In this chapter, we will discuss the main services and cryptographic primitives that .NET Framework and .NET Core offer to professionals. Knowing what services and cryptographic primitives a development technology has to offer is very important, especially if you don’t want to develop the cryptographic algorithms and security schemes from scratch.
Cryptographic primitives
Encryption using a secret key
Encryption using a public key
Digital signatures
Hash values
Random number generation
Support for Suite B
Cryptography Next Generation (CHG) classes
Communication through the Internet is not inherently secure, and in this case encryption needs to be used with the goal of guaranteeing the security of such communication. The communication between these network entities is likely to be read by unauthorized third parties, or even altered. As you have seen before, the purpose of cryptography is to protect the data from being viewed or modified by parties who are not authorized to do so. With the help of the .NET Framework, we have cryptographic classes that are designed to be used within System.Security.Cryptography (see Chapter 9), a namespace that handles cryptography functions and their operations. Also, we are dealing with wrappers for the unmanaged CryptoAPI (Microsoft Cryptography API). Meanwhile, others are fully implemented and tested accordingly. The nice thing is that once we create a new instance of a specific encryption algorithm class, the keys are automatically generated in order to be used as easy as possible, using default properties that are very secure.
This being said, in the following sections we will provide a quick synopsis of the most important encryption algorithms that are supported by the .NET Framework (ClickOnce, Suite B, and CNG), features that were introduced starting with .NET Framework 3.5.
Encryption Using a Secret Key
The encryption algorithms based on a secret key use a single secret key for the encryption and decryption processes. It is very important to guarantee the security of the key from unauthorized parties or services. Any unauthorized party that has access to the key can use it to decrypt data or encrypt other data, claiming and impersonating the real authorized party.
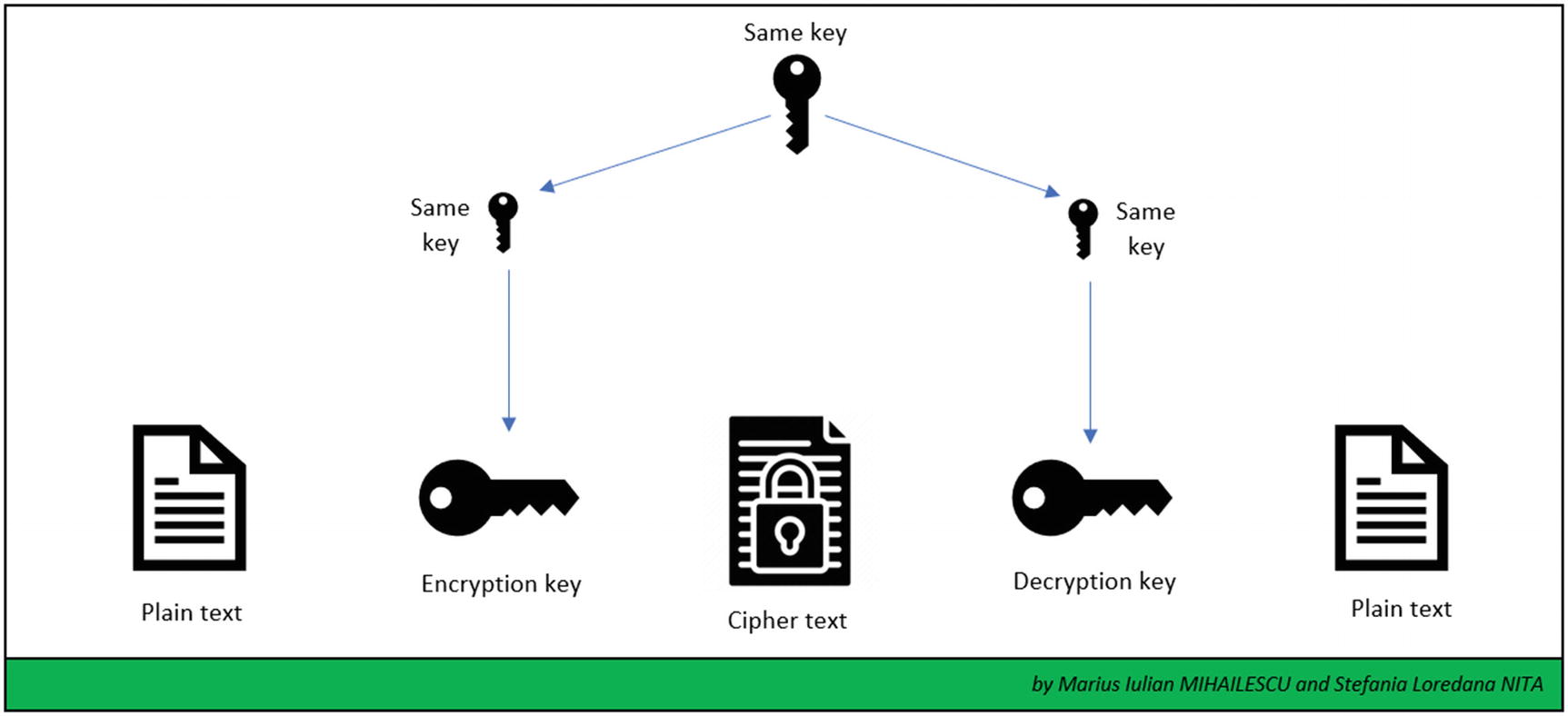
Symmetric encryption
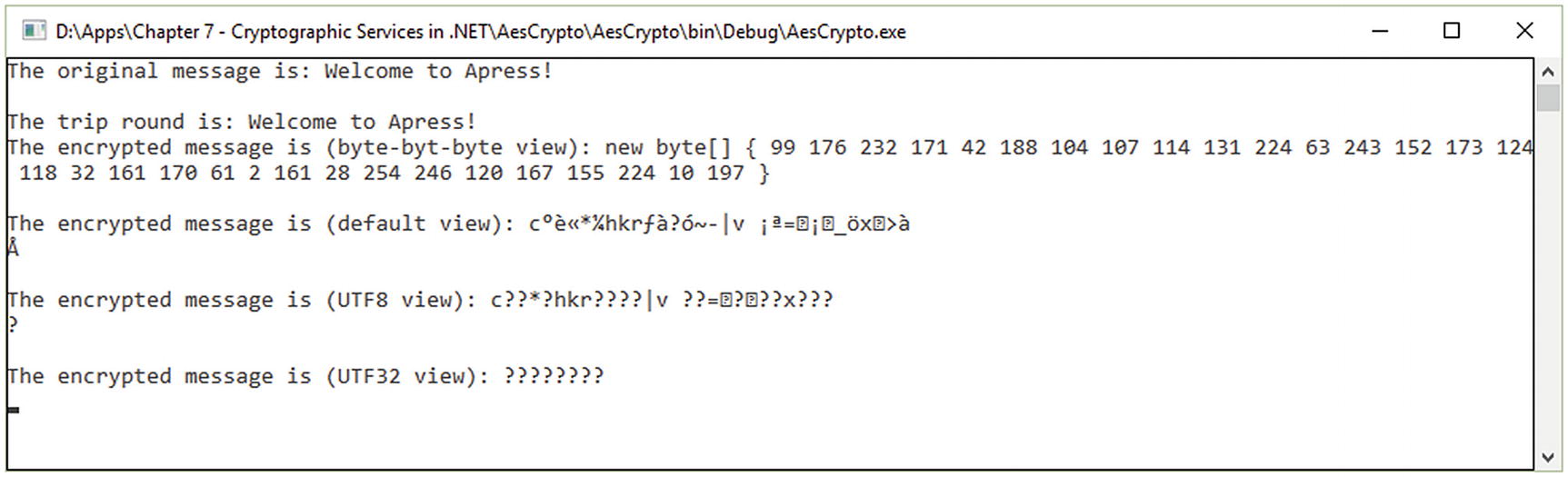
AES execution
AES Implementation Using AesManaged
RijndaelManaged Implementation
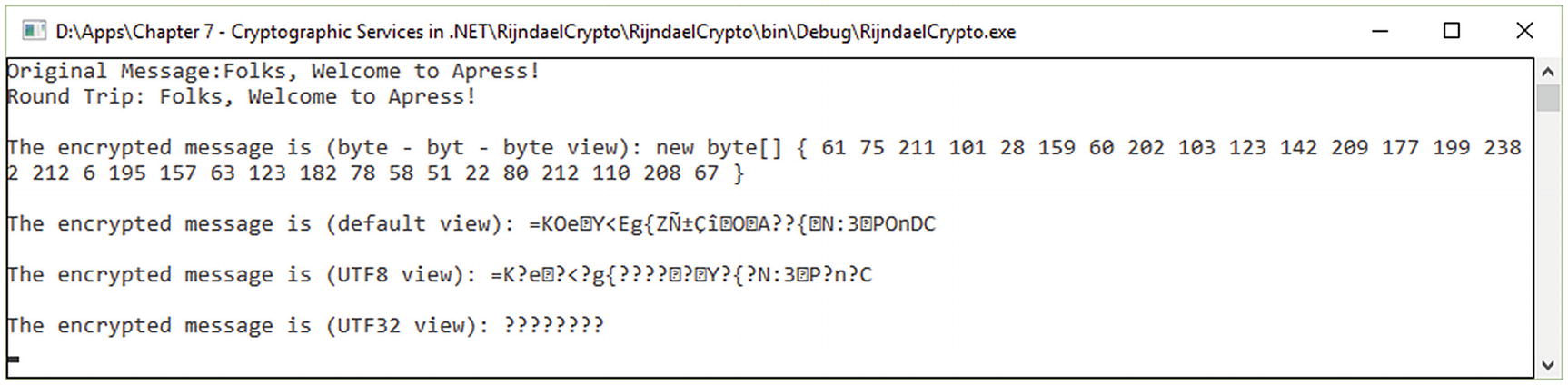
Example of RijndaelManaged
In the following example, we will do two cases of implementation for the DES algorithm. Despite the fact that is overcomed, it is a good example of how cryptographic algorithms and primitives should be treated practically. What makes these two implementations different from the rest of the implementations that exist in real practice is that the first example (see Figure 7-4, Figure 7-5, and Listing 7-3) is doing the encryption/decryption within a file and the second example (see Figure 7-6 and Listing 7-4) is doing the encryption/decryption in memory. When we are dealing with complex systems that use files (such as clear JSON files for Hadoop systems or big data environments), one of the solutions is to design the cryptographic primitives in such way that we are doing the encryption/decryption properly of the files or in the memory without exposing something that could impact the business.

DES algorithm with encryption/decryption in a file
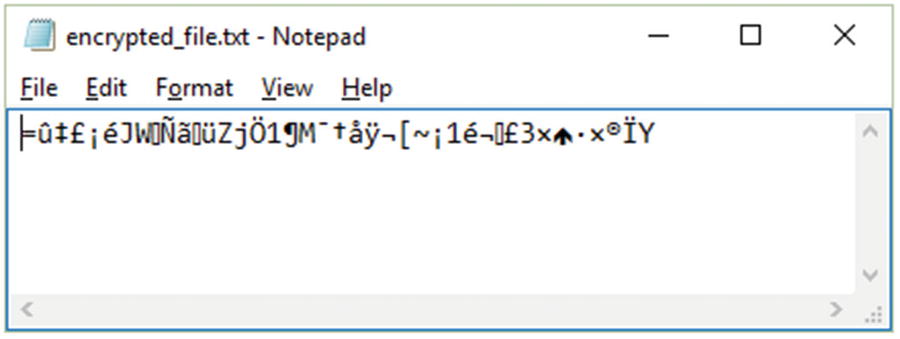
DES encryption result
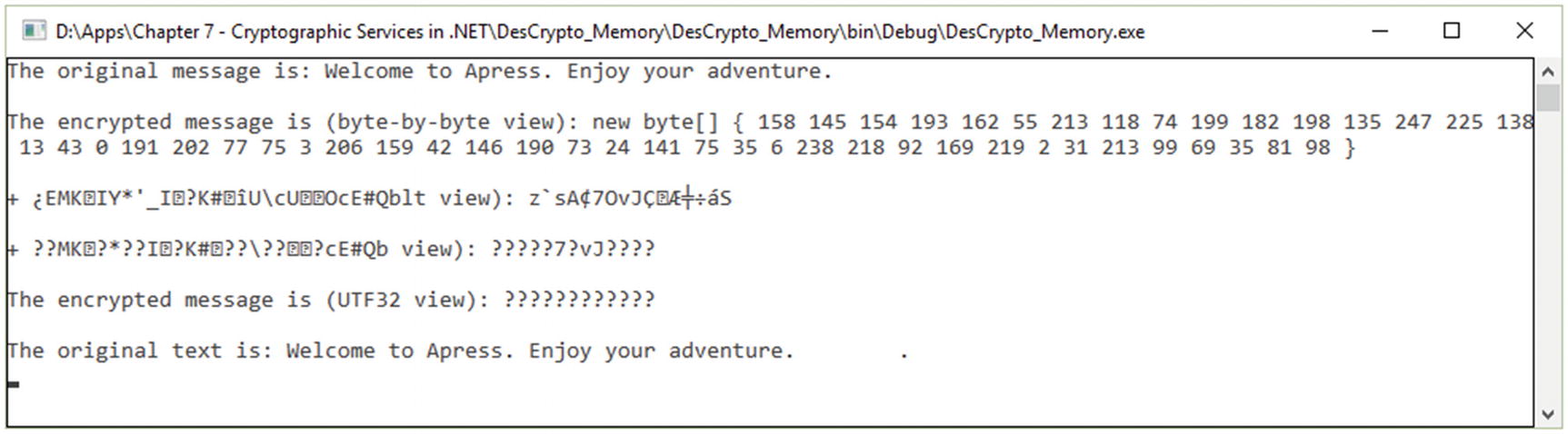
DES encryption and decryption in memory
Example of Implementation of the DES Algorithm Using DESCryptoServiceProvider
Implementation of DES Encryption and Decryption in Memory
Encryption Using a Public Key
Public key encryption uses a private key that must be stored secretly in such way that unauthorized parties or malicious users cannot access it. Also, it is uses a public key which can be made available to anyone. The relation between the public key and the private key is mathematically based. The data that is encrypted using the public key can only be decrypted using the private key. In this situation, the data that has been signed using the private key can be verified using only the public key.
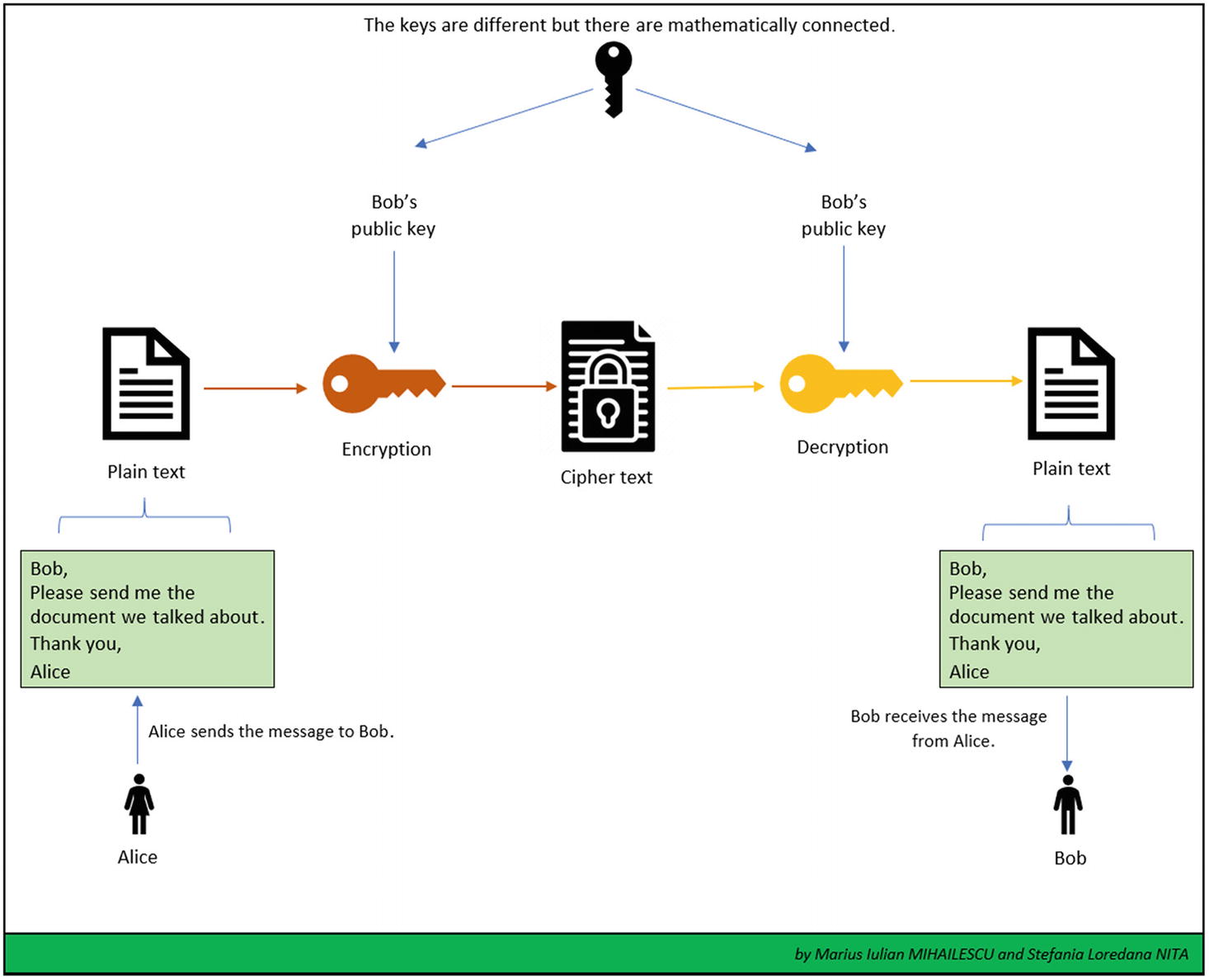
Public-key encryption
Algorithms based on a public key use a fixed buffer size. It is very important to mention that the secret key and algorithms based on it use a buffer that is represented as a variable and the size varies.
Regarding the chain of data, there is a difference between public-key algorithms and symmetric-key algorithms. Symmetric-key algorithms chain data together into streams, and public-key algorithms don’t have this ability. The streaming model is not the same for the asymmetric operations as for symmetric operations.
Encryption using a public key uses a larger space for the key representation. The space used by symmetric-key encryptions is much smaller compared with the public key encryptions.
Public keys are very easy to distribute because there is no need to have a security mechanism. If necessary, there are mechanisms to verify and check the identity of the sender.
To create a digital signature with the goal of verifying and checking the identity of the sender, public-key algorithms such as RSA and DSA can be used with success.
Regarding speed, public-key algorithms are very slow if we compare them with symmetric algorithms. They are designed in such way that no large amount of data can be encrypted. Thus, public-key algorithms are recommended only for a small amount of data.
DSACryptoServiceProvider [1]. The implementations are similar and they can be done in the same way as the ones from Listing 7-1, 7-2, or 7-3.
RSACryptoServiceProvider [2]. For an example of an implementation, see Listing 7-5 and Figure 7-8.
ECDiffieHellman [3]. The implementations are similar and they can be done in the same way as the ones from Listing 7-1, 7-2, or 7-3.
ECDiffieHellmanCng [4]. The implementations are similar and they can be done in the same way as the ones from Listing 7-1, 7-2, or 7-3.
ECDiffieHellamnCngPublicKey [5]. The implementations are similar and they can be done in the same way as the ones from Listing 7-1, 7-2, or 7-3.
ECDiffieHellmanKeyDerivationFunction [6]. The implementations are similar and they can be done in the same way as the ones from Listing 7-1, 7-2, or 7-3.
ECDsaCng [7]. For an example of an implementation of ECDSA (Elliptic Curve Digital Signature Algorithm), see Listing 7-5 .
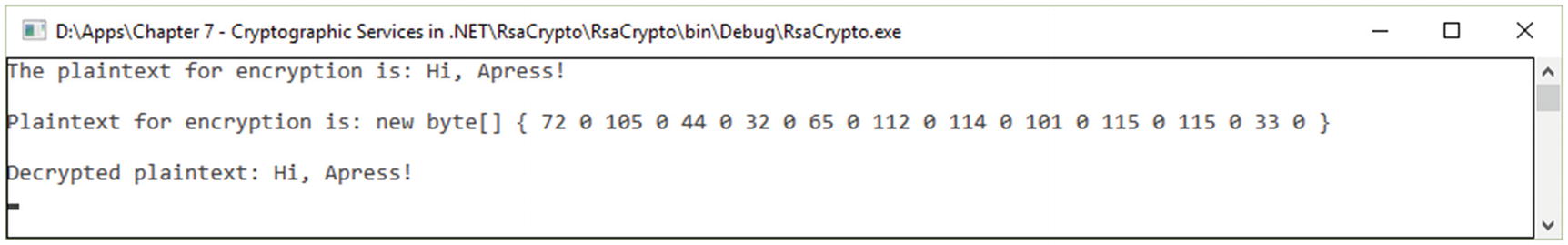
RSA example encryption
Implementation of RSA Using RSACryptoServiceProvider
Digital Signature
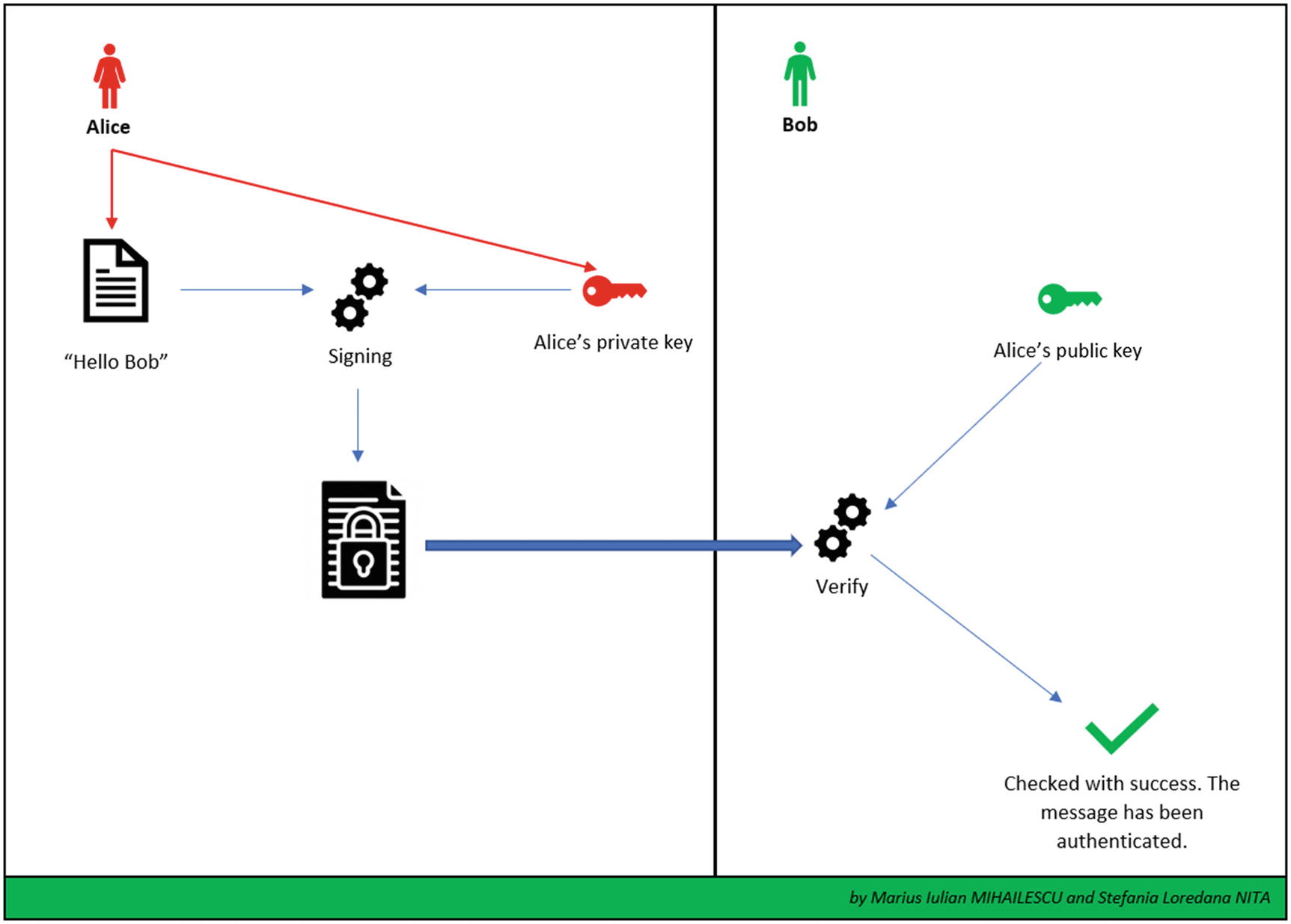
ECDsaCng example

Digital signature
Implementation of ECDsaCng
Hash Values
The purpose of a hash algorithm is to map binary values that are represented as having an arbitrary length to smaller binary values that have a fixed length. A hash value is represented as a numerical value that represents a specific piece of data.
RIPEMD160 Implementation

RIPEMD160 example with a hash value for an *.iso file
Example of SHA256 implementation
SHA256Managed Implementation
Random Number Generation
Many cryptographic operations are based on the generation of random numbers. As an example, let’s consider cryptographic keys that are required to be random as much as possible in such way that it will impossible to reproduce them.
The RNGCryptoServiceProvider class [20] provides a professional implementation of a cryptographic random number generation (RNG) based on the implementation that is provided by the cryptographic service provided (CSP).
ClickOnce Manifests
ClickOnce [21] is a deployment technology that provides the ability to create a self-updating windows-based application. It offers a minimal user interaction and it is as easy as possible to use.
ClickOnce technology is still used within small and medium businesses. There are challenges due to the security of the signatures and the collection of signatures. Consumer applications are largely developed in UWP or Win32 and use different technologies for the deployment process. Some internal business applications use different deployment technologies these days.
ManifestSignatureInformation class [22]. Used to obtain information related to the manifest signature. This can be achieved with the help of the VerifyMethod method. An example method for verifying the signature of a manifest can be seen in Listing 7-9.
ManifestKinds enumeration [23]. This enumeration is used to mention which manifests should be checked. The output of the checking process is represented by an enumeration value within SignatureVerificationResult enum type [24].
ManifestSignatureInformationCollection class [25]. The class provides guidance related to the read-only collection of the objects of the ManifestSignatureInformation class [26] for verifying the signatures.
Verifying the Signature with X509
StrongNameSignatureInformation class [27]. The class holds the (strong) name of the signature and its information for a specific manifest.
AuthenticodeSignatureInformation class [28]. Represents a special type of signature, called authenticode, which is contained together with the signature information for a specific manifest.
TimestampInformation class [29]. Gets the time stamp on an authenticode signature.
TrustStatus enum. Checks if an authenticode signature can be trusted or not .
Suite B Support
.NET Framework 3.5 offers support for Suite B , an important set of cryptographic algorithms published by the National Security Agency (NSA). In 2018, NSA replaced Suite B with the Commercial National Security Algorithm Suite (CNSA) [31].
Advanced Encryption Standard (AES) algorithm. Support for key sizes 128, 192, and 256.
Secure Hash Algorithm SHA-1, SHA-256, SHA-384, and SHA-512
Elliptic Curve Digital Signature Algorithm (ECDSA). There is support for 256-bit, 384-bit, and 521-bit curves.
Elliptic Curve Diffie-Hellman (ECDH) algorithm. There is support for 256-bit, 384-bit, and 521-bit curves. This is used for key exchanges and secret agreements.
Cryptography Next Generation Classes
The CNG classes offer support for managed wrappers related to native CNG operations and functions. It is very important to mention that CNG is the replacement for CryptoAPI. All of the classes contain “CNG” as part of their name. The main class or CNG wrapper is CngKey [32], which is a container class that contains an abstraction of the storage and the way the CNG keys will be used.
With the help of this class, we can store a public key or key pair in a secure way and have the possibility of referring to it based on a string name. Classes related to elliptic curves, such as ECDsaCng for signatures and ECDiffieHellmanCng [33] for encryption operations, can use CngKey instances [34].
Conclusion
The chapter covered the most important cryptographic services from the .NET Framework, starting with version 3.5. Professionals can perform complex implementation tasks of different cryptographic algorithms and providers.
Symmetric encryption key algorithms
Asymmetric encryption key algorithms
Digital signatures
Hash algorithms and working with their values
Random number generation
ClickOnce manifests and solutions for checking their identities
Suite B support and its main role
Bibliography
- [1]
DSACryptoServiceProvider Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.dsacryptoserviceprovider?view=netcore-3.1.
- [2]
RSACryptoServiceProvider Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.rsacryptoserviceprovider?view=netcore-3.1.
- [3]
ECDiffieHellman Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.ecdiffiehellman?view=netcore-3.1.
- [4]
ECDiffieHellmanCng Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.ecdiffiehellmancng?view=dotnet-plat-ext-3.1.
- [5]
ECDiffieHellmanCngPublicKey Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.ecdiffiehellmancngpublickey?view=dotnet-plat-ext-3.1.
- [6]
ECDiffieHellmanKeyDerivation Function Enum. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.ecdiffiehellmankeyderivationfunction?view=dotnet-plat-ext-3.1.
- [7]
ECDsaCng Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.ecdsacng?view=dotnet-plat-ext-3.1.
- [8]
DSACryptoServiceProvider Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.dsacryptoserviceprovider?view=netcore-3.1.
- [9]
RSACryptoServiceProvider Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.rsacryptoserviceprovider?view=netcore-3.1.
- [10]
ECDsa Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.ecdsa?view=netcore-3.1.
- [11]
ECDsaCng Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.ecdsacng?view=dotnet-plat-ext-3.1.
- [12]
HMACSHA1 Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.hmacsha1?view=netcore-3.1.
- [13]
MACTripleDES Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.mactripledes?view=netframework-4.8.
- [14]
MD5CryptoServiceProvider Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.md5cryptoserviceprovider?view=netcore-3.1.
- [15]
RIPEMD160 Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.ripemd160?view=netframework-4.8.
- [16]
SHA1Managed Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.sha1managed?view=netcore-3.1.
- [17]
SHA256ManagedClass. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.sha256managed?view=netcore-3.1.
- [18]
SHA384Managed Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.sha384managed?view=netcore-3.1.
- [19]
SHA512Managed Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.sha512managed?view=netcore-3.1.
- [20]
RNGCryptoServiceProvider Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.rngcryptoserviceprovider?view=netcore-3.1.
- [21]
ClickOnce Security and Deployment. Available online: https://docs.microsoft.com/en-us/visualstudio/deployment/clickonce-security-and-deployment?view=vs-2019.
- [22]
ManifestSignatureInformation Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.manifestsignatureinformation?view=netframework-4.8.
- [23]
ManifestKinds Enum. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.manifestkinds?view=netframework-4.8.
- [24]
SignatureVerificationResult Enum. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.signatureverificationresult?view=netframework-4.8.
- [25]
ManifestSignatureInformationCollection Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.manifestsignatureinformationcollection?view=netframework-4.8.
- [26]
ManifestSignatureInformation Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.manifestsignatureinformation?view=netframework-4.8.
- [27]
StrongNameSignaureInformation Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.strongnamesignatureinformation?view=netframework-4.8.
- [28]
AuthenticodeSignatureInformation Class. Available online : https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.x509certificates.authenticodesignatureinformation?view=netframework-4.8.
- [29]
TimestampInformation Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.x509certificates.timestampinformation?view=netframework-4.8.
- [30]
TrustStatus Enum. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.x509certificates.truststatus?view=netframework-4.8.
- [31]
Commercial National Security Algorithm. Available online: https://apps.nsa.gov/iaarchive/programs/iad-initiatives/cnsa-suite.cfm.
- [32]
CngKey Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.cngkey?view=dotnet-plat-ext-3.1.
- [33]
ECDiffieHellmanCng Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.ecdiffiehellmancng?view=dotnet-plat-ext-3.1.
- [34]
CngKey Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.cngkey?view=dotnet-plat-ext-3.1.
- [35]
CngProvider Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.cngprovider?view=dotnet-plat-ext-3.1.
- [36]
CngAlgorithm Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.cngalgorithm?view=dotnet-plat-ext-3.1.
- [37]
CngProperty Struct. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.cngproperty?view=dotnet-plat-ext-3.1.
- [38]
AesManaged Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.aesmanaged?view=netcore-3.1.
- [39]
DesCryptoServiceProvider Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.aesmanaged?view=netcore-3.1.
- [40]
RC2CryptoServiceProvider Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.aesmanaged?view=netcore-3.1.
- [41]
RijndelManaged Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.rijndaelmanaged?view=netcore-3.1.
- [42]
TripleDESCryptoService Provider Class. Available online: https://docs.microsoft.com/en-us/dotnet/api/system.security.cryptography.tripledescryptoserviceprovider?view=netcore-3.1.
