There was a reviewer a while back who wrote that my pictures didn’t have any beginning or any end. He didn’t mean it as a compliment, but it was. It was a fine compliment.
—Jackson Pollock
Disruptive technology means that we keep the benefits of the existing things and enjoy the new tech’s advantages. Let’s take electric cars as an example. They provide all the benefits of traditional gasoline cars – they can drive, have a somewhat comparable price, and are still as safe and convenient as the best “dirty” cars. But on top of that, electric cars are “green” and less noisy. If we follow this logic, which can be observed with any other innovative technology, the new payment systems based on crypto must provide all the benefits of the traditional banking system and plastic cards, even before we get decentralization, universal access, and other new features.
If we want cryptocurrencies to go mainstream as a new payment system, we must ensure some degree of privacy currently provided by corporate systems such as Visa or PayPal. The last thing we want is to publish our credit card statements for anyone to study, but this is precisely what public ledgers of most cryptocurrencies do!
Fortunately, there is a solution to this problem: privacy coins based on unique privacy-centric blockchain technologies. There are three most bold designs and implementations of privacy coins: Zcash (ZEC),1 Dash (DASH),2 and Monero (XMR).3 Perhaps, Monero is the most outstanding one as it has a stunning design.
Why Monero Is Important
In my opinion, Monero is the second most important crypto innovation since Bitcoin. Some experts can argue, of course, because there are other inventions such as Ethereum’s “supercomputer.” They are also right since those inventions are very important for the evolution of crypto. However, let’s remember the original purpose of Bitcoin, the very first cryptocurrency. I will cite the Bitcoin white paper once again: “electronic payment system based on cryptographic proof instead of trust, allowing any two willing parties to transact directly with each other without a trusted third party.”4 The keyword here is the payment system . That’s the original purpose of Bitcoin and all other cryptocurrencies – replacing traditional centralized payment technologies with the decentralized alternative.
Bitcoin or Ethereum transaction records are available publicly, in clear text. Despite some degree of anonymity, it is not impossible to establish a link between a wallet and the identity of its owner. That’s why Monero, as the most successful privacy-centric cryptocurrency, is a considerable step toward broad consumer and business acceptance. Since buyers and merchants will never agree to “publish” their day-to-day transaction records, perhaps privacy-centric crypto is the only way to go mainstream.
In a chapter about cryptography, I told you that explaining cryptography without math is very difficult. I was afraid of even thinking about explaining Monero. It sounds like it’s impossible to talk about Monero without higher math, tough cryptography, and, finally, some source code fragments. And yet I will try at least because I believe that everyone who wants to use crypto in any way needs to know and understand privacy coins, especially Monero.
CryptoNote
Not surprisingly , Monero is not the only and not the first privacy-centric cryptocurrency. iPhone wasn’t the first smartphone. Tesla wasn’t the first electric car. And so in crypto, there were and still are other attempts to create privacy coins, even before Monero. Like how we count the era of blockchain and cryptocurrencies from Satoshi Nakamoto’s white paper, we can measure the age of privacy coins from the CryptoNote white paper.5 Like the legendary Bitcoin proposal, the CryptoNote manuscript was authored by an incognito person, with the pseudonym Nicolas van Saberhagen, and published on October 17, 2013. While we don’t know who this person (or group?) is, no one can stop us from speculating. Maybe Satoshi and Nicolas are the same people?

A timeline depicts the release dates of various versions of crypto notes and Monero origins from July 2012 to January 2015.
The forking tree of CryptoNote-based coins. Source: ihodl.com 7
So, when Sergei started to immerse himself into the jungle of the original source code, he found something he did not like. According to Sergei, his findings pointed out that Russian secret intelligence services had created the Monero source code. He refused to provide the proof and almost immediately aborted his participation in the project. Sergei said he does not want to be involved as he fears for his life. Maybe it was simply paranoia, which is a “side effect” of many talented people. I don’t know. I am just transmitting the story to you as it is. What I know for sure is that Monero reliably keeps all its secrets!
Now let’s go back to the CryptoNote white paper. The document defines several principles of a new cryptocurrency that was supposed to fix Bitcoin’s flaws. While it’s mainly focused on privacy features like “untraceable transactions” and “unlikeable payments,” it’s also proposed other exciting innovations such as a new proof-of-work mining algorithm and a different emission schedule. Let’s review the privacy features as those are things we mainly like Monero for.
Untraceability and Unlinkability
To understand what untraceability and unlinkability are, let’s look at the Bitcoin blockchain one more time. On a very high level, as we reviewed previously, Bitcoin transactions consist of inputs, which are outputs of the sender’s previous transactions, and outputs, which the recipient can spend in the future. The sender wallet’s private key digitally signs the inputs and outputs, so the funds’ movements can be traced throughout the blockchain. The outputs are sent to a specific recipient address (derived from the recipient wallet’s public key), so they can be linked to the recipient’s wallet.
The transaction can be more complex because a single bitcoin wallet can generate multiple addresses. A recipient who wants to hide his identity can generate a new wallet address for each new incoming transaction. Those addresses can only be linked if you know the wallet’s private key, which means the outside observer won’t be able to link those multiple transaction outputs to a single recipient’s wallet. At a glance, this feature looks like an excellent security and privacy mechanism, but the idyll breaks quickly when it comes to the need to spend those outputs.
When such a user, who received bitcoins through multiple transactions using unique addresses, wants to spend, they need to create a new transaction that includes these various outputs as new inputs signed by the same private key. This fact explicitly points to the ownership, linking previously unlinked transactions to the user wallet .
Cryptographic Monero Technologies
Cryptographic Techniques Used in Monero
Cryptographic Technique | Type | Privacy or Security Feature | What It Does |
|---|---|---|---|
Stealth addresses | Privacy | Protecting identity of recipient | Hiding (encrypting) the recipient’s address8 |
Ring signatures | Privacy | Protecting identity of the sender | Hiding the sender’s address by adding multiple “fake” senders9 |
Pedersen commitments | Privacy | Protecting transaction amount from public view | Hiding transaction amount by replacing it with equations that can be still publicly validated without knowing the exact amount10 |
Range proofs (recently replaced by bulletproofs) | Security | Protecting transaction amount from public view; preventing fraudulent transactions that generate funds | Allows the validator to make sure that transaction amount is not reversed (no new funds are generated)11 |
Key images | Security | Preventing double-spending | This technique allows users to spend their funds only once, although no one still can see the details of transactions12 |
Diffie-Hellman key exchange | Security and privacy | Used in encoding and decoding of the stealth address | Used to secretly communicate a shared secret between anonymous sender and recipient to secretly transmit the output that can be spent only by the recipient13 |
While the main three techniques – stealth addresses, ring signatures, and Pedersen commitments – ensure privacy, there are additional techniques, range proofs and key images, that are required to secure the transactions in addition to standard blockchain security measures such as digital signatures. These extra security controls are necessary because, unlike pseudonymous crypto such as Bitcoin, Monero hides important transaction details from observers, making it impossible to validate transactions using just digital signatures. Let’s review these techniques and see how they work together to create amazing technology.
View and Spend Keys
Before we move to privacy and security techniques, let’s see how Monero wallet addresses are different from Bitcoin and other cryptos. When you see a Monero address for the first time, you can immediately notice it is longer than a Bitcoin one.
This is because it consists of two public keys: the public view key and the public spend key . The senders use both these public keys when they create a transaction. The wallet owner uses the private view key to see the transactions. The private spend key is used to make transfers (spend).
Since transactions on the Monero blockchain are invisible to anyone besides their senders and recipients, the wallet owners can provide the private view key to someone if they want them to see their transactions, but without any risk of spending their funds. This feature, for example, can be used for audit purposes. But if you want to spend Monero coins, you have to have the private spend key.
Similar to Bitcoin, Monero keys and address can be generated from the mnemonic seed, so you can store your wallet offline (write it to a piece of paper) as a sequence of 25 English words, like this: gels adhesive corrode hawk iguana husband kitchens inmate geyser video sapling taunts razor essential abyss jewels sabotage aunt bifocals boyfriend knee hornet superior together adhesive. So, you can always restore your Monero wallet (both keys, the address, and all the transactions) as long as you keep those words.

A webpage depicts a notification on a Monero page. It shows the message when someone tries to check the transaction history.
This happens if you try to check the transaction history associated with the Monero address
Stealth Addresses
Not every Monero user today knows that the first versions of Monero, which were based mainly on the CryptoNote protocol, did not provide complete privacy. For example, transaction amounts were still visible. But protecting the recipient’s identity was the first, most obvious, and perhaps the easiest-to-understand privacy feature, allowing me to review it more thoroughly.

An illustration. Alice sends coins to Bob, creating a stealth address constructed from a public address and transaction public key. Bob decodes and determines that the transaction belongs to him.
Alice sends coins to Bob using a stealth address
To be more specific, what the sender Alice does when creating a transaction is encrypt the actual address of the recipient (A, B) with the one-time private key of the transaction r. There are two public keys, A and B (both taken from the actual recipient’s wallet address), and one private key, r (randomly generated by Alice), used to create the stealth address P. The public key from the randomly generated pair is added to the transaction as a transaction key R, in addition to the destination stealth address P.
Now, here is the very important part. To find the incoming transaction, the “invisible” recipient Bob needs to scan the entire blockchain and decipher the stealth addresses of each transaction using his private keys (a, b) and the public key of the transaction R. Bob uses his address (or more precisely, the two private keys that comprise his address – the view key a and the spend key b), the stealth address P, and the transaction key R to check whether the transaction belongs to him. Yes, this can be a very long and CPU power–consuming process, and that’s why the Monero wallet is very different from other cryptos.
But fortunately, there are techniques that are used to optimize the finding of transactions. For example, the Monero wallet does not scan the entire blockchain every time you launch it. Instead, it examines the recent transaction only and remembers where it stopped the scanning last time .
Ring Signatures

An illustration depicts six senders connected to a recipient. Sender 2 and the recipient are shaded dark, and senders 1, 3, 4, 5, and 6 are shaded light.
Ring signature – all senders look valid, but only one of them is real
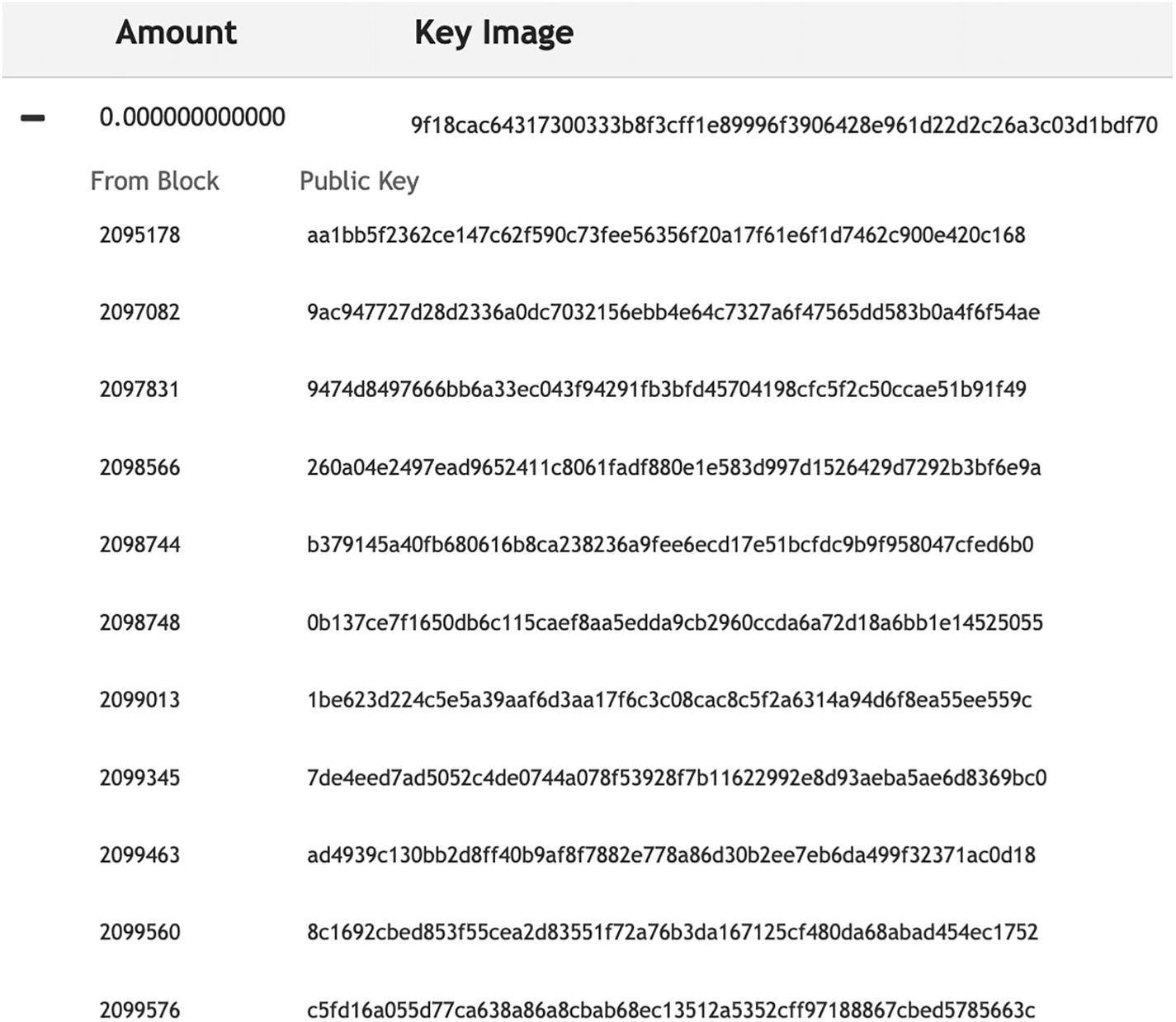
An image depicts 11 rows of entries under column labels, from block and public key. The image has two headers, namely, the amount and the key image.
Eleven outputs are included in the ring signature; only one of them is the real input
Only one of these public keys comes from the actual sender and is used as an input for the transaction. Remember that amounts are also confidential, so it doesn’t matter how much previous transactions contain.
You may say that since the actual sender is in the group, there is still an indirect reference to the sender’s identity. That’s true, but don’t forget that the recipient is also unknown. So, if we translate your Monero transaction to plain English, it will look like “someone, maybe it’s you, maybe not, send some unknown amount to someone unknown. Even if I suspect you are the sender, I cannot prove it because it can also be anyone from the group of eleven people.” Using this transaction’s output as an input, the next transaction will make this “knowledge” even more miserable. Another 11 senders will be added to the list of potential sources, which eventually wholly removes any traces of the authentic original sender.
Churning
So, in conjunction with stealth addresses, ring signatures provide solid privacy to both the sender and the recipient. Want to get it even stronger? Use the technique that is called churning – send your funds to yourself.14 This way, you increase the “distance” between the original sender and your current spendable output, adding more “fake” senders and stealth recipient addresses in the mid dle.
Pedersen Commitments and Range Proofs
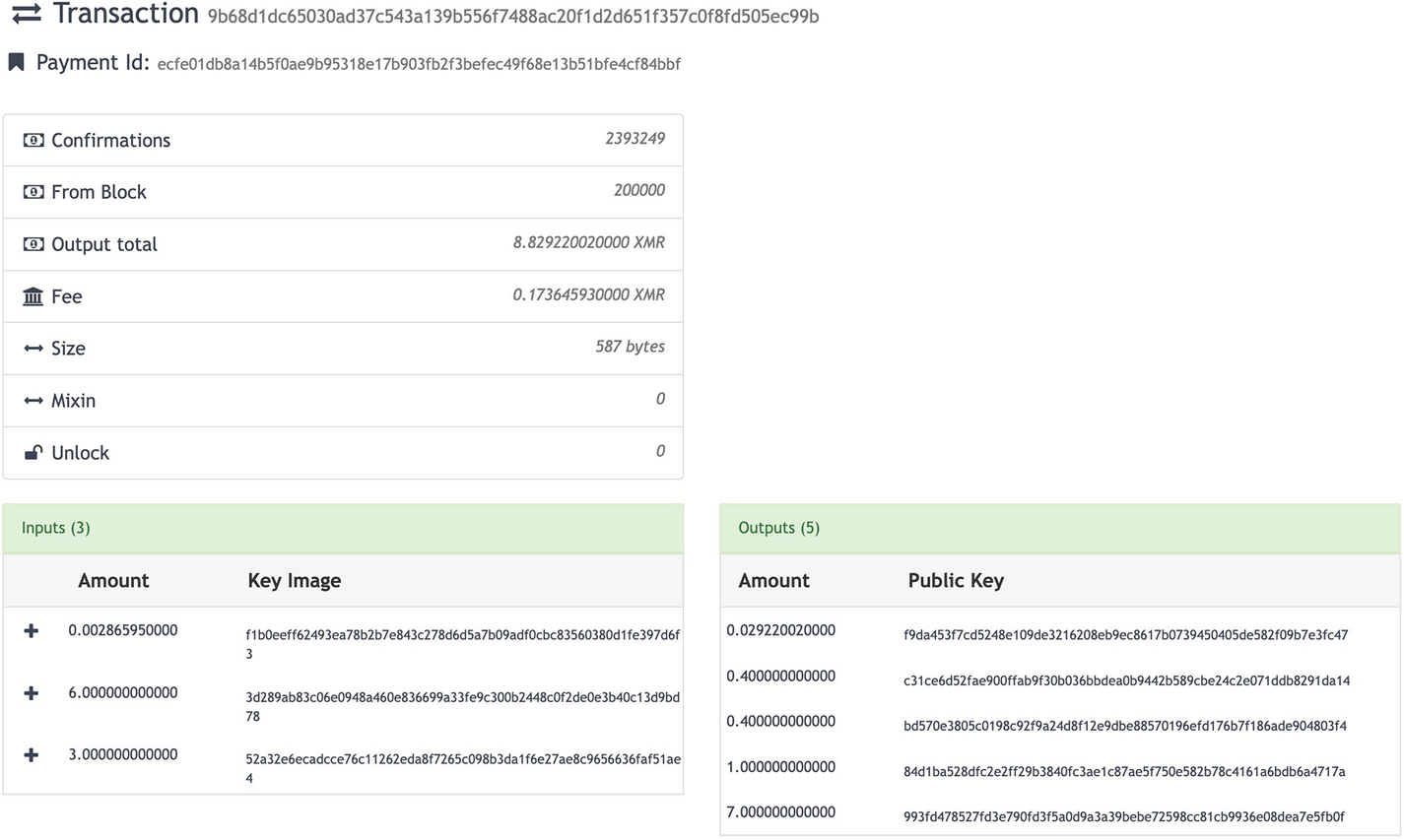
An image depicts the details of a transaction at the top. At the bottom is a list of input and output entries. The values of the amounts are visible.
Monero transaction before RingCT with visible amounts
Pedersen commitments were part of Ring Confidential Transactions, or RingCT, a cryptographic mechanism introduced in a white paper authored by Shen Noether.16 RingCT was first used in Monero in 2017. It is based on ring signatures described earlier.
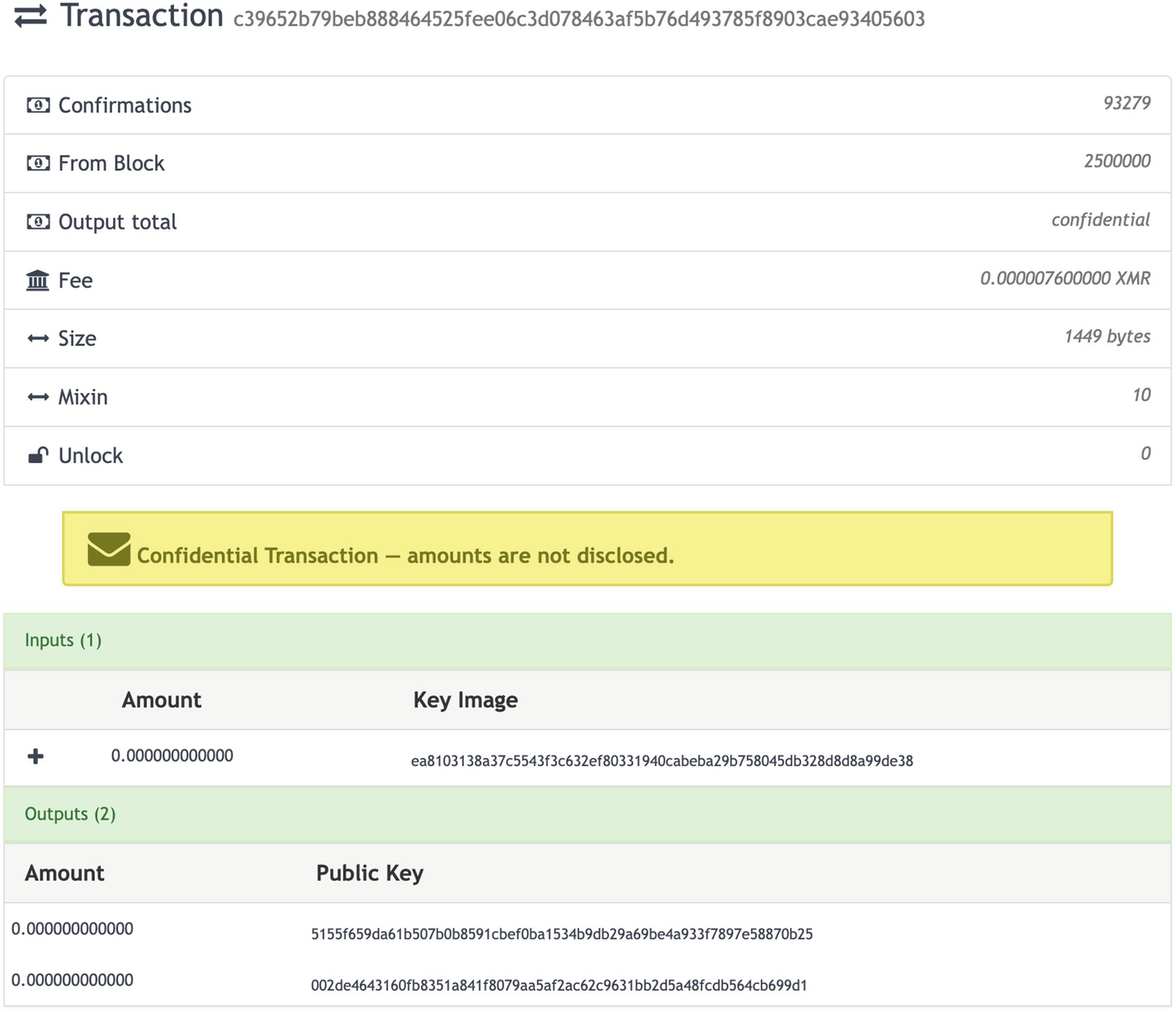
An image depicts the details of a transaction at the top. At the bottom is a list of input and output entries that have the amount and keys.
Monero transaction from block 2,500,000 with the hidden amount
Range proofs are needed to ensure that the committed amount is greater than zero and less than the limit to prevent fraudulent manipulations and create free money. Range proofs were recently replaced by more efficient bulletproofs, which do the same by doing it faster and using less transaction space, which is so valuable in blockchains.
Key Images
All these privacy and secrecy features are great, but if Monero transactions are so hidden, how does it protect itself from double-spending? The sender, the recipient, and the transaction amount are hidden. Yet, the network (i.e., essentially anyone who has a copy of the blockchain) should be able to validate the transaction and make sure the funds are not double-spent. The former is done through RingCT, which validates the sender and the amount without public disclosure. But the latter is done using an additional mechanism called key images.
Each Monero transaction includes a key image for each input used in the transaction (you can see the key image in Figure 6-7). The key image is generated using the one-time public key of the corresponding input and the secret shared between the sender and the recipient.
The key image is part of the ring signature and uniquely represents the public key associated with the output of the previous transaction that is being spent. If the input public key owner tries to spend the associated funds again, the resulting key image will be the same. Otherwise, the ring signature won’t be valid. So, before adding a new transaction to the blockchain, the validators (miner nodes) scan the entire blockchain to ensure the same key image was not present in previous transactions.
Learn More About Monero
I should say that I realize that understanding Monero is a challenging task that deserves a separate book. After reading this short chapter, I cannot imagine that you fully understand it, but at least I hope it gives you some starting point. If you want to learn more about Monero, you can find the list of references that I believe will save you some time you would otherwise spend googling.
Understanding Monero Cryptography, Privacy is an excellent description of Monero math which consists of two blog articles: Introduction (which talks about ECC, the particular curve, private and public “keys,” and a bonus section on how Monero addresses are generated) 18 and Part 2 – Stealth Addresses.19 Despite it being short, this is one of the best descriptions of Monero basics. Unfortunately, the author apparently lost interest in writing and discontinued the series, so the other essential elements of Monero’s design remained without his coverage.
Zero to Monero: A technical guide to a private digital currency for beginners, amateurs, and experts:20 This is a free book, which is the complete Monero reference, but I warn you: it has a lot of heavy math… If you are not afraid of math, this book is for you. Otherwise, the following one will be more useful to you.
Mastering Monero: The future of private transactions:21 This is also a free book, very detailed, but unlike Zero to Monero, it has a minimum amount of math required for understanding. Thus, it is more suitable for nonmathematician readers.
Finally, Table 6-1, which contains the list of cryptographic techniques used in Monero, has references for each entry that best describes the corresponding technology.
What’s Next?
I think the emergence of Monero in its importance is not inferior to the invention of Bitcoin. This becomes especially obvious when you look at crypto as a payment system that must compete with plastic cards, which have no intention to give up their positions anytime soon. After all, if we seriously consider cryptocurrencies as an alternative to plastic cards, it is clear that no one will use a coin that exposes all our financial operations to the public. To continue this discussion, the next chapter is all about the primary purpose of crypto: processing payments.
Crypto payments are very different from cash and plastic cards that most people still use these days. If crypto technology is so wonderful, why haven’t we abandoned our leather wallets and switched to paying with crypto yet? I will answer this question in the next chapter, which will help transition to the next part of this book: Using Crypto. You will also learn how to spend Bitcoin and other coins and tokens in places that would not seem to accept crypto at first glance.
