
Creating secure communications over a WAN is not completely out of your control. Deciding on the best WAN solution for your business depends on your requirements and budget. Security policies outline how each connection type should be configured and protected. The security policies also outline roles and responsibilities. Keep in mind that private WANs security is typically configured by the service provider. Your security policies need to include how to deal with the vendor and how to validate the security configuration.
The biggest question for companies using the Internet to connect their offices is how to keep communication secure and private. A common solution is called a virtual private network (VPN). VPN solutions can be managed in-house. By setting up network devices at both offices, you can create an encrypted tunnel. All communications between the offices are then protected from eavesdropping, and the data passed through the tunnel remain secure. There are dedicated network devices whose only function is to create and manage VPN traffic. These devices are called VPN concentrators. Many firewalls also have the capability to create and maintain a VPN tunnel.
SD-WAN
When it comes to WAN, the business is generally concerned with reliability, speed, and cost. An emerging network, SD-WAN in many ways better balances these interests. Several companies are competing for this emerging market, with each providing unique offerings.
To best illustrate and drive a deep understanding of what SD-WAN is and how it differs from the traditional WAN, we will examine Cisco’s SD-WAN offering. When we use the term SD-WAN in this chapter, we are referring to Cisco’s offering. Nonetheless, for discussion purposes, the Cisco approach to the SD-WAN network model is broad and provides a good illustrative model of the broader SD-WAN architecture.
The traditional WAN would connect the home office to the branches through a circuit. As a company grows into hundreds of branches, the number of dedicated circuit connections can get enormously expensive. Each of these connections must be encrypted. Essentially, we securely connect through the WAN to each branch site. We can look for a cheaper solution using an Internet connection to the home office, but it cannot guarantee reliability like a dedicated circuit.
What is SD-WAN, and how does it differ from the traditional WAN? The game-changer was the migration of core transition data center applications into the cloud. The Internet has been with us for a long time, but the migration of applications to the cloud has changed the way we think about accessing these applications. Today you may be using Office 365, Google Drive, or Dropbox. Many applications can now sit in Google Cloud or Azure.
Traditionally a branch would connect to the home office to access the application, then on the same circuit consume the information. As applications moved to the cloud, the old model no longer made sense in all cases. It does not make sense for a branch to access the home office, the home office to access the cloud, and then return the cloud information back to the branch, especially if the home office is thousands of miles away and the cloud application is hosted close to the branch.
We have to make sure all these connections work seamlessly, reliably, and fast. SD-WAN extends traditional WAN by adding local Internet connections to the branch. The traditional WAN circuit can still exist in the branch. Thus SD-WAN augments WAN capability; the SD-WAN model does not replace the traditional WAN model. You still have routers (referred to as the data plane) that send data from branch to home office. Under SD-WAN, the control plane has become a lot smarter and is no longer part of the router but a standalone management system. From an auditor’s lens, these management systems contain the rules that need to be assessed.
This decoupling of routing decisions (i.e., control plane) from the router itself means the router has less CPU-intensive work, which leads to higher performance capability. But simply decoupling the control plane and data plane does not make it smarter. What does make it smarter is that these management systems (including the control plane) can monitor the WAN connections and make smarter decisions.
Sometimes circuits would go down, and we would have failover to the secondary circuit. That works, but then you have other times where performance for some apps might just be poor over one circuit. It wasn’t down; it was just degraded. Consequently, it would not failover. The user would see agonizingly slow or no responses. From the user’s standpoint, the circuit is unusable. Yet a perfectly good secondary circuit was not accessible because there was no failover. Under SD-WAN, the performance of both circuits is monitored, and traffic routed appropriately. If the primary circuit biomes are degraded, traffic is routed to the secondary circuit.
These routing rules under SD-WAN can also apply to specific applications such as Voice over Internet Protocol (VoIP). We’ve all experienced VoIP phone calls that sound like an echo or with lots of static. Under SD-WAN, you could set a threshold value, for example, 100 milliseconds of latency or below. When that threshold is exceeded, the VoIP call is routed to an alternative circuit.
From a branch location view, you can have an SD-WAN with the traditional circuit to the home office and an alternate connection to the Internet. The smarter SD-WAN model will automatically route the user to the best connection! What does this mean for the user? If they are accessing an Internet application, they no longer have to travel back and forth to the home office. The user automatically is routed to the Internet if that is the fastest path to the application. Poor local Internet connection. No problem. The user is routed to the home office Internet connection through the traditional WAN circuit. Cisco has reported seeing in some highly distributed environments, as much as 40% improvement in performance using SD-WAN over the traditional WAN.
The SD-WAN model brings more information capability than is possible with a traditional WAN. Under an SD-WAN model, you can apply filtering rules to network traffic. This highly simplifies filters such as URL filters. Rather than applying those filters at every endpoint, such filters can be defined once and applied across the entire WAN traffic.
In sum, many experts look at software-based WAN network models, such as SD-WAN, as the trend in the near future.
Implementing Proper Security Controls for the WAN Domain
The primary control type you will use in the WAN Domain for any data is encryption. You have many encryption choices, and the right control depends on how you’ll use the data and which component applies the encryption methods. Your application may encrypt your data, or another component may encrypt the connection in another domain. You will learn about different approaches to encryption later in this chapter. Some solutions require multiple layers of controls. You select the best controls that support a few general principles. These are the same principles that apply in the LAN-to-WAN Domain:
-
No data in the WAN Domain should ever be transmitted in cleartext.
-
When using encryption, select the algorithm based on needs. Don’t just select the largest key.
-
Assume an attacker can intercept and examine any network messages.
Figure 12-3 shows a simple diagram of how a VPN tunnel protects encrypted data as it moves across the Internet.
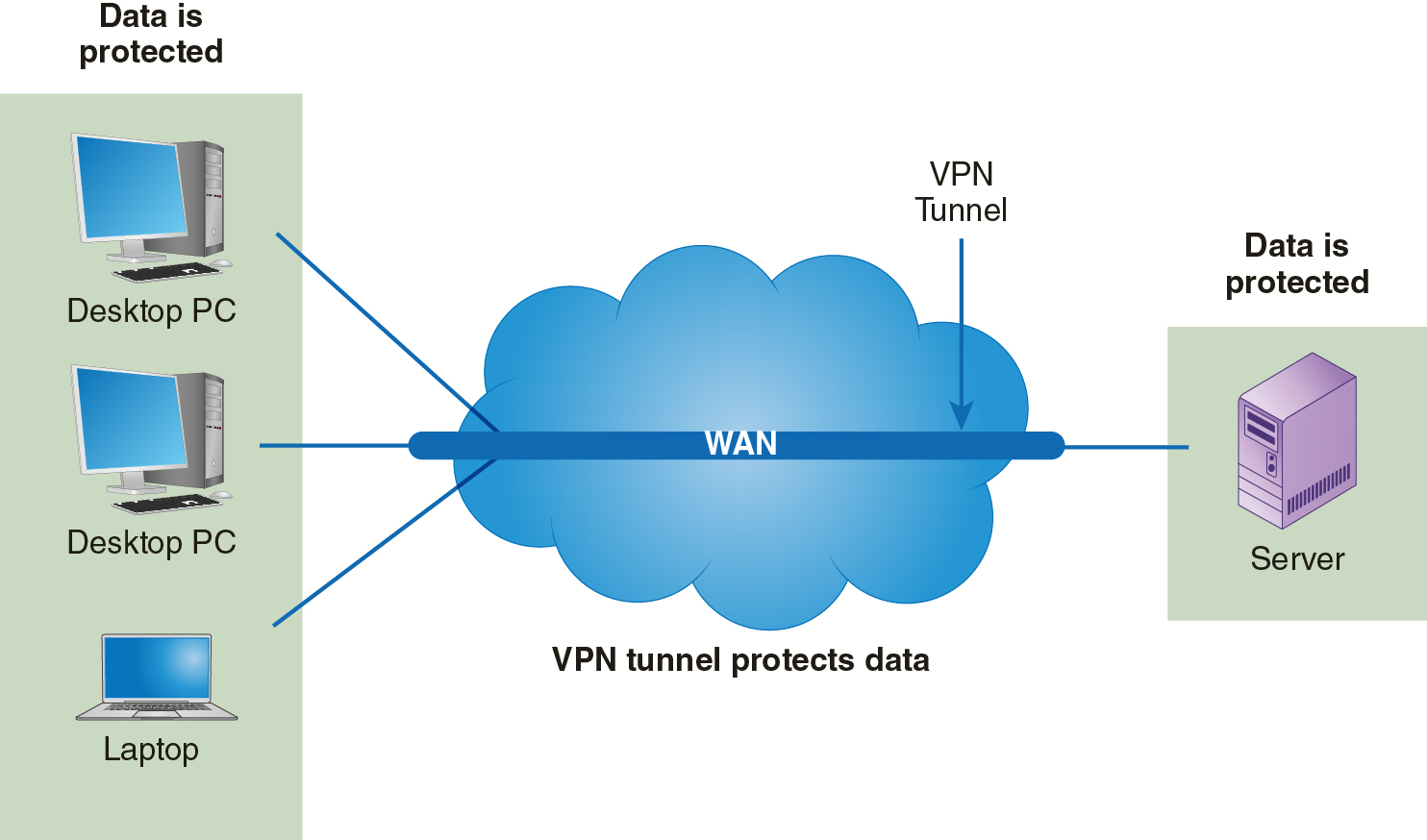
FIGURE 12-3 Protecting WAN traffic using encryption.
