We’ve talked about how to surf the Web safely and covered the basics of digital communications. Now we need to cover a few other related topics that have to do with your online behavior in general. We’ll cover online banking and shopping, social media, cloud storage services, and just commonsense tips for living in the digital age.
Banking and Shopping Online
As we discussed in previous chapters of this book, the security standards used by almost all banking and shopping websites are sufficient for protecting your credit card information, at least during the transaction. As long as you see the little lock icon to the left side of the web address box, your communications with the far end are encrypted and secure.1 The real concern is saving your credit card information for future use. While most large online retailers do a good job guarding this data, there have definitely been situations where hackers have managed to steal users’ credit card information from these sites. But, as I said earlier in this book, fraudulent credit card charges are not a huge issue for the credit card owner—the credit card companies will not hold you liable for these charges, and you will never actually be out any money (assuming you report the charges in a timely manner, of course). This is not the case with debit cards, however. Debit cards provide immediate access to the funds in your bank account. If those funds are taken, they’re gone until you can convince your bank to reimburse you. This is why it’s always best to do your online shopping with a credit card instead of a debit card, if at all possible.
But the issue we’re discussing here is whether you should store your credit card information on a given website to make future purchases easier. You should feel safe doing this with any major, reputable retailer, if you plan to do a lot of shopping there. But know that you can also put your credit card information in a password manager like LastPass and rapidly fill in all the relevant info on any online shopping site. So, instead of trusting the retailer with this info, you can just trust it to your password manager. Since the risks are fairly low, it’s really a matter of personal preference. I tend to save my credit card info on sites where I do a lot of shopping and use LastPass to fill in my credit card info on other sites. (I also use virtual, one-time credit card numbers—I’ll explain this in the checklist at the end of this chapter.)
Online banking is another practice that makes some people very nervous. Because banks are doing everything possible to reduce the need to hire human beings, it’s actually becoming expensive to avoid online banking. Banks have taken to charging their customers for excessive in-branch transactions that require a live person. Like it or not, online banking is here to stay, and it’s the only way to avoid the growing list of banking fees. Like online shopping, interacting with your bank online is perfectly secure and safe. You should feel at ease checking balances, making transfers, and paying bills using your computer or smartphone. I know it seems scary, but financial institutions have been sending trillions of dollars in financial transactions over computer networks for decades, and they have a vested interest in doing it securely.
However, what you may want to do is to set some reasonable limits on what someone can do with your accounts. I say “someone” because we’re talking about the case where someone other than yourself has gained access to one or more of your accounts. This is true whether you use online banking or not, actually. For example, overdraft protection can be helpful for you if you accidentally write a check that your primary account can’t cover, but if you allow unlimited overdraft protection, this could also allow someone who manages to steal your checkbook or debit card to drain multiple accounts! So, you should talk to your local bank representative about putting commonsense limits on your bank accounts and be careful about how your various accounts are linked together. This is similar to creating a regular, non-admin computer account. You’re guarding against the case where someone gets access to your account and limiting the amount of damage they can do.
It pays to be vigilant, as well. You should check in on all your online financial accounts from time to time, looking for suspicious activity and verifying the account balances. Many online banking sites offer automatic notifications for all sorts of specific activities on your account like transfers, withdrawals, and purchases over a certain amount. You can also be notified of things like password and account changes, overdrafts, large deposits, and so on. This is a great way to keep tabs on your account activity.
Credit Bureaus and Identity Theft
Identify theft is one of the nastiest problems you can deal with because it can negatively affect you for years, even if you do everything right. If someone manages to open a line of credit in your name and runs up a huge bill and these bills go to collection agencies, they could hound you for a long time.
Much of this hinges on some shadowy but powerful organizations called credit bureaus . The “Big Three” credit bureaus—Equifax, Experian, and TransUnion—know all about you. And yet you are not their customers; you’re their product. You can’t take your business elsewhere if you don’t like their service. You indirectly agreed to give these companies your information by agreeing to terms of service with your banks, credit card companies, utility companies, and loan agencies. The bureaus track all of your spending and debt and then generate a single score that supposedly determines your creditworthiness. The precise algorithm for calculating your credit score is a closely guarded secret, and even your access to your own credit history is strictly limited (one copy of your report for free, per year, per bureau).
In 2017, Equifax suffered a massive security breach, and the records of almost 150 million customers (nearly half the US population) were stolen. Equifax’s response was slow and insufficient, and yet to date there have been no real consequences for the company,2 or even the industry as a whole.
While many financially savvy people are aware of the “Big Three” credit bureaus, many are less aware of the Work Number and the National Consumer Telecommunications and Utilities Exchange (NCTUE). The Work Number is a service provided by Equifax that collects wage information from employers on about one-third of the working US population. This information is being used to do things like verify your employment history for prospective employers and validate your income for loans and social services.
The NCTUE is a sort of specialized credit bureau that is focused on cellular services but is also being used by utilities companies. While this company appears to be a consortium of agencies, most of them appear to ultimately be owned by (wait for it) Equifax.
To be fair, these agencies do provide a valuable service that many consumers and lenders rely on. The problems are that they are not responsive to consumers and their security mechanisms have proven to be abysmal.
You can’t currently opt out of these credit services, meaning that they will still collect your data—and it will therefore remain at risk of being stolen or abused. However, you can at least protect yourself from someone opening new credit in your name (i.e., identity theft) by implementing a credit freeze . The process is painful (and we’ll go over this in the checklist), but at least now it’s free everywhere thanks to some legislation passed in 2018. Freezing your credit means that your credit score and credit history will not be available to anyone for any reason. This means you can’t get a new credit card or a new loan without first “thawing” your account. But realize that your credit history is also often checked for other reasons: signing up for utility services, getting a new cell phone, applying for a job, and so on. When this happens and you need to grant access to your credit report, you’ll have to find out which credit bureau they use and temporarily thaw your account.
Cloud Storage Services
Everything is moving to “the cloud.” That is, more and more of our services and data are going online. As we discussed in Chapter 5, Apple and Microsoft have made it nearly mandatory to sign up for their cloud accounts to use their products. However, in this chapter I’m focusing on cloud storage services. These services give you a virtual hard drive somewhere out on the Internet where you can store just about any type of computer file.
There are dozens of cloud storage providers these days, all claiming to protect your data with “military-grade” or “unbreakable” encryption. As we discussed with online backup, you need to understand who holds the keys to your encrypted data. In most cases the answer is “them,” unless you explicitly take steps to change that behavior.
The simplest analogy for this is renting space in a physical storage facility, like U-Store-It or PODS. You buy a certain size container (the larger it is, the more it costs to rent), and then you put your excess stuff in the box. When you’re ready to leave, you lock it. But who keeps the key? Would you be comfortable leaving the only key with the owner of the rental facility? That would mean anyone who could convince the owner to open that container would have full access to whatever is stored there. Most places allow you to keep the key (or perhaps there are two locks on the door and you each keep one key). This isn’t only for your protection; it also neatly absolves the rental facility from responsibility for protecting access to the key and deciding who should be allowed to check out that key. The owner knows that, if necessary, they could break your lock and gain access, too—for instance, if you die or lose the key or if a law enforcement officer comes knocking with a warrant.
However, the default key arrangement for cloud storage is usually the exact opposite—the storage provider keeps the key, not you. Again, this means anyone who can convince (or coerce) the owner into coughing up the key can gain full access to all your digital stuff. It also means the owner (or any of employees) has complete access, as well. However, some of these cloud storage providers will give you the option to provide and manage your own key. You have a password manager, so you can use it to safely store these keys. There are also applications you can use that will manage this encryption for you, in the case where the storage provider doesn’t offer the option for you to keep the keys. They will encrypt all your data before it’s stored and decrypt it when you need it. You can think of it as a second lock or a container within a container.
Sometimes, though, this is just too much hassle. Encrypting your data in the cloud means that it’s harder to share with other people, and it may break some nice features (like searching by file name or content). The thing to keep in mind if you’re not going to hold the encryption keys yourself is that whatever you put in the cloud could potentially be seen by someone else. As long as you don’t care about that, then you can forget about pre-encrypting the data. It’s important to realize, however, that just because you’ve deleted a file from this cloud service, they may still have a copy. For example, when you delete a file from Dropbox, you can actually log in to your Dropbox account on a web browser and undelete it! That means it was never really deleted in the first place. These services may keep multiple copies, as well—so that if you change a file, they may retain a copy of what it looked like beforehand. They do this not to be sneaky (probably) but to help you recover something if you accidentally alter or delete it.
Social Media
Now we finally come to the web services that we lovingly refer to as social media. This includes things like Facebook, Twitter, Instagram, LinkedIn, TikTok, and Pinterest.3 The stated purpose of these services is to allow people to find, connect, and share things with other people. However, I’m here to tell you that the actual purpose of these sites is to compile massive dossiers on as many people as possible and sell that data for money. The profit model for all of these “free” services is to provide companies with highly targeted advertising on the principle that catering to an individual’s tastes, income, education, religion, and so on will make them much more likely to buy. Social media services are the most colossally effective Trojan horses ever created by humans. People willingly provide hordes and gobs of extremely personally information on these sites. Even if you try to restrict access to your closest friends and family, you’ve already given the service provider permission to share this information with third parties (this is buried somewhere in your “terms of service”).
Probably the best recent example of this is the Cambridge Analytica scandal.4 It’s a long story, but basically a political research and marketing company wanted to learn about as many US voters as possible. Working with a psychology researcher named Aleksandr Kogan, Cambridge Analytica (CA) created a fun little Facebook survey called “This Is Your Digital Life” that attracted 270,000 people to respond. When you take these surveys, you’re granting the third-party survey maker access your Facebook data. However, Facebook also allows third parties to gain access to all of your Facebook friends’ information, too. This allowed Cambridge Analytica to amass a database of highly personal information on nearly 90 million Facebook users. Using this data for marketing purposes was against Facebook’s policy, but CA lied and said it was using it for academic research.
But the real problem isn’t policy, enforcement, or even security. The problem is that this data is being collected in the first place. The mere existence of so much highly personal information begs for it to be stolen and/or abused. On a personal level, people will invariably use this data to stalk love interests, check up on spouses or ex-lovers, dig into the lives of celebrities and politicians, and so on. It’s just human nature. At the corporate and government level, the potential for abuse is almost limitless. The only way to prevent this is to not collect the data in the first place. Since we can’t prevent these companies from collecting the data, the next best option is to just never use these services.
Yeah, yeah, I know. That ship sailed a long time ago for most of you. You can argue that it won’t really do you much good to quit at this point, and frankly most people just can’t give it up. These social media services are wildly popular because people truly enjoy using them to share all sorts of information with friends and family. So, let’s just acknowledge that and move forward. In the checklist for this chapter, I will give you some specific advice on how to lock down access to your social media accounts and how to avoid giving out the wrong types of information. But if you’re ready to make the break, I’ll also tell you how to delete your accounts. (You can do it! I did. In the wake of the Cambridge Analytica debacle, I deleted both my Facebook accounts.)
It’s also important to note much of the juiciest personal information on social media is provided willingly by the account owner (i.e., you). Most posts on social media are public by default. This has all sorts of implications. First of all, how many websites still use “personal questions” to recover your account when you forget your password? Common questions are “what street did you grow up on” or “what the make of your first car” or “who was your first employer.” Much of this information is there for the taking on Facebook.
If you turned your Social Security number into a dollar amount, how rich would you be?
Your porn name is the name of your first pet plus your mother’s maiden name. What’s yours?
Those may seem painfully obvious to you, but these quizzes, polls, and games glean lots of other personal information.
But there’s even more ways that you give juicy information to these service (and potentially to bad guys): metadata—specifically photo metadata. Let me give you just one example. John McAfee (of antivirus company fame) was sought as a “person of interest” in a murder in Belize. McAfee is rather paranoid and said he believed the local police would kill him—so he fled the country. He did a covert interview with Wired magazine that included a photo of McAfee at a hidden location. But the magazine failed to remove the photo metadata before posting it online. This photo metadata (called EXIF data, or Exchangeable Image File format) contained the exact longitude and latitude of the photo, along with the date and time. Turns out, he was in a posh resort in Guatemala. This nearly got him extradited back to Belize, but McAfee claimed that he faked a heart attack to give his lawyer time to come save him. He was eventually deported to the United States. Belize didn’t pursue him, but McAfee said they did seize and auction off all his stuff. (He’s not the most trustworthy news source.)
Summary
Online banking and shopping are actually very safe, in most cases. As long as you deal with a reputable retailer, make sure your connection is secured, and use a credit card from a major bank, you should be fine.
Identity theft is one of the most difficult attacks to recover from. To prevent someone from opening new credit in your name and sticking you with the bill, your best option is to freeze your credit.
Cloud services provide extremely convenient ways to access and share your files, pictures, and other data, but you need to understand who holds the keys to that online storage and know that your storage provider may save copies of your files long after you “delete” them.
Social media services like Facebook and Twitter collect unprecedented amounts of information on their customers, and they make money by selling that information to advertisers. You need to be mindful of what information you give them and what you share with others.
Checklist
The checklist for this chapter sort of covers the “rest of the Internet”—things like online banking and shopping, social media, and online behavior in general. The items here are a bit of a hodge-podge of online safety guidelines, tips, and tricks.
Tip 9-1. Lock Down Your Apple/Microsoft Accounts
It’s almost impossible to avoid setting up Apple and Microsoft accounts. These cloud services are deeply embedded into most recent versions of Mac OS, iOS (iPhone and iPad), and Windows. But you can still tweak the settings on these accounts to better protect your privacy.
In this section, we’ll lock down the settings on your computer and online. (In Chapter 11, we show you how to lock down your iOS and Android cloud settings.) There’s no way to sugarcoat this…there are a ton of settings here. I’m not going to go through every single one of them, just the key ones. Regardless, I suggest you poke around and at least familiarize yourself with what’s there. The other hard truth is that these settings change often. The settings for Windows 10 changed while I was writing this book. And when new settings show up, they’re often “on” by default (i.e., set to the least private option). This is the world we live in now.
As you read through all of these settings, keep in mind that all of the talk about “personalization” and “interests” and “history” is really about building up a profile on you that may be shared with others (on purpose or via hacking). The way they customize your experience is by collecting data about you. Just say no wherever you can. Until we have strict privacy laws or change the Internet profit model, you have to assume that all of this is more for their benefit, not yours.
Tip 9-1a. Microsoft Windows 10
- 1.
On your computer, open Settings. Open Privacy.
- 2.
Under the General tab, I would turn off everything except maybe “Let websites provide locally relevant content”. This would limit search results to English sites, for example (Figure 9-1). This probably only affects their Edge browser, anyway (and you’re using Firefox, right?).
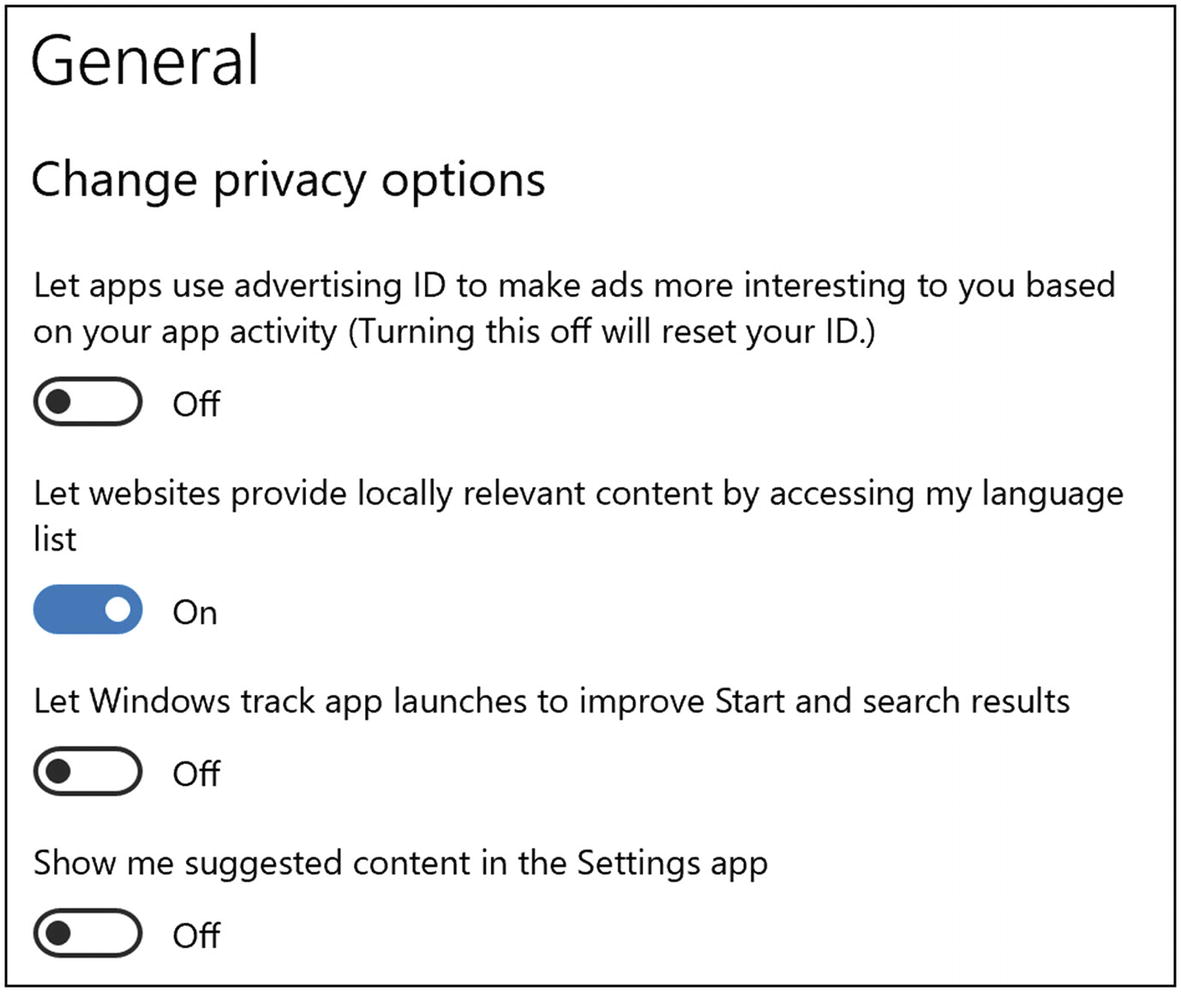
Windows 10 General privacy settings
- 3.
Under the Speech tab, you can disable Cortana—which is Microsoft’s personal digital assistant. It can be really fun to use, but realize that it means your computer is constantly listening to you and sending some audio snippets to Microsoft if it believes you said “Hey, Cortana”. If that creeps you out, disable this.
- 4.
Under the “Diagnostics & Feedback” tab, I would turn everything off—especially the “tailored experiences” (Figure 9-2).
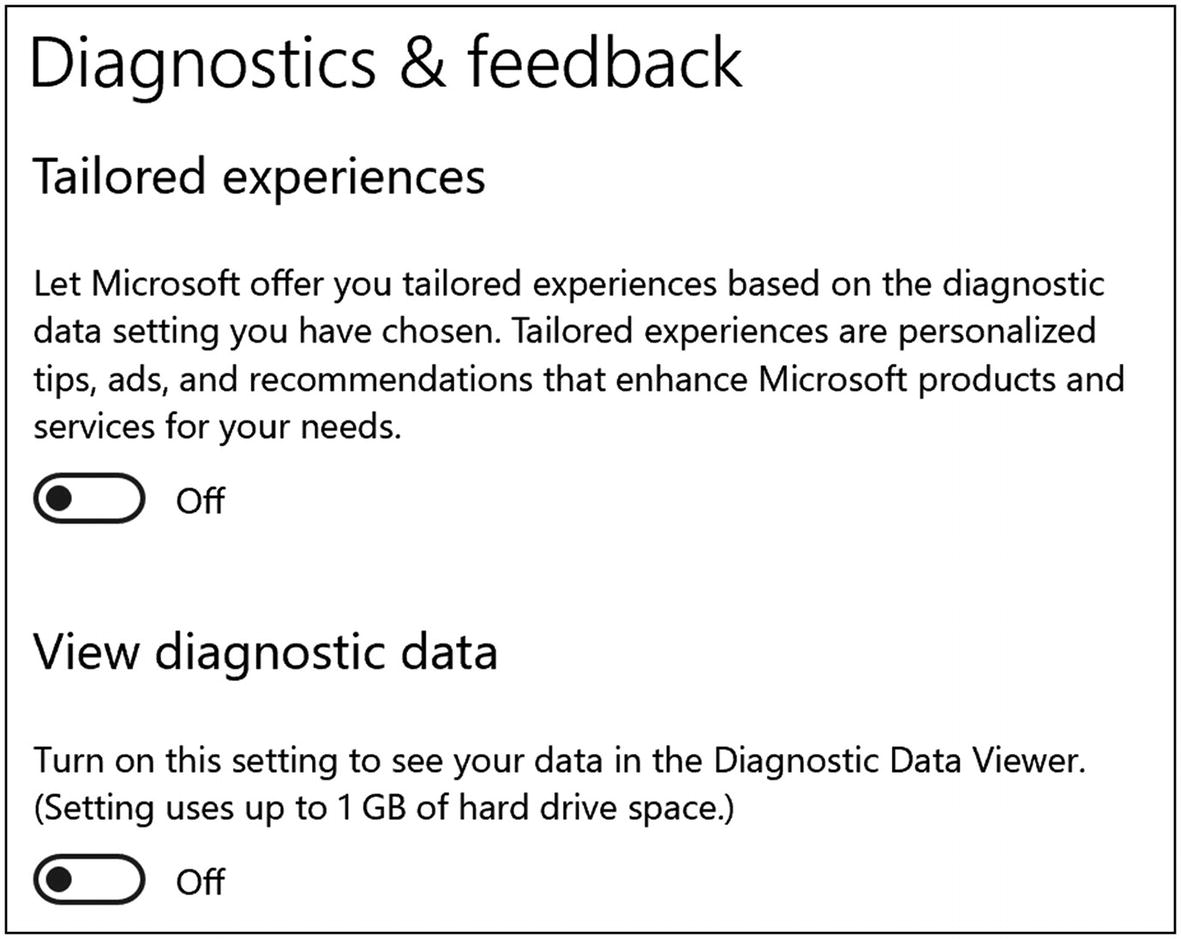
Windows 10 Diagnostics & feedback settings
- 5.Under the “Activity history” tab, disable sending history to Microsoft.
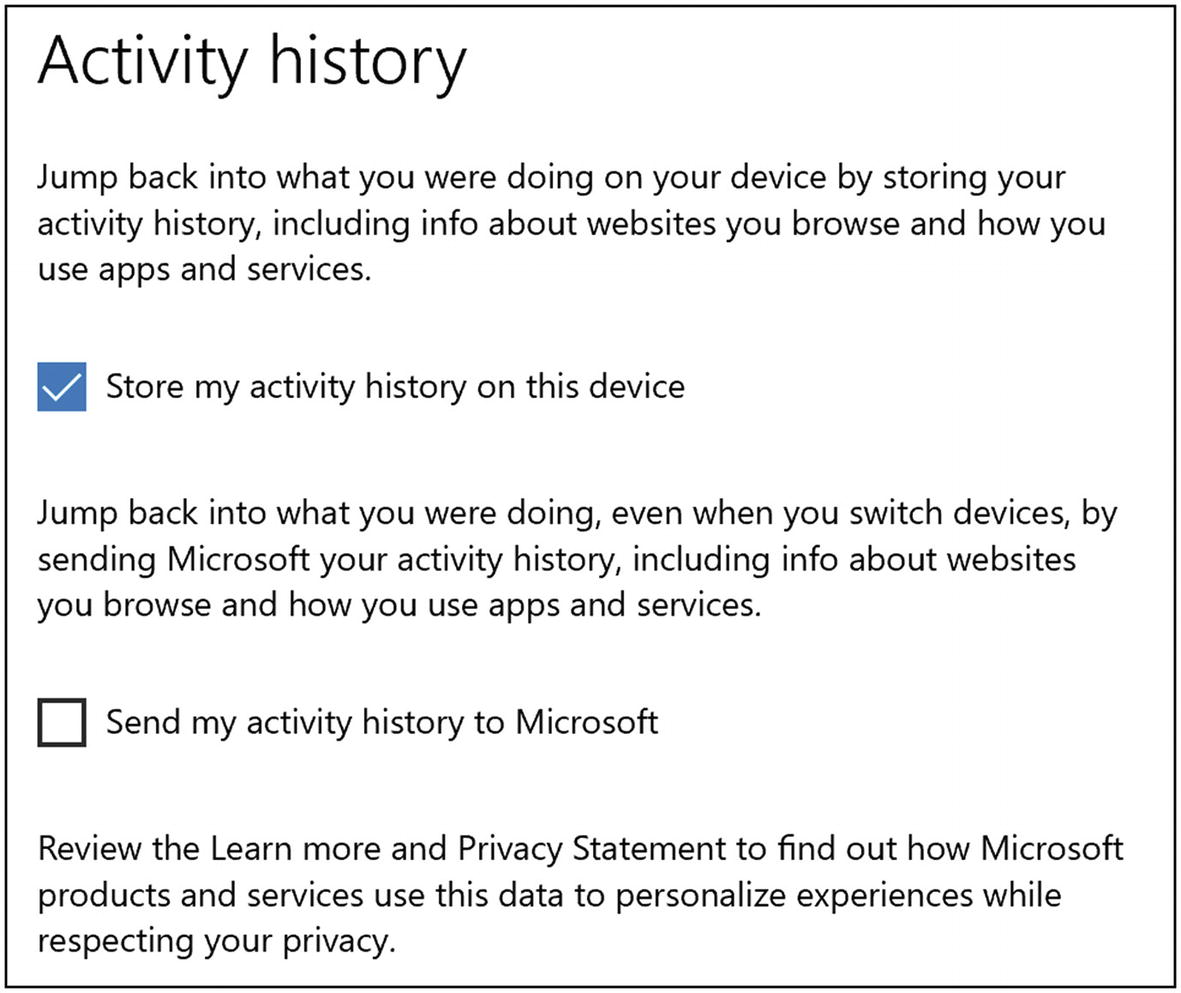 Figure 9-3
Figure 9-3Windows 10 Activity history settings
- 6.Under “App permissions”, there are a gazillion settings, but they basically fall into the same pattern. You can enable or disable a particular feature for all people and all applications, or you can enable/disable a feature on a per-application level. Unfortunately, the descriptions are not always clear—but again, you can change your mind later. Disable things where you can, and when you find that you need them, you can turn them back on. The important ones to restrict for privacy are
Location
Microphone
Camera
Account info
Contacts
Calendar
- 7.
Go back to the main Settings window and search on “Start settings”. Turn off “Show suggestions occasionally in Start”. (Notice how they slip in “occasionally”; they’re trying to get you to leave this alone.)
Finally , you should also go to your Microsoft online account, if you have one, and review the privacy settings there. Most of the settings are handled earlier, but there are a few general account settings you might want to change. In particular, you should click the “Ad settings” tab and turn off all personalization options.
Tip 9-1b. Mac OS
- 1.
Go to System Preferences and find your iCloud settings. Click the “Apple ID” button.
- 2.
From the Apple ID settings, click iCloud at the left. You will then see several options for services to sync or back up in iCloud (Figure 9-4).
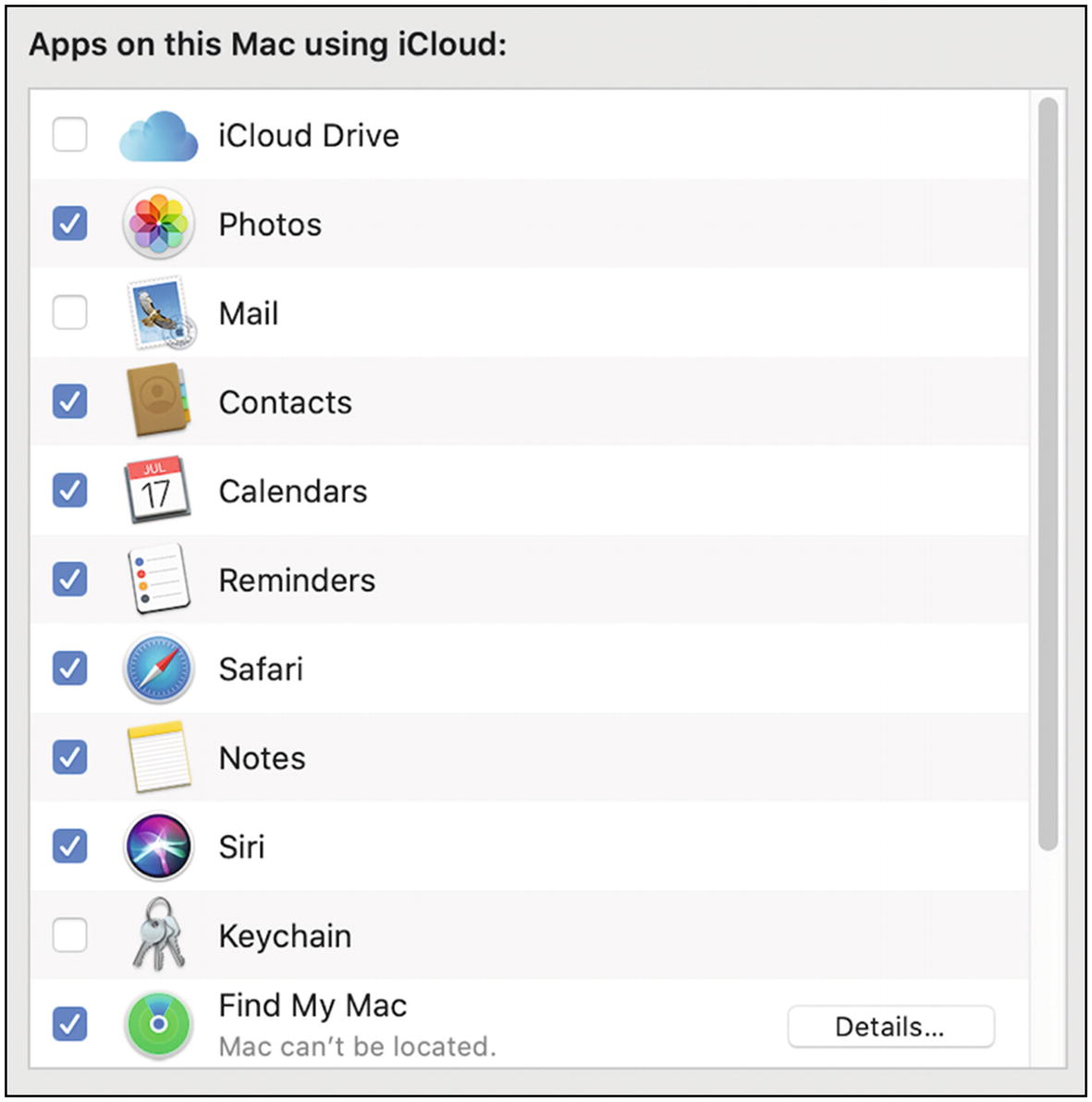
Mac OS iCloud settings
- 3.You’ll want to make your own choices for each of these, but here are some specific things to consider:
iCloud Drive is Apple’s built-in cloud storage service, like Dropbox but with more Apple-centric features. Apple pushes you to use this constantly, which is annoying. And the amount of free space they give you (5GB) won’t cover much. But for $0.99 per month you can get a lot more (50GB). Just realize that currently anything you back up this way is accessible to Apple—you can’t encrypt this with your own password (yet).
I would disable Keychain backup to iCloud. You have LastPass for managing your passwords. While this can be convenient because it’s built into all of Apple’s products, it’s currently not as secure as LastPass. (This may change with time. Apple is becoming very serious about its security and privacy.)
If you have a laptop (MacBook), I strongly encourage you to enable Find My Mac. It’s less useful for desktop computers that never leave the confines of your home, but if you’re at all worried about your computer being stolen, you should enable this feature that can help you find it.
You need to decide how much information you want to put into iCloud. Look at the other settings here and disable anything you don’t need to synchronize with other Apple devices.
- 4.
Next open Security & Privacy settings under System Preferences (Figure 9-5).
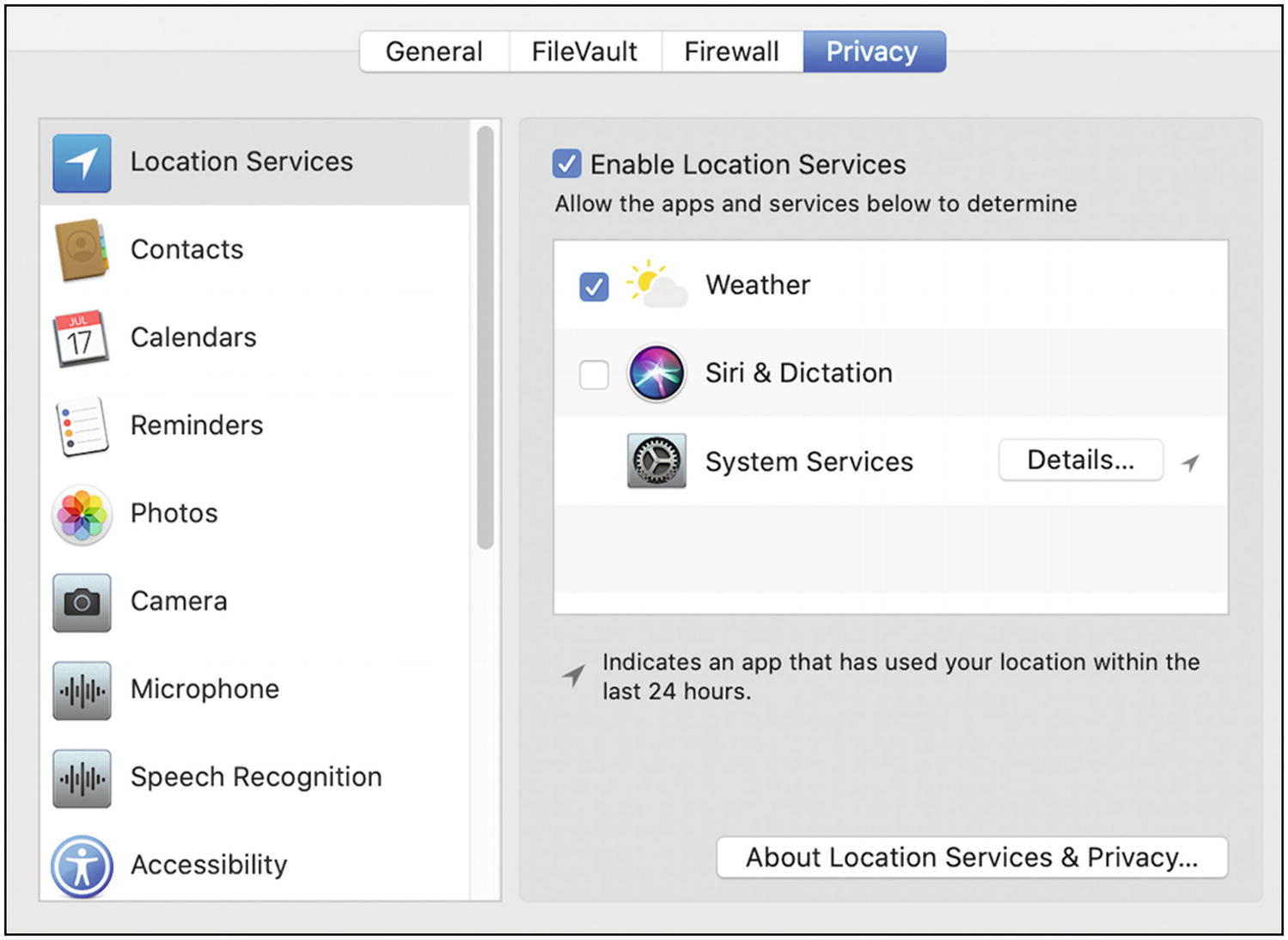
Mac OS Security & Privacy settings
- 5.If necessary, unlock the settings by clicking the padlock at the lower left. There are several settings here. The basic idea is that you want to limit access to potentially private things to only those applications that truly need it. When in doubt, turn it off—you can always turn it back on. The important ones to restrict for privacy are
Location
Microphone
Camera
Account info
Contacts
Calendar
To learn more about Apple’s privacy settings, you can go to https://privacy.apple.com .
Tip 9-2. Use Throwaway Email Accounts
Many websites will ask you to create an account to view their content or access key portions of their website. This mainly allows them to send you marketing emails or sell your contact info to advertisers. To ensure that you’ve given them a valid email address, these sites will often block access until you click a special link they send to you via email. If you don’t plan to regularly use this site, creating a new, unique user ID and password can be very annoying.
- Shared logins : The following sites will give you some preexisting accounts that people have shared so that you may not have to create an account for yourself.
login2.me
bugmenot.com
- Disposable email accounts : When you go to these sites, they provide you with a throwaway email account. You can check your email for a short period of time and then abandon it.
10minutemail.com
throwawaymail.com
maildrop.cc
guerrillamail.com
mailinator.com (warning: emails are viewable by anyone)
- Email aliases : Some email services offer you the ability to create email aliases. These are email addresses that will forward directly to your normal email inbox, but you can cancel them at any time, effectively blocking that person from being able to ever reach you again—without abandoning your real account.
Gmail: Simply add any set of characters after a plus sign to your email address. For example, if your real address is [email protected], you can give out [email protected] and the email will go to the original address.
Fastmail: https://www.fastmail.com/help/receive/aliases.html
Firefox Relay : This is a really interesting new option from Mozilla that allows you to create email aliases on the fly. Mozilla will then forward these emails to your regular email account, masking your actual email address. And if the service you signed up for starts abusing your email account, you can simply disable this alias to cut them off—without affecting your real account.
Sign-In with Apple : You’ve undoubtedly seen “Sign in with Google” and “Sign in with Facebook” all over the place. I’ll tell you why you shouldn’t use those later in this chapter. But the Apple version was specifically offered as a privacy-centric version of these sorts of services. It allows you to avoid creating a new account with the website—another user ID and password to keep track of. Instead, you sign in using your Apple credentials, and Apple basically vouches for you. But the key feature is that when you do this, you can generate a custom, private email address to give to the website (an alias). This will hide your real email address. Apple will handle forwarding emails from the dummy address to your real address. And if you ever want to cut this site off, you can remove this dummy email address without affecting your real email account.
One important thing to note about using Apple’s or Firefox’s anonymous email features: it will make it hard or even impossible to work with that site’s customer support if something is wrong with your account. The first thing they’ll need is your user ID, which is usually your email address. And you may have no idea what was generated for you. I would only use these services for accounts you could throw away and start over at any time (i.e., where the need for an account only benefits them, not you).
Tip 9-3. Use Credit Cards Online (Not Debit Cards)
Quite simply, if someone charges something to your credit card without your permission, you’re not actually out any money—the credit card company is. As long as you report the fraudulent charge in a timely manner, you won’t be responsible for the charge. With debit cards, that money is actually gone from your bank account, and you then have to fight to get it back. So, whenever you shop online (or over the phone), use a credit card.
Tip 9-4. Use Virtual Credit Card Numbers
Some credit cards offer a one-time-use “virtual” credit card number . This is a great option for buying something online from a store that you will probably never do business with again. This is usually done online, through your credit card account website, but it can be hard to find—call the number on the back of your card and ask about this service. This service will generate a throwaway 16-digit credit card number that will work only one time. It comes with its own expiration date, security code, and everything. The charge will show up on your regular bill. Just be sure to save that temporary card info until you’ve received the merchandise, in case you need to return it or something.
The Capital One service, Eno, allows you to create cards that act as aliases for your real credit card. Unlike single-use virtual numbers, you assign these cards to a particular merchant. This has at least two benefits. First, if that company is hacked, the card info will be useless to the hacker—it works only for that vendor. Second, if your real card is ever lost or stolen, these alias cards will not be affected. They will still be tied to your account and will be associated with your new credit card number.
The Apple credit card (Apple Card) offers a lot more privacy than your average credit card. You need to realize that Visa, Mastercard, and others are keeping track of everything you buy, and using it for their own purposes as well as selling it in some supposedly anonymous form to third parties. Apple doesn’t share or sell any of this, except with Goldman Sachs (the bank backing the card)—and supposedly they don’t allow Goldman Sachs to sell or share it, either (outside of Goldman Sachs). If you couple it with Apple Pay, it adds even more layers of privacy with randomly generated card numbers and limiting access to cardholder information.
And finally, there’s a company called (tantalizingly enough) Privacy.com that runs another anonymizing, virtual credit card service. The number of features is truly amazing. But you have to trust this company enough to give them direct access to your bank account. They address this on their FAQ page, if you’re interested. However, for a company with “privacy” in its name, it seems more like the service is about security (protecting your real bank/credit card account by using virtual, temporary ones). I read their privacy policy and didn’t find it terribly convincing. But for security purposes, it’s an interesting concept .
Tip 9-5. Give Your Credit Card Company a Heads-Up
Because credit card companies are ultimately the ones on the hook for illicit purchases, they have implemented all sorts of automatic antifraud protections. Their computers are well aware of where you live and what sorts of things you typically buy. If you suddenly buy something in a foreign country or make a large purchase from an online store, they may turn off the card until they can talk to you and verify that the charges were legit. To avoid this, you can give them a call ahead of time to let them know you’ll be traveling abroad or will be buying something expensive from a place you don’t normally shop. (Note that if they have your cell number or email address, and you give them permission, they will text or email you when you have suspicious charges, giving you a chance to validate the purpose before they disable your card.)
Tip 9-6. Set Up Restrictions on Your Financial Accounts
Services such as overdraft protection, funds transfers, and linked accounts can be convenient. However, you need to think about what someone else could do if they were to somehow gain access to your checkbook, ATM card, or debit card. Anything you can do with it, they can also do. Don’t link two accounts unless you really need to (like with overdraft protection). If possible, put limits on daily withdrawal and transfer amounts. If you need to, you should always be able to go into your bank branch if you need to exceed these limits—but at least in that case you will deal with a human that can verify your identity.
Tip 9-7. Turn On Account Alerts
Many online banks, credit card companies, and financial firms have ways to create alerts on various types of account activity including being able to set trigger levels. For example, you can be alerted whenever someone withdraws more than $200 from an ATM or charges more than $300 on your credit card in one day. These are really fantastic ways to keep tabs on your accounts. I highly recommend that you use them.
Tip 9-8. Freeze Your Credit
The most potent way to prevent an identity thief from opening a new line of credit in your name and sticking you with the bill is to freeze your credit at the Big Three credit agencies: Equifax, Experian, and TransUnion. When you freeze your credit, you prevent banks, lenders, credit card companies, employers, and really anyone from obtaining your credit record. This effectively prevents anyone from getting a new credit card or loan or bank account in your name (including yourself). If you need to do any of these things, you will need to find out which credit bureau is needed and temporarily “thaw” your account. Thanks to recent legislation, this process is now completely free (as it should be). For a freeze, you will have to individually contact all three agencies.
If you know you will be needing to access your credit report frequently (making the freeze/thaw process too painful), you might instead set a fraud alert on your account. It will require that they contact you before opening any new credit lines in your name. This is also free but will expire after a year. You only need to contact one of the Big Three agencies for this—that agency will contact the other two for you. (And because the credit bureaus make money on each credit request, they will often try to convince you to use a fraud alert instead of a full freeze. Don’t be distracted—if you can handle a full freeze, definitely do it.)
Equifax: https://www.freeze.equifax.com
TransUnion: https://www.transunion.com/credit-freeze
Tip 9-9. Use Private Cloud Storage Services
Cloud storage providers will probably encrypt your data, but if they also hold the key, then it’s possible for that data to be viewed by employees, hackers, or legal authorities. And you should assume that your data will be saved forever (even if you delete it).
This tool can also be used to create encrypted vault folders on your computer, as well (i.e., you’re not limited to cloud storage folders).
Tip 9-10. Don’t Broadcast Your Travel Plans
While it’s good to give your credit card company a heads-up on travel, you shouldn’t be broadcasting this information on Facebook or Twitter or any other social media (at least not as a public post). Criminals actually monitor social media sites looking for people who will be away from home for extended periods of time. You should also refrain from posting vacation pictures during your vacation to a public location, as well. Post them to a private service or just post them when you get home. (See the next tip, too.)
Similarly, you should never post pictures of your airline tickets or boarding passes online. You should also be careful how you dispose of your boarding pass and presumably your airline-printed luggage tags, even after your flight. These codes can contain things like your name, frequent flier number, record locator number, and other personally identifiable information. This information could be used to alter or even cancel your next flight or be used to gain access to your frequent flier account, among other things.
Tip 9-11. Scrub Your Files Before Sharing
Files today can come with a lot of hidden data embedded in the document. This metadata can contain your name, address, GPS location, camera settings, and much, much more. This data is very helpful to you and your applications that read these files but can also be valuable to bad guys.
Photos contain a ton of info called EXIF (Exchange Image File format) data. If you upload pictures of your kids at the local park or at their school or friends’ house, those pictures contain the date, time, and GPS location. You might not want to be sharing those online.
Microsoft Office files and PDF files are also known for containing a lot of metadata, including your full name and possible contact information.
So before you share a file, you should scrub out any private metadata. While some social media sites will automatically do this for you, I wouldn’t count on it. You can usually see this information by looking at a file’s “properties.” How you do this will depend on your operating system and the type of file you’re viewing. You can also try uploading your file to one of these sites to view the metadata:
- 1.
To remove metadata from most photo formats as well as PDF files, you can try one of these two free applications:
- 2.
To remove metadata from Microsoft Office files (Word, Excel, PowerPoint), you can use Microsoft’s Document Inspector—though this seems to only be available on Windows, not Mac. However, you should be able to save a copy of the file with all the metadata removed. With the document open, go to the File menu, then Info, and then Inspect Document. There should be an option to “Remove personal information from file properties on save”.
Tip 9-12. Don’t Sign In Using Facebook, Google, Etc.
You’ll see many sites now offering to let you sign in using your Google, Facebook, or Microsoft credentials instead of setting up a dedicated account for that site. Sure, this is convenient (and should actually be secure), but it means that you’re allowing Google or Facebook to track you on these sites. Since you have a kick-butt password manager, it’s no big deal to set up a dedicated account on each of these sites with unique passwords. Or try using throwaway accounts for one-time access (covered earlier).
Tip 9-13. Don’t Divulge Too Much Personal Info Online
This is a tough one. For whatever reason, people love to overshare on sites like Facebook, Twitter, Pinterest, and Instagram. But just remember that this information lasts forever and could be seen by anyone, despite any restrictions you try to put on your account or whatever privacy policy the social media site claims to follow. When you forget your password, how do you recover it? Most sites will ask you to answer three questions that supposedly only you would know the answer to. Where did you go to college? What’s your mother’s maiden name? What’s the name of your first pet or car? This is precisely the sort of information people post on social media. This information can also be used to impersonate you on the phone, as well.
Unfortunately, for social media, financial, medical, insurance, and other important accounts, you will often have to give them complete and valid information. If nothing else, this information may be required to recover access to your account if you forget your password or are locked out for some reason.
However, when signing up for unimportant online accounts—like any account you could just replace with a new account—you should give them as little information as possible. You can even lie, to some extent. Instead of signing up with John Doe, try just using John D. Instead of giving your correct birthday, just give them something close enough. For child accounts, which often enable parental controls and age-based content, you can give a date that’s closer to the actual birth date. Don’t give them your full address, if you can help it. Often a ZIP code is sufficient, unless they need to ship you something.
Tip 9-14. Be Wary of Using DNA Services
There are services available today like 23andMe and Ancestry.com that allow you to use your own DNA to track your heritage and perhaps find long-lost relatives. Some services even claim to help you identify possible future health risks. While there is obvious value to these services, you need to realize that there are many scary ways this data can be abused, as well. Law enforcement and intelligence agencies are using these DNA databases to find people—or, importantly, their relatives. Because you share a significant percentage of your DNA with your parents, your siblings, and your children, you are actually also submitting their DNA when you submit your own. While we can hope that your DNA will be stored securely and access will only ever be granted to law enforcement when presented with a valid, court-reviewed warrant, I wouldn’t count on either. Databases can be hacked. Companies can be coerced. People do things they’re not supposed to.
Worse yet, companies are constantly looking for new ways to bump up their stock price, and monetizing data they already have is an easy way to do that. They may change their privacy policy and slip in something like “by continuing to use this service” or “by installing this update” you agree to the change. What if your health or life insurance company could get your DNA? Or what if your DNA is sold off to a medical research company and they didn’t anonymize it properly? What if drug companies could pay to send mailers to people likely to have various genetic illnesses? Think carefully before you give up your DNA.
Tip 9-15. Account Recovery Questions: Lie
Since password and account recovery is usually accomplished by providing the answer to a few simple questions, why not protect your accounts by simply providing the wrong answers? Nothing says you have to answer these questions truthfully. You just need to be able to faithfully provide the same answers when asked again later. Whoever is trying to hack your account will be trying to give the right answer, and they can’t possibly succeed if you lied.
One method would be to alter the real answers in some predictable way. Most of these questions have one-word answers, so just find some method for modifying the answer that only you know. Maybe prefix each answer word with not or some other prefix. Or repeat the word twice, or even just the first letter. For example, let’s say the question is “What was your mother’s maiden name?” If the real answer is Brown, try NOTBrown or nworB or BrownBrown or BBrown.
If you really want to kick it up a notch, use LastPass to generate totally random answers to these questions—use the password generator. (You may need to disable special characters.) Just be sure to save these answers in LastPass. I would probably save them in the “Notes” section of the website’s vault entry or, if necessary, create a new secure note just for these answers.
Tip 9-16. Limit Who Can See Your Stuff
Most social media services provide ways for you to reduce who can see what you post, who can view your profile, and who can find or contact you. Take advantage of these settings by dialing them down as low as you can stand. Put your “friends” into groups, granting full access only to the handful of people who really deserve it.
There are so many social media services and that’s only the tip of the iceberg in terms of companies that are collecting your data. Here are two websites that have some good guides for changing your privacy settings on social media and other services:
Tip 9-17. Don’t Give Out Your Email Credentials
Many social media sites offer to help you find friends by looking at your email contact lists. To do that, they just need your email ID and password. Don’t worry, we won’t use it for anything else, really! Don’t do it. Just don’t. You would not only be giving them access to all of your email contacts but all your emails, as well…forever (or until you change your password). On Google, it’s even worse—your email account password is also the password for Google Docs, Google Calendar, and dozens of other Google services.
Tip 9-18. Enable Two-Factor Auth Wherever You Can
Note that if you have the option of using an authenticator app (like Google Authenticator and Authy) or using a text message (SMS), you should definitely use the authenticator app. Text messaging isn’t as secure as it should be. It’s better than nothing, however, so if that’s your only option, take it—and when they inevitably offer the time-based authenticator app option, switch to this method.5
Tip 9-19. Read the Terms of Service (or Not)
How many times have you actually read the entire terms of service or the end-user license agreement (EULA) before signing up for some online service or installing an application on your phone or computer? No one does. We just check the box that said we read it and click Accept. Sadly, even if you did read it, you probably wouldn’t learn much. The use of legalese and pleasant-sounding euphemisms make it really hard to truly understand what you’re agreeing to. I encourage you to try it, though—go read Facebook’s or Google’s or LinkedIn’s privacy policy, from top to bottom.6 See if you can figure out what data they collect and who they share it with.
Tip 9-20. Know What They Know
Many of the big online services have a way for you to download all of your information in one fell swoop—every email, every post, every picture, every “like,” every friend, every contact… you get the idea. I recommend you try this, if for no other reason than to understand the sheer quantity of information these companies have on you. Pay special attention to any marketing information—the ads they’ve picked for you, the demographics they’ve guessed for you, and so on.
Instagram: https://help.instagram.com/181231772500920
Twitter: https://help.twitter.com/en/managing-your-account/how-to-download-your-twitter-archive
LinkedIn: https://www.linkedin.com/help/linkedin/answer/50191/accessing-your-account-data
Pinterest: https://help.pinterest.com/en/articles/change-your-privacy-settings
Tip 9-21. Lock Down Your Social Media Accounts
Instagram: https://help.instagram.com/116024195217477
Twitter: https://help.twitter.com/en/managing-your-account/accessing-your-twitter-data
LinkedIn: https://www.linkedin.com/help/linkedin/answer/50191/accessing-your-account-data
Yahoo: https://yahoo.mydashboard.oath.com/select-download-data?dataType=user
Pinterest: https://help.pinterest.com/en/articles/change-your-privacy-settings
Tip 9-22. Close Accounts You Don’t Use
Instagram: https://help.instagram.com/448136995230186
Twitter: https://support.twitter.com/articles/15358-deactivating-your-account#
LinkedIn: https://www.linkedin.com/help/linkedin/answer/63?lang=en
Pinterest: https://help.pinterest.com/en/article/deactivate-or-close-your-account
Google: https://support.google.com/accounts/answer/32046?hl=en
You should also go back and delete/close any other old online accounts you no longer use. You may forget about them, but your data is still there, waiting to be abused or stolen. If you’ve been using a password manager long enough, you can look through all your saved passwords to find old accounts. If you’ve had an email account for a long time, you may be able to search your emails for “welcome” messages or “verify your account” requests. Or you could check out the site Just Delete Me to help jog your memory (and get help deleting your account):
Tip 9-23. Delete Your Facebook History
Facebook recently provided a tool to delete some or all of your history. Until this point, your only option was to delete your entire account. Now you have a new Manage Activity tool that will let you selectively archive or trash old posts and pictures in bulk.
At the time of this writing, the tool was only available via the mobile phone app, but a web version should be out soon. You can go to this website for help:
https://about.fb.com/news/2020/06/introducing-manage-activity
Tip 9-24. Use Privacy-Respecting Alternatives
Google’s free email, calendar, and docs apps are really amazingly powerful and easy to use. I was an early adopter when they came on the scene many years ago. But over the years, Google has decided to mine this treasure trove for personal data, and so now you might be wanting to find some alternatives that will respect your privacy.
Google has an amazing number of free apps and services, including some you may not realize are owned by Google, like Waze, YouTube, and Android. The Restore Privacy website has a lot of wonderful information, including this extensive list of Google alternatives:
https://restoreprivacy.com/google-alternatives
For a truly secure and fully functional Google Docs replacement, I really like CryptPad. It has many different “pad” types—not just replacements for word processing, spreadsheets, and slide shows, but also whiteboards, polls, and even cloud storage:
Tip 9-25. Avoid TikTok Entirely
TikTok is a Chinese social media platform for sharing short videos. It’s mostly used by younger people, but not exclusively. While most social media platforms are privacy nightmares, TikTok appears to be operating at a whole new level—reportedly stealing tons of user data without proper permission, including “draft” videos that were never officially posted.7 In June 2020, a class action suit was proposed in a California court to address these claims. That same month, India (where TikTok is very popular) banned the app over privacy concerns.8 It’s possible the company will address some of these issues, but their track record is extremely shady and I could never trust it, personally.
As this book was going to press, there have been several major developments in the TikTok saga, including a threatened US ban on the app or forced sale of US operations to a US company. TikTok then sued the US government. There are censorship and political issues here, but the bottom line is that I still think it best to just avoid this app altogether.
