As organizations move away from cabled networks in favor of communicating wirelessly, a host of security concerns need to be addressed. Wireless LANs using radio waves are easier to intercept than LANs that use physical wires. Go to a hotel, an airport, or the local McDonald’s. Many organizations now provide wireless connectivity to their customers. Unfortunately, the ease of use provided also come with increased risks. An attacker can be outside of an organization compromising a wireless network. In this chapter, you will learn about different types of wireless networks, authentication methods, and the importance of wireless encryption.
- 1.
Identify various types of wireless networks.
- 2.
Identify authentication methods and types of wireless encryption.
- 3.
Explain the methodology of wireless hacking.
- 4.
Apply wireless commands and tools.
- 5.
Examine plaintext wireless traffic, wired equivalent privacy (WEP) traffic, and Wi-Fi protected access (WPA) traffic.
Types of Wireless Networks
Peer-to-peer network : In a peer-to-peer network, every computer can communicate directly with other computers on the same network without going through an access point. They may not be able to access the wired LAN, though.
Extension to a wired network : If an access point is placed between the wired network and the wireless devices, the wired network is extended. The access point connects the wireless LAN to the wired LAN, so wireless devices can access LAN resources.
Multiple access points : Multiple access points can be used to cover a larger area, enabling a user to seamlessly move throughout the coverage.
LAN-to-LAN wireless network: LAN-to-LAN wireless networks use access points to provide wireless connectivity between local computers on one network to computers on a different network.
Wireless Standards
Range of Wireless Standards Available
Specification | Speed | Frequency Range |
|---|---|---|
802.11a | 54 Mbps | 5.2 GHz |
802.11b | 11 Mbps | 2.4 GHz |
802.11g | 11 Mbps/54 Mbps | 2.4 GHz |
802.11i | 11 Mbps/54 Mbps | 2.4 GHz |
802.11n | 124-248 Mbps | 2.4 GHz/5.2 GHz |
Service Set Identifier
An SSID is a unique name given to the wireless local area network (WLAN) that can be up to 32 characters long. All devices and access points that are part of the wireless LAN must use the same SSID. SSIDs do not provide security for the WLAN since it can be sniffed in plaintext. Many devices are shipped with default SSIDs.
802.1x Authentication Process
The IEEE 802.1x standard defines ways used to authenticate a user prior to granting access to network and the authentication server, for example a RADIUS server. 802.1X acts through an intermediate device, like an edge switch, allowing ports to transmit normal traffic if the connection is appropriately authenticated. This avoids unauthorized clients from accessing the publicly available ports on a switch, keeping unauthorized users out of a LAN.
Remote Authentication Dial in User Service, or RADIUS, is a client/server protocol that uses port 1813 to offer centralized authentication, authorization, and accounting for computers to connect and use the available network services.
- 1.
The AP issues a challenge to a wireless client.
- 2.
The wireless client responds with its identity.
- 3.
The AP forwards the identity to the RADIUS server.
- 4.
The RADIUS server sends a request to the client via the AP.
- 5.
The client responds to the RADIUS server with its credentials via the AP.
- 6.
The RADIUS server sends an encrypted authentication key if the credentials are good.
- 7.
The AP transmits to the client.

The 802.1x authentication process
802.11 Vulnerabilities
Beacon frames broadcast the SSID so that users can locate the network. Any station can impersonate another station or access point. An attacker can interfere with the authentication and association, which can force the stations to redo the authentication and association process.
Access points have capabilities for MAC address filtering. However, the MAC address doesn’t provide a strong security mechanism since it can be observed and replicated. MAC addresses appear in plaintext. There is a specific MAC address on each network card and that address can be modified via the ifconfig command.
Wired Equivalent Privacy
A wired equivalent privacy is designed to provide a WLAN with a level of security comparable with that of a wired LAN and is a stream cipher that uses RC4 (www.geeksforgeeks.org/rc4-encryption-algorithm/). The input to the stream cipher algorithm is an initialization vector (IV) sent in plaintext and a secret key. The total length for the IV and the secret key is either 64 or 128 bits. A busy access point can use all available IV values (224) within hours, and then the IV values are reused. There are two issues to consider: a cyclic redundancy check 32 bit (CRC32) is not sufficient to ensure the cryptographic integrity of a packet, and it is vulnerable to dictionary attacks.
Wi-Fi Protected Access 2
Wi-Fi Protected Access 2 (WPA2) utilizes a 256-bit preshared key from 8 to 63 bytes long. When users have passphrases that are less than 20 characters, they are vulnerable to an offline dictionary attack. WPA2 offers two modes of operation: WPA2-Personal and WPA2-Enterprise. WPA2-Personal uses a setup password while WPA2-Enterprise uses a server to confirm the user. WPA2 access implements the AES encryption algorithm to provide government-grade security.
Temporal Key Integrity Protocol
Temporal Key Integrity Protocol (TKIP) is an element of the IEEE 802.11i encryption standard. It is the designated successor to WEP and eliminates the drawbacks that WEP had without requiring the replacement of equipment. TKIP implements key mixing, which means that the secret key is combined with the initialization vector before passing it on to the stream cipher.
Changes from WEP to TKIP include adding a message integrity protocol to prevent tampering. TKIP changed the rules of IV selection so it now changes the encryption key for every time frame. Other changes are an increase in the size of IV to 48 bits and a new mechanism to distribute and change broadcast keys.
Four-Way Handshake

Four-way handshake
Hacking Wireless Networks
A laptop running Network Stumbler, passive scanners (Kismet or KisMAC), or active beacon scanners (MacStumbler or iStumbler) can be used to hack a wireless network. Network Stumbler or Kismet will tell an attacker how a network is encrypted.
Rogue Access Points
Unauthorized access points can allow anyone with a wireless device onto the network. Access points can be cloaked by putting them in stealth mode. Cloaked access points are not detected by active scanners like Network Stumbler. A passive scanner is required to detect a cloaked access point. The methods used to locate access points include requesting a beacon and sniffing the air. Tools that can be used to cloak access points include Fakeap, Network Stumbler, and MiniStumbler.
Iwconfig Command

Managed mode

Monitor mode
Airodump -ng Command
Aireplay -ng Command

Aireplay-ng command

The aireplay–ng command used in a deauthentication attack
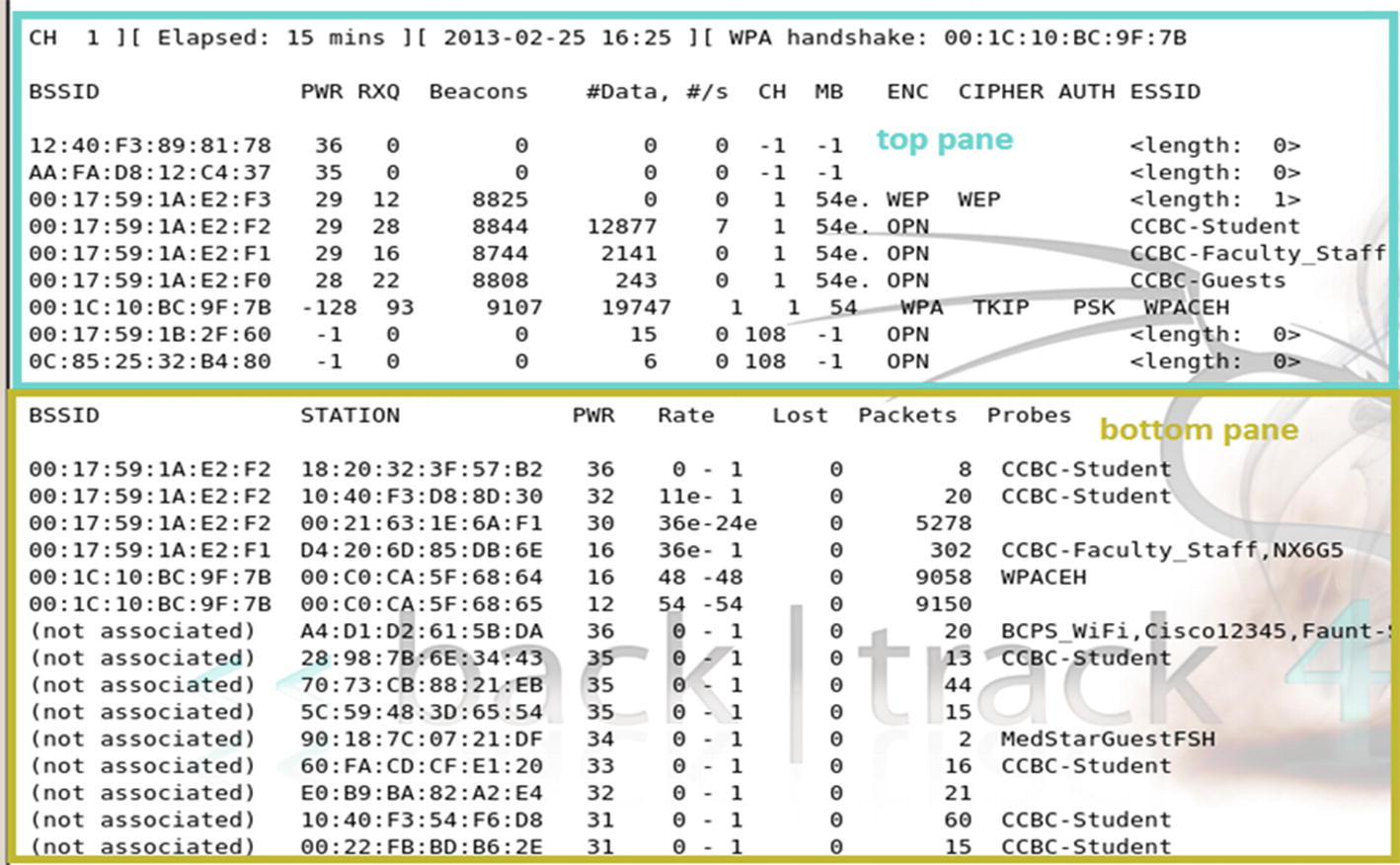
Monitoring an Unsecured WLAN

FTP traffic capture

Following the TCP stream
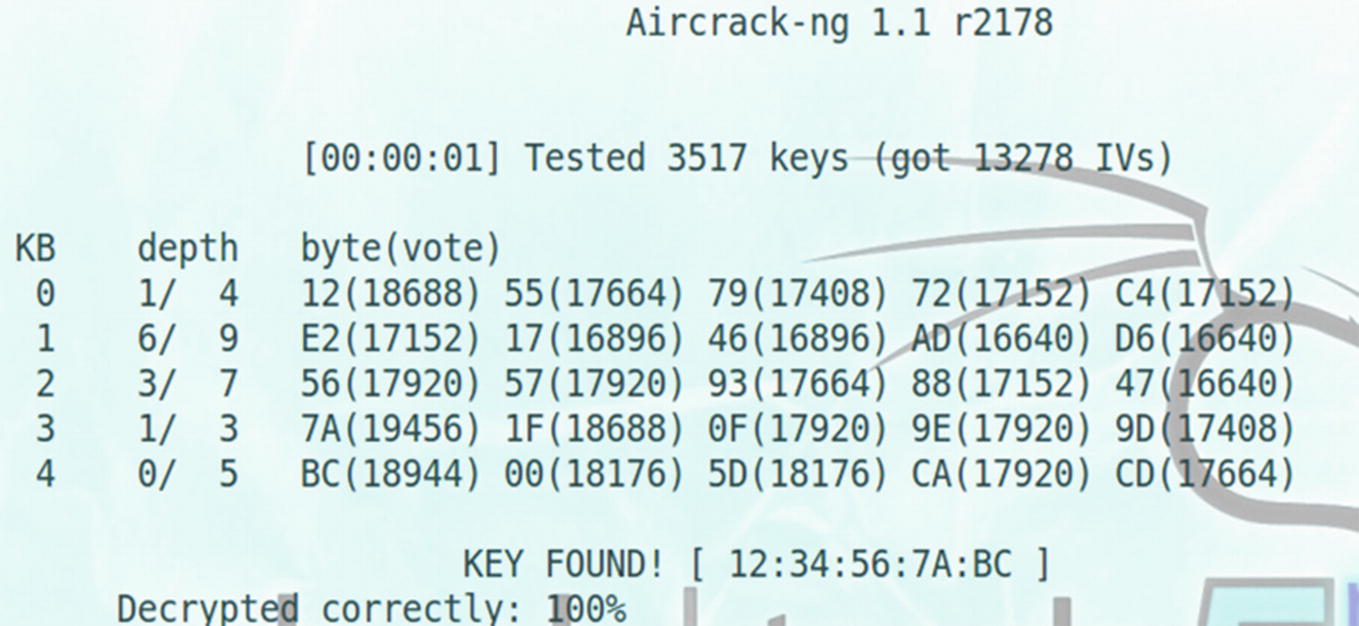
Using Aircrack –ng
Summary
As the number of organizations using wireless LANs increases, so too do the risks that can compromise a network. In this chapter, you reviewed the various types of wireless networks, authentication methods, and wireless encryption. You learned the importance of increasing security to protect systems due to the concerns associated with the use of wireless LANS.