In this chapter, we want to propose a methodology for cryptanalysis methods in general and how to apply it in a quick and efficient way. This method is for classic and actual (modern) cryptography/cryptanalysis algorithms and methods. Quantum cryptography is not included at this moment.
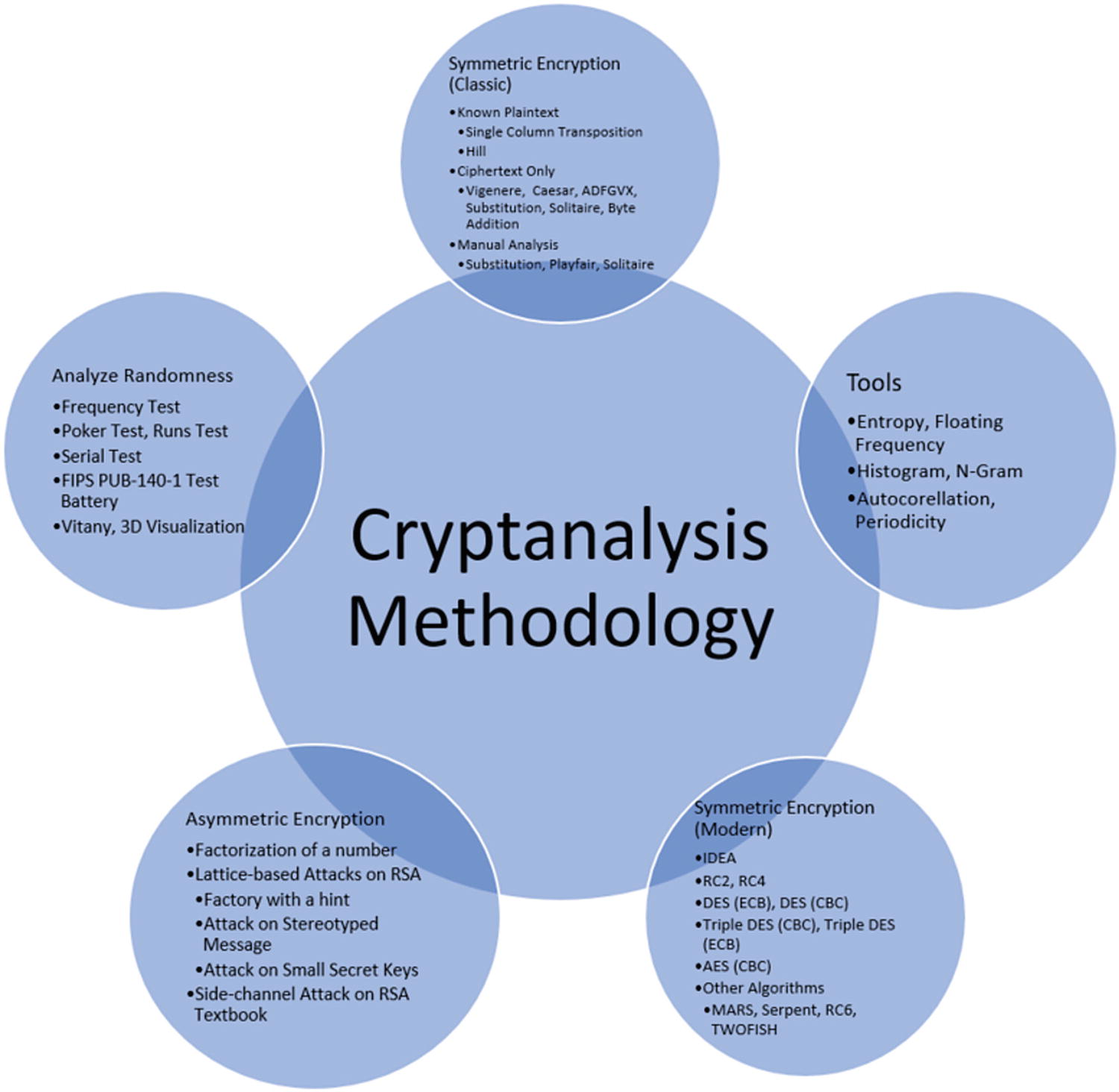
Cryptanalysis methodology
Implementing cryptanalysis methods is a very tricky task to achieve if you don’t have the proper information about the cryptographic method. This being said, the cryptanalysis process consists of two general steps. Step 1 consists of identifying what kind of cryptanalysis should be performed, and Step 2 what we know about cryptography algorithms. Based on these two steps, we can move on to Step 3 for building a proper attack model and Step 4 for choosing the proper tools.
Step 1. What kind of cryptanalysis should be performed? This is where the cryptanalyst decides, together with their business environment, what role they will play: a legal and authorized cryptanalyst (ethical hacker) or a malicious one (cracker). Once they decide their role, they move to Step 2.
Step 2. If they are a legitimate cryptanalyst, there are two things they should know before getting started: the cryptography algorithm and the cryptographic key . According to some cryptanalysts, this is not a necessary requirement but in some cases it will be very useful to know. Once these two things are known, they can easily perform cryptanalysis methods and test the security of the business.
Ciphertext-only attack
Known-plaintext attack
Chosen-plaintext attack
- Chosen-ciphertext attack
Adaptive chosen-ciphertext attack
Indifferent chosen-ciphertext attack
Penetration tools: Kali Linux, Parrot Security, BackBox
Forensics: DEFT, CAINE, BlackArch, Matriux
Databases: sqlmap (standalone version), Metasploit framework (standalone version), VulDB
Web and network: Wireshark, Nmap, Nessus, Burp Suite, Nikto, OpenVas
Other tools: CryptTool (very useful and amazing tool)
The tools mentioned above represent only a selection of those that are very powerful and can produce the desired result.
Ciphertext-Only Attack (COA)
COA is one of the weakest attacks due to the fact that it can be easily used by the cryptanalyst because he just encoded the message.
The attacker (cryptanalyst) will have access to a set of ciphertexts. The attack is deemed successful if the corresponding plaintexts are deduced together with the key.
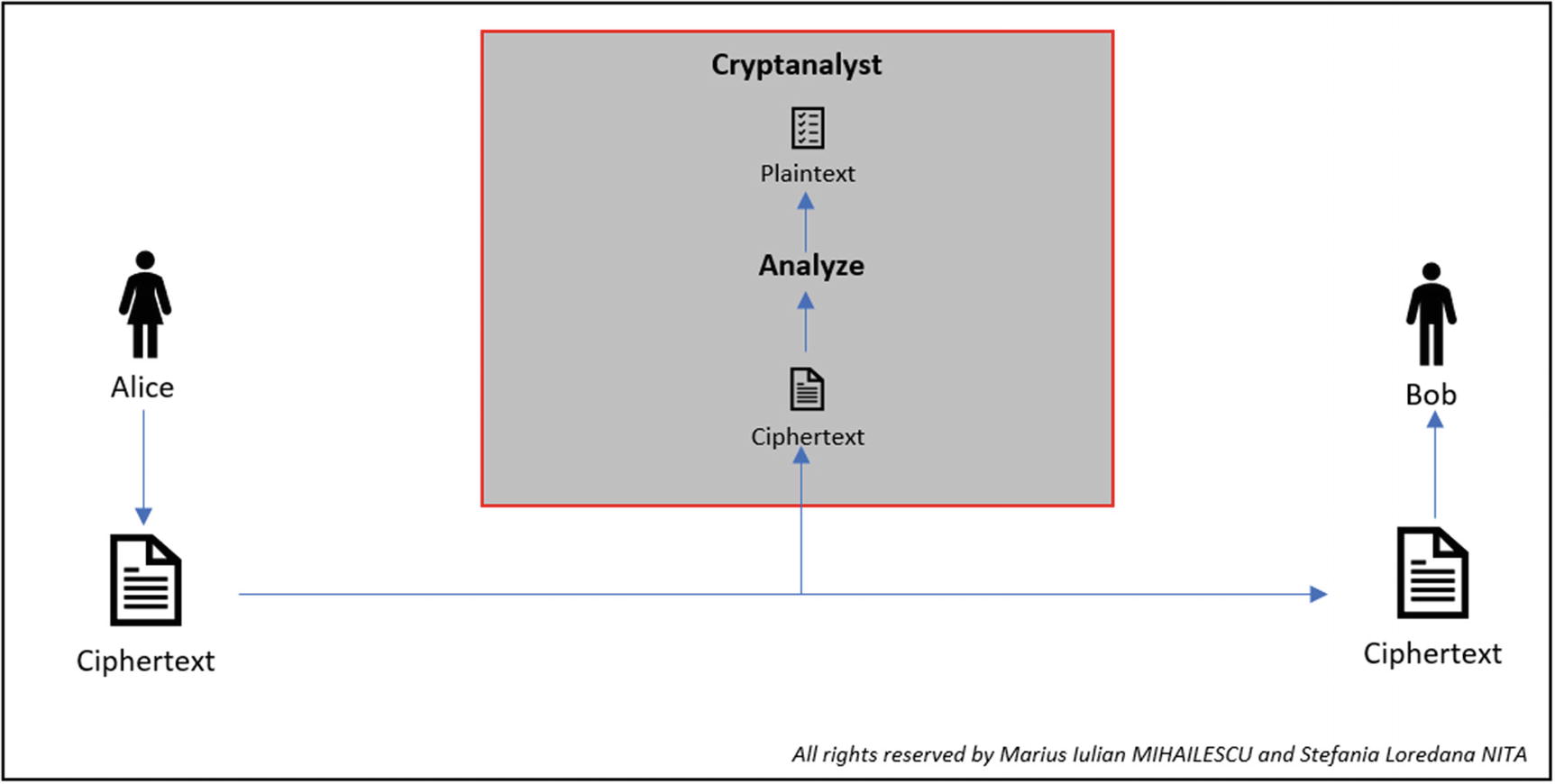
COA representation
Known-Plaintext Attack (KPA)
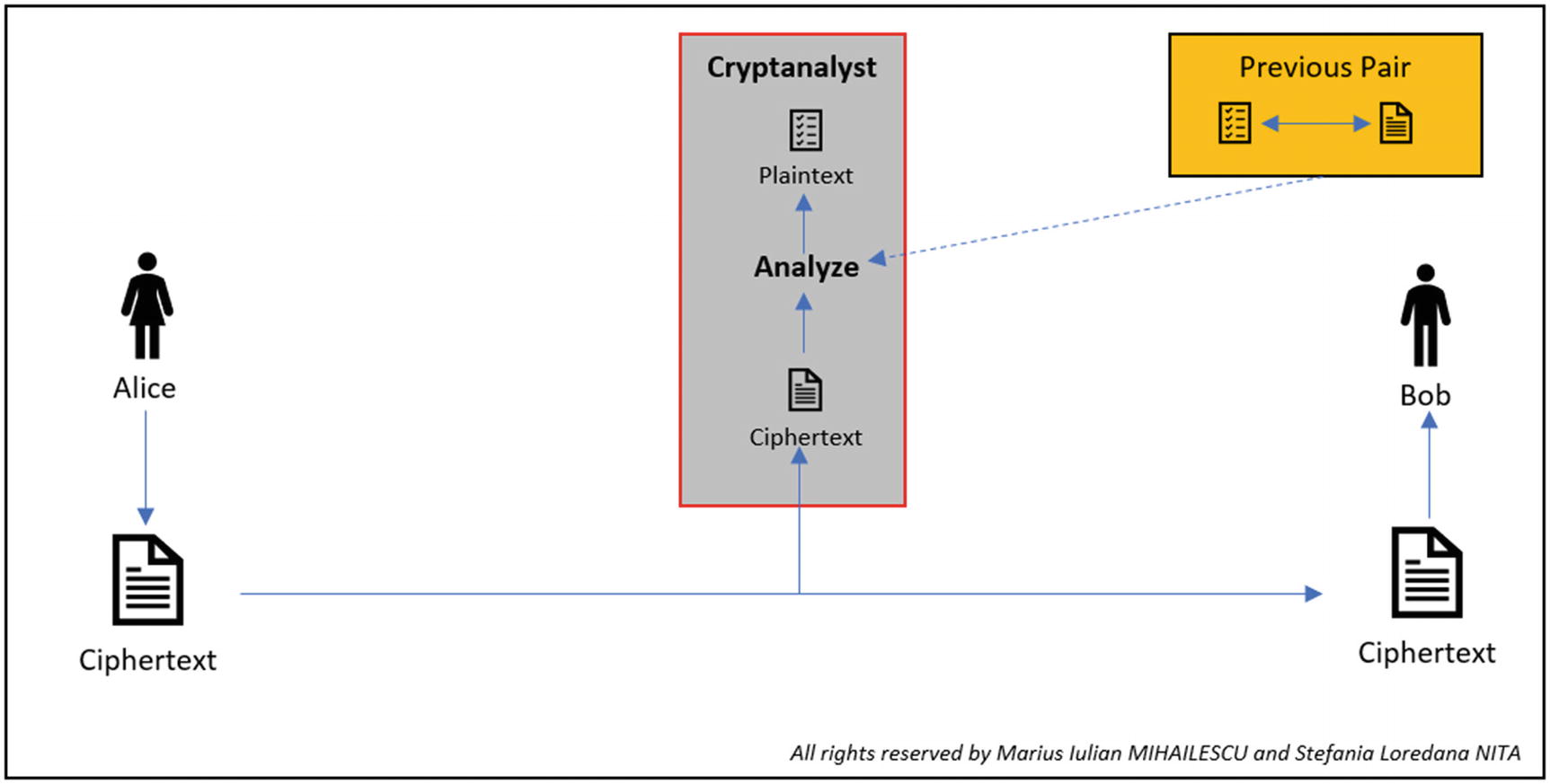
KPA representation
The cryptanalyst will select the plaintext, but they will notice the pair formed from plaintext and ciphertext. The chance of success is better compared to COA. Simple ciphers are quite vulnerable to this attack.
Chosen-Plaintext Attack (CPA)
The cryptanalyst selects the plaintext that has been send using an encryption algorithm and he observes how the ciphertext is generated. This can be seen as an active model in which the cryptanalyst has the chance to select the plaintext and to realize the encryption.
Having the possibility to choose any plaintext, the cryptanalyst can also observe details about the ciphertext, which gives him a strong advantage to understand how the algorithm works inside and the chance to get possession of the secret key.
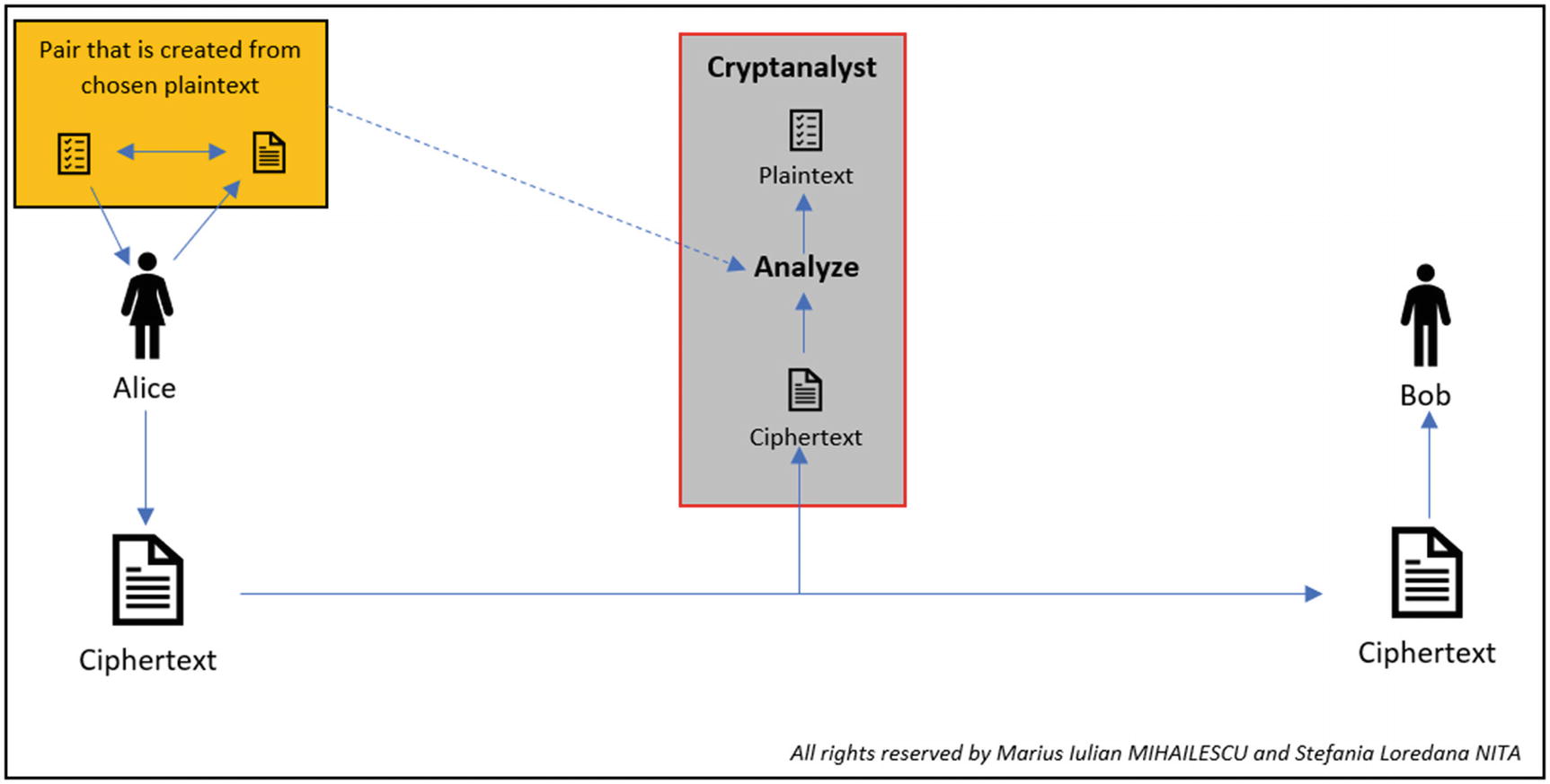
CPA representation
Automatic Generation of Random Keys

The keys and possible passwords generated. We choose three characters for short time process purpose only
Chosen-Ciphertext Attack (CCA)

CCA representation
Conclusion
Have a good understanding of the attack models
Follow a simple and straightforward methodology for knowing where you are within the cryptanalysis process
Simulate and generate a database with keys and possible passwords
Bibliography
- [1]
Abu Yusuf Yaqub ibn Ishaq al-Sabbah Al-Kindi www.trincoll.edu/depts/phil/philo/phils/muslim/kindi.html.
- [2]
Philosophers: Yaqub Ibn Ishaq al-Kindi Kennedy-Day, K. al-Kindi, Abu Yusuf Ya‘qub ibn Ishaq (d. c.866–73). www.muslimphilosophy.com/ip/kin.html.
- [3]
Ahmad Fouad Al-Ehwany, “Al-Kindi” in A History of Muslim Philosophy Volume 1. New Delhi: Low Price Publications. pp. 421-434. 1961.
- [4]
Ismail R. Al-Faruqi and Lois Lamya al-Faruqi, Cultural Atlas of Islam, New York: Macmillan Publishing Company. pp. 305-306. 1986 Encyclopaedia Britannica, Inc. (1969). Encyclopaedia Britannica. Chicago: William Benton.
- [5]
J.J. O’Connor and E.F Robertson, E.F. Abu Yusuf Yaqub ibn Ishaq al-Sabbah Al-Kindi. 1999.
