| 5 | Recognizing Lock-In |
Visionaries tell us that the Internet will soon deliver us into that most glorious form of capitalism, the “friction-free” economy. How ironic, then, is the event that will usher in the next millennium: the dreaded Year 2000 Problem, a testament to the enormous rigidities that plague the information economy.
We agree that the Internet will make shopping easier than ever, but much of the talk about friction is fiction. You don’t have to drive to the store to order a new computer, but your choices for the future will still be hemmed in by the selections you made in the past. Like it or not, in the information age, buyers typically must bear costs when they switch from one information system to another. Understanding these costs of switching technologies, or even brands, is fundamental to success in today’s economy.
Compare cars and computers. When the time comes to replace the Ford you’ve been driving for several years, there is no compelling reason to pick another Ford over a GM or a Toyota. Your garage will hold a Chevy just as well as a Ford, it won’t take long to learn the controls of a Toyota, and you can haul the same trailer with either vehicle. In short, you can easily transfer your investments in “automotive infrastructure” to another brand of car. In contrast, when the time comes to upgrade the Macintosh computer you’ve been using for years, you are going to need a mighty good reason to pick a PC or a Unix machine instead of another Mac. You own a bunch of Mac software, you are familiar with how to use the Mac, your Mac printer may have years of good service left in it, and you probably trade files with other Mac users. You are facing significant costs if you decide to switch from one information technology to another.
With the Mac you have made significant durable investments in complementary assets that are specific to that brand of machine. These investments have differing economic lifetimes, so there’s no easy time to start using a new, incompatible system. As a result, you face switching costs, which can effectively lock you into your current system or brand.
When the costs of switching from one brand of technology to another are substantial, users face lock-in. Switching costs and lock-in are ubiquitous in information systems, and managing these costs is very tricky for both buyers and sellers. Simple rules, such as “Don’t get locked in” or “Evaluate costs on a life-cycle basis,” don’t help much. In using or selling information systems, fully anticipating future switching costs, both yours and those of your customers, is critical. Lock-in can be a source of enormous headaches, or substantial profits, depending on whether you are the one stuck in the locked room or the one in possession of the key to the door. The way to win in markets with switching costs is neither to avoid lock-in nor to embrace it. You need to think strategically: look ahead and reason back.
This advice probably seems a bit cryptic, but its implications will become clear in this chapter and the next. Here we describe the common patterns that give rise to switching costs so as to help you properly measure switching costs and recognize situations involving lock-in. In the next chapter we’ll show you how to use lock-in to your advantage, or at least to neutralize others who try to use it against you.
But before classifying switching costs and analyzing business strategy in the presence of lock-in, let’s look at a few examples of the problems it can cause.
EXAMPLES OF LOCK-IN
The best way to understand the phenomenon of lock-in is to examine lock-in in action. The examples here show how large companies (Bell Atlantic) and individuals (with assigned telephone numbers) alike can fall prey to lock-in.
Bell Atlantic
In the mid- to late-1980s, Bell Atlantic invested $3 billion in AT&T’s 5ESS digital switches to run its telephone network. These are large, complex devices that sell for millions of dollars each—essentially, specialized mainframe computers linked to transmission and other equipment. In effect, Bell Atlantic selected AT&T over Northern Telecom and Siemens to bring its telephone system into the digital age. No doubt AT&T’s switches were impressive at the time, but did Bell Atlantic look ahead to the mid-1990s and take steps to protect itself from the ensuing lock-in?
The problem? The 5ESS switches employ a proprietary operating system controlled by AT&T. So, every time Bell Atlantic wanted to add a new capability, or connect these switches to a new piece of peripheral hardware, Bell Atlantic found itself reliant on AT&T to provide the necessary upgrades for the operating system and to develop the required interfaces. Since it was extremely expensive for Bell Atlantic to replace the AT&T equipment, Bell Atlantic was locked into the AT&T switches.
This left AT&T in the driver’s seat. AT&T was in the powerful position of having monopoly control over a wide range of enhancements and upgrades to its switches. For example, when Bell Atlantic wanted its system to be able to recognize toll-free calls to telephone numbers beginning with “888,” Bell Atlantic had to negotiate with AT&T, since AT&T had not provided Bell Atlantic with the computer code necessary for Bell Atlantic to develop this capability itself. Dealing from a position of strength, AT&T charged Bell Atlantic $8 million for the software that recognized 888 numbers. Similarly, when Bell Atlantic wanted to offer “voice dialing,” so that customers could speak a name rather than dial a telephone number, Bell Atlantic again had to turn to AT&T, which charged $10 million for the software. In both of these cases, Bell Atlantic believed that it could have obtained the software on better terms had it been able to shop around for the necessary improvements.
From AT&T’s position, its installed base of 5ESS switches was an extremely valuable asset, expected to generate a nice stream of revenues. According to Bell Atlantic, AT&T’s aftermarket software upgrades account for between 30 percent and 40 percent of its switch-related revenues. Annual upgrades to the operating system from Bell Atlantic alone (one of a number of large switch buyers) were around $100 million per year. In addition, AT&T stood to make lucrative sales of peripheral equipment to Bell Atlantic. AT&T had incentives to provide improvements and upgrades to the switches and the ability to charge dearly for them. AT&T also stood to gain, at least in the short run, by using its control over proprietary interfaces to prevent others from offering compatible equipment that might compete with AT&T’s own offerings.
Bell Atlantic was none too happy about AT&T’s strong position in the aftermarket for upgrades and plug-ins to AT&T 5ESS switches. In fact, in 1995, Bell Atlantic sued AT&T for monopolization.
Why did Bell Atlantic put up with all this? Because Bell Atlantic would bear substantial costs if it tried to replace the AT&T switches with those of another switch supplier. These switches have a useful lifetime of fifteen years or more, and they are costly to remove and reinstall. Furthermore, the switches Bell Atlantic had paid for and used were worth much less on the used market than they were new, in part because any buyer would also have to deal with AT&T for enhancements and upgrades.
This is a fine example of lock-in. Once Bell Atlantic purchased and installed the AT&T switches, it was locked in to AT&T—that is, dependent on AT&T to use the switches effectively. To put this differently, Bell Atlantic would bear significant switching costs in replacing the AT&T gear with another brand of equipment.
Computer Associates
Another nice example of lock-in is illustrated by the plight of companies that have massive databases on large IBM mainframe computers running highly specialized software. These companies are heavily locked into these computers and their operating systems, making the business of supplying the necessary software quite lucrative, especially for software supplied by only a small number of vendors.
A major beneficiary of this particular lock-in to IBM mainframe computers is Computer Associates. Computer Associates is the leading supplier of a variety of systems management software that works with IBM’s MVS (Multiple Virtual Storage) and VSE/ESA (Virtual Storage Extended/Enterprise Systems Architecture) operating systems. Computer Associates’ products include tape management software, disk management software, job scheduling software, and security software for the VSE operating environment, and tape management software and job scheduling software for the MVS operating environment.
Computer Associates earned $3.5 billion in revenues in its fiscal year ending March 1996, making it the third largest independent software company, behind Microsoft and Oracle. Computer Associates enjoyed revenues of $432,000 per employee, versus Microsoft’s $422,000 and Oracle’s $180,000.
Lock-in occurs in this market on two separate levels: the system level and the vendor level. Customers are certainly loathe to switch computers or operating systems; they are locked into an IBM system. But they are also wary of switching vendors for their systems management software; they are locked into their software suppliers, too. Since this software is mission critical, the risks in using a new vendor, especially an unproven one, are substantial. Switching costs for customers include the risk of a substantial disruption in operations. And for critical pieces of information technology, the danger of disruption can dwarf out-of-pocket switching costs. The fact that Computer Associates software is known to work allows it to command a hefty premium for its software.
Of course, a customer strongly locked into an IBM VSE or MVS operating system is not as firmly locked into Computer Associates for its systems management software. Much of this software is available from alternative sources. However, in 1995 Computer Associates moved to reduce those choices and gain greater control of these customers by acquiring Legent Corporation, the second largest independent supplier of software for IBM-compatible mainframe computer systems, for $1.8 billion. Recognizing that this acquisition would restrict the choices of these locked-in consumers, the U.S. Department of Justice required Computer Associates to spin off certain software products as a condition of completing the acquisition of Legent.
In this situation, locked-in customers were partially protected from exploitation by the oversight of the Justice Department’s Antitrust Division. You can ill afford to be passive if you seek this protection, however. If a proposed merger or acquisition narrows your choices materially, you can improve your chances of blocking the deal, or extracting concessions from the merging parties, by alerting the Federal Trade Commission (FTC) and the Justice Department of your concerns. These agencies have strong powers to prevent deals that are adverse to the interests of consumers. But beware: to really help yourself, you must be ready to testify to your own vulnerability in open court.
Mass Market Lock-In
Our examples so far have involved huge switching costs, like those to Bell Atlantic of replacing switches worth billions of dollars. Do not be misled: even when switching costs appear low, they can be critical for strategy. A million customers, each of whom has switching costs of $100, are just as valuable, collectively, as a single customer whose switching costs are $100 million. The point is that you must compare any switching costs to revenues on a per-customer basis and add up these costs across your entire installed base to value that base. These principles apply equally to customers who are businesses or households.
To illustrate how “small” switching costs can have a profound impact on strategies and market outcomes, one need only follow the current contentious debate in telecommunications regarding “number portability,” namely, your ability to keep your local telephone number when (and if) you choose a new local telephone company. The issue: do you have the right to keep your telephone number when you select MCI as your local carrier, or does your local Bell company have the right to hang onto your phone number, forcing you to change numbers if you want to use MCI? AT&T, MCI, and Sprint are pushing for number portability; the local Bell companies are dragging their feet. Everyone recognizes that number portability is critical if local telephone competition is to become a reality. The cost per person of changing phone numbers may not be huge, but when you add up these costs across millions of telephone subscribers, the stakes grow large.
Regulatory obligations are forcing the incumbent local telephone companies to offer number portability as soon as possible. Debate is currently raging over whether these local monopolists are in fact complying with those duties by offering “interim number portability,” which typically involves remote call forwarding. Would-be competitive local exchange carriers are pushing hard for incumbent carriers to develop “true” number portability. This is reminiscent of the debate over “equal access” long-distance dialing in the mid-1980s. Back then, MCI and Sprint were handicapped in the long-distance telephone market when customers had to dial extra digits to use their services. The lesson is that small consumer switching costs can constitute large barriers to entry, especially for mass-market products.
The market for on-line services provides another example of how “small” switching costs can have a large market impact. Changing from America Online to another Internet service provider (ISP) requires changing one’s e-mail address. In comparison with buying a new mainframe computer, it is cheap to switch e-mail addresses. However, in comparison with the monthly fees for on-line services, the cost of changing e-mail addresses is not negligible. Furthermore, the incumbent Internet service provider may raise these switching costs by refusing to forward mail sent to an old address. For example, e-mail sent to AOL users who have discontinued their service is bounced back to the sender.
One Internet business that has exploited this e-mail address lock-in is Hotmail. Hotmail offers free e-mail service via a Web browser that can be used from any Internet service provider. So how does Hotmail make money? Hotmail places ads on the border surrounding the e-mail workspace. Hotmail also asks each new user to fill out a form indicating his or her interests, and the ads are then targeted to each user’s special interests. This is an example of the kind of personalized advertising we discussed earlier in the book. Hotmail’s 9.5 million subscribers made its Web site the fourteenth most visited site on the Web and caught the attention of both Microsoft and Netscape. Microsoft recently acquired Hotmail for an estimated $300 million–$400 million: not bad for a company that has yet to turn a profit.
Some professional organizations, such as the Association for Computing Machinery, offer e-mail forwarding as a way to avoid address lock-in. CalTech and other universities offer this service to alumni, which, not incidentally, helps them keep in touch with potential donors.
Address lock-in may be a “small” problem for individual users, but it is a major headache for large organizations. One of the reasons that the recent debates about how to manage Internet domain names have been so heated is the potential lock-in problems. Imagine starting a Web site, building a customer following, and then being told that your Web address was being taken away from you by the central authority, or that your annual fees for using “your” Web address were being raised sharply. Fears such as these have prompted intense interest in the management of the Domain Name System and other aspects of Internet governance.
A final example of why small lock-in matters involves user behavior on the Web. Several user studies have documented that people don’t read Web content the way they read paper content. Web readers are very fickle; if you lose their interest, you quickly lose their presence. Web years move seven times as rapidly as ordinary years, but Web attention spans are seven times shorter as well.
Part of the explanation for this behavior is ergonomic—it’s just unpleasant reading text on a computer monitor. But part of the explanation is switching costs. When you pick up a magazine or a book and sit in your favorite chair, you have to exert effort, however small, to switch to a different magazine or book. When you are looking at one Web page, other pages are just a mouseclick away.
This means that writing for the Web is different from writing for paper. You have to get your message across quickly and concisely. Requiring readers to change the screen, by either scrolling or clicking, gives them a good excuse to go to a different site. A Web surfer in motion tends to stay in motion—and a Web reader standing still has probably just gone for a snack.
Switching Costs Are Ubiquitous
Switching costs are the norm, not the exception, in the information economy. As you consider your own business, we suspect that you, too, will recognize lock-in and switching costs as factors that you must deal with on a regular basis. Perhaps your customers will become locked into your products and services; certainly you are susceptible to lock-in yourself in your own use of information systems.
You compete at your own peril if you do not recognize lock-in, protect yourself from its adverse effects, and use it to your advantage when possible. In many markets involving the storage, manipulation, or transmission of information, hard-core, tangible lock-in is substantial, and fortunes can be made or lost by anticipating or neglecting its role. If you are a supplier seeking new customers, you have to overcome customer inertia and lock-in to rivals. If you are a locked-in customer, you may find yourself in a weak bargaining position that could have been avoided by negotiating protections for yourself at the outset. Alternatively, you might seek an initial “sweetener” to compensate you for anticipated lock-in, if you can see it coming.
This chapter will help you learn to recognize switching costs and lock-in and to assess their significance. Remember, lock-in is a two-edged sword; you may loathe it as a customer yet embrace it as a supplier. Either way, you must understand switching costs and be able to anticipate and measure them. In the next chapter, we’ll see how to craft strategy based on that understanding.
VALUING AN INSTALLED BASE OF CUSTOMERS
To understand lock-in and deal with it effectively, the first step is to recognize what constitutes true switching costs. Switching costs measure the extent of a customer’s lock-in to a given supplier. When America Online (AOL) decides how aggressively to seek new customers, and how to price to its existing customers, it must be able to measure customers’ switching costs. Put differently, AOL must value what is perhaps its most important asset, namely, its installed base of customers. Like credit-card companies, long-distance telephone companies, and cable-television companies, Internet service providers need to estimate their revenue stream from a new customer to figure out how much to spend to acquire that customer. A similar exercise is necessary when buying customers wholesale, as when banks buy credit-card portfolios or when IBM acquired Lotus. This is harder than you might think.
We’ve emphasized the customer’s switching costs so far, but the supplier also bears some costs when it acquires a new customer. These may be small, such as creating a new entry in a database, or they may be quite large, such as assembling a team of support personnel. Both the customer’s and the supplier’s costs are important. Adding them up gives the total switching costs associated with a single customer; these costs are the key to valuing an installed base.
The total cost associated with Customer C switching from Supplier A to Supplier B is the cost that must be borne collectively by Customer C and by Supplier B to place the customer in a position with Supplier B that is comparable to the one that Customer C currently has with Supplier A.
Look at how this concept plays out in the long-distance telephone business. When you switch your long-distance service from AT&T to MCI, the total switching costs include your time and trouble in making the move, plus the marketing and setup costs incurred by MCI. There’s not a lot that MCI can do to reduce these costs. If MCI offers you $25 to change carriers, this tactic has no impact on total switching costs: the switching costs borne by you fall by $25, and those borne by MCI rise by $25. What if MCI offers you 100 free minutes of calling as a sweetener? If you value these minutes at 15 cents per minute, or $15 in total, they reduce your switching costs by $15. If the cost to MCI of offering these minutes is 5 cents per minute (for access charges, say), or $5 in total, the costs borne by MCI rise by only $5. The free-minutes offer has reduced total switching costs by $10. Whenever the seller enjoys a nice margin (price minus marginal cost) on its products or services, there is scope for in-kind sweeteners of this sort to lower total switching costs.
You might find it odd to look at extra costs borne not just by the customer but also by the new supplier, but this is essential for a sound analysis of whether it is worthwhile to acquire a new customer. Whether you or MCI spends the time or bears the cost of shifting your longdistance account from AT&T does not alter the fact that the time and money spent is a cost of switching brands. Indeed, very often new suppliers will help subsidize customers who are switching brands; for example, the Apollo computerized reservation system compensated travel agents for payments owed by the travel agent to the rival Sabre system if the agent stopped using Sabre. Nowadays, long-distance telephone companies are offering signing bonuses in the form of free minutes to attract customers from rival carriers.
How much should you spend to attract a new customer? The answer depends on the costs that you and your new customer both bear. Suppose, for example, that you are an ISP trying to build your customer base. Imagine that switching Internet providers involves $50 worth of hassle for the customer, and it costs you $25 to set up a new account, so the total switching costs are $75. You should encourage a customer to switch only if you expect the discounted flow of profit from this customer to be greater than $75. If you anticipate a discounted flow of profit of $100, you can afford to offer the consumer a couple of free months of service (valued at $25 per month) to overcome the $50 switching costs, pay the $25 account setup costs, and still be left with $25 of profit. Alternatively, you could invest $50 in advertising (rather than the free months) to convince the customer that switching to your service from his or her current ISP is worth the hassle. But if you anticipate a present value of only $70 of profit from the new customer, it just isn’t worth trying to attract him, since the total switching costs of $75 exceed the benefits of $70.
In many cases, the disruption in service associated with changing suppliers is a major consideration, as we saw in the Computer Associates case. For mission-critical information and communications, these disruption costs can make up the bulk of the switching costs. Worse yet for customers, these costs are potentially subject to strategic manipulation by the vendor. For example, would-be competitors in local telephone service are finding in trials that customers tend to lose telephone service for a period of time when switching service to them from the incumbent local exchange carriers. Needless to say, this disruption is a huge barrier to switching local telephone companies, especially for business customers, and the subject of repeated complaints to regulators.
Measuring customer switching costs is a big piece of valuing an installed base of customers. As a rule of thumb, the profits a supplier can expect to earn from a customer are equal to the total switching costs, as just defined, plus the value of other competitive advantages the supplier enjoys by virtue of having a superior product or lower costs than its rivals. Customer perceptions are paramount: a brand premium based on superior reputation or advertising is just as valuable as an equal premium based on truly superior quality. As a general principle, if your rivals have cost and quality similar to yours, so that your market is highly competitive, the profits that you can earn from a customer—on a going-forward, present-value basis—exactly equal the total switching costs. Life is more complicated if you cannot easily measure these switching costs, especially if customers differ widely in their switching costs, but the same principle still applies.
To illustrate this principle, consider the value of your patronage to your local telephone company. Under current FCC rules, local phone companies are required to make their facilities available at cost to would-be competitors seeking to provide basic telephone service. Under these conditions, the local phone company can expect to earn a profit on basic service only if it can command a premium based on its brand name, or if consumers bear switching costs in using other carriers. Take a customer for whom the hassle of switching phone numbers has a monetary cost of $100. Our valuation principle says that the incumbent telephone company can earn precisely $100 in extra profits from this customer, in present-value terms. This might come in the form of a $1 per month premium over the rates charged by competitors (since $1 per month in perpetuity has a present value of roughly $100 at conventional interest rates).
The day the regulators mandate full number portability, and ensure that switching phone companies is easy and involves no disruption in service, consumer switching costs will tumble close to zero—essentially, to the transaction costs of changing carriers. When that day comes, the value of the incumbent phone company’s installed base will decline. The prospect of that day arriving reduces the per-customer value of the incumbent carrier’s installed base from a perpetuity to a shorter and shorter annuity. You can see why incumbent carriers are resisting the move to full number portability. Likewise, entrants are fighting hard to force the Bell companies to reconfigure their operational support systems to enable customers to switch smoothly to their services. Once full number portability is in place, the Bell companies will lose one (of several) advantages that they currently enjoy based on their incumbency position in local telephone markets. Anticipating the arrival of competition, local companies are seeking to enter long-distance markets, to become ISPs, and generally to bolster their customer relationships and customer loyalty to withstand the eventual reduction in customer switching costs.
This same valuation principle applies when switching costs are based on the ownership of durable capital equipment or long-term contractual commitments. For example, Ticketmaster enters into multi-year contracts to provide stadiums and other venues with ticketing services. A would-be competitor of Ticketmaster (there are a few, encouraged by Pearl Jam’s very public dispute with Ticketmaster) must either wait for these contracts to expire (by which time the contract-based switching costs will be absent) or buy the venue out of its contract. If the venue purchases a ticketing system dedicated to Ticketmaster, trains its employees to use the Ticketmaster system, or publicizes that its customers can obtain tickets at Ticketmaster outlets, the switching costs will outlive the contract, however. As we’ll see, one of the distinctive features of information-based lock-in is that it tends to be so durable: equipment wears out, reducing switching costs, but specialized databases live on and grow, enhancing lock-in over time.
Our valuation principle can be used for several purposes:
- First, by anticipating the value of tomorrow’s installed base of customers, you can determine how much to invest today—in the form of price discounting, advertising, or R&D, for example—to attract more customers and build that installed base.
- Second, you can use these methods to evaluate a target company whose installed-base of customers constitutes a major asset. Rather than figure out the revenue and cost streams associated with the target company’s customers, you may be able to take a shortcut and calculate these customers’ switching costs.
- Third, valuation information will help inform decisions affecting your customers’ switching costs—for example, your product design and compatibility decisions.
CLASSIFICATION OF LOCK-IN
So far we’ve said the following about lock-in:
- Customer lock-in is the norm in the information economy, because information is stored, manipulated, and communicated using a “system” consisting of multiple pieces of hardware and software and because specialized training is required to use specific systems.
- Switching costs must be evaluated relative to revenues on a per-customer basis. Even “small” switching costs can be critical in mass markets such as the telephone industry or consumer electronics.
- Total switching costs include those borne by the consumer to switch suppliers and those borne by the new supplier to serve the new consumer.
- As a rule of thumb, the present discounted value to a supplier of a locked-in customer is equal to that customer’s total switching costs, plus the value of all other advantages enjoyed by the incumbent supplier based on lower costs or superior product quality, real or perceived.
We are now ready to look more closely at the underlying sources of switching costs, with an eye to their strategic implications. There are a handful of types of switching costs that arise in one industry after another. Table 5.1 summarizes our classification of lock-in. Knowing these patterns will help you identify and anticipate lock-in, estimate your switching costs or those of your customers, and plan accordingly. We will examine each entry of the table in detail.
Contractual Commitments
Our first category of lock-in is the most explicit: a contractual commitment to buy from a specific supplier. Common sense dictates that you should not commit yourself to a single supplier unless the price is specified. Nonetheless, many contracts give the seller the discretion to make annual adjustments in rates, subject to certain limits, or even to charge so-called “reasonable” rates. Beware of these vague protections when you are buying. Even with ironclad price protection, there is inevitably some room for the vendor to control nonprice variables, such as the quality of service provided. Buyers are well advised to consider such “noncontractible” aspects of the product or service in advance. Indeed, price commitments sought by customers from vendors can be positively harmful if they merely induce the vendor to exploit lock-in by reducing quality and other nonprice dimensions of service.
Table 5.1. Types of Lock-In and Associated Switching Costs
| Type of Lock-In | Switching Costs |
| Contractual commitments | Compensatory or liquidated damages |
| Durable purchases | Replacement of equipment; tends to decline as the durable ages |
| Brand-specific training | Learning a new system, both direct costs and lost productivity; tends to rise over time |
| Information and databases | Converting data to new format; tends to rise over time as collection grows |
| Specialized suppliers | Funding of new supplier; may rise over time if capabilities are hard to find/maintain |
| Search costs | Combined buyer and seller search costs; includes learning about quality of alternatives |
| Loyalty programs | Any lost benefits from incumbent supplier, plus possible need to rebuild cumulative use |
The extent of lock-in depends on the nature of the contract. One contractual form, a requirements contract, commits the buyer to purchase all of its requirements exclusively from a specific seller for an extended period of time. In another form, a minimum order-size commitment, the buyer promises to make a certain quantity of purchases, potentially leaving open the option of turning elsewhere for additional supplies as needed if the original vendor is not performing well.
With explicit contractual commitments, the damages for breach of the contract can loom large and may constitute the bulk of the switching costs. Of course, a new supplier may be willing to buy you out of your current contract (probably to lock you in anew). Alternatively, you can compensate your existing supplier under your contract and still come out ahead if your new supplier offers a sufficient discount. If the liquidated damages in your existing contract are large enough, you really will be locked in. Also, be careful about evergreen contracts, which automatically renew sixty or ninety days before the initial ending date.
When negotiating such contracts, think beyond the terms, conditions, and duration of the contract itself. Anticipate your switching costs and options after the contract terminates. For example, if you purchase a specialized piece of equipment with a ten-year lifetime, and if you arrange for a three-year service contract at the time of purchase, consider what your service options will be for the remaining seven years after the initial contract expires. If you enter into a five-year contract with a vendor to manage your customer databases, think carefully about the switching costs you will face in five years time if you seek to change vendors. Design the contract to minimize those costs, perhaps by reserving for yourself nonexclusive rights to some of the computer code developed to manage or exploit your data.
Durable Purchases
In looking at Bell Atlantic and Computer Associates, we examined examples of lock-in involving the purchase of expensive, durable equipment (telephone switches and mainframe computers and operating systems, respectively) at one point in time, followed by purchases of complementary products at a later time (transmission equipment or voice messaging equipment, and systems management software, respectively). This is one of the most common and important patterns of lock-in: after the initial purchase is made, the customer must buy follow-on products that work with the durable equipment. As a result, many suppliers of durable equipment—be it medical equipment sold by Siemens to hospitals, large copiers sold by Xerox to corporations, or Zip drives sold by Iomega to individuals and businesses—derive the bulk of their profits, if not their revenues, from “aftermarket” sales.
In these situations, the economic lifetime of the durable equipment is critical. If the equipment quickly depreciates in economic value, perhaps because of rapid technological progress, then expenditures on that equipment do not lock customers in for very long, or very strongly. If there is a market for used equipment, so the customer can recover some of the initial outlay for the equipment upon replacing it, switching costs are again reduced. Indeed, rival vendors seeking to make their own new-equipment sales often reduce customers’ switching costs by accepting used equipment for trade-in at above-market prices. Active used-equipment markets facilitate this tactic.
With durable hardware, switching costs tend to fall over time as the hardware depreciates. Thus, lock-in tends to be self-limiting. The switching costs, which here are the cost of replacing the existing hardware with equally capable hardware (or the cost of replacing the existing hardware with superior, state-of-the-art hardware, less the extra benefits of that hardware) fall as the user’s machine ages. Rapid technological advance reduces hardware lock-in.
There is an exception to the principle that hardware lock-in declines with time: when a customer has multiple pieces of similar equipment and enjoys efficiencies from having all or most of its equipment come from the same vendor. In this case, even when one machine is fully depreciated, the customer still bears large switching costs because of the other complementary equipment. The customer is least attached to the incumbent supplier when most of its equipment is nearing the end of its useful lifetime. The supplier is most vulnerable to being replaced at just such a point of minimal lock-in, just as the weakest link governs the strength of a chain. Recognizing this, the supplier may aim for its customers to have staggered equipment vintages or may offer inducements to replace older equipment before the end of its lifetime to maximize the minimal lock-in.
One effective way for customers to reduce or eliminate switching costs based on durable equipment is to rent or lease the equipment rather than buying it. By pushing more transactions into the “foremarket” and out of the “aftermarket,” the buyer takes advantage of the flexibility to be enjoyed prior to becoming locked-in. For example, if you contract for complements such as repair parts and maintenance service when you initially rent or lease a copier, you need not worry that service prices will rise during the lifetime of the lease. Extended warranties serve the same function. In contrast, if you buy the copier, even with an initial service contract, you may still be subject to a steep price increase to renew when the original service contract expires.
Another key issue with this type of lock-in is the extent of choice available to the locked-in consumer: technology lock-in is not the same as vendor lock-in. Customer lock-in is far less important if there remain many alternative suppliers of the complementary products purchased later. Bell Atlantic is not reliant on AT&T if there are alternative suppliers of transmission equipment (or other software and hardware) that attaches to the AT&T switch. In other words, the aftermarket choices are an important part of understanding the entire pattern of equipment purchase and lock-in, an observation that will be important in our discussion of interfaces and compatibility in Chapter 7.
The fact is, most durable equipment requires follow-on purchases, making this pattern of lock-in extremely common. Obviously, a great deal of equipment is durable. Beyond that, however, there are all manner of complementary products that customers need in the future. Upgrades and product improvements are common, both for durable equipment and for other durable investments including computer software. Very often only the original vendor offers these upgrades, perhaps owing to patent or copyright protection that the vendor enjoys. Aftermarket service and spare parts are a necessity for most equipment, and they may also be supplied exclusively or largely by the equipment manufacturer. Notable examples include computer hardware, high-speed printers and copiers, telecommunications equipment, aircraft, weapons systems, and medical equipment. In fact, aftermarket policies constitute a key strategic choice for manufacturers of high-tech, durable equipment.
The limits of these strategies are now being tested in the courts. Indeed, a whole cottage industry has sprung up in which customers are suing manufacturers under the antitrust laws via class actions, alleging that the manufacturers have impeded their ability to obtain aftermarket service from independent service organizations (ISOs). These ISOs also are suing manufacturers directly, emboldened by a key 1992 Supreme Court decision (Image Technical Services v. Eastman Kodak) ruling that manufacturers may be found to have monopoly power in their own brand-specific aftermarkets and are not immune from antitrust challenges by competition with other equipment manufacturers.
Brand-Specific Training
A pattern of lock-in similar to that associated with the purchase of durable products results when personnel are trained to use them. This training is often brand-specific, in that considerable additional time and effort would be required to learn to work with a new brand of product with equal proficiency. In this case, the complementary products are the durable product itself and the training that is specific to it. General training (as opposed to brand-specific training) does not give rise to lock-in. As we will discuss in Chapter 8 in regard to strategic standard setting, a key question for buyers and sellers is whether training can be effectively transferred to other brands of software, perhaps through the use of standardized user interfaces or protocols.
With brand-specific training, switching costs tend to rise with time, as personnel become more and more familiar with the existing system. The opposite is true for durable hardware, which becomes less costly to replace as it ages and as new models with superior performance are introduced.
The obvious example for many of us is computer software. We all know how time consuming it can be to learn to use a new piece of software, much less to become adept at it. And the training costs associated with replicating one’s proficiency with a familiar piece of software tend to grow the more experience one has with the familiar program. Moreover, the software vendor can maintain high switching costs by introducing a series of upgrades that offer enhanced capabilities in return for the investment of additional time learning the new features.
Of course, a new brand can emerge that is easy to learn, thus reducing switching costs. Indeed, one strategy for breaking into a market with significant brand-specific customer training is to imitate existing brands or otherwise develop a product that is easy to learn. Borland tried this with Quattro Pro, aimed at Lotus 1-2-3 users, and Microsoft Word has built-in, specially designed help for (former!) WordPerfect users.
With brand-specific training, lock-in can easily outlive an individual piece of equipment. This is most evident when customers desire to standardize all of their equipment by using a single vendor. For example, commercial airlines now place great value on “fleet commonality”— that is, on having most if not all of the aircraft in their fleet come from a single airframe manufacturer, and even with a similar cockpit configuration. Airlines have found that a uniform fleet can result in substantial savings on maintenance and training costs and can improve flight safety. This is one of the reasons why American, Delta, and Continental recently agreed to buy all of their new aircraft from Boeing over the next twenty years. Indeed, the demand for fleet commonality hastened the demise of McDonnell-Douglas: lacking a full family of aircraft, and lacking loyal customers with an all-Douglas fleet, McDonnell-Douglas threw in the towel in 1996, concluding that it could no longer survive in the commercial aircraft industry, and agreed to be acquired by Boeing.
Information and Databases
In our third type of switching cost, the complementary products giving rise to lock-in are the hardware and software used to store and manage information, on the one hand, and the information or database itself, on the other. Users with massive information encoded in a specialized format are vulnerable if and when they require new hardware or improved software to work with the data. In these situations, a key question is whether the information can easily be ported over to another system. You must ask yourself what are the costs of transferring the information and what aspects of the information would be lost in a transfer.
Many of the examples in this book fit into this category. For example, consumers purchase a CD player and then build up a library of CDs. When the CD player starts skipping (a seemingly inevitable event), or when new and better audio technologies appear on the scene, the consumer is locked into the CD format. In this case, the information cannot be transferred, making it important for anyone selling equipment that reads new formats, such as DVD, to make that equipment back-ward-compatible—that is, capable of reading CDs as well. Videotape players, laser disks, DVDs, and phonographs in an earlier day all conform to this pattern of hardware/software switching costs.
Computer software programs and data files are another critical category of format-specific information. In these cases, like the library of CDs, the library of information grows over time, causing lock-in to grow stronger with time. Any system in which information is collected over time in special formats raises these issues. Tax preparation software that incorporates tax information from prior years, accountant software that relies on historical data, and graphics software that uses designs developed over time are all examples of this type of lock-in. For years, Ashton-Tate’s dBase language was enormously valuable because so many users had written programs in the dBase language. It’s typically far easier to transfer raw data from one format to another than to port over code. In all of these cases, vendors’ strategies revolve around methods designed to raise or lower consumers’ switching costs and capitalize on the crucial distinction between proprietary and standardized formats.
With information and databases, switching costs tend to rise with time as more and more information comes to reside in the historical database. One way for users to limit these switching costs is to insist on employing standardized formats and interfaces, if possible, or to insist that the vendor publish its interface specifications so as to permit competition from fully or largely compatible products. We discuss such “open” interfaces further in Chapter 8.
Specialized Suppliers
Another important pattern arises when buyers purchase specialized equipment gradually over time. As a buyer, remember that your choices today will dictate your needs tomorrow. By picking a single supplier of that equipment, you will become dependent on that source in the future. Your initial purchases of the equipment are complementary to later purchases because of the advantages of sticking with a single brand for all of your purchases.
Worse yet from the customer’s point of view, comparable alternative suppliers may no longer exist after the initial bid is awarded to a single winner. Remember, with specialized equipment, the switching costs depend on the ability of new suppliers to offer comparable equipment when needed in the future. If the durable equipment or software is highly specialized, it will be relatively difficult to find alternative suppliers in the future, giving the incumbent vendor the advantage of substantial lock-in for the next round of purchases.
More and more companies in the information economy are facing lock-in to specialized suppliers. Yet this pattern is hardly unique to information industries. In fact, a large sector of our economy has been dealing with this problem for decades at least: the defense sector. The Department of Defense takes flack now and again for its procurement practices, but we believe that today’s information sector can learn much from the Pentagon’s methods of dealing with specialized suppliers, especially in the 1990s, during which time the defense contractor base has been sharply downsized.
Very often the Pentagon finds that the losers in the bidding to produce a complex weapons system cannot maintain the necessary specialized capabilities without ongoing business. Furthermore, the winner surely gains from its experience and comes to know the customer’s needs better as part of fulfilling its contract. This problem plagues all buyers of state-of-the-art technology: now that NASA has picked Lockheed Martin’s “Venturestar” design for its next-generation, single-stage-to-orbit space shuttle, it won’t be easy for NASA to turn to others in the future should Lockheed’s performance prove lacking. To a lesser extent, relationships between advertising firms, accounting firms, and law firms and their corporate clients also exhibit lock-in to specialized suppliers.
The upshot is that large buyers with specialized needs commonly find their options limited after they initially pick a supplier to serve them. The Pentagon often handles this by carefully structuring the competition for a single, huge, long-term procurement contract. For example, in 1996 the Pentagon “down-selected” from three to two the number of possible suppliers for the Joint Strike Fighter, funding additional development by Boeing and Lockheed Martin but dropping McDonnell Douglas. Over the next five years, Lockheed Martin and Boeing will develop prototypes for this new combat aircraft, with funding of some $2.2 billion by the Department of Defense. Then, around 2002, the Pentagon will pick a single supplier after a fly-off between the competing prototypes. The winner stands to earn revenues of some $200 billion over the lifetime of the Joint Strike Fighter program.
If the Pentagon could fully anticipate its needs and obtain contractual commitments from the winner as part of the process of selecting the ultimate winner, lock-in would not be an issue. But the world is not so simple. Even if the Pentagon obtains the option to buy a large number of planes at a specified cost, there will inevitably be issues down the line—such as the cost of making improvements to the plane in 2006 that were not envisioned in 2002—in which the winner will have some bargaining leverage by virtue of the Pentagon’s lock-in. True, the Pentagon is a powerful buyer, with strong auditing rights to monitor costs and limit payments, and the contractor has a strong incentive not to be seen as exploiting its position as the sole supplier so as not to lose future competitions. Nevertheless, a significant degree of lock-in is inevitable.
We discuss procurement strategies below, but note here two important ones from the Pentagon’s perspective: (1) get a variety of commitments and options as part of selecting the winner for a big contract and/or (2) keep alive an alternative source of supply, a strategy commonly known as dual sourcing. For example, in 1997 the Air Force decided to fund development of new low-cost rockets known as Evolved Expendable Launch Vehicles by both Lockheed Martin and Boeing rather than choosing just one of the companies. The Pentagon realized that two companies could be supported in part because of the growing commercial demand for rockets. Even when true dual sourcing is not possible because of specialized needs and large fixed costs, a large buyer can make efforts to nurture capabilities at more than one supplier to spur future rivalry. The Pentagon does this by providing its contractors with funds to maintain their capabilities to develop new designs and to bid on the next major contract.
Many high-tech firms are familiar with dual sourcing from the now-famous story of IBM and Intel. IBM attempted to keep its options open via dual sourcing when it selected a supplier of the microprocessors for its personal computers back in the early 1980s. In choosing Intel, IBM insisted on having a second source as an alternative to Intel. This created an opening for Advanced Micro Designs (AMD). To us, the Intel story illustrates the limitations of dual sourcing from the buyer’s (IBM’s) point of view: disagreements between Intel and AMD over the scope and duration of AMD’s rights under its dual-sourcing agreement led to protracted litigation between Intel and AMD, and Intel has captured a commanding share of the market during the 1990s. The lesson: dual sourcing is most likely to be successful in the long run with two strong sources rather than one strong and one weak source. In rapidly moving markets, the buyer is best protected if each source has the independent ability to develop and improve its own technology over time.
Dual sourcing is clearly in the interest of purchasers who want to keep their options open. Less obvious is the fact that dual sourcing can also be in the interest of suppliers. If you are trying to get your technology established, the comfort of two or more sources can help convince potential customers to put their trust in you. We’ll discuss this tactic further in Chapter 8 when we examine the logic of open systems and standards.
Search Costs
Our next category includes switching costs that are more mundane, but not to be ignored, especially in mass markets: the search costs incurred by buyers and sellers to find each other and establish a business relationship. These costs may seem small, but ask yourself how often you shop around for a new travel agent, insurance agent, or bank. Do you really know you are getting the best deal possible? Will your search behavior or loyalty change as more vendors become available on-line?
As we stressed above in defining switching costs, what matters in evaluating the extent of lock-in caused by search costs are the “two-sided” search costs, as borne by both customers and would-be suppliers. Search costs borne by consumers when switching brands include the psychological costs of changing ingrained habits, the time and effort involved in identifying a new supplier, and the risks associated with picking an unknown supplier. Search costs borne by would-be suppliers in reaching and acquiring new customers include promotional costs, the costs of actually closing the deal, the cost of setting up a new account, and the risks involved in dealing with an unknown customer, such as credit risk.
The credit card industry displays many of these search costs: customers tend not to move their credit card balances from one bank to another, and card-issuing banks spend considerable amounts on direct mail and other promotional activities in search of new customers. Likewise, banks find it costly to attract new accounts because of the danger of adverse selection—that is, ending up with customers who will ultimately default on their balances or, oddly enough, customers who will not incur finance charges at all and thus who are less profitable to the bank. Banks recoup these expenses in the form of high interest rates on consumer credit. Indeed, a bank portfolio with $100 million in credit card receivables would typically be worth around $120 million when sold to another issuer or when securitized. This is one nice example in which the market explicitly values a bank’s installed base of “loyal” credit card customers.
Search costs depend on the time and expense involved in locating an attractive new supplier and the costs incurred by vendors in locating customers. If you are a customer who tends to be loyal, switching vendors only rarely, this can work to your advantage: if you can communicate this to potential suppliers, they will value your account all the more if your “churn” rate is likely to be low.
In the information economy, various search costs are likely to be reduced. This claim of the proponents of the “friction-free economy” is certainly correct. Distribution on the Internet is going to be far cheaper than it has ever been in the past, both for information products and for traditional items. Based on our principles for valuing an installed base of customers, reductions in search costs can represent a grave threat to the value of established mass-market companies lacking truly superior products. Advances in distribution will have an especially important effect on consumers who are currently the most costly to reach.
Even if search costs fall, however, there will always be some degree of pure consumer inertia and loyalty to incumbent vendors. This inertia and loyalty are due in part to our human limitations: no matter how inexpensive it becomes for suppliers to send messages to prospective customers, it will remain costly for customers (even with the help of their computer agents) to review and evaluate these proposals. So, even if banks can broadcast messages to prospective customers via the Internet, saving on direct mail costs, consumers will still need to take the time to sort through the proposals and run the risk of rejection, or loss of privacy, if they apply for a new credit card.
Loyalty Programs
Our next category of lock-in might be called “artificial lock-in” because it is entirely a construct of firms’ strategies. We are referring to the increasingly popular programs in which customers are rewarded for their repeat purchases. These loyalty programs involve explicit inducements to customers to buy largely or exclusively from a single vendor.
The most popular and well-known of these are the airlines’ frequent flier programs. Recently, hotels have followed suit with frequent guest programs. Even local retailers use this tactic, giving one unit for free after ten purchases. For example, our local film store will develop one roll of film for free after you have paid for ten rolls. The nearby Mexican restaurant does the same with burritos, if you remember to bring along your card and have it punched.
Loyalty programs create switching costs in two ways. First, you may forfeit certain credits if you stop buying from your regular supplier. If you have 15,000 miles in your airline account, and it takes 25,000 miles to get a free ticket, the 15,000 miles will be lost if you fail to fly another 10,000 miles before they expire. These switching costs can be minimized by changing carriers after cashing in the bulk of your credits. Second, and more important, are benefits based on cumulative usage, such as double miles or preferential service for members who fly more than 50,000 miles a year. These benefits become part of the total switching costs: either the customer loses them (a customer switching cost) or the new carrier matches them (a supplier switching cost). As on-line commerce explodes, more and more companies will adopt loyalty programs giving preferential treatment to customers based on their historical purchases precisely to create such switching costs.
Loyalty programs will become far easier to administer as companies keep more and more information about their customers’ purchasing patterns, as we saw in the discussion of personalized pricing in Chapter 2. Already, many retailers collect detailed information on individual customers’ buying patterns; with these databases at their disposal, these suppliers are well placed to target their promotional efforts based on customers’ historical buying patterns or to offer discounts based on cumulative purchases. We predict an enormous informational tug-of-war: companies will increasingly use customer-specific information both to identify and contact attractive new prospects and to implement loyalty programs to retain existing customers.
In the information economy, the traditional sources of friction such as search costs and distribution costs will be eroded. But the same computational power that reduces these frictions allows for the creation of new “synthetic frictions” such as loyalty programs. Frictions don’t disappear—they just mutate into new forms.
The variations on these discount programs are virtually endless. You can offer your customers a discount for buying exclusively from you or for committing to a certain minimum order size. You can offer discounts for customers who buy more than they did last year. You can utilize volume discounts to encourage customers to keep buying from you rather than sampling other suppliers. Or, to attract new customers, you can offer introductory discounts as a way of helping defray their costs of switching to you from a rival. Perhaps the ultimate weapon here is to base the offer you make to a prospective new customer on information about that customer’s status in your rival’s loyalty program.
We anticipate that more and more businesses will use loyalty programs as customer information becomes more detailed and more widely available. In addition, complementary suppliers will coordinate their programs, much as hotels and airlines now cooperate in their repeat-buyer programs. With on-line trading, the possibilities will explode. And keeping track of historical sales of different products will be a lot easier than licking Green Stamps or having your card punched every time you buy a burrito.
With loyalty-inducing programs, customers can with relative ease calculate the costs they bear when switching vendors, both in terms of lost awards and of reduced marginal returns to additional business. Some vendors will buy credits from their competitors, much like competitive upgrades in the software industry. For example, an airline will often offer “gold status” to someone who holds gold status on a competing airline in hopes of inducing them to switch carriers.
The on-line book store Amazon.com has a very nice twist on a loyalty program. In the “Associates Program,” anyone who recommends a book on his or her Web site can add a link to Amazon that can be used by those who wish to purchase the book through Amazon. In exchange, the site that created the link to Amazon gets a “referral fee” of 5⅛ percent of the purchase price of the book. As of March 1998, there were more than 35,000 Amazon associates.
This base of associates gives Amazon a potent weapon in its battle with Barnes & Noble. Barnes & Noble has struck back with its Affiliates Program, which offers on-line bookstores order processing, payment, and shipping services and up to 7 percent of the revenue from book sales. Amazon responded with a special deal for the top 500 Web sites, giving them a bonus 50 percent larger than the standard payment.
We think Amazon could make an even better response: they should base the royalty rate on cumulative referrals, giving a payoff only after the consumer passes certain milestones. If Amazon structures the rates correctly, their associates will want to stick with only one on-line book provider, who will most likely be Amazon. Just as it is costly to switch to another frequent flyer program, it will be costly for associates to switch to another on-line book service.
SUPPLIERS AND PARTNERS FACE LOCK-IN, TOO
We’ve spoken so far as if buyers are uniquely susceptible to switching costs. Not so. Although we will continue to focus on buyers’ switching costs, suppliers are hardly immune to lock-in. The fact is, anyone who makes investments that are specific to a particular supplier, customer, or partner is subject to lock-in for the economic lifetime of those investments. The key point is that the investments will have to be written down if the customer or partner walks, balks, or simply fails.
In fact, it is not uncommon for suppliers and customers to be locked in to each other at the same time. Such bilateral, or two-sided, lock-in can lead to a certain balance of terror, not to mention some high-stakes negotiations. The classic case was that of a railroad that built a spur line to serve an individual customer, such as a coal mine or a coal-fired power plant. Once the line was built, it had little or no value apart from serving the one customer, so the railroad was locked into that customer. At the same time, the customer would find it very expensive to finance a new spur line, so the customer was locked into the railroad, leading to what economists call a bilateral monopoly. The same relationship exists in the information economy when a software vendor writes a specialized piece of software for an individual client.
Nor is lock-in restricted to customers and suppliers; partners are susceptible as well. For example, Pratt & Whitney, as the manufacturer of certain aircraft engines designed specifically for Douglas aircraft, was long locked into McDonnell Douglas, even though it had no intention of selling the engines directly to McDonnell Douglas.
We see seller lock-in, bilateral lock-in, and partner lock-in frequently in information industries. Software houses that initially specialized in writing software for Apple computers learned all too soon that they needed to retool and thus bear very real switching costs: they had to become adept at writing programs to run on DOS or Windows. Likewise for companies specializing in writing games for Sony’s PlayStation or the Nintendo 64 platform.
The same economic principles that give rise to buyer lock-in also describe seller lock-in and partner lock-in. Even when you’re not the buyer, you need to be alert when making investments that will leave you in a weak bargaining position in the future. If you’re a supplier, you can protect your downside by getting your customer(s) to commit to buying enough from you to cover most, if not all, of your costs. One nice way to do this is to have a large customer defray some or all of the costs of designing a product tailored to that customer, while reserving the rights to make distinct versions of the product for other customers. If you’re a partner, think like a customer: get commitments from your partner on rollout dates, product specs, and prices. There’s no point in developing software for a machine that is late to market or so expensive that few end users buy one.
THE LOCK-IN CYCLE
Lock-in is inherently a dynamic concept, growing out of investments made, and needs realized, at different points in time. Switching costs can grow or shrink with time, but they do not stand still.
We have developed a diagram to help you think dynamically about lock-in. The diagram applies to all of the flavors of lock-in we have just discussed. We call this the lock-in cycle, as shown in Figure 5.1.
The easiest place to hop onto the lock-in cycle is at the brand selection point—that is, when the customer chooses a new brand. Brand choice could mean purchasing a new multimillion dollar switch, buying a videodisk player, purchasing a new software program, or signing up for a new frequent-flier program. The first time a specific customer picks a brand, that customer will have no preference for any one brand based on lock-in. You are not born “locked in”; you only get locked in by virtue of choices you make. The next time around the cycle, the playing field will not be so level, however.
Figure 5.1. The Lock-In Cycle
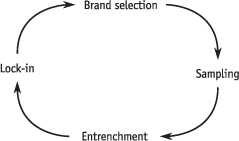
Brand selection is followed by the sampling phase, during which the customer actively uses the new brand and takes advantage of whatever inducements were made to give it a try. One of the dangers of offering powerful sweeteners to attract new customers is that they will take the free sample but never turn into revenue-paying customers. Some book clubs take this risk in offering eight books for a dollar; others require new members to buy a minimum number of books at regular prices. As we discussed in Chapter 2 on pricing, extending introductory offers to new customers is especially tempting for information providers because of the low marginal cost of information. This is all the more so with a CD that costs less than a dollar to produce, in comparison with printed material that could cost five dollars or more to produce.
Customers who do more than sample move into the entrenchment phase. This is when the consumer really gets used to the new brand, develops a preference for that brand over others, and perhaps becomes locked in to that brand by making complementary investments. Usually, the supplier tries to drag out this phase and delay active consideration of other brands, hoping that the customers’ switching costs will go up. The entrenchment phase culminates in lock-in when the switching costs become prohibitively expensive.
We return to the brand selection point when the customer either switches brands or actively considers alternative brands without selecting them. Of course, circumstances will have changed in comparison with their last time around the cycle. Certainly the customer’s switching costs are higher than the first time around. For specialized products, as in our Pentagon examples, some alternative suppliers may have dropped out in the interim or lost capabilities. On the other hand, new technologies can emerge.
The most basic principle in understanding and dealing with lock-in is to anticipate the entire cycle from the beginning. In fact, you need to go beyond any one trip around the circle and anticipate multiple cycles into the future in forming your strategy from the outset. Valuing your installed base is part of looking ahead: by figuring out how much customers will be worth to you in the future (next time around the cycle), you can decide how much to invest in them now (by inducing them to take the next step and enter the sample phase, for example). This is especially true if switching costs are rising over time (as with information storage and brand-specific training) rather than falling over time (as with durable equipment that depreciates and will be replaced by new and superior models).
The next chapter looks more closely at each point in this cycle, both from the perspective of buyers and suppliers, drawing out lessons and suggesting winning strategies.
LESSONS
- Switching costs are the norm in information industries. They can be huge—as when Bell Atlantic invested billions of dollars in telephone switches with a proprietary AT&T operating system—or small—as when consumers must obtain credit approval to get a new credit card. Either way, fortunes can be made or lost based on lock-in and switching costs. You just cannot compete effectively in the information economy unless you know how to identify, measure, and understand switching costs and map strategy accordingly.
- As a customer, failure to understand switching costs will leave you vulnerable to opportunistic behavior by your suppliers. Even if you cannot avoid some lock-in, you may miss out on the up-front sweetener that would help the bitter lock-in pill go down better.
- As a supplier, switching costs are the key to valuing your installed base. You will be unlikely to successfully build an installed base of customers—one of the most potent assets in the information economy—unless you can overcome the initial costs of switching customers from rival firms. To help defray these costs, you must anticipate customers’ lock-in cycle, including the costs your would-be customers will incur if they ever leave you.
- Fortunately, lock-in arises in one industry after another according to certain identifiable patterns. All of these patterns conform to the lock-in cycle, from brand selection point, through the sampling and entrenchment phases, and back to the next brand selection point. To map strategy for one part of the lock-in cycle, you must understand and anticipate the entire cycle.
- The essence of lock-in is that your choices in the future will be limited by your investments today. These linkages differ from one technology to another, but are predictable. We have identified seven primary economic patterns leading to lock-in: contractual commitments, durable equipment and aftermarkets, brand-specific training, information and databases, specialized suppliers, search costs, and loyalty programs. By taking stock of your own expenditures over time in these areas, and those of your customers (and suppliers), you can systematically identify how lock-in affects your business.
In the next chapter, we build on these principles to help you shape your strategies to make lock-in work for you, not against you.
